Decrypt Profiles Overview
Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL, also called Transport Layer Security (TLS), ensures the secure transmission of data between a client and a server through a combination of privacy, authentication, confidentiality, and data integrity. SSL relies on certificates and private–public key exchange pairs for this level of security.
Server authentication guards against fraudulent transmissions by enabling a Web browser to validate the identity of a Web server. Confidentiality mechanisms ensure that communications are private. SSL enforces confidentiality by encrypting data to prevent unauthorized users from eavesdropping on electronic communications. Finally, message integrity ensures that the contents of a communication have not been tampered with.
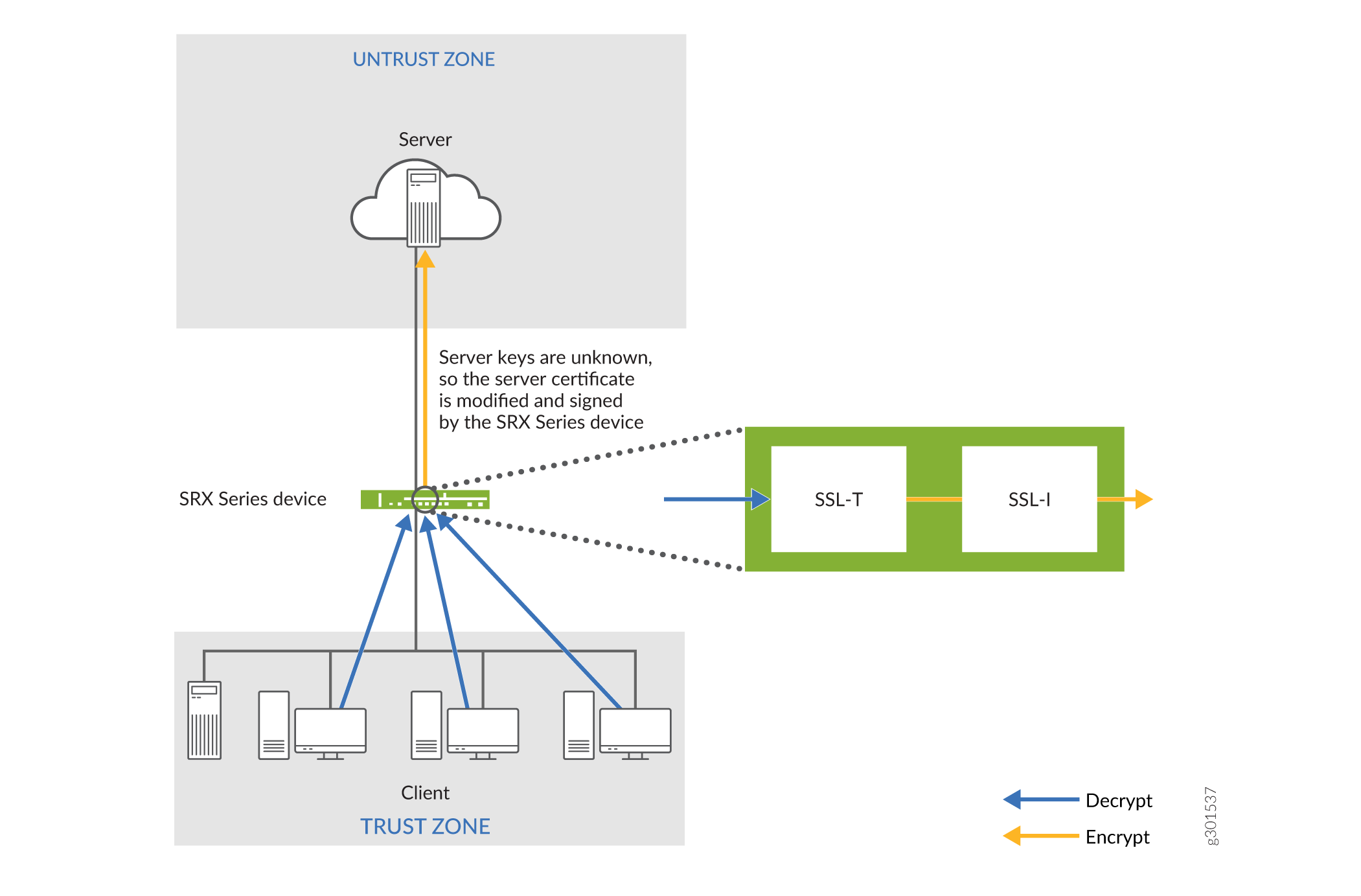
SSL proxy performs SSL encryption and decryption between the client and the server, but neither the server nor the client can detect its presence. SSL proxy ensures that it has the keys to encrypt and decrypt the payload:
-
For the server, SSL proxy acts as a client—SSL proxy generates the shared pre-master key, it determines the keys to encrypt and decrypt.
-
For the client, SSL proxy acts as a server—SSL proxy first authenticates the original server and replaces the public key in the original server certificate with a key that is known to it. It then generates a new certificate by replacing the original issuer of the certificate with its own identity and signs this new certificate with its own public key (provided as a part of the proxy profile configuration). When the client accepts such a certificate, it sends a shared pre-master key encrypted with the public key on the certificate. Because SSL proxy replaced the original key with its own key, it is able to receive the shared pre-master key. Decryption and encryption take place in each direction (client and server), and the keys are different for both encryption and decryption.
The below figure shows how SSL proxy works on an encrypted payload. SSL proxy uses the following services:
-
SSL-T-SSL terminator on the client side.
-
SSL-I-SSL initiator on the server side.
Supported Ciphers in Proxy Mode
An SSL cipher comprises encryption ciphers, authentication method, and compression. The below table displays a list of supported ciphers. NULL ciphers are excluded.
The following SSL protocols are supported:
-
SSLv3
-
TLS1
|
SSL Cipher |
Key Exchange Algorithm |
Data Encryption |
Message Integrity |
|---|---|---|---|
|
RSA_WITH_RC4_128_MD5 |
RSA key exchange |
128-bit RC4 |
MD5 hash |
|
RSA_WITH_RC4_128_SHA |
RSA key exchange |
128-bit RC4 |
Secure Hash Algorithm (SHA) hash |
|
RSA_WITH_DES_CBC_SHA |
RSA key exchange |
DES CBC |
SHA hash |
|
RSA_WITH_3DES_EDE_CBC_SHA |
RSA key exchange |
3DES EDE/CBC |
SHA hash |
|
RSA_WITH_AES_128_CBC_SHA |
RSA key exchange |
128-bit AES/CBC |
SHA hash |
|
RSA_WITH_AES_256_CBC_SHA |
RSA key exchange |
256-bit AES/CBC |
SHA hash |
|
RSA_EXPORT_WITH_RC4_40_MD5 |
RSA-export |
40-bit RC4 |
MD5 hash |
|
RSA_EXPORT_WITH_DES40_CBC_SHA |
RSA-export |
40-bit DES/CBC |
SHA hash |
|
RSA_EXPORT1024_WITH_DES_CBC_SHA |
RSA 1024 bit export |
DES/CBC |
SHA hash |
|
RSA_EXPORT1024_WITH_RC4_56_MD5 |
RSA 1024 bit export |
56-bit RC4 |
MD5 hash |
|
RSA_EXPORT1024_WITH_RC4_56_SHA |
RSA 1024 bit export |
56-bit RC4 |
SHA hash |
|
RSA-WITH-AES-256-GCM-SHA384 |
RSA key exchange |
256-bit AES/GCM |
SHA384 hash |
|
RSA-WITH-AES-256-CBC-SHA256 |
RSA key exchange |
256-bit AES/CBC |
SHA256 hash |
|
RSA-WITH-AES-128-GCM-SHA256 |
RSA key exchange |
128-bit AES/GCM |
SHA256 hash |
|
RSA-WITH-AES-128-CBC-SHA256 |
RSA key exchange |
128-bit AES/CBC |
SHA256 hash |
Server Authentication
Implicit trust between the client and the device (because the client accepts the certificate generated by the device) is an important aspect of SSL proxy. It is extremely important that server authentication is not compromised; however, in reality, self-signed certificates and certificates with anomalies are in abundance. Anomalies can include expired certificates, instances of common name not matching a domain name, and so forth.
You can specify that the SSL proxy should ignore server authentication completely. In this case, SSL proxy ignores errors encountered during the server certificate verification process (such as CA signature verification failure, self-signed certificates, and certificate expiry).
You can specify whether the SSL proxy should ignore server authentication errors or not during the creation of an SSL proxy profile.
-
If you specify that server authentication errors should not be ignored, the following scenarios occur:
-
If authentication succeeds, a new certificate is generated by replacing the keys and changing the issuer name to the issuer name that is configured in the root CA certificate in the proxy profile.
-
If authentication fails, the connection is dropped.
-
-
If you specify that server authentication errors should be ignored, the following scenarios occur:
Note:We do not recommend that you configure this option for authentication because configuring it results in websites not being authenticated at all. However, you can use this option to effectively identify the root cause for dropped SSL sessions.
-
If the certificate is self-signed, a new certificate is generated by replacing the keys only. The issuer name is not changed. This ensures that the client browser displays a warning that the certificate is not valid.
-
If the certificate has expired or if the common name does not match the domain name, a new certificate is generated by replacing the keys and changing the issuer name to SSL-PROXY: DUMMY_CERT:GENERATED DUE TO SRVR AUTH FAILURE. This ensures that the client browser displays a warning that the certificate is not valid.
-
Root CA
In a public key infrastructure (PKI) hierarchy, the root CA is at the top of the trust path. The root CA identifies the server certificate as a trusted certificate.
Trusted CA List
SSL proxy ensures secure transmission of data between a client and a server. Before establishing a secure connection, SSL proxy checks certificate authority (CA) certificates to verify signatures on server certificates. For this reason, a reasonable list of trusted CA certificates is required to effectively authenticate servers.
Session Resumption
An SSL session refers to the set of parameters and encryption keys that are created when a full handshake is performed. A connection is the conversation or active data transfer that occurs within the session. The computational overhead of a complete SSL handshake and generation of primary keys is considerable. In short-lived sessions, the time taken for the SSL handshake can be more than the time for data transfer. To improve throughput and still maintain an appropriate level of security, SSL session resumption provides a mechanism for caching sessions. This way, session information, such as the pre-master secret key and agreed-upon ciphers, can be cached for both the client and the server. A session ID identifies the cached information. In subsequent connections, both parties agree to use the session ID to retrieve the information rather than create pre-master secret key. Session resumption shortens the handshake process and accelerates SSL transactions.
SSL Proxy Logs
When logging is enabled in a decrypt profile, the SSL proxy can generate the messages shown in the below table.
|
Log Type |
Description |
|---|---|
|
All |
All logs are generated. |
|
Warning |
Logs used for reporting warnings. |
|
Info |
Logs used for reporting general information. |
|
Error |
Logs used for reporting errors. |
|
Session Whitelisted |
Logs generated when a session is allowed. |
|
Session Allowed |
Logs generated when a session is processed by SSL proxy even after encountering some minor errors. |
|
Session Dropped |
Logs generated when a session is dropped by SSL proxy. |
All logs contain similar information; the message field contains the reason for the log generation. One of three prefixes shown below identifies the source of the message. Other fields are descriptively labeled.
|
Prefix |
Description |
|---|---|
|
system |
Logs generated because of errors related to the device or an action taken as part of the decrypt profile. Most logs fall into this category. |
|
openssl error |
Logs generated during the handshake process if an error is detected by the openssl library. |
|
certificate error |
Logs generated during the handshake process if an error is detected in the certificate (X.509 related errors). |
Use the Decrypt Profiles page to view and to manage decrypt profiles. To access this page, click .
Field Descriptions
|
Field |
Description |
|---|---|
|
Name |
Name of the decrypt profile. |
|
Preferred Cipher |
Preferred cipher associated with the profile. |
|
Custom Ciphers |
The set of ciphers, if the preferred cipher is Custom, which the SSH server uses to perform the encryption and the decryption functions. |
|
Exempted Address |
Addresses that are exempted from decrypt processing. |
|
Description |
Description of the decrypt profile. |
|
Root Certificate |
Root certificate associated with the decrypt profile. |
|
Field |
Description |
|---|---|
|
General Information |
|
|
Name |
Name of the decrypt profile. |
|
Description |
Description of the decrypt profile. |
|
Preferred Cipher |
Preferred cipher associated with the proxy profile. |
|
Custom Ciphers |
The set of ciphers, if the preferred cipher is Custom, which the SSH server uses to perform the encryption and the decryption functions. |
|
Flow Trace Enabled |
Indicates whether flow tracing is enabled or disabled. |
|
Certificates |
Displays the root certificate and the trusted certificate authorities associated with the root certificate. |
|
Exempted Address |
Addresses that are exempted from decrypt processing. |
|
Exempted URL Categories |
URL categories that are exempted from decrypt processing. |
|
Actions |
|
|
Ignore |
Indicates whether server authentication failure is ignored (Enabled) or not (Disabled). |
|
Session Resumption |
Indicates whether session information is cached to enable session resumption (Enabled) or not (Disabled). |
|
Logging |
If logging is enabled, indicates the type of events that are logged. |
|
Renegotiation |
Indicates the type of renegotiation required for a change in SSL parameters after creating a session and establishing the SSL tunnel transport. |
