Migrate Policy Enforcer Release 23.1R1 to Policy Enforcer Release 24.1R1.
Starting in Junos Space Security Director Release 24.1R1, you cannot use standalone Policy Enforcer. You'll need to migrate to Policy Enforcer running on Security Director Insights 24.1R1.
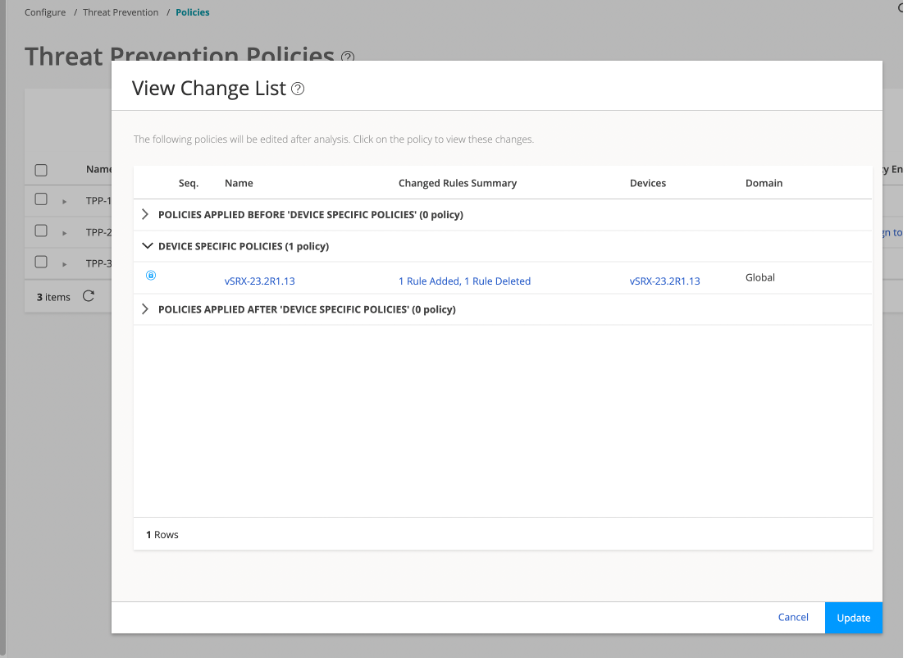
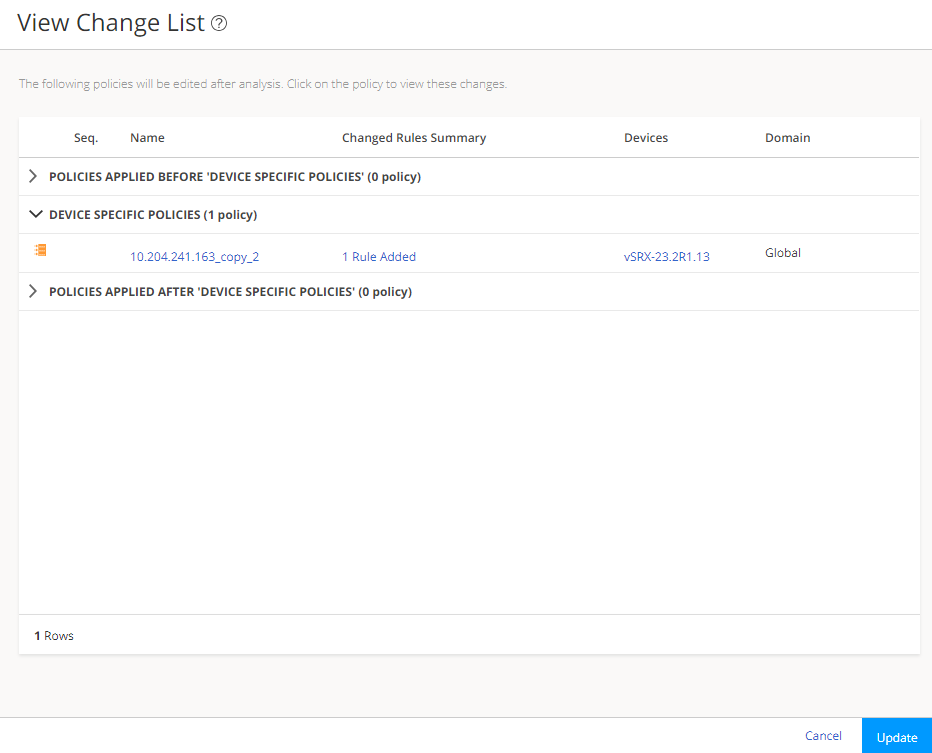
You must migrate the standalone Policy Enforcer Release 23.1R1 data to Security Director Insights 24.1R1.
