Deploy vSRX Virtual Firewall from the Azure CLI
Starting in Junos OS Release 15.1X49-D80 and Junos OS Release 17.3R1, you can deploy the vSRX Virtual Firewall from the Azure CLI and customize the vSRX Virtual Firewall VM deployment settings and dependencies based on your network requirements in Microsoft Azure Cloud.
Use the following procedure to deploy and configure vSRX Virtual Firewall as a virtual security appliance in a Microsoft Azure virtual network from the Azure CLI. In this procedure, you use the Azure CLI running in Azure Resource Manager (ARM) mode.
Be sure you have an account for and a subscription to Microsoft Azure before deploying the vSRX Virtual Firewall to Azure (see Microsoft Azure).
If you do not have an Azure subscription, then you can create a free account before you begin. See the Microsoft Azure website for more details.
From the Azure portal, you must first manually deploy the vSRX Virtual Firewall image (only once) by using either the vSRX Next Generation Firewall (BYOL) or the vSRX Next Generation Firewall (PAYG) SKU to accept the EULA terms. This is a requirement before you can deploy the vSRX Virtual Firewall image from the Azure CLI. By default, the Azure portal deployment tool uses vSRX Next Generation Firewall (BYOL) SKU as the source image. Use your Microsoft account username and password to log into the Microsoft Azure portal.
You will encounter a MarketplacePurchaseEligibilityFailed error if do not first accept the EULA terms for the vSRX Virtual Firewall image in the Azure portal before attempting to deploy the vSRX Virtual Firewall image from the Azure CLI.
Install the Microsoft Azure CLI
To install and log in to the Microsoft Azure CLI:
Download the vSRX Virtual Firewall Deployment Tools
Juniper Networks provides a set of scripts, templates, parameter files, and configuration files in Juniper’s GitHub repository. These tools are intended to help simplify the deployment of the vSRX Virtual Firewall to Azure when using the Azure CLI.
For background information on the scripts, templates, parameter files, and configuration files, see Before You Deploy vSRX Using the Azure CLI.
To download the vSRX Virtual Firewall deployment tools:
Change Parameter Values in the vSRX Virtual Firewall.parameter.json File
In the vsrx.parameters.json file, you need to modify parameter values specific to your vSRX Virtual Firewall deployment in Microsoft Azure. These parameters are used as part of the automatic deployment performed by the deploy-azure-vsrx.sh script.
Keep in mind that by default vSRX Virtual Firewall uses fxp0 as the egress interface to the Internet. For features requiring Internet connections that use a revenue port (such as VPN, Content Security, and so on), routing instances are required to isolate the traffic between the management network and the revenue network.
To change parameter values in the vsrx.parameters.json file:
Deploy the vSRX Virtual Firewall Using the Shell Script
The deploy-azure-vsrx.sh shell script deploys the vSRX Virtual Firewall virtual machine in a resource group that is based on your Azure Cloud geographic location. The script uses the storage account and network values defined in the vsrx.parameters.json file.
To deploy vSRX Virtual Firewall to the Azure virtual network:
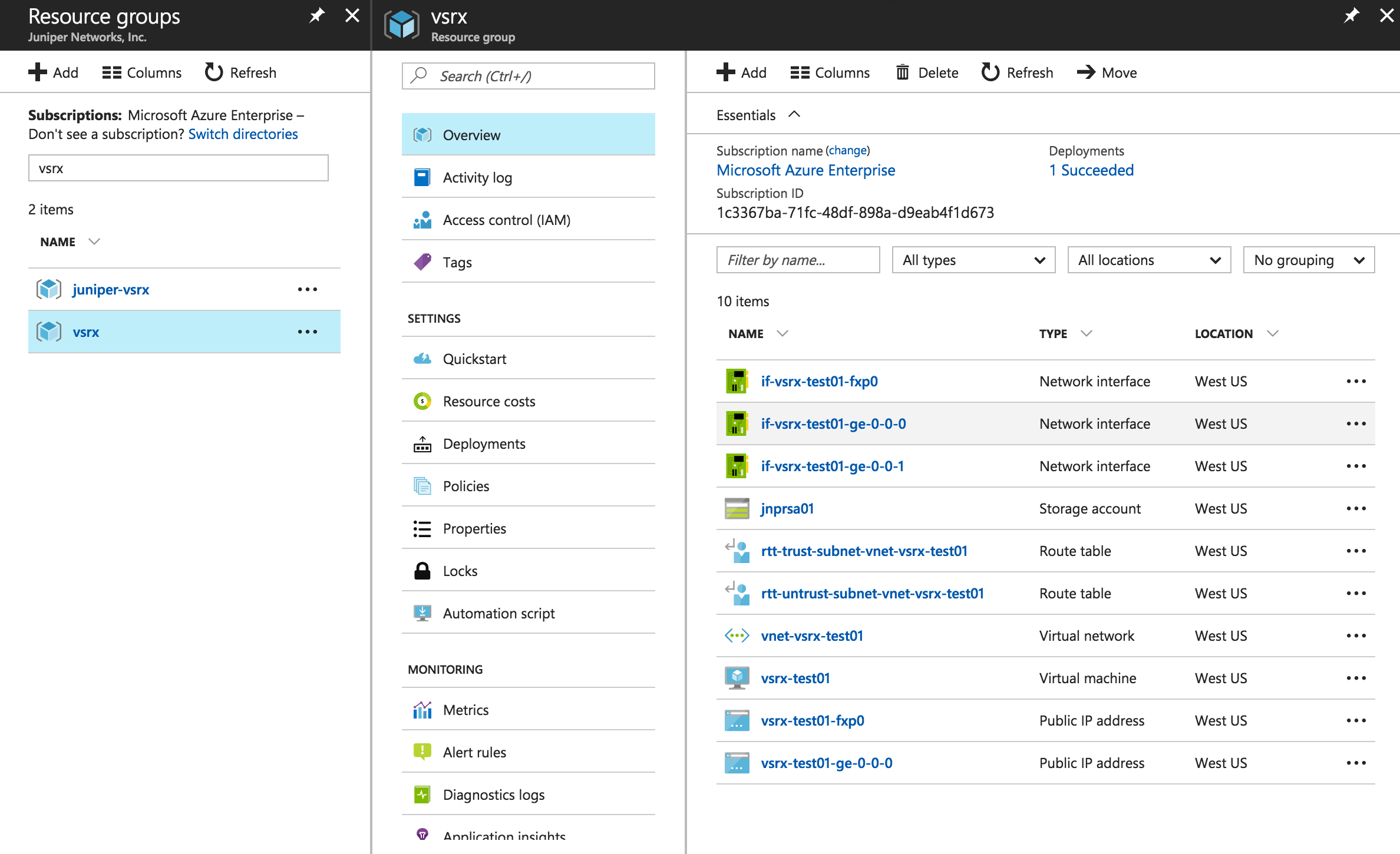
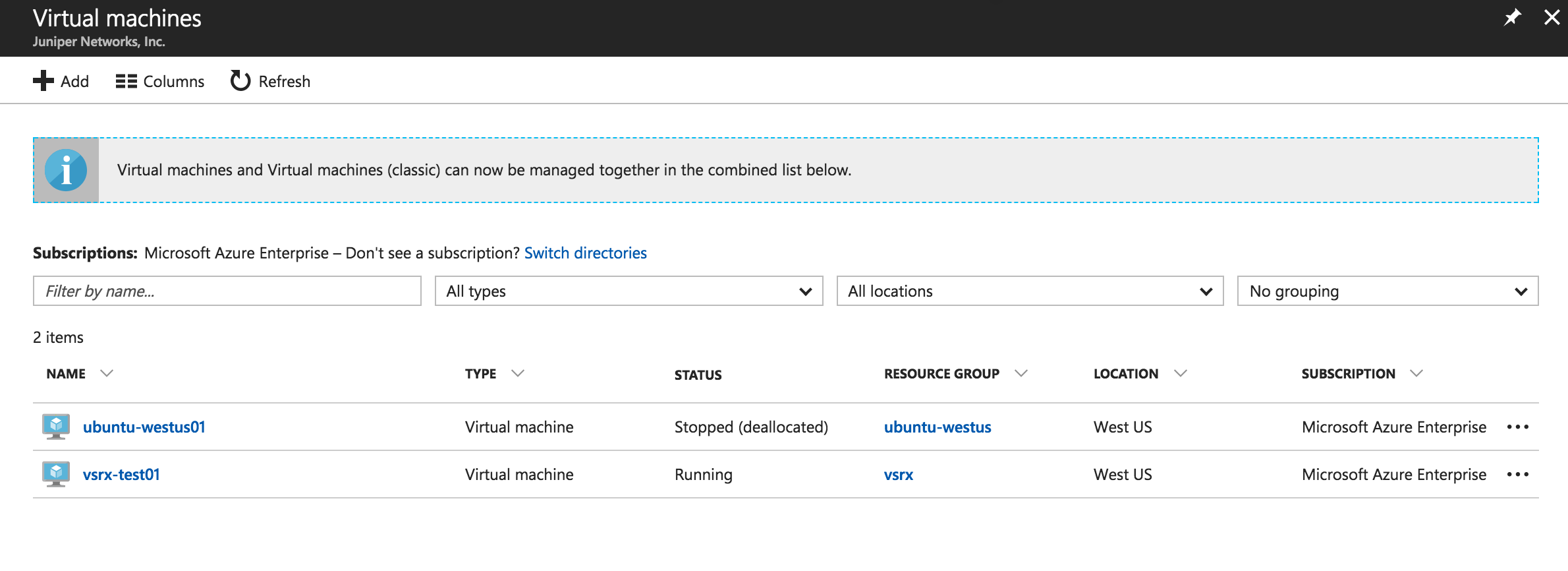
Verify Deployment of vSRX Virtual Firewall to Microsoft Azure
To verify the deployment of the vSRX Virtual Firewall instance to Microsoft Azure:
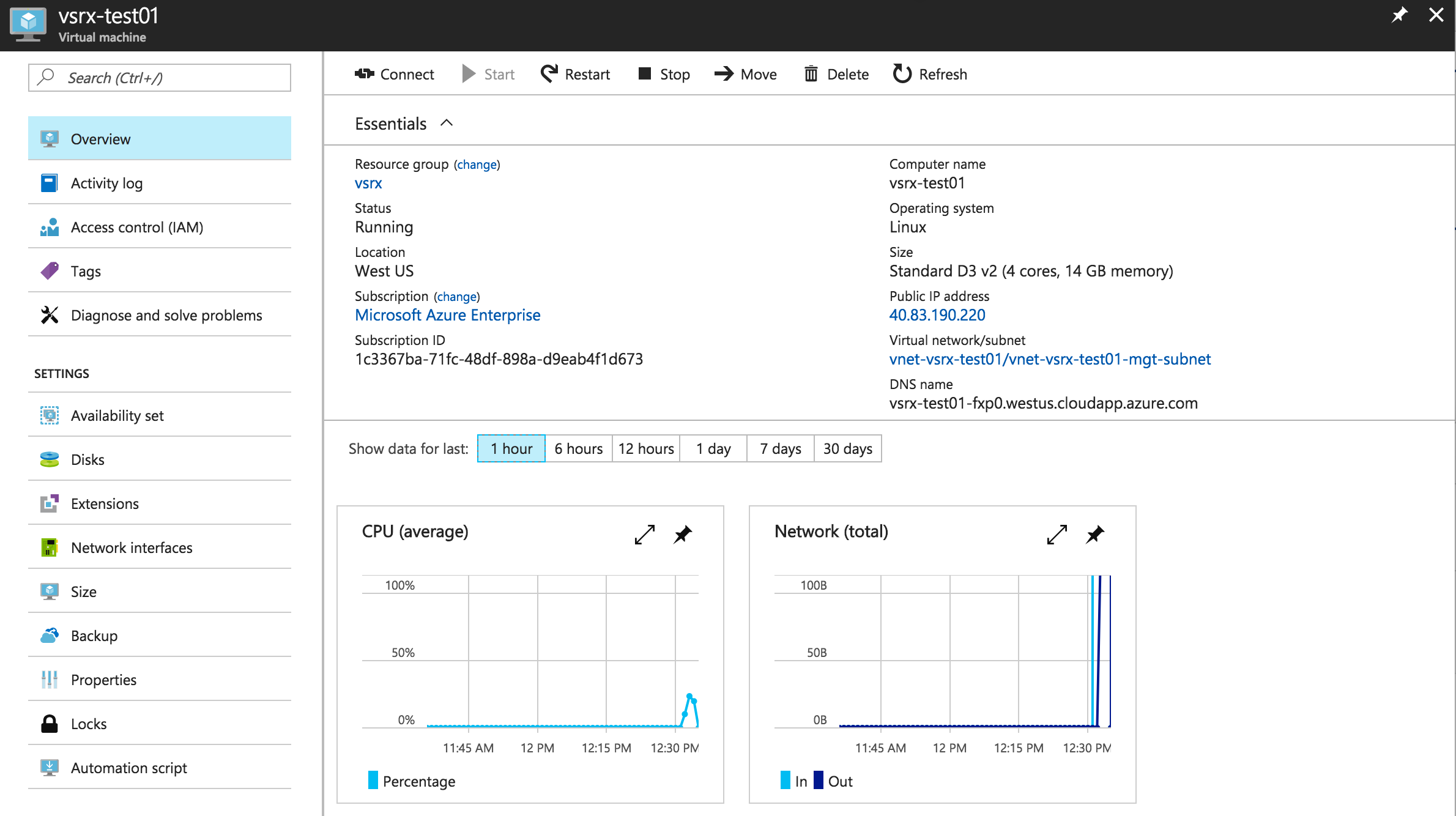
Log In to a vSRX Virtual Firewall Instance
After vSRX Virtual Firewall deployment is completed, the vSRX Virtual Firewall instance is automatically powered on and launched. At this point you can use an SSH client to log in to the vSRX Virtual Firewall instance.
In Microsoft Azure, individuals and enterprises can host servers and services on the cloud as a pay-as-you-go (PAYG) or bring-your-own-license (BYOL) service. For the vSRX Virtual Firewall on Microsoft Azure deployment, only the BYOL model is supported.
To log in to the vSRX Virtual Firewall VM:
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.