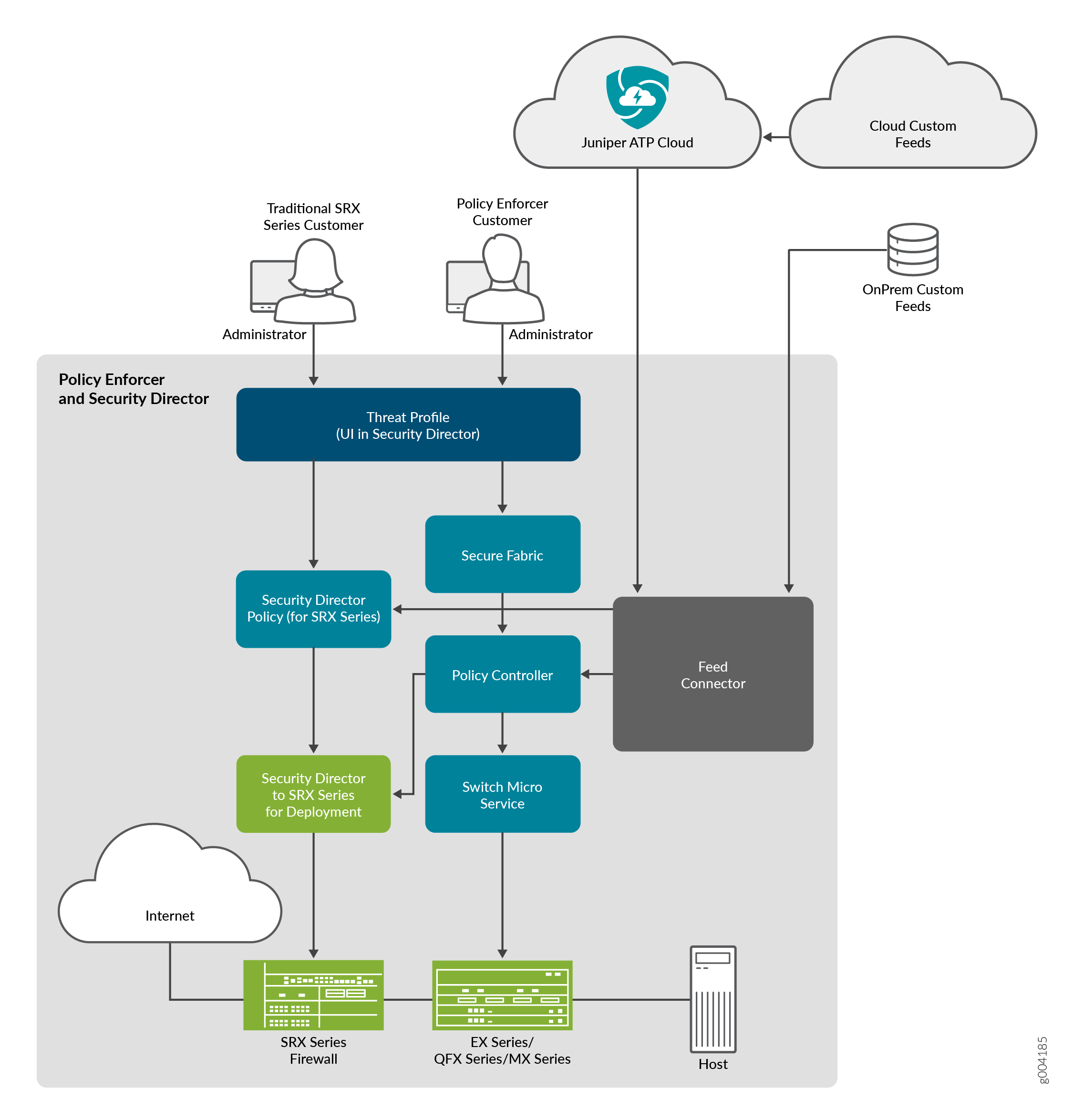
Policy Enforcer Overview
Policy Enforcer, a component of the Junos Space Security Director user interface, integrates with Juniper ATP Cloud to provide centralized threat management and monitoring to your Juniper connected security network, giving you the ability to combine threat intelligence from different solutions and act on that intelligence from one management point.
It also automates the enforcement of security policies across the network and quarantines infected endpoints to prevent threats across firewalls and switches. Working with Juniper ATP Cloud, it protects perimeter-oriented threats as well as threats within the network. For example, if a user downloads a file from the Internet and that file passes through an SRX Series firewall, the file can be sent to the Juniper ATP Cloud cloud for malware inspection. If the file is determined to be malware, Policy Enforcer identifies the IP address and MAC address of the host that downloaded the file. Based on a user-defined policy, that host can be put into a quarantine VLAN or blocked from accessing the Internet.
