To migrate your on-premises security policies to Secure Edge,
you must convert the security policy rules to Secure Edge policy. Use the Add SRX policy rules
to Secure Edge policy page to add rules from the SRX policy to Secure Edge policy.
The Secure Edge policy supports only a single pair of zones
(trust to untrust). All the selected zones of the SRX policy in the source endpoints are
converted as trust zone. The destination endpoints are converted as untrust zone.
Note:
Before initiating the conversion of SRX policy rules to Secure Edge policy, the system
administrator must ensure that the source identities referred in the SRX policy rules are
in-sync with JIMS Secure Edge source identities. This is to avoid any customization issues
at a later stage.
To add the SRX policy rules to Secure Edge policy:
-
Select .
The Secure Edge Policy page appears.
-
From the More list, select Add rules from SRX policy.
The Add SRX policy rules to Secure Edge policy page appears.
-
Select the SRX policy to be added to the Secure Edge policy and click
Next.
The Getting Started page provides additional information about adding the SRX
policy rules to Secure Edge policy, as shown in
Figure 1.
Figure 1: Getting Started Page
-
Click Next.
-
Complete the configuration as shown in the following table.
Table 1: Fields on the Add Rule Options page
| Field |
Description |
| Add Rule Options |
|
Name
|
Name of the SRX policy.
|
|
Source (trust) zones
|
Select zones in the existing rules that are applicable for the Internet.
These zones are set as source (trust) zones in the Secure Edge policy
rule.
|
|
Destination (untrust) zones
|
Select zones in the existing rules that are applicable for the Internet.
These zones are set as destination (untrust) zones in the Secure Edge policy
rule.
|
-
Click Next.
The Rules Review page appears, as shown in Figure 2
Figure 2: Rules Review Page
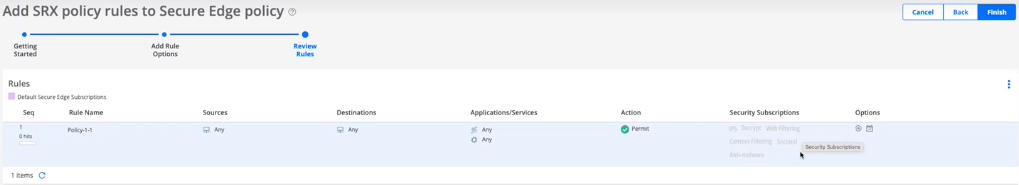
-
In the Review Rules page, preview the converted rules.
For the advanced security profiles conversion, Secure Edge policy takes the following
actions:
-
IPS—Policy is ignored and not converted. Default IPS of Secure Edge policy is
associated. For more information, see IPS Profiles Overview.
-
Content filtering—Policy is ignored and not converted. Default Content filtering
profile of Secure Edge policy is associated. For more information, see Content Filtering Profiles Overview.
-
Decrypt profile—Decrypt profiles are converted as it is except for the root
certificate. The root certificate set is converted to Secure Edge with the name
"jsec-ssl-proxy-root-cert". The decrypt profile name is prefixed with “jse-“.
-
Web filtering—Profile is converted and a new Secure Edge Web Filtering profile is
created with categories that map to current actions and defaults.
-
Antivirus profile—Profile is ignored and not converted.
-
Antispam profile—Profile is ignored and not converted.
-
SecIntel profile—SecIntel profiles are converted as it is. The profile name is
prefixed with “jse-“.
-
Anti-malware profiles—SMTP and IMAP Anti-malware profiles are ignored and not
converted. HTTP Anti-malware profile is converted as it is. The profile name is
prefixed with “jse-“.
-
Click Finish after reviewing the rules.
A job is created to add rules to Secure Edge. Once the conversion is successful, you
are taken back to the Secure Edge Policy page. The converted rules are appended at the
bottom of the existing Secure Edge policy rules. You can reorder the converted rules. You
can perform all the other operations on the converted rules.
Figure 3: Secure Edge Policy Page
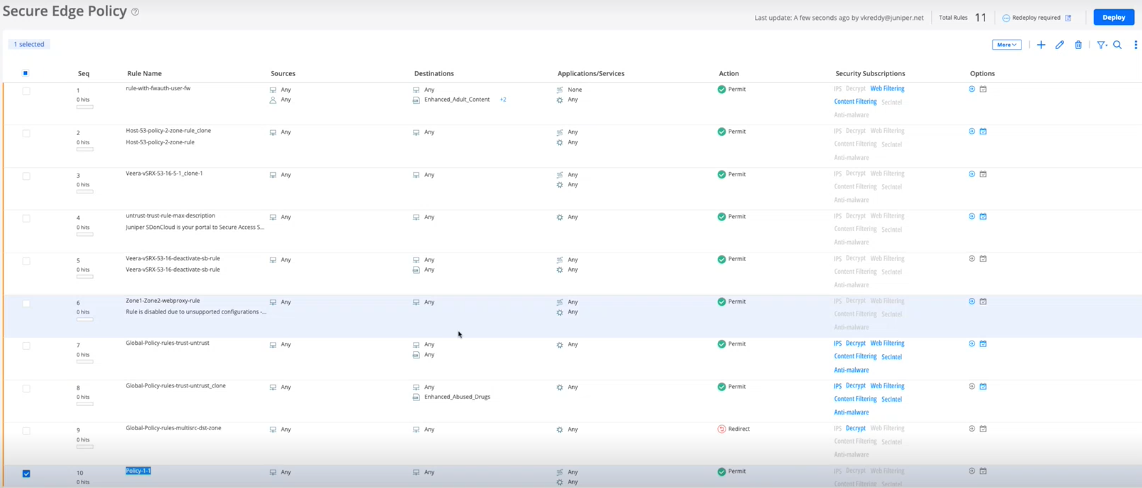
The final step is to deploy the converted policy. Select the policy and click
Deploy.
Note:
-
You cannot reconvert SRX policy rules that are already converted to the Secure Edge
Policy rules. However, if you have added new rules to that particular SRX policy, only
the newly added rules are added to the Secure Edge policy rules.
-
Global rules are selected only if they are matched with the selected source and
destination zones. Global rules that are not associated with a source or destination
zone are ignored and not converted.



