Configure an Amazon Virtual Private Cloud for vSRX Virtual Firewall
Before you begin, you need an Amazon Web Services (AWS) account and an Identity and Access Management (IAM) role, with all required permissions to access, create, modify, and delete Amazon Elastic Compute Cloud (Amazon EC2), Amazon Simple Storage Service (S3), and Amazon Virtual Private Cloud (Amazon VPC) objects. You should also create access keys and corresponding secret access keys, X.509 certificates, and account identifiers. For better understanding of AWS terminologies and their use in vSRX Virtual Firewall AWS deployments, see Understand vSRX with AWS.
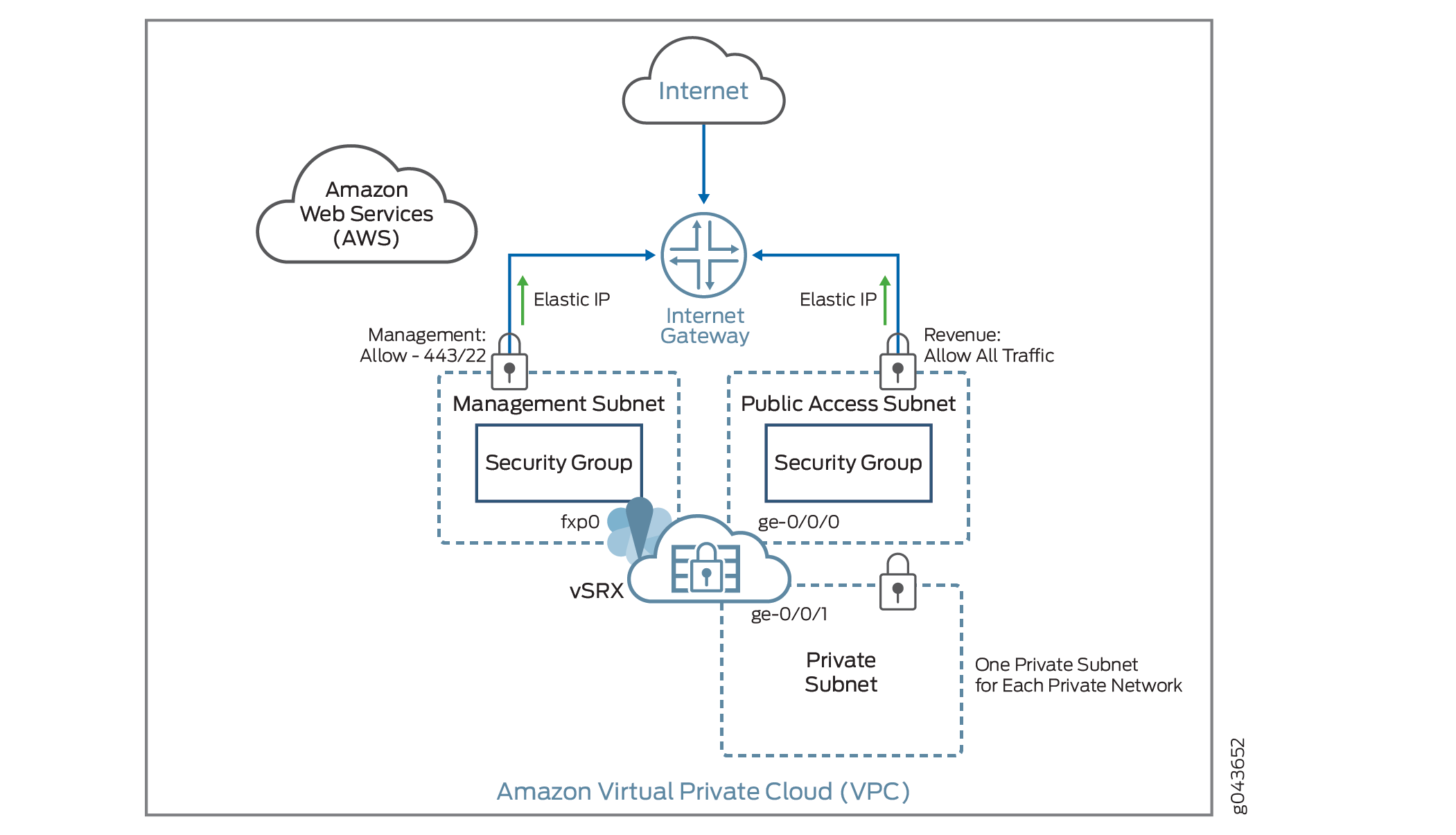
Figure 1 shows an example of how you can deploy vSRX Virtual Firewall to provide security for applications running in a private subnet of an Amazon VPC.