Figure 1 illustrates the flow diagram of Policy Enforcer over a traditional SRX Series configuration.
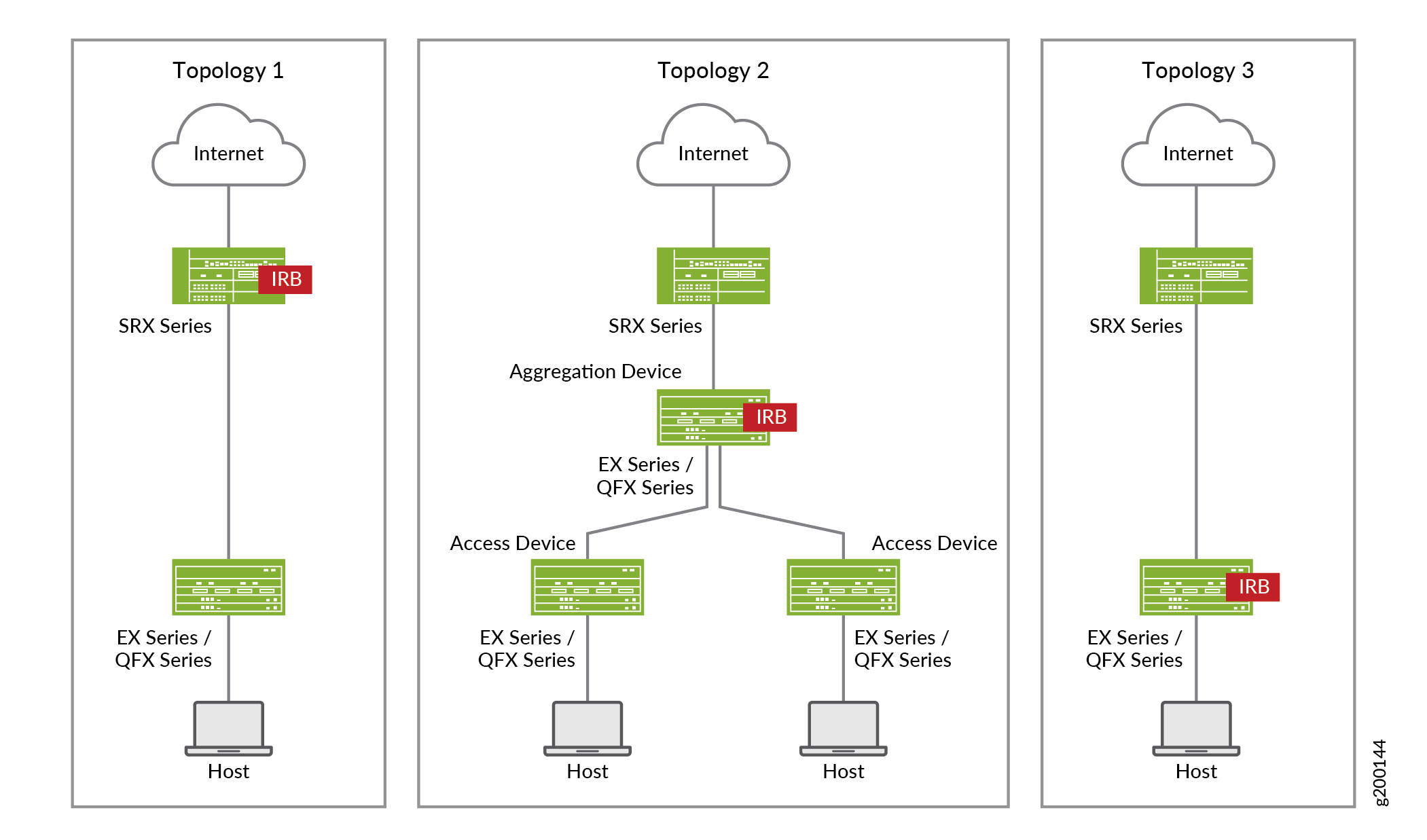
Supported Topologies
Policy Enforcer supports the following topologies:
-
Client to Layer 2 switch to Layer 3 SRX (IRB)
-
Client to Layer 2 switch to Layer 3 switch (IRB)
-
Client to Layer 2/Layer 3 switch (IRB)
Figure 2 illustrates the Policy Enforcer deployment topologies.