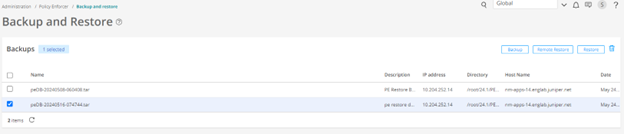
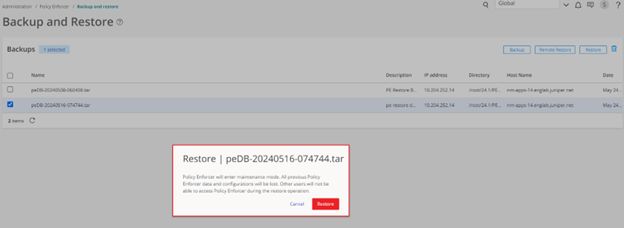
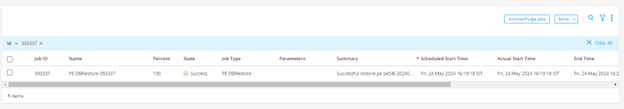
Policy Enforcer migration procedure is based on the existing backup and restore functionality.
You must migrate the standalone Policy Enforcer Release 23.1R1 data to Security Director Insights 24.1R1.
Before migrating Standalone Policy Enforcer to Security Director Insights Policy Enforcer, you must first upgrade from Junos Space Network Management Platform 23.1R1 or Security Director 23.1R1 to Junos Space Network Management Platform 24.1R1 or Security Director 24.1R1 respectively.
For more details on the upgrade procedure, see Upgrade to Junos Space Network Management Platform Release 24.1R1.
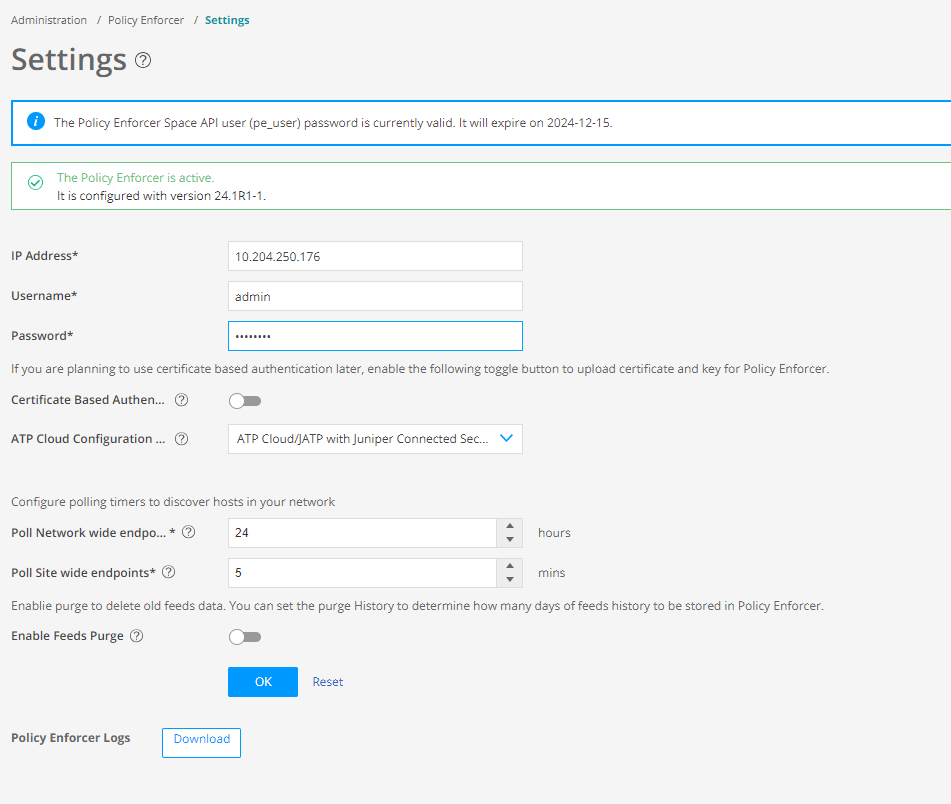
To migrate Standalone Policy Enforcer to Security Director Insights Policy Enforcer: