Example: Inter-VLAN Filter Based Forwarding
SUMMARY This NCE illustrates how to use the Filter-based Forwarding (FBF) feature to implement advanced security inspection for selected inter-VLAN traffic flows in a EVPN-VXLAN fabric.
Requirements
This EVPN-VXLAN fabric uses the edge-routed bridging (ERB) model. Inter-VLAN routing happens on the leaf devices. This example assumes the ERB fabric is in place so the focus can be placed on using FBF to select flows for security inspection. The detailed configurations at the end of the example show the configuration needed for a working ERB baseline in addition to the FBF needed to inspect specific flows. The example topology is shown below.
For background information and configuration details for an ERB EVPN-VXLAN fabric see EVPN-VXLAN Architecture and Technology.
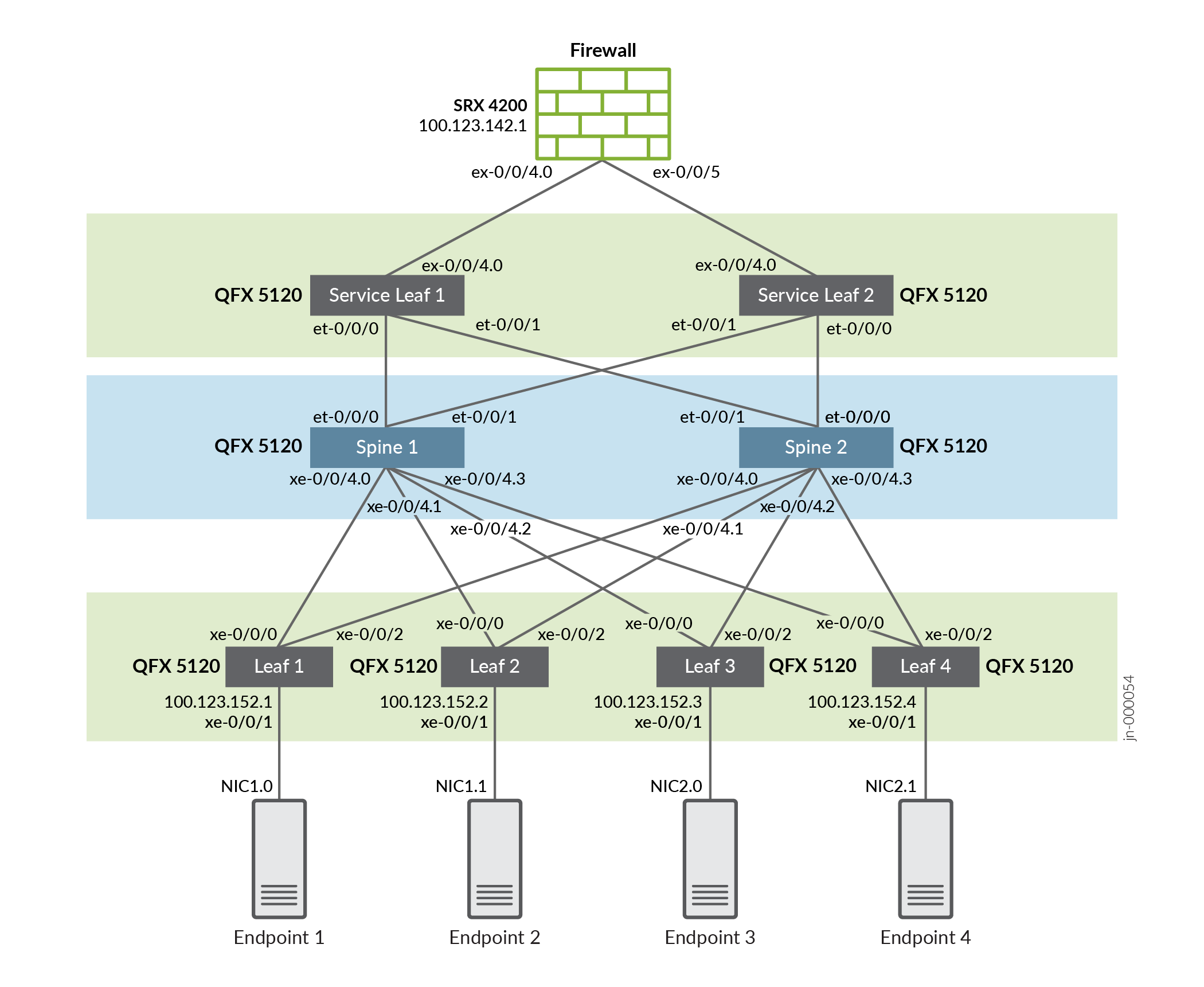
Topology
This NCE describes an EVPN-VXLAN fabric that is comprised of four server leaf switches, two underlay spine switches, two service leaf switches, and a firewall.
Spine Nodes
- QFX5120-32C series switches running Junos version 20.2R2
Server Leaf
- QFX5120-48Y series switches running Junos version 20.3R1
Service Leaf
- QFX5120-32C series switches running Junos version 20.2R2
Firewall
- SRX 4200 Services Gateway running Junos version 20.1R2
Step-by-Step Configurations
In the following configuration, we connect Endpoint 11 to Server Leaf-1. We also create a new routing instance, INSPECT_VRF, and configure it to export and import type-5 routes with Service Leaf-1 and Service Leaf-2. We use filter-based forwarding to redirect traffic from Endpoint 11 to Endpoint12 to the INSPECT_VRF.
Server Leaf-1
-
On Server Leaf-1, set up the INSPECT_VRF routing instance:
set routing-instances INSPECT_VRF routing-options multipath set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes vni 9991 set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes export T5_INSPECT_EXPORT set routing-instances INSPECT_VRF description "VRF for Firewall-1" set routing-instances INSPECT_VRF instance-type vrf set routing-instances INSPECT_VRF interface lo0.991 set routing-instances INSPECT_VRF route-distinguisher 10.80.224.140:9991 set routing-instances INSPECT_VRF vrf-target target:64730:991 set routing-instances INSPECT_VRF vrf-table-label set interfaces lo0 unit 991 family inet address 192.168.91.1/32
-
Add a static route for Endpoint 11 that points to Tenant1_VRF:
set routing-instances INSPECT_VRF routing-options static route 10.1.110.11/32 next-table Tenant1_VRF.inet.0
-
The Inspect_VRF needs to advertise a type-5 static host route for Endpoint 11 so the firewall can receive the traffic. The firewall also needs to advertise a default route for Leaf 1:
set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct then accept set policy-options policy-statement T5_INSPECT_EXPORT term fm_static from protocol static set policy-options policy-statement T5_INSPECT_EXPORT term fm_static then accept
-
Now we need to set up firewall filter for Leaf-1. The filter matches traffic from Endpoint 11 to Endpoint 21, and redirects these packets to the INSPECT_VRF. All other traffic is routed as usual in the Tenant1_VRF:
set firewall family inet filter SecureTraffic term EP11_to_EP21 from source-address 10.1.110.11/32 set firewall family inet filter SecureTraffic term EP11_to_EP21 from destination-address 10.1.111.21/32 set firewall family inet filter SecureTraffic term EP11_to_EP21 then count EP11_to_EP21 set firewall family inet filter SecureTraffic term EP11_to_EP21 then routing-instance INSPECT_VRF set firewall family inet filter SecureTraffic term Allow_All then count Normal_Count set firewall family inet filter SecureTraffic term Allow_All then accept
-
On Leaf-1, we need to apply the firewall filter to VLAN 110 traffic as it traverses IRB.110 (this is the interface connected to Endpoint 11):
set interfaces irb unit 110 virtual-gateway-accept-data set interfaces irb unit 110 family inet filter input SecureTraffic set interfaces irb unit 110 family inet address 10.1.110.100/24 virtual-gateway-address 10.1.110.1 set interfaces irb unit 110 virtual-gateway-v4-mac e4:5d:37:11:10:01
Server Leaf-2
Next, we need to create the SECURE_VRF routing instance on Server Leaf-2 in order to export and import type-5 routes with both Service Leaf-1 and Service Leaf-2. As before, we use filter-based forwarding to redirect traffic from Endpoint 21 to Endpoint 11 into the INSPECT VRF.
-
On Server Leaf-2, set up the INSPECT_VRF routing instance:
set routing-instances SECURE_VRF routing-options multipath set routing-instances SECURE_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances SECURE_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances SECURE_VRF protocols evpn ip-prefix-routes vni 9992 set routing-instances SECURE_VRF protocols evpn ip-prefix-routes export T5_SECURE_EXPORT set routing-instances SECURE_VRF description "VRF for SECURED FIREWALL TRAFFIC" set routing-instances SECURE_VRF instance-type vrf set routing-instances SECURE_VRF interface lo0.992 set routing-instances SECURE_VRF route-distinguisher 10.80.224.141:9992 set routing-instances SECURE_VRF vrf-target target:64730:992 set routing-instances SECURE_VRF vrf-table-label set interfaces lo0 unit 992 family inet address 192.168.92.2/32
-
Configure a static route for Endpoint 21 that points to Tenant1_VRF:
set routing-instances SECURE_VRF routing-options static route 10.1.111.21/32 next-table Tenant1_VRF.inet.0
-
Inside the SECURE_VRF, we need to advertise a type-5 static host route for Endpoint 21 so the firewall can receive the traffic. The firewall also needs to advertise a default route for Leaf 2:
set policy-options policy-statement T5_SECURE_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_SECURE_EXPORT term fm_direct then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_static from protocol static set policy-options policy-statement T5_SECURE_EXPORT term fm_static then accept
-
As before, we now need to set up firewall filter for Leaf-2. This time, the filter matches traffic from Endpoint 21 to Endpoint 11, and redirects these packets to the SECURE_VRF. All other traffic is routed as usual in the Tenant1_VRF:
set firewall family inet filter SecureResponseTraffic term EP21_to_EP11 from source-address 10.1.111.21/32 set firewall family inet filter SecureResponseTraffic term EP21_to_EP11 from destination-address 10.1.110.11/32 set firewall family inet filter SecureResponseTraffic term EP21_to_EP11 then count EP21_to_EP11 set firewall family inet filter SecureResponseTraffic term EP21_to_EP11 then routing-instance SECURE_VRF set firewall family inet filter SecureResponseTraffic term Allow_All then accept
-
Finally, on Leaf-2, we need to apply the firewall filter to VLAN 111 traffic as it traverses IRB.111 (this is the interface connected to Endpoint 21).
set interfaces irb unit 111 virtual-gateway-accept-data set interfaces irb unit 111 family inet filter input SecureResponseTraffic set interfaces irb unit 111 family inet address 10.1.111.101/24 virtual-gateway-address 10.1.111.1 set interfaces irb unit 111 virtual-gateway-v4-mac e4:5d:37:11:11:01
Service Leaf-1
Service Leaf-1 includes both the INSPECT_VRF and SECURE_VRF routing instances, and it connects the service leaf and the firewall, as shown in the following figure. Interface IRB.991 is in the INSPECT VRF and interface IRB.992 is in the SECURE VRF.
In both routing instances, the service leaf establishes EBGP peering with the firewall, from which it receives a default route. Service Leaf-1 advertises the default routes to the server leafs using type-5, and from them receives specific host routes for Endpoint 11 and Endpoint 21, which it then advertises to the firewall using EBGP.
-
The connection from the service leaf to the firewall is a trunk port that contains VLAN 991 and VLAN 992, each with a IRB. interface, as shown here:
set interfaces xe-0/0/4:0 description "SRX Firewall 1: xe-0/0/4" set interfaces xe-0/0/4:0 mtu 9192 set interfaces xe-0/0/4:0 unit 0 family ethernet-switching interface-mode trunk set interfaces xe-0/0/4:0 unit 0 family ethernet-switching vlan members V991 set interfaces xe-0/0/4:0 unit 0 family ethernet-switching vlan members V992 set interfaces irb unit 991 family inet address 10.81.91.2/30 set interfaces irb unit 992 family inet address 10.81.92.2/30
-
We need to set up the routing instances on Service Leaf-1:
set routing-instances INSPECT_VRF description "VRF for Firewall-1" set routing-instances INSPECT_VRF instance-type vrf set routing-instances INSPECT_VRF interface irb.991 set routing-instances INSPECT_VRF interface lo0.991 set routing-instances INSPECT_VRF route-distinguisher 10.80.224.138:9991 set routing-instances INSPECT_VRF vrf-target target:64730:991 set routing-instances INSPECT_VRF vrf-table-label set routing-instances INSPECT_VRF routing-options multipath set routing-instances INSPECT_VRF protocols bgp group Firewall-1 type external set routing-instances INSPECT_VRF protocols bgp group Firewall-1 export FW1_Export set routing-instances INSPECT_VRF protocols bgp group Firewall-1 local-as 64730 set routing-instances INSPECT_VRF protocols bgp group Firewall-1 neighbor 10.81.91.1 peer-as 64777 set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes vni 9991 set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes export T5_INSPECT_EXPORT set routing-instances SECURE_VRF description "VRF for SECURED FIREWALL TRAFFIC" set routing-instances SECURE_VRF instance-type vrf set routing-instances SECURE_VRF interface irb.992 set routing-instances SECURE_VRF interface lo0.992 set routing-instances SECURE_VRF route-distinguisher 10.80.224.138:9992 set routing-instances SECURE_VRF vrf-target target:64730:992 set routing-instances SECURE_VRF vrf-table-label set routing-instances SECURE_VRF routing-options multipath set routing-instances SECURE_VRF protocols bgp group Firewall-1 type external set routing-instances SECURE_VRF protocols bgp group Firewall-1 export FW1_Export set routing-instances SECURE_VRF protocols bgp group Firewall-1 local-as 64730 set routing-instances SECURE_VRF protocols bgp group Firewall-1 neighbor 10.81.92.1 peer-as 64777 set routing-instances SECURE_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances SECURE_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances SECURE_VRF protocols evpn ip-prefix-routes vni 9992 set routing-instances SECURE_VRF protocols evpn ip-prefix-routes export T5_SECURE_EXPORT set interfaces lo0 unit 991 family inet address 192.168.91.253/32 set interfaces lo0 unit 992 family inet address 192.168.92.253/32 set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct then accept set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_SECURE_EXPORT term fm_direct then accept set policy-options policy-statement T5_SECURE_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_SECURE_EXPORT term Default_Route then accept set policy-options policy-statement FW1_Export from protocol evpn set policy-options policy-statement FW1_Export then accept
-
We also need to set up the policy statements on Service Leaf-1:
set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct then accept set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_SECURE_EXPORT term fm_direct then accept set policy-options policy-statement T5_SECURE_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_SECURE_EXPORT term Default_Route then accept set policy-options policy-statement FW1_Export from protocol evpn set policy-options policy-statement FW1_Export then accept
Service Leaf-2
The configuration on Service Leaf-2 is similar to the Service Leaf-1 configuration.
-
Here we set up firewall interconnect Service Leaf-2:
set interfaces xe-0/0/4:0 description "SRX Firewall-1: xe-0/0/5" set interfaces xe-0/0/4:0 mtu 9192 set interfaces xe-0/0/4:0 unit 0 family ethernet-switching interface-mode trunk set interfaces xe-0/0/4:0 unit 0 family ethernet-switching vlan members V991 set interfaces xe-0/0/4:0 unit 0 family ethernet-switching vlan members V992 set interfaces irb unit 991 family inet address 10.81.91.6/24 set interfaces irb unit 992 family inet address 10.81.92.6/24
-
Here we set up the routing instances on Service Leaf-2:
set routing-instances INSPECT_VRF description "VRF for Firewall-1" set routing-instances INSPECT_VRF instance-type vrf set routing-instances INSPECT_VRF interface irb.991 set routing-instances INSPECT_VRF interface lo0.991 set routing-instances INSPECT_VRF route-distinguisher 10.80.224.139:9991 set routing-instances INSPECT_VRF vrf-target target:64730:991 set routing-instances INSPECT_VRF vrf-table-label set routing-instances INSPECT_VRF routing-options multipath set routing-instances INSPECT_VRF protocols bgp group Firewall-1 type external set routing-instances INSPECT_VRF protocols bgp group Firewall-1 export FW1_Export set routing-instances INSPECT_VRF protocols bgp group Firewall-1 local-as 64730 set routing-instances INSPECT_VRF protocols bgp group Firewall-1 neighbor 10.81.91.5 peer-as 64777 set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes vni 9991 set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes export T5_INSPECT_EXPORT set routing-instances SECURE_VRF description "VRF for SECURED FIREWALL TRAFFIC" set routing-instances SECURE_VRF instance-type vrf set routing-instances SECURE_VRF interface irb.992 set routing-instances SECURE_VRF interface lo0.992 set routing-instances SECURE_VRF route-distinguisher 10.80.224.139:9992 set routing-instances SECURE_VRF vrf-target target:64730:992 set routing-instances SECURE_VRF vrf-table-label set routing-instances SECURE_VRF routing-options multipath set routing-instances SECURE_VRF protocols bgp group Firewall-1 type external set routing-instances SECURE_VRF protocols bgp group Firewall-1 export FW1_Export set routing-instances SECURE_VRF protocols bgp group Firewall-1 local-as 64730 set routing-instances SECURE_VRF protocols bgp group Firewall-1 neighbor 10.81.92.5 peer-as 64777 set routing-instances SECURE_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances SECURE_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances SECURE_VRF protocols evpn ip-prefix-routes vni 9992 set routing-instances SECURE_VRF protocols evpn ip-prefix-routes export T5_SECURE_EXPORT set interfaces lo0 unit 991 family inet address 192.168.91.254/32 set interfaces lo0 unit 992 family inet address 192.168.92.254/32
-
And lastly, we set up the policy statements on Service Leaf-2:
set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct then accept set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_SECURE_EXPORT term fm_direct then accept set policy-options policy-statement T5_SECURE_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_SECURE_EXPORT term Default_Route then accept set policy-options policy-statement FW1_Export from protocol evpn set policy-options policy-statement FW1_Export then accept
Firewall
The firewall interfaces are configured as VLAN tagged interfaces. It establishes two EBGP sessions with each service leaf, as shown in Figure 2.
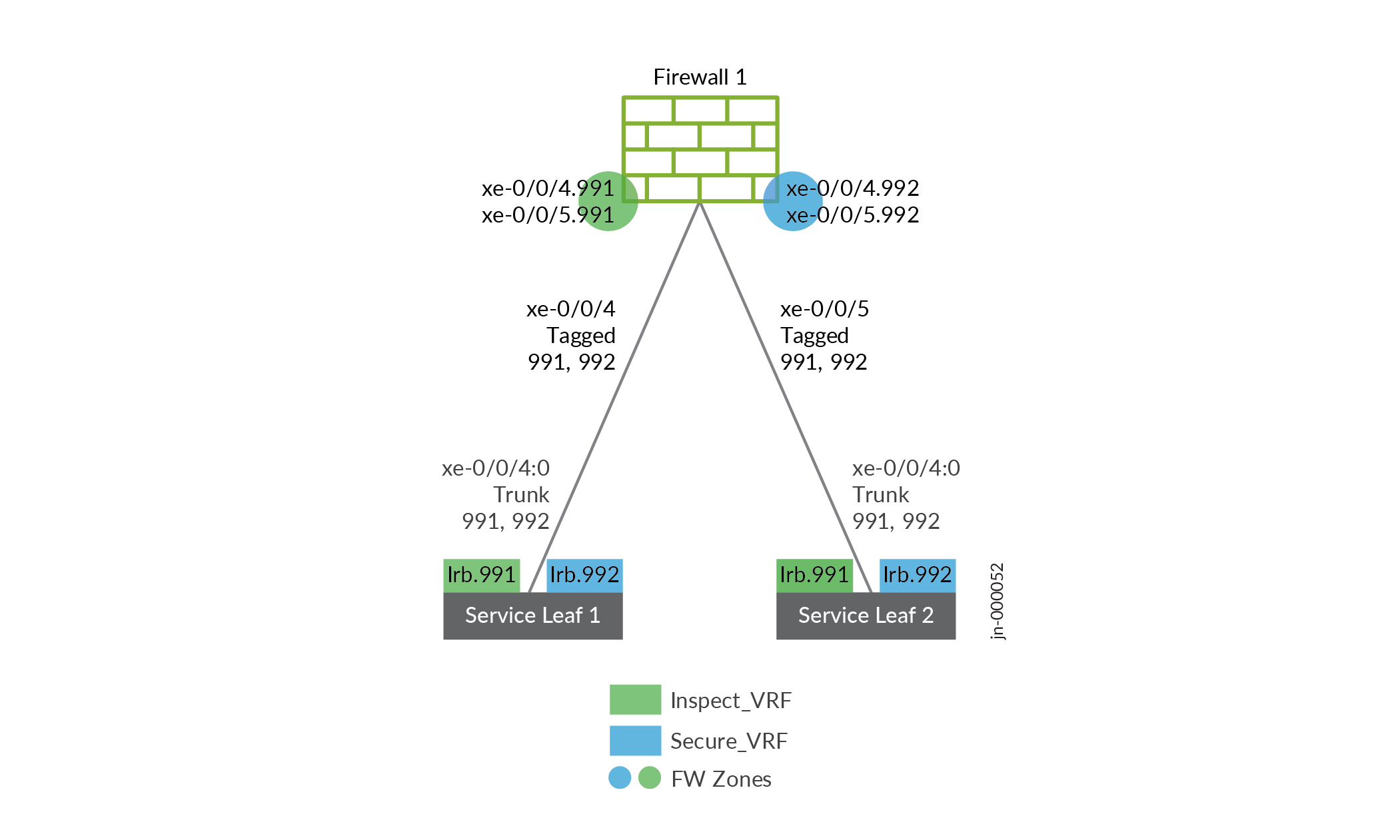
-
Here, we set up the Firewall-1 service leaf interconnect shown in the image, as well as the BGP peering and route export:
set interfaces xe-0/0/4 vlan-tagging set interfaces xe-0/0/4 unit 991 vlan-id 991 set interfaces xe-0/0/4 unit 991 family inet address 10.81.91.1/30 set interfaces xe-0/0/4 unit 992 vlan-id 992 set interfaces xe-0/0/4 unit 992 family inet address 10.81.92.1/30 set interfaces xe-0/0/5 vlan-tagging set interfaces xe-0/0/5 unit 991 vlan-id 991 set interfaces xe-0/0/5 unit 991 family inet address 10.81.91.5/30 set interfaces xe-0/0/5 unit 992 vlan-id 992 set interfaces xe-0/0/5 unit 992 family inet address 10.81.92.5/30 set protocols bgp group ServiceLeaf type external set protocols bgp group ServiceLeaf export Export-Default-Route set protocols bgp group ServiceLeaf local-as 64777 set protocols bgp group ServiceLeaf neighbor 10.81.91.2 peer-as 64730 set protocols bgp group ServiceLeaf neighbor 10.81.92.2 peer-as 64730 set protocols bgp group ServiceLeaf neighbor 10.81.91.6 peer-as 64730 set protocols bgp group ServiceLeaf neighbor 10.81.92.6 peer-as 64730 set policy-options policy-statement Export-Default-Route term 10 from route-filter 0.0.0.0/0 exact set policy-options policy-statement Export-Default-Route term 10 then accept set policy-options policy-statement Export-Default-Route term 100 then reject
-
Now we need to set up the zones and policies configuration for Firewall-1. We put traffic traversing logical interface 991 into the INSPECT_Zone, and traffic traversing logical interface 992 into the SECURE_Zone.
set security zones security-zone INSPECT_Zone address-book address EP11 10.1.110.11/32 set security zones security-zone INSPECT_Zone host-inbound-traffic system-services all set security zones security-zone INSPECT_Zone host-inbound-traffic protocols all set security zones security-zone INSPECT_Zone interfaces xe-0/0/4.991 set security zones security-zone INSPECT_Zone interfaces xe-0/0/5.991 set security zones security-zone SECURE_Zone address-book address EP21 10.1.111.21/32 set security zones security-zone SECURE_Zone host-inbound-traffic system-services all set security zones security-zone SECURE_Zone host-inbound-traffic protocols all set security zones security-zone SECURE_Zone interfaces xe-0/0/4.992 set security zones security-zone SECURE_Zone interfaces xe-0/0/5.992
-
To restrict communication from Endpoint 11 to Endpoint 21 to specific protocols only, (Ping, HTTPS, SSH, and UDP to support trace route from the servers) we create security policies for traffic between the INSPECT_Zone and SECURE_Zone:
set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match source-address 10.1.110.11 set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match destination-address 10.1.111.21 set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match application junos-https set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match application junos-ssh set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match application junos-ping set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match application junos-udp-any set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 then permit set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Block_All match source-address any set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Block_All match destination-address any set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Block_All match application any set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Block_All then deny
-
You define a policy that accepts all traffic from the SECURE zone to the INSPECT zone:
set security policies from-zone SECURE_Zone to-zone INSPECT_Zone policy Allow_All match source-address any set security policies from-zone SECURE_Zone to-zone INSPECT_Zone policy Allow_All match destination-address any set security policies from-zone SECURE_Zone to-zone INSPECT_Zone policy Allow_All match application any set security policies from-zone SECURE_Zone to-zone INSPECT_Zone policy Allow_All then permit
Verification
The commands and output in this section validate that FBF is working correctly for the traffic between EP11 and EP21.
- Generate pings between EP11 and EP21. While the pings are flowing, first
clear, and then display firewall counters at leaf 1 and leaf
2:
{master:0} jcluser@Leaf1>clear firewall all {master:0} root@Leaf1> show firewall Filter: SecureTraffic Counters: Name Bytes Packets EP11_to_EP21 1484 14 . . . {master:0} root@Leaf1> show firewall Filter: SecureTraffic Counters: Name Bytes Packets EP11_to_EP21 2332 22The output from Leaf 1 confirms that the BMS ping traffic is hitting the SecureTraffic filter and the firewall term that redirects the traffic to the INSPECT_VRF. Similar results are noted at Leaf2 for the SecureResponseTraffic filter that steers the replies into the SECURE_VRF.
- Display security flow information on the SRX
device:
jcluser@firewall>clear firewall all root@firewall> show security flow session | match icmp In: 10.1.110.11/5554 --> 10.1.111.21/31;icmp, Conn Tag: 0x0, If: xe-0/0/5.991, Pkts: 1, Bytes: 84, Out: 10.1.111.21/31 --> 10.1.110.11/5554;icmp, Conn Tag: 0x0, If: xe-0/0/4.992, Pkts: 0, Bytes: 0, In: 10.1.110.11/5554 --> 10.1.111.21/32;icmp, Conn Tag: 0x0, If: xe-0/0/5.991, Pkts: 1, Bytes: 84, Out: 10.1.111.21/32 --> 10.1.110.11/5554;icmp, Conn Tag: 0x0, If: xe-0/0/4.992, Pkts: 0, Bytes: 0, In: 10.1.110.11/5554 --> 10.1.111.21/33;icmp, Conn Tag: 0x0, If: xe-0/0/5.991, Pkts: 1, Bytes: 84,The output confirms that the BMS ping traffic is being inspected by the firewall. This confirms FBF is directing traffic sent by EP11 to EP21 from the leaf to the service leaf, and from there to the firewall device.
- Trace the path between EP11 and EP21. You expect to see underlay forwarding
hops through the firewall device.
The results are shown in Figure 3
Note: The traffic from EP11 is encapsulated into VXLAN and sent from leaf 1 to the service leaf. The service leaf decapsulates the traffic and routes it as native IP to the firewall device, which allows the underlay hops to be exposed in the output of the trace route.Figure 3: EP11 to EP21 Trace route With FBF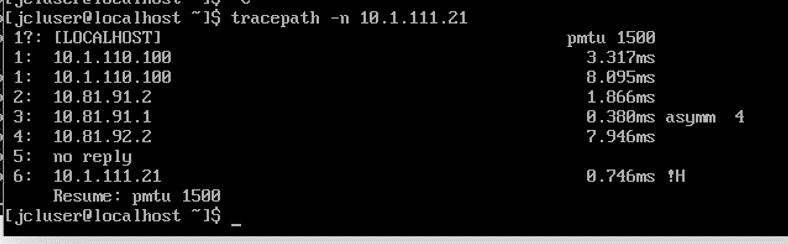
The trace route output from EP11 (BMS 1) shows the additional fabric forwarding hops used to steer traffic through the firewall. In the output, hops 1 and 6 represent the IRB interfaces in leaf 1 and leaf 2, respectively. The 10.81.91.2 hop, in contract, represents the irb.991 interface, housed in the INSPECT_VRF, on service leaf 1. These results add additional confirmation that EP11 to EP21 traffic is correctly directed through the firewall.
- Deactivate the firewall filter applied to the IRB interface at both leaf 1
and leaf 2. Be sure to commit the
changes.
{master:0}[edit] root@Leaf1# deactivate interfaces irb unit 110 family inet filter input{master:0}[edit] root@Leaf2# deactivate interfaces irb unit 111 family inet filter inputRepeat the trace route between EP11 and EP21. The results are shown in Figure 4
Figure 4: EP11 to EP21 Trace route Without FBF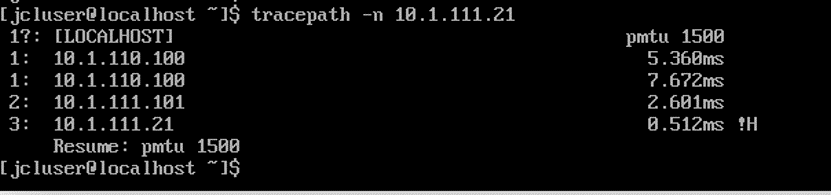
The trace route output show that with the filter deactivated the EP11 to EP21 traffic flows directly between the IRB interfaces in the leaf devices. With FBF remove the service leaves and firewall device are no longer in the forwarding path between these endpoints.
Complete Device Configurations
This section provides the full configurations for all devices used in this example. Site specific configuration for user login, system services, logging, and the management interface is omitted.
Configuration for Spine-1
set system host-name Spine1 set chassis fpc 0 pic 0 port 4 channel-speed 10g set interfaces et-0/0/0 mtu 9200 set interfaces et-0/0/0 unit 0 family inet address 10.80.224.30/31 set interfaces et-0/0/1 mtu 9200 set interfaces et-0/0/1 unit 0 family inet address 10.80.224.0/31 set interfaces xe-0/0/4:0 mtu 9200 set interfaces xe-0/0/4:0 unit 0 family inet address 10.80.224.2/31 set interfaces et-0/0/4:1 unit 0 family ethernet-switching vlan members default set interfaces et-0/0/4:1 unit 0 family ethernet-switching storm-control default set interfaces xe-0/0/4:1 mtu 9200 set interfaces xe-0/0/4:1 unit 0 family inet address 10.80.224.4/31 set interfaces et-0/0/4:2 unit 0 family ethernet-switching vlan members default set interfaces et-0/0/4:2 unit 0 family ethernet-switching storm-control default set interfaces xe-0/0/4:2 mtu 9200 set interfaces xe-0/0/4:2 unit 0 family inet address 10.80.224.6/31 set interfaces et-0/0/4:3 unit 0 family ethernet-switching vlan members default set interfaces et-0/0/4:3 unit 0 family ethernet-switching storm-control default set interfaces xe-0/0/4:3 mtu 9200 set interfaces xe-0/0/4:3 unit 0 family inet address 10.80.224.8/31 set interfaces lo0 unit 0 family inet address 10.80.224.149/32 set forwarding-options storm-control-profiles default all set policy-options policy-statement ECMP-POLICY then load-balance per-packet set policy-options policy-statement FROM_Lo0 term 10 from interface lo0.0 set policy-options policy-statement FROM_Lo0 term 10 then accept set policy-options policy-statement FROM_Lo0 term 20 then reject set policy-options policy-statement FROM_UNDERLAY_BGP term 10 from protocol bgp set policy-options policy-statement FROM_UNDERLAY_BGP term 10 then accept set policy-options policy-statement UNDERLAY-EXPORT term LOOPBACK from route-filter 10.80.224.128/25 orlonger set policy-options policy-statement UNDERLAY-EXPORT term LOOPBACK from route-filter 10.0.0.0/24 orlonger set policy-options policy-statement UNDERLAY-EXPORT term LOOPBACK then accept set policy-options policy-statement UNDERLAY-EXPORT term DEFAULT then reject set policy-options policy-statement UNDERLAY-IMPORT term LOOPBACK from route-filter 10.80.224.128/25 orlonger set policy-options policy-statement UNDERLAY-IMPORT term LOOPBACK from route-filter 10.0.0.0/24 orlonger set policy-options policy-statement UNDERLAY-IMPORT term LOOPBACK then accept set policy-options policy-statement UNDERLAY-IMPORT term DEFAULT then reject set routing-options forwarding-table export ECMP-POLICY set routing-options forwarding-table ecmp-fast-reroute set protocols bgp group EVPN_FABRIC type internal set protocols bgp group EVPN_FABRIC description "manage connection from leaves" set protocols bgp group EVPN_FABRIC local-address 10.80.224.149 set protocols bgp group EVPN_FABRIC family evpn signaling set protocols bgp group EVPN_FABRIC cluster 10.80.224.149 set protocols bgp group EVPN_FABRIC local-as 64730 set protocols bgp group EVPN_FABRIC multipath set protocols bgp group EVPN_FABRIC neighbor 10.80.224.139 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.140 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.141 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.142 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.143 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.138 set protocols bgp group EVPN_FABRIC vpn-apply-export set protocols bgp group UNDERLAY type external set protocols bgp group UNDERLAY description "Connection to EBGP UNDERLAY" set protocols bgp group UNDERLAY import UNDERLAY-IMPORT set protocols bgp group UNDERLAY family inet unicast set protocols bgp group UNDERLAY export UNDERLAY-EXPORT set protocols bgp group UNDERLAY local-as 10021 set protocols bgp group UNDERLAY multipath multiple-as set protocols bgp group UNDERLAY bfd-liveness-detection minimum-interval 350 set protocols bgp group UNDERLAY bfd-liveness-detection multiplier 3 set protocols bgp group UNDERLAY neighbor 10.80.224.9 peer-as 65015 set protocols bgp group UNDERLAY neighbor 10.80.224.7 peer-as 65014 set protocols bgp group UNDERLAY neighbor 10.80.224.3 peer-as 65012 set protocols bgp group UNDERLAY neighbor 10.80.224.5 peer-as 65013 set protocols bgp group UNDERLAY neighbor 10.80.224.1 peer-as 65011 set protocols bgp group UNDERLAY neighbor 10.80.224.31 peer-as 65009 set protocols bgp hold-time 10 set protocols bgp log-updown set protocols lldp interface all set protocols igmp-snooping vlan default set vlans default vlan-id 1
Configuration for Spine-2
set system host-name Spine2 set chassis fpc 0 pic 0 port 4 channel-speed 10g set interfaces et-0/0/0 mtu 9200 set interfaces et-0/0/0 unit 0 family inet address 10.80.224.10/31 set interfaces et-0/0/1 mtu 9200 set interfaces et-0/0/1 unit 0 family inet address 10.80.224.32/31 set interfaces xe-0/0/4:0 mtu 9200 set interfaces xe-0/0/4:0 unit 0 family inet address 10.80.224.12/31 set interfaces xe-0/0/4:1 mtu 9200 set interfaces xe-0/0/4:1 unit 0 family inet address 10.80.224.14/31 set interfaces xe-0/0/4:2 unit 0 family inet address 10.80.224.16/31 set interfaces et-0/0/4:3 unit 0 family inet dhcp vendor-id Juniper-qfx5120-32c set interfaces xe-0/0/4:3 mtu 9200 set interfaces xe-0/0/4:3 unit 0 family inet address 10.80.224.18/31 set interfaces lo0 unit 0 family inet address 10.80.224.150/32 set forwarding-options storm-control-profiles default all set policy-options policy-statement ECMP-POLICY then load-balance per-packet set policy-options policy-statement FROM_Lo0 term 10 from interface lo0.0 set policy-options policy-statement FROM_Lo0 term 10 then accept set policy-options policy-statement FROM_Lo0 term 20 then reject set policy-options policy-statement FROM_UNDERLAY_BGP term 10 from protocol bgp set policy-options policy-statement FROM_UNDERLAY_BGP term 10 then accept set policy-options policy-statement UNDERLAY-EXPORT term LOOPBACK from route-filter 10.80.224.128/25 orlonger set policy-options policy-statement UNDERLAY-EXPORT term LOOPBACK then accept set policy-options policy-statement UNDERLAY-EXPORT term DEFAULT then reject set policy-options policy-statement UNDERLAY-IMPORT term LOOPBACK from route-filter 10.80.224.128/25 orlonger set policy-options policy-statement UNDERLAY-IMPORT term LOOPBACK then accept set policy-options policy-statement UNDERLAY-IMPORT term DEFAULT then reject set routing-options forwarding-table export ECMP-POLICY set routing-options forwarding-table ecmp-fast-reroute set protocols bgp group EVPN_FABRIC type internal set protocols bgp group EVPN_FABRIC description "manage connection from leaves" set protocols bgp group EVPN_FABRIC local-address 10.80.224.150 set protocols bgp group EVPN_FABRIC family evpn signaling set protocols bgp group EVPN_FABRIC cluster 10.80.224.150 set protocols bgp group EVPN_FABRIC local-as 64730 set protocols bgp group EVPN_FABRIC multipath set protocols bgp group EVPN_FABRIC neighbor 10.80.224.139 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.140 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.141 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.142 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.143 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.138 set protocols bgp group EVPN_FABRIC vpn-apply-export set protocols bgp group UNDERLAY type external set protocols bgp group UNDERLAY description "Connection to EBGP UNDERLAY" set protocols bgp group UNDERLAY import UNDERLAY-IMPORT set protocols bgp group UNDERLAY family inet unicast set protocols bgp group UNDERLAY export UNDERLAY-EXPORT set protocols bgp group UNDERLAY local-as 10022 set protocols bgp group UNDERLAY multipath multiple-as set protocols bgp group UNDERLAY bfd-liveness-detection minimum-interval 350 set protocols bgp group UNDERLAY bfd-liveness-detection multiplier 3 set protocols bgp group UNDERLAY neighbor 10.80.224.13 peer-as 65012 set protocols bgp group UNDERLAY neighbor 10.80.224.19 peer-as 65015 set protocols bgp group UNDERLAY neighbor 10.80.224.11 peer-as 65011 set protocols bgp group UNDERLAY neighbor 10.80.224.17 peer-as 65014 set protocols bgp group UNDERLAY neighbor 10.80.224.15 peer-as 65013 set protocols bgp group UNDERLAY neighbor 10.80.224.33 peer-as 65009 set protocols bgp hold-time 10 set protocols bgp log-updown set protocols lldp port-id-subtype interface-name set protocols lldp interface all set protocols lldp-med interface all set protocols igmp-snooping vlan default
Configuration for Server Leaf-1
set system host-name Leaf1 set system root-authentication encrypted-password "$6$yMrAzWii$mH8/hzspVvEAWSta.W2sbI3Fkjh5DpY.QMJhvyXP1ZfFWZ4E0KLfzlPZISlUqElTGmzeKEuE9EDths9PviIwR/" set system login user jcluser uid 2000 set system login user jcluser class super-user set system login user jcluser authentication encrypted-password "$6$yz5sIC9j$Z3P7ygtxzWAdfjDFXUmz787lCqquxA0YbkseMs9W1ZxyDOIsXBwJer1ShHlrBp3obTitLJGYbrVk3IdIR5DfI." set system services ssh root-login allow set interfaces xe-0/0/0 mtu 9200 set interfaces xe-0/0/0 unit 0 family inet address 10.80.224.3/31 set interfaces xe-0/0/2 mtu 9200 set interfaces xe-0/0/2 unit 0 family inet address 10.80.224.13/31 set interfaces irb unit 110 virtual-gateway-accept-data set interfaces irb unit 110 family inet filter input SecureTraffic set interfaces irb unit 110 family inet address 10.1.110.100/24 virtual-gateway-address 10.1.110.1 set interfaces irb unit 110 virtual-gateway-v4-mac e4:5d:37:11:10:01 set interfaces irb unit 111 family inet address 10.1.111.1/24 set interfaces irb unit 111 virtual-gateway-v4-mac e4:5d:37:11:11:01 set interfaces irb unit 112 family inet address 10.1.112.1/24 set interfaces irb unit 112 virtual-gateway-v4-mac e4:5d:37:11:12:01 set interfaces lo0 unit 0 description "** dc-leaf1-lo0" set interfaces lo0 unit 0 family inet address 10.80.224.140/32 set interfaces lo0 unit 110 family inet address 192.168.110.1/32 set interfaces lo0 unit 110 family inet6 address 2001:db8::192:168:110:1/128 set interfaces lo0 unit 112 family inet address 192.168.112.1/32 set interfaces lo0 unit 112 family inet6 address 2001:db8::192:168:112:1/128 set interfaces lo0 unit 991 family inet address 192.168.91.1/32 set forwarding-options storm-control-profiles default all set forwarding-options vxlan-routing next-hop 32768 set forwarding-options vxlan-routing overlay-ecmp set policy-options policy-statement ECMP-POLICY then load-balance per-packet set policy-options policy-statement FROM_Lo0 term 10 from interface lo0.0 set policy-options policy-statement FROM_Lo0 term 10 then accept set policy-options policy-statement FROM_Lo0 term 20 then reject set policy-options policy-statement FROM_UNDERLAY_BGP term 10 from protocol bgp set policy-options policy-statement FROM_UNDERLAY_BGP term 10 then accept set policy-options policy-statement T5_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_EXPORT term fm_direct then accept set policy-options policy-statement T5_EXPORT term fm_static from protocol static set policy-options policy-statement T5_EXPORT term fm_static then accept set policy-options policy-statement T5_EXPORT term fm_v4_host from protocol evpn set policy-options policy-statement T5_EXPORT term fm_v4_host from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement T5_EXPORT term fm_v4_host then accept set policy-options policy-statement T5_EXPORT term fm_v6_host from route-filter 0::0/0 prefix-length-range /128-/128 set policy-options policy-statement T5_EXPORT term fm_v6_host then accept set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct then accept set policy-options policy-statement T5_INSPECT_EXPORT term fm_static from protocol static set policy-options policy-statement T5_INSPECT_EXPORT term fm_static then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_SECURE_EXPORT term fm_direct then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_static from protocol static set policy-options policy-statement T5_SECURE_EXPORT term fm_static then accept set firewall family inet filter SecureTraffic term EP11_to_EP21 from source-address 10.1.110.11/32 set firewall family inet filter SecureTraffic term EP11_to_EP21 from destination-address 10.1.111.21/32 set firewall family inet filter SecureTraffic term EP11_to_EP21 then count EP11_to_EP21 set firewall family inet filter SecureTraffic term EP11_to_EP21 then routing-instance INSPECT_VRF set firewall family inet filter SecureTraffic term Allow_All then accept set routing-instances INSPECT_VRF routing-options static route 10.1.110.11/32 next-table Tenant1_VRF.inet.0 set routing-instances INSPECT_VRF routing-options multipath set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes vni 9991 set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes export T5_INSPECT_EXPORT set routing-instances INSPECT_VRF description "VRF for Firewall1" set routing-instances INSPECT_VRF instance-type vrf set routing-instances INSPECT_VRF interface lo0.991 set routing-instances INSPECT_VRF route-distinguisher 10.80.224.140:9991 set routing-instances INSPECT_VRF vrf-target target:64730:991 set routing-instances INSPECT_VRF vrf-table-label set routing-instances Tenant1_VRF routing-options multipath set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes vni 9110 set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes export T5_EXPORT set routing-instances Tenant1_VRF description "VRF for tenant Tenant_1" set routing-instances Tenant1_VRF instance-type vrf set routing-instances Tenant1_VRF forwarding-options dhcp-relay dhcpv6 overrides relay-source lo0.110 set routing-instances Tenant1_VRF forwarding-options dhcp-relay dhcpv6 forward-only set routing-instances Tenant1_VRF forwarding-options dhcp-relay dhcpv6 forward-only-replies set routing-instances Tenant1_VRF forwarding-options dhcp-relay dhcpv6 group all interface irb.110 set routing-instances Tenant1_VRF forwarding-options dhcp-relay dhcpv6 server-group dhcp-servers-v6 2001:db8::10:1:140:188 set routing-instances Tenant1_VRF forwarding-options dhcp-relay dhcpv6 active-server-group dhcp-servers-v6 set routing-instances Tenant1_VRF forwarding-options dhcp-relay relay-option-82 set routing-instances Tenant1_VRF interface irb.110 set routing-instances Tenant1_VRF interface irb.111 set routing-instances Tenant1_VRF interface lo0.110 set routing-instances Tenant1_VRF route-distinguisher 10.80.224.140:9110 set routing-instances Tenant1_VRF vrf-target target:64730:110 set routing-instances Tenant1_VRF vrf-table-label set routing-instances Tenant2_VRF routing-options multipath set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes vni 9112 set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes export T5_EXPORT set routing-instances Tenant2_VRF description "VRF for tenant Tenant_1" set routing-instances Tenant2_VRF instance-type vrf set routing-instances Tenant2_VRF interface irb.112 set routing-instances Tenant2_VRF interface lo0.112 set routing-instances Tenant2_VRF route-distinguisher 10.80.224.140:9112 set routing-instances Tenant2_VRF vrf-target target:64730:112 set routing-instances Tenant2_VRF vrf-table-label set routing-options router-id 10.80.224.140 set routing-options autonomous-system 64730 set routing-options forwarding-table export ECMP-POLICY set routing-options forwarding-table ecmp-fast-reroute set routing-options forwarding-table chained-composite-next-hop ingress evpn set protocols bgp group EVPN_FABRIC type internal set protocols bgp group EVPN_FABRIC description "Connection to EVPN Fabric RRs (tenants.bgp_reflector)" set protocols bgp group EVPN_FABRIC local-address 10.80.224.140 set protocols bgp group EVPN_FABRIC family evpn signaling set protocols bgp group EVPN_FABRIC local-as 64730 set protocols bgp group EVPN_FABRIC multipath set protocols bgp group EVPN_FABRIC neighbor 10.80.224.149 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.150 set protocols bgp group UNDERLAY type external set protocols bgp group UNDERLAY description "Connection to EBGP UNDERLAY" set protocols bgp group UNDERLAY family inet unicast set protocols bgp group UNDERLAY export FROM_Lo0 set protocols bgp group UNDERLAY export FROM_UNDERLAY_BGP set protocols bgp group UNDERLAY local-as 65012 set protocols bgp group UNDERLAY multipath multiple-as set protocols bgp group UNDERLAY bfd-liveness-detection minimum-interval 350 set protocols bgp group UNDERLAY bfd-liveness-detection multiplier 3 set protocols bgp group UNDERLAY neighbor 10.80.224.12 peer-as 10022 set protocols bgp group UNDERLAY neighbor 10.80.224.2 peer-as 10021 set protocols bgp hold-time 10 set protocols bgp log-updown set protocols evpn encapsulation vxlan set protocols evpn extended-vni-list 110 set protocols evpn extended-vni-list 111 set protocols evpn extended-vni-list 112 set protocols l2-learning global-mac-table-aging-time 600 set protocols l2-learning global-mac-ip-table-aging-time 300 set protocols l2-learning decapsulate-accept-inner-vlan set protocols lldp interface all set protocols igmp-snooping vlan default set switch-options vtep-source-interface lo0.0 set switch-options route-distinguisher 10.80.224.140:1 set switch-options vrf-target target:64730:1 set switch-options vrf-target auto set vlans default vlan-id 1 set vlans v110 vlan-id 110 set vlans v110 l3-interface irb.110 set vlans v110 vxlan vni 110 set vlans v111 vlan-id 111 set vlans v111 l3-interface irb.111 set vlans v111 vxlan vni 111 set vlans v112 vlan-id 112 set vlans v112 l3-interface irb.112 set vlans v112 vxlan vni 112
Configuration for Server Leaf-2:
set system host-name Leaf2 set interfaces xe-0/0/0 mtu 9200 set interfaces xe-0/0/0 unit 0 family inet address 10.80.224.5/31 set interfaces xe-0/0/1 unit 0 family ethernet-switching interface-mode trunk set interfaces xe-0/0/1 unit 0 family ethernet-switching vlan members v110 set interfaces xe-0/0/1 unit 0 family ethernet-switching vlan members v111 set interfaces et-0/0/2 unit 0 family inet dhcp vendor-id Juniper-qfx5120-48y-8c set interfaces ge-0/0/2 unit 0 family inet dhcp vendor-id Juniper-qfx5120-48y-8c set interfaces xe-0/0/2 mtu 9200 set interfaces xe-0/0/2 unit 0 family inet address 10.80.224.15/31 set interfaces irb unit 110 virtual-gateway-accept-data set interfaces irb unit 110 family inet address 10.1.110.101/24 virtual-gateway-address 10.1.110.1 set interfaces irb unit 110 virtual-gateway-v4-mac e4:5d:37:11:10:01 set interfaces irb unit 111 virtual-gateway-accept-data set interfaces irb unit 111 family inet filter input SecureResponseTraffic set interfaces irb unit 111 family inet address 10.1.111.101/24 virtual-gateway-address 10.1.111.1 set interfaces irb unit 111 virtual-gateway-v4-mac e4:5d:37:11:11:01 set interfaces irb unit 112 family inet address 10.1.112.101/24 virtual-gateway-address 10.1.112.1 set interfaces irb unit 112 virtual-gateway-v4-mac e4:5d:37:11:12:01 set interfaces lo0 unit 0 description "** dc-leaf2-lo0" set interfaces lo0 unit 0 family inet address 10.80.224.141/32 set interfaces lo0 unit 110 family inet address 192.168.110.2/32 set interfaces lo0 unit 110 family inet6 address 2001:db8::192:168:110:2/128 set interfaces lo0 unit 112 family inet address 192.168.112.2/32 set interfaces lo0 unit 112 family inet6 address 2001:db8::192:168:112:2/128 set interfaces lo0 unit 992 family inet address 192.168.92.2/32 set forwarding-options storm-control-profiles default all set forwarding-options vxlan-routing next-hop 32768 set forwarding-options vxlan-routing overlay-ecmp set policy-options policy-statement ECMP-POLICY then load-balance per-packet set policy-options policy-statement FROM_Lo0 term 10 from interface lo0.0 set policy-options policy-statement FROM_Lo0 term 10 then accept set policy-options policy-statement FROM_Lo0 term 20 then reject set policy-options policy-statement FROM_UNDERLAY_BGP term 10 from protocol bgp set policy-options policy-statement FROM_UNDERLAY_BGP term 10 then accept set policy-options policy-statement T5_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_EXPORT term fm_direct then accept set policy-options policy-statement T5_EXPORT term fm_static from protocol static set policy-options policy-statement T5_EXPORT term fm_static then accept set policy-options policy-statement T5_EXPORT term fm_v4_host from protocol evpn set policy-options policy-statement T5_EXPORT term fm_v4_host from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement T5_EXPORT term fm_v4_host then accept set policy-options policy-statement T5_EXPORT term fm_v6_host from route-filter 0::0/0 prefix-length-range /128-/128 set policy-options policy-statement T5_EXPORT term fm_v6_host then accept set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct then accept set policy-options policy-statement T5_INSPECT_EXPORT term fm_static from protocol static set policy-options policy-statement T5_INSPECT_EXPORT term fm_static then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_SECURE_EXPORT term fm_direct then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_static from protocol static set policy-options policy-statement T5_SECURE_EXPORT term fm_static then accept set firewall family inet filter SecureResponseTraffic term EP21_to_EP11 from source-address 10.1.111.21/32 set firewall family inet filter SecureResponseTraffic term EP21_to_EP11 from destination-address 10.1.110.11/32 set firewall family inet filter SecureResponseTraffic term EP21_to_EP11 then count EP21_to_EP11 set firewall family inet filter SecureResponseTraffic term EP21_to_EP11 then routing-instance SECURE_VRF set firewall family inet filter SecureResponseTraffic term Allow_All then accept set routing-instances SECURE_VRF routing-options static route 10.1.111.21/32 next-table Tenant1_VRF.inet.0 set routing-instances SECURE_VRF routing-options multipath set routing-instances SECURE_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances SECURE_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances SECURE_VRF protocols evpn ip-prefix-routes vni 9992 set routing-instances SECURE_VRF protocols evpn ip-prefix-routes export T5_SECURE_EXPORT set routing-instances SECURE_VRF description "VRF for SECURED FIREWALL TRAFFIC" set routing-instances SECURE_VRF instance-type vrf set routing-instances SECURE_VRF interface lo0.992 set routing-instances SECURE_VRF route-distinguisher 10.80.224.141:9992 set routing-instances SECURE_VRF vrf-target target:64730:992 set routing-instances SECURE_VRF vrf-table-label set routing-instances Tenant1_VRF routing-options multipath set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes vni 9110 set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes export T5_EXPORT set routing-instances Tenant1_VRF description "VRF for tenant Tenant_1" set routing-instances Tenant1_VRF instance-type vrf set routing-instances Tenant1_VRF interface irb.110 set routing-instances Tenant1_VRF interface irb.111 set routing-instances Tenant1_VRF interface lo0.110 set routing-instances Tenant1_VRF route-distinguisher 10.80.224.141:9110 set routing-instances Tenant1_VRF vrf-target target:64730:110 set routing-instances Tenant1_VRF vrf-table-label set routing-instances Tenant2_VRF routing-options multipath set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes vni 9112 set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes export T5_EXPORT set routing-instances Tenant2_VRF description "VRF for tenant Tenant_1" set routing-instances Tenant2_VRF instance-type vrf set routing-instances Tenant2_VRF interface irb.112 set routing-instances Tenant2_VRF interface lo0.112 set routing-instances Tenant2_VRF route-distinguisher 10.80.224.141:9112 set routing-instances Tenant2_VRF vrf-target target:64730:112 set routing-instances Tenant2_VRF vrf-table-label set routing-options static route 0.0.0.0/0 next-hop 100.123.0.1 set routing-options router-id 10.80.224.141 set routing-options autonomous-system 64730 set routing-options forwarding-table export ECMP-POLICY set routing-options forwarding-table ecmp-fast-reroute set routing-options forwarding-table chained-composite-next-hop ingress evpn set protocols bgp group EVPN_FABRIC type internal set protocols bgp group EVPN_FABRIC description "Connection to EVPN Fabric RRs (tenants.bgp_reflector)" set protocols bgp group EVPN_FABRIC local-address 10.80.224.141 set protocols bgp group EVPN_FABRIC family evpn signaling set protocols bgp group EVPN_FABRIC local-as 64730 set protocols bgp group EVPN_FABRIC multipath set protocols bgp group EVPN_FABRIC neighbor 10.80.224.149 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.150 set protocols bgp group UNDERLAY type external set protocols bgp group UNDERLAY description "Connection to EBGP UNDERLAY" set protocols bgp group UNDERLAY family inet unicast set protocols bgp group UNDERLAY export FROM_Lo0 set protocols bgp group UNDERLAY export FROM_UNDERLAY_BGP set protocols bgp group UNDERLAY local-as 65013 set protocols bgp group UNDERLAY multipath multiple-as set protocols bgp group UNDERLAY bfd-liveness-detection minimum-interval 350 set protocols bgp group UNDERLAY bfd-liveness-detection multiplier 3 set protocols bgp group UNDERLAY neighbor 10.80.224.4 peer-as 10021 set protocols bgp group UNDERLAY neighbor 10.80.224.14 peer-as 10022 set protocols bgp hold-time 10 set protocols bgp log-updown set protocols evpn encapsulation vxlan set protocols evpn extended-vni-list 110 set protocols evpn extended-vni-list 111 set protocols evpn extended-vni-list 112 set protocols l2-learning global-mac-table-aging-time 600 set protocols l2-learning global-mac-ip-table-aging-time 300 set protocols l2-learning decapsulate-accept-inner-vlan set protocols lldp port-id-subtype interface-name set protocols lldp interface all set protocols igmp-snooping vlan default set switch-options vtep-source-interface lo0.0 set switch-options route-distinguisher 10.80.224.143:1 set switch-options vrf-target target:64730:1 set switch-options vrf-target auto set vlans v110 vlan-id 110 set vlans v110 l3-interface irb.110 set vlans v110 vxlan vni 110 set vlans v111 vlan-id 111 set vlans v111 l3-interface irb.111 set vlans v111 vxlan vni 111 set vlans v112 vlan-id 112 set vlans v112 l3-interface irb.112 set vlans v112 vxlan vni 112
Configuration for Service Leaf-1
set system host-name ServiceLeaf1 set chassis fpc 0 pic 0 port 4 channel-speed 10g set interfaces et-0/0/0 mtu 9200 set interfaces et-0/0/0 unit 0 family inet address 10.80.224.31/31 set interfaces et-0/0/1 mtu 9200 set interfaces et-0/0/1 unit 0 family inet address 10.80.224.33/31 set interfaces xe-0/0/4:0 description "SRX Firewall 1: xe-0/0/4" set interfaces xe-0/0/4:0 mtu 9192 set interfaces xe-0/0/4:0 unit 0 family ethernet-switching interface-mode trunk set interfaces xe-0/0/4:0 unit 0 family ethernet-switching vlan members V991 set interfaces xe-0/0/4:0 unit 0 family ethernet-switching vlan members V992 set interfaces et-0/0/4:1 unit 0 family inet dhcp vendor-id Juniper-qfx5120-32c set interfaces irb unit 991 family inet address 10.81.91.2/30 set interfaces irb unit 992 family inet address 10.81.92.2/30 set interfaces lo0 unit 0 family inet address 10.80.224.138/32 set interfaces lo0 unit 110 family inet address 192.168.110.253/32 set interfaces lo0 unit 110 family inet6 address 2001:db8::192:168:110:253/128 set interfaces lo0 unit 112 family inet address 192.168.112.253/32 set interfaces lo0 unit 112 family inet6 address 2001:db8::192:168:112:253/128 set interfaces lo0 unit 991 family inet address 192.168.91.253/32 set interfaces lo0 unit 992 family inet address 192.168.92.253/32 set forwarding-options storm-control-profiles default all set policy-options policy-statement ECMP-POLICY then load-balance per-packet set policy-options policy-statement FROM_Lo0 term 10 from interface lo0.0 set policy-options policy-statement FROM_Lo0 term 10 then accept set policy-options policy-statement FROM_Lo0 term 20 then reject set policy-options policy-statement FROM_UNDERLAY_BGP term 10 from protocol bgp set policy-options policy-statement FROM_UNDERLAY_BGP term 10 then accept set policy-options policy-statement FW1_Export from protocol evpn set policy-options policy-statement