The following procedures outline how to create and prepare an Amazon VPC for vSRX Virtual Firewall. The procedures describe how to set up an Amazon VPC with its associated Internet gateway, subnets, route table, and security groups.
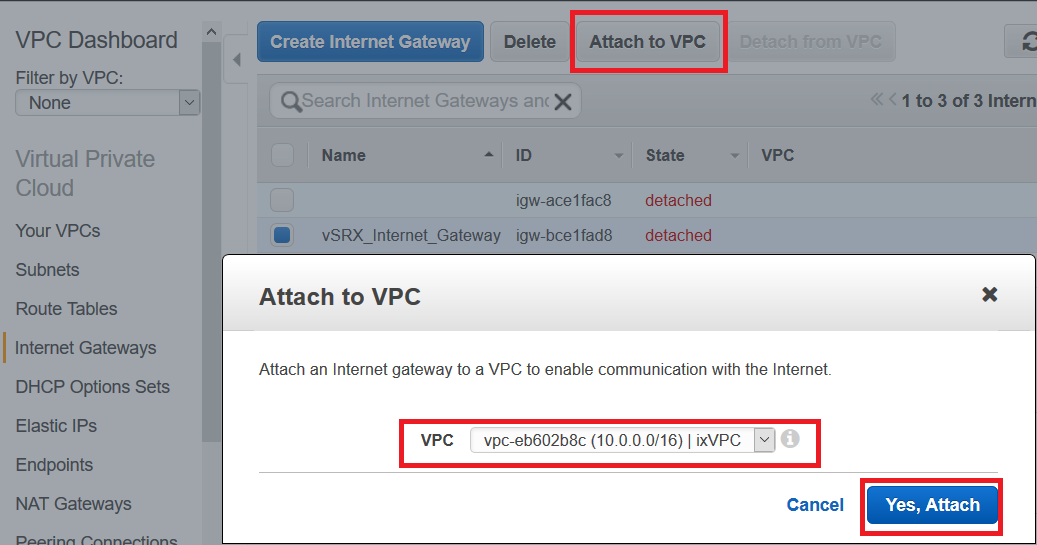
Step 1: Create an Amazon VPC and Internet Gateway
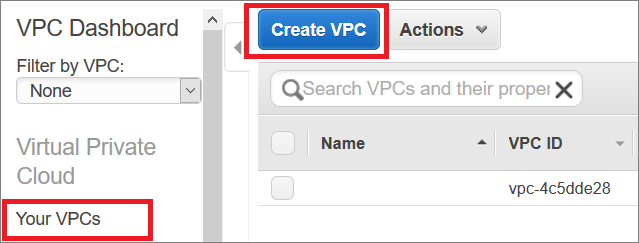
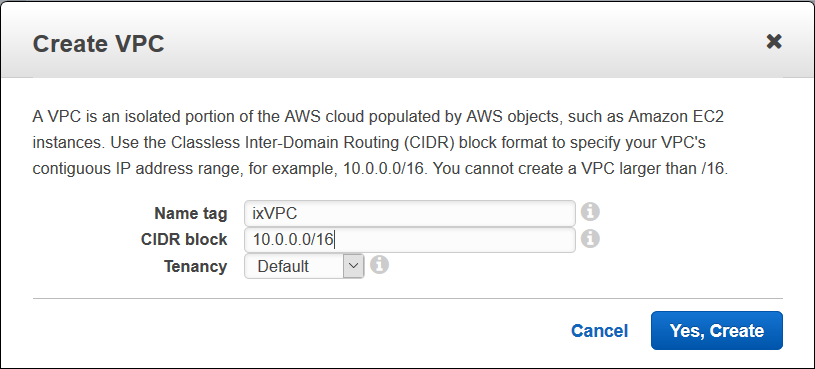
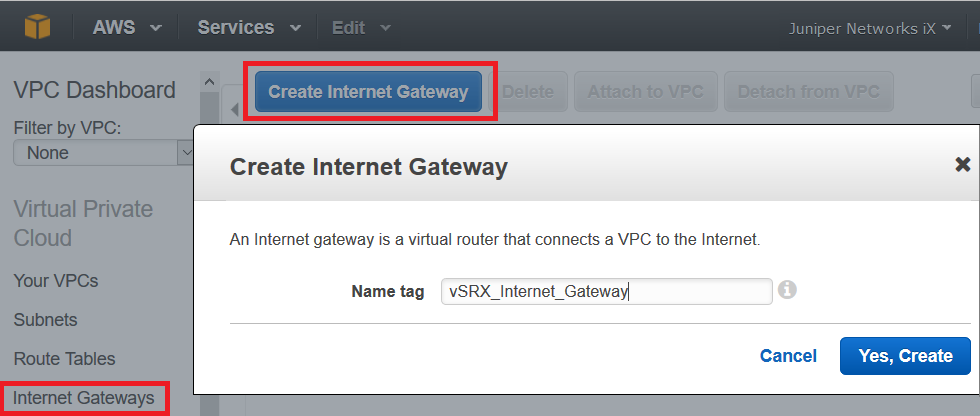
Use the following procedure to create an Amazon VPC and an Internet gateway. If you have already have a VPC and an Internet gateway, go to Step 2: Add Subnets for vSRX Virtual Firewall.
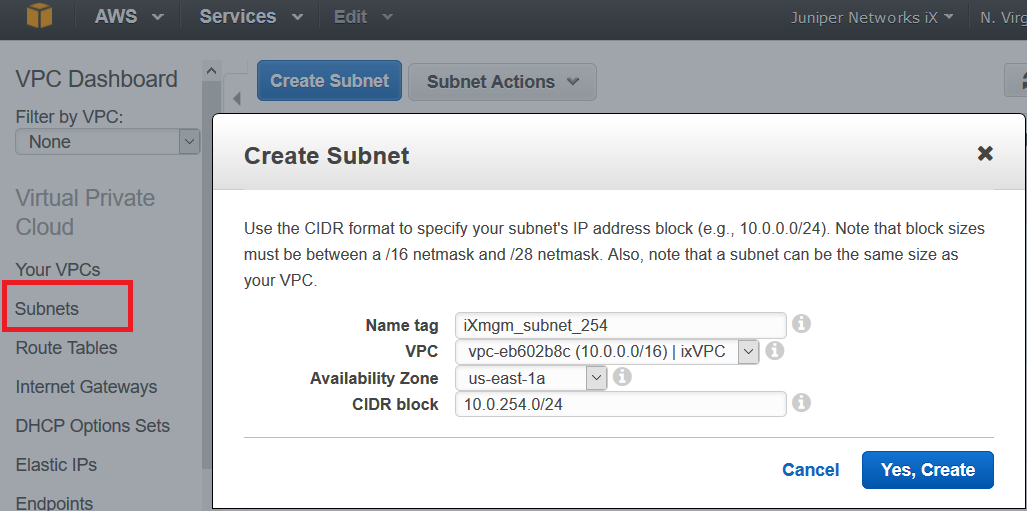
Step 2: Add Subnets for vSRX Virtual Firewall
In the Amazon VPC, public subnets have access to the Internet gateway, but private subnets do not. vSRX Virtual Firewall requires two public subnets and one or more private subnets for each individual instance group. The public subnets consist of one for the management interface (fxp0) and one for a revenue (data) interface. The private subnets, connected to the other vSRX Virtual Firewall interfaces, ensure that all traffic between applications on the private subnets and the Internet must pass through the vSRX Virtual Firewall instance.
To create each vSRX Virtual Firewall subnet:
Repeat these steps for each subnet you want to create and attach to the vSRX Virtual Firewall instance.
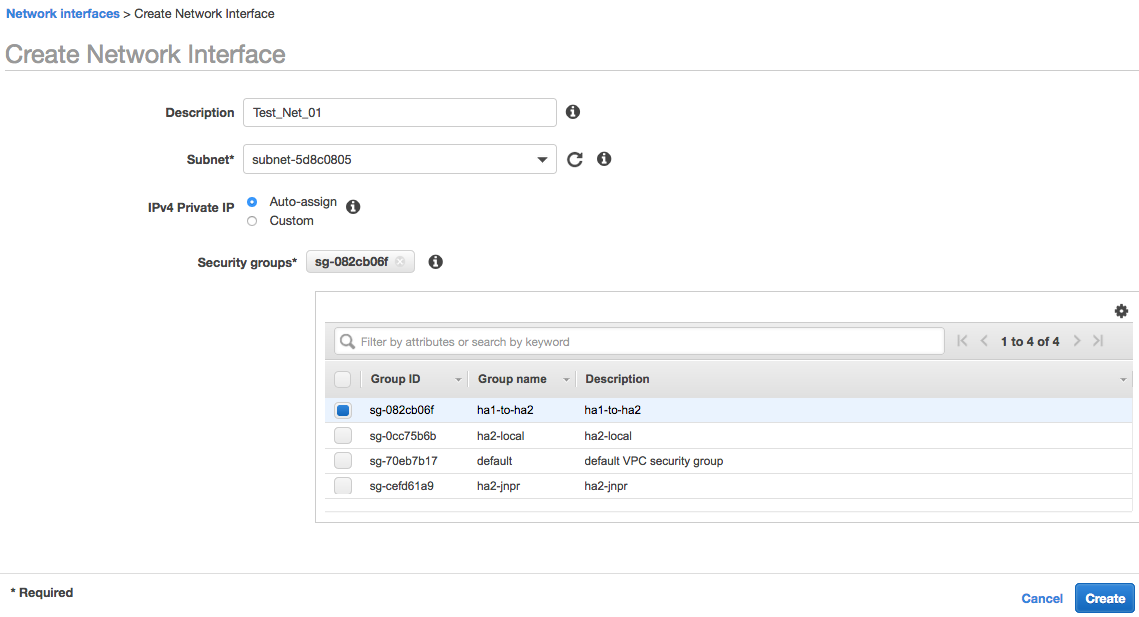
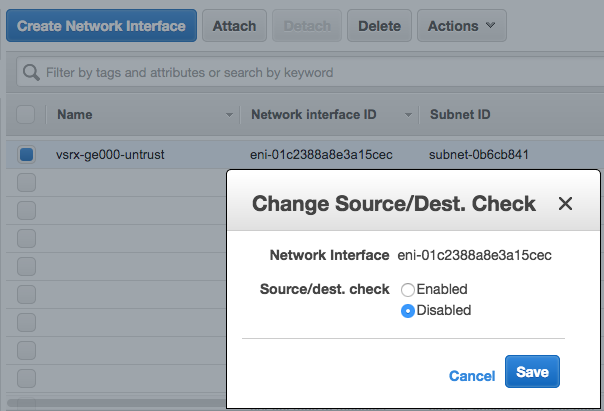
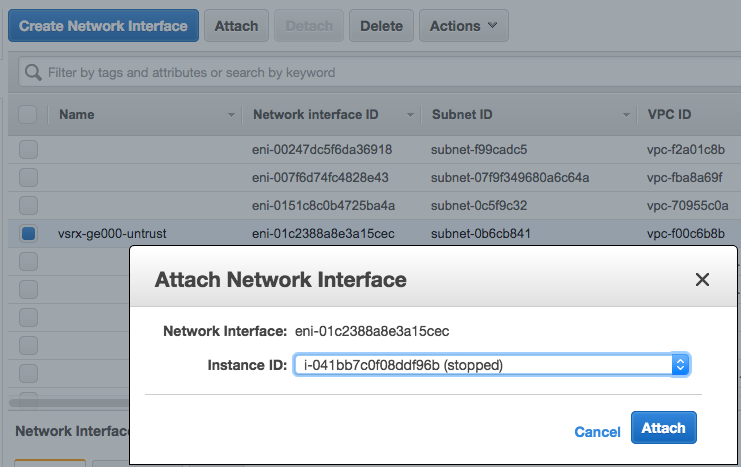
Step 3: Attach an interface to a Subnet
To attach an interface to a subnet:
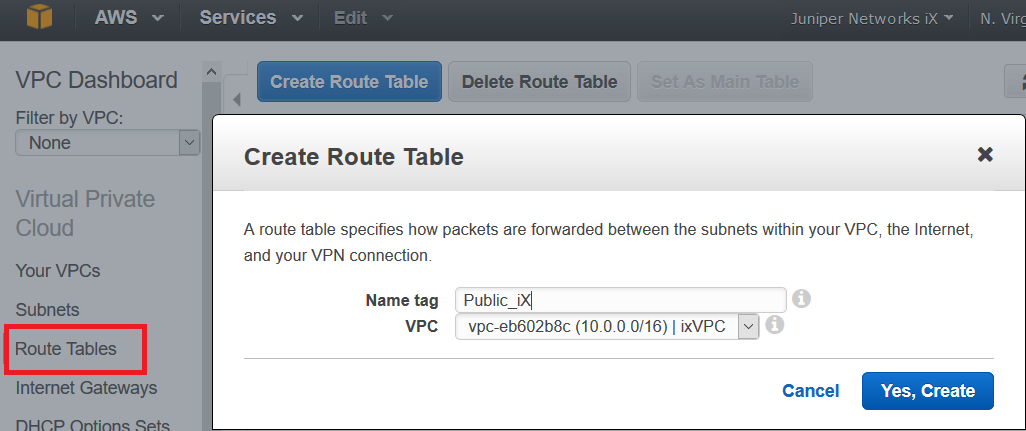
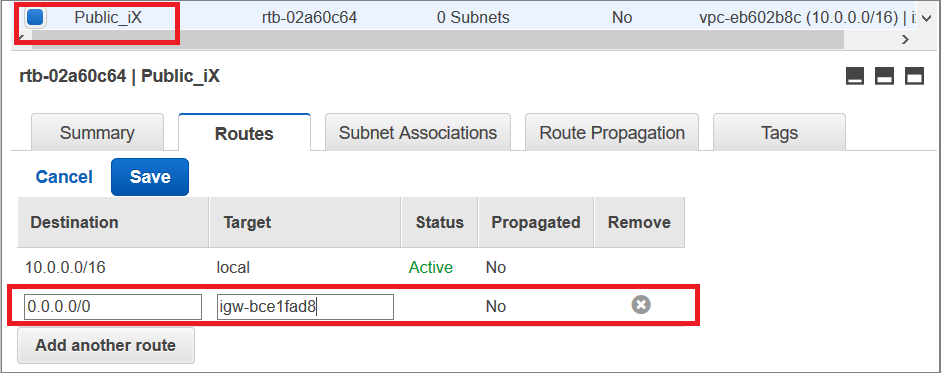
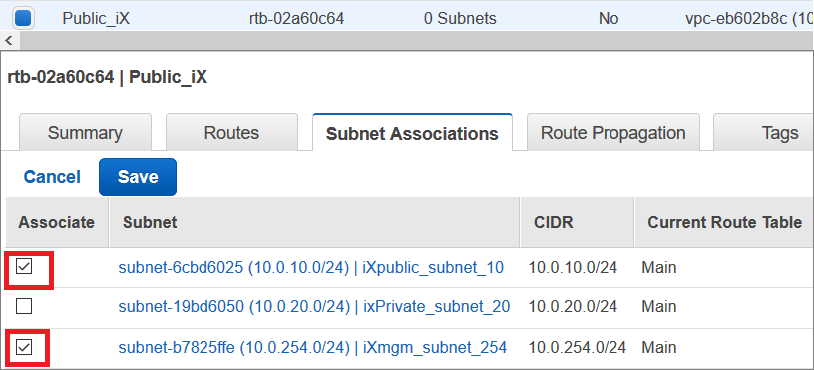
Step 4: Add Route Tables for vSRX Virtual Firewall
A main route table is created for each Amazon VPC by default. We recommend that you create a custom route table for the public subnets and a separate route table for each private subnet. All subnets that are not associated with a custom route table are associated with the main route table.
To create the route tables:
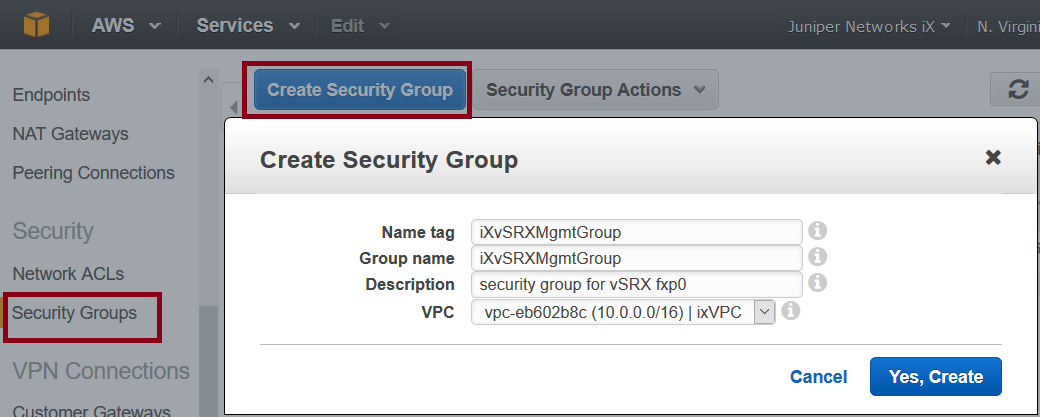
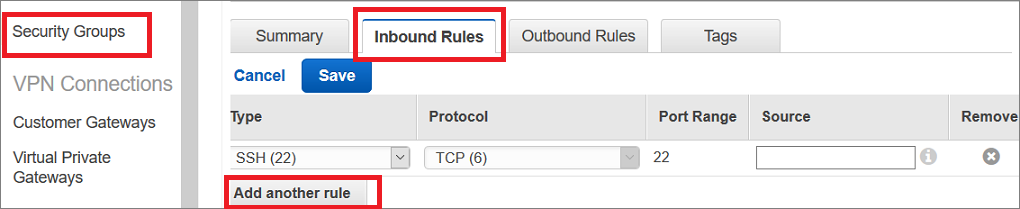
Step 5: Add Security Groups for vSRX Virtual Firewall
A default security group is created for each Amazon VPC. We recommend that you create a separate security group for the vSRX Virtual Firewall management interface (fxp0) and another security group for all other vSRX Virtual Firewall interfaces. The security groups are assigned when a vSRX Virtual Firewall instance is launched in the Amazon EC2 Dashboard, where you can also add and manage security groups.
To create the security groups: