Understanding Juniper Connected Security for VMware NSX-T Integration
This section presents an overview of how Juniper Networks vSRX Virtual Services Gateway integrates in the VMware NSX-T environment as an advanced security service with Junos Space Security Director as its security manager.
VMware NSX-T Overview
VMware NSX-T is VMware’s network virtualization platform for the Software Defined Data Center (SDDC). Like server virtualization, network virtualization de-couples the network functions from the physical devices. VMware NSX-T is designed to address application frameworks and architectures that have heterogeneous endpoints and technology stacks. VMware NSX-T is not directly coupled with vShpere and therefore it supports various Hypervisors, Containers, BareMetal, and public clouds such as Amazon Web Service and Azure. With VMware NSX-T, you can design hybrid cloud for organizations where critical data and services are hosted within private cloud and web services or high availability application in Public clouds.
VMware NSX-T is the latest generation of VMware’s network virtualization product series. NSX-T is the successor to NSX-V. NSX-T supports third-party Hypervisors and next generation overlay encapsulation protocols such as Generic Network Virtualization Encapsulation (Geneve). NSX-T acts as a network Hypervisor that allows software abstraction of various network services that include logical switch (segments), logical routers (Tier-0 or Tier-1 Gateway), logical firewalls, logical load balancers, and logical VPNs.
VMware NSX-T provides L2-L4 stateful firewall features, network segmentations, multi tenancy support, L2/L3 VPN, load balancer, DHCP, source/destination NAT and many more services at Edge Gateway. VMware NSX-T provides framework to integrate the advanced security services as North-South at Edge Gateway.
Each virtual machine running in NSX-T environment can be protected with a full stateful firewall engine at a very granular level policy. Such policies can be application specific including services. vSRX runs as a service virtual machine and provides advanced services such as L4 to L7 services.
To deploy the advanced security features of the vSRX Virtual Services Gateway in the VMware NSX-T environment, the Junos Space Security Director, vSRX, and NSX-T Manager operate together as a solution to fully automate the provisioning and deployment of the vSRX to protect applications and data from advanced cyberattacks.
vSRX Integration with NSX-T Manager and Junos Space Security Director
To deploy the advanced security features of the vSRX Virtual Services Gateway in the VMware NSX-T environment, the Junos Space Security Director, vSRX, and NSX-T Manager operate together as a joint solution to fully automate the provisioning and deployment of the vSRX to protect applications and data from advanced cyberattacks.
Integration of the vSRX VM in the VMware NSX-T environment involves use with the following management software:
-
Junos Space Security Director—The centralized security management platform responsible for service registration and configuration of each vSRX instance. The Security Director provides you with the ability to manage a distributed network of virtualized and physical firewalls from a single location. The Security Director functions as the management interface between the NSX-T Manager and the vSRX Services Gateway. Security Director manages the firewall policies on all vSRX instances.
-
NSX-T Manager—The centralized network management component of VMware NSX.
The NSX-T Manager is added as a registered device in the Security Director and communication is bidirectionally synchronized by the Junos Space Policy Enforcer between the two management platforms. All shared objects (such as security groups) are synchronized between the NSX-T Manager and Security Director. This includes the IP addresses of all VMs, including the vSRX agent VMs. Security Director creates an address group for each security group synchronized from the NSX-T Manager, along with the addresses of each member of the security group. The security groups discovered from the NSX-T Manager are mapped to dynamic address groups (DAG) in Security Director. Policy Enforcer retains the mapping of all IP addresses between security groups and dynamic address groups.
The vSRX Services Gateway is deployed as a partner service appliance in the VMware NSX-T environment. Use the security policies to direct all VM traffic through the vSRX VM for L4 through L7 advanced security analysis.
High-Level Workflow
Figure 1 provides a high-level workflow of how the NSX-T Manager, Security Director, and vSRX interact to deploy vSRX as a security service in the VMware NSX-T environment.
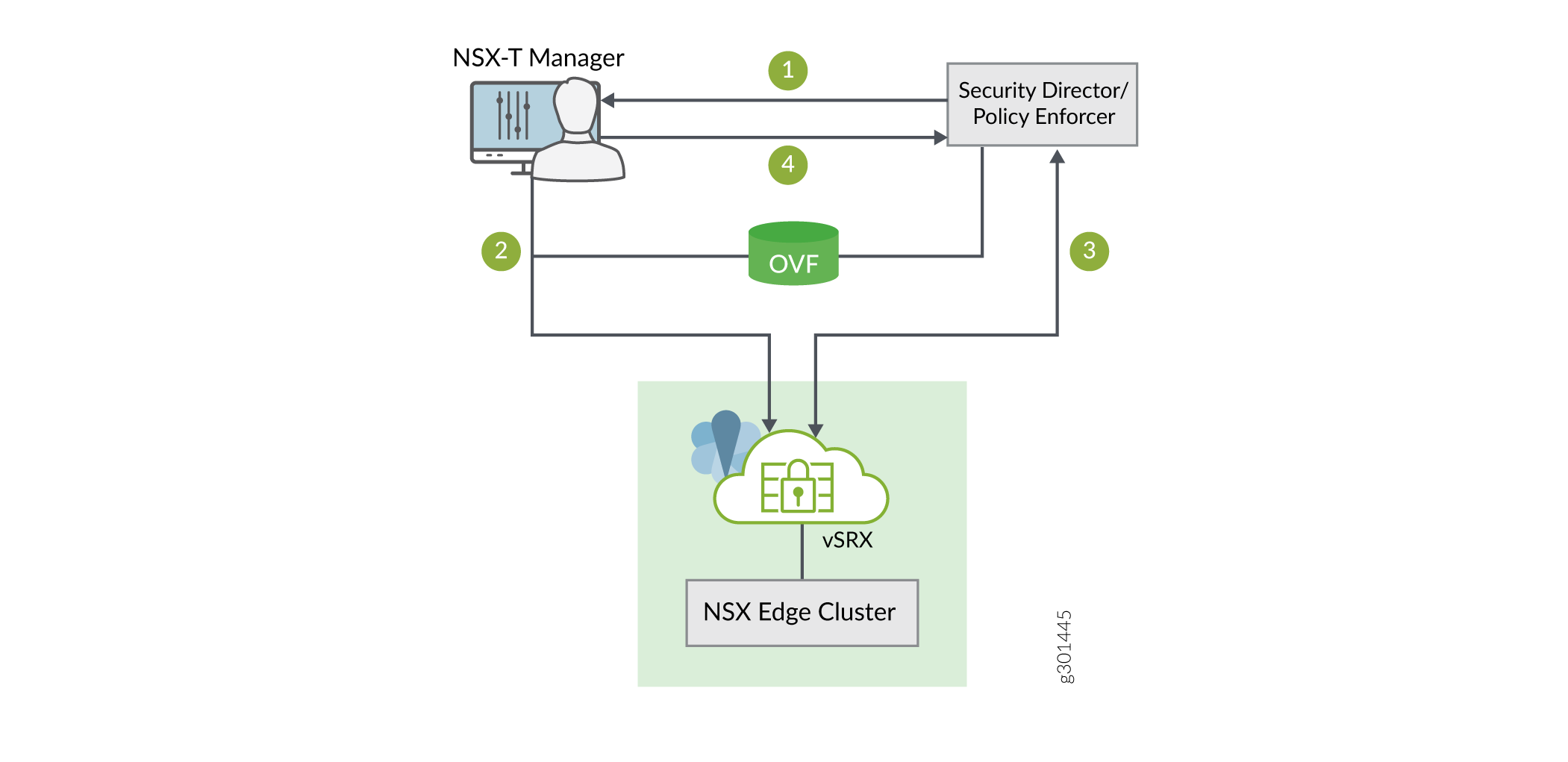
-
The Junos Space Security Director initiates communication with the NSX-T Manager. The Security Director discovers, registers, and adds the NSX-T Manager as a device in its database. The Security Director also deploys the vSRX instance from the .ovf file and registers it as a security service. The NSX-T Manager and its inventory of shared objects (for example, security groups) and addresses are then synchronized with the Security Director. The registration process uses Policy Enforcer to enable bidirectional communication between Security Director and the NSX-T Manager.
-
The NSX-T Manager deploys the registered vSRX instance as a Juniper security service to the NSX Edge Cluster. The deployment is based on the vSRX .ovf file.
-
After the vSRX agent VM is provisioned as a security service, NSX-T Manager notifies Security Director by using REST API callbacks. Security Director pushes the initial boot configurations and Junos OS configuration policies to each vSRX agent VM to support the NSX-T security group. Security Director is aware of the NSX-T security groups and corresponding address groups, and all deployed vSRX agent VMs are automatically discovered.
Security policies redirect relevant network traffic originating from the VMs in a specific security group to the Juniper security service vSRX agent VM for further analysis.
The Security Director dynamically synchronizes the object database to all vSRX agent VMs deployed in NSX Edge Cluster. Security groups discovered from NSX-T Manager are mapped to a dynamic address group (DAG) in Security Director. The Security Director manages the firewall policies on the vSRX agent VMs. Using Security Director, you create advanced security service policies (for example, an application firewall policy or an IPS policy) and then push those policies.
-
The NSX-T Manager continue to send real-time updates on changes in the virtual environment to Security Director.
