ON THIS PAGE
Example: Branch Deployment Using NFX350 NextGen uCPE
This example shows how to configure network visibility and performance monitoring on the LAN ports of NFX350 uCPE. It also shows you how to onboard an Ubuntu20.04-based VNF to support a Nagios XI instance. The VNF is based on the cloud image of Ubuntu20.04. The Nagios XI server provides local network visibility and performance monitoring to support proactive risk mitigation and timely problem remediation.
The configuration of the Nagios XI server is beyond the scope of this document.
Requirements
One NFX350-S2 device.
Note:This example was validated against a NFX350-S2 device. This example also supports the use of NFX350-S1 and NFX350-S3 devices.
Junos OS Release 20.1R1 or later.
This example has been revalidated on Junos OS Release 20.3R1.
Ubuntu 20.04 operating system.
The workstation used in this example to generate the iso and qcow2 files is based on an Ubuntu 20.04
operating system. If you are using a workstation other than Ubuntu,
such as Windows or Centos, the steps needed to generate the iso and the qcow2 files may differ slightly.
Overview
In this example, we set up a branch NFX350 uCPE to provide wired Intranet connectivity and Internet access to employees at the remote site. Internet access is facilitated with an Ethernet link. An Ubuntu 20.04-based VNF is onboarded on the NFX350 device to support a Nagios XI server. The Nagios XI server provides local network visibility and performance monitoring on the LAN ports of NFX350.
Topology
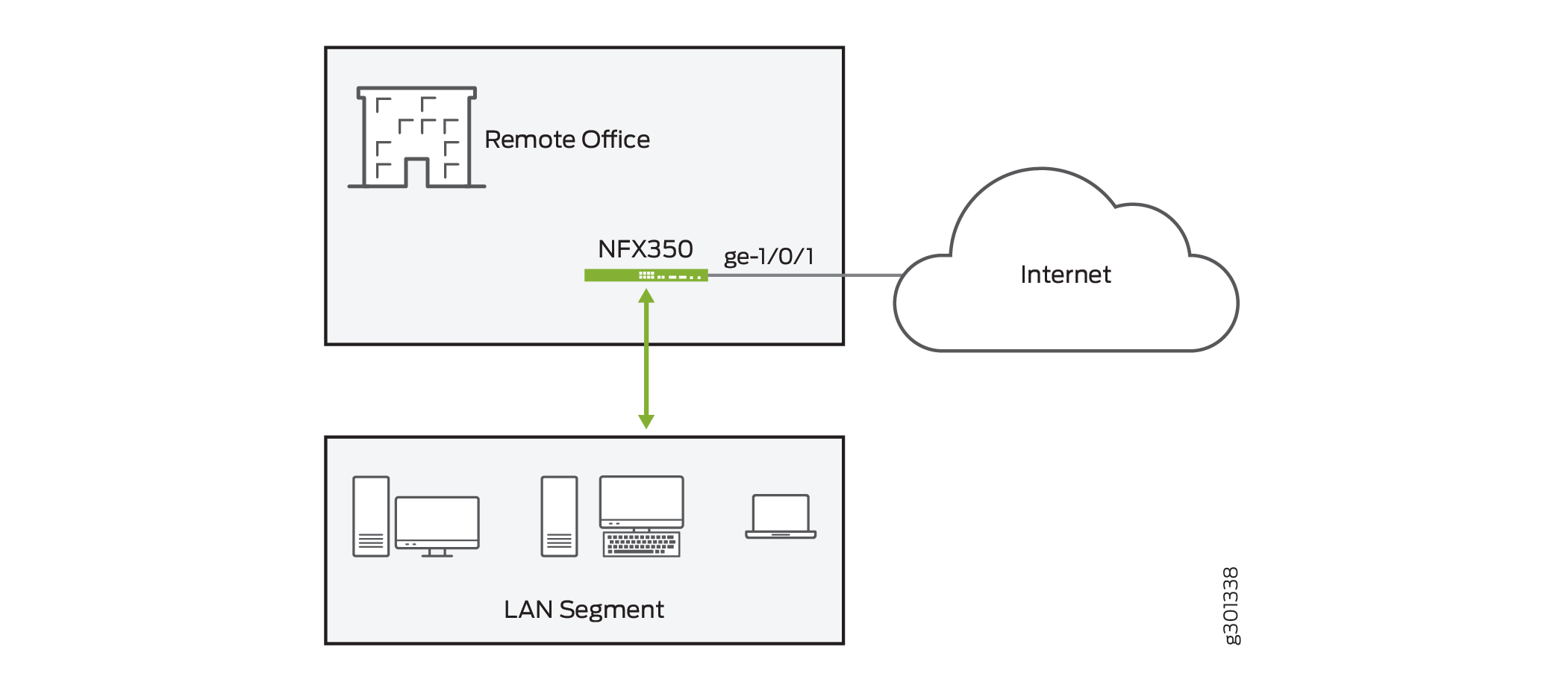
Figure 1 shows a remote branch office that is connected to the Internet using the NFX350.
The VNF service chaining and interface configuration details are depicted in Figure 2:
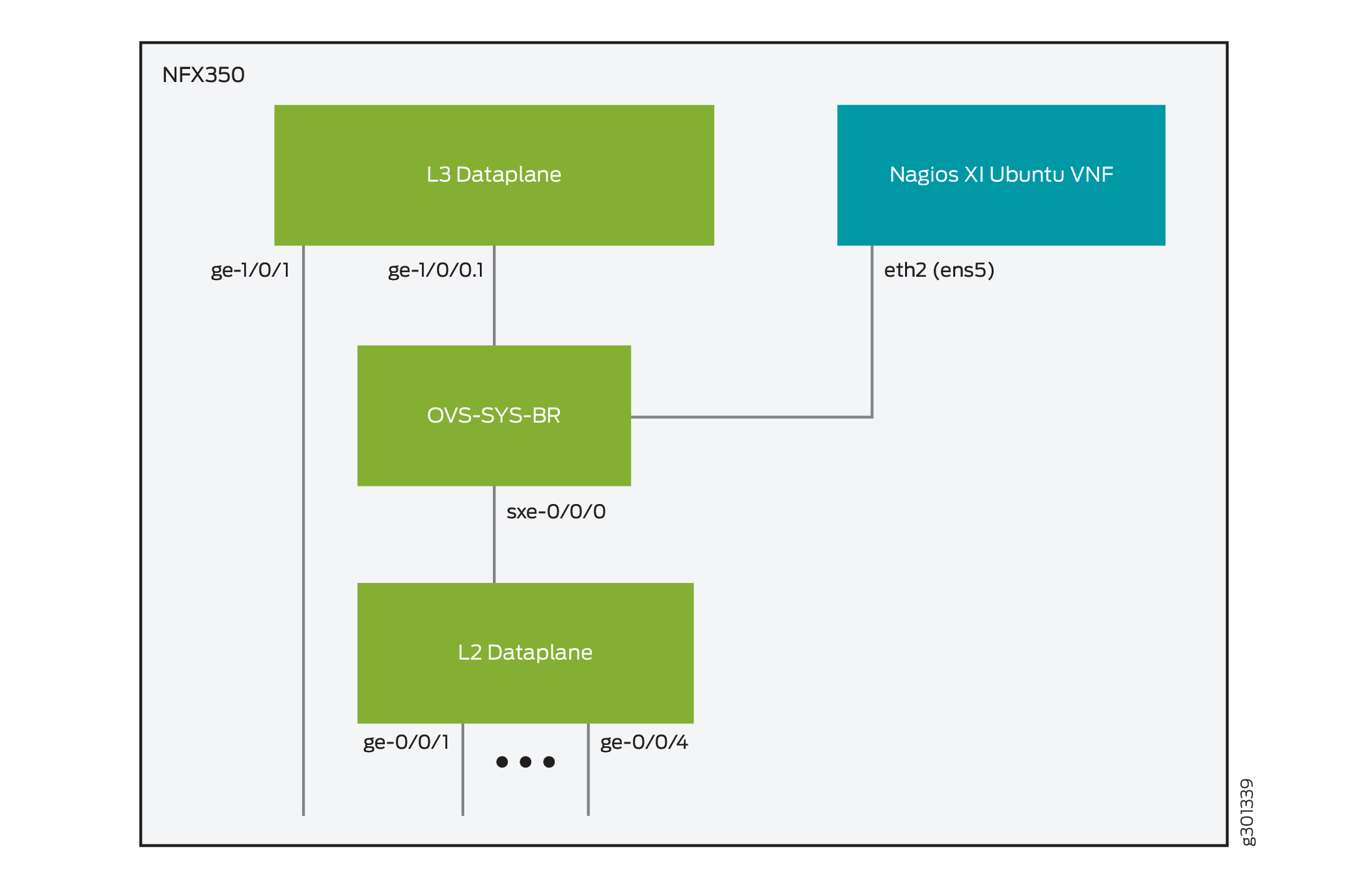
In the topology Figure 2:
The broadband Internet link is connected to interface ge-1/0/1
The 1 Gbps Ethernet links of the NFX350 device are connected to VLAN 100
VLAN 100 is associated to the sxe-0/0/0 interface and is also configured on interface ge-1/0/0 under unit 100. This logical interface is used for the DHCP server to provide network address configuration to the devices connected to the front ports of the NFX350 device.
The eth2 interface of the VNF is configured as an access port in VLAN 100. The eth2 interface is recognized by the Ubuntu operating system as ens5.
In this example, there are two security zones (untrust and trust) configured on the NFX350 device. The separation of the interfaces into security zones enables the separation of traffic to mitigate the risks the corporate Intranet is exposed to. Security zones also serve as a vehicle to achieve clear and simplified implementation of security policies. The untrust zone hosts the interfaces that have access to the Internet. The internal interfaces in the corporate Intranet are in the trust zone. Specifically, ge-1/0/1interface is in untrust zone, while the rest of the LAN interfaces are in the trust zone. Figure 3 and the following table show the interfaces, security zones, and security policy configurations:
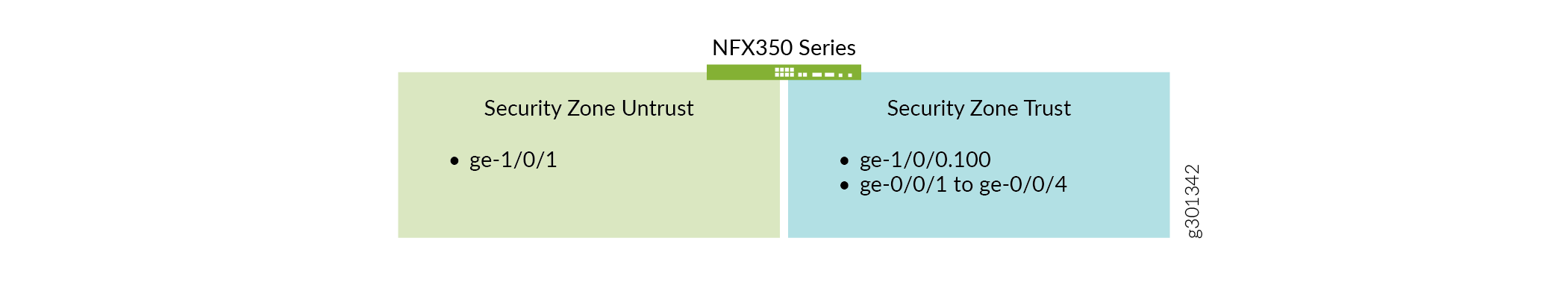
Table 1 shows the desired behavior of the security policies for the traffic between the zones.
From Zone |
To Zone |
Security Policy Behavior to Allow Traffic |
|---|---|---|
trust |
trust |
Not Applicable |
untrust |
untrust |
Not Applicable |
trust |
untrust |
Allowed |
untrust |
trust |
Trust-initiated only. Allow the return traffic for traffic that is initiated in the trust zone. |
Table 2 summarizes the VLAN information and IP address information for the interfaces.
Interface |
VLAN ID |
IP Address |
Network Mask |
|---|---|---|---|
ge-1/0/1 |
— |
DHCP |
— |
ge-1/0/0.100 |
100 Note:
The default VLAN has VLAN ID value as 1. |
192.168.2.1 |
255.255.255.0 |
Configuration
Perform these tasks to deploy a NFX350 uCPE based branch office with network visibility and LAN performance monitoring:
- Stage Ubuntu 20.04-based VNF
- Fine-tune the NFX Mode of Operation
- Configure VNF
- Configure Zone-based Firewall and NAT
- Configure DHCP Server for LAN Users
- Run the Nagios XI Installation Script
Stage Ubuntu 20.04-based VNF
Step-by-Step Procedure
The following steps describe how to stage an Ubuntu 20.04-based VNF:
Download the cloud-based ubuntu-20.04-server-cloudimg-amd64.vmdk image file of Ubuntu 20.04 from the official Ubuntu website on the workstation.
user@workstation$wget -nc https://cloud-images.ubuntu.com/releases/focal/release/ubuntu-20.04-server-cloudimg-amd64.vmdk
Convert the ubuntu-20.04-server-cloudimg-amd64.vmdk image file to qcow2 file format.
user@workstation$qemu-img convert -f vmdk -O qcow2 ubuntu-20.04-server-cloudimg-amd64.vmdk ubuntu-20.04-server-cloudimg-amd64.qcow2
Note:You may need to install qemu-utils on your Ubuntu workstation to run the
qemu-imgcommands.Create a copy of the qcow2 file for your VNF. The name of the VNF is nagios-ubuntu and the name of the qcow2 file is nagiosxi-ubuntu.qcow2.
user@workstation$cp ubuntu-20.04-server-cloudimg-amd64.qcow2 nagiosxi-ubuntu.qcow2
Open your favorite text editor on the workstation and create the cloud-init configuration file for the VNF. The cloud-init configuration contains basic information such as identifying this is a #cloud-config, the password for the default user (ubuntu), configuration stanzas that do not allow password expiration for the user, and the configuration to allow password authentication to the VNF. By default, the cloud-based Ubuntu image allows only the SSH key-based authentication. The hostname for the VNF is also defined in the file. The VNF is named nagios-ubuntu. In this example, the cloud-init configuration file for the VNF is named nagiosxi-ubuntu.txt.
#cloud-config password: $ABC123 chpasswd: { expire: False } ssh_pwauth: True hostname: nagiosxi-ubuntuCreate an iso file from the nagiosxi-ubuntu.txt config-init file named nagiosxi-ubuntu.iso. The nagiosxi-ubuntu.iso file is stored in the same directory.
Note:You may need to install cloud-image-utils on your Ubuntu workstation to run the
cloud-localdscommand.user@workstation$cloud-localds ./nagiosxi-ubuntu.iso nagiosxi-ubuntu.txt
Copy the nagiosxi-ubuntu.qcow2 and the nagiosxi-ubuntu.iso files to the
/var/publicdirectory on the NFX350 device. Make sure to use the correct credentials if you want to use the following method to copy the files to the NFX350 uCPE. For example, the root user’s credentials are used here to copy the files to the NFX350 device.user@workstation$scp nagiosxi-ubuntu.iso root@nfx-350-s2:/var/public/ user@workstation$scp nagiosxi-ubuntu.qcow2 root@nfx-350-s2:/var/public/
Fine-tune the NFX Mode of Operation
Step-by-Step Procedure
The following steps describe how to fine-tune the NFX mode of operation:
Set the NFX for compute mode. Compute mode provides maximum resources for third-party VNFs.
Note:The NFX350 device reboots after you set compute mode.
user@host>request vmhost mode compute
Configure support for hugepages on the NFX350 device. These are memory pages that do not get swapped out of memory. In this example, there are four hugepages created for use by the VNF.
[edit] user@host#set system memory hugepages page-size 1024 page-count 4 user@host#commit and-quit
Reboot the NFX350 device in order for the hugepages configuration to take effect.
user@host>request vmhost reboot
Configure VNF
Step-by-Step Procedure
The following steps describe how to configure the VNF:
Create the VNF and assign it the name nagios-ubuntu. You also need to set the path to the image (
/var/public/nagiosxi-ubuntu.qcow2) for the VNF.[edit] user@host#set virtual-network-functions nagios-ubuntu image /var/public/nagiosxi-ubuntu.qcow2 user@host#set virtual-network-functions nagios-ubuntu image image-type qcow2
Configure the VNF to have 2 CPUs, enable hardware virtualization for the CPUs, and dedicate 2 GB of memory for the VNF. It’s mandatory that you configure the CPU count and allocate memory with hugepage support for the VNF. For Ubuntu 20.04 cloud image, it’s recommended that the user configure a minimum of 1 CPU and at least 1 GB of memory.
[edit] user@host#set virtual-network-functions nagios-ubuntu virtual-cpu count 2 user@host#set virtual-network-functions nagios-ubuntu virtual-cpu features hardware-virtualization user@host#set virtual-network-functions nagios-ubuntu memory size 2097152 user@host#set virtual-network-functions nagios-ubuntu memory features hugepages
Map the eth2 interface to the VLAN 100.
[edit] user@host#set virtual-network-functions nagios-ubuntu interfaces eth2 mapping vlan mode access user@host#set virtual-network-functions nagios-ubuntu interfaces eth2 mapping vlan members 100
Mount the cloud-init image nagios-ubuntu.iso file as CD-ROM drive:
[edit] user@host#set virtual-network-functions nagios-ubuntu storage vdb type cdrom source file /var/public/nagiosxi-ubuntu.iso
Add the VLAN 100 to the ge-0/0/1 to ge-0/0/4 interfaces. Also configure this VLAN for the sxe-0/0/0 interface.
[edit] user@host#set interfaces ge-0/0/1 unit 0 family ethernet-switching vlan members vlan100 user@host#set interfaces ge-0/0/2 unit 0 family ethernet-switching vlan members vlan100 user@host#set interfaces ge-0/0/3 unit 0 family ethernet-switching vlan members vlan100 user@host#set interfaces ge-0/0/4 unit 0 family ethernet-switching vlan members vlan100 user@host#set interfaces sxe-0/0/0 unit 0 family ethernet-switching vlan members vlan100
Results
The following are the results:
Configure Zone-based Firewall and NAT
Step-by-Step Procedure
The following steps describe how to configure zone-based firewall filters and NAT:
Create a security zone trust and assign the Layer 3 interface ge-1/0/0.0 to that zone. The ge-1/0/0.0 Layer 3 interface acts as a DHCP server for the LAN connected devices. The ge-1/0/0.0 interface is the default interface and it is part of the default configuration of the NFX350 device.
[edit] user@host#set security zones security-zone trust host-inbound-traffic system-services all user@host#set security zones security-zone trust host-inbound-traffic protocols all user@host#set security zones security-zone trust interfaces ge-1/0/0.0
Create a security zone untrust and assign the Layer 3 interface ge-1/0/0.100. You can configure the host-inbound-traffic parameters as needed. In this example all host inbound services and protocols are enabled.
[edit] user@host#set security zones security-zone untrust host-inbound-traffic system-services all user@host#set security zones security-zone untrust host-inbound-traffic protocols all user@host#set security zones security-zone untrust interfaces ge-1/0/0.100
Note:In a production environment it’s a best practice to restrict the protocols and services to only those that are explicitly required for each security zone.
Create security policies to allow the traffic within the security zone trust.
[edit] user@host#set security policies from-zone trust to-zone trust policy default-permit match source-address any user@host#set security policies from-zone trust to-zone trust policy default-permit match destination-address any user@host#set security policies from-zone trust to-zone trust policy default-permit match application any user@host#set security policies from-zone trust to-zone trust policy default-permit then permit
Create security policies to allow all traffic from security zone trust to security zone untrust.
[edit] user@host#set security policies from-zone trust to-zone untrust policy trust-to-untrust match source-address any user@host#set security policies from-zone trust to-zone untrust policy trust-to-untrust match destination-address any user@host#set security policies from-zone trust to-zone untrust policy trust-to-untrust match application any user@host#set security policies from-zone trust to-zone untrust policy trust-to-untrust then permit
Create a rule to source NAT traffic sent from zone trust into zone untrust.
[edit] user@host#set security nat source rule-set trust-to-untrust from zone trust user@host#set security nat source rule-set trust-to-untrust to zone untrust user@host#set security nat source rule-set trust-to-untrust rule source-nat-rule match source-address 0.0.0.0/0 user@host#set security nat source rule-set trust-to-untrust rule source-nat-rule then source-nat interface
Configure DHCP Server for LAN Users
Step-by-Step Procedure
The following steps describe how to configure the DHCP server:
Create a sub-interface for ge-1/0/0 in the default VLAN. This is needed because an interface is required for the DHCP server.
[edit] user@host#set interfaces ge-1/0/0 vlan-tagging user@host#set interfaces ge-1/0/0 unit 100 vlan-id 100 user@host#set interfaces ge-1/0/0 unit 100 family inet address 192.168.2.1/24
Create the DHCP address pool and set the ge-1/0/0.1 interface as the gateway. The following DHCP address pool parameters are used in this example:
Name of the DHCP address pool is jdhcp-group.
User-assigned IP addresses range from 192.168.2.2 to 192.168.2.254.
Gateway IP address is 192.168.2.1.
DNS server address is 8.8.8.8.
[edit] user@host#set access address-assignment pool jdhcp-group family inet network 192.168.2.0/24 user@host#set access address-assignment pool jdhcp-group family inet range junosRange low 192.168.2.2 user@host#set access address-assignment pool jdhcp-group family inet range junosRange high 192.168.2.254 user@host#set access address-assignment pool jdhcp-group family inet dhcp-attributes router 192.168.2.1 user@host#set access address-assignment pool jdhcp-group family inet dhcp-attributes name-server 8.8.8.8 user@host#set access address-assignment pool jdhcp-group family inet dhcp-attributes propagate-settings ge-1/0/1.100
Commit the configuration.
[edit] user@host#commit and-quit
Run the Nagios XI Installation Script
Step-by-Step Procedure
The following steps describe how to run the Nagios XI installation script:
The configuration of the Nagios XI server is beyond the scope of this document.
Login to the nagios-ubuntu VNF with username ubuntu and the password, specified in the cloud-config file.
user@host>request virtual-network-functions nagios-ubuntu ssh user-name ubuntu
Become a super user and run the Nagios XI installation script.
ubuntu@nagios-ubuntu$sudo su root@nagios-ubuntu#curl https://assets.nagios.com/downloads/nagiosxi/install.sh | sh
The configuration of the network interfaces, as well as the NAGIOS XI server on the Ubuntu VNF is omitted.
Verification
To confirm that the configuration is working properly, perform the following tasks:
- Verifying the VNF is Up and Running
- Verifying the Resource Utilization for the VNF
- Verifying the Interface State
Verifying the VNF is Up and Running
Purpose
Verify that the VNF was spun up successfully.
Action
From operational mode, enter the show virtual-network-functions
nagios-ubuntu detail command.
user@host> show virtual-network-functions nagios-ubuntu detail Virtual Network Function Information ------------------------------------ Id: 3 Name: nagios-ubuntu UUID: ad80da24-7b5d-461b-b13e-40c0671f097e State: Running Liveliness: alive IP Address: 192.0.2.102 VCPUs: 2 Maximum Memory: 2097152 KiB Used Memory: 53360 KiB Used 1G Hugepages: 2 Used 2M Hugepages: 0 Error: None
Meaning
The output shows the details of nagios-ubuntu VNF such as state, liveliness, errors, as well as memory usage.
Verifying the Resource Utilization for the VNF
Purpose
Verify what resources the VNF system is currently using such as CPU time, memory usage, and also the MAC address information of the interface.
Action
From operational mode, enter the show system visibility
vnf nagios-ubuntu command.
user@host> show system visibility vnf nagios-ubuntu VNF Memory Usage -------------------------------------------------------------------------------------------------------------------- Name Maximum Memory (KiB) Used Memory (KiB) Used 1G Hugepages Used 2M Hugepages -------------------------------------- --------------------- ------------------ ------------------ ----------------- nagios-ubuntu 1048576 1094359 2 0 VNF CPU Statistics (Time in ms) ----------------------------------------------------------------------------------- Name CPU Time System Time User Time -------------------------------------- ------------------ ------------ ------------ nagios-ubuntu 42961490 337100 87290 VNF MAC Addresses ----------------------------------------------------------- VNF MAC ----------------------------------------- ----------------- nagios-ubuntu_ethdef0 D0:DD:49:E8:56:CD nagios-ubuntu_ethdef1 D0:DD:49:E8:56:CE nagios-ubuntu_eth2 D0:DD:49:E8:56:CF VNF Internal IP Addresses --------------------------------------------------------- VNF IP ----------------------------------------- --------------- nagios-ubuntu 192.0.2.100 VNF Interfaces -------------------------------------------------------------------------------------------------------- VNF Interface Type Source Model MAC IPv4-address -------------------- --------- --------- ------------ ---------- ----------------- --------------------- nagios-ubuntu vnet4 network default virtio d0:dd:49:e8:56:cd -- nagios-ubuntu vnet5 bridge eth0br virtio d0:dd:49:e8:56:ce -- nagios-ubuntu nagios-ubuntu_eth2 vhostuser -- virtio d0:dd:49:e8:56:cf -- VNF Disk Information --------------------------------------------------------------------------------------------------------- VNF Disk File ----------------------------- ----------- --------------------------------------------------------------- nagios-ubuntu vda /var/internal-disk1/nagiosxi-ubuntu.qcow2 VNF Disk Usage ------------------------------------------------------------------------------ VNF Disk Read Req Read Bytes Write Req Write Bytes -------------------- --------- ---------- ------------ ---------- ------------ nagios-ubuntu vda 1075436 71651675648 2029516 14869693952 VNF Port Statistics ---------------------------------------------------------------------------------------------------------------------------- VNF Port Rcvd Bytes Rcvd Packets Rcvd Error Rcvd Drop Trxd Bytes Trxd Packets Trxd Error Trxd Drop -------------------- --------- ------------ ------------ ---------- --------- ------------ ------------ ---------- --------- nagios-ubuntu vnet4 38488916 560669 0 0 31394363 351950 0 0 nagios-ubuntu vnet5 297008038 1498280 0 0 22957609 281578 0 0 root@tme-nfx350-s2> show system visibility vnf nagios-ubuntu VNF Memory Usage -------------------------------------------------------------------------------------------------------------------- Name Maximum Memory (KiB) Used Memory (KiB) Used 1G Hugepages Used 2M Hugepages -------------------------------------- --------------------- ------------------ ------------------ ----------------- nagios-ubuntu 1048576 1094451 0 0 VNF CPU Statistics (Time in ms) ----------------------------------------------------------------------------------- Name CPU Time System Time User Time -------------------------------------- ------------------ ------------ ------------ nagios-ubuntu 42974751 337270 87310 VNF MAC Addresses ----------------------------------------------------------- VNF MAC ----------------------------------------- ----------------- nagios-ubuntu_ethdef0 D0:DD:49:E8:56:CD nagios-ubuntu_ethdef1 D0:DD:49:E8:56:CE nagios-ubuntu_eth2 D0:DD:49:E8:56:CF VNF Internal IP Addresses ---------------------------------------------------
Meaning
The output shows the system details of nagios-ubuntu VNF such as memory usage, CPU time, MAC addresses, and IP addresses.
Verifying the Interface State
Purpose
Verify and monitor the state of the interface.
Action
From operational mode, enter the show vmhost network
nfv-back-plane command.
user@host> show vmhost network nfv-back-plane
Network Name : ovs-sys-br
...
Interface : nagios-ubuntu_eth2
Type : dpdkvhostuser, Link type : Full-Duplex, MAC : 00:00:00:00:00:00
MTU : 1500, Link State :up, Admin State : up
Native Vlan ID : None, Vlan mode : Access, Vlan Members : 100
IPV4 : None, Netmask : None
IPV6 : None, IPV6 netmask : None
Rx-packets : 0
Rx-drops : 0
Rx-errors : 0
Tx-packets : 0
Tx-drops : 0
Tx-errors : 0
...Meaning
The output shows the details of the interface nagios-ubuntu_eth2 such as interface, link state, and admin state.
