Monitor SRX Series Firewall Deployed as WAN Edge
Use the WAN Edges page, the Insights page, and the Alerts page to quickly find device information, event details, and alerts for your SRX Series Firewalls.
In monitoring a Juniper® SRX Series Firewall deployed as a WAN edge device, you’ll explore the most efficient ways to monitor your WAN edge device in the Juniper Mist™ portal following your initial deployment phase.
Monitoring WAN Edges
From the left menu, select WAN Edges WAN Edgesto view basic device monitoring information. Notice the organization name at the top of the portal. This is the largest container and represents your entire organization. Beneath the organization name, you can see your site devices in either a List format or a graphical Topology format.
In this example, Live Demo is your organization, and LD_CUP_SRX_1 is the selected WAN edge device.
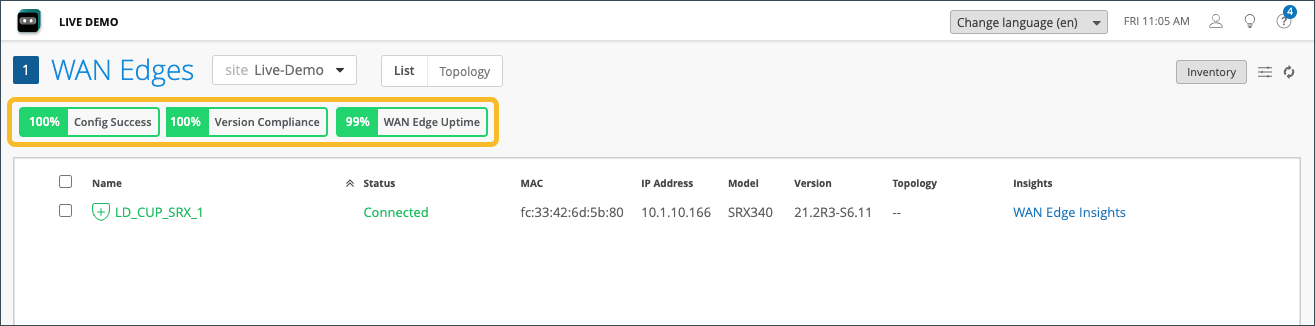
The tiles across the top provide high-level information:
- Config Success—Percentage of online WAN edges with successful configuration.
- Version Compliance—Percentage of WAN edges that have the same software version per model.
- WAN Edge Uptime—Percentage of time a WAN edge was up during the past seven days, averaged across all WAN edges.
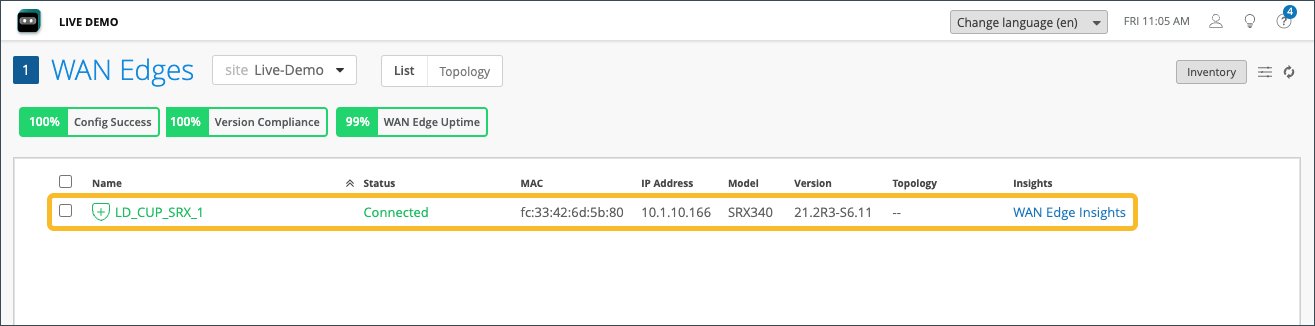
Beneath, you'll find WAN edge device details as shown in Table 1.
| Fields | Description |
|---|---|
| Name | Name |
| Status | Connected or disconnected |
| MAC | MAC address |
| IP Address | IP address |
| Model | Juniper Networks® SRX Series Firewalls or Juniper® Session Smart™ Routers. |
| Version | SRX Software Version |
| Topology | Hub or Spoke |
| Insights | Provides a direct link to the WAN Edge Insights page. |
The Topology format presents the same information as the List view. For example, if you hover over the LD_CUP_SRX_1 device, you'll see the same information that displayed in the List view.
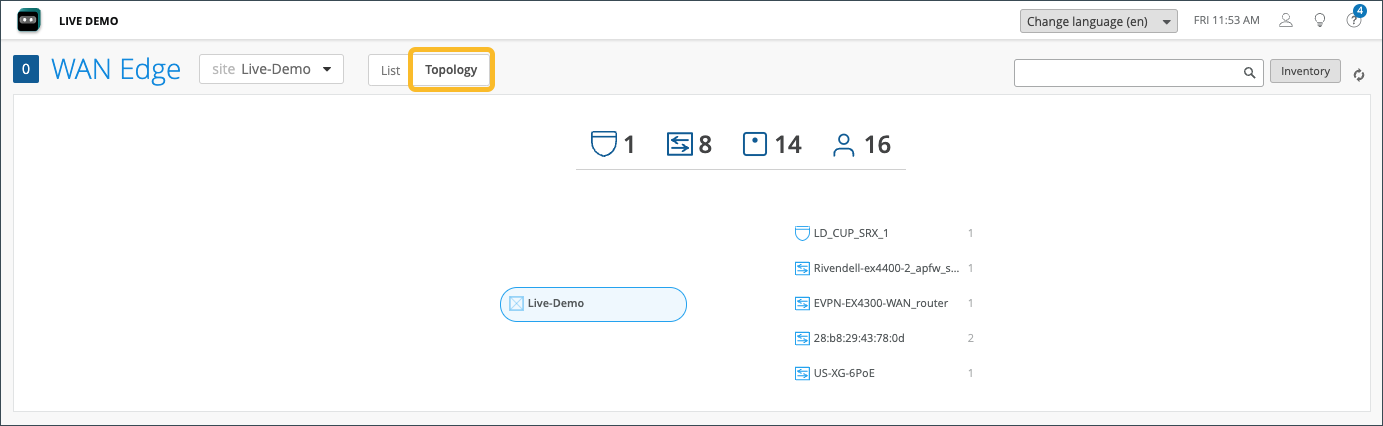
On both the List and Topology view, selecting your WAN edge device (LD_CUP_SRX_1 in this example) brings you to its Device Information page. The Device Information page provides different categories of monitoring information for your WAN edge device.
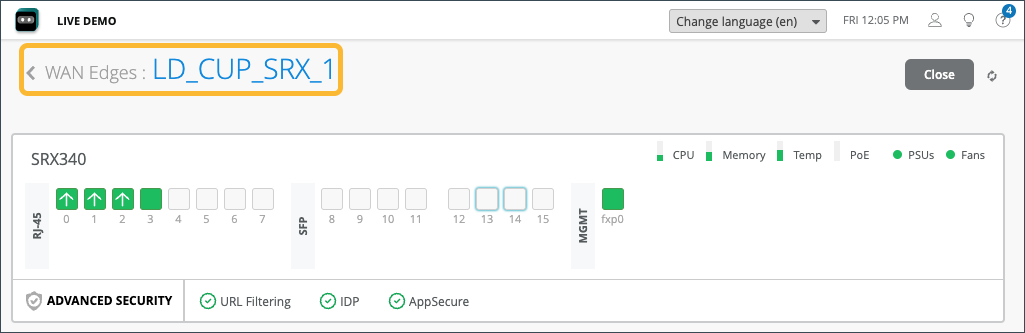
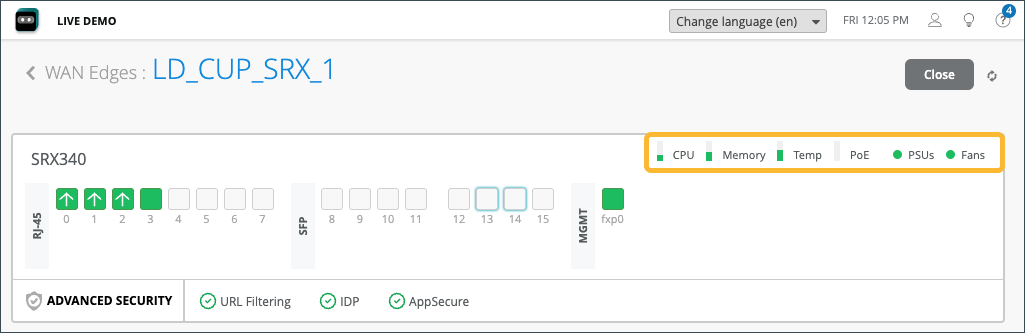
The first thing you’ll notice on the Device Information Page are details about the WAN edge device you selected, (LD_CUP_SRX_1 in our figure). The information includes a graphical front view of the device ports and baseline status information such as CPU and memory utilization.
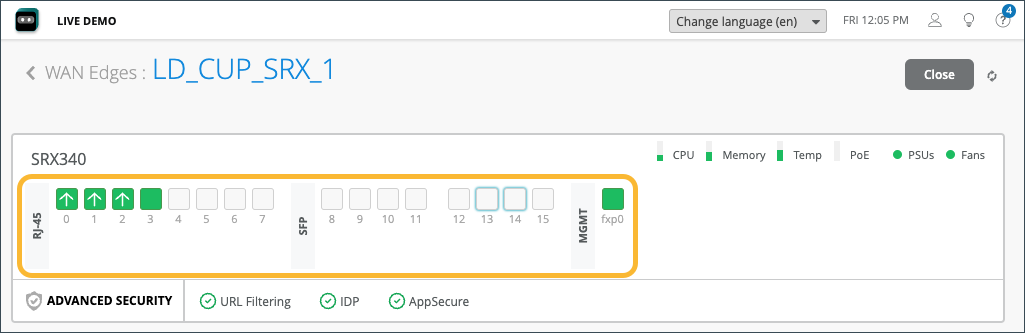
For each Gigabit Ethernet interface, you’ll find link information.
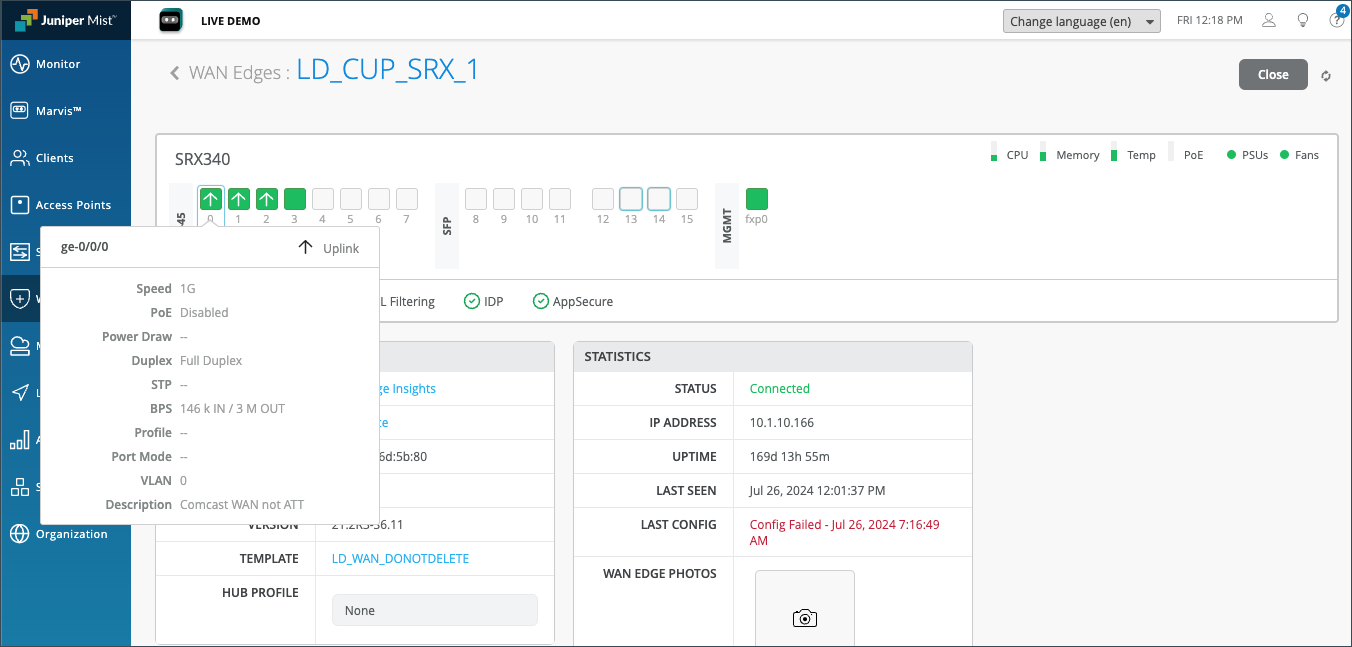
| Fields | Description |
|---|---|
| Speed | Rated speed |
| PoE | Enabled or disabled |
| Power Draw | Measured PoE power draw |
| Duplex | Full or half |
| STP | True or false |
| BPS | Bits/second |
| Profile | The name of the Port profile assigned to the port |
| Port Mode | The mode of the port profile configuration (Trunk, Access, Port Network, or VoIP Network) |
| VLAN | VLAN tag |
| Description | Interface description |
The CPU, Memory, and other status icons indicate how your device behaves. Hover over each status icon for deeper insights.
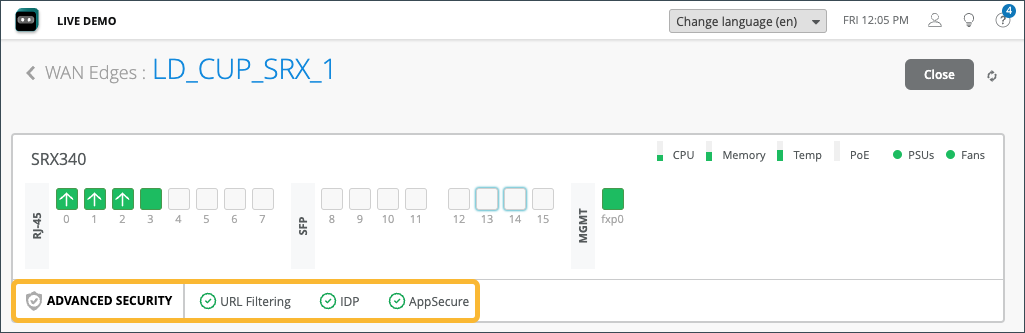
Advanced Security information is listed below the device ports with a check mark or an X, indicating whether URL filtering, intrusion detection and prevention (IDP), or AppSecure (for application visibility) is active on this device. Here, URL filtering, IDP, and AppSecure are active with the green check mark.
Below the port information and security section, you’ll find generalized data for your WAN edge device, including:
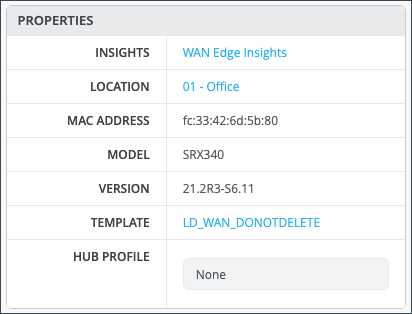
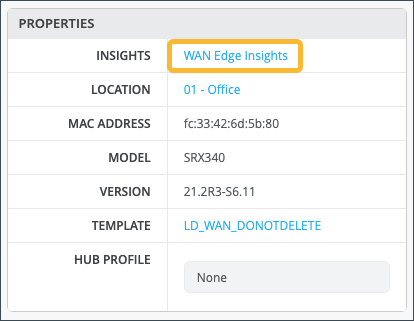
Properties contains generalized platform-related information.
| Field | Description |
| Insights | Provides a direct link to WAN Edge Insights. |
| Location | Provides floorplan information. |
| MAC Address | MAC Address for the SRX device. |
| Model | Indicates if model type is SSR or SRX. |
| Version | Version of SRX Software. |
| Template | The WAN edge template applied to the device. |
| Hub Profile | The Hub Profile applied to the device. |
Statistics displays action information about your platform.
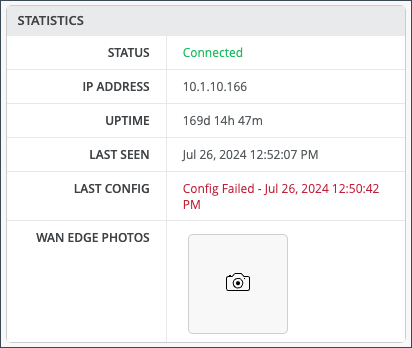
| Field | Description |
| Status | Connected/Disconnected |
| IP Address | The IP address of the WAN edge device |
| Uptime | Day/Hour/Min uptime information |
| Last Seen | Last login |
| Last Config | Last Commit |
| WAN Edge Photos | Photos of the WAN edge device |
If you configured DHCP servers on the WAN router itself, there will also be a DHCP Statistics pane with information about the leased IPs.
-
DHCP Statistics presents IP information related to dynamic distributed IP addresses.
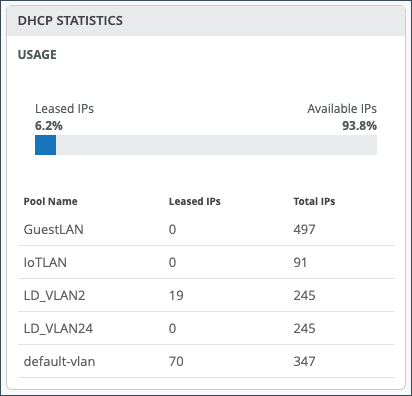
| Field | Description |
| Usage | The total figure presented as a percentage of Leased and Available IPs. |
| Pool Name | The name for given pool of addresses. |
| Leased IPs | Number of used IP addresses in each pool. |
| Total IPs | Total number of available IP addresses in each pool. |
Scrolling down the Device Information page, you’ll find configuration information for your WAN edge. Usually, WAN edges inherit templates or profiles. However, you can make individual changes to the configuration to be pushed to the device. In this example, a standalone WAN Edge Template was used.
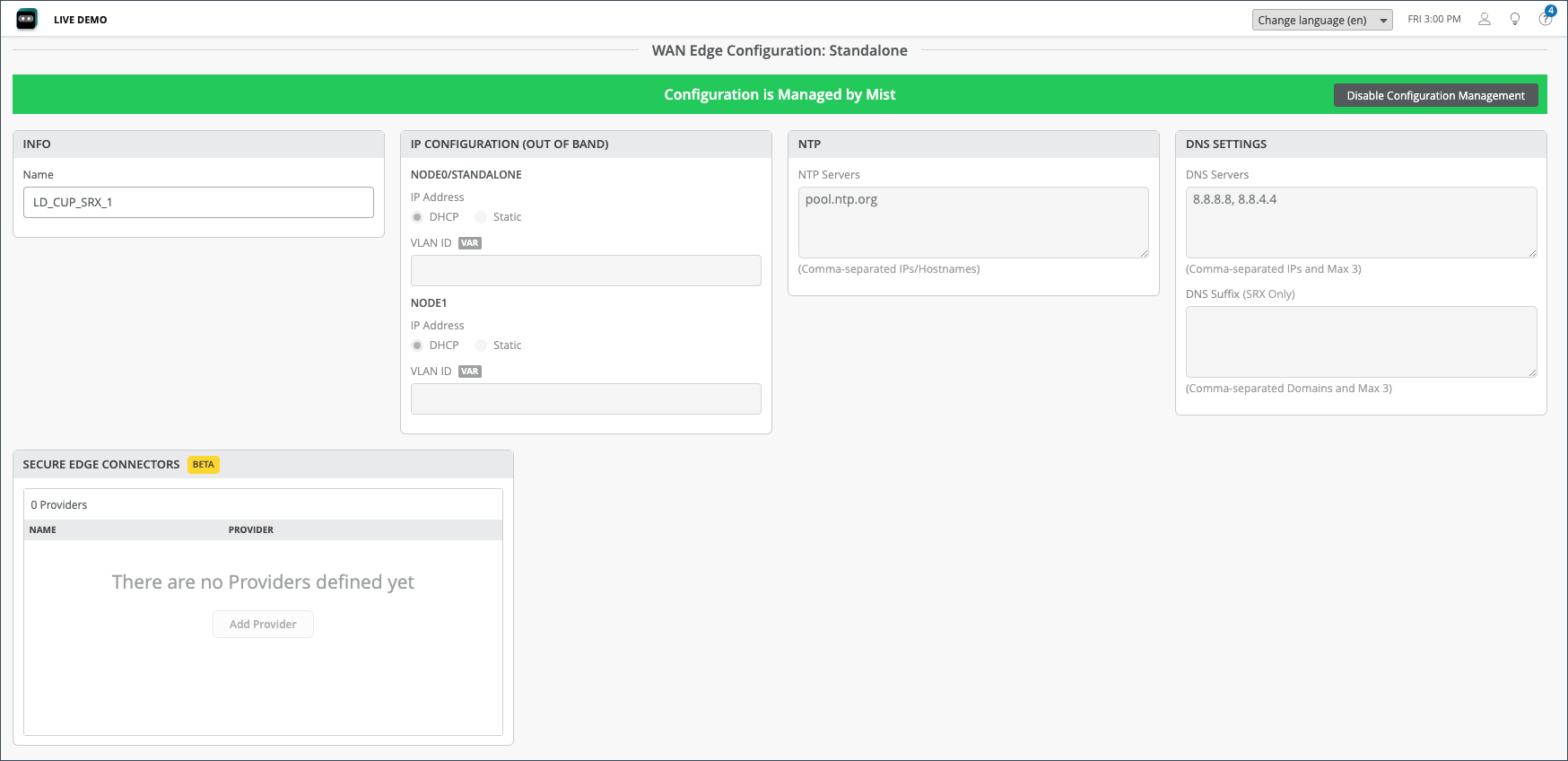
| Field | Description |
| Info | The name of the SRX device. |
| IP Configuration | Node0/standalone DHCP/Static, VLAN ID, node 1 DHCP/Static, VLAN ID. |
| NTP | Time Servers IP/Hostnames. |
| DNS Settings | DNS Servers, DNS Suffix (SRX only DNS suffix info). |
| Secure Edge Connectors (BETA) | Provider for the Secure Edge Connector. |
Scrolling past the configuration, you’ll find information for your connected WANs and LANs.
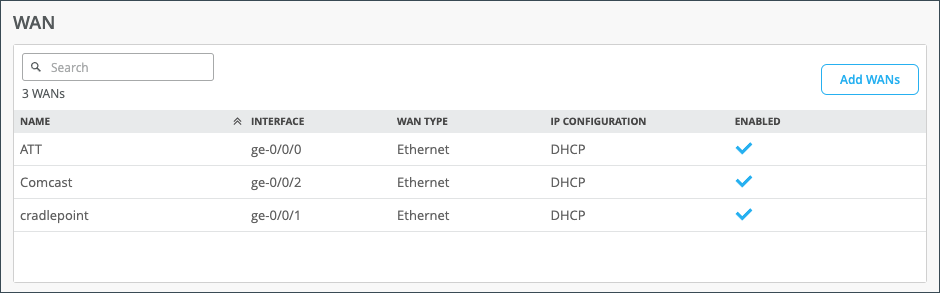
| Field | Description |
| Name | Selected WAN Interface Name |
| Interface | Supports one of these interfaces for aggregation: ge-0/0/1, ge-0/0/1-5, or reth0. |
| WAN Type | Ethernet, DSL (SRX Only), or LTE |
| IP Configuration | DHCP, Static, or PPPoE |
| Enabled | Check mark indicates that the interface is enabled. |
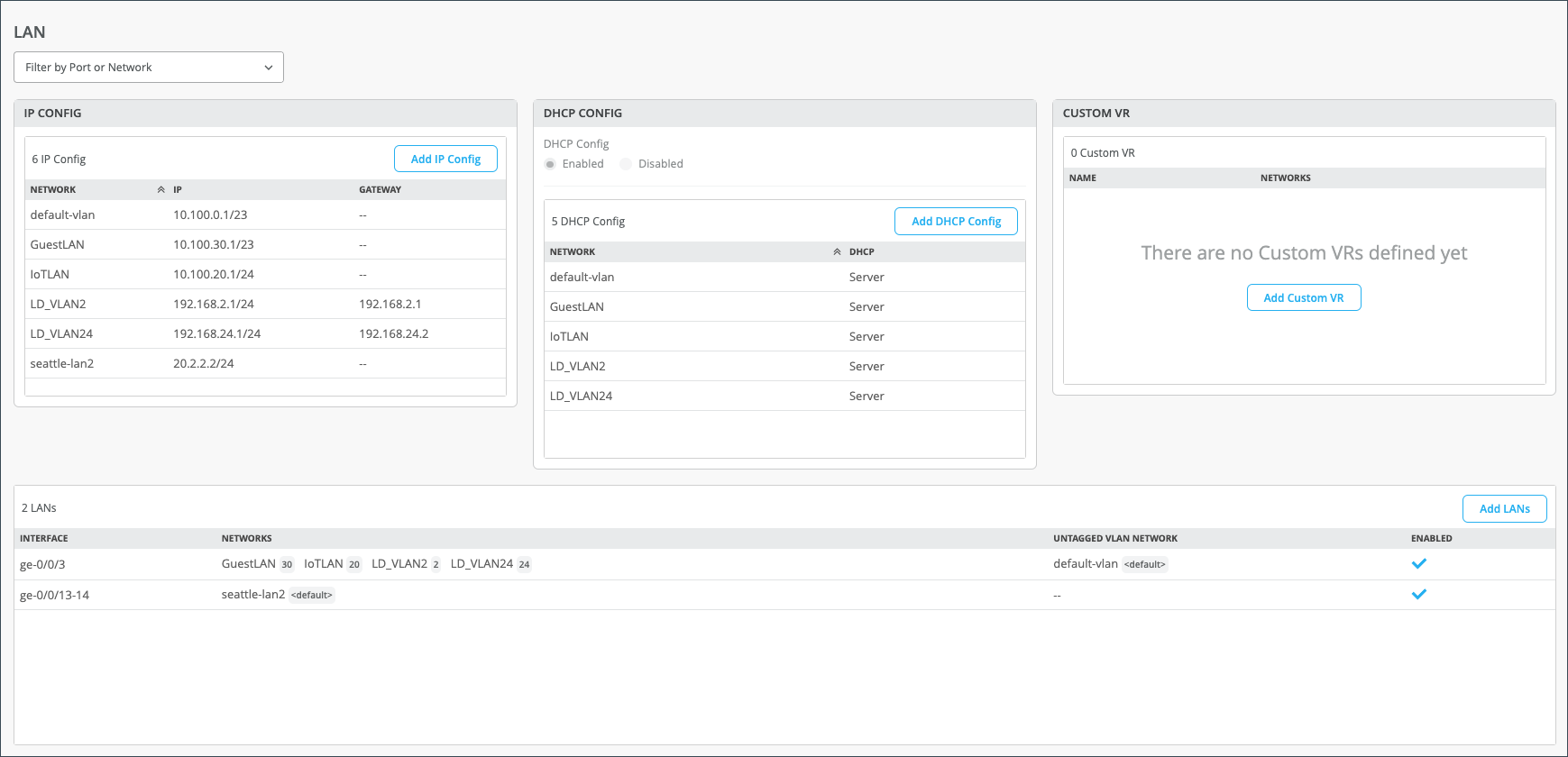
| Field | Description |
| IP Config | Network, IP Address, Prefix Length. |
| DHCP Config | Server or Relay. |
| Custom VR | A virtual router that you can configure to be used in automatic route leaking. |
| LANs |
|
Scrolling down, you have sections for Traffic Steering, Application Policies, and Routing (OSPF, BGP, Routing Policies, and Static Routes).
The Traffic Steering and Application Policies sections show how you use the SRX Series Firewall to create rules for path preference and routing behavior. Note that on the SRX Series Firewall deployed as a WAN edge, the Application Policy and Traffic Steering path determine destination zones and must be assigned.
Traffic Steering enables you to define different paths that traffic can take to reach its destination. Traffic Steering policies allow you to specify the paths for traffic to traverse, as well as the strategies for utilizing those paths.
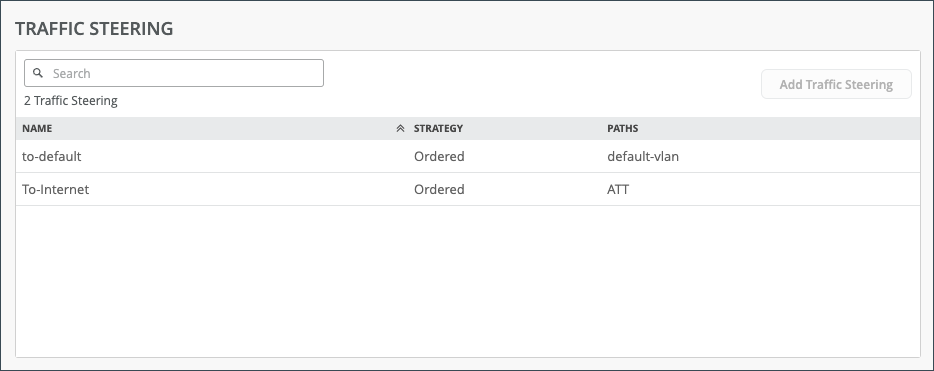
| Field | Description |
| Name | The name of the Traffic Steering policy. |
| Strategy | Ordered, weighted, ECMP. |
| Paths | LAN, WAN, Untagged VLAN (SRX only). |
Application Policies are security policies in the Juniper WAN Assurance design, where you define which network and users can access which applications, and according to which traffic steering policy. You must create Networks, Applications, and establish Traffic Steering profiles to define an Application Policy. These elements become matching criteria to allow access to or block access from applications or destinations.
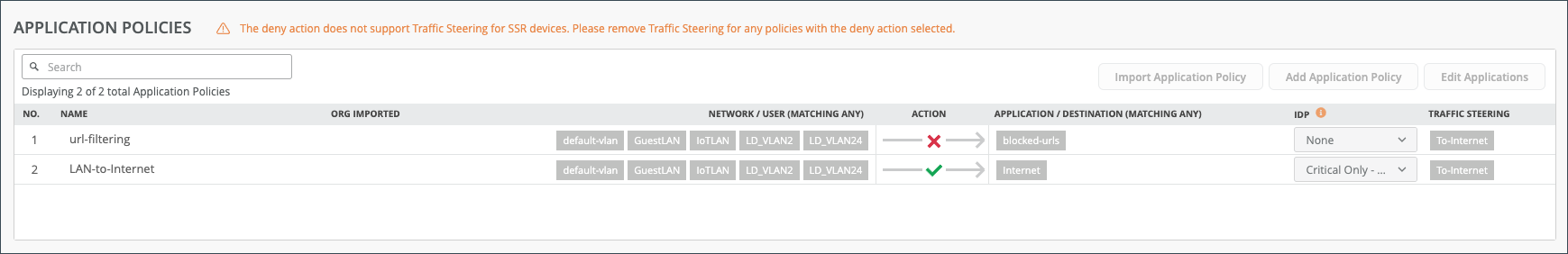
In the Juniper Mist™ cloud portal, the Networks or Users setting determines the source zone. The Applications and Traffic Steering settings determine the destination zone. Traffic Steering paths determine the destination zone in Juniper Networks® SRX Series Firewalls, so ensure that you assign Traffic Steering profiles to the Application Policies.
| Field | Description |
| Number | Ordered Policy Number |
| Name | Application policy name |
| Org Imported | Indicates if the policy was pushed down from the Organization level to the Site. |
| Network/User (Matching Any) | The “source” of your traffic |
| Action | Allow/Block |
| Application/Destination (Matching Any) | The “destination” for your traffic. |
| IDP | Indicates IDP/URL filtering (requires separate license) |
| Traffic Steering | Indicates path for traffic |
Open Shortest Path First (OSPF) is used to determine the best path for forwarding IP packets. OSPF segments a network to improve scalability and control the flow of routing information. See OSPF .
|
Field |
Description |
|---|---|
|
Area |
The identification area that your OSPF network or SRX Series Firewall belongs to. |
|
Type |
This is the OSPF Area type. Select Default (Area 0), Stub, or Not So Stubby Area (NSSA). |
|
Networks |
The name of your OSPF network. |
| Enabled |
Selecting this check box causes the Enable OSPF Areas button to become selectable. |
You can configure Border Gateway Protocol (BGP) for your SRX Series Firewall deployed as a WAN edge device. You can also manually add a BGP Group here.
| Field | Description |
| Name | BGP Name |
| Peering Network | The type of network being used for your BGP peering (WAN or LAN). |
| Type | Type of BGP Route (Internal or External) |
| Local AS | Autonomous System Number |
| Export | Export Route |
| Import | Import Route |
| Neighbors | Neighbor Route |
| Neighbor AS | Autonomous System Number for Neighbor Route |
The Routing Policies section enables you to configure path preference and allows you to determine traffic behavior.
|
Field |
Description |
|---|---|
|
Name |
The name of your routing policy. |
|
Terms |
These are the policy conditions such as prefix, routing protocol, and actions. |
Static routes allow you to manually define the routes that your SRX Series Firewall deployed as a WAN edge device will use.
|
Field |
Description |
|---|---|
|
Name |
The name of your static route. |
|
Gateway |
The gateway that your static route will use when routing traffic. |
View Device Information and WAN Edge Insights
WAN Edge Insights
The Properties pane for your selected WAN edge links to WAN Edge Insights. Click WAN Edge Insights for the next level of information about your WAN edge device.
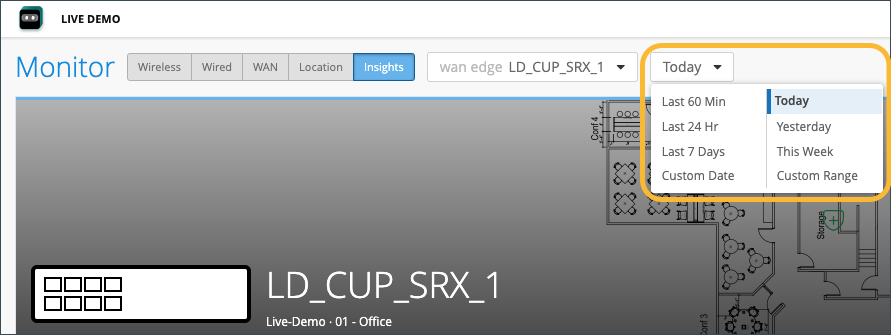
Next to the selected WAN edge (LD_CUP_SRX_1) on the Insights page, you can select a time frame for selected information. The default view is Today, but this can be set to a customized date or range of dates. Below this, you find (when the site location information is configured) where this WAN edge is configured via a street map.
With your time frame selected, WAN Edge Events displays a time line of the traffic through the WAN edge during your specified time, and also displays a list of events.
Select a specific event in the listed WAN Edge Events for greater detail of the Good, Neutral, and Bad events.
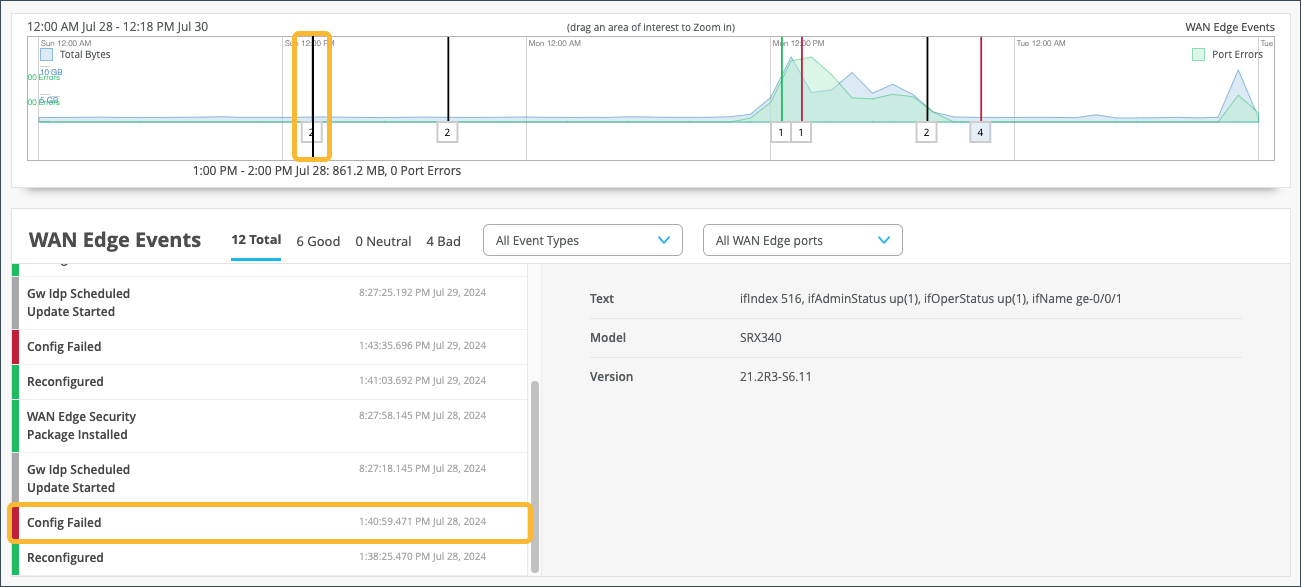
Your selection expands and displays detailed information about the selected time.
For a detailed portion of time, select a window of time with the mouse cursor. By doing this, you’re able to adjust the window of events and isolate specific Good, Neutral, and Bad occurrences that happened on your network. With a smaller section, you’ll get a more detailed view of that period.
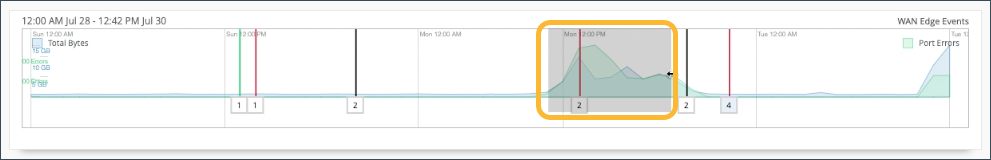
Scroll down on the WAN Edge Events page for deeper insights within your selected period.
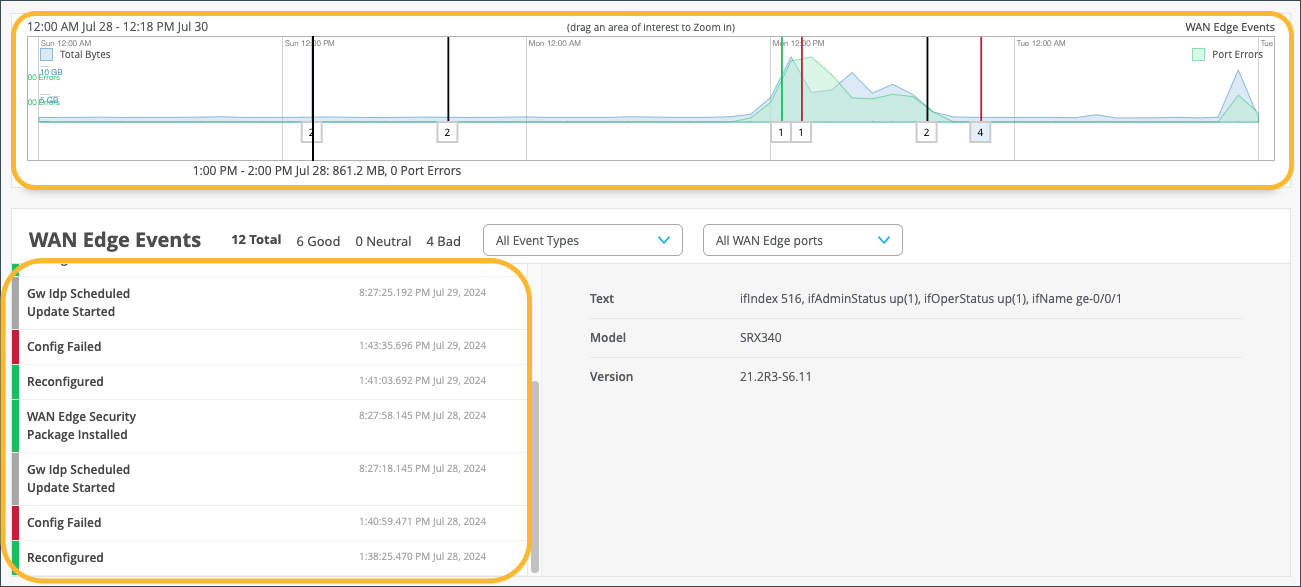
In the WAN Edge Events, you can narrow down the type of event by selecting a modifier in the Event Type drop-down menu. You can also filter your search by limiting the event types to a specific port.

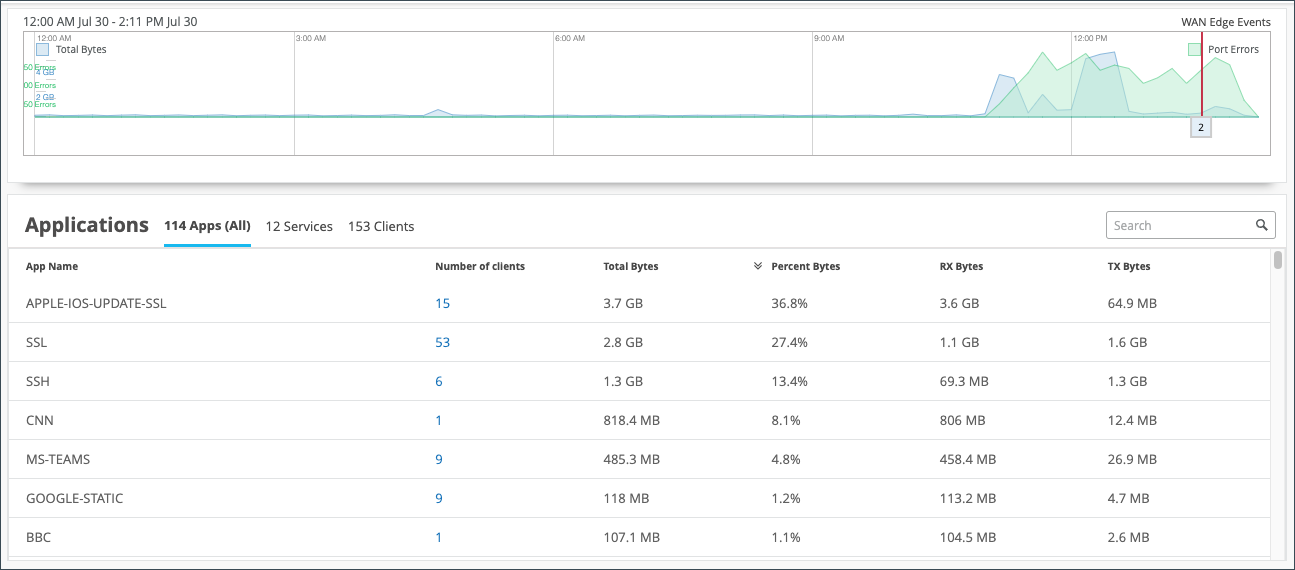
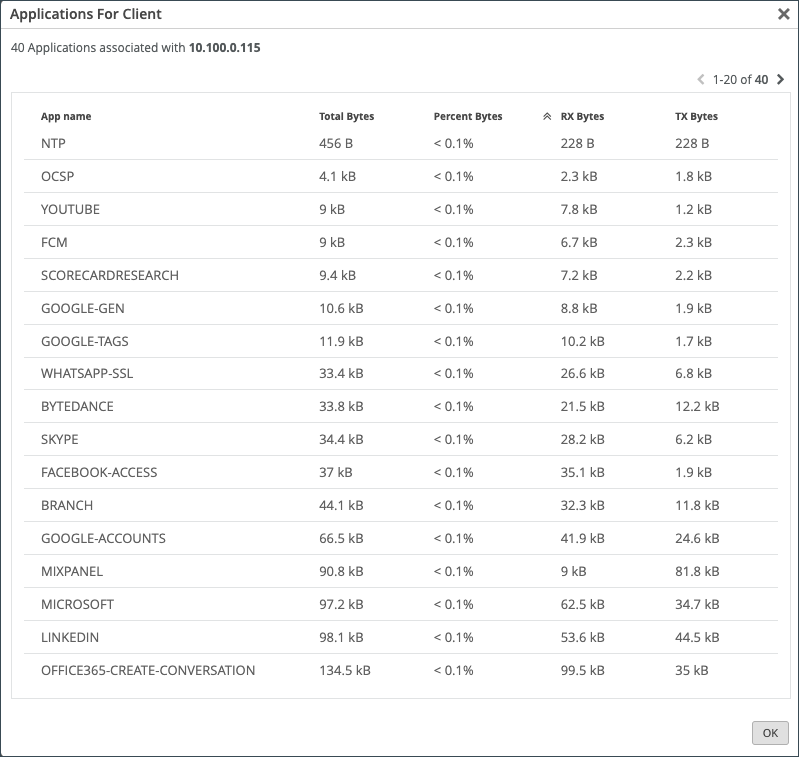
On the WAN Edge Events page, you can also view reports on applications on the Applications pane. On this pane:
- You can use the applications pane to monitor and troubleshoot specific application behavior.
- You can hover over the App Name to see more details about the services.
- You can view a client's use of a particular application by clicking the Clients tab.
Ensure you’ve had a few hours for these metrics to be populated following initial deployment.
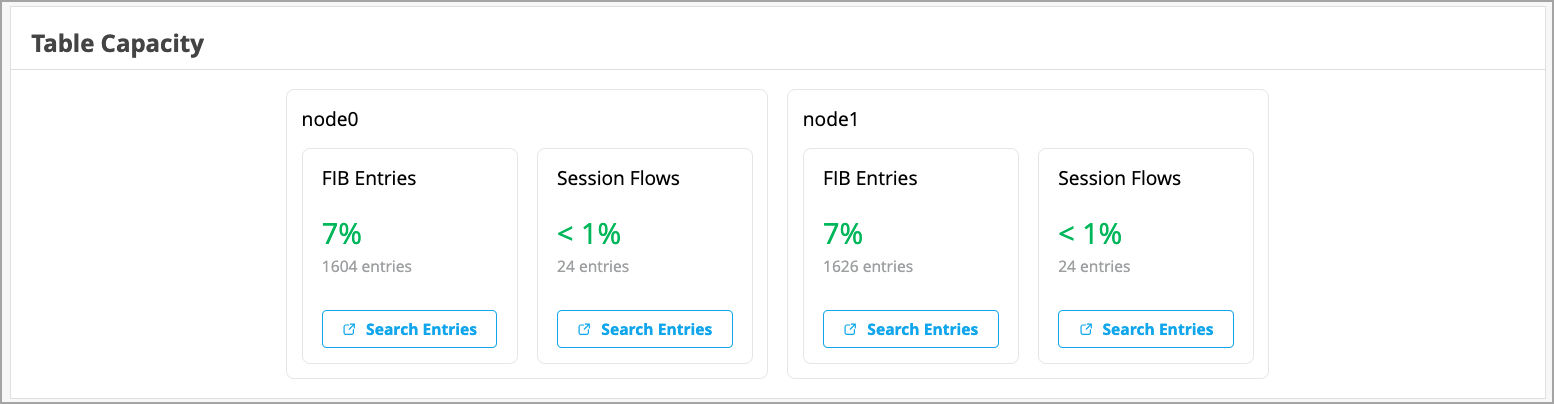
The WAN Edge Insights page provides the following indicators in the Table Capacity section:
-
FIB Entries: Displays the current number of FIB entries and the percentage of utilization; essentially showing how much of the available FIB space is currently being used.
-
Session Flows: Displays the current number of active sessions and the percentage of session flow utilization based on the device's capacity.
In the case of a high availability cluster, Table Capacity indicators are displayed for each node.
You can also click the Search Entries button under each metric to open a shell view in a new window where you can search for entries after specifying filters.
In the Number of Clients column, you can click on the number to see more information about the clients using the application such as the Client name, MAC Address, IP Address, Device Type, and Bytes being used.
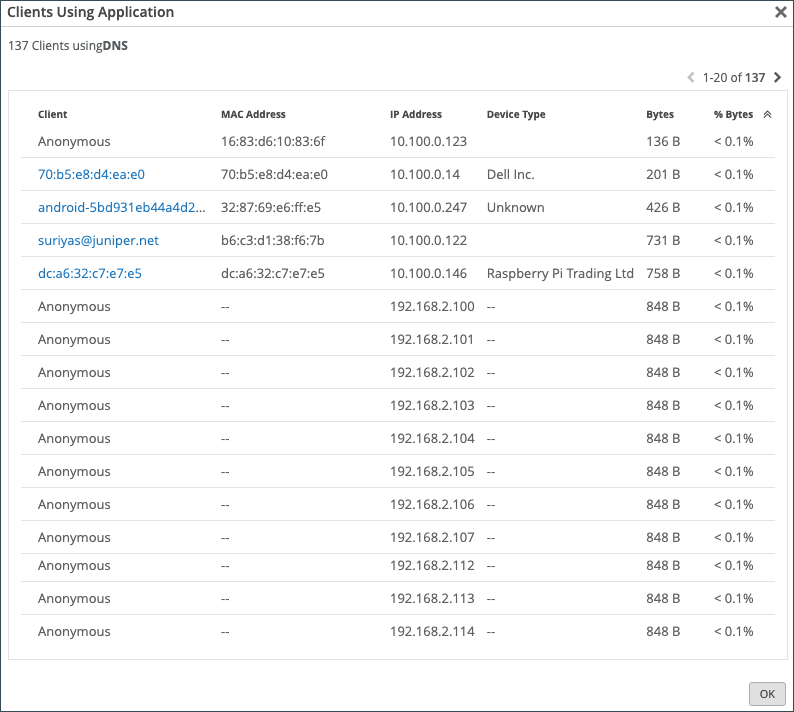
For SRX Series Firewalls deployed as a WAN edge running a DHCP server, clients using that application will display a HostName in the Client column if available. Otherwise, the MAC address will be displayed. Device Type and MAC Address columns will be populated as well.
Back on the Applications pane, you can click the Clients tab to see how much bandwidth a particular client is using. You can click the number in the Number of applications column to see more information.
The Application Path Insights (BETA) section shows you which applications are using the most bandwidth according to the selected Application Policy and Network. It displays the effective application flow over the path for the selected Application Policy. You can also change the Data Type to Sessions to see the number of sessions occurring per application. Hover over a section of the graph to view the bandwidth or sessions per application as well as jitter, loss, and latency.
The Application Path Insights visualization data is available only if the configuration is managed by Juniper Mist.
Have you ever been on an important Zoom or Teams call and experienced jitter or latency? This is a bad experience for anyone, but if you're the network operator, it's even worse. You don't want the CEO yelling at you because their shareholder meeting went bad. With Juniper's WAN Assurance Application Insights dashboard, you could do something about it.
This dashboard shows you which applications are using bandwidth at any given time. Given those insights, you can easily set policies to remediate issues, such as prioritizing some applications, blocking others, or working with your ISP to gain more bandwidth. Application Insights dashboard also lets you verify that your policies were configured correctly, and you can easily see the top 10 applications by bandwidth utilized, quickly adding and removing applications from this list.
And that's the power of WAN Assurance App Insights in 60 seconds.
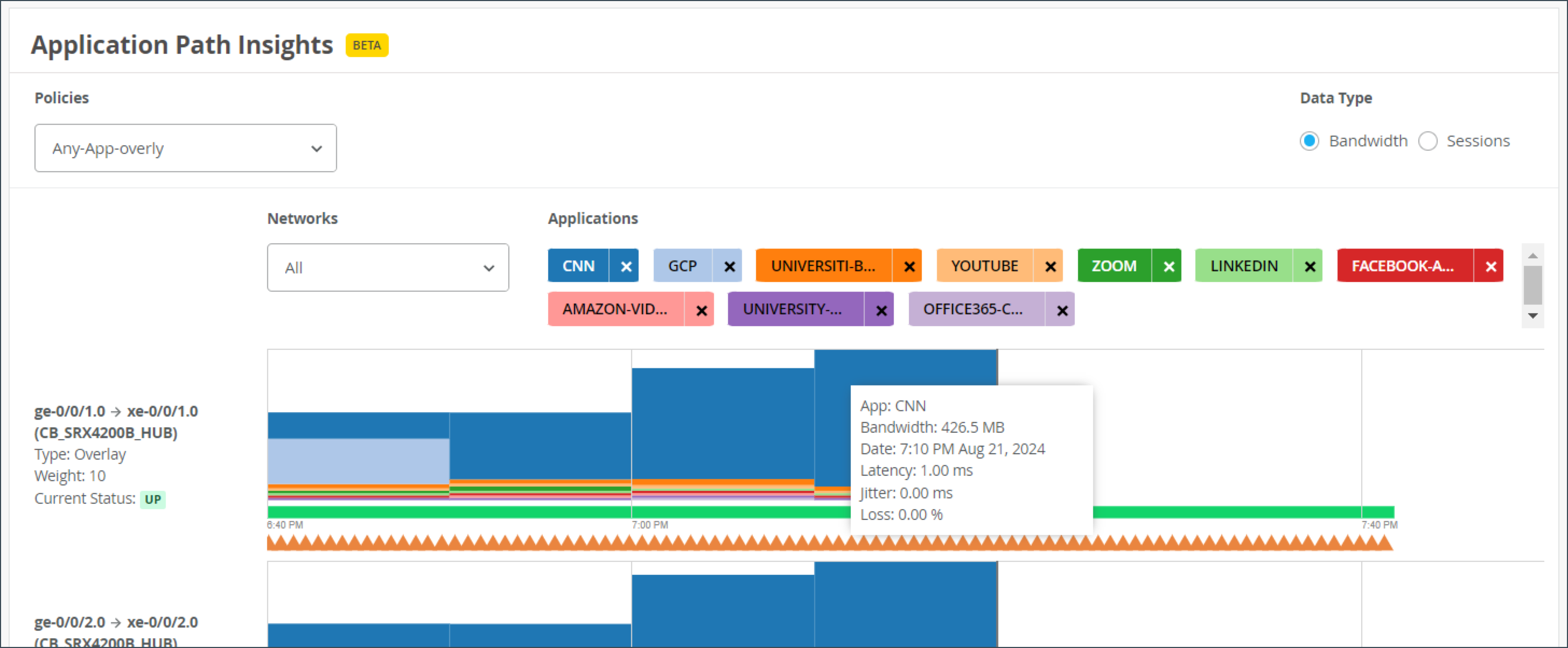
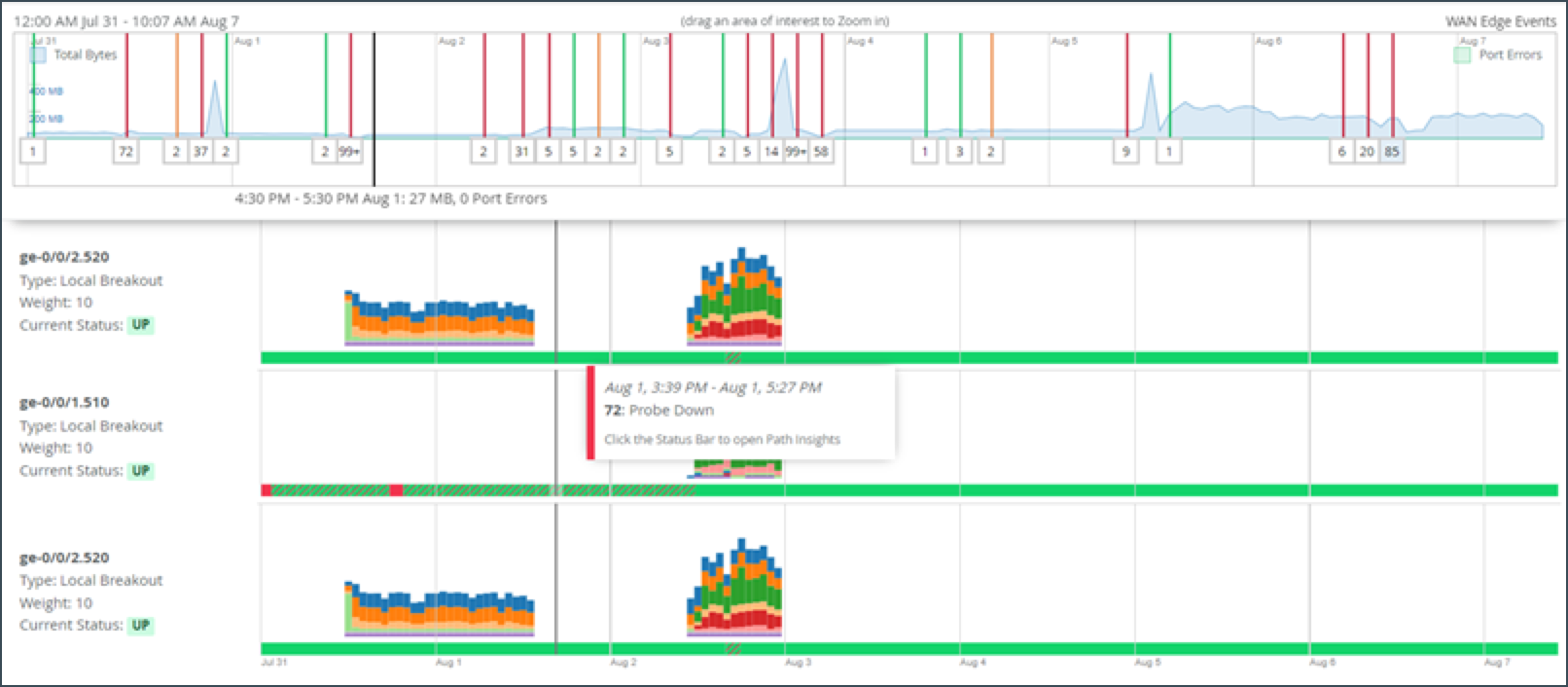
The path state bar shows path state information over a timeline, and path state events are indicated by segments highlighted in different colors. For example, Path Up events are shown in green and Path Down events are shown in red.
You can hover over the highlighted portions of the path state bar to view a summary of path state events.
The Application Path Insights section also includes a summary view on the lefthand side that displays recent path state events.
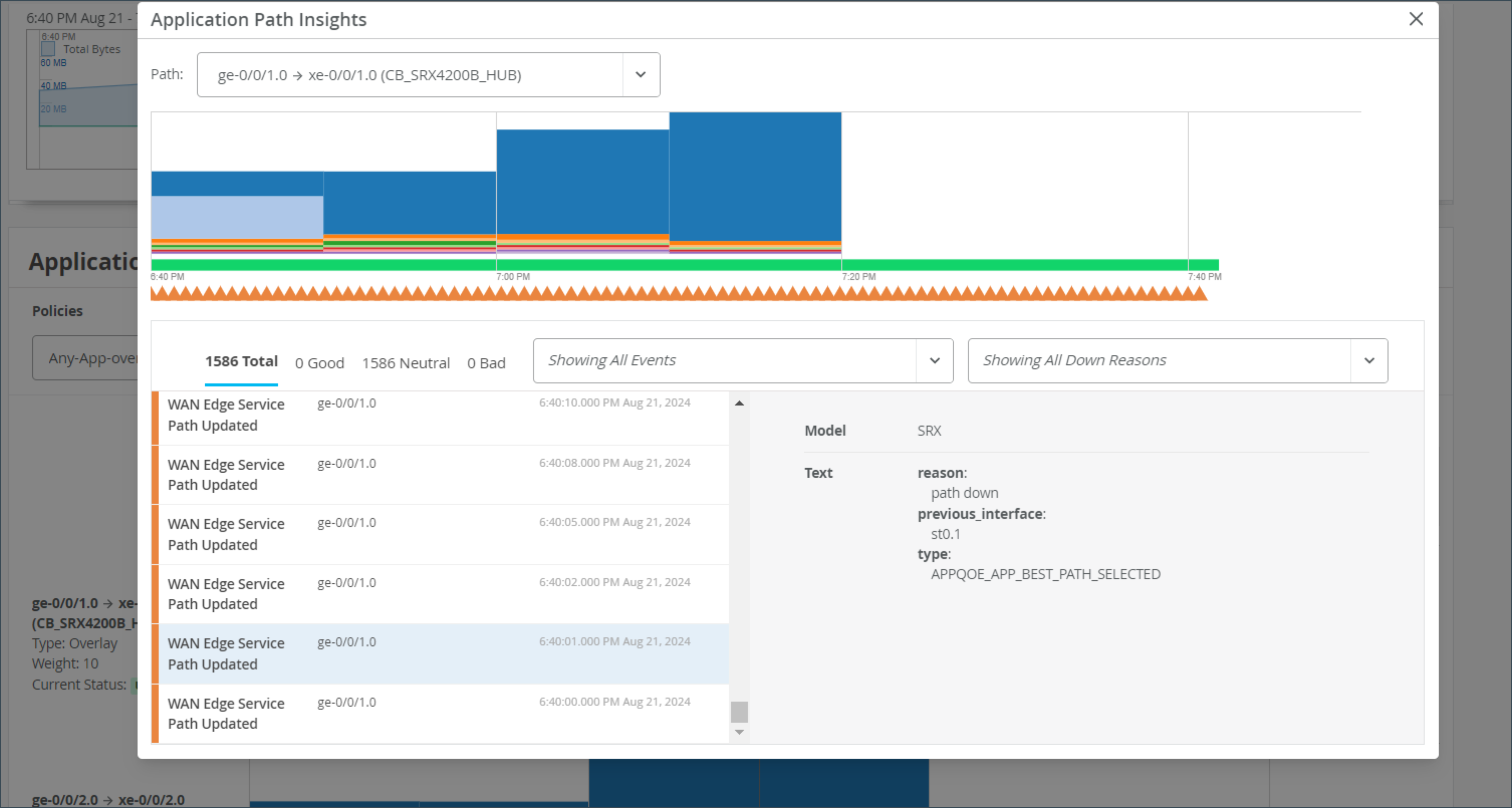
If you click on the bar, you will get a pop-up window where you can view more detailed information about the path state events. The list of events displays on the left and when you select an event, the reason for the event displays on the right.
Path state events include:
- Path Update
- Port Up
- Port Down
- Path Up
- Path Down
Path state reasons include:
- Probe Down
- Peer Path Up
- Peer Path Down
- Config Change
- Best Path Selected
- SLA Metric Violation
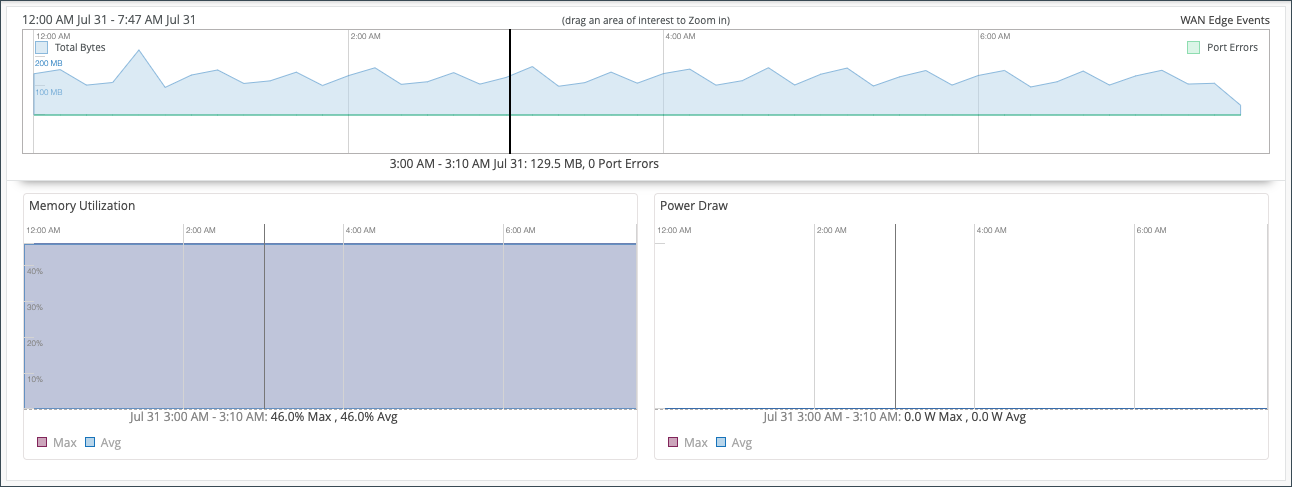
The WAN Edge Device Charts include Control Plane CPU, Data Plane CPU, Memory Utilization, and Power Draw.
The Control Plane CPU and Data Plane CPU charts show you the percentage of CPU utilization for both max and average.
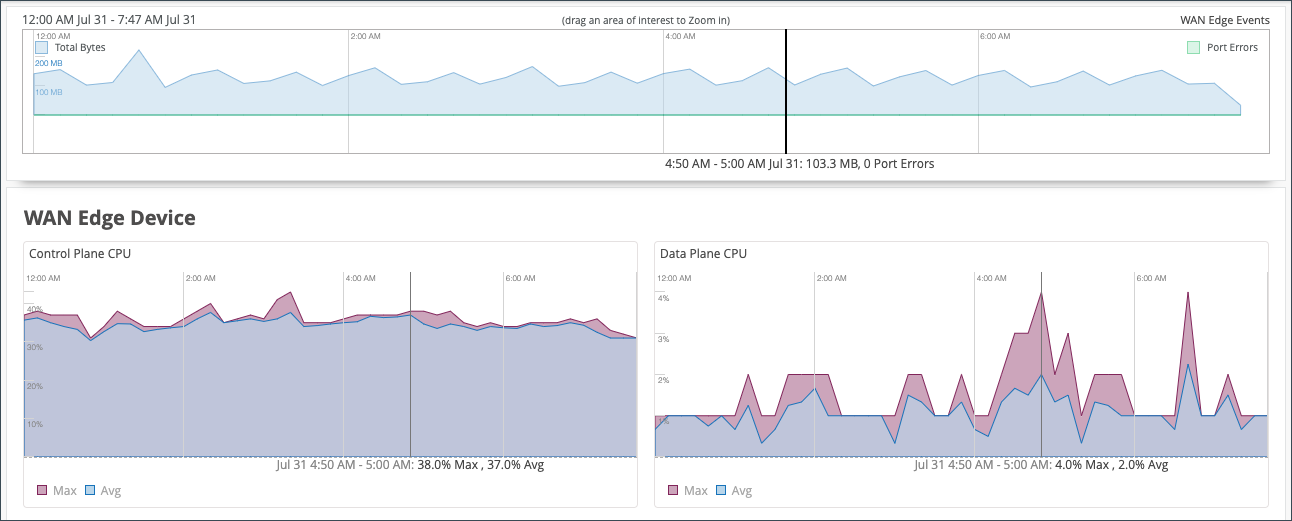
Memory Utilization and Power Draw shows you the percentage for both max and average.
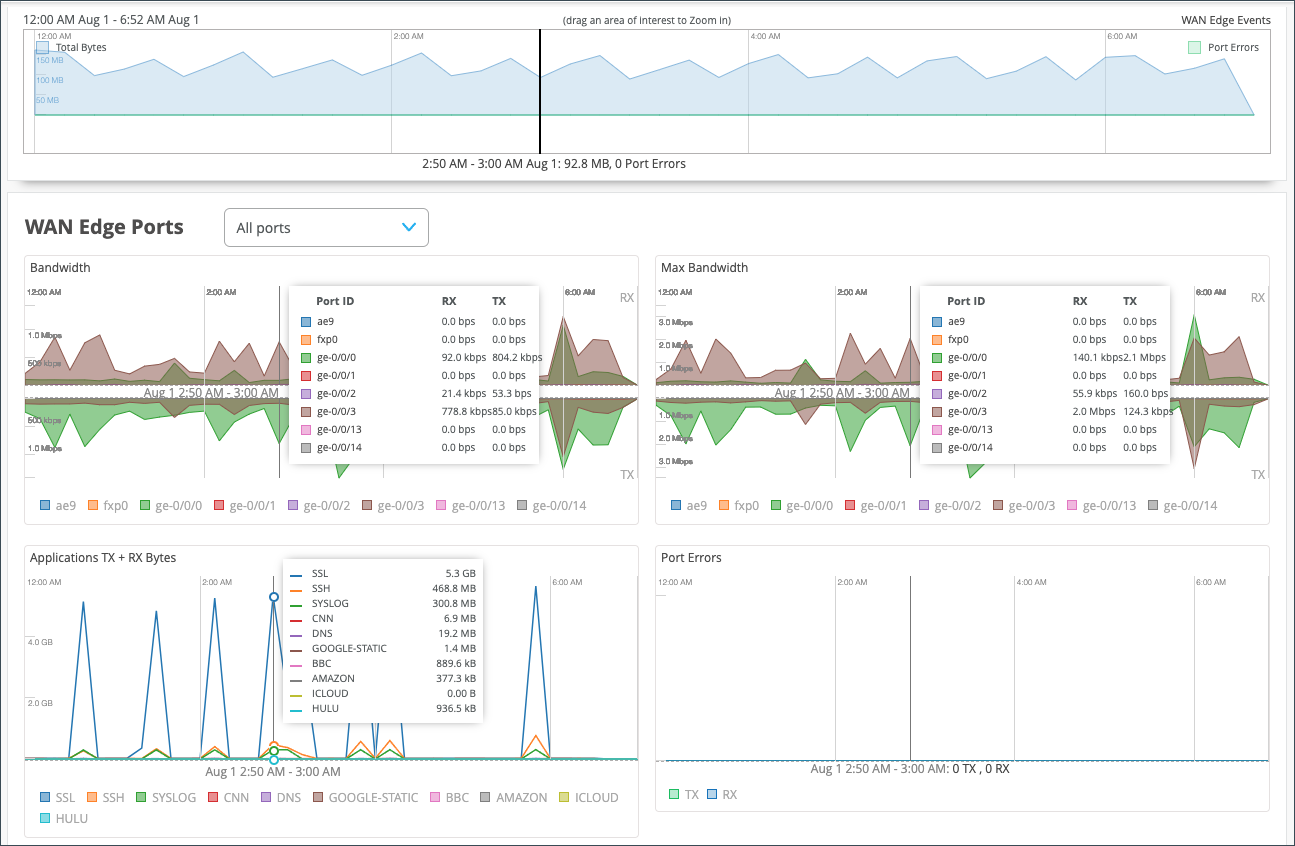
- In the Bandwidth chart, you will see the bandwidth utilization metrics in megabits per second (Mbps) for that particular interface.
- The Max Bandwidth chart displays insights into the highest point of link utilization recorded for received power signal (RX) and transmitted power signal (TX) packets on each port during the day. The data is shown in Mbps.
In the last three WAN Edge Ports charts, you’ll find Applications TX + RX Bytes, Port Errors, and IPsec Traffic. Hover over the charts to find out more information.
- The Applications TX + RX Bytes chart outlines transmit and receive data information, which can be isolated at an application level by clicking on the application name at the bottom of the chart to see Client, MAC address, IP address, device type, and bytes for bandwidth utilization.
- The IPsec Traffic chart displays IPsec traffic for transmit and receive packets during the day in kilobytes or megabytes.
-
The Port Errors graph displays port errors detected on the WAN Edge device over a period of time. Port errors are ethernet data link error counts that include all possible ethernet errors reported by the port device driver. Exact types of errors vary by device driver, and the total may include but is not limited to CRC errors, collisions, etc. Errors are counted in both the transmit (TX) and receive (RX) direction. The graph displays the total for all ports, or for a particular port based on the WAN Edge Ports selection.
Peer Path Statistics
This applies only to Session Smart Routers deployed as WAN edge devices in Juniper Mist™ WAN Assurance. Therefore, no data will be populated in this section for SRX Series Firewalls deployed as a WAN edge device.
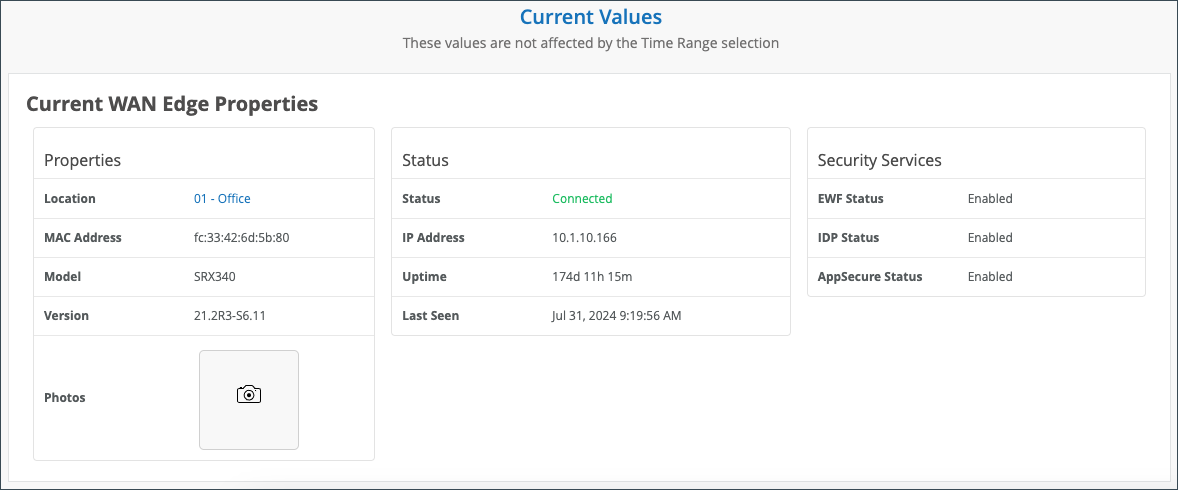
The final section of your WAN Edge Insights page is Current WAN Edge Properties. Time range selections do not impact information in the Current Values pane.
View Alerts for Interfaces Status
In Juniper Mist, alerts present network and device issues that are ongoing. You can view alerts on the Juniper Mist portal by selecting Monitor > Alerts.
You can set up alerts and email updates for when certain ports on a WAN Edge device go online or offline. To configure alerts for specific ports, you need to label these ports in the LAN or WAN settings of a WAN Edge device.
To configure the alerts and notifications for specific port, you must:
- Change the WAN or LAN settings to label the specified ports in the WAN Edge
template or at device-level configuration page.
- In the Juniper Mist portal, select Organization > WAN >
WAN Edge Templates and select the WAN or LAN
configuration that you want to update (or add a new configuration).
To configure this at the device-level, select WAN Edges on the left-navigation bar and select the WAN or LAN configuration of the selected device.
- Under Interface, enter the port or ports, and then select the
Enable “Up/Down Port” Alert Type check-box.
Figure 38: Marking LAN Port or WAN Interface as Critical Interface
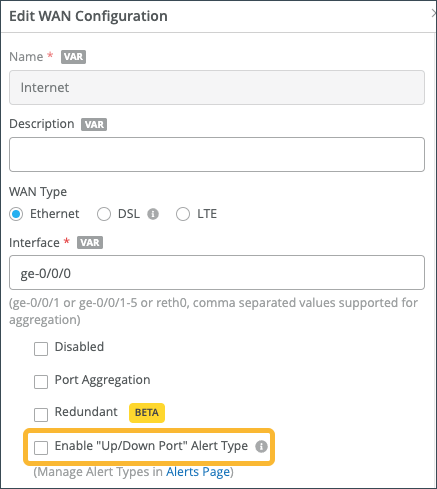
Repeat these steps for all critical ports.
- In the Juniper Mist portal, select Organization > WAN >
WAN Edge Templates and select the WAN or LAN
configuration that you want to update (or add a new configuration).
- Configure alerts and e-mail notifications for the specified ports on the Alerts
page.
- Go to Monitor > Alerts > Alerts
Configuration and use the following check-boxes to
enable alerts for the selected port:
Critical WAN Edge Port Up
Critical WAN Edge Port Down
Figure 39: Alerts Configuration for Critical Ports
See Alert Configuration for details.
When you enable alerts and notifications:
- You'll receive an e-mail notification whenever a port transitions from one state to another.
- You can delay alerts about when the WAN edge gateway goes offline to prevent repeated alerts in the case of connectivity flaps by clicking the pencil icon and setting a time threshold.
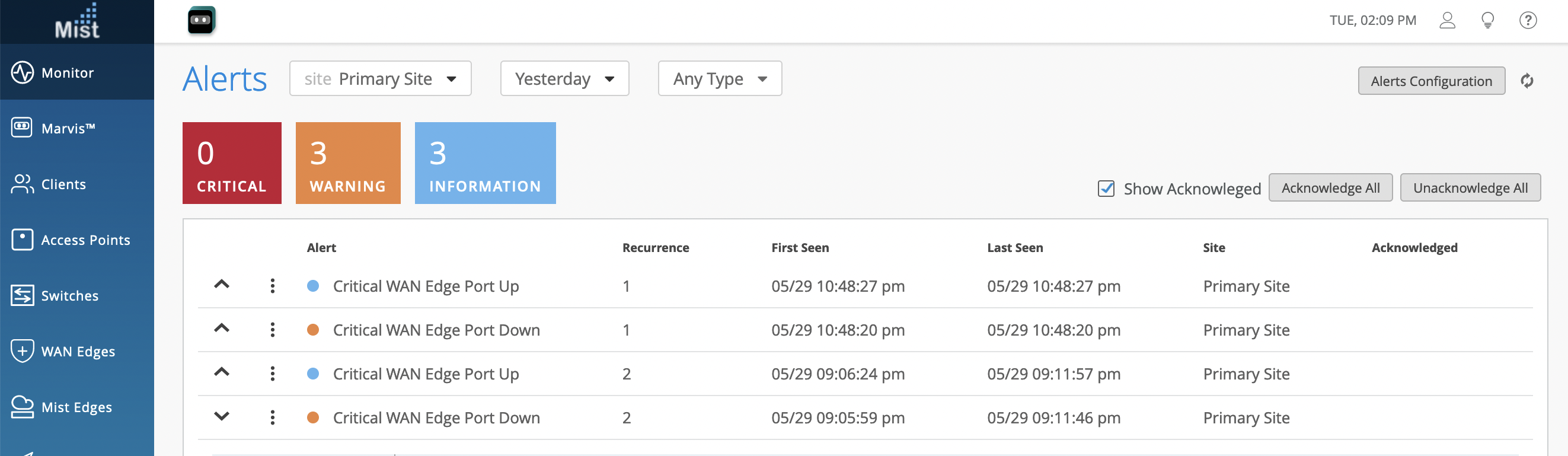
- You can view the status in Monitor > Alerts page. Figure 40
shows an example of the critical port status on the Juniper Mist
Alerts dashboard.Figure 40: Critical WAN Edge Port Status
- Go to Monitor > Alerts > Alerts
Configuration and use the following check-boxes to
enable alerts for the selected port:
