Use Case
SUMMARY This Network Configuration Example (NCE) shows how you can use Filter Based Forwarding (FBF) to redirect network flows in an EVPN-VXLAN environment. For example, you may want to send the traffic through a security stack for advanced, on-demand security inspection, or you can use the method to perform load sharing for flows across a firewall.
Note that although this example is built on an EVPN-VXLAN fabric, in order to focus on the FBF, we do not go into the details of the fabric.
Overview
In secure data center deployments macro-segmentation is implemented by redirecting all Inter-VLAN traffic through a firewall. While this addresses the security requirements, it does introduce other shortcomings:
- The firewall needs to scale to handle all the inter-VLAN traffic,
- It can add latency to the inter-VLAN traffic,
- It requires that all inter-VLAN traffic be inspected, even for flows that don't require advanced security.
In contrast, the in-demand security inspection demonstrated in this NCE is designed so that only those flows (for example, macro-segmentations) that need advanced inspection are routed through the firewall – all other inter-VLAN traffic flows are handled in the fabric. There are several clear benefits to handling traffic in this way:
- You can target for inspection only those flows that need it, and you can enable or disable flows to the service as needed,
- Since only flows targeted for advanced inspection are routed through the firewall, the resource is used more efficiently,
- Flows that don't need advanced security are not subjected to added latency.
Inter-VLAN FBF lets you control the next-hop selection for flows by defining layer-3 input packet filters, which examine the packet header and chose the filter action on the basis of a routing-instance. Packets that pass through the filter are compared against a set of rules to classify them and determine membership in a set. Classified packets are forwarded to a routing table that you specify in the filter action, which then forwards them to the next hop as defined for the destination address entry. The filter itself is applied on the same layer-3 IRB interface as the VXLAN routing.
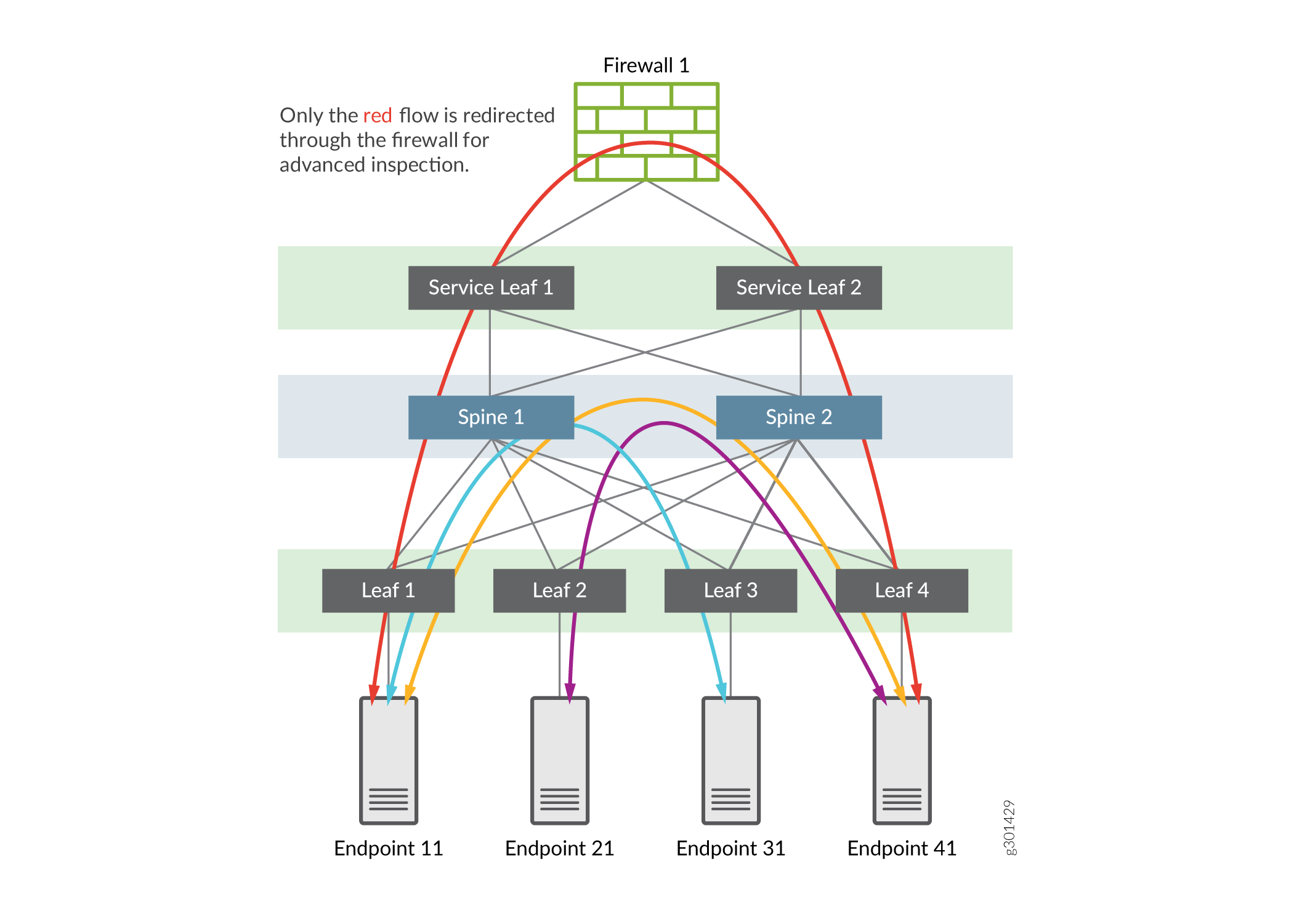
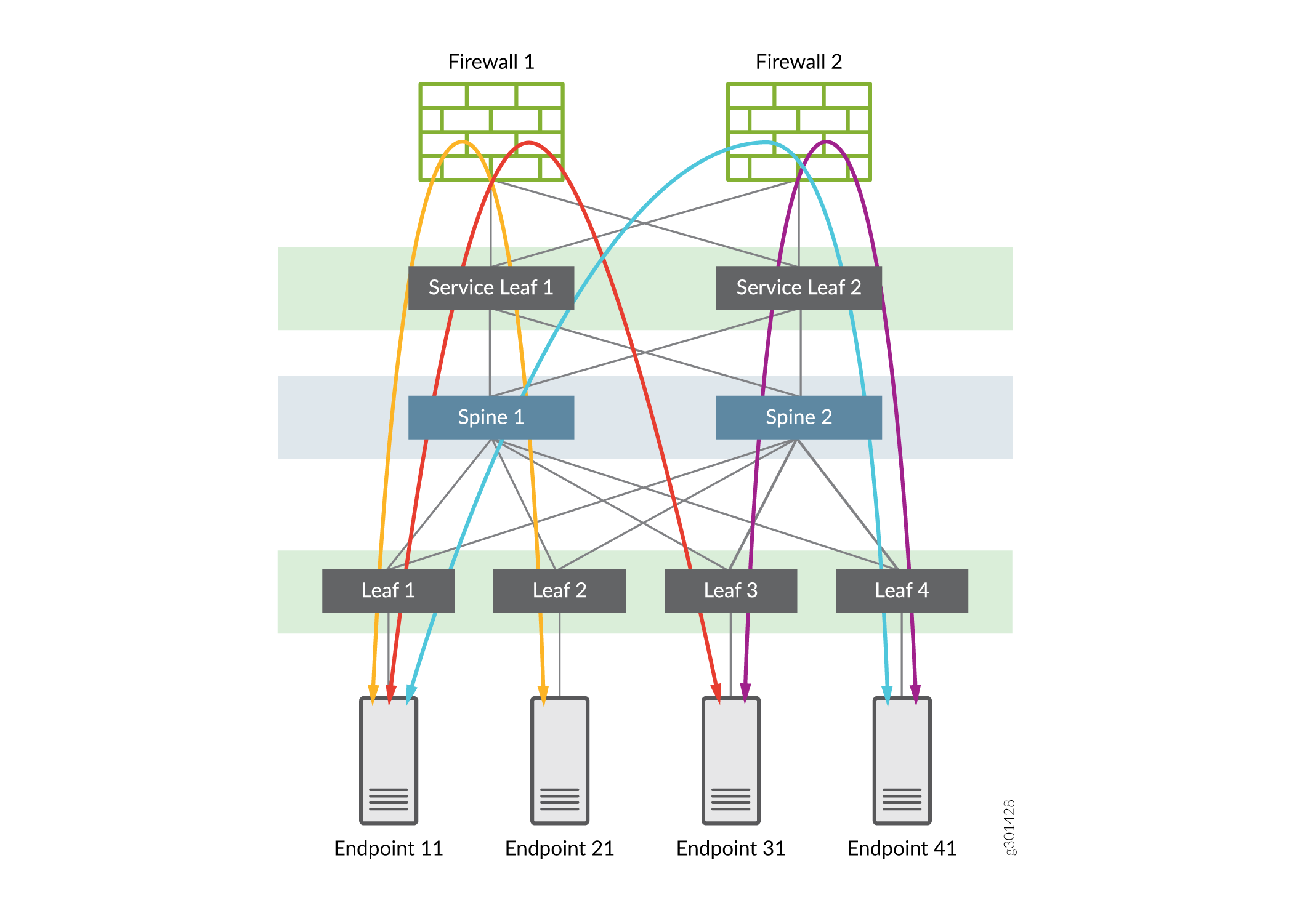
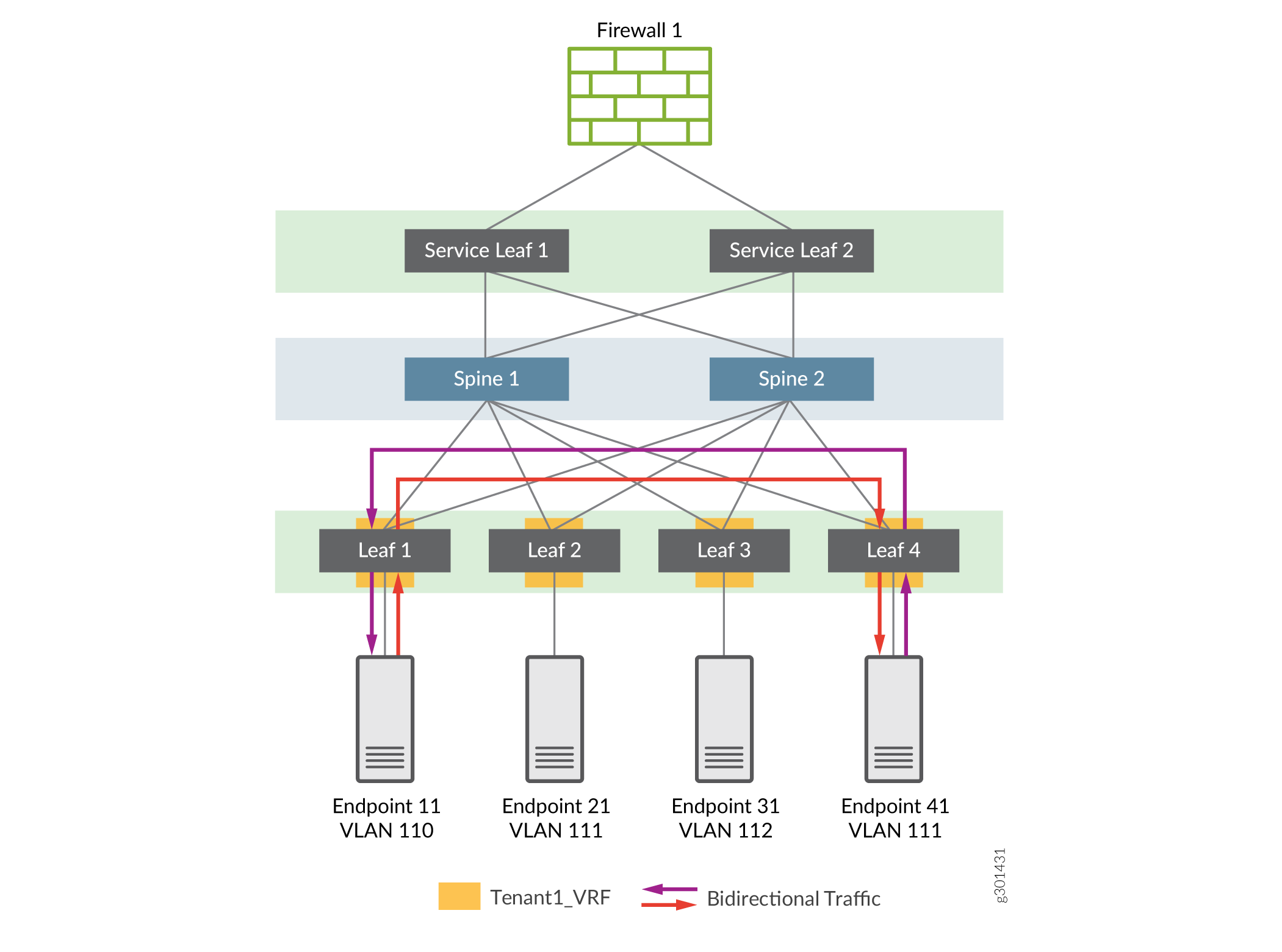
Normal traffic flows for Intra-VRF Inter-VLAN traffic
The path for Inter-VLAN traffic in Tenant1_VRF that does not require advanced security and so does not go through the firewall. The traffic flow is between Endpoint 11 and Endpoint 41, which belong to different VLANs that are part of the same routing instance, such as Tenant1_VRF. Type-5 host routes provide the symmetric IRB Inter-VLAN routing between these endpoints.
For the illustration, assume the following:
- VLANs 110 and 111 are part of Tenant1_VRF
- VLAN 112 is part of Tenant2_VRF
The endpoint to VLAN mappings are as follows:
- Endpoint 11 to VLAN 110
- Endpoint 21 to VLAN 111
- Endpoint 31 to VLAN 112
- Endpoint 41 to VLAN 111
The traffic flows between endpoints are as follows:
- Traffic from Endpoint 11 to Endpoint 41 does not require security inspection
- Traffic from Endpoint 21 to Endpoint 41 does not require security inspection
- You want to inspect traffic from Endpoint 11 to Endpoint 21 (so this traffic must be routed through the firewall)
- Traffic between Endpoints in Tenant1_VRF and Tenant2_VRF follow the traditional Inter-VRF macro-segmentation model, that is, all Inter-VRF traffic is routed through the firewall
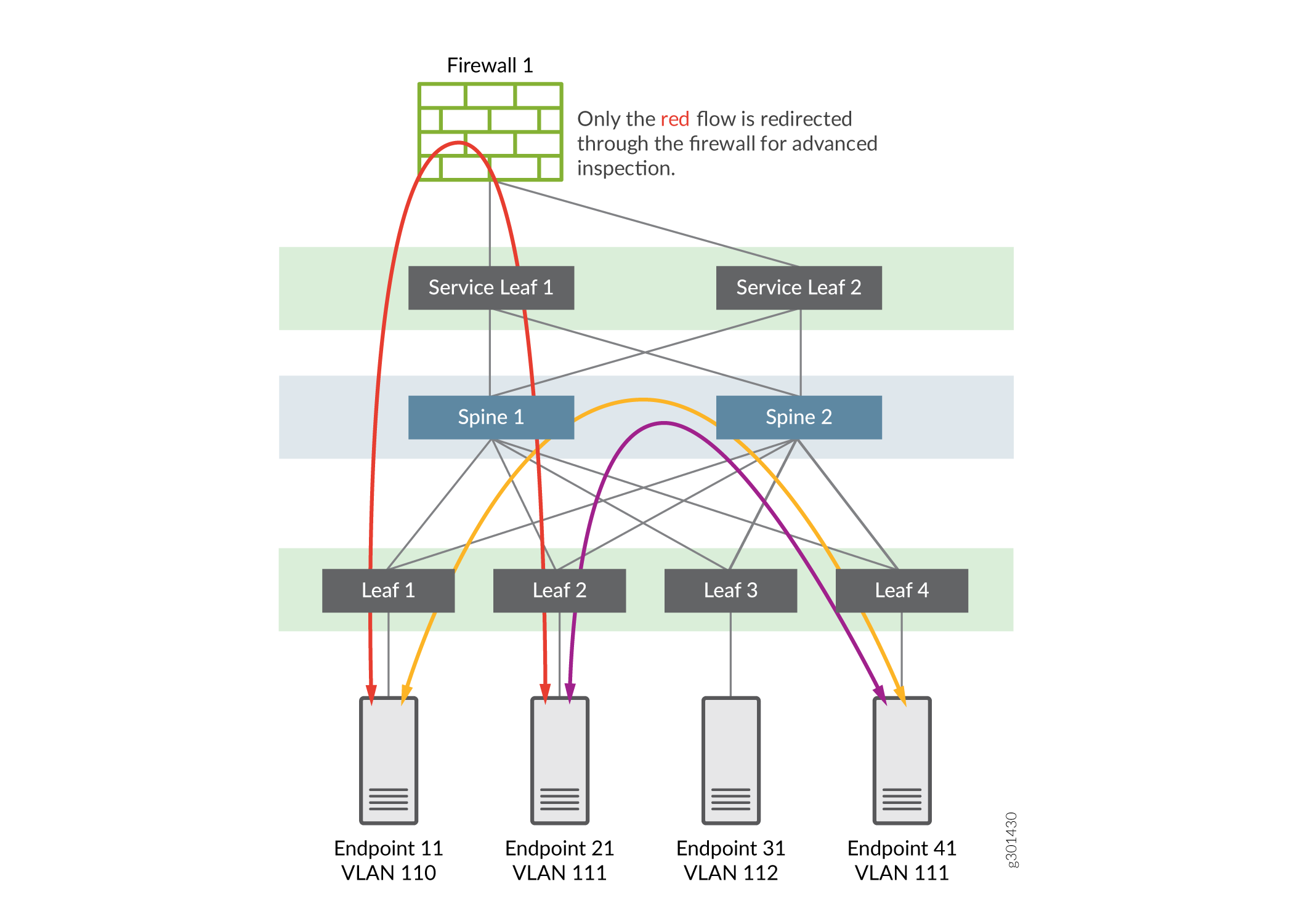
Inspected traffic flow for Intra-VRF Inter-VLAN traffic
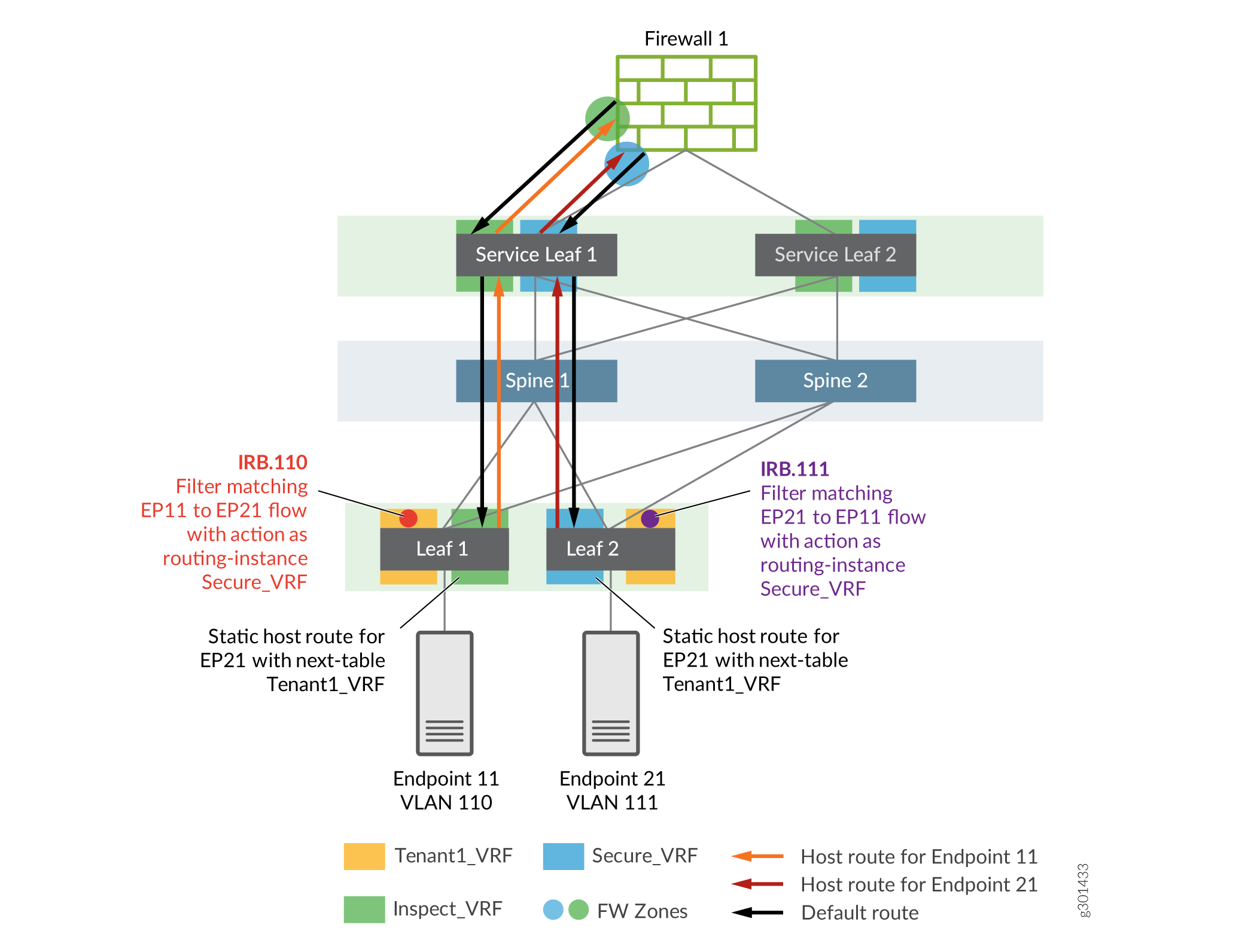
The figure below shows the topology used in this NCE. The scenario is that Endpoint 21 is a server on which sensitive information is stored, and to which Endpoint 11 connects. The network administrator wants to secure access to the server and has set up advanced security inspection on the traffic passing to the server from Endpoint 11.
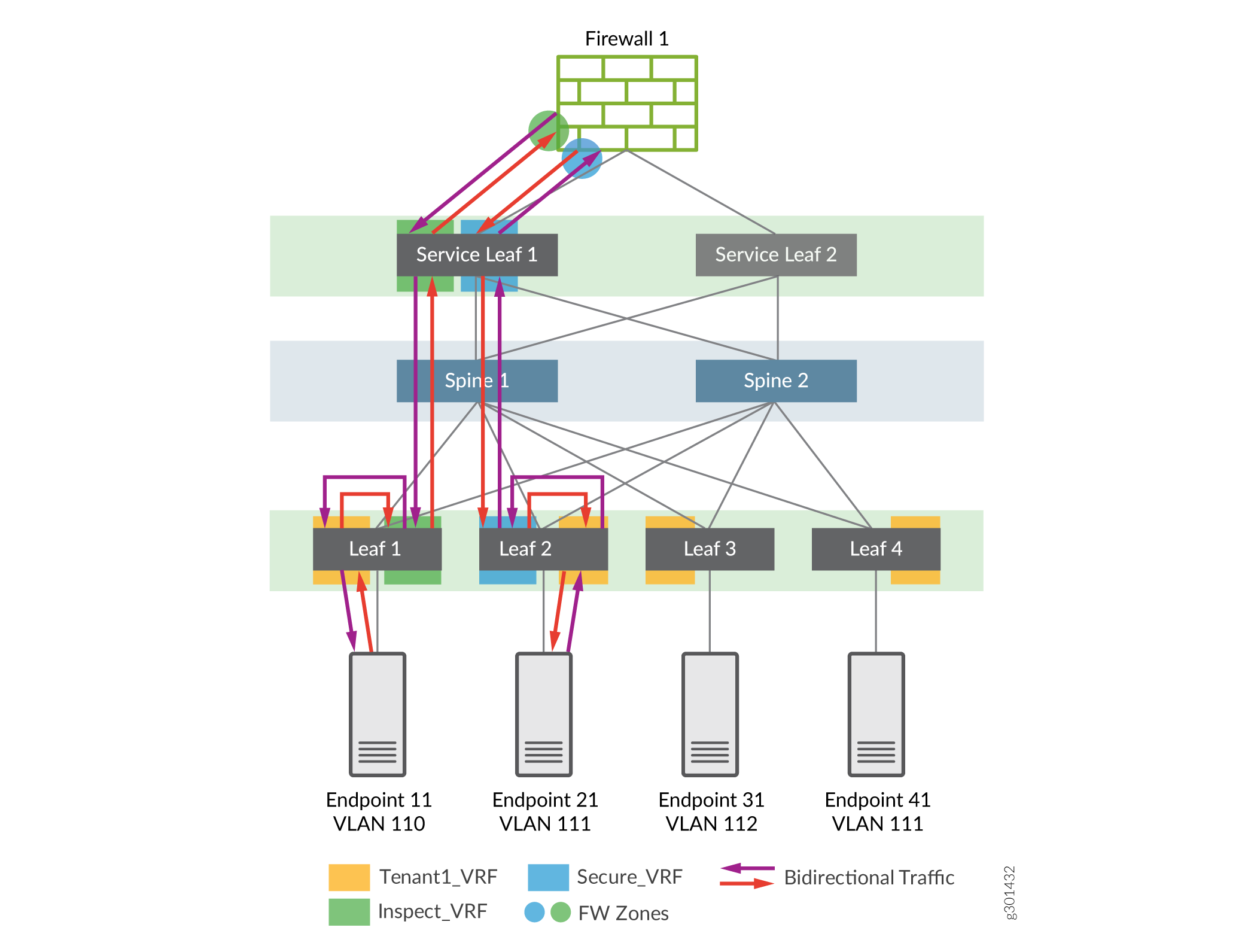
A virtual routing and forwarding (VRF) instance, called Tenant1_VRF is set up with two VLANs, VLAN 110 and VLAN 111. Endpoint 11 is part of VLAN 110. Endpoint 21 is part of VLAN 111.
Traffic between the endpoints is bidirectional and the firewall is stateful. Therefore, routing on the network must be (and is) symmetric. We create two new VRFs for this purpose:
- INSPECT_VRF
- We use the INSPECT VRF to route uninspected traffic from Endpoint 11 to Endpoint 21 through the firewall. Likewise, the firewall also places traffic returning from Endpoint 21 to Endpoint 11 in this VRF
- To redirect matching traffic to INSPECT VRF, the firewall filter is applied to the IRB.110 interface on the Leaf-1
- The firewall advertises a default route into INSPECT VRF
- Leaf-1 advertises a host route for Endpoint 11 towards the firewall
- SECURE_VRF
- We use SECURE VRF to carry inspected traffic from the firewall to Endpoint 21. Return traffic from Endpoint 21 is routed back through SECURE VRF towards the firewall
- A firewall filter applied to the IRB.111 interface on Leaf-2 redirects matching traffic to SECURE VRF
- The firewall advertises a default route into SECURE VRF
- Leaf-2 advertises a host route for Endpoint 21 towards the firewall