FW1_Export then accept set policy-options policy-statement T5_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_EXPORT term fm_direct then accept set policy-options policy-statement T5_EXPORT term fm_static from protocol static set policy-options policy-statement T5_EXPORT term fm_static then accept set policy-options policy-statement T5_EXPORT term fm_v4_host from protocol evpn set policy-options policy-statement T5_EXPORT term fm_v4_host from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement T5_EXPORT term fm_v4_host then accept set policy-options policy-statement T5_EXPORT term fm_v6_host from protocol evpn set policy-options policy-statement T5_EXPORT term fm_v6_host from route-filter 0::0/0 prefix-length-range /128-/128 set policy-options policy-statement T5_EXPORT term fm_v6_host then accept set policy-options policy-statement T5_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_EXPORT term Default_Route then accept set policy-options policy-statement T5_EXPORT term Default_Route_v6 from route-filter ::/0 exact set policy-options policy-statement T5_EXPORT term Default_Route_v6 then accept set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct then accept set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_SECURE_EXPORT term fm_direct then accept set policy-options policy-statement T5_SECURE_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_SECURE_EXPORT term Default_Route then accept set routing-instances INSPECT_VRF routing-options multipath set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes vni 9991 set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes export T5_INSPECT_EXPORT set routing-instances INSPECT_VRF protocols bgp group Firewall-1 type external set routing-instances INSPECT_VRF protocols bgp group Firewall-1 export FW1_Export set routing-instances INSPECT_VRF protocols bgp group Firewall-1 local-as 64730 set routing-instances INSPECT_VRF protocols bgp group Firewall-1 neighbor 10.81.91.1 peer-as 64777 set routing-instances INSPECT_VRF description "VRF for Firewall-1" set routing-instances INSPECT_VRF instance-type vrf set routing-instances INSPECT_VRF interface irb.991 set routing-instances INSPECT_VRF interface lo0.991 set routing-instances INSPECT_VRF route-distinguisher 10.80.224.138:9991 set routing-instances INSPECT_VRF vrf-target target:64730:991 set routing-instances INSPECT_VRF vrf-table-label set routing-instances SECURE_VRF routing-options multipath set routing-instances SECURE_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances SECURE_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances SECURE_VRF protocols evpn ip-prefix-routes vni 9992 set routing-instances SECURE_VRF protocols evpn ip-prefix-routes export T5_SECURE_EXPORT set routing-instances SECURE_VRF protocols bgp group Firewall-1 type external set routing-instances SECURE_VRF protocols bgp group Firewall-1 export FW1_Export set routing-instances SECURE_VRF protocols bgp group Firewall-1 local-as 64730 set routing-instances SECURE_VRF protocols bgp group Firewall-1 neighbor 10.81.92.1 peer-as 64777 set routing-instances SECURE_VRF description "VRF for SECURED FIREWALL TRAFFIC" set routing-instances SECURE_VRF instance-type vrf set routing-instances SECURE_VRF interface irb.992 set routing-instances SECURE_VRF interface lo0.992 set routing-instances SECURE_VRF route-distinguisher 10.80.224.138:9992 set routing-instances SECURE_VRF vrf-target target:64730:992 set routing-instances SECURE_VRF vrf-table-label set routing-instances Tenant1_VRF routing-options multipath set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes vni 9110 set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes export T5_EXPORT set routing-instances Tenant1_VRF instance-type vrf set routing-instances Tenant1_VRF interface xe-0/0/28:1.110 set routing-instances Tenant1_VRF interface lo0.110 set routing-instances Tenant1_VRF route-distinguisher 10.80.224.138:9110 set routing-instances Tenant1_VRF vrf-target target:64730:110 set routing-instances Tenant1_VRF vrf-table-label set routing-instances Tenant2_VRF routing-options multipath set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes vni 9112 set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes export T5_EXPORT set routing-instances Tenant2_VRF instance-type vrf set routing-instances Tenant2_VRF interface xe-0/0/28:0.112 set routing-instances Tenant2_VRF interface xe-0/0/28:1.112 set routing-instances Tenant2_VRF interface lo0.112 set routing-instances Tenant2_VRF route-distinguisher 10.80.224.138:9112 set routing-instances Tenant2_VRF vrf-target target:64730:112 set routing-instances Tenant2_VRF vrf-table-label set routing-options router-id 10.80.224.138 set routing-options autonomous-system 64730 set routing-options forwarding-table export ECMP-POLICY set routing-options forwarding-table ecmp-fast-reroute set routing-options forwarding-table chained-composite-next-hop ingress evpn set protocols bgp group EVPN_FABRIC type internal set protocols bgp group EVPN_FABRIC description "Connection to EVPN Fabric RRs (tenants.bgp_reflector)" set protocols bgp group EVPN_FABRIC local-address 10.80.224.138 set protocols bgp group EVPN_FABRIC family evpn signaling set protocols bgp group EVPN_FABRIC local-as 64730 set protocols bgp group EVPN_FABRIC multipath set protocols bgp group EVPN_FABRIC neighbor 10.80.224.149 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.150 set protocols bgp group UNDERLAY type external set protocols bgp group UNDERLAY description "Connection to EBGP UNDERLAY" set protocols bgp group UNDERLAY family inet unicast set protocols bgp group UNDERLAY export FROM_Lo0 set protocols bgp group UNDERLAY export FROM_UNDERLAY_BGP set protocols bgp group UNDERLAY local-as 65009 set protocols bgp group UNDERLAY multipath multiple-as set protocols bgp group UNDERLAY bfd-liveness-detection minimum-interval 350 set protocols bgp group UNDERLAY bfd-liveness-detection multiplier 3 set protocols bgp group UNDERLAY neighbor 10.80.224.30 peer-as 10021 set protocols bgp group UNDERLAY neighbor 10.80.224.32 peer-as 10022 set protocols bgp hold-time 10 set protocols bgp log-updown set protocols l2-learning global-mac-table-aging-time 600 set protocols l2-learning global-mac-ip-table-aging-time 300 set protocols lldp port-id-subtype interface-name set protocols lldp interface all set protocols lldp-med interface all set protocols igmp-snooping vlan default set vlans V991 vlan-id 991 set vlans V991 l3-interface irb.991 set vlans V992 vlan-id 992 set vlans V992 l3-interface irb.992
Configuration for Service Leaf-2
set system host-name ServiceLeaf2 set chassis fpc 0 pic 0 port 4 channel-speed 10g set interfaces et-0/0/0 mtu 9200 set interfaces et-0/0/0 unit 0 family inet address 10.80.224.11/31 set interfaces et-0/0/1 mtu 9200 set interfaces et-0/0/1 unit 0 family inet address 10.80.224.1/31 set interfaces xe-0/0/4:0 description "SRX Firewall-1: xe-0/0/5" set interfaces xe-0/0/4:0 mtu 9192 set interfaces xe-0/0/4:0 unit 0 family ethernet-switching interface-mode trunk set interfaces xe-0/0/4:0 unit 0 family ethernet-switching vlan members V991 set interfaces xe-0/0/4:0 unit 0 family ethernet-switching vlan members V992 set interfaces irb unit 991 family inet address 10.81.91.6/24 set interfaces irb unit 992 family inet address 10.81.92.6/24 set interfaces lo0 unit 0 description "** qfx10k-svador" set interfaces lo0 unit 0 family inet address 10.80.224.139/32 set interfaces lo0 unit 110 family inet address 192.168.110.254/32 set interfaces lo0 unit 110 family inet6 address 2001:db8::192:168:110:254/128 set interfaces lo0 unit 112 family inet address 192.168.112.254/32 set interfaces lo0 unit 112 family inet6 address 2001:db8::192:168:112:254/128 set interfaces lo0 unit 991 family inet address 192.168.91.254/32 set interfaces lo0 unit 992 family inet address 192.168.92.254/32 set forwarding-options storm-control-profiles default all set policy-options policy-statement ECMP-POLICY then load-balance per-packet set policy-options policy-statement FROM_Lo0 term 10 from interface lo0.0 set policy-options policy-statement FROM_Lo0 term 10 then accept set policy-options policy-statement FROM_Lo0 term 20 then reject set policy-options policy-statement FROM_UNDERLAY_BGP term 10 from protocol bgp set policy-options policy-statement FROM_UNDERLAY_BGP term 10 then accept set policy-options policy-statement FW1_Export from protocol evpn set policy-options policy-statement FW1_Export then accept set policy-options policy-statement T5_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_EXPORT term fm_direct then accept set policy-options policy-statement T5_EXPORT term fm_static from protocol static set policy-options policy-statement T5_EXPORT term fm_static then accept set policy-options policy-statement T5_EXPORT term fm_v4_host from protocol evpn set policy-options policy-statement T5_EXPORT term fm_v4_host from route-filter 0.0.0.0/0 prefix-length-range /32-/32 set policy-options policy-statement T5_EXPORT term fm_v4_host then accept set policy-options policy-statement T5_EXPORT term fm_v6_host from protocol evpn set policy-options policy-statement T5_EXPORT term fm_v6_host from route-filter 0::0/0 prefix-length-range /128-/128 set policy-options policy-statement T5_EXPORT term fm_v6_host then accept set policy-options policy-statement T5_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_EXPORT term Default_Route then accept set policy-options policy-statement T5_EXPORT term Default_Route_v6 from route-filter ::/0 exact set policy-options policy-statement T5_EXPORT term Default_Route_v6 then accept set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_INSPECT_EXPORT term fm_direct then accept set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_INSPECT_EXPORT term Default_Route then accept set policy-options policy-statement T5_SECURE_EXPORT term fm_direct from protocol direct set policy-options policy-statement T5_SECURE_EXPORT term fm_direct then accept set policy-options policy-statement T5_SECURE_EXPORT term Default_Route from route-filter 0.0.0.0/0 exact set policy-options policy-statement T5_SECURE_EXPORT term Default_Route then accept set routing-instances INSPECT_VRF routing-options multipath set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes vni 9991 set routing-instances INSPECT_VRF protocols evpn ip-prefix-routes export T5_INSPECT_EXPORT set routing-instances INSPECT_VRF protocols bgp group Firewall-1 type external set routing-instances INSPECT_VRF protocols bgp group Firewall-1 export FW1_Export set routing-instances INSPECT_VRF protocols bgp group Firewall-1 local-as 64730 set routing-instances INSPECT_VRF protocols bgp group Firewall-1 neighbor 10.81.91.5 peer-as 64777 set routing-instances INSPECT_VRF description "VRF for Firewall-1" set routing-instances INSPECT_VRF instance-type vrf set routing-instances INSPECT_VRF interface irb.991 set routing-instances INSPECT_VRF interface lo0.991 set routing-instances INSPECT_VRF route-distinguisher 10.80.224.139:9991 set routing-instances INSPECT_VRF vrf-target target:64730:991 set routing-instances INSPECT_VRF vrf-table-label set routing-instances SECURE_VRF routing-options multipath set routing-instances SECURE_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances SECURE_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances SECURE_VRF protocols evpn ip-prefix-routes vni 9992 set routing-instances SECURE_VRF protocols evpn ip-prefix-routes export T5_SECURE_EXPORT set routing-instances SECURE_VRF protocols bgp group Firewall-1 type external set routing-instances SECURE_VRF protocols bgp group Firewall-1 export FW1_Export set routing-instances SECURE_VRF protocols bgp group Firewall-1 local-as 64730 set routing-instances SECURE_VRF protocols bgp group Firewall-1 neighbor 10.81.92.5 peer-as 64777 set routing-instances SECURE_VRF description "VRF for SECURED FIREWALL TRAFFIC" set routing-instances SECURE_VRF instance-type vrf set routing-instances SECURE_VRF interface irb.992 set routing-instances SECURE_VRF interface lo0.992 set routing-instances SECURE_VRF route-distinguisher 10.80.224.139:9992 set routing-instances SECURE_VRF vrf-target target:64730:992 set routing-instances SECURE_VRF vrf-table-label set routing-instances Tenant1_VRF routing-options multipath set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes vni 9110 set routing-instances Tenant1_VRF protocols evpn ip-prefix-routes export T5_EXPORT set routing-instances Tenant1_VRF instance-type vrf set routing-instances Tenant1_VRF interface xe-0/0/28:0.110 set routing-instances Tenant1_VRF interface xe-0/0/28:1.110 set routing-instances Tenant1_VRF interface xe-0/0/39:0.0 set routing-instances Tenant1_VRF interface lo0.110 set routing-instances Tenant1_VRF route-distinguisher 10.80.224.139:9110 set routing-instances Tenant1_VRF vrf-target target:64730:110 set routing-instances Tenant1_VRF vrf-table-label set routing-instances Tenant2_VRF routing-options multipath set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes advertise direct-nexthop set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes encapsulation vxlan set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes vni 9112 set routing-instances Tenant2_VRF protocols evpn ip-prefix-routes export T5_EXPORT set routing-instances Tenant2_VRF instance-type vrf set routing-instances Tenant2_VRF interface xe-0/0/28:0.112 set routing-instances Tenant2_VRF interface xe-0/0/28:1.112 set routing-instances Tenant2_VRF interface lo0.112 set routing-instances Tenant2_VRF route-distinguisher 10.80.224.139:9112 set routing-instances Tenant2_VRF vrf-target target:64730:112 set routing-instances Tenant2_VRF vrf-table-label set routing-options router-id 10.80.224.139 set routing-options autonomous-system 64730 set routing-options forwarding-table export ECMP-POLICY set routing-options forwarding-table ecmp-fast-reroute set routing-options forwarding-table chained-composite-next-hop ingress evpn set protocols bgp group EVPN_FABRIC type internal set protocols bgp group EVPN_FABRIC description "Connection to EVPN Fabric RRs (tenants.bgp_reflector)" set protocols bgp group EVPN_FABRIC local-address 10.80.224.139 set protocols bgp group EVPN_FABRIC family evpn signaling set protocols bgp group EVPN_FABRIC local-as 64730 set protocols bgp group EVPN_FABRIC multipath set protocols bgp group EVPN_FABRIC neighbor 10.80.224.149 set protocols bgp group EVPN_FABRIC neighbor 10.80.224.150 set protocols bgp group UNDERLAY type external set protocols bgp group UNDERLAY description "Connection to EBGP UNDERLAY" set protocols bgp group UNDERLAY family inet unicast set protocols bgp group UNDERLAY export FROM_Lo0 set protocols bgp group UNDERLAY export FROM_UNDERLAY_BGP set protocols bgp group UNDERLAY local-as 65011 set protocols bgp group UNDERLAY multipath multiple-as set protocols bgp group UNDERLAY bfd-liveness-detection minimum-interval 350 set protocols bgp group UNDERLAY bfd-liveness-detection multiplier 3 set protocols bgp group UNDERLAY neighbor 10.80.224.0 peer-as 10021 set protocols bgp group UNDERLAY neighbor 10.80.224.10 peer-as 10022 set protocols bgp hold-time 10 set protocols bgp log-updown set protocols l2-learning global-mac-table-aging-time 600 set protocols l2-learning global-mac-ip-table-aging-time 300 set protocols lldp port-id-subtype interface-name set protocols lldp interface all set protocols lldp-med interface all set protocols igmp-snooping vlan default set vlans V991 vlan-id 991 set vlans V991 l3-interface irb.991 set vlans V992 vlan-id 992 set vlans V992 l3-interface irb.992
Configuration for Firewall
set system host-name firewall set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match source-address 10.1.110.11 set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match destination-address 10.1.111.21 set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match application junos-https set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match application junos-ssh set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match application junos-ping set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 match application junos-udp-any set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Allow_EP11_to_EP21 then permit set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Block_All match source-address any set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Block_All match destination-address any set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Block_All match application any set security policies from-zone INSPECT_Zone to-zone SECURE_Zone policy Block_All then deny set security policies from-zone SECURE_Zone to-zone INSPECT_Zone policy Allow_All match source-address any set security policies from-zone SECURE_Zone to-zone INSPECT_Zone policy Allow_All match destination-address any set security policies from-zone SECURE_Zone to-zone INSPECT_Zone policy Allow_All match application any set security policies from-zone SECURE_Zone to-zone INSPECT_Zone policy Allow_All then permit set security zones security-zone INSPECT_Zone address-book address 10.1.110.11 10.1.110.11/32 set security zones security-zone INSPECT_Zone address-book address EP11 10.1.110.11/32 set security zones security-zone INSPECT_Zone host-inbound-traffic system-services all set security zones security-zone INSPECT_Zone host-inbound-traffic protocols all set security zones security-zone INSPECT_Zone interfaces xe-0/0/4.991 set security zones security-zone INSPECT_Zone interfaces xe-0/0/5.991 set security zones security-zone SECURE_Zone address-book address 10.1.111.21 10.1.111.21/32 set security zones security-zone SECURE_Zone address-book address EP21 10.1.111.21/32 set security zones security-zone SECURE_Zone host-inbound-traffic system-services all set security zones security-zone SECURE_Zone host-inbound-traffic protocols all set security zones security-zone SECURE_Zone interfaces xe-0/0/4.992 set security zones security-zone SECURE_Zone interfaces xe-0/0/5.992 set interfaces xe-0/0/4 vlan-tagging set interfaces xe-0/0/4 unit 991 vlan-id 991 set interfaces xe-0/0/4 unit 991 family inet address 10.81.91.1/30 set interfaces xe-0/0/4 unit 992 vlan-id 992 set interfaces xe-0/0/4 unit 992 family inet address 10.81.92.1/30 set interfaces xe-0/0/5 vlan-tagging set interfaces xe-0/0/5 unit 991 vlan-id 991 set interfaces xe-0/0/5 unit 991 family inet address 10.81.91.5/30 set interfaces xe-0/0/5 unit 992 vlan-id 992 set interfaces xe-0/0/5 unit 992 family inet address 10.81.92.5/30 set policy-options policy-statement Export-Default-Route term 10 from route-filter 0.0.0.0/0 exact set policy-options policy-statement Export-Default-Route term 10 then accept set policy-options policy-statement Export-Default-Route term 100 then reject set protocols bgp group ServiceLeaf type external set protocols bgp group ServiceLeaf export Export-Default-Route set protocols bgp group ServiceLeaf local-as 64777 set protocols bgp group ServiceLeaf neighbor 10.81.91.2 peer-as 64730 set protocols bgp group ServiceLeaf neighbor 10.81.92.2 peer-as 64730 set protocols bgp group ServiceLeaf neighbor 10.81.91.6 peer-as 64730 set protocols bgp group ServiceLeaf neighbor 10.81.92.6 peer-as 64730
