Example: Configuring Central Web Authentication with EX Series Switches and Aruba ClearPass
This configuration example illustrates how to use EX Series switches and Aruba ClearPass to implement central Web authentication of guest users. Specifically, it illustrates how to use the following EX Series switch features in conjunction with Aruba ClearPass:
The built-in firewall filter JNPR_RSVD_FILTER_CWA, which allows a guest endpoint that has not yet been authenticated to access the services required for central Web authentication while blocking access to the rest of the network.
The Juniper-CWA-Redirect-URL RADIUS VSA, which allows Aruba ClearPass to pass the redirect URL to the switch as part of the authentication process.
RADIUS CoA support, which allows an EX Series switch to dynamically change the firewall filter in effect for a guest endpoint after the endpoint is authenticated.
This topic covers:
Requirements
This example uses the following hardware and software components for the policy infrastructure:
An EX4300 switch running Junos OS Release 15.1R3 or later
An Aruba ClearPass Policy Manager platform running 6.3.3.63748 or later
Overview and Topology
This network configuration example uses the topology shown in Figure 1. A guest laptop connects to port ge-0/0/22 of an EX4300 switch. The Aruba ClearPass server provides both ClearPass Guest and ClearPass Policy Management services.
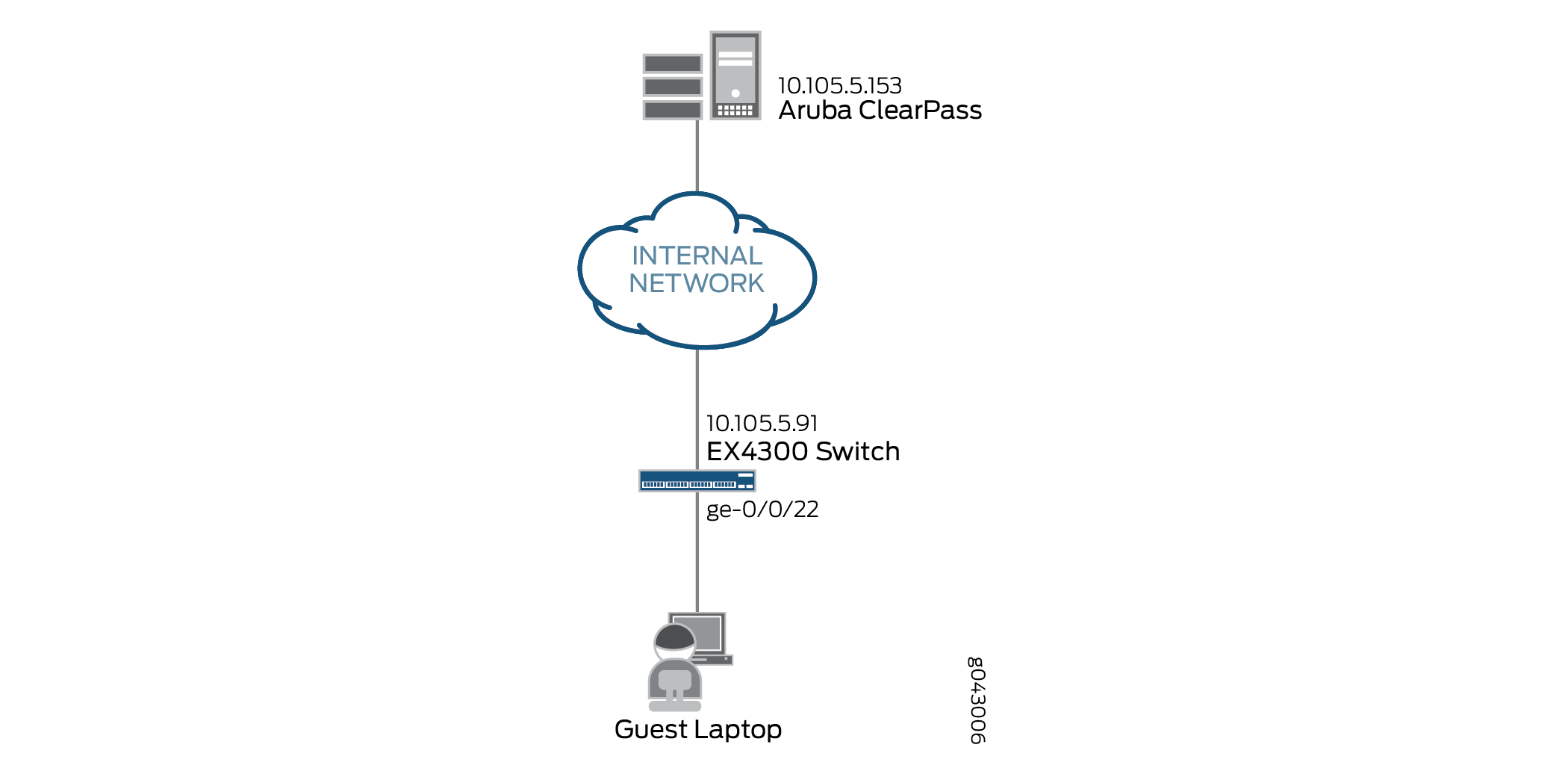
Both 802.1X and MAC RADIUS authentication are enabled on port ge-0/0/22. Because the guest laptop does not have a 802.1X client, the switch does not receive any EAPoL packets from the laptop and 802.1X authentication fails. The EX4300 switch automatically tries MAC RADIUS authentication next. A MAC RADIUS enforcement policy in Aruba ClearPass is configured to send a RADIUS access-accept message for unknown clients attempting MAC RADIUS authentication, along with the name of the JNPR_RSVD_FILTER_CWA built-in filter and the redirect URL for the Aruba ClearPass Guest login page.
When the guest user opens a browser and attempts to access a webpage, the EX4300 switch redirects the browser to the Aruba ClearPass Guest login page, where the guest enters the guest credentials. A Web authentication enforcement policy in Aruba ClearPass is configured to add the guest endpoint to the endpoint repository and to send a RADIUS CoA message to the switch. This message tells the switch to change the firewall filter associated with the endpoint to guest_access_policy_1, which is configured on the switch. This filter permits the guest to access everything except the internal network.
Configuration
This section provides step-by-step instructions for:
- Configuring the EX4300 Switch
- Configuring Aruba ClearPass Guest
- Configuring Aruba ClearPass Policy Manager
Configuring the EX4300 Switch
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them in a text file, remove any line breaks, change any details necessary to match your network configuration, copy and paste the commands into the CLI at the [edit] hierarchy level, and then enter commit from configuration mode.
[edit] set access radius-server 10.105.5.153 dynamic-request-port 3799 set access radius-server 10.105.5.153 secret password set access radius-server 10.105.5.153 source-address 10.105.5.91 set access profile CP-Test-Profile accounting-order radius set access profile CP-Test-Profile authentication-order radius set access profile CP-Test-Profile radius authentication-server 10.105.5.153 set access profile CP-Test-Profile radius accounting-server 10.105.5.153 set access profile CP-Test-Profile radius options nas-identifier 10.105.5.91 set system services web-management http set system services web-management https system-generated-certificate set protocols dot1x authenticator authentication-profile-name CP-Test-Profile set protocols dot1x authenticator interface ge-0/0/22.0 mac-radius set protocols dot1x authenticator interface ge-0/0/22.0 supplicant multiple set vlans v100 description "Quarantine VLAN" set vlans v100 vlan-id 100 set interfaces ge-0/0/22 unit 0 family ethernet-switching interface-mode access set interfaces ge-0/0/22 unit 0 family ethernet-switching vlan members v100 set firewall family ethernet-switching filter guest_access_policy_1 term Block_Internal from ip-destination-address 192.168.0.0/16 set firewall family ethernet-switching filter guest_access_policy_1 term Block_Internal then discard set firewall family ethernet-switching filter guest_access_policy_1 term Allow_All then accept
Step-by-Step Procedure
The general steps to configure the EX4300 switch are:
Configure the connection to the Aruba ClearPass Policy Manager.
Create the access profile used by the 802.1X protocol. The access profile tells the 802.1X protocol which authentication server to use and the authentication methods and order.
Enable HTTP and HTTPS services.
Configure the 802.1X protocol.
Configure the VLAN used by the guest endpoints.
Configure Ethernet switching on the access port.
Create the firewall policy that blocks access to the internal network.
To configure the EX4300 switch:
Provide the RADIUS server connection information.
[edit access] user@EX4300# set radius-server 10.105.5.153 dynamic-request-port 3799 user@EX4300# set radius-server 10.105.5.153 secret password user@EX4300# set radius-server 10.105.5.153 source-address 10.105.5.91
Configure the access profile.
[edit access] user@EX4300# set profile CP-Test-Profile accounting-order radius user@EX4300# set profile CP-Test-Profile authentication-order radius user@EX4300# set profile CP-Test-Profile radius authentication-server 10.105.5.153 user@EX4300# set profile CP-Test-Profile radius accounting-server 10.105.5.153 user@EX4300# set profile CP-Test-Profile radius options nas-identifier 10.105.5.91
Enable HTTP and HTTPS services. These services must be enabled for URL redirection.
[edit system services] user@EX4300# set system services web-management http user@EX4300# set system services web-management https system-generated-certificate
Configure the 802.1X protocol to use CP-Test-Profile, and enable the protocol on each access interface. In addition, configure the interfaces to support MAC RADIUS authentication and to allow more than one supplicant, each of which must be individually authenticated.
By default, the switch will first attempt 802.1X authentication. If it receives no EAP packets from the endpoint, indicating that the endpoint does not have an 802.1X supplicant, or if the 802.1X authentication fails, it then tries MAC RADIUS authentication.
[edit protocols] user@EX4300# set dot1x authenticator authentication-profile-name CP-Test-Profile user@EX4300# set dot1x authenticator interface ge-0/0/22.0 mac-radius user@EX4300# set dot1x authenticator interface ge-0/0/22.0 supplicant multiple
Configure the VLAN used in this example.
[edit vlans] user@EX4300# set v100 description "Quarantine VLAN" user@EX4300# set v100 vlan-id 100
Configure the access port.
The access port is configured to be in VLAN v100, the quarantine VLAN. This VLAN will be used by the endpoint if Aruba ClearPass does not send dynamic VLAN information when it authenticates the endpoint.
[edit interfaces] user@EX4300# set ge-0/0/22 unit 0 family ethernet-switching interface-mode access user@EX4300# set ge-0/0/22 unit 0 family ethernet-switching vlan members v100
Configure a firewall filter, guest_access_policy_1, to be used for the endpoint after the guest credentials have been authenticated by Aruba ClearPass Guest.
This filter blocks the endpoint from accessing the internal network (192.168.0.0/16), while permitting access to the Internet.
[edit firewall] user@EX4300# set family ethernet-switching filter guest_access_policy_1 term Block_Internal from ip-destination-address 192.168.0.0/16 user@EX4300# set family ethernet-switching filter guest_access_policy_1 term Block_Internal then discard user@EX4300# set family ethernet-switching filter guest_access_policy_1 term Allow_All then accept
Results
From configuration mode, confirm your configuration
by entering the following show commands.
user@EX4300# show access
radius-server {
10.105.5.153 {
dynamic-request-port 3799;
secret "$9$FYxf3A0Ehrv87yl7Vs4DjfTz3Ct0BIcre"; ## SECRET-DATA
source-address 10.105.5.91;
}
}
profile CP-Test-Profile {
accounting-order radius;
authentication-order radius;
radius {
authentication-server 10.105.5.153;
accounting-server 10.105.5.153;
options {
nas-identifier 10.105.5.91;
}
}
}
user@EX4300# show system services
web-management {
http;
https {
system-generated-certificate;
}
}
user@EX4300# show protocols
dot1x {
authenticator {
authentication-profile-name CP-Test-Profile;
interface {
ge-0/0/22.0 {
supplicant multiple;
mac-radius;
}
}
}
} user@EX4300# show interfaces
ge-0/0/22 {
unit 0 {
family ethernet-switching {
vlan {
members v100;
}
}
}
}
user@EX4300# show vlans
v100 {
description "Quarantine VLAN";
vlan-id 100;
}
user@EX4300# show firewall
family ethernet-switching {
filter guest_access_policy_1 {
term Block_Internal {
from {
ip-destination-address {
192.168.0.0/16;
}
}
then discard;
}
term Allow_All {
then accept;
}
}
}If you are done configuring the device, enter commit from configuration mode.
Configuring Aruba ClearPass Guest
Step-by-Step Procedure
The general steps for configuring Aruba ClearPass Guest are:
Set up the guest user account.
Configure the guest login page.
To configure Aruba ClearPass Guest:
Log in to ClearPass Guest. For example:
https://10.105.5.153/guest/
Set up the guest user account.
Step-by-Step Procedure
Click Create New Guest Account.
Provide the details for the guest user account, as shown below. Be sure to note the password, which is automatically generated.
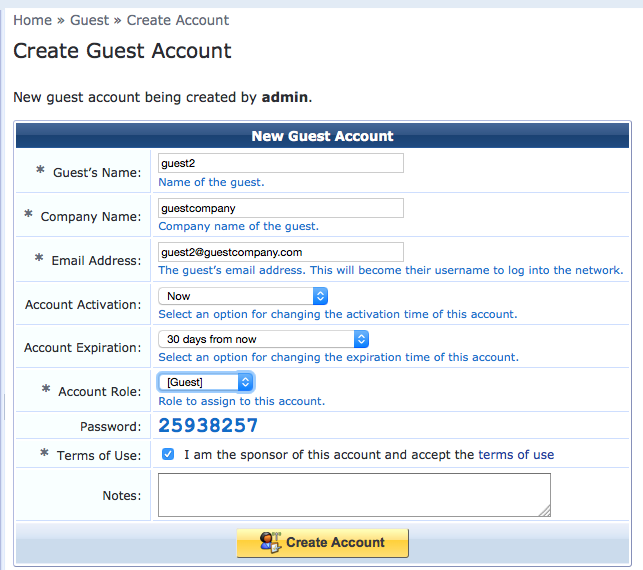
Click Create Account.
Configure the guest access login page.
Step-by-Step Procedure
Select Configuration > Web Logins.
Note:If you are using a recent version of Aruba ClearPass Guest, you might need to select Configuration > Pages > Web Logins.
In the Web Logins page, click Create a new web login page.
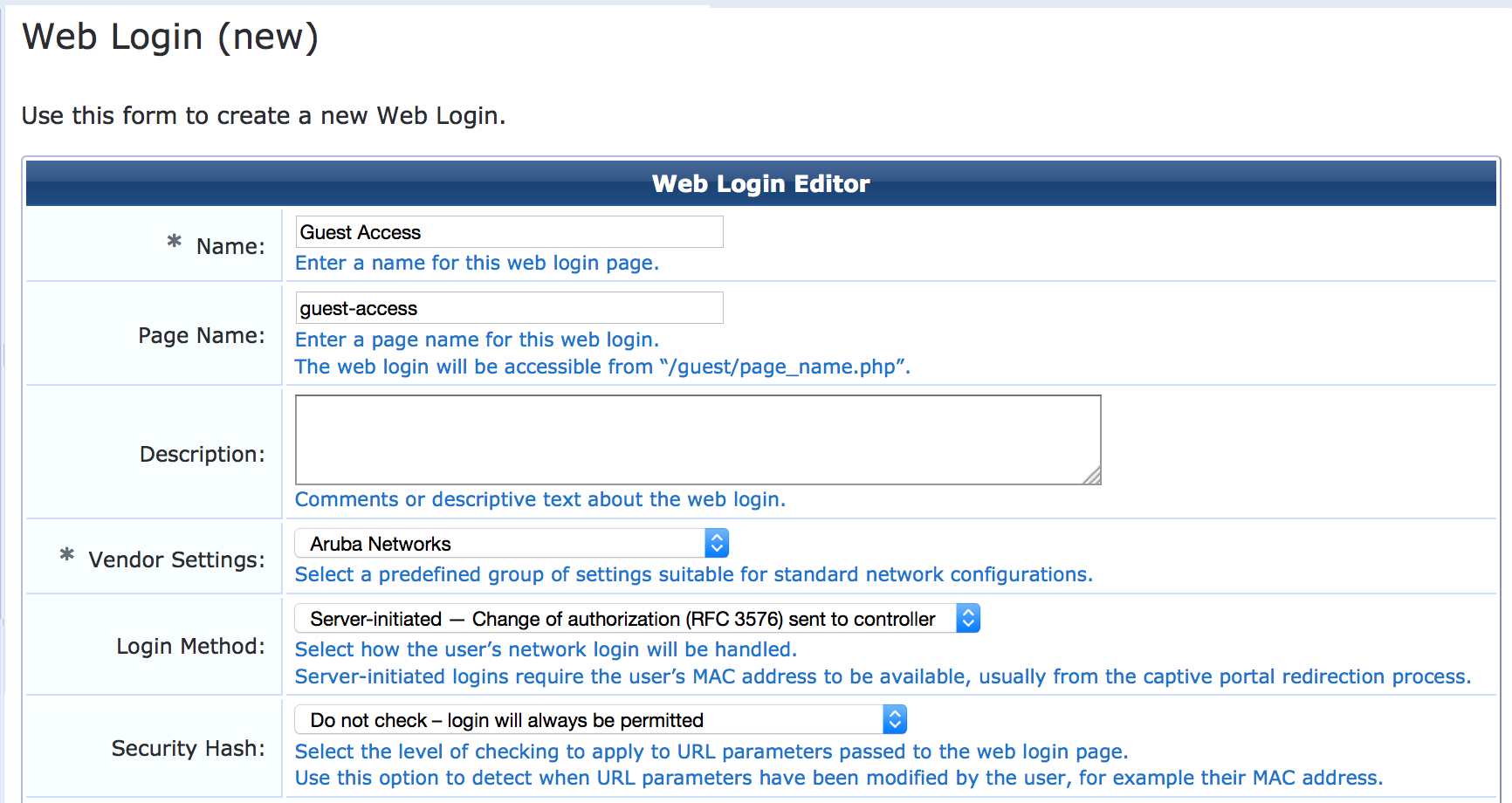
In the Web Login Editor, provide a name for Web login page you are creating, specify the login page name as it appears in the URL, and set Login Method to Server-Initiated – Change of authorization (RFC 3576) sent to controller.
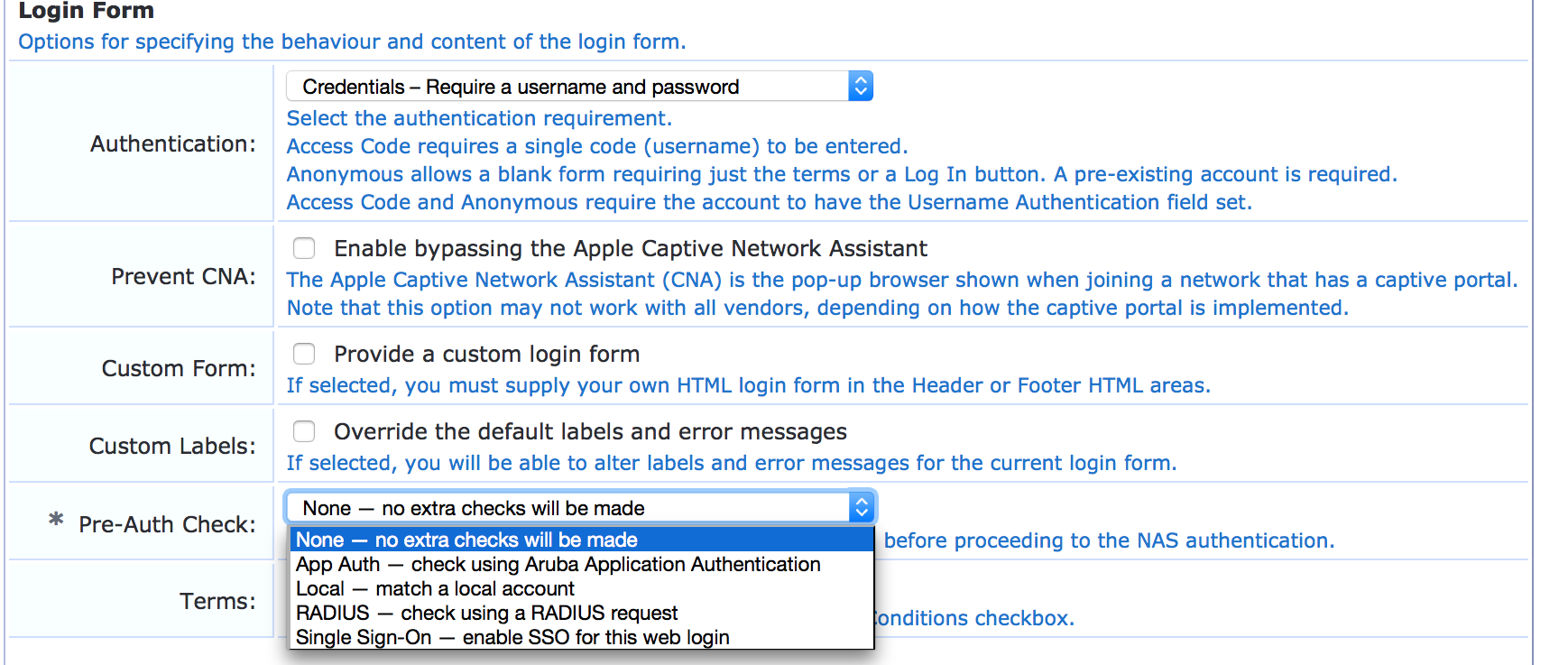
In the Login Form section of the Web Login page, set Pre-Auth Check to None – no extra checks will be made.
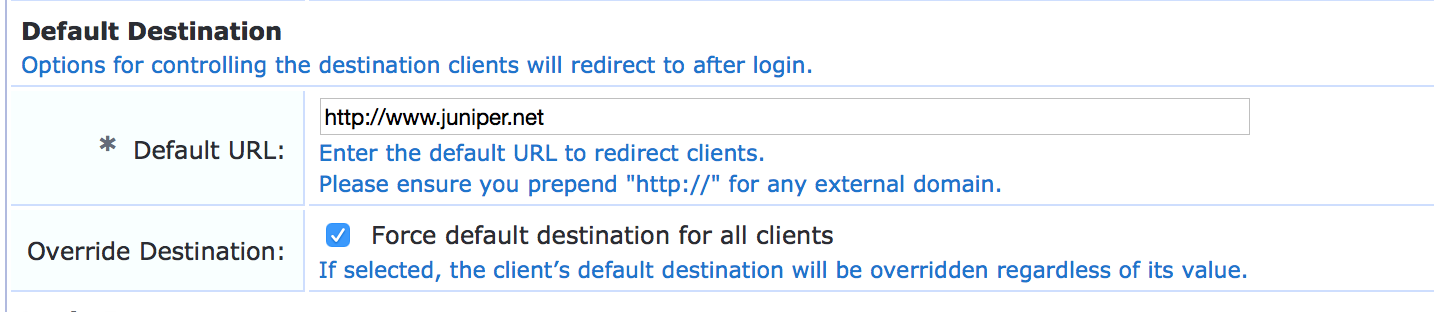
In the Default Destination section, enter a default URL to which the guest gets redirected after successful authentication. In this example, the guest is redirected to the Juniper Networks home page after authentication.
Configuring Aruba ClearPass Policy Manager
Step-by-Step Procedure
The general steps for configuring Aruba ClearPass are:
Modify the Juniper Networks RADIUS dictionary file so that it includes new Juniper Networks RADIUS attributes.
Add the EX4300 as a network device.
Create the following enforcement profiles:
A profile that is enforced after MAC RADIUS authentication.
A profile that is enforced after central Web authentication.
Create two enforcement policies:
A policy that is invoked when MAC RADIUS authentication is used.
A policy that is invoked when centeral Web authentication is used.
Define the MAC RADIUS authentication service and the Web authentication service.
To configure Aruba ClearPass:
Update the Juniper Networks RADIUS dictionary file.
A Juniper Network RADIUS dictionary file comes preinstalled on Aruba ClearPass. Junos OS Release 15.1R3 for EX Series switches adds support for three new Juniper Networks VSAs, which need to be added to the dictionary file.
Step-by-Step Procedure
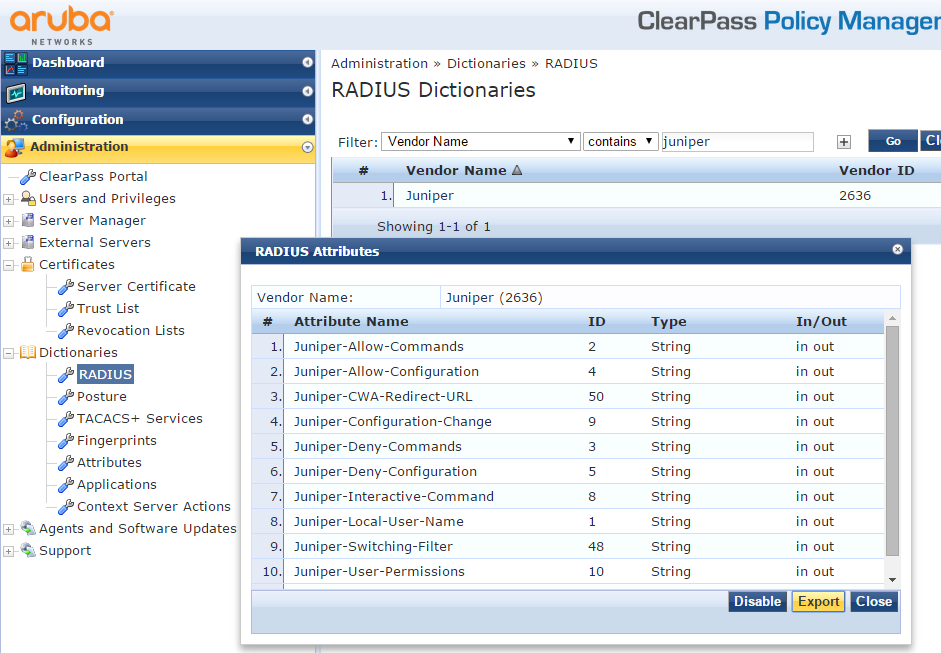
In Aruba ClearPass, navigate to Administration > Dictionaries > RADIUS.
In the RADIUS Dictionaries window, use the Filter field to search for Juniper under Vendor Name.
Click the Juniper dictionary name, and then click Export to save the RadiusDictionary.xml file to your desktop.
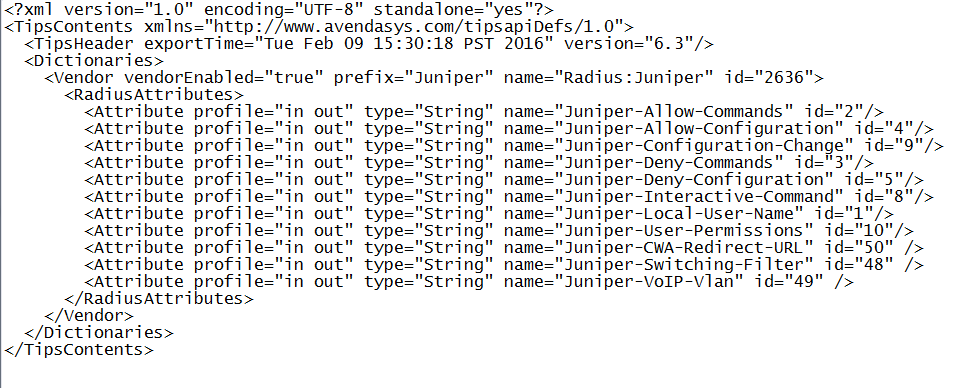
Copy the following three attributes, paste them into RadiusDictionary.xml, and save the file.
<Attribute profile="in out" type="String" name="Juniper-CWA-Redirect-URL" id="50" /> <Attribute profile="in out" type="String" name="Juniper-Switching-Filter" id="48" /> <Attribute profile="in out" type="String" name="Juniper-VoIP-Vlan" id="49" />
The dictionary file should look like this when you complete the paste:
Import the dictionary file into Aruba ClearPass by clicking
 in the RADIUS Dictionaries window and browsing
to the file.
in the RADIUS Dictionaries window and browsing
to the file.
After you have imported the file, the Juniper dictionary file should look like this:
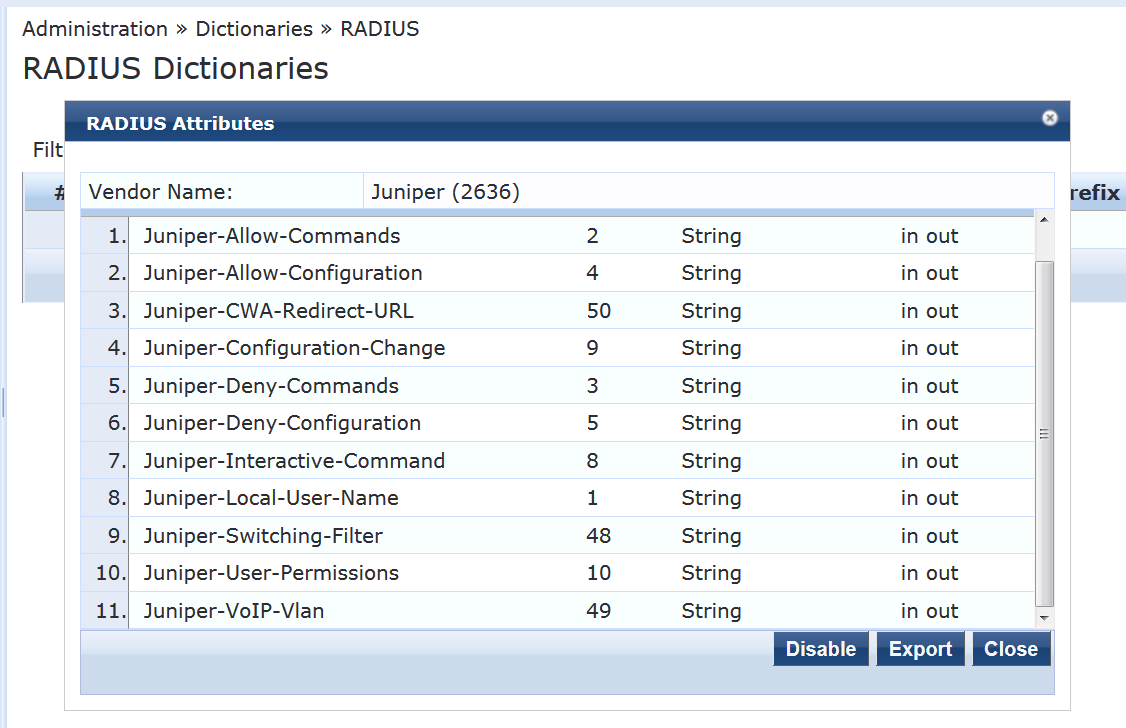
Add the EX4300 switch as a network device.
Step-by-Step Procedure
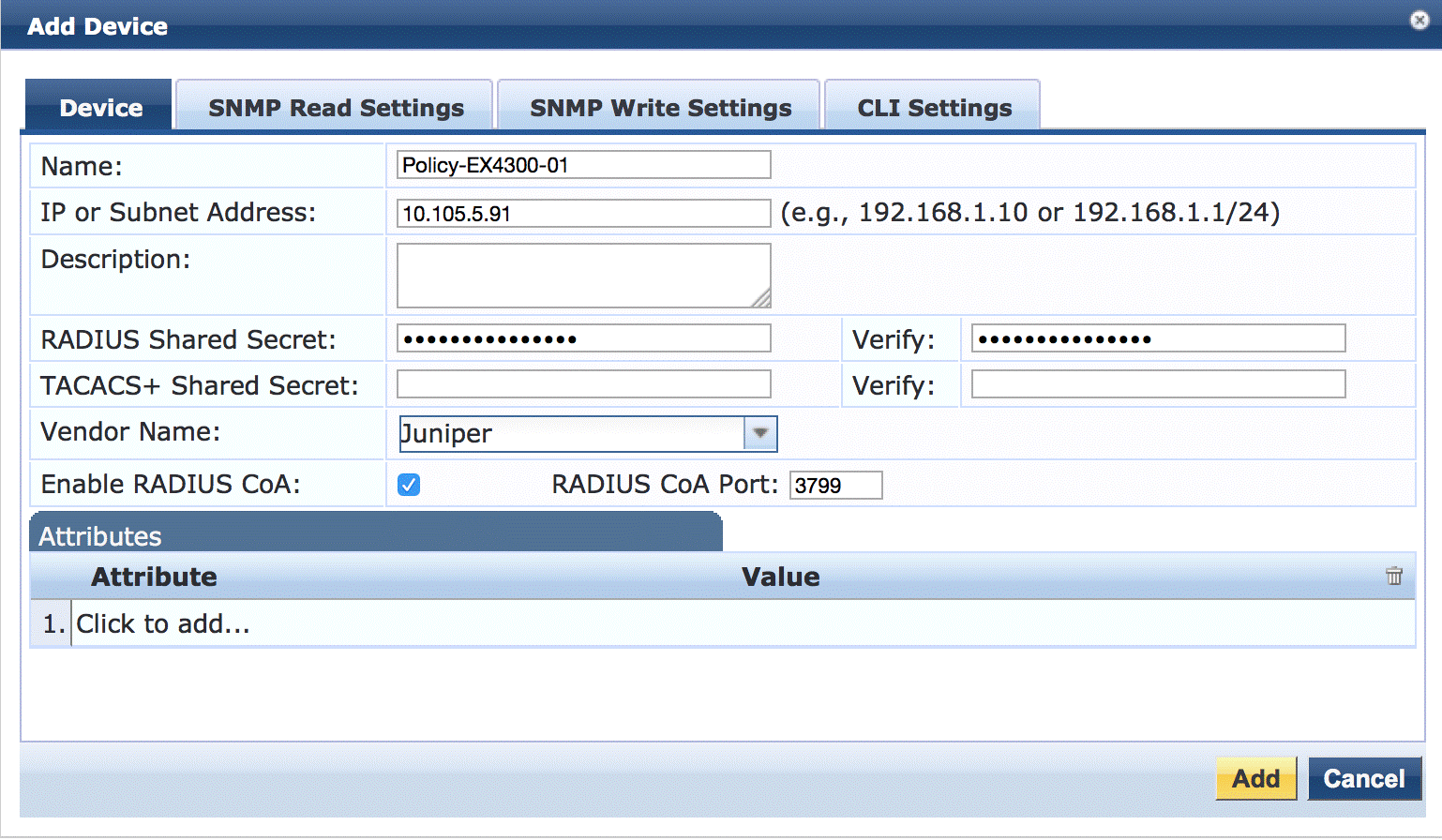
Under Configuration > Network > Devices, click Add.

On the Device tab, enter the hostname and IP address of the switch and the RADIUS shared secret that you configured on the switch. Set the Vendor Name field to Juniper.
Create the enforcement profile to be used for MAC RADIUS authentication.
This profile provides the switch with the name of the built-in firewall filter JNPR_RSVD_FILTER_CWA and the redirect URL for Aruba ClearPass Guest.
Step-by-Step Procedure
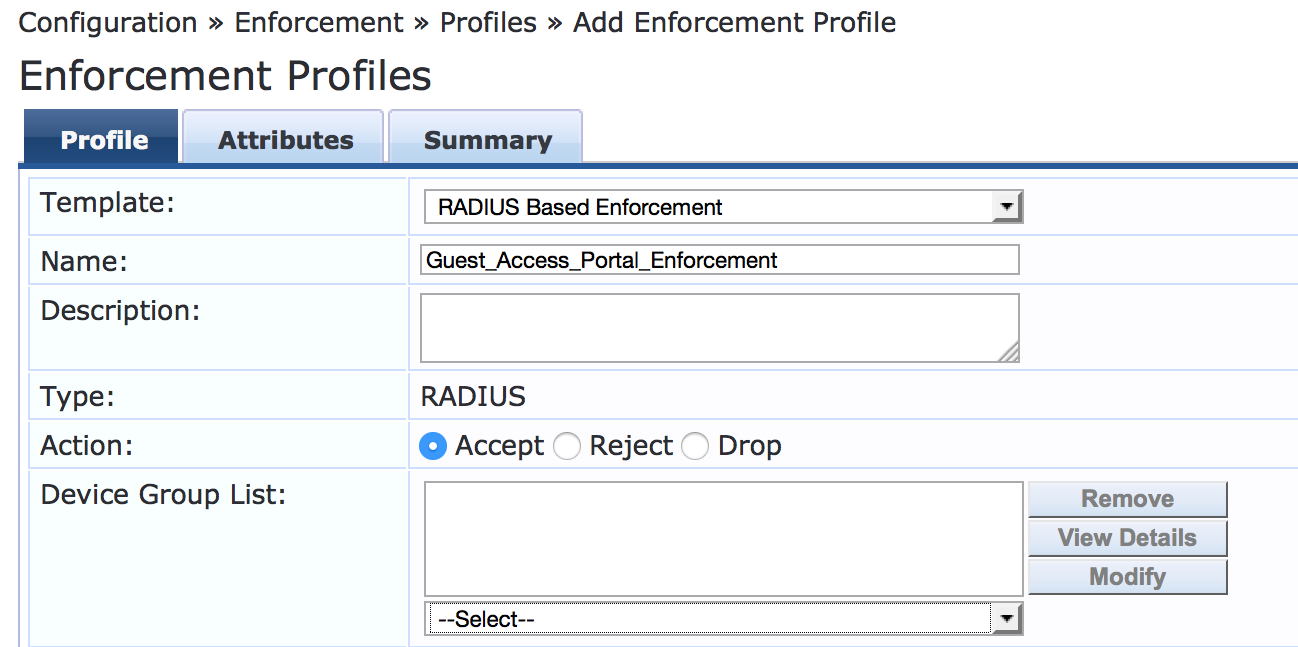
Under Configuration > Enforcement > Profiles, click Add.
On the Profile tab, set Template to RADIUS Based Enforcement and type the profile name, Guest_Access_Portal_Enforcement, in the Name field.
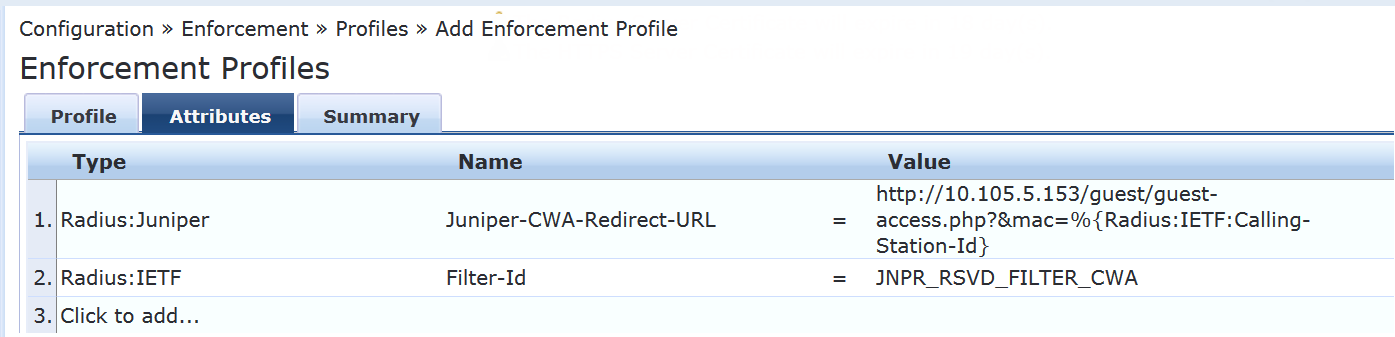
On the Attributes tab, configure the following attributes:
Juniper-CWA-Redirect-URL—Type the following URL:
http://10.105.5.153/guest/guest-access.php?&mac=%{Radius:IETF:Calling-Station-Id}This URL must contain the IP address of the Aruba ClearPass Guest server. It also passes the MAC address of the endpoint to ClearPass Guest (
Radius:IETF:Calling-Station-Id).Filter-Id—Type the following filter name:
JNPR_RSVD_FILTER_CWA
Configure an enforcement profile to be used for central Web authentication.
This profile is configured as a RADIUS Change of Authorization (CoA) profile. It tells Aruba ClearPass to send a RADIUS CoA to the switch, informing it to change the firewall filter in effect for the endpoint from JNPR_RSVD_FILTER_CWA to guest_access_policy_1.
Step-by-Step Procedure
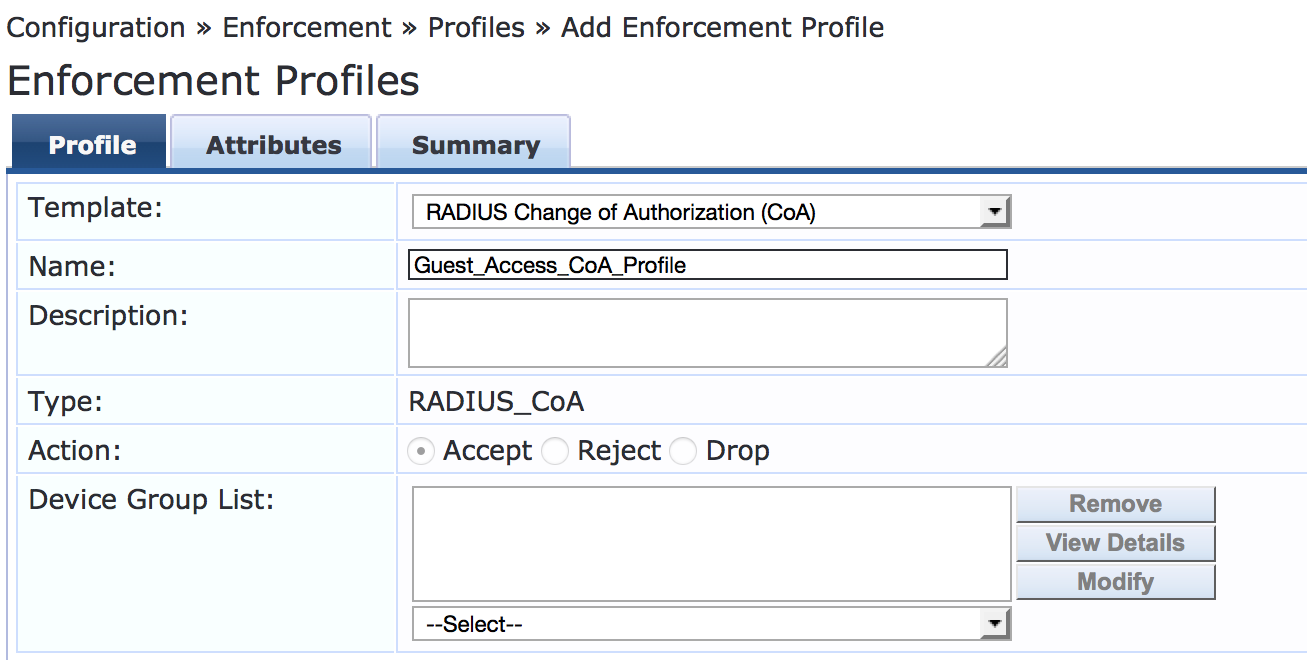
Under Configuration > Enforcement > Profiles, click Add.
On the Profile tab, set Template to RADIUS Change of Authorization (CoA) and type the profile name, Guest_Access_CoA_Profile, in the Name field.
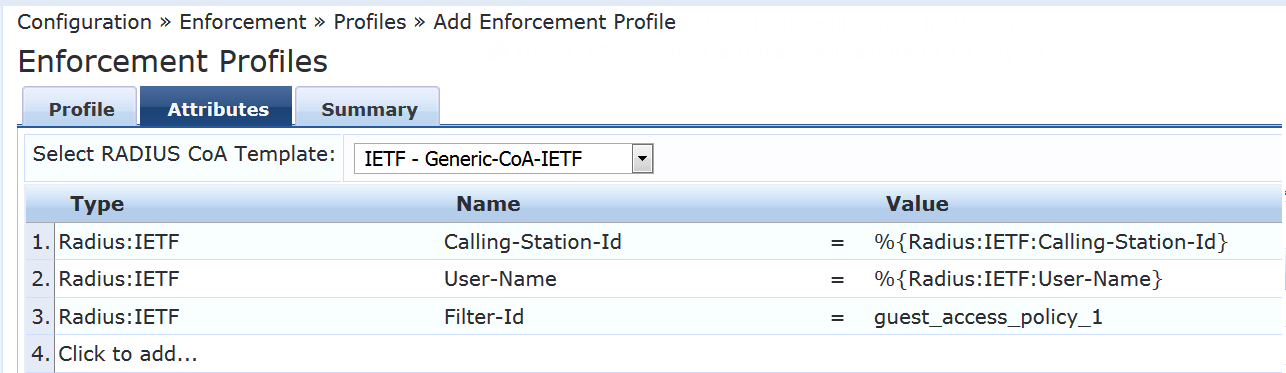
On the Attributes tab, set Select RADIUS CoA Template to IETF - Generic-CoA-IETF and enter the attributes as shown. All values must be typed in or copied and pasted from this document. The values do not appear in the selection lists.
%{Radius:IETF:Calling-Station-Id} %{Radius:IETF:User-Name} guest_access_policy_1
Configure the MAC RADIUS authentication enforcement policy.
The MAC RADIUS policy tells Aruba ClearPass to apply the Guest_Access_Portal_Enforcement profile to all endpoints undergoing MAC RADIUS authentication that are not already known to ClearPass—that is, are not in the endpoint repository.
Step-by-Step Procedure
Under Configuration > Enforcement > Policies, click Add.
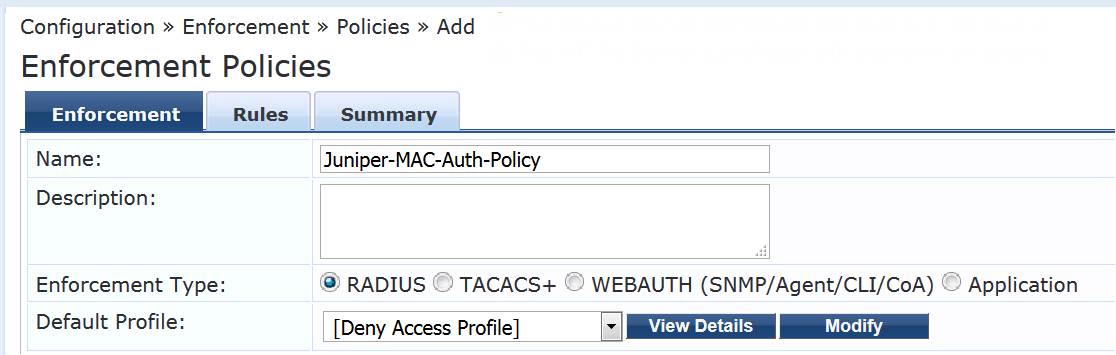
On the Enforcement tab, type the name of policy (Juniper-MAC-Auth-Policy) and set the Default Profile to the predefined profile [Deny Access Profile].
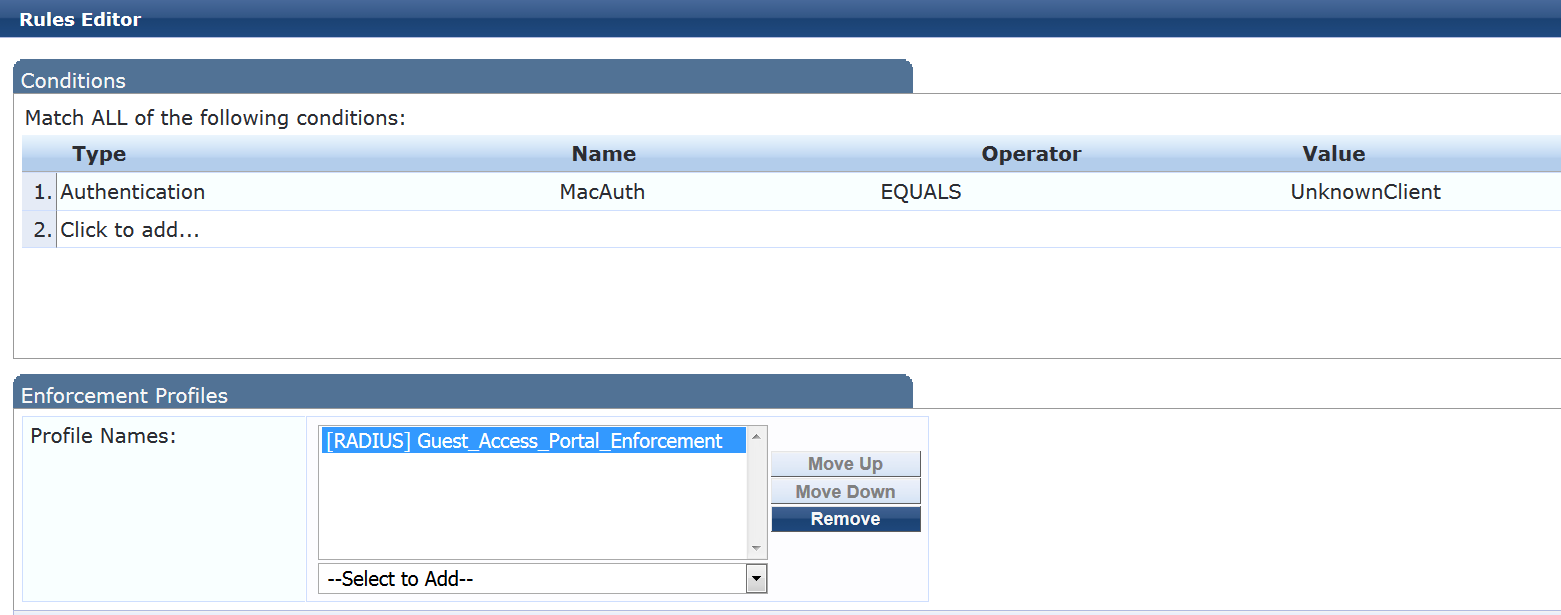
On the Rules tab, click Add Rule and add the rule shown.
This rule permits the Guest_Access_Portal_Enforcement profile to take effect for endpoints that are not known to Aruba ClearPass.
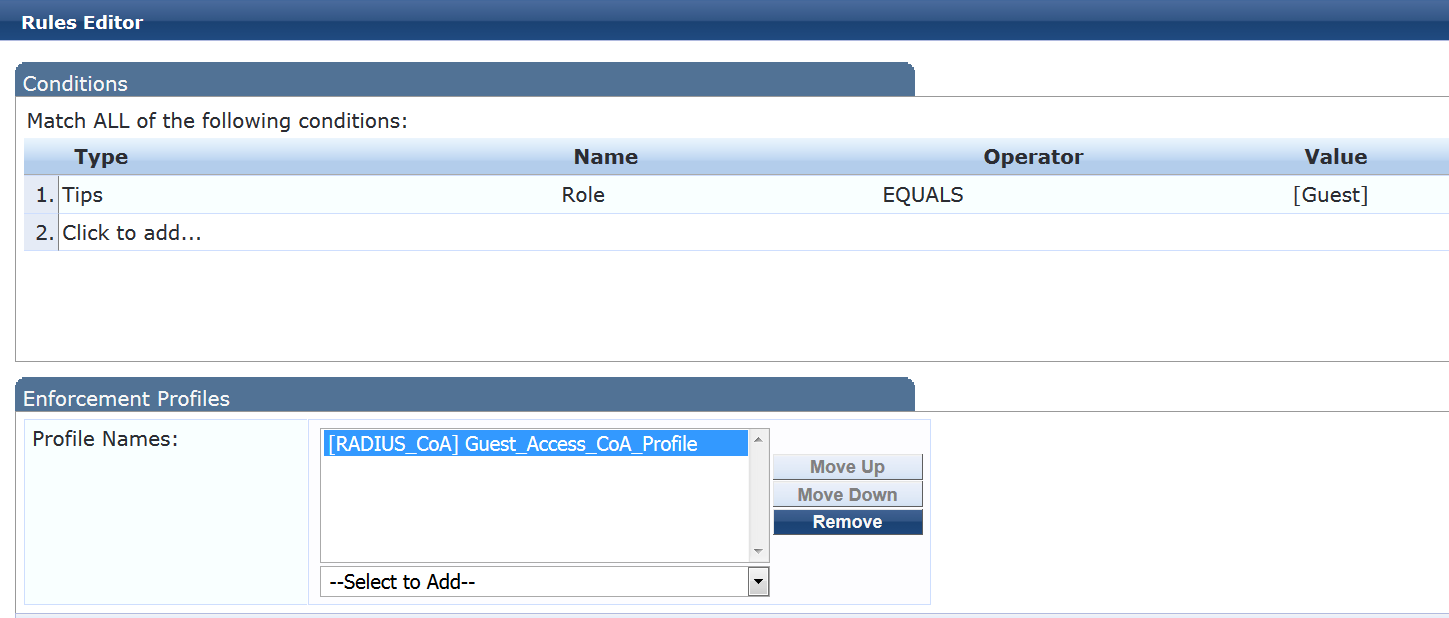
Configure the Web authentication enforcement policy.
This policy takes effect after the guest is redirected to the Aruba ClearPass Guest and ClearPass Guest authenticates the guest. It tells Aruba ClearPass to add the endpoint to the endpoint repository and to apply the Guest_Access_CoA_Profile.
Step-by-Step Procedure
Under Configuration > Enforcement > Policies, click Add.
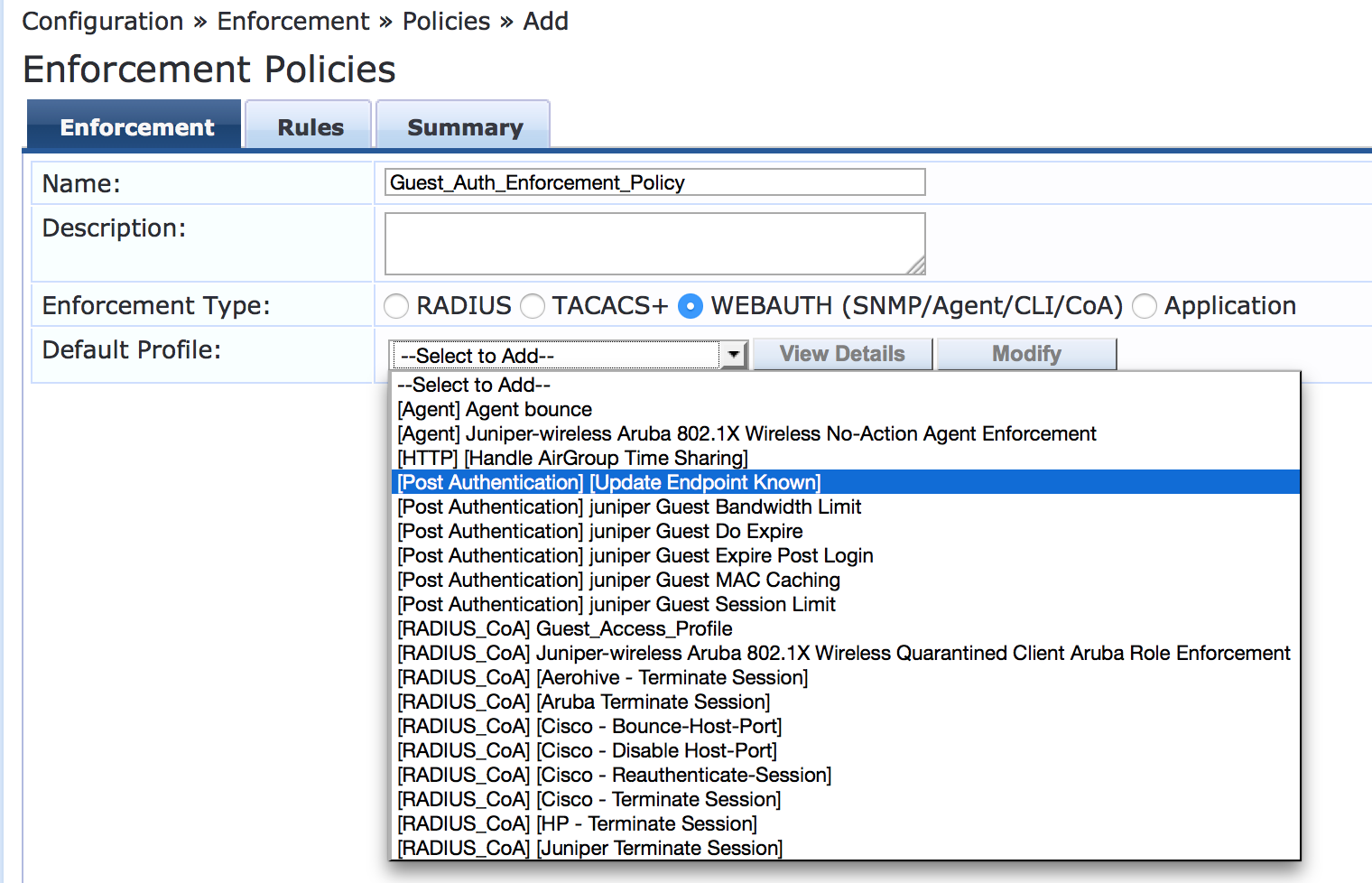
On the Enforcement tab, type the name of the policy (Guest_Auth_Enforcement_Policy) and set Default Profile to [Post Authentication][Update Endpoint Known]. This is a predefined profile that results in the endpoint being added as a known endpoint in the endpoint repository.
On the Rules tab, click Add Rule and add the rule shown.
This rule tells Aruba ClearPass to apply the Guest_Access_CoA_Profile enforcement profile to any endpoint that ClearPass Guest has assigned to role Guest.
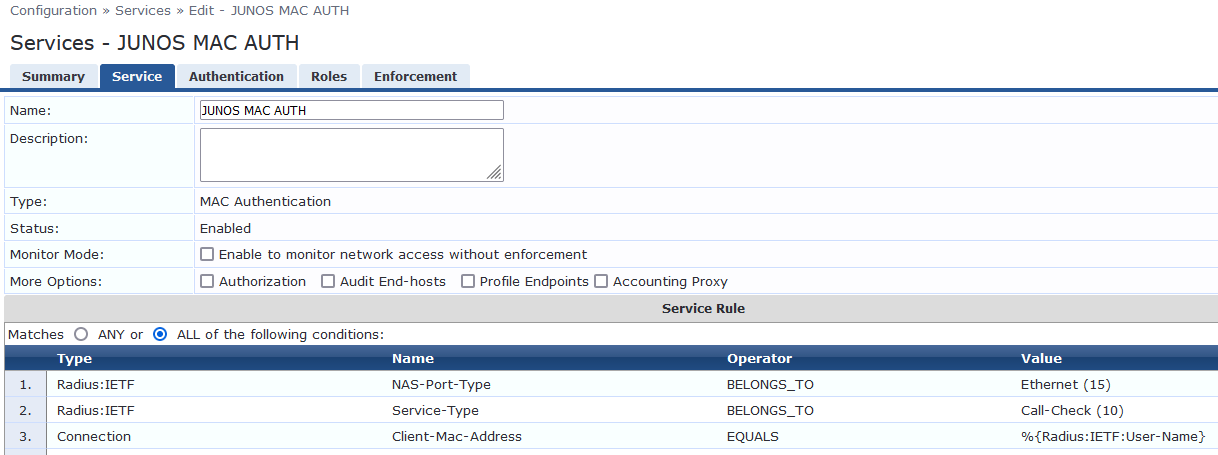
Configure the MAC RADIUS authentication service.
The configuration for this service results in MAC RADIUS authentication being performed when the RADIUS User-Name attribute and the Client-MAC-Address attribute received have the same value.
Step-by-Step Procedure
Under Configuration > Services, click Add.
On the Services tab, fill out the fields as shown.
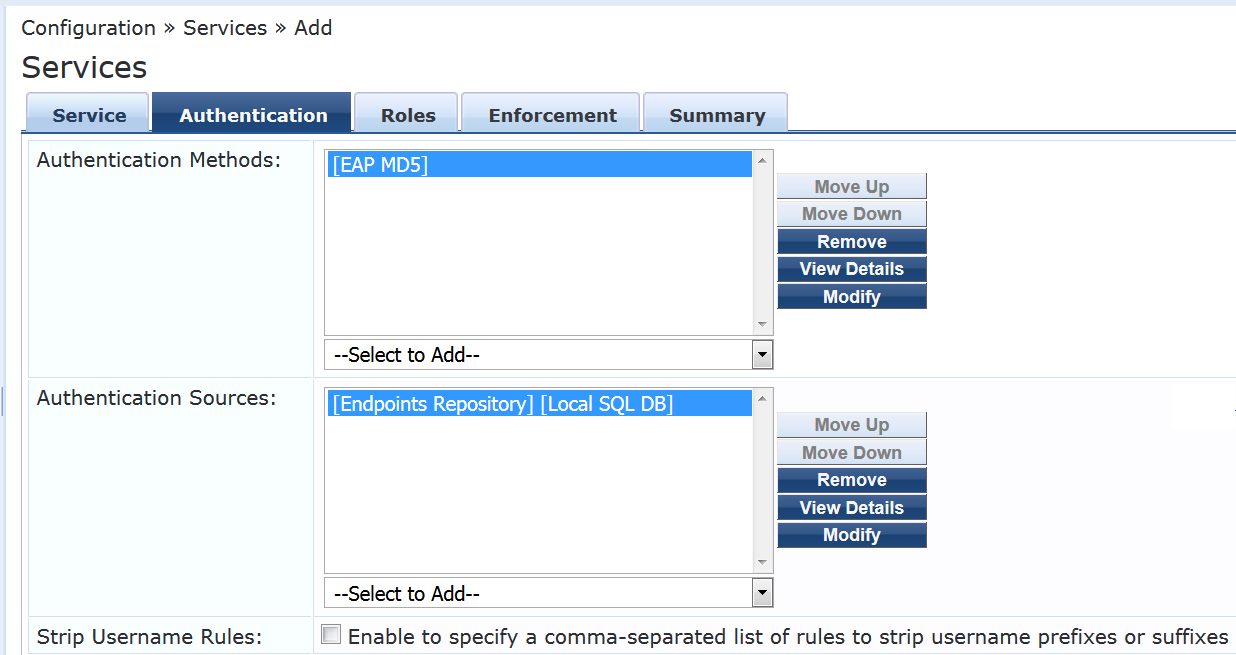
On the Authentication tab:
Delete [MAC AUTH] from the Authentication Methods list and add [EAP MD5] to the list.
Select [Endpoints Repository] [Local SQL DB] in the Authentication Sources list.
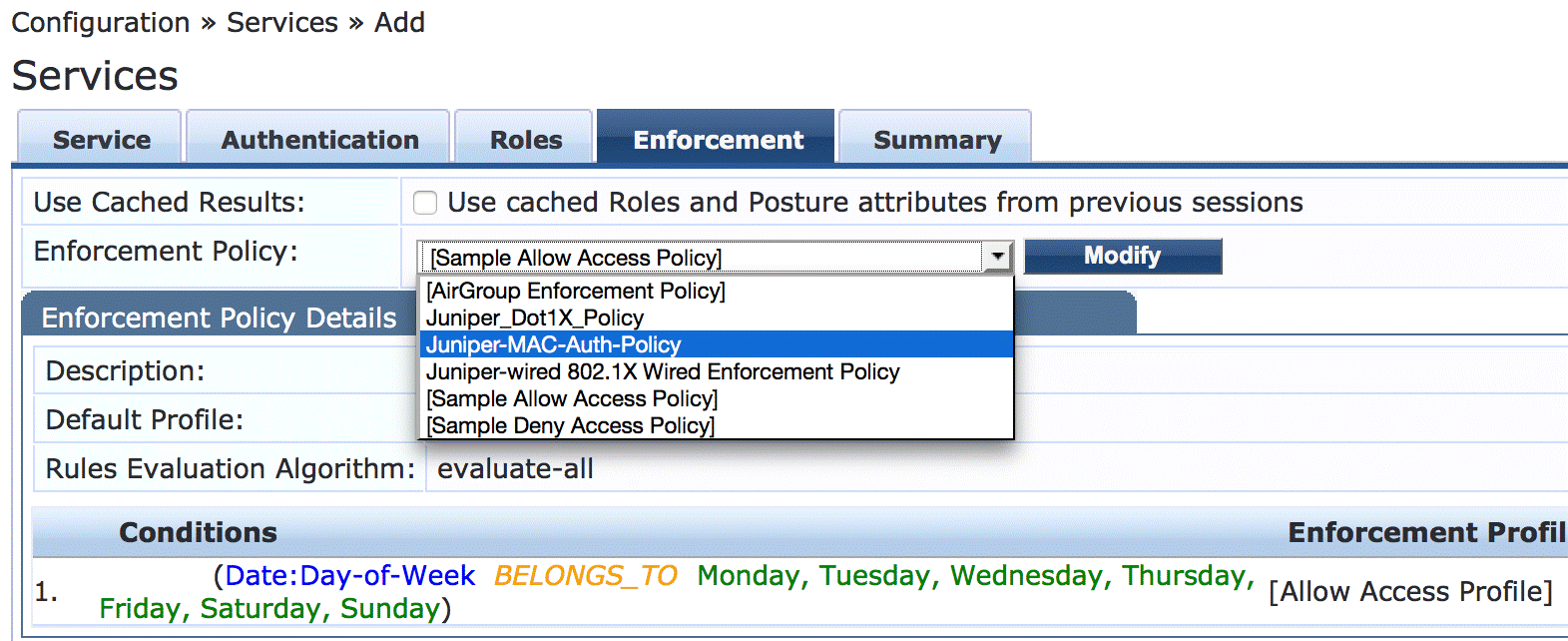
On the Enforcement tab, select Juniper-MAC-Auth-Policy.
Configure the Web-based authentication service.
Step-by-Step Procedure
Under Configuration > Services, click Add.
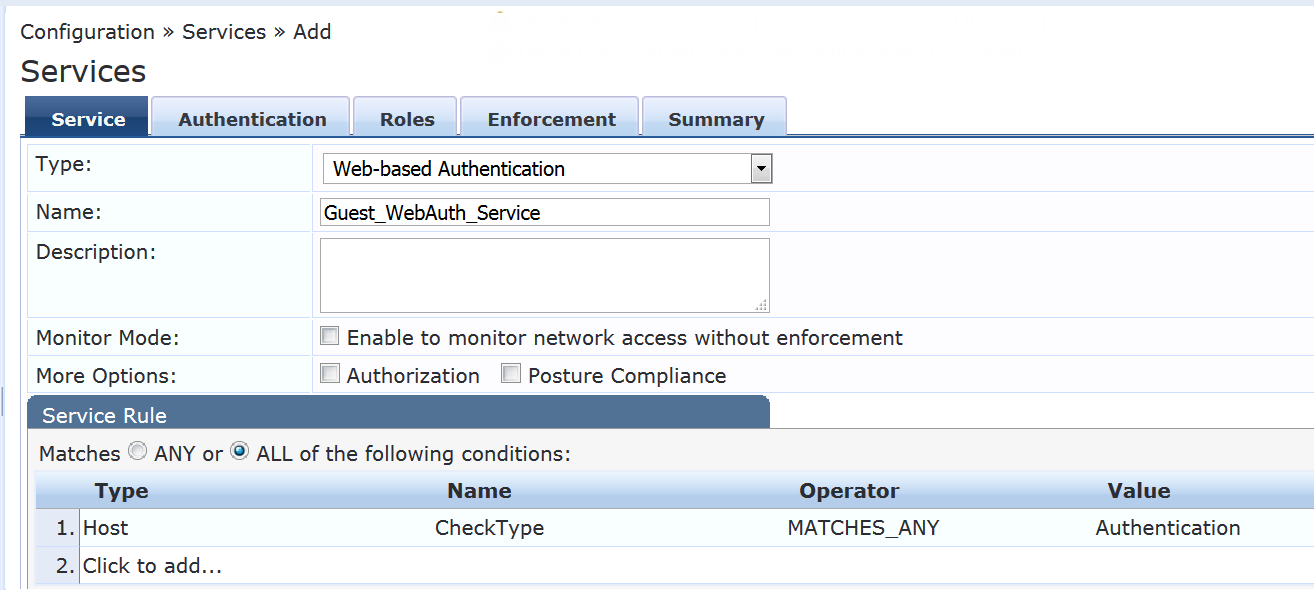
On the Service tab, fill out the fields as shown.
The service rule is the default service rule when you select Web-based Authentication. It allows Web-based authentication requests from any client.
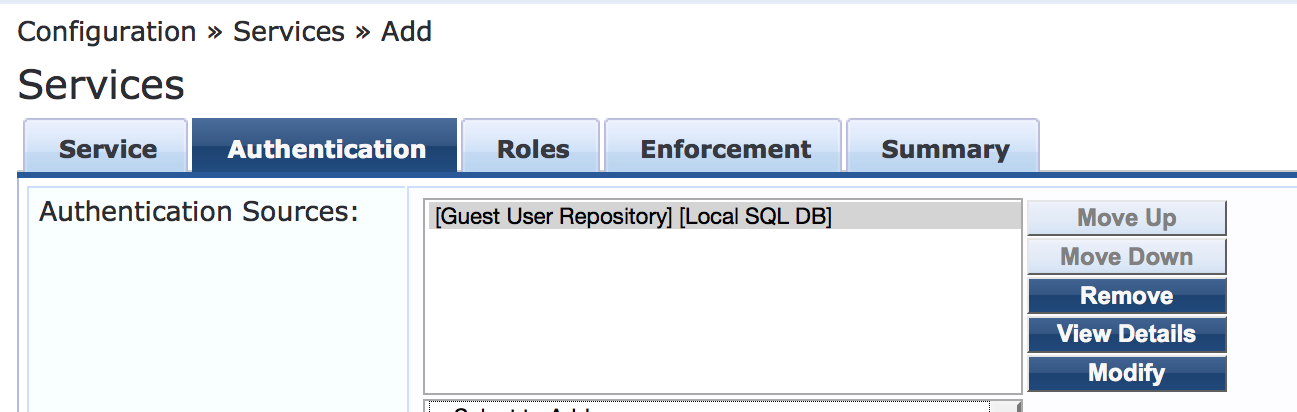
On the Authentication tab, set Authentication Sources to [Guest User Repository][Local SQL DB].
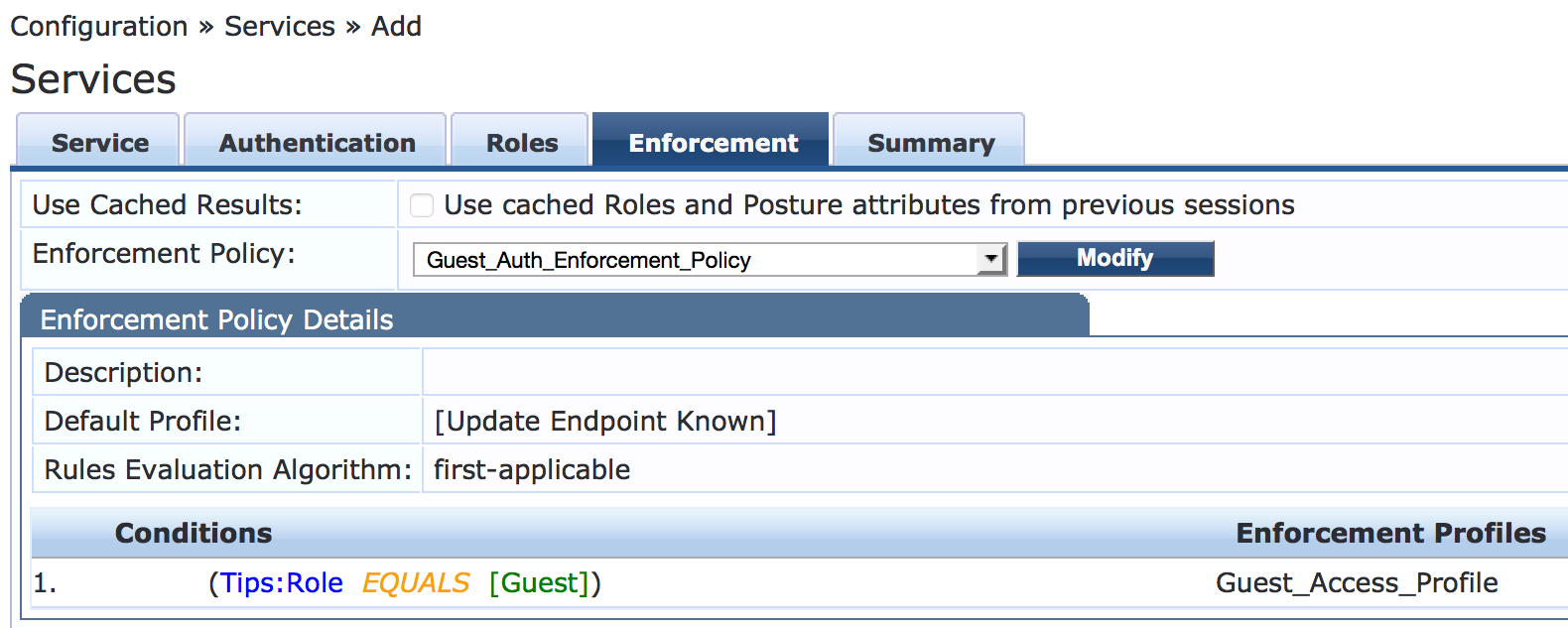
On the Enforcement tab, set Enforcement Policy to Guest_Auth_Enforcement_Policy.
Verification
Confirm that the configuration is working properly.
- Verifying Central Web Authentication
- Verifying Status of Authentication Requests on Aruba ClearPass Policy Manager
Verifying Central Web Authentication
Purpose
Verify that the guest user’s browser is redirected to Aruba ClearPass Guest for authentication and that the guest is successfully authenticated after entering the guest credentials.
Action
Connect a laptop to port ge-0/0/22 on the EX4300 switch.
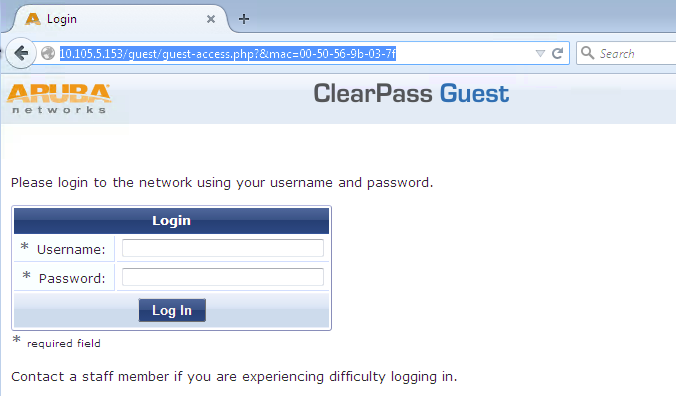
Open a Web browser on the laptop and attempt to access a webpage.
The ClearPass Guest login page should appear as shown.
On the EX Series switch, enter the following
showcommand:user@EX4300> show dot1x interface ge-0/0/22 detail ge-0/0/22.0 Role: Authenticator Administrative state: Auto Supplicant mode: Multiple Number of retries: 3 Quiet period: 60 seconds Transmit period: 30 seconds Mac Radius: Enabled Mac Radius Restrict: Disabled Mac Radius Authentication Protocol: EAP-MD5 Reauthentication: Enabled Configured Reauthentication interval: 3600 seconds Supplicant timeout: 30 seconds Server timeout: 30 seconds Maximum EAPOL requests: 2 Guest VLAN member: not configured Number of connected supplicants: 1 Supplicant: 0050569b037f, 00:50:56:9B:03:7F Operational state: Authenticated Backend Authentication state: Idle Authentication method: CWA Authentication Authenticated VLAN: v100 Dynamic Filter: JNPR_RSVD_FILTER_CWA Session Reauth interval: 3600 seconds Reauthentication due in 3566 seconds Session Accounting Interim Interval: 600 seconds Accounting Update due in 566 seconds CWA Redirect URL : http://10.105.5.153/guest/guest-access.php?&mac=00-50-56-9b-03-7fThe output shows that the endpoint has been authenticated, that the authentication method currently in effect is central Web authentication (
CWA Authentication), and that the JNPR_RSVD_FILTER_CWA firewall filter and the redirect URL are also in effect.In the ClearPass Guest login page, enter the guest e-mail address and the automatically generated password that you noted when you configured Aruba ClearPass Guest.
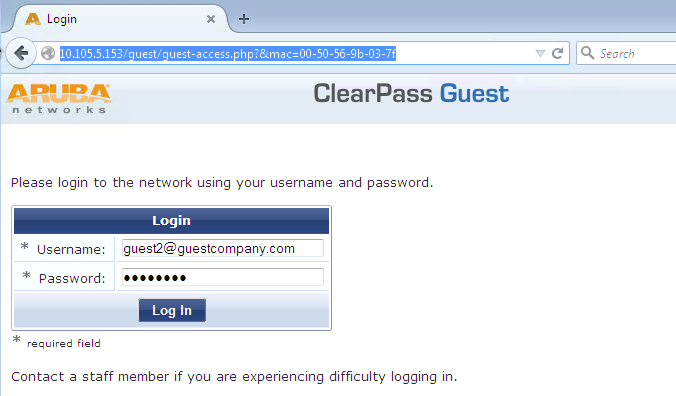
After you log in, your browser should be redirected to the Juniper Networks home page, as configured in Aruba ClearPass Guest.
On the EX Series switch, enter the following show command:
user@EX4300> show dot1x interface ge-0/0/22 detail ge-0/0/22.0 Role: Authenticator Administrative state: Auto Supplicant mode: Multiple Number of retries: 3 Quiet period: 60 seconds Transmit period: 30 seconds Mac Radius: Enabled Mac Radius Restrict: Disabled Mac Radius Authentication Protocol: EAP-MD5 Reauthentication: Enabled Configured Reauthentication interval: 3600 seconds Supplicant timeout: 30 seconds Server timeout: 30 seconds Maximum EAPOL requests: 2 Guest VLAN member: not configured Number of connected supplicants: 1 Supplicant: 0050569b037f, 00:50:56:9B:03:7F Operational state: Authenticated Backend Authentication state: Idle Authentication method: Mac Radius Authenticated VLAN: v100 Dynamic Filter: guest_access_policy_1 Session Reauth interval: 3600 seconds Reauthentication due in 3434 seconds Session Accounting Interim Interval: 600 seconds Accounting Update due in 434 secondsThe output shows that the guest_access_policy_1 firewall filter is now in effect. The switch received the RADIUS CoA from Aruba ClearPass after the endpoint was authenticated by central Web authentication, telling it which firewall filter to use.
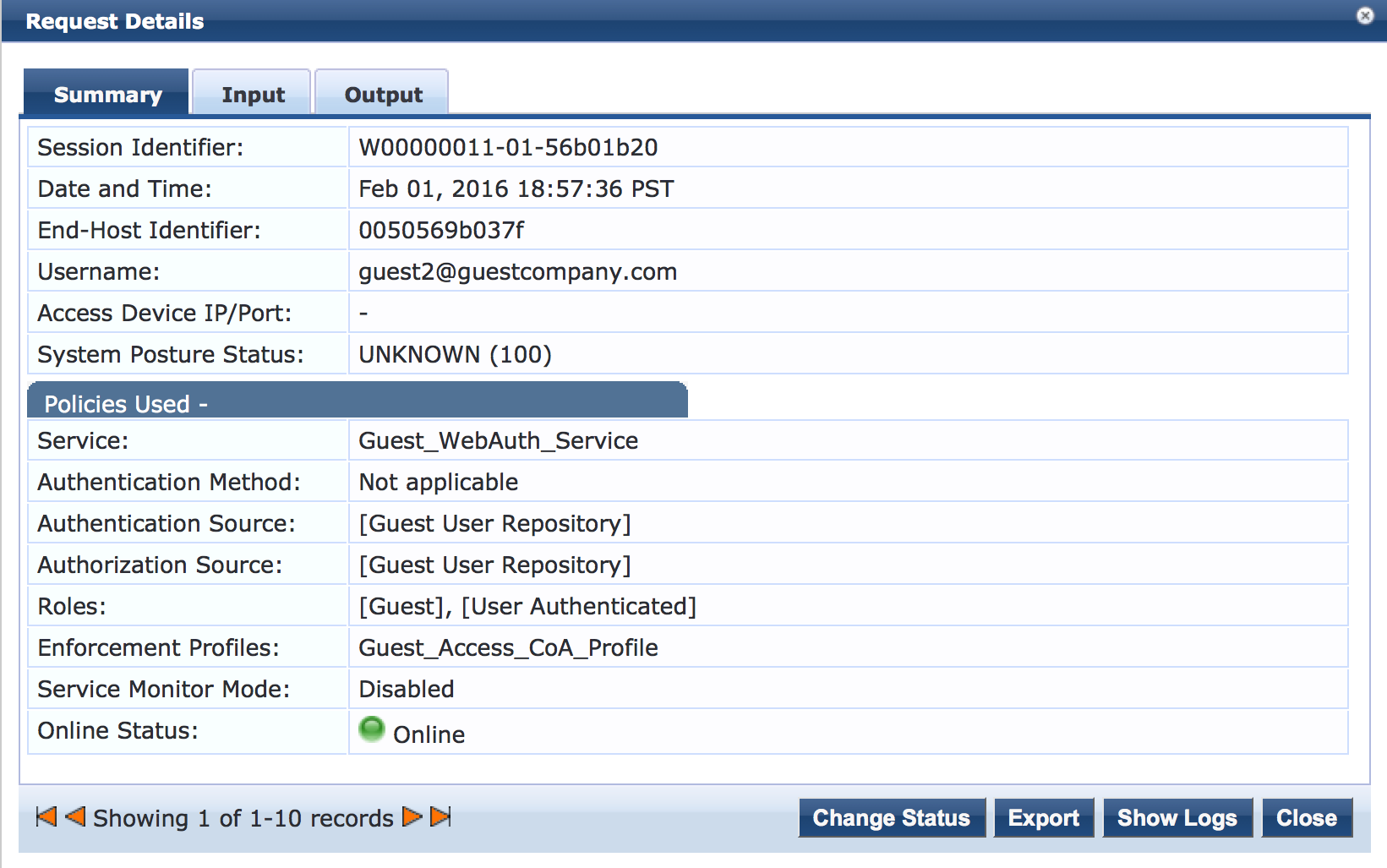
Verifying Status of Authentication Requests on Aruba ClearPass Policy Manager
Purpose
Verify that the endpoints are being correctly authenticated and that the correct RADIUS attributes are being exchanged between the switch and Aruba ClearPass.
Action
Go to Monitoring > Live Monitoring > Access Tracker to display the status of the authentication requests.
The Access Tracker monitors authentication requests as they occur and reports on their status.
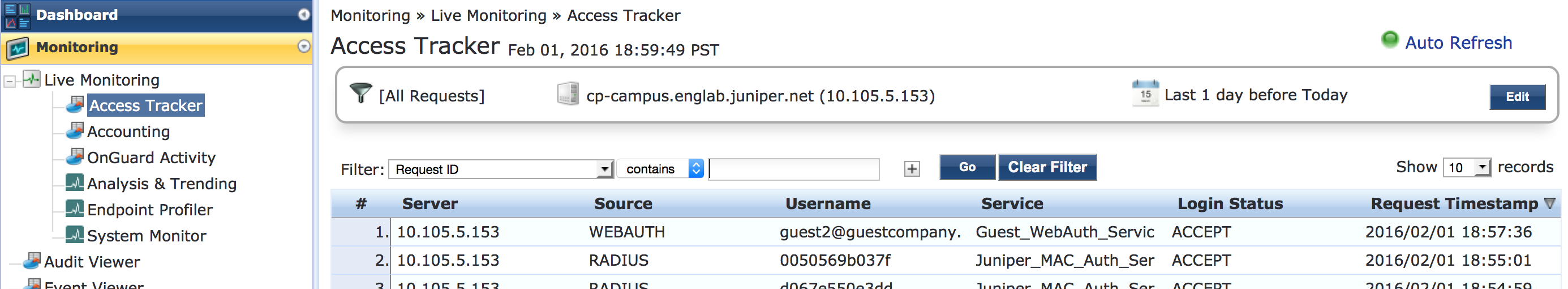
To get more details on the initial MAC RADIUS authentication request from the endpoint, click the request (line 2 of Access Tracker request table).
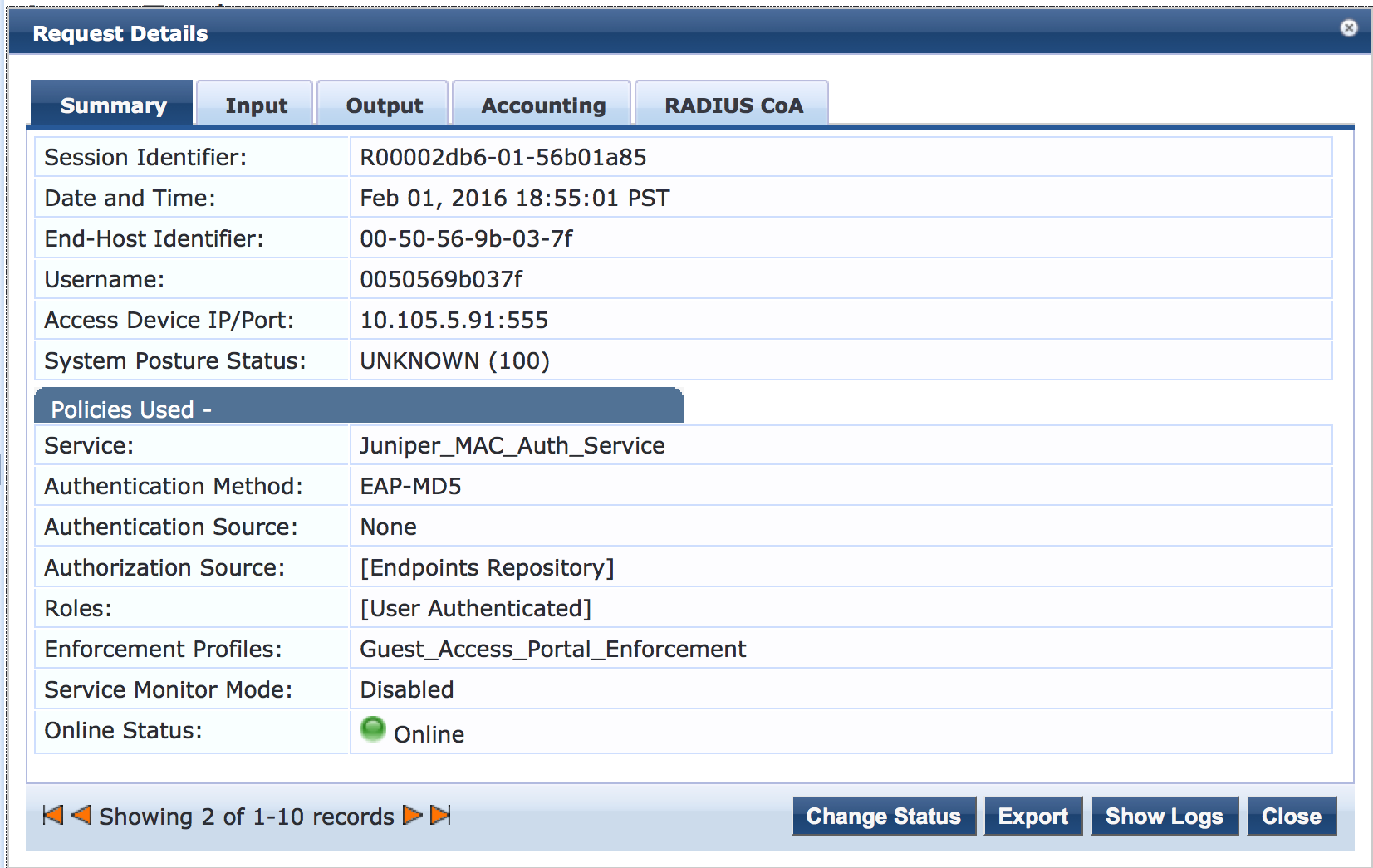
To get more details on the Web authentication request from the endpoint, click the request (line 1 of the Access Tracker request table).