Technical Overview
This section shows how the Juniper Connected Security building blocks work together to provide a comprehensive security solution for your enterprise.
Components of Juniper Connected Security Solution
Figure 1 shows a high-level workflow of how Policy Enforcer, Security Director, Juniper Networks® Advanced Threat Prevention Cloud (ATP Cloud), and Junos devices interact to provide a secure network deployment with Juniper Connected Security.
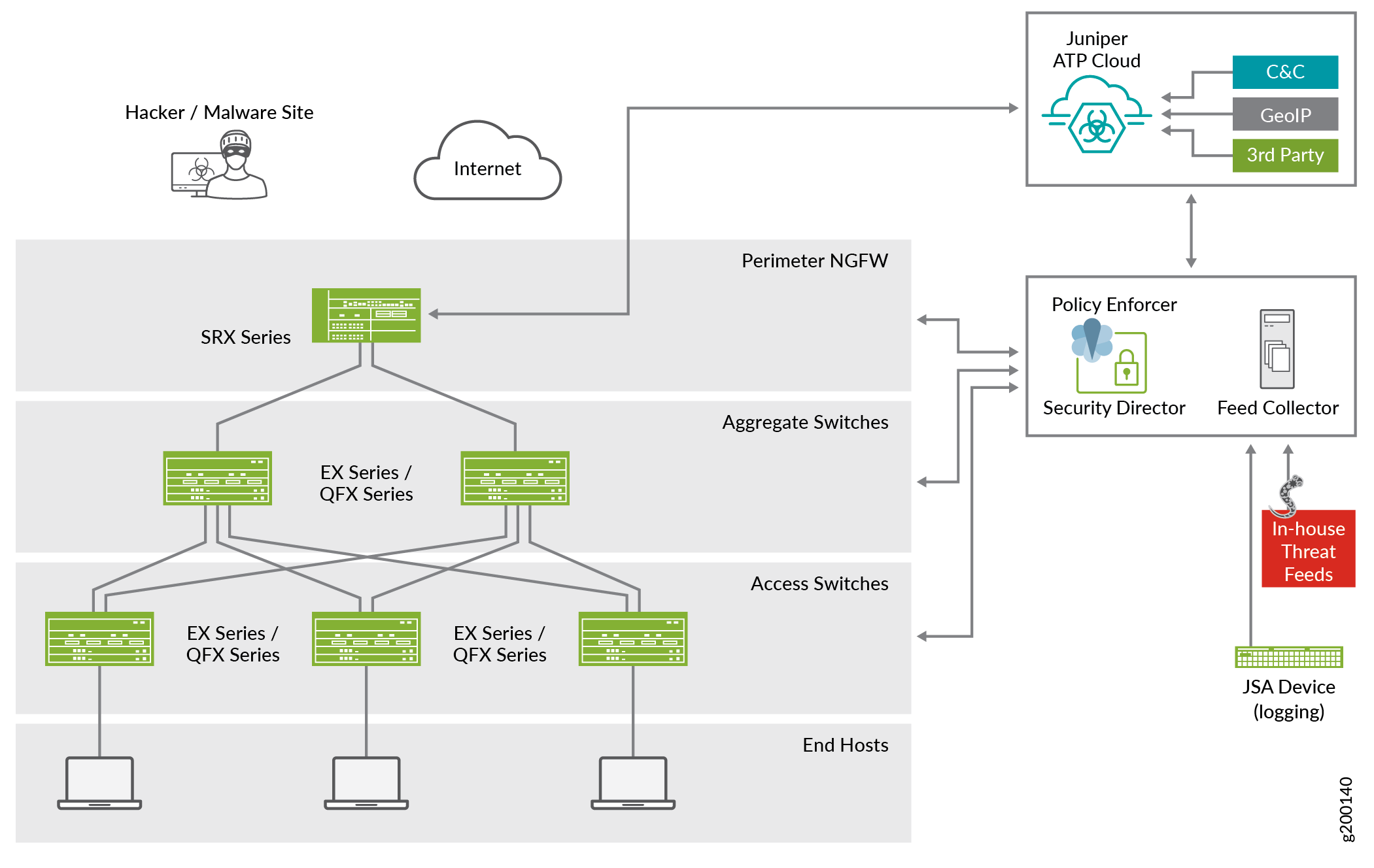
EX Series switches deliver switching services in branch, campus, and data center networks. QFX Series switches are high-performance, low-latency, edge devices optimized for data center environments.
In the Juniper Connected Security solution, clients/endpoints are connected to EX Series and QFX Series switches with endpoint protection software. These switches provide access security and control.
SRX Series Services gateways provide security enforcement and deep inspection across all network layers and applications.
In the context of the Juniper Connected Security solution, SRX Series devices are deployed as perimeter firewalls connected to Juniper ATP Cloud for anti-malware services.
Juniper ATP Cloud identifies varying levels of risk, and provides a higher degree of accuracy in threat protection. It integrates with SRX Series gateways to deliver deep inspection, inline malware blocking, and actionable reporting.
Policy Enforcer uses information gathered and reported by Juniper ATP Cloud to learn about the threats and rapidly respond to new threat conditions. With this information, Policy Enforcer can automatically update policies and deploy new enforcement to firewalls and switches, quarantining and tracking infected hosts to stop the progress of threats.
Policy Enforcer identifies an infected host by its IP and MAC address, allowing tracking and continued blocking of the host even if it moves to another switch or access point on the network.
With these components working together, threats are detected more quickly by leveraging threat intelligence from multiple sources (including third-party feeds). Network security can adapt dynamically to real-time threat information so that security policies are enforced consistently.
Juniper Connected Security Workflow Overview
The following examples provide a high-level workflow of how Juniper Connected Security components work together to detect and block an infected endpoint, track the infected endpoint, and automatically quarantine it or block it from accessing the Internet.
Infected Host Detection and Tracking
Let’s take a look at a typical enterprise with clients, endpoints, access switches, and wireless access points. When a client becomes compromised because of contact with an endpoint outside the corporate network, it becomes a threat to other hosts in the network. You must be able to control the infected host to ensure the problem doesn’t spread.
Figure 2 shows an infected host tracking workflow.
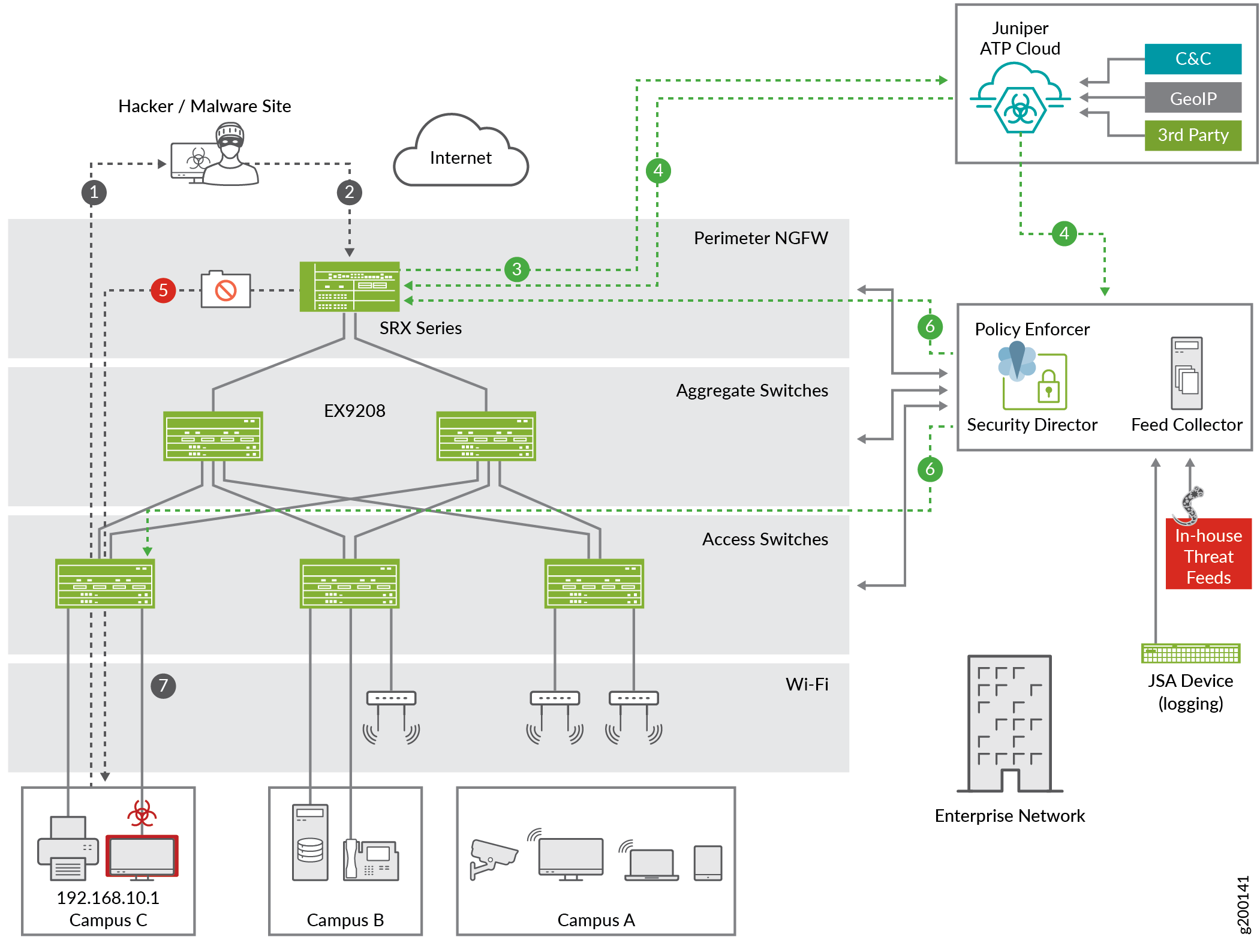
This scenario involves the following steps:
A user (192.168.10.1) in Campus C connects to a site on the Internet and downloads a file.
The file is scanned at the perimeter firewall (SRX Series device).
Based on user-defined policies, the firewall sends the file to an anti-malware service (Juniper ATP Cloud) for analysis.
Juniper ATP Cloud detects that the file contains malware, identifies 192.168.10.1 as an infected host, and notifies the SRX device and Policy Enforcer.
The firewall blocks the file, preventing it from being downloaded.
Policy Enforcer identifies the IP address and MAC address of the host that downloaded the file and pushes a security policy onto the firewalls, and firewall filters onto the switches, to prevent further threats.
The infected endpoint, connected to EX Series switch in Campus C, is quarantined.
The movement of infected endpoints and the resulting change in network IP addresses can easily evade security in perimeter-only protection architectures.
As the scenario continues, the infected host moves to a different location (Campus B) and receives a new IP address, as shown in Figure 3.
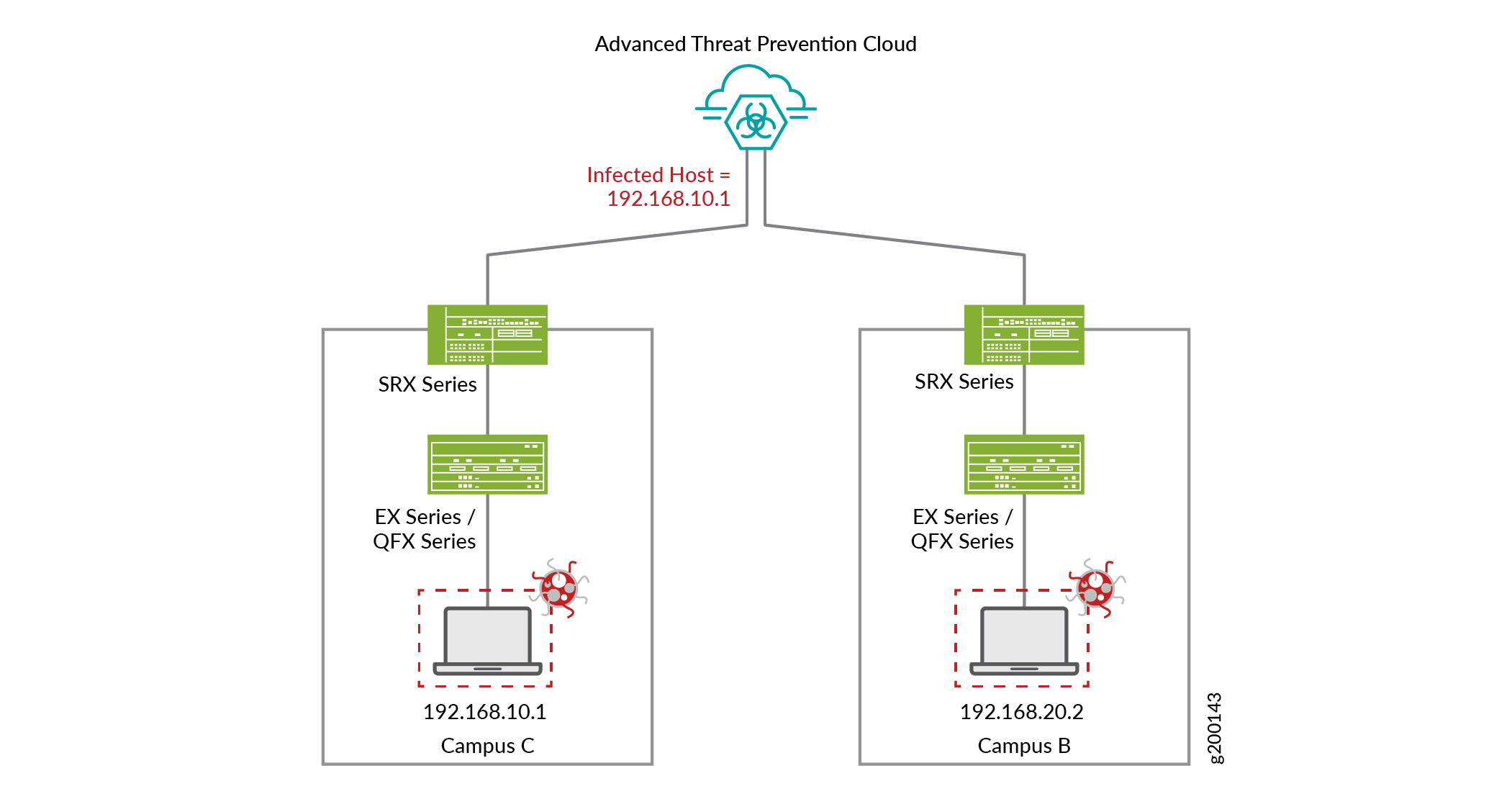
Policy Enforcer keeps track of infected host movement and informs Juniper ATP Cloud of the new MAC address-to-IP address binding. When the infected host moves to its new location (in Campus B), Policy Enforcer recognizes the host as a continuing threat and blocks it from the network.
Protection from Botnet C&C Attacks
When a host on the network tries to initiate contact with a possible command and control (C&C) server on the Internet, the SRX Series device can work with Juniper ATP Cloud, Security Director, and Policy Enforcer to intercept the traffic and perform an enforcement action based on real-time intelligence feed information that identifies the C&C server IP address and URL.
Figure 4 shows an example of how the Juniper Connected Security solution provides protection from botnet C&C attacks.
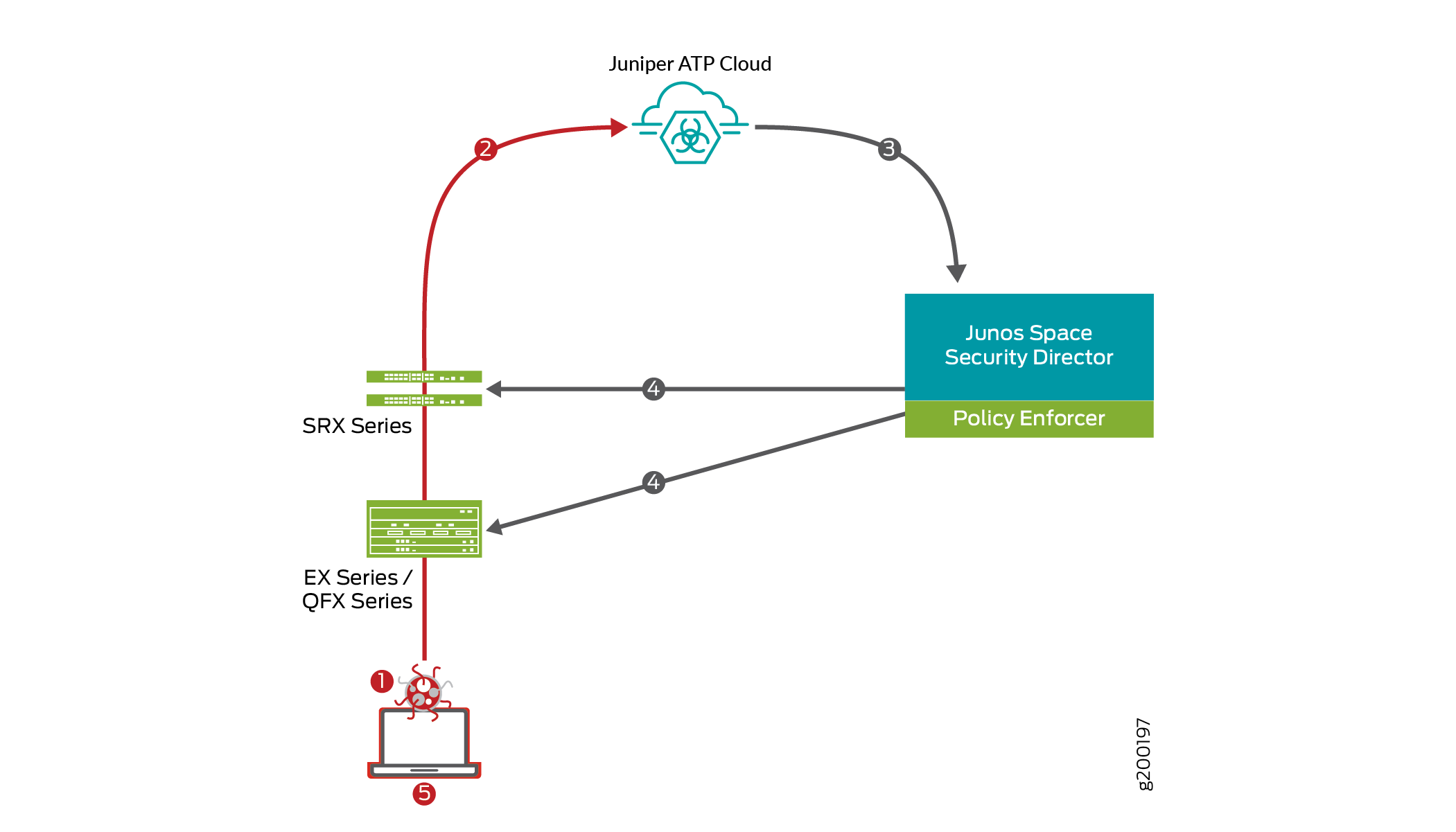
This scenario involves the following steps:
A user downloads a file from the Internet.
The SRX Series device receives the downloaded file and checks its security profile to see if any additional action must be performed. If required, it sends file to Juniper ATP Cloud for malware inspection.
The inspection determines this file is malware and informs Policy Enforcer of the results.
An enforcement policy is automatically deployed to the SRX device and EX/QFX switches.
The infected endpoint is quarantined.
