Juniper Secure Connect Overview
Explore Juniper Secure Connect as your remote access VPN solution. Learn about its features and benefits.
With today’s modern, distributed workforce, your organization needs to keep remote users connected and productive while ensuring business continuity and security. Your organization needs to provide endpoint protection as part of a comprehensive and connected security strategy. Juniper Secure Connect® is a Juniper Networks remote access VPN solution that addresses these needs.
Juniper Secure Connect is a client-based SSL-VPN solution that allows you to securely connect and access protected resources on your network.
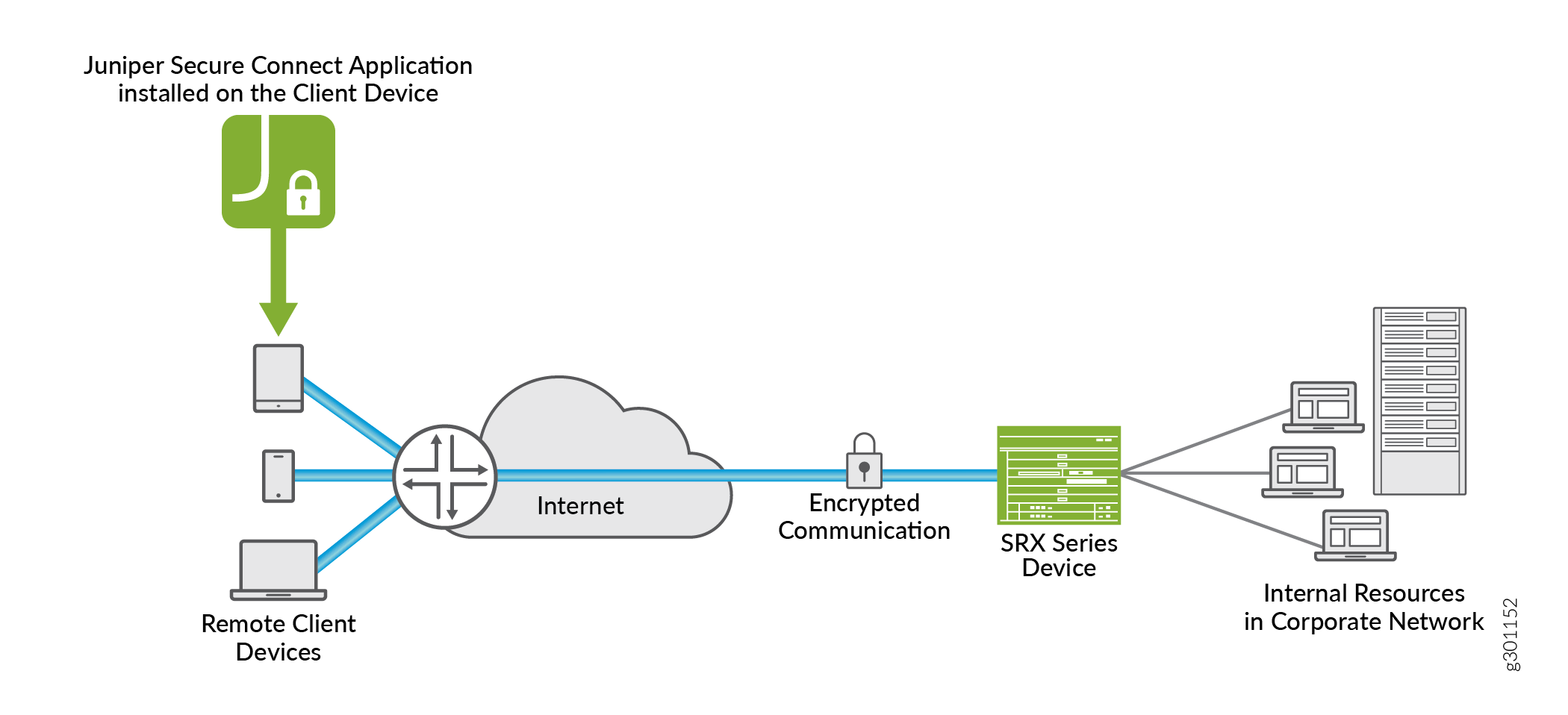
Figure 1 illustrates the Juniper Secure Connect remote access solution for establishing secure VPN connectivity for remote users at different locations. The solution allows your device to connect securely to the corporate network through encrypted tunnels over the internet.
Feature Support for Juniper Secure Connect
|
Feature |
Description |
|---|---|
|
Multi-Platform support |
Supports Windows, macOS, Android, and iOS platforms. |
|
Windows Pre-domain logon |
Allows users to log on to the local Windows system through an already established VPN tunnel (using Windows Pre-Logon) so that it is authenticated to the central Windows domain or Active Directory. |
|
Configuration support |
Automatically validates that the most current policy is available before establishing the connection. |
|
Biometric user authentication |
Allows the user to protect their credentials using the operating system’s built-in biometric authentication support. |
|
Multi-Factor Authentication (MFA) |
Allows you to use multi-factor authentication to extend the authentication. |
|
Security Assertion Markup Language (SAML) |
Allows you to use SAML authentication supporting single sign-on (SSO) federated identity. |
|
IKE Support |
Supports IKEv1 and IKEv2 with SSL VPN. |
|
Juniper Secure Connect license |
Licenses are available in 1-year, 3-year, and 5-year subscription models. SRX Series Firewalls and vSRX Virtual Firewall include two built-in free concurrent user/device licenses for testing. |
Benefits of Juniper Secure Connect
-
Flexible and secure SSL VPN access to remote users from any location.
-
Less complexity with no additional hardware as you can use the existing SRX Series Firewalls deployed in your network.
-
Central management of remote users, remote clients, and policies using CLI, J-Web, Security Director, and Security Director Cloud.
-
Support with various bring-your-own device (BYOD) running on the most common OS types such as Windows, macOS, iOS, and Android.
What's Next
Read the following topics to know more about Juniper Secure Connect:
