Understanding the Policy Enforcer Connector API
The Policy Enforcer Connector framework supports integration of Policy Enforcer with other external third party systems for the following capabilities:
Threat remediation of endpoints for both infected and DDOS attacks on a multivendor network.
Application level micro segmentation advanced Layer 7 firewall security for workloads in public and private clouds, and for on-premises deployments.
Based on the integration requirement with the specific external system, the connector plugins can be implemented in adherence to the Connector Framework API specification. Currently, Policy Enforcer bundles the following plug-ins:
Aruba ClearPass, Cisco Identify Services Engine (ISE), ForeScout CounterAct, Pulse Policy Secure for threat remediation use cases.
Amazon Web Services (AWS), Microsoft Azure, VMWare NSX, and Juniper Contrail Cloud controllers for application Layer 7 advance firewall security.
Policy Enforcer provides a set of APIs and schemas to third party vendors to implement the plug-in accordingly. The plug-in can be deployed in a separate Virtual Machine (VM) and communicate with Policy Enforcer via the HTTP protocol after registering with Policy Enforcer, as shown in Figure 1.
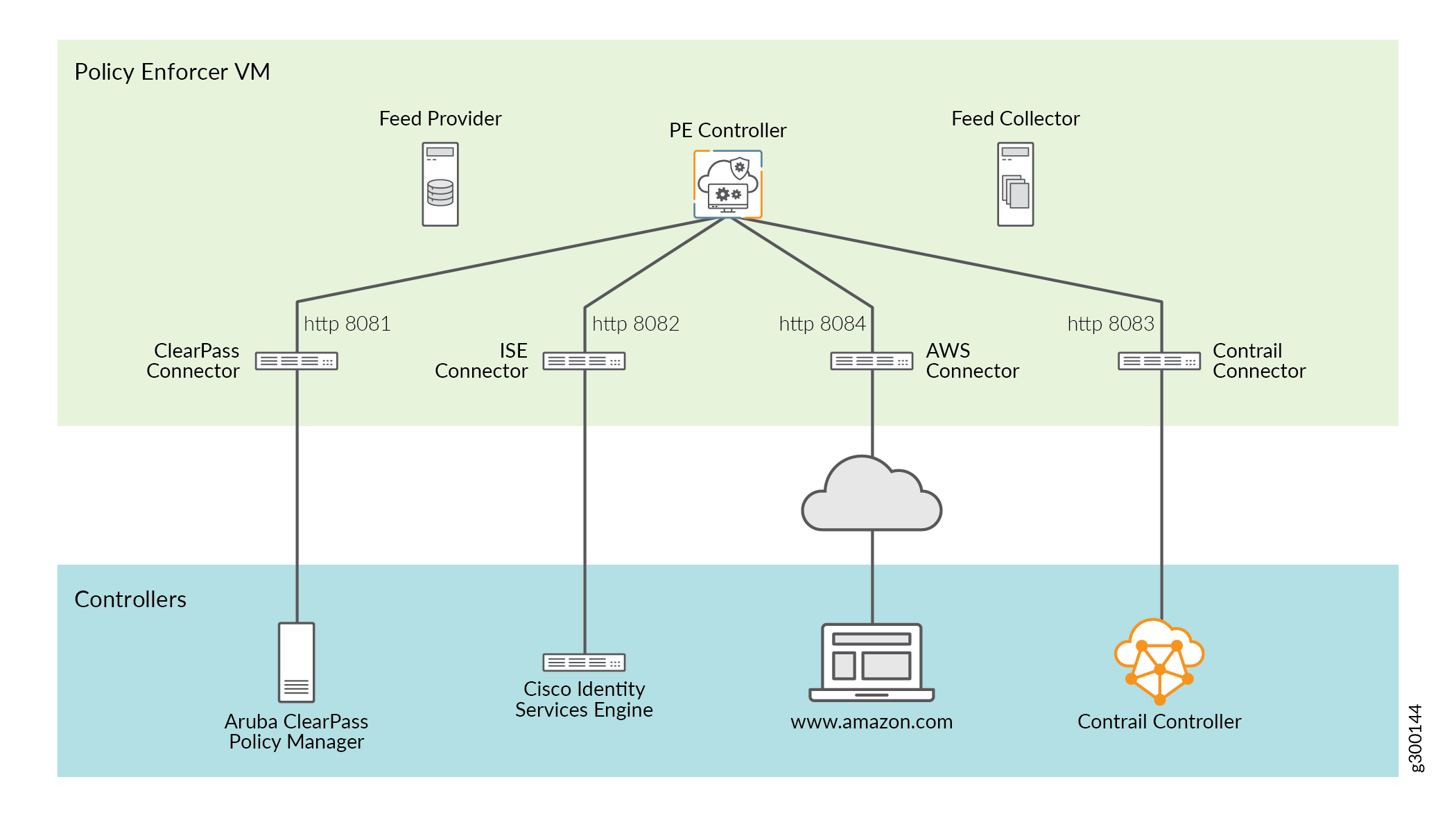
Configure a connector for third-party products to unify policy enforcement across all network elements. You must allocate a new port number when you create a new connector. For each connector, you must instantiate connector instances. These connector instances are similar to logical configurations within the connector servers. You require connector instances for every unique address space that you want to support.
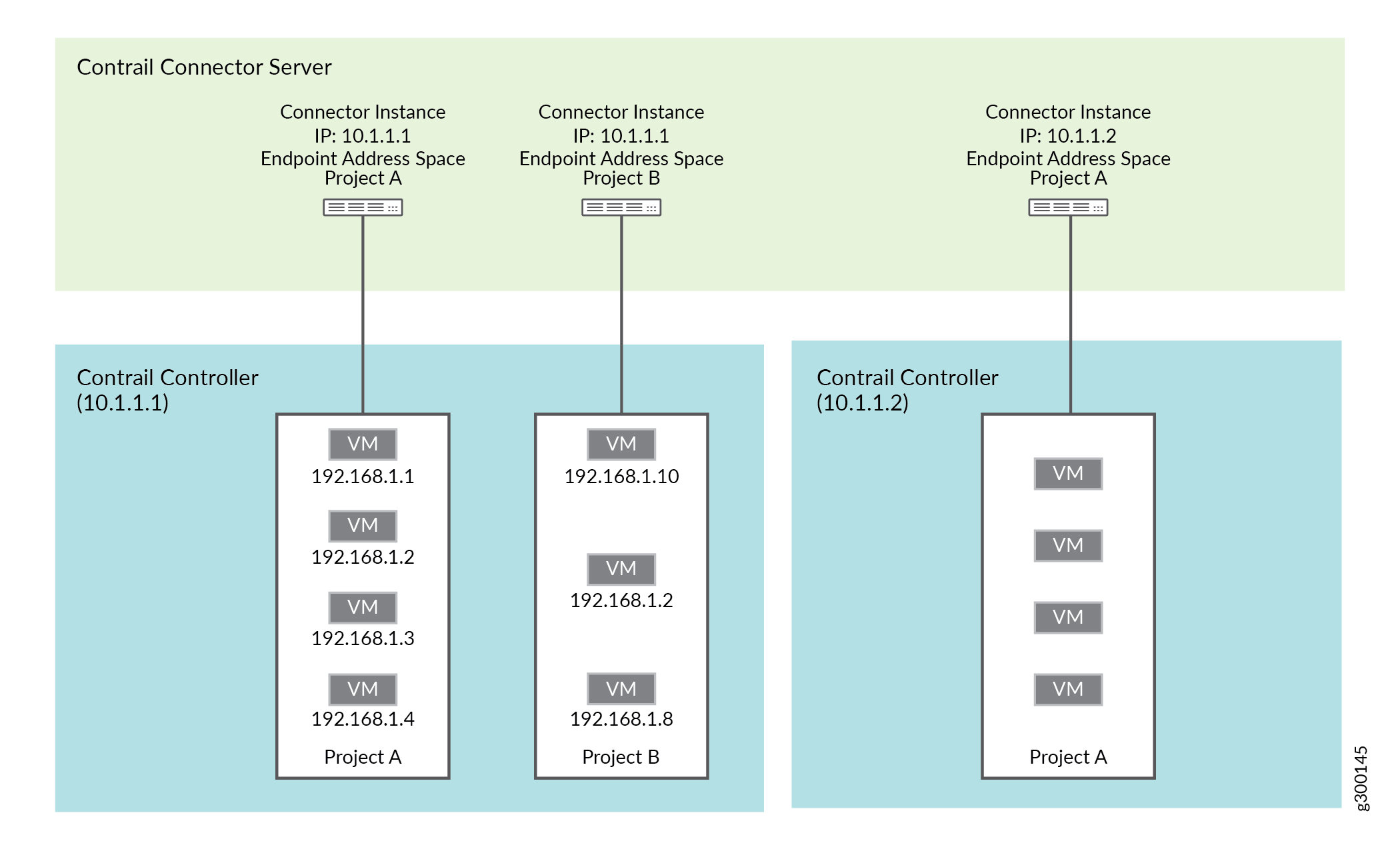
For example, in Contrail system, Projects implement the unique address spaces for set of VMs, as shown in Figure 2. There could be overlapping address spaces between projects. However, you must instantiate connector instances and point them to these address spaces in your connector server. Instantiate a connector instance identified by the controller IP address (the address of the external controller system) and provide the name for an endpoint address space. The combination of the controller IP address and the endpoint address space name identifies the connector instance.
Inputs to instantiate a connector are received through the Policy Enforcer user interface (UI) and passed them to an appropriate connector instance through the POST API call. Use the POST /connector/instances API and specify the following parameters:
Controller IP address
Controller port number
Username of the controller
Password of the controller
Endpoint address space information
Type—Specify Project for Contrail and VPC for AWS.
Name—Unique name for the specified Project or VPC.
Once you create a connector instance, the connector server allocates a unique connector ID. You can use this connector ID to initiate a GET call to retrieve the same information that you configured using the POST method.
