Configuring the Firewall-as-a-Service (FWaaS) Plug-in
Juniper Networks Firewall-as-a-Service (FWaaS) plug-in builds on top of Juniper ML2 and L3 plug-ins. It enables Neutron to configure firewall rules and policies on SRX and vSRX devices. In OpenStack, a tenant can create a firewall and assign a security policy to it. A security policy is a collection of firewall rules. Figure 1 illustrates the relationship of firewall rules, firewall policy, and firewall.

Firewall Rule - Defines the source address and port(s), destination address and port(s), protocol and the action to be taken on the matching traffic.
Firewall Policy - Collection of firewall rules
Firewall - Represents a firewall device.
When you enable a FwaaS plug-in, the SRX or vSRX should act as a router as well as a firewall. The administrator must ensure this while setting up the topology.
Supported Devices
SRX and vSRX series devices
Plug-in Configuration
Before proceeding further, ensure that the following pre-requisites are met:
Topology is set up
devices is added to jnpr_devices table
compute nic → physical network alias mapping is added to jnpr_nic_mapping table.
Compute → Switch connectivity is captured in jnpr_switchport_mapping table (needed for L2 VLAN orchestration)
L2 plug-in is set up. This is optional if you are using a 3rd party ML2 plug-in.
L3 plug-in is set up to use the SRX/vSRX as the router.
To configure Neutron to use Juniper FwaaS service plug-in:
Update the Neutron configuration file
/etc/neutron/neutron.conffile and append service_plug-ins with the following:service_plug-ins = neutron.services.juniper_l3_router.dmi.l3.JuniperL3Plugin, neutron_fwaas.services.juniper_fwaas.dmi.fwaas.JuniperFwaaS
Add firewall to the topology:
admin@controller:~$ jnpr_device add -d dns-name-or-device-ip-address -c firewall -u root-user -p root_password
Define the downlink trunk port on the SRX device on which the RVIs are created by the plug-in.
Update the plug-in database with the port on the SRX device to which the Aggregation Switch is connected:
admin@controller:~$ jnpr_device_port -d srx-device-name-or-switch-ip-address -p port-on-the-srx -t port-type
For example:
admin@controller:~$ jnpr_device_port add -d srx1 –p ge-0/0/1 –t Downlink
Allocate the firewall to a tenant or as a default for all tenants:
admin@controller:~$ jnpr_allocate_device add -t project_id -d SRX/vSRX ip
To allocate the firewall as a default to all the tenants that do not have a firewall allocated to them, use the below command:
admin@controller:~$ jnpr_allocate_device add -t default -d SRX/vSRX ip
Enable Horizon to show Firewall panel.
To display the Firewall panel under the Networks group in the Horizon user interface, open
/usr/share/openstack-dashboard/openstack_dashboard/local/local_settings.py, and update the following configuration:enable_firewall: TrueAfter completing the FWaaS plug-in configuration, restart the following:
Neutron-Server
Ubuntu – service neutron-server restart
CentOS – systemctl restart neutron-server
Apache (restarts Horizon)
Ubuntu – service apache2 restart
CentOS – systemctl restart httpd
From the Horizon GUI, create firewall rules and associate them to a policy. Create a firewall and assign the routers and the firewall policy to it.
On the SRX, you can verify a firewall zone for each routing instance and the corresponding policies pushed within the zones.
Configuring a Dedicated Perimeter Firewall
Requirement of each tenant varies according to the performance and cost of the firewall. For example, a dedicated firewall for better performance and compliance, a lower cost firewall enabled by sharing network resources, or a firewall with a complete administrative access to the networking device so as to leverage the advanced services provided by the device. To meet different requirements of each tenant, the cloud provider must have the provision to allocate dedicated or shared network resources to the tenants.
By using Juniper Networks FwaaS plug-in, a service provider can allocate dedicated or shared resources (physical or virtual) to the tenants.
For example, the service provider can create and configure firewall as follows according to the requirement of the tenant:
Economy - Allocates a shared SRX or vSRX for a group of tenants
Silver - Allocates a dedicated SRX or vSRX per tenant with default specifications
Gold - Allocates a high-end SRX or vSRX
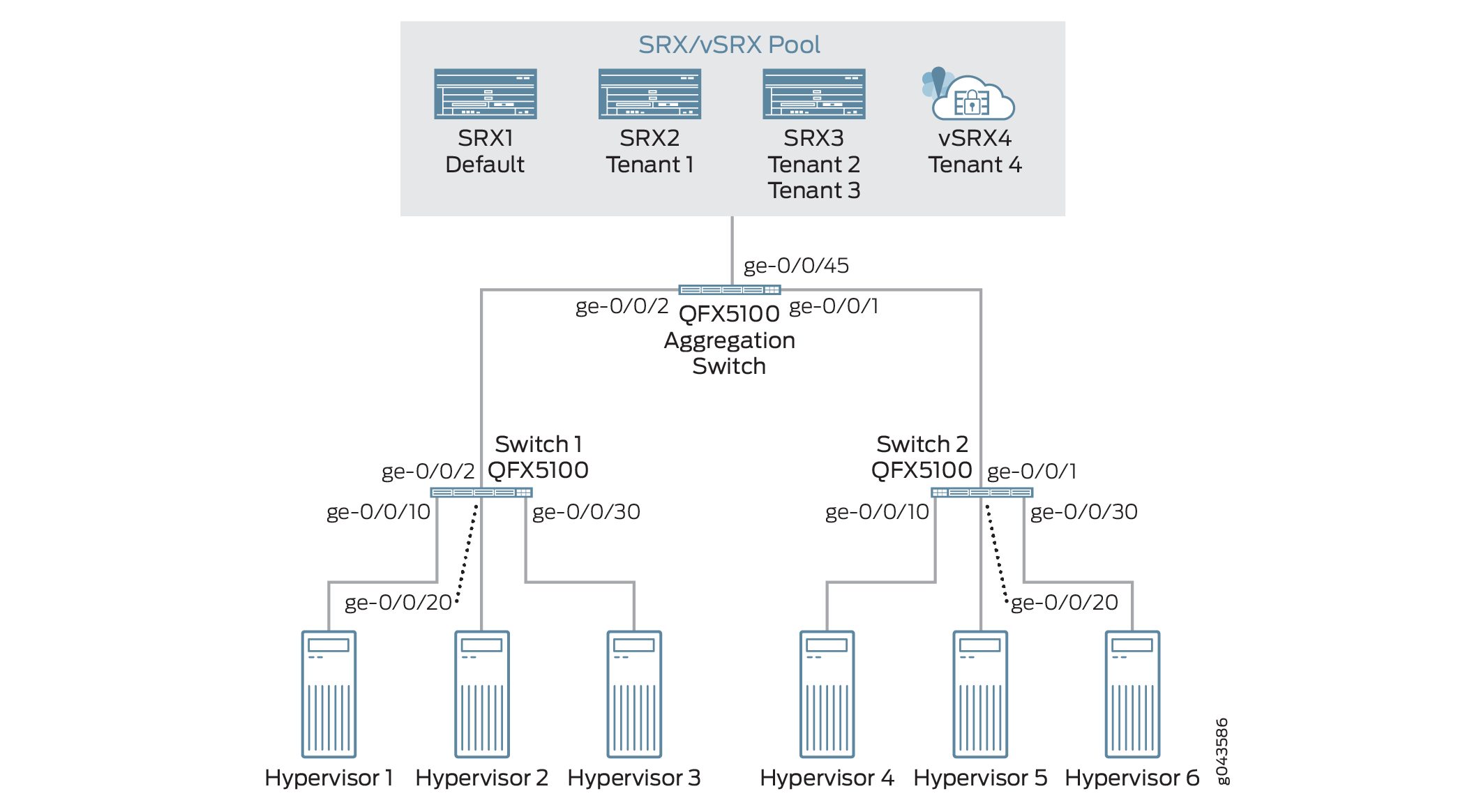
As seen in the Figure 2, you can dedicate SRX/vSRX to a tenant or a group of tenants. This procedure is transparent to the tenant and is done using the supplied CLI tools along with Juniper OpenStack Neutron plug-in.
To allocate a dedicated SRX cluster to a tenant:
Configuring High Availability and Virtual Router Redundancy Protocol
FwaaS plug-in supports High Availability with Virtual
Router Redundancy Protocol (HA with VRRP). In order to use this functionality,
you must create a VRRP pool and assign one of the devices in the pool
to a tenant by using the jnpr_allocate_device command.
To create a VRRP pool and to assign a device to a tenant:
