Palo Alto Prisma Access Integration for SASE Health (BETA)
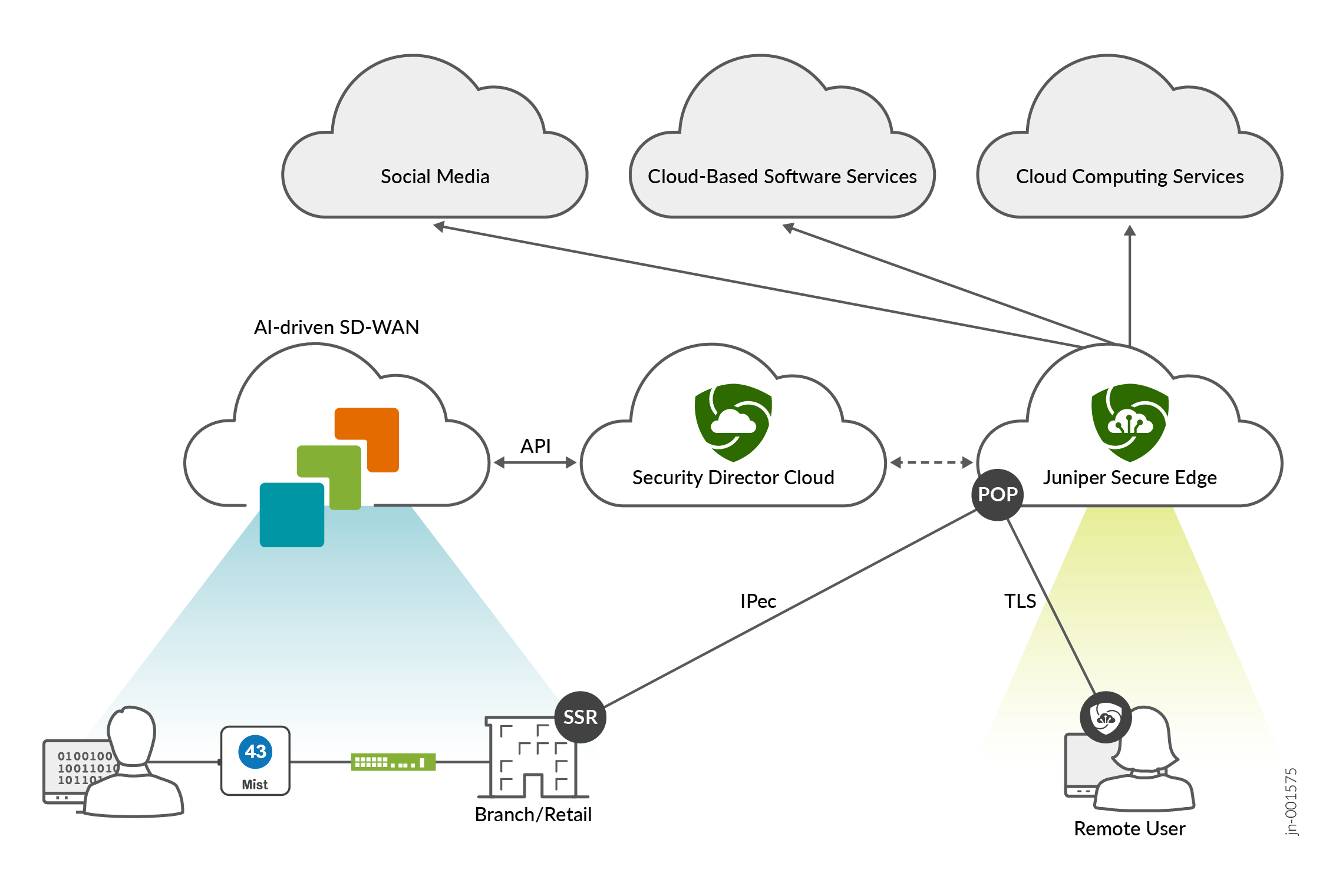
You can integrate a Palo Alto Prisma Access account with Juniper Mist™ WAN Assurance for single-pane-of-glass troubleshooting directly from the Mist portal.
You can integrate a Palo Alto Prisma Access account with Juniper Mist™ WAN Assurance to get a single-pane-of-glass view for troubleshooting and debugging. This integration enables you to view Prisma Access events and tunnel statistics in real-time directly from the Mist portal, so you don't have to navigate between platforms while troubleshooting.
Palo Alto Prisma Access is a cloud-based security platform that ensures secure and fast access to applications and data for users regardless of their location. If you use both Prisma Access and Mist WAN Assurance, an IPsec tunnel is used for end-to-end communication between the two. For example, if standalone WAN Edge devices need to reach specific applications, they can do so securely through the IPsec tunnel between the devices and the Prisma cloud.
Mist automatically provisions these IPsec tunnels, which significantly reduces the amount of manual configuration required by you and also reduces risk of human error. This automatic tunnel provisioning means that you do not need to configure on both sides, as the configuration you do in Mist will be replicated in Strata Cloud Manager.
This integration delivers critical insights in real-time for your WAN Edge devices, Prisma Access, and applications. You can use these insights to quickly and efficiently diagnose and resolve site issues.
Benefits and Requirements
| Benefits |
|
| Requirements |
|
To integrate a Prisma Access account with Mist WAN Assurance, you must complete the following steps.
Configure User Access Role in the Prisma Strata Cloud Manager and Obtain Credentials for Mist
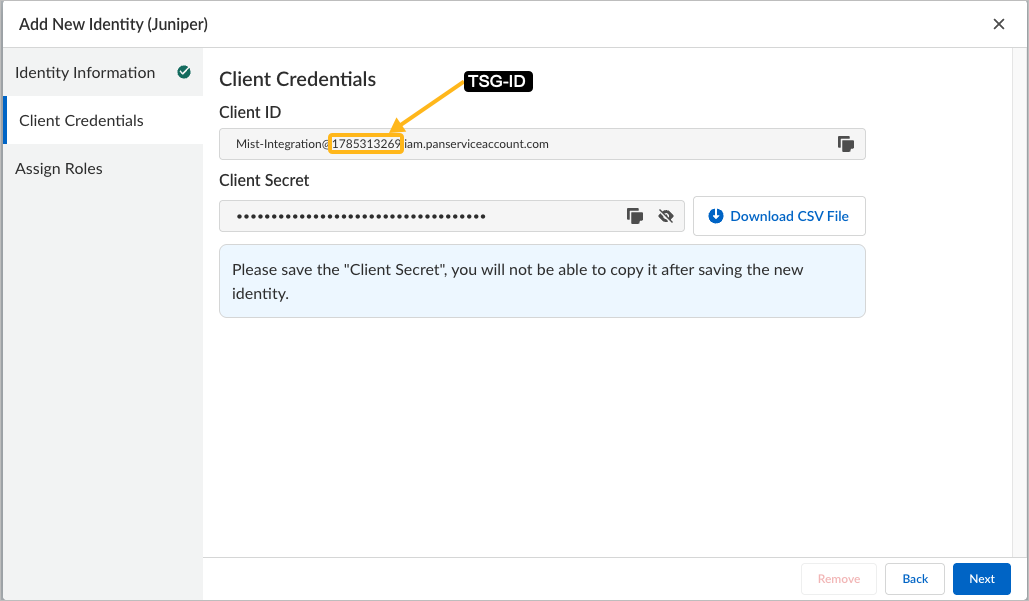
To control access to your applications and services, configure a user Access Role in Prisma. You'll set up the role through the Strata Cloud Manager. Then store the user credentials so that they can be entered into the Juniper Mist portal for account linking.
Add Prisma Access Account as a Secure Edge Connector
- From the left menu of the Juniper Mist portal, select Organization > Admin > Settings.
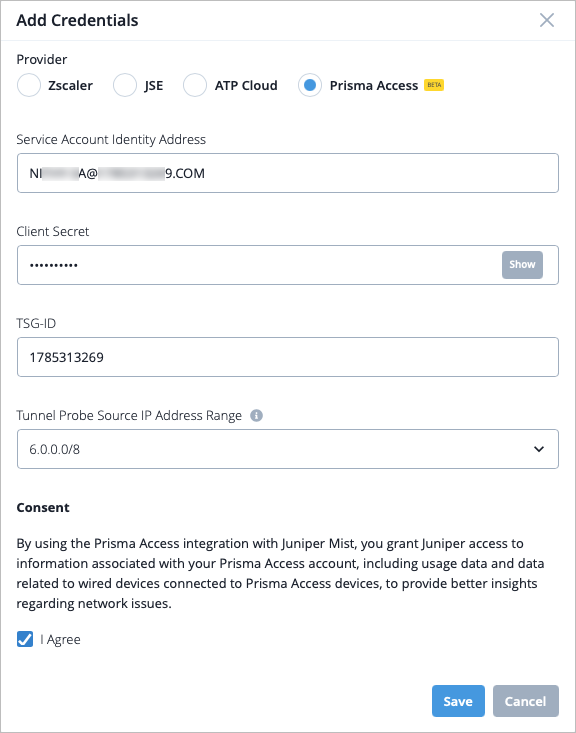
- In the Secure WAN Edge Integration section, click Add Credentials.
-
Enter the credentials you copied from the Prisma Strata Cloud
Manager.
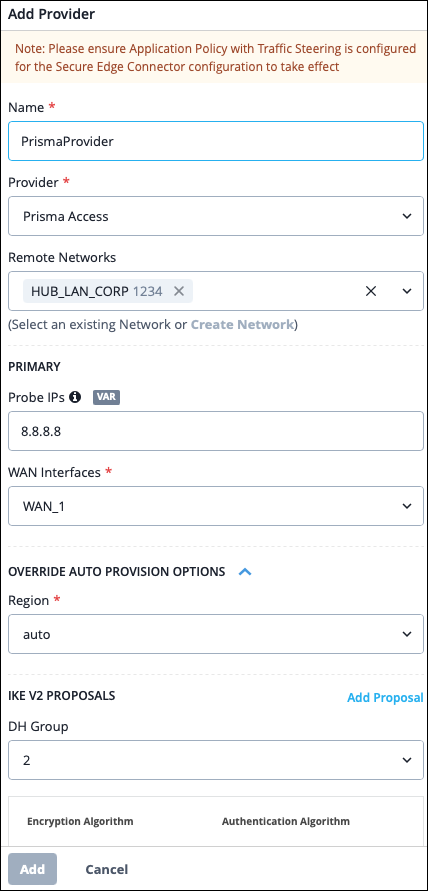
Auto Provision IPsec Tunnels
Mist's automatic Prisma tunnel provisioning requires very minimal configuration. You only need to configure in Mist, and that configuration will be replicated in the Strata Cloud Manager automatically.
Most aspects of the configuration are automatically set for you. All you have to do to configure your tunnel is enter a name, provider, and WAN interface. Some of the fields that are automatically configured for you include the Region, where Mist automatically finds your region for the tunnel based on your Prisma tenant information, and Data Center, where Mist automatically finds the closest geographically located Point of Presence (POP) to your service connection. However, you can configure these fields with other values if necessary.
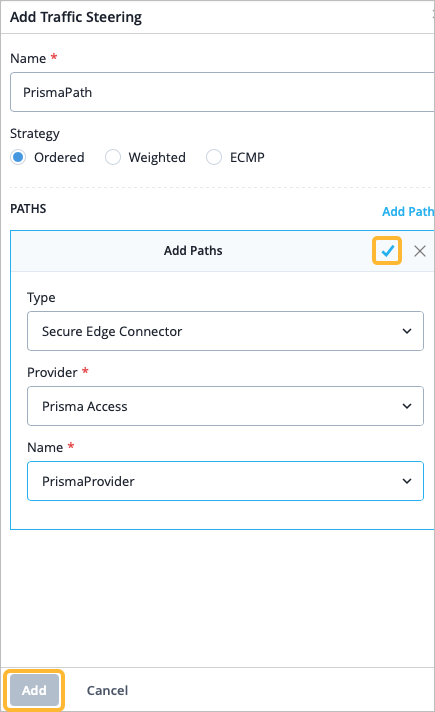
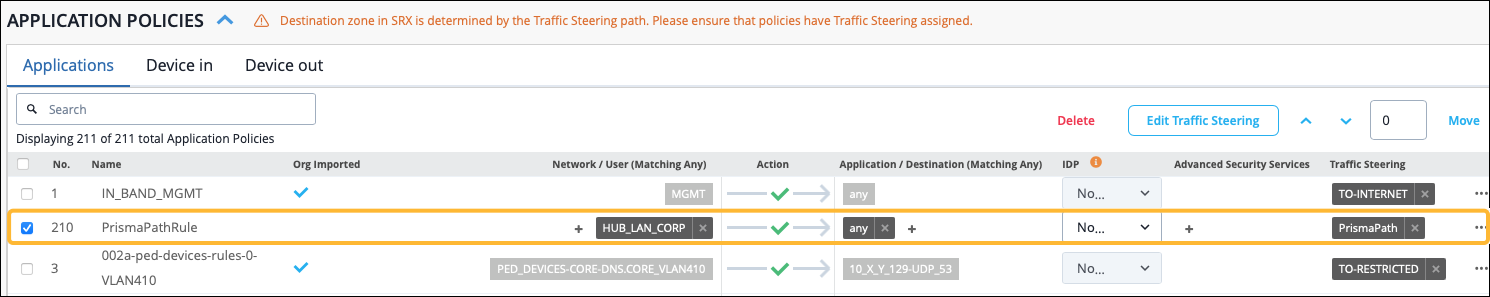
Configure Traffic Steering and Application Policies
Tunnel Verification:
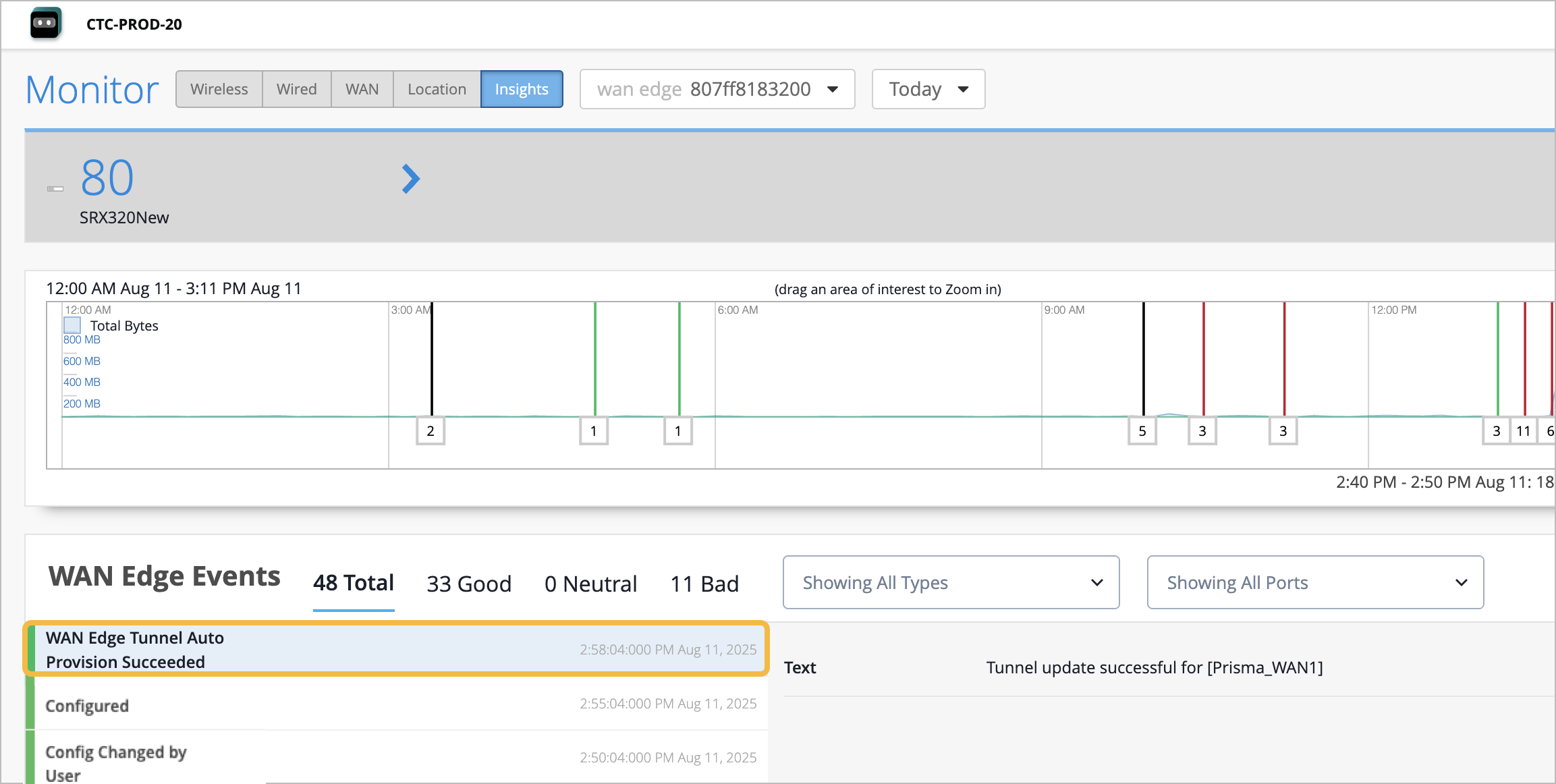
The IPsec configuration is pushed to any WAN Edge devices that belong to a site that has the template assigned, and a tunnel from the device to the closest Prisma cloud is brought up. To see the IPsec status, select WAN Edges > WAN Edges from the left menu, then click the WAN Edge device, and finally, click WAN Edge Insights.You can verify the established tunnel's details on the WAN Edge Insights page of the device once the WAN Edge Tunnel Auto Provision Succeeded event appears under WAN Edge Events.
Prisma Events
-
Juniper Mist supports the following Prisma Access Events:
Remote Networks:
-
Prisma RN ECMP BGP Down
-
Prisma RN ECMP BGP Flap
-
Prisma RN ECMP Proxy Tunnel Down
-
Prisma RN ECMP Proxy Tunnel Flap
-
Prisma RN Primary WAN BGP Down
-
Prisma RN Primary WAN BGP Flap
-
Prisma RN Primary WAN BGP Up
-
Prisma RN Primary WAN Proxy Tunnel Down
-
Prisma RN Primary WAN Proxy Tunnel Flap
-
Prisma RN Primary WAN Tunnel Down
-
Prisma RN Primary WAN Tunnel Flap
-
Prisma RN Primary WAN Tunnel Up
-
Prisma RN Secondary WAN BGP Down
-
Prisma RN Secondary WAN BGP Flap
-
Prisma RN Secondary WAN BGP Up
-
Prisma RN Secondary WAN Proxy Tunnel Down
-
Prisma RN Secondary WAN Proxy Tunnel Flap
-
Prisma RN Secondary WAN Tunnel Down
-
Prisma RN Secondary WAN Tunnel Flap
-
Prisma RN Secondary WAN Tunnel Up
Service Connection:
-
Prisma Service Connection Primary WAN BGP Down
-
Prisma Service Connection Primary WAN BGP Flap
-
Prisma Service Connection Primary WAN Proxy Tunnel Down
-
Prisma Service Connection Primary WAN Proxy Tunnel Flap
-
Prisma Service Connection Primary WAN Tunnel Down
-
Prisma Service Connection Primary WAN Tunnel Flap
-
Prisma Service Connection Secondary WAN Proxy Tunnel Down
-
Prisma Service Connection Secondary WAN Proxy Tunnel Flap
-
Prisma Service Connection Secondary WAN Tunnel Down
-
Prisma Service Connection Secondary WAN Tunnel Flap
-
Prisma Service Connection WAN BGP Down
-
Prisma Service Connection WAN BGP Flap
Note:A Prisma Access icon displays next to any Prisma Access events received from Strata Cloud Manager. The information in the Prisma Access event comes directly from Strata Cloud Manager.
-
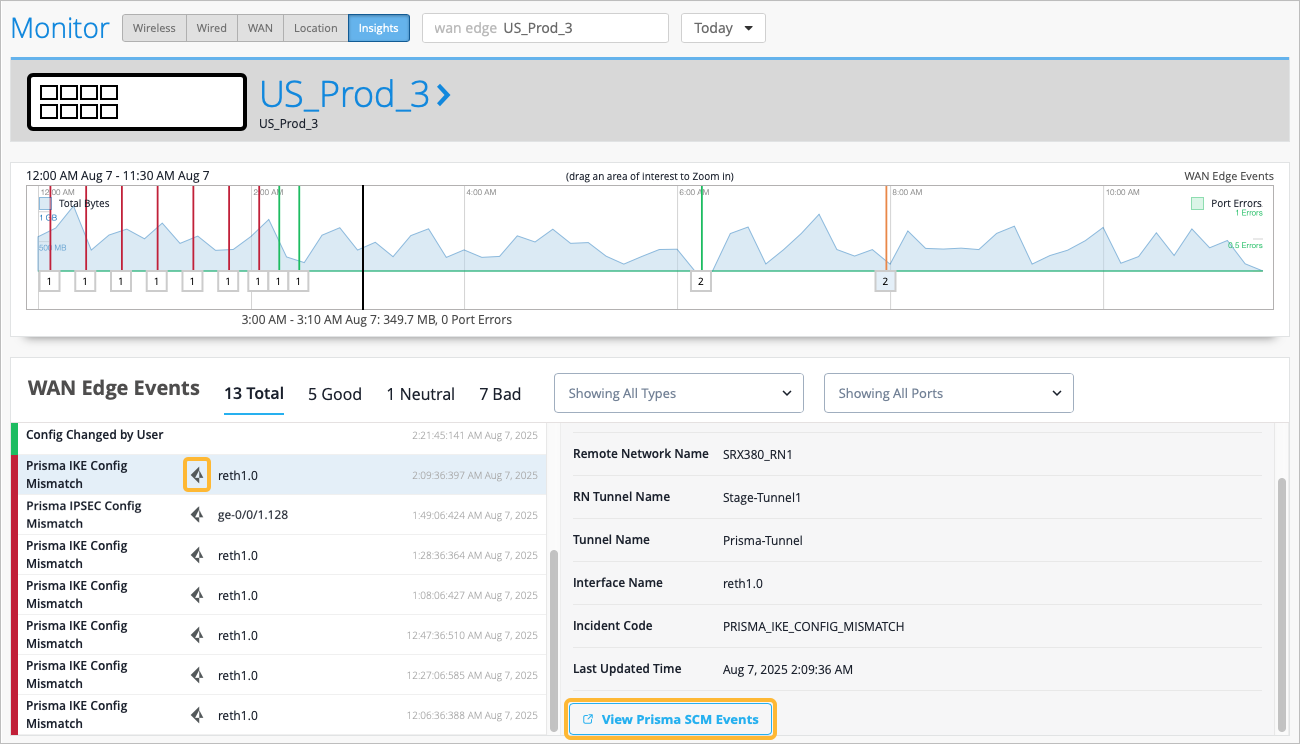
When you select a Prisma Access event, you have the View Prisma SCM Incidents button available to you. Select the button if you need to see more details about the Prisma incident from Prisma SCM.
-
