Use Case 1: Configure IPS Policy in a Firewall Policy
An intrusion prevention system (IPS) policy enables you to selectively enforce various attack detection and prevention techniques on the network traffic passing through an IPS-enabled device. In this section, you’ll learn how to create an IPS policy and then assign the IPS policy to a firewall policy rule that is assigned to a device running Junos OS Release 18.2 or later.
What's Next
To learn more about IPS features, see Junos Space Security Director User Guide.
Benefits
-
Assign a different IPS policy to each firewall policy rule.
-
IPS policy matches are handled within the standard or unified firewall policy to which the IPS policy is assigned.
-
Simplifies application-based security policy management at Layer 7.
-
Provides greater control and extensibility to manage dynamic applications traffic.
Before You Begin
-
Install Junos Space Security Director and Log Collector. See Junos Space Security Director Installation and Upgrade Guide.
-
Ensure that IPS is enabled on the SRX Series device.
-
Ensure that the SRX Series device runs Junos OS Release 18.2 or later.
-
Although this use case has been specifically validated against Junos Space Security Director Release 19.3 and an SRX Series device running Junos OS Release 18.2, you can use Junos OS Release 18.2 or later.
-
Only mandatory fields and other required fields are included in the procedures in this use case.
Overview
Starting in Junos Space Security Director Release 19.3, you cannot assign devices running Junos OS Release 18.2 and later to an IPS policy from the IPS Policies page. You’ll need to assign an IPS policy to a firewall policy rule for devices running Junos OS Release 18.2 and later. The CLI configuration for the IPS policy is generated along with the standard or unified firewall policy to which the IPS policy is assigned. When an IPS policy is configured in a firewall policy, the traffic that matches the specified criteria is checked against the IPS rule bases. This type of configuration can be used to monitor traffic to and from the secure area of an internal network as an added security measure for confidential communications.
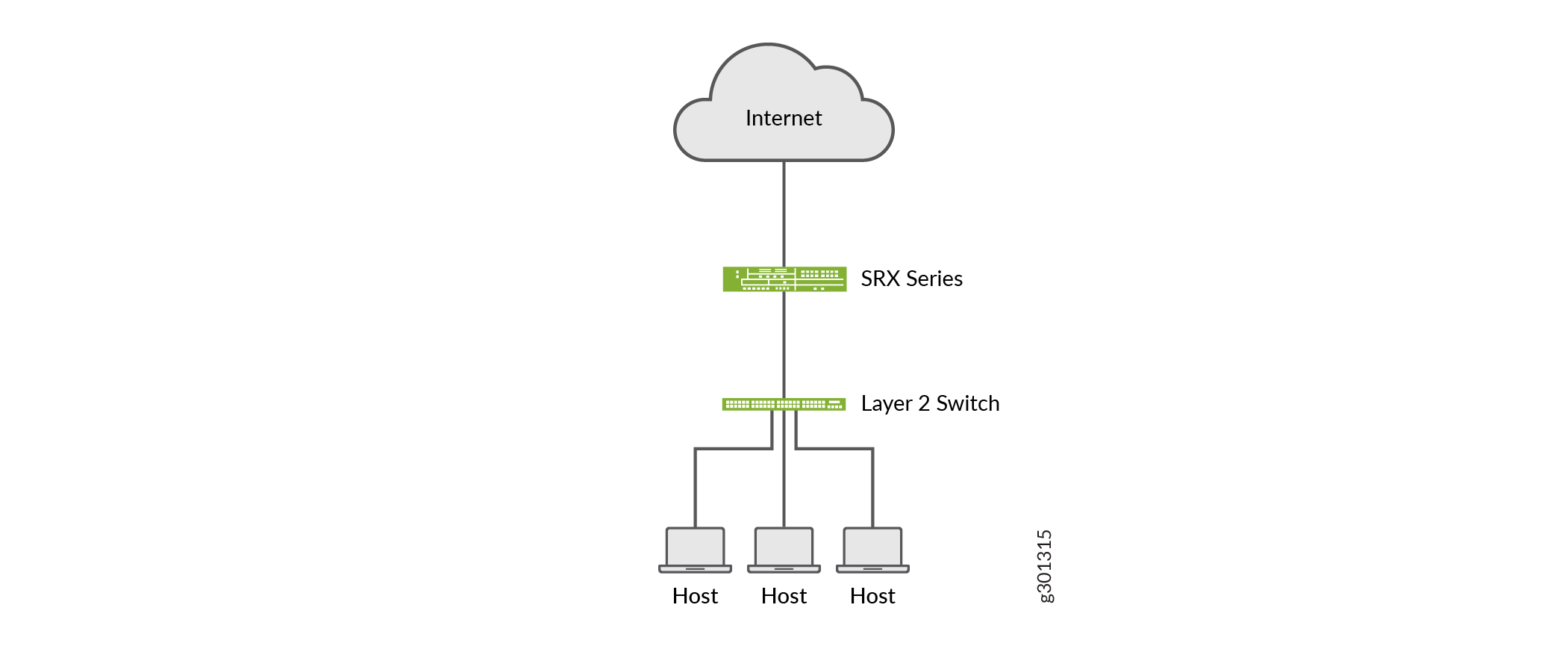
In the following topology, we have an enterprise local area network behind a Layer 2 switch. The switch is connected to an SRX Series firewall that has IPS enabled and inspects all the traffic traveling in and out of the network. The SRX Series device can be in any form: hardware, virtual, or containerized.
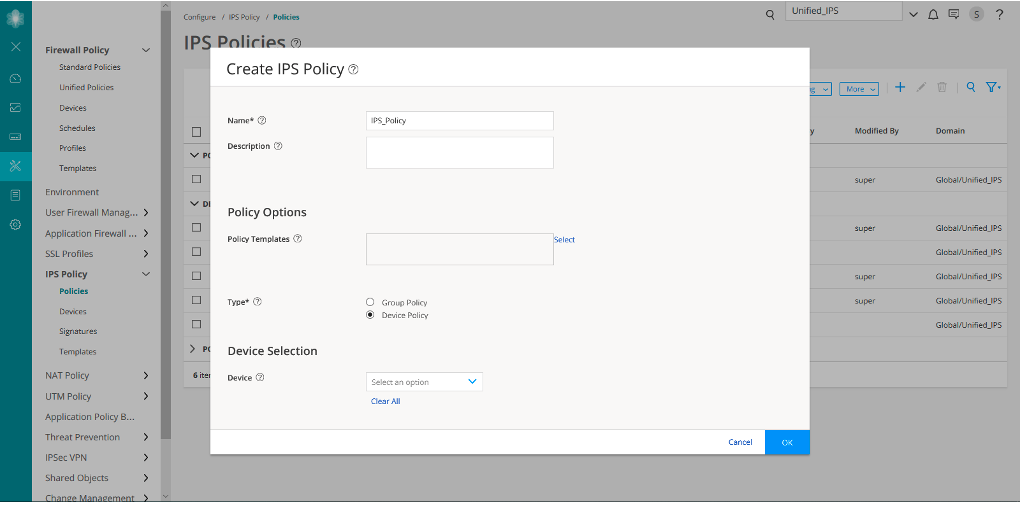
Create an IPS Policy
Let’s first create an IPS policy that we will then configure on an SRX Series device running Junos OS Release 18.2:
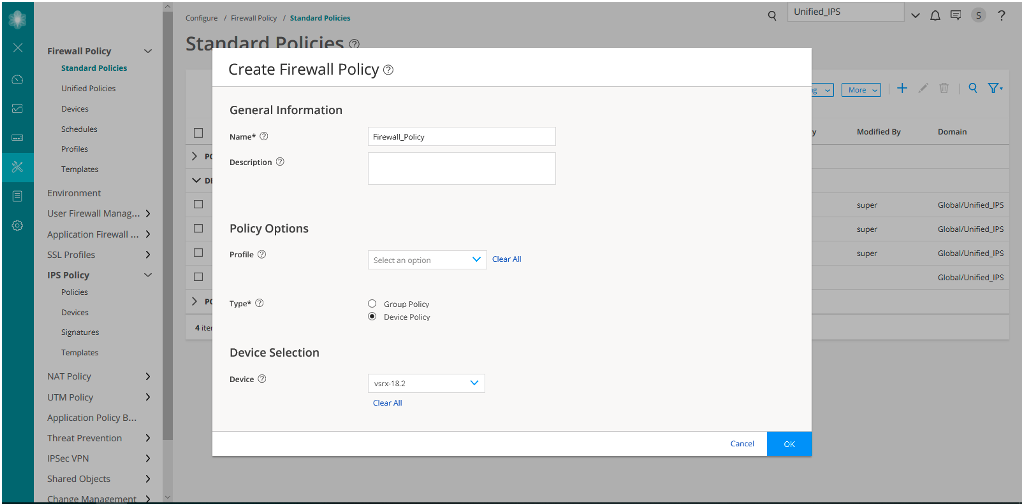
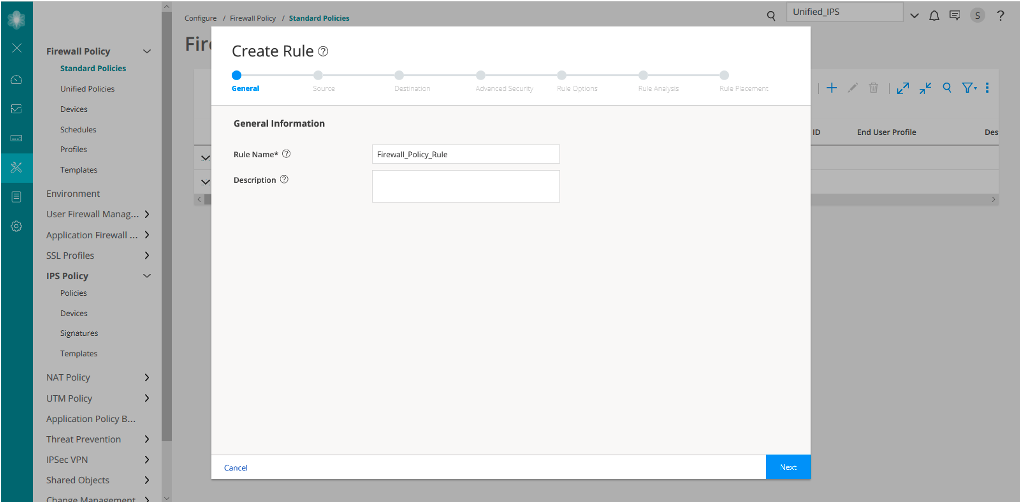
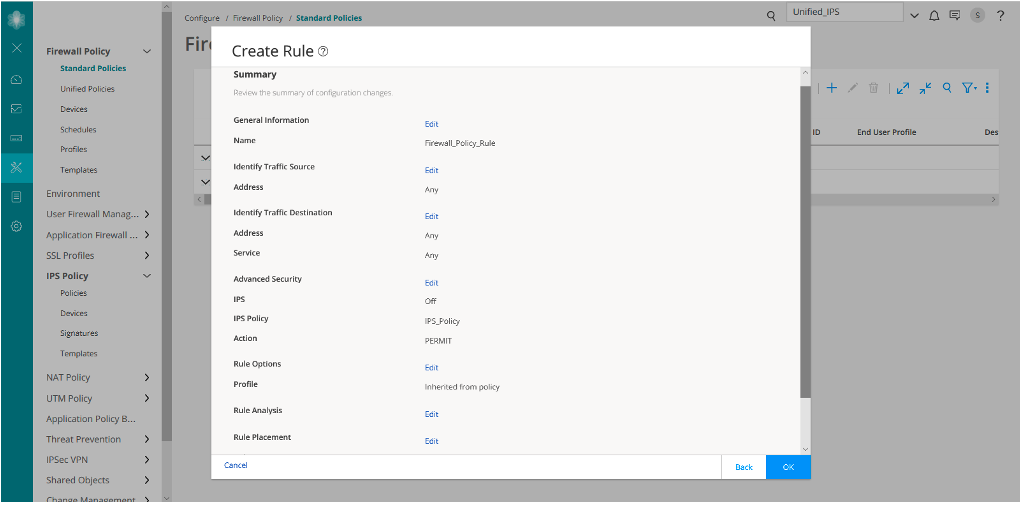
Assign the IPS Policy to a Firewall Policy Rule
Now let’s assign the created IPS policy to a firewall policy rule:
Similar to Firewall_Policy_Rule, we have created another rule Firewall_Policy_Rule2.
Verify the IPS Policy Assignment to Firewall Policy
Purpose
Let's verify that the firewall policy that you created includes the IPS policy that you created (IPS_Policy).
Action
-
Select Configure > Firewall Policy > Standard Policies.
The Standard Policies page is displayed.
-
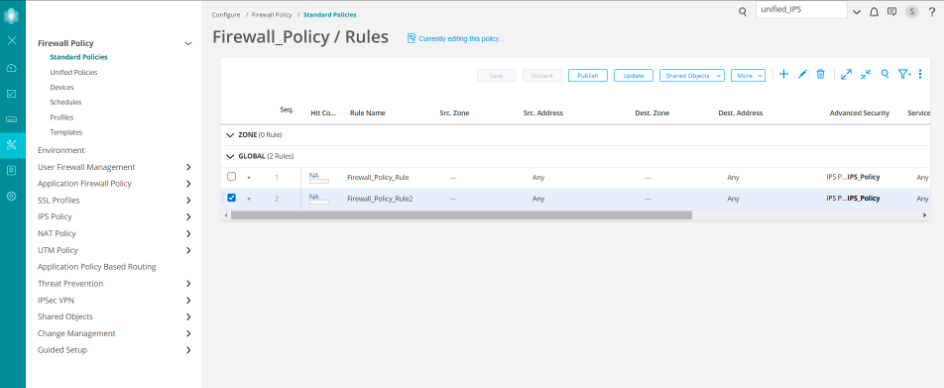
Click the rules for the firewall policy named (Firewall_Policy).
The Firewall_Policy/Rules page is displayed. In the Advanced Security column, the IPS policy named IPS_Policy is displayed for both the rules that you created (Firewall_Policy_Rule and Firewall_Policy_Rule2).
CLI Configuration
You’ll see that the IPS_Policy policy is assigned to the Firewall_Policy_Rule and Firewall_Policy_Rule2 rules.
##Security Firewall Policy: global ##
set security policies global policy Firewall_Policy_Rule
match application any
set security policies global policy Firewall_Policy_Rule
match destination-address any
set security policies global policy Firewall_Policy_Rule
match source-address any
set security policies global policy Firewall_Policy_Rule
then permit application-services idp-policy IPS_Policy
set security policies global policy Firewall_Policy_Rule2
match application any
set security policies global policy Firewall_Policy_Rule2
match destination-address any
set security policies global policy Firewall_Policy_Rule2
match source-address any
set security policies global policy Firewall_Policy_Rule2
then permit application-services idp-policy IPS_Policy
##IDP Configurations##
set security idp idp-policy IPS_Policy rulebase-ips rule
Device-1 match application default
set security idp idp-policy IPS_Policy rulebase-ips rule
Device-1 match attacks predefined-attack-groups "Additional Web Services
- Info"
set security idp idp-policy IPS_Policy rulebase-ips rule
Device-1 match from-zone any
set security idp idp-policy IPS_Policy rulebase-ips rule
Device-1 match to-zone any
set security idp idp-policy IPS_Policy rulebase-ips rule
Device-1 then action recommended