Enable Guest Portal Single Sign-On Access with OneLogin™ (One Identity)
Use this information if you want to integrate with OneLogin™ to authenticate guest users.
Juniper Mist supports SAML 2.0 for device authentication onto the network. As such, you can set up a Single Sign-On (SSO) WLAN for guest access using OneLogin™ (now One Identity) as the Identity Provider (IdP). SAML SSO allows users to log on once to their identity provider, and then seamlessly access multiple other web applications without having to log in again. Both Juniper Mist guest portal and OneLogin support RADIUS EAP-TTLS/PAP and EAP-PEAP/MSCHAPv2 authentication methods.
Before you begin setting up the Guest Portal, you should have admin credentials for your OneLogin portal and already have a SAML application (or be ready to create one).
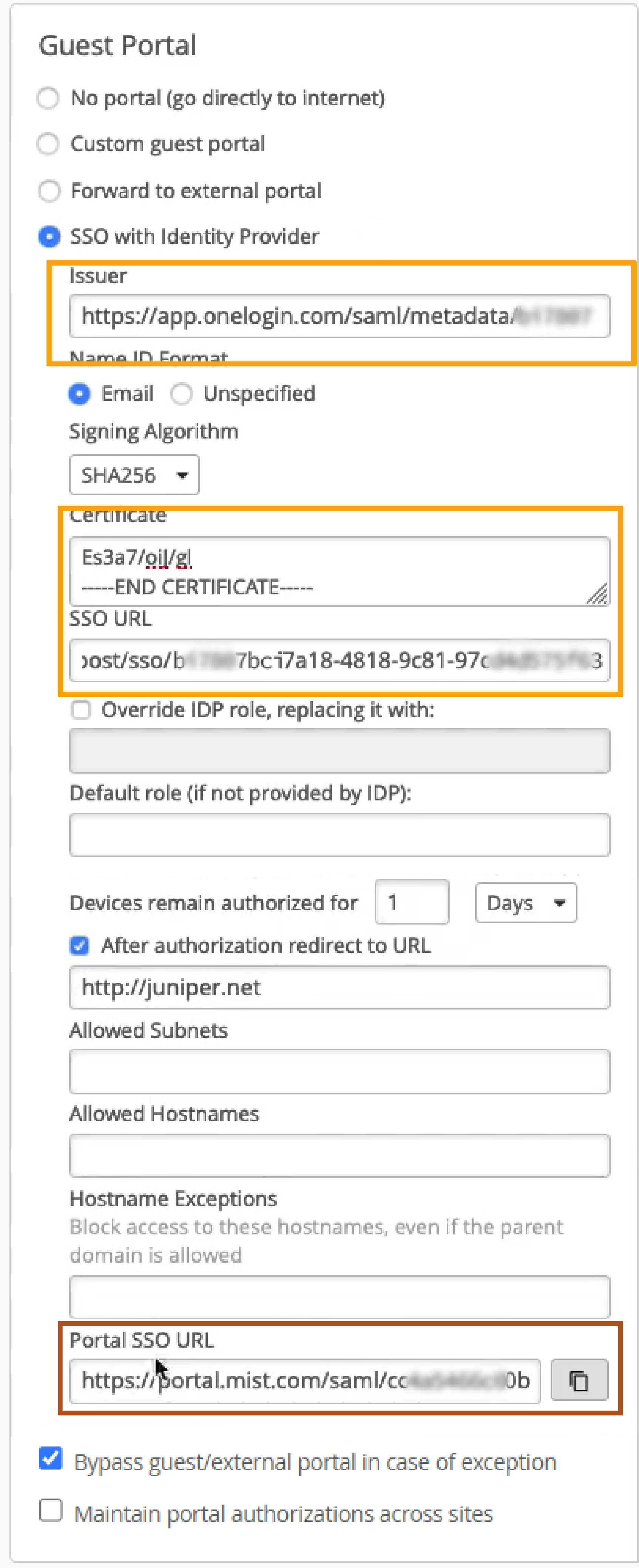
You'll need the following information from the OneLogin SAML application (Figure 1) to configure the OneLogin SSO in the Juniper Mist portal (Figure 2).
In addition, you'll need to copy the Portal SSO URL from the Mist portal to your OneLogin application to complete that side of the setup (the Portal SSO URL doesn't get created until after you save the initial WLAN configuration, so you actually loop back to the WLAN configuration page).
-
For the OneLogin application, the Signature Algorithm should be set to SHA-256. At the same time as you make this change, you can copy and save the X.509 Certificate for later use in the Juniper Mist portal. The x.509 certificate is the public certificate that establishes trust between OneLogin and your Juniper Mist Guest Portal.
-
From your OneLogin application, copy and save the values shown for Issuer URL and SAML 2.0 Endpoint. You may need to change the SAML Issuer type field for these options to be available. See SAML Custom Connector Advanced.
Figure 1: OneLogin SAML App SSO Configuration Screen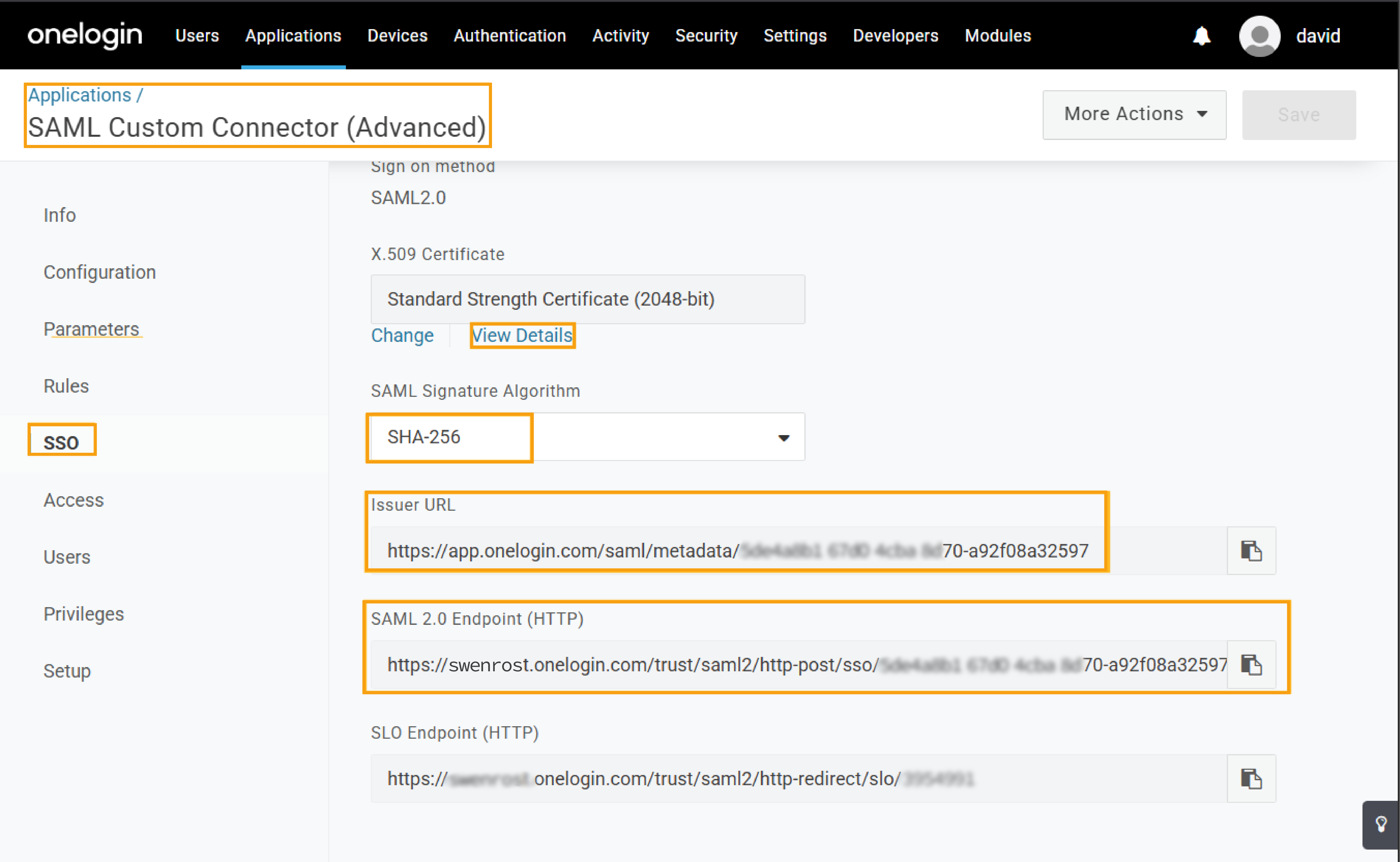
To set up a WLAN with SSO access from OneLogin: