ON THIS PAGE
Planning and Design Phase
Network Assessment
The Network Assessment phase is foundational for successful Juniper deployment. This involves a detailed evaluation of the current network environment. It includes an inventory and analysis of the wired infrastructure—such as switches and cabling—and the wireless setup, including access points and their coverage. Key considerations during this phase include understanding the specific demands of user density and critical application requirements (for example, real-time voice and video, large data transfers, or the unique needs of IoT devices). A comprehensive review of current security policies and compliance mandates is essential. Existing WAN connectivity and Internet egress points must also be evaluated. This ensures the Juniper solution integrates smoothly, meets performance expectations, and aligns with the organization's security posture.
To help understand the current network infrastructure, ensure your analysis answers the questions in each of the following categories:
-
For Existing Switches
- What are the makes, models, and quantities of existing switches at each location?
- What is the current firmware or OS version running on these switches?
- What is the age and warranty status of the existing switching infrastructure?
- Are the switches Layer 2 or Layer 3? If L3, what routing capabilities do they have?
- What is the current port utilization on key switches (for example, core, aggregation, access)?
- Are you using any high-availability mechanisms (for example, stacking, MLAG, VRRP)?
- What is the power over Ethernet (PoE) capabilities of the access switches, and what is the current PoE budget utilization?
- What is the current network segmentation strategy (for example, VLANs, subnets)?
- Are you using any network access control (NAC) solutions with the switches?
-
For Existing Access Points (APs):
- What are the makes, models, and quantities of existing wireless APs?
- What Wi-Fi standards do they support (for example, 802.11ac, 802.11ax/Wi-Fi 6, Wi-Fi 6E)?
- What is the current firmware version of the APs?
- How are the APs currently powered (PoE or external power)?
- What is the current wireless controller solution (if any), and is it on-premises or cloud-managed?
- What are the existing SSIDs, their security configurations (for example, WPA2-Enterprise, PSK), and associated VLANs?
- Are there any existing wireless site survey reports available?
- What is the perceived wireless performance and coverage in key areas?
- Are there known dead spots or performance issues?
- Are there any location-based services or IoT devices currently utilizing the wireless network?
-
For Existing Cabling:
- What type of Ethernet cabling is in place (for example, Cat5e, Cat6, Cat6a, fiber)?
- What is the age and condition of the existing cabling infrastructure?
- Are there detailed cabling diagrams or documentation available?
- What is the current capacity of the backbone cabling between network closets/buildings?
- Are there any known cabling issues (for example, damaged cables, poorly terminated connections)?
- Is there sufficient spare cabling capacity for future expansion, especially for new APs or higher speed wired devices?
-
User density and application requirements (voice,
video, data, IoT):
- What is the peak number of concurrent users expected in different areas (for example, office floors, conference rooms, and common areas)?
- What is the primary business-critical applications (for example, ERP, CRM, VDI) and their bandwidth/latency requirements?
- Is there significant use of real-time applications like Voice over IP (VoIP) or video conferencing (for example, Zoom, Microsoft Teams)? What are their QoS requirements?
- What types of IoT devices will be connected to the network (for example, sensors, cameras, smart building controls)? What are their connectivity and security needs?
- What are the typical data transfer patterns and volumes (for example, large file transfers, cloud backups)?
- Are there any specific bandwidth guarantees, or quality of service (QoS) policies required for certain user groups or applications?
- How many devices per user are expected (for example, laptop, smartphone, tablet, wearable)?
- What are the peak usage times for the network?
-
Security policies and compliance requirements:
- What are the organization's existing security policies (for example, acceptable use, data classification, access control)?
- Which industry-specific or regulatory compliance standards must the network adhere to (for example, HIPAA, PCI DSS, GDPR, ISO 27001, NIST)?
- Are there specific requirements for network segmentation, micro-segmentation, or isolation of sensitive data?
- What are the current authentication and authorization mechanisms in place (for example, Active Directory, RADIUS, 802.1X)?
- What are the requirements for guest access, and how is it currently secured and managed?
- Are there any existing intrusion detection/prevention systems (IDS/IPS), firewalls, or security information and event management (SIEM) solutions?
- What are the requirements for data encryption, both in transit and at rest?
- Are there specific policies for BYOD (Bring Your Own Device) or corporate-owned device management?
- What is the organization's incident response plan, and how does network security integrate with it?
- Are there any requirements for logging, auditing, and reporting of network security events?
-
Existing WAN connectivity and internet egress
points:
- What types of WAN connections are currently in use (for example, MPLS, broadband, dedicated internet access, 4G/5G LTE)?
- What are the bandwidth capacities of each WAN link at each location?
- What are the current service providers for WAN and internet connectivity?
- Are there any existing SD-WAN solutions in place, and if so, what is their architecture and vendor?
- What are the primary internet egress points for the organization?
- Are there any specific requirements for WAN redundancy or failover?
- What are the current latency and packet loss experienced across WAN links?
- How is traffic prioritized across the WAN today (for example, QoS policies)?
- Are there any direct cloud connections (for example, AWS Direct Connect, Azure ExpressRoute, Google Cloud Interconnect)?
-
What are the current costs associated with WAN and internet services?
High-Level Design
The high-level design (HLD) phase translates the assessment findings into a strategic blueprint for the new Juniper network. This involves defining the overall network topology, typically a hierarchical structure with core, aggregation, and access layers, leveraging Juniper EX Series Switches for robust wired connectivity. A comprehensive IP addressing scheme and VLAN planning must be established to ensure efficient traffic flow and logical network segmentation. For the wireless network, detailed coverage and capacity planning, often informed by site surveys, will dictate optimal Juniper Mist AP placement to meet user density and application performance requirements. A key aspect of the HLD is defining security zones to isolate user groups and device types, while integrating with identity systems (for example, RADIUS, Active Directory) and security tools for a unified, secure network.
- Network topology (core, aggregation, access layers).
- IP addressing scheme and VLAN planning.
- Wireless coverage and capacity planning (site surveys, AP placement).
- Security zone segmentation.
- Integration points with existing systems (identity management, security tools).
Juniper has brought true innovation to the networking space with the world’s first AI-driven wired and wireless network. The Juniper Mist™ AI platform makes networking predictable, reliable, and measurable with unprecedented visibility into the user experience. Time-consuming manual IT tasks are replaced with AI-driven proactive automation and self-healing capabilities, lowering networking operational costs, and saving substantial time and money. Juniper also brings enterprise-grade Wi-Fi, Bluetooth® Low Energy (BLE), and IoT together so businesses can increase the value of their wireless networks through personalized location services, such as wayfinding, proximity notifications, and asset location. With the patented virtual BLE (vBLE) technology, no battery beacons or manual calibration are required.
Juniper Mist™ Wired and Wireless Assurance brings cloud management and Mist AI™ to campus fabrics. They set a new standard for network management by moving your campus deployment toward AI-driven operations, which helps deliver better experiences to connected devices. The Juniper Mist cloud streamlines deployment and management of your campus fabric, while Mist AI simplifies operations and improves visibility into the performance of connected devices.
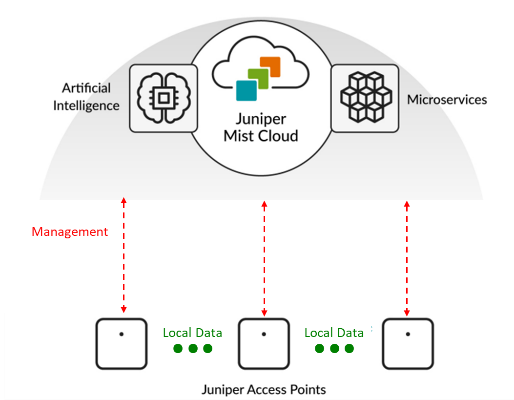
Juniper Mist Edge seamlessly integrates into a Juniper switching and wireless network by serving as a localized extension of the cloud-based Mist architecture. For customers, this means the benefits of a modern, AI-driven network can be achieved without requiring a complete overhaul of their existing infrastructure. The Juniper Mist Edge appliance handles functions that require on-premises processing, such as traffic tunneling from Juniper Wireless APs and acting as a proxy for Juniper switches. This enables secure communication with the Mist Cloud for centralized management and monitoring, even when the devices are located behind firewalls or proxies. This hybrid approach offers advantages such as maintaining a centralized data plane for campus or branch networks (a key factor for organizations transitioning from legacy controller-based architectures), seamless roaming, enhanced traffic isolation and security, and the flexibility to deploy new microservices at the edge as needed. This integration provides customers with increased network flexibility, operational efficiency, and a robust platform for managing wired and wireless networks through a single, intelligent interface.
Distributed Approach
Communication between the Juniper Mist Cloud and APs uses HTTPS/TLS with AES-128 encryption, and mutual authentication is provided by a combination of digital certificate and per-AP shared key created during manufacturing. A 4096-bit key is used for the certificate signature. User data traffic is processed and forwarded locally at the Access Point Network Interface utilizing the local network infrastructure. Therefore, SSID to VLAN mapping is configured per SSID, and the switch port connecting to the AP should be configured as a trunk if you use multiple VLANs. The figure below shows the high-level architecture.
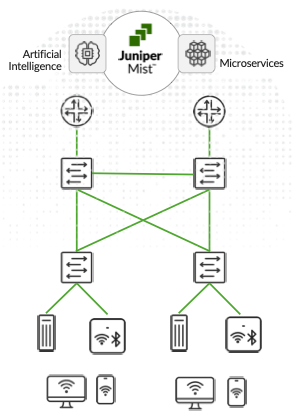
This setup is ideal for any enterprise running up to 1,000 APs in a single roaming domain or up to 2,000 concurrent connected user devices, with the ability to configure switch ports for adapting the local traffic breakout.
Centralized (Tunneled) Approach
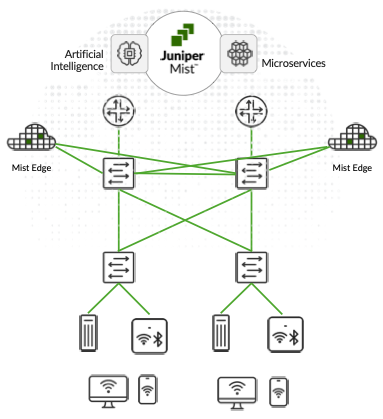
While Juniper Mist can run smoothly without tunneling services as explained in the previous section, in some use cases, you might need to consider tunneling the AP’s traffic back to a central location. For that, Juniper extends its microservices to the campus using Mist Edge appliances. Juniper Mist Edge extends AI-native wireless agility and scale to the campus edge without the need for legacy wireless controllers. Juniper Mist Edge allows data centralization, which is useful for organizations limited by legacy network designs, and for those that want seamless wireless mobility for guests and remote access.
When using Juniper Mist Edge, organizations gain the advantage of having localized data analyzed by the Juniper Mist microservices cloud and the Marvis AI engine. The unique combination delivers agility, reliability, and operational simplicity while enabling simplified, seamless, large campus roaming and secure IoT with dynamic segmentation. Having a Juniper AI-Native Networking Platform streamlines IT operations with unprecedented automation and insight.
Juniper Mist Edge Use Cases
Juniper Mist Edge solves multiple wireless challenges while increasing network and operational efficiency. We recommend Mist Edge deployments for:
- VXLAN deployment, such as Campus Fabric Core-Distribution or Campus Fabric IP Clos.
- More than 1,000 APs and 2,000 concurrently connected devices in a single roaming domain.
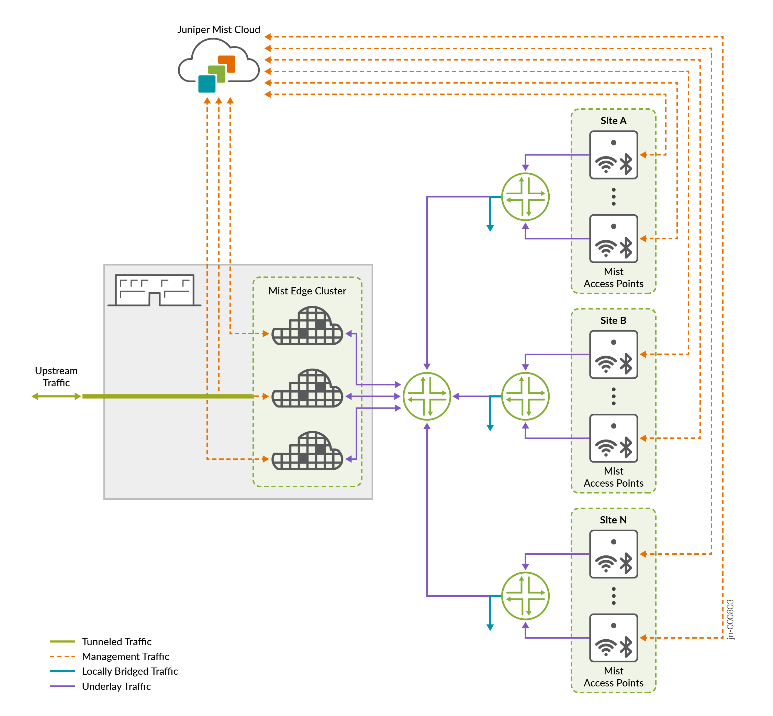
- Deployments exceeding 100K wireless clients—For these large deployments, we recommend configuring multiple Mist Edge tunnels, each carrying AP traffic from different WLANs to two or more Mist Edge clusters that do not share the same L2 VLAN. This tunnel configuration is known as geo-segmentation. The Mist Edges can be housed in the same data center or can be geographically separated.
- Easy migration from a legacy controller architecture to a modern microservices cloud without impacting the existing network design.
- Extending VLANs to distributed branches and telecommuters, thereby replacing remote VPN technology.
- Separating guest access and corporate traffic.
- Providing dynamic traffic segmentation for IoT devices.
Tunneling Microservices
Juniper APs use standards-based L2TPv3 technology, or IPsec in a teleworker scenario, to tunnel traffic to and from the Mist Edge for selected WLANs. This provides flexibility to use a combination of distributed and centralized data planes, where needed, to meet customer requirements. A deployment with Mist Edge can also support locally bridged and tunneled WLANs.
The tunneling service enables you to preserve the VLAN configuration at your edge switches while transitioning to a Mist microservices cloud architecture. You accomplish this by tunneling your traffic through a centralized cluster of Mist Edge devices while maintaining the ability to separate SSIDs and users onto different networks. The tunneling service also supports seamless mobility for devices running latency-sensitive applications, allowing them to maintain performance as they roam across the campus. A Juniper Mist Edge cluster will operate intelligently to deliver scalable and reliable performance by optimizing broadcast and multicast traffic delivery. Configuration of the tunnels is simplified through the power of the Juniper Mist cloud and its zero-touch provisioning capabilities.
Tunneled WLANs and Flexible Traffic Redirection
Many times, Wi-Fi deployments have a requirement to bridge the WLAN locally as well as support separate overlays for guest access and corporate wireless network traffic. The microservices architecture provides the flexibility to form multiple tunnels to different Mist Edge appliances based on the wireless configuration requirements. For instance, at one site, the WLAN could be bridged locally, a guest WLAN could be tunneled to the DMZ using one Mist Edge device, and the corporate SSID could be tunneled to the data center for access to corporate resources using another Mist Edge device.
High Availability and Clustering
Juniper Mist Edge supports elastically scalable clusters, with options for backup clusters, composed of an unlimited number of nodes. The Mist Edge cluster design for the tunneling microservice is guided by aggregate capacity considerations and based on the number of APs, the number of clients, and throughput expectations.
Active/active tunneling clusters deliver higher availability and resiliency than traditional N+1 standby architectures and ensure redundancy while balancing the AP traffic between Mist Edges with zero idle capacity. Mist Edge supports multiple layers of redundancy to ensure WLAN survivability in the event of a catastrophic network failure. Multiple Mist Edge nodes within a cluster allow APs to associate with any surviving node in the event of a failure. If an entire cluster goes offline within a data center, Mist APs can fail over to a different cluster hosted in a different data center to assure network survivability.
Additionally, the Mist Edge architecture allows for the standby cluster for one site to be the Primary cluster for another site, ensuring full utilization of resources and reduced operating costs.
Juniper APs separate the control and management functions from the data plane and will continue to function even if the connection to the Mist Edge goes down.
Design Considerations for L2 Redundancy

APs located at multiple sites can effectively terminate tunnels to Mist Edges that belong to the primary cluster (active/active), as specified in the Mist Tunnel Configuration. To ensure L2 redundancy, the cluster must consist of a minimum of two Edges. This arrangement provides robust network coverage and enhances overall system reliability. Regardless of the number of Mist Edges in a cluster, all the edges will be active, and the ap tunnels will be load balanced across them. The cloud decides and pushes down a list of the mist edges for tunnel termination. Each AP receives a list with a different order of edges, the order of the edges determines the preferred edge for the AP.
If multiple sites are tunneling traffic to a cluster with more than one edge, apps from within a site may terminate tunnels on different edge. This is the default behavior and recommended, since it achieves optimal load balancing. However, this behavior can be fine-tuned to tunnel traffic from a particular site to terminate on a single edge. This can be configured through the Tunnel Host Selection section under the Mist Clusters in the UI.
If multiple mist edges reside on the same L2 segment in your network, we recommend them to be added to the same cluster in active/active mode. We recommend to design for 80 percent capacity on Mist edge. For ME-X6 SKU, which supports a max of 5000 AP tunnels, we should plan for 4000 AP tunnels which is 80 percent of the max tunnels. In case of multiple Mist Edge loss situation, the tunnel terminator service can be oversubscribed temporarily.
Design Considerations for Data Center Redundancy
When designing data center redundancy or L3 separated networks, Mist Edges should be partitioned into Primary and Secondary clusters. All the Mist Edges that are part of Primary Cluster are active, and the Edges in Secondary Cluster are in a standby mode. Each cluster in the distributed data centers may have one or more mist edges. L3 redundancy can also be achieved with one edge each in Primary and secondary clusters. This will be an active standby deployment.
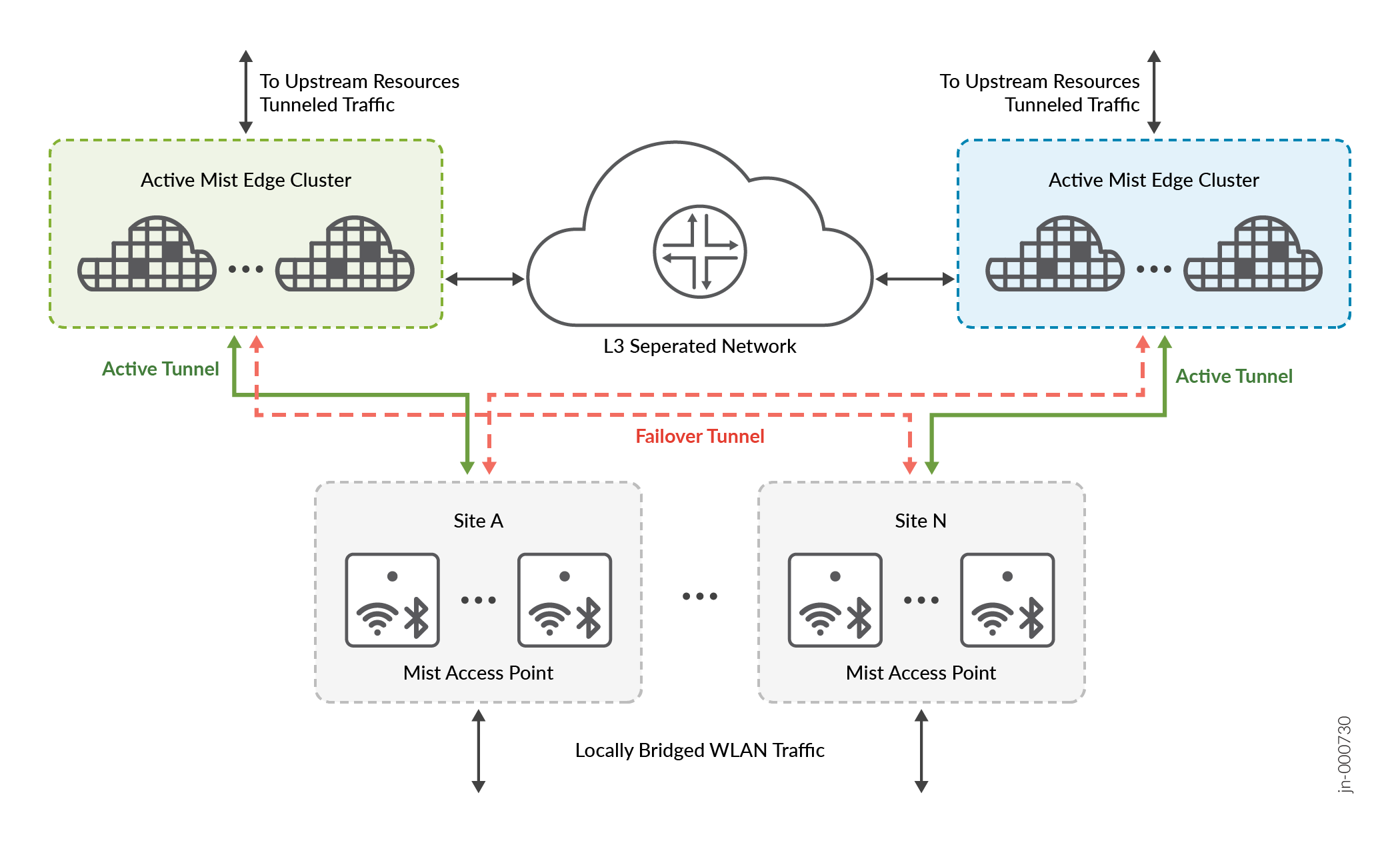
The user interface provides the capability to handle up to two cluster failovers, making it an optimal solution for most campus deployments. However, if additional levels of failover protection are necessary, this can easily be accomplished through API integration, allowing for custom configuration to meet specific requirements.
In the case of distributed datacenters, separated geographically, Site A geographically closer to data center A, can be assigned Mist Cluster A as the primary cluster and Mist Cluster B in data center B and the secondary cluster. Site B can be assigned to actively terminate tunnels on cluster B, which serves as primary cluster and uses cluster A as secondary cluster. Refer to the diagram and configuration below.
AP does not form concurrent tunnels to a secondary cluster member, dotted lines are for illustration only.
.png)
The configuration for the above deployment can be achieved using the UI on the Mist Tunnel page. Select the tunnel and configure the Primary and Secondary cluster options. The same tunnel object can be used for mapping the tunneled WLAN, found in WLAN configuration, at multiple sites which need to have “Mist Cluster A” as the preferred cluster and “Mist Cluster B” for L3 redundancy. Mist APs do not support simultaneous active and standby tunnels.
Details about how to configure Mist Edge cluster/clusters are explained in the centralized deployment section.
Low-Level Design
The low-level design (LLD) phase provides the granular detail necessary for implementation, transforming the high-level blueprint into actionable configurations. This includes specifying the exact Juniper EX Series Switch models for each network layer, along with precise port assignments for connected devices and uplinks. For the wireless component, specific Juniper Access Point (AP) models will be chosen, and their precise mounting details and power requirements (for example, PoE) will be documented. Comprehensive cabling requirements, encompassing Ethernet types (Cat6a for multi-gigabit) and fiber specifications, will be outlined. Detailed VLAN configurations will be defined, along with the selection and configuration of routing protocols such as OSPF, BGP, or advanced EVPN-VXLAN for scalable and flexible campus fabrics. Wireless SSID configurations will cover authentication methods (for example, WPA3-Enterprise), encryption standards, and Quality of Service (QoS) policies to prioritize critical applications. Furthermore, explicit security policy definitions, including firewall rules and access control lists, will be documented. Finally, the LLD will detail high availability and redundancy mechanisms, such as Juniper's Virtual Chassis technology for switches or Easy EVPN LAG (EZ-LAG), to ensure network resilience and uptime.
- Specific Juniper EX Series Switch models and port assignments.
- Juniper Access Point (AP) models and mounting details.
- Cabling requirements (Ethernet, fiber, PoE).
- Detailed VLAN configurations, routing protocols (OSPF, BGP, EVPN-VXLAN).
- Wireless SSID configurations (authentication, encryption, QoS).
- Security policy definitions (firewall rules, access control lists).
-
High availability and redundancy mechanisms (Virtual Chassis, EZ-LAG).
Licensing and Subscriptions
This section outlines the necessary Juniper licensing and subscription requirements to enable the full functionality of the AI-Driven wired and wireless solution. It is crucial to identify and procure the appropriate Juniper Mist Cloud subscriptions, which are fundamental for leveraging Mist AI capabilities such as WiFi Management and Assurance, Marvis for Wired Network, Marvis for Wireless, and Location Services. These subscriptions activate the cloud-managed intelligence and automation that are central to Juniper's offering. Additionally, this section covers any specific licenses required for the Juniper EX Series Switches and Juniper Access Points themselves, ensuring all hardware components are properly licensed for operation within the Juniper ecosystem and can fully integrate with the Mist Cloud services. Proper licensing ensures access to features, support, and ongoing updates.
- Juniper Mist Cloud subscriptions
-
Switch and AP licenses

