IPsec VPN Overview
IPsec VPN is a secure networking protocol suite that encrypts and authenticates data to create private tunnels over public networks, commonly used for site-to-site and remote access connections. Read the following topic to understand how to securely connect remote networks using Juniper Security Director Cloud and SRX Series Firewalls.
IPsec VPN provides a means to securely communicate with remote computers across a public WAN such as the Internet. A VPN connection can link two LANs using a site-to-site VPN or a remote dial-up user and a LAN. The traffic that flows between these two points passes through shared resources such as routers, switches, and other network equipment that comprise the public WAN. To secure VPN communication that passes through the WAN, you need to create an IPsec tunnel.
Juniper Security Director Cloud simplifies the management and deployment of IPsec VPNs. In general, VPN configurations are tedious and repetitive when deploying over a large number of SRX Series Firewalls. With Juniper Security Director Cloud, you can use VPN profiles to group common settings and apply the profiles to multiple VPN tunnel configurations across multiple SRX Series Firewalls. You can deploy site-to-site and hub-and-spoke VPNs. Juniper Security Director Cloud determines the necessary deployment scenarios and publishes the required configuration for all SRX Series Firewalls.
Benefits
- Encrypts data to ensure confidentiality and integrity.
- Verifies the identity of communicating peers.
- Enables secure access to private networks over the internet.
IPsec VPN Types
Juniper Security Director Cloud supports policy-based and route-based IPsec VPNs on SRX Series Firewalls.
Here's a comparison of policy-based and route-based IPsec VPNs on Juniper SRX Series Firewalls.
| Feature | Policy-Based VPN | Route-Based VPN |
|---|---|---|
| Supported Topology | Site-to-site only | Hub-and-spoke, full mesh |
| Number of Endpoints | Two endpoints | Two or more endpoints |
| Scalability | Limited | High |
| Flexibility | Less flexible | More flexible |
| Enterprise-Class Deployment | Not ideal | Recommended |
| Criteria | Use Policy-Based Tunnel Mode | Use Route-Based Tunnel Mode |
|---|---|---|
| Remote Gateway Type | Non-Juniper device | Juniper device |
| Traffic Restriction | Specific application traffic | General traffic |
| NAT Requirements | Not required | Source or destination NAT required |
| Routing Protocols | Static routing | Dynamic routing (such as OSPF, BGP) |
| Redundancy (Primary/Backup VPNs) | Not supported | Supported |
When you create either type of VPN in Juniper Security Director Cloud, a topology view is displayed. You can click the icons in the topology to configure the remote gateway.
IPsec VPN and Logical Systems
Juniper Security Director Cloud views each logical system as any other security device and takes ownership of the security configuration of the logical system. In Juniper Security Director Cloud, each logical system is managed as a standalone security device.
Juniper Security Director Cloud ensures that the tunnel interfaces are exclusively assigned to the individual logical systems of a device. No tunnel interface is assigned to more than one logical system of the same device.
Juniper Security Director Cloud does not support VPN over Point-to-Point Protocol over Ethernet (PPPoE).
IPsec VPN Topologies
Juniper Security Director Cloud supports the following IPsec VPN topologies:
-
Site-to-Site VPNs—Connects two sites in an organization together and allows secure communications between the sites.
Figure 1: Site-to-Site VPN
-
Hub-and-Spoke (establishment all peers)—Connects branch offices to the corporate office in an enterprise network. You can also use this topology to connect spokes together by sending traffic through the hub.
Figure 2: Hub-and-Spoke (establishment all peers)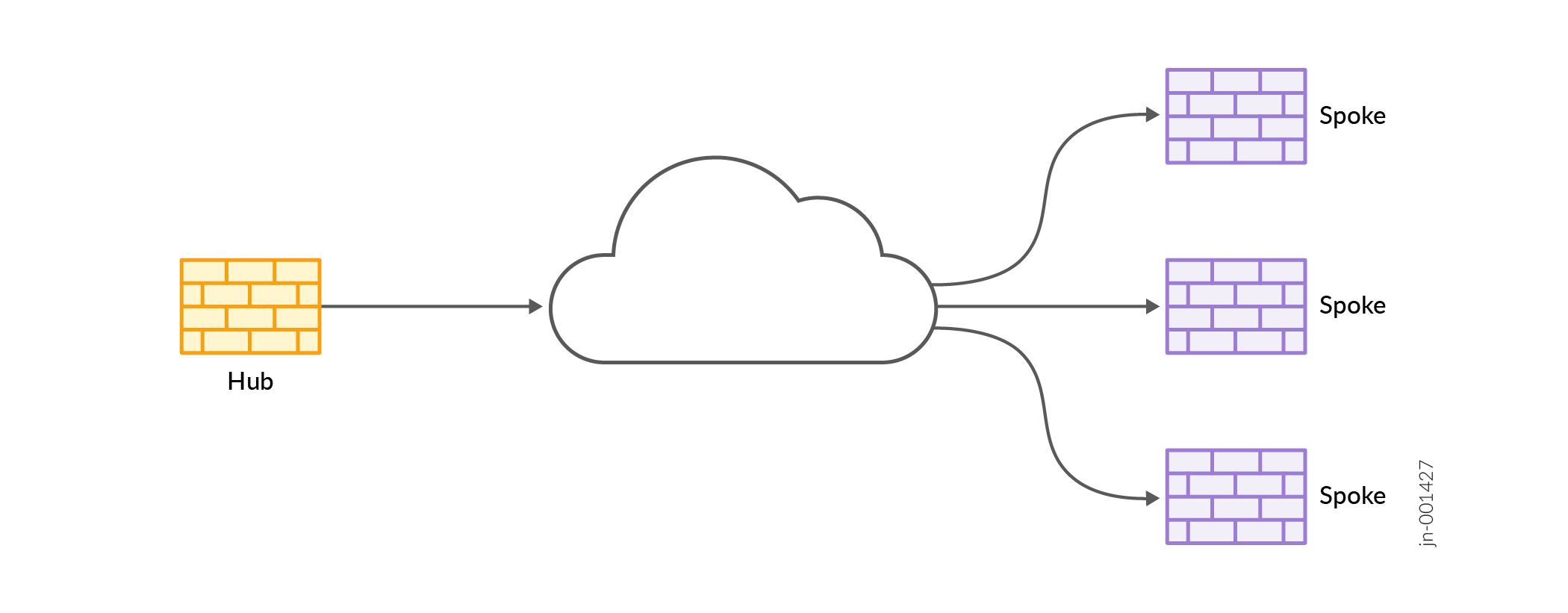
-
Hub-and-Spoke (establishment by spokes)—Autovpn supports an IPsec VPN aggregator called a hub that serves as a single termination point for multiple tunnels to remote sites called spokes. Autovpn allows network administrators to configure a hub for current and future spokes. No configuration changes are required on the hub when spoke devices are added or deleted, which allows administrators flexibility in managing large-scale network deployments.
Figure 3: Hub-and-Spoke (establishment by spokes)
-
Hub-and-Spoke (Auto Discovery VPN)—Auto Discovery VPN (ADVPN) is a technology that allows the central hub to dynamically inform spokes about a better path for traffic between two spokes. When both spokes acknowledge the information from the hub, the spokes establish a shortcut tunnel and change the routing topology for the host to reach the other side without sending traffic through the hub.
Figure 4: Hub-and-Spoke (Auto Discovery VPN)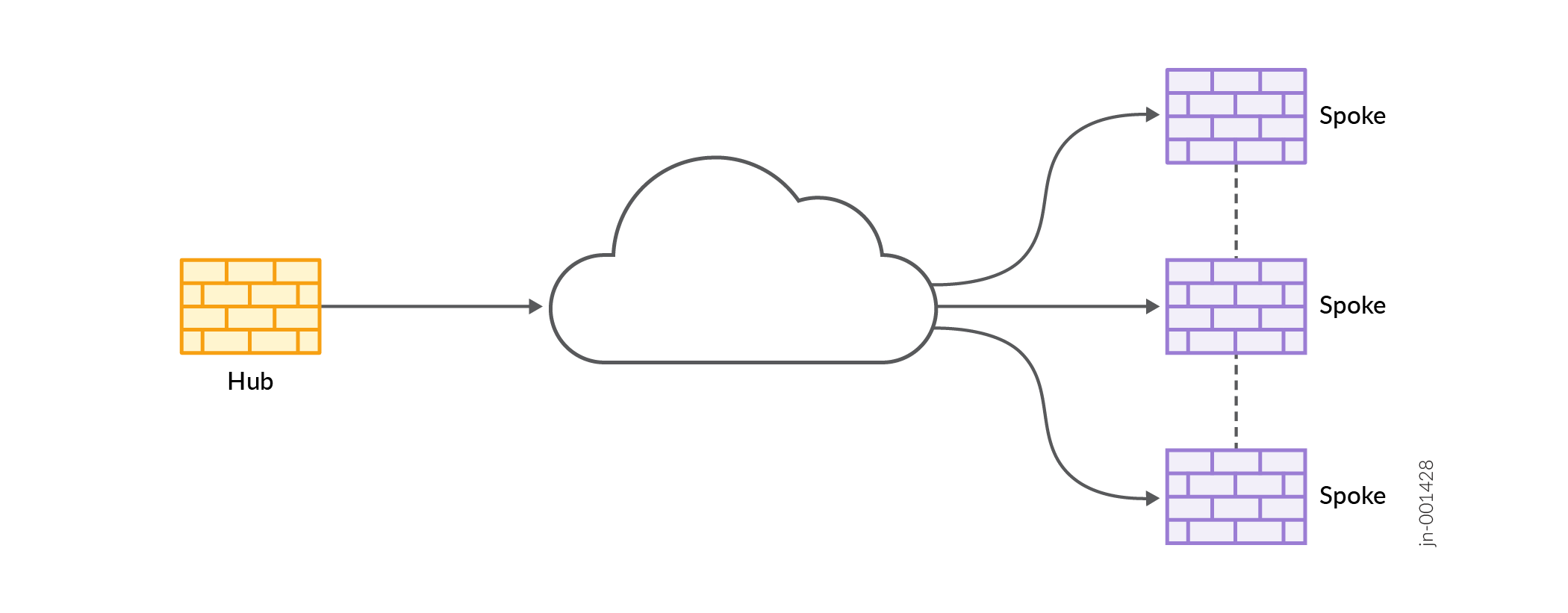
-
Remote Access VPN (Juniper Secure Connect)—Juniper Secure Connect provides secure remote access for the users to connect to the corporate networks and resources remotely using the Internet. Juniper Secure Connect downloads the configuration from SRX Series Firewalls Services devices and chooses the most effective transport protocols during connection establishment.
Figure 5: Remote Access VPN (Juniper Secure Connect)
IPsec VPN Configurations
IPsec VPN Modes
Juniper Security Director Cloud supports two VPN traffic exchange modes:
-
Tunnel Mode—This mode encapsulates the original IP packet within another packet in the VPN tunnel. This is most commonly used when hosts within separate private networks want to communicate over a public network. Both VPN gateways establish the VPN tunnel to each other, and all traffic between the two gateways appears to be from the two gateways, with the original packet embedded within the exterior IPsec packet.
-
Transport Mode—This mode does not encapsulate the original packet in a new packet like the tunnel mode. The transport mode sends the packet directly between the two hosts that have established the IPsec tunnel.
The Tunnel mode is the most common VPN mode on the Internet because it easily allows entire networks, particularly those with private address space, to communicate over public IP networks. The Transport mode is primarily used when encrypting traffic between two hosts to secure communication where IP address overlap is not an issue, such as between a host and a server on a private network.
IPsec VPN Routing
SRX Series Firewalls must know how to reach destination networks. This can be configured through the use of static routing or dynamic routing.
In Juniper Security Director Cloud route-based VPNs support OSPF, RIP, and eBGP routing along with static routing. Static routing requires that administrators specify the list of host or network addresses at each site as part of the VPN.
For example, in a retail scenario, where thousands of spokes can be part of a VPN, the static routing approach generates a huge configuration at each device. Static routing requires administrators to manually configure each route, and problems might occur when the infrastructure changes or when the administrators do not have access to the addresses for the protected network. Keeping routes up-to-date manually also creates a tremendous overhead.
IKE Authentication
Internet Key Exchange negotiations only provide the ability to establish a secure channel over which two parties can communicate. You still need to define how they authenticate each other. This is where IKE authentication is used to ensure that the other party is authorized to establish the VPN. The following IKE authentications are available:
-
Preshared key authentication—The most common way to establish a VPN connection is to use preshared keys, which is essentially a password that is the same for both parties. This password must be exchanged in advance in an out-of-band mechanism, such as over the phone, through a verbal exchange, or through less secure mechanisms, even e-mail. The parties then authenticate each other by encrypting the preshared key with the peer’s public key, which is obtained in the Diffie-Hellman exchange.
Preshared keys are commonly deployed for site-to-site IPsec VPNs, either within a single organization or between different organizations. A preshared key must consist of at least 8 characters with 12 or more characters recommended comprising a combination of letters, numbers, and non-alphanumeric characters, along with different cases for the letters. Preshared keys should not use a dictionary word.
-
Certificate authentication—Certificate-based authentication is considered more secure than preshared key authentication because the certificate key cannot be compromised easily. Certificates are also more ideal in larger scale environments with numerous peer sites that should not all share a preshared key. Certificates are composed of a public and private key and can be signed by a primary certificate known as a certificate authority (CA). In this way, certificates can be checked to see if they are signed with a trusted CA.
Field Descriptions - IPsec VPNs Page
|
Field |
Description |
|---|---|
|
Name |
The name of the IPsec VPN. |
|
Description |
The description of the IPsec VPN. |
|
VPN Topology |
The types of deployment topologies for IPsec VPN, such as site-to-site, hub-and-spoke, and remote access VPNs. |
|
Profile Type |
The type of VPN profile, such as Inline Profile or Shared Profile. |
|
Profile Name |
The name of the VPN profile. The security parameters are defined in this profile to establish the VPN connection between two sites. |
|
Tunnel Mode |
The tunnel mode, such as Route Based or Policy Based. |
|
Configuration State |
The configuration state of the IPsec VPN. |
|
Status |
You can verify your VPN configurations before updating the configuration to the device.
|
|
Created by |
The email address of the user who created the IPsec VPN. |
