Signature Details
To access the malware signature details page, go to.
- Monitor > Files > HTTP File Download
- Monitor > Files > Email Attachments
- Monitor > Files > SMB File Download
Click Signature ID link to go to the Signature Details page.
Use the Signature Details page to view the malware signature details. The malware signatures are provided by Juniper ATP Cloud to the SRX Series Firewalls. When an SRX Series Firewall detects a malware file, the device can block the file immediately based on these malware signatures and the advanced anti-malware (AAMW) policy that is configured on the SRX Series Firewall. The malware signatures are shared with the SRX Series Firewalls whenever there is an update in Juniper ATP Cloud. For each malware signature hit, the SRX Series Firewall provides the malware signature hit report to Juniper ATP Cloud.
This page is divided into several sections:
-
Report False Positive—Click this button to launch a new screen to send a report to Juniper Networks, informing if the report is a false positive or a false negative. Juniper will investigate the report, however, this investigation does not change the verdict. If you want to make a correction (mark system as clean) you must do it manually.
-
Threat Level—This is the threat level assigned (0-10). This box also provides the signature filename, threat category and the action taken.
-
Prevalence—Provides information about how often this malware has been seen, how many individual hosts on the network downloaded the file, and the protocol used.
| Field | Description |
|---|---|
| General | Displays signature information of the associated file |
| Static Analysis | Displays information about file type or file source associated with the signature. The file types that are supported are PE/DLL, doc, docx Office - old format, office - new format, PDF, RTF. |
| Behavior Analysis | Displays the behavior analysis for the file associated with the signature |
| Network Activity | Displays the network activity for the file associated with the signature |
| Behavior Details | Displays the behavior data for the file associated with the signature |
Signature Summary
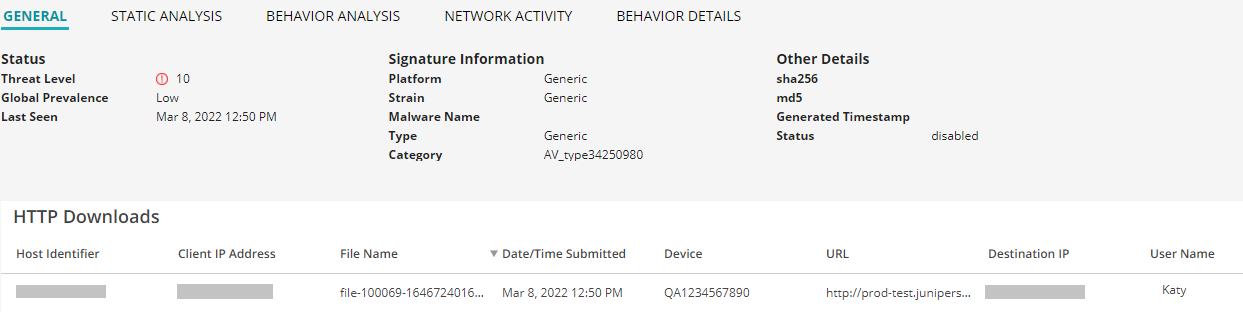
The General tab displays the details for the file associated with the signature. Please note that this file might not be the exact file seen in your network. It is the file used to generate the signature that your file has triggered. The details include file category, timestamp of when the signature was created, statistics about how often the signature was hit, the current status of the signature (enabled/disabled), and so on.
|
Field |
Definition |
|---|---|
| Status | |
|
Threat Level |
This is the assigned threat level 0-10. 10 is the most malicious. |
|
Global Prevalence |
How often this file has been seen across different customers. |
|
Last Scanned |
The time and date of the last scan to detect the suspicious file |
| Signature Information | |
| Platform |
The target OS of the file Example: Win32 |
| Strain | If possible, Juniper ATP Cloud determines the strain of malware detected. Example: Outbrowse.1198, Visicom.E, Flystudio |
|
Malware Name |
If possible, Juniper ATP Cloud determines the name of the malware. |
|
Type |
If possible, Juniper ATP Cloud determines the type of threat. Example: Trojan, Application, Adware |
|
Category |
If possible, Juniper ATP Cloud determines the category of threat. |
| Other Details | |
|
sha256 and md5 |
One way to determine whether a file is malware is to calculate a checksum for the file and then query to see if the file has previously been identified as malware. |
| Generated Timestamp | The time when the signature was generated. |
| Status | The current status of the signature (enabled/disabled) |
HTTP Downloads
This section displays the list of hosts that have downloaded the suspicious file. Click the IP address to be taken to the Host Details page for this host. Click the Device Serial number to be taken to the Devices page. From there you can view device versions and version numbers for the Juniper ATP Cloud configuration, including profile, allowlist, and blocklist versions. You can also view the malware detection connection type for the device: telemetry, submission, or C&C event.
Static Analysis
Juniper ATP Cloud provides static analysis and machine learning (ML) to determine if the file is potentially malicious.
Behavior Analysis
Juniper ATP Cloud provides network behavioral analysis and ML to analyze the behavior of the sample, including the connections it makes to various hosts. However, the analysis is still for primarily sandboxed sample analysis and not for connection analysis.
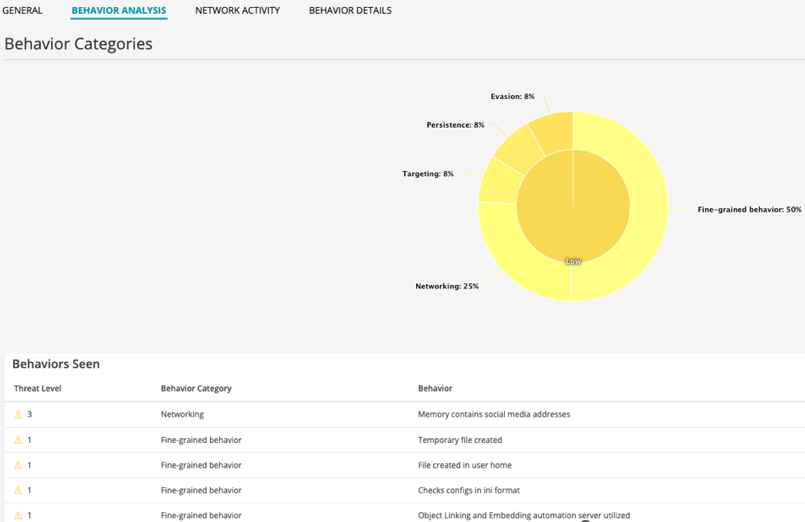
Behavior analysis tab displays the file execution behavior trends in a radar chart with malware categories or behaviors on each axis. This data helps us better identify the category of a malware and map that category to a severity.
The malware priority is classified into low, medium, and high.
|
Behavior Category |
Sample Behavior Definition |
|---|---|
|
Targeting |
Checks volume information |
|
Fine-grained Behavior |
Contains code to communicate with device drivers. Contains code to delete services. Memory allocated in system DLL range |
|
Obfuscation |
Utilizes known code obfuscation techniques. |
|
Evasion |
Contains code to detect VMs. Contains large amount of unused code (likely obfuscated code). Contains code to determine API calls at runtime. |
|
Persistence |
Modifies registry keys to run application during startup. |
|
Networking |
Memory or binary contains Internet addresses. |
Network Activity
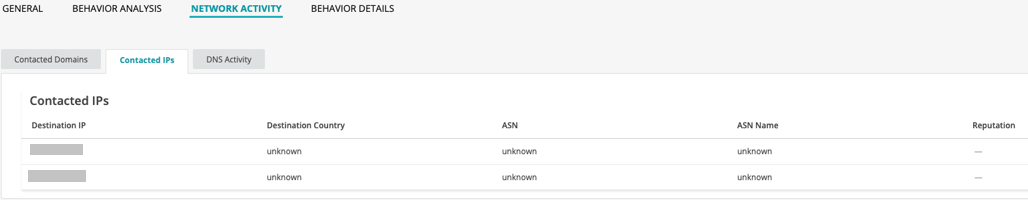
In the Network Activity section, you can view information in the following tabs:
-
Contacted Domains—If available, lists any domains that were contacted while executing the file in the Juniper ATP Cloud sandbox.
-
Contacted IPs—If available, lists all IPs that were contacted while executing the file, along with the destination IP’s country, ASN, and reputation. The reputation field is based on Juniper IP intelligence data destination.
-
DNS Activity— This tab lists DNS activity while executing the file, including reverse lookup to find the domain name of externally contacted servers. This tab also provides the known reputation of the destination servers.
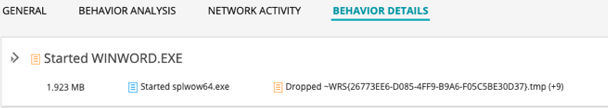
Behavior Details
This section displays the behavior data for the file associated with the signature.