SAML Authentication in Juniper Secure Connect
Read this topic to learn about Security Assertion Markup Language (SAML) based user authentication in Juniper Secure Connect.
SAML Overview
Security Assertion Markup Language (SAML) is an XML-based framework for exchanging authentication and authorization data between the service provider (SP) and the identity provider (IdP). SAML enables Single Sign-On (SSO) that allows users to log in once and then seamlessly access multiple applications without having to reenter their credentials each time.
Juniper Secure Connect supports remote user authentication using SAML version 2 (SAML 2.0). When you run a VPN service using the iked process, the SRX Series Firewalls supports this feature.
SAML Components for Juniper Secure Connect
Following are the key components in SAML for Juniper Secure Connect:
-
Principal (User)—The user who requests for services such as the remote access VPN connection. Any remote user of the Juniper Secure Connect is the Principal. The browser available on the user's device (such as a Windows laptop) is used as an agent for SSO.
-
Identity Provider (IdP)—The entity that authenticates users and provides identity assertions to the service provider. The IdP generates an authentication assertion to indicate that the user has been authenticated. Okta and Microsoft Azure are examples for IdPs.
-
Service Provider (SP) —Entity that provides the service to the user. It relies on the assertions from the IdP to grant access to the user. In Juniper Secure Connect, the SRX Series Firewall functions as the SP delivering remote access VPN service.
-
SAML Assertion—An XML-based message that carries user's authentication and authorization information. Assertions are used to transfer user identity information from the IdP to the SP.
-
SAML Binding—Defines how the SAML messages are transmitted between the IdP and SP. SRX Series Firewall supports SP initiated SSO profile over HTTP Redirect and HTTP POST bindings.
-
SAML Metadata—An XML-based data that describe the IdP and SP attributes such as entity ID, certificates, bindings, URLs, and so on. These entities interact with each other. SRX Series Firewalls allow you to import the IdP metadata and export SP metadata.
Table 1 shows the list of SAML feature support in SRX Series Firewall.
|
SAML Features |
Support |
|---|---|
|
SAML Version |
Not compatible with SAMLv1. |
|
SAML Profiles |
|
|
SAML Bindings |
|
|
Service Provider Hash Algorithms |
Default is SHA-256. |
|
Assertion-cache |
|
|
Support for High Availability |
No high availability support for authentication sessions that are in progress. |
Benefits
-
Improved user experience—SAML provides SSO capabilities in multi-application access scenarios. With a single login, in-addition to Juniper Secure Connect, you can connect to multiple applications offered by different service providers. You don't need to enter different credentials for different applications.
-
Enhanced security—SAML provides enhanced security for the Juniper Secure Connect remote user by providing single point of authentication using a secure IdP. SAML doesn't share user credentials with the service provider. SAML transfers only the identity information to the service provider ensuring that the credentials are sent only to the IdP and not each and every service provider.
-
Easy integration—As an open standard, SAML facilitates easy integration with any IdP for Juniper Secure Connect remote user authentication.
-
Reduced cost—SAML allows the service provider to reduce the cost of maintaining multiple user account details.
How SAML Works in Juniper Secure Connect
Consider the following points when configuring remote user authentication using SAML for Juniper Secure Connect.
-
When you choose SAML for remote user authentication in Juniper Secure Connect, ensure you have an agreement with the IdP. You must be aware about the configuration settings related to the IdP that the service provider should be aware of.
-
Set SAML as the authentication method for the access profile. See authentication-order (Access Profile).
-
Configure the SAML access parameters such as Identity Provider (IdP) and Service Provider (SP) settings. See saml.
-
Specify the SAML settings for the access profile. See saml (Access Profile).
-
If you prefer not to cache SAML assertions from the IdP, set the preference in the SAML options. See saml-options.
-
To authenticate Juniper Secure Connect remote user with SAML, both the remote access VPN profile and the IKE gateway AAA access profiles should be SAML-based.
Figure 1 illustrates the SAML-based user authentication workflow in Juniper Secure Connect.
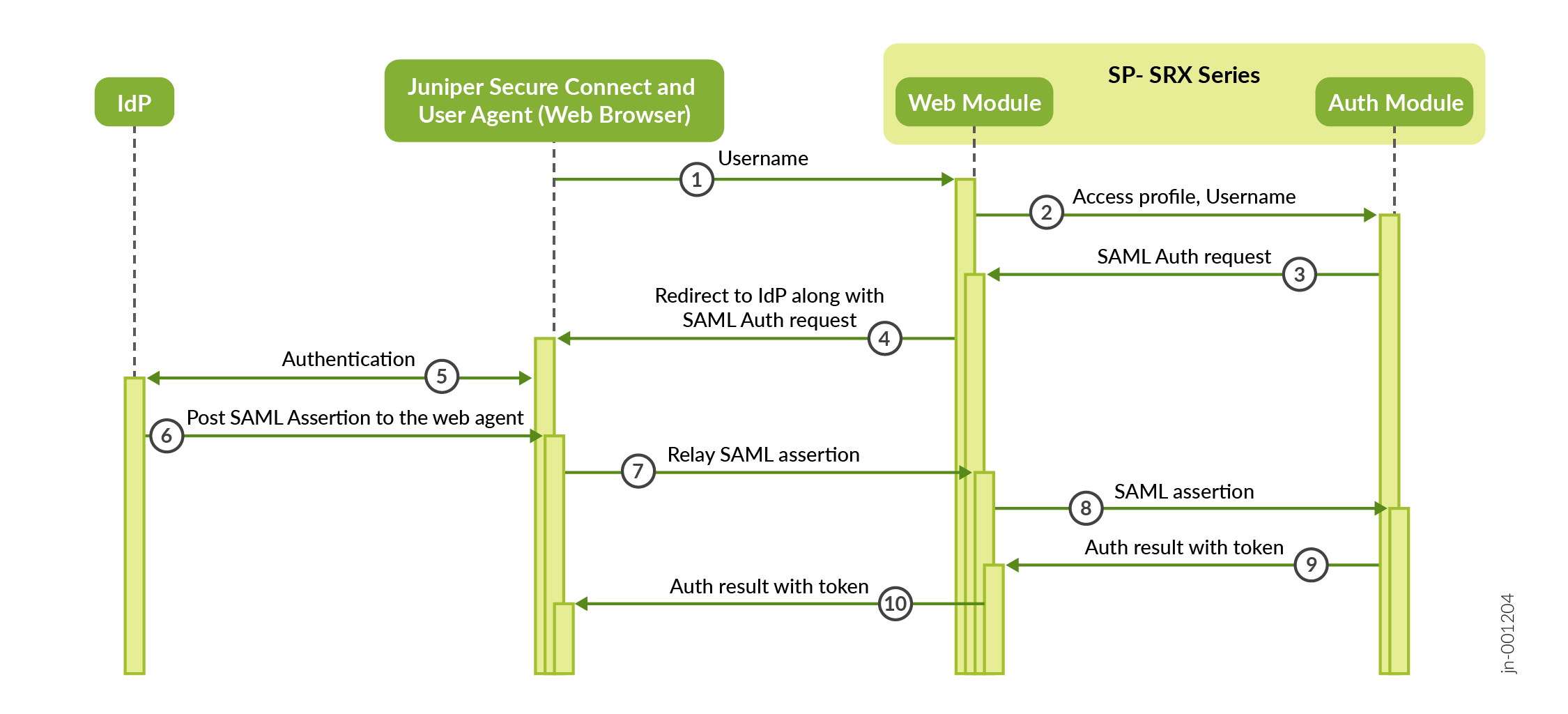
Juniper Secure Connect remote user sends a connection request to the SRX Series Firewalls, specifying a particular username and connection profile.
SRX Series Firewall checks the access profile to determine if the profile uses SAML as an authentication method. An access profile can contain multiple IdPs for different domains. The user's domain determines the selection of the IdP. For example, if the username is user1@domain1 and domain1 is configured within the access profile, the firewall selects the corresponding IdP for domain1. If domain1 is not configured, the firewall uses the IdP configured under the
anydomain. Similarly, if the username doesn’t contain an email format, such as user1, the firewall selects the IdP configured under theanydomain by default.The firewall sends the SAML authentication request to Juniper Secure Connect.
Juniper Secure Connect launches a web-browser (user-agent) and redirects the SAML authentication request to the IdP.
The IdP authenticates the user.
If the authentication is successful, the IdP sends SAML assertion using an HTTP POST request.
The web-browser relays the SAML assertion to the SRX Series Firewall.
The SRX Series Firewall receives the SAML assertion and validates it.
When the SAML assertion is valid, the firewall sends the authentication result along with a valid SAML assertion token to Juniper Secure Connect.
Juniper Secure Connect establishes remote access VPN tunnel with the SRX Series Firewall after the SAML authentication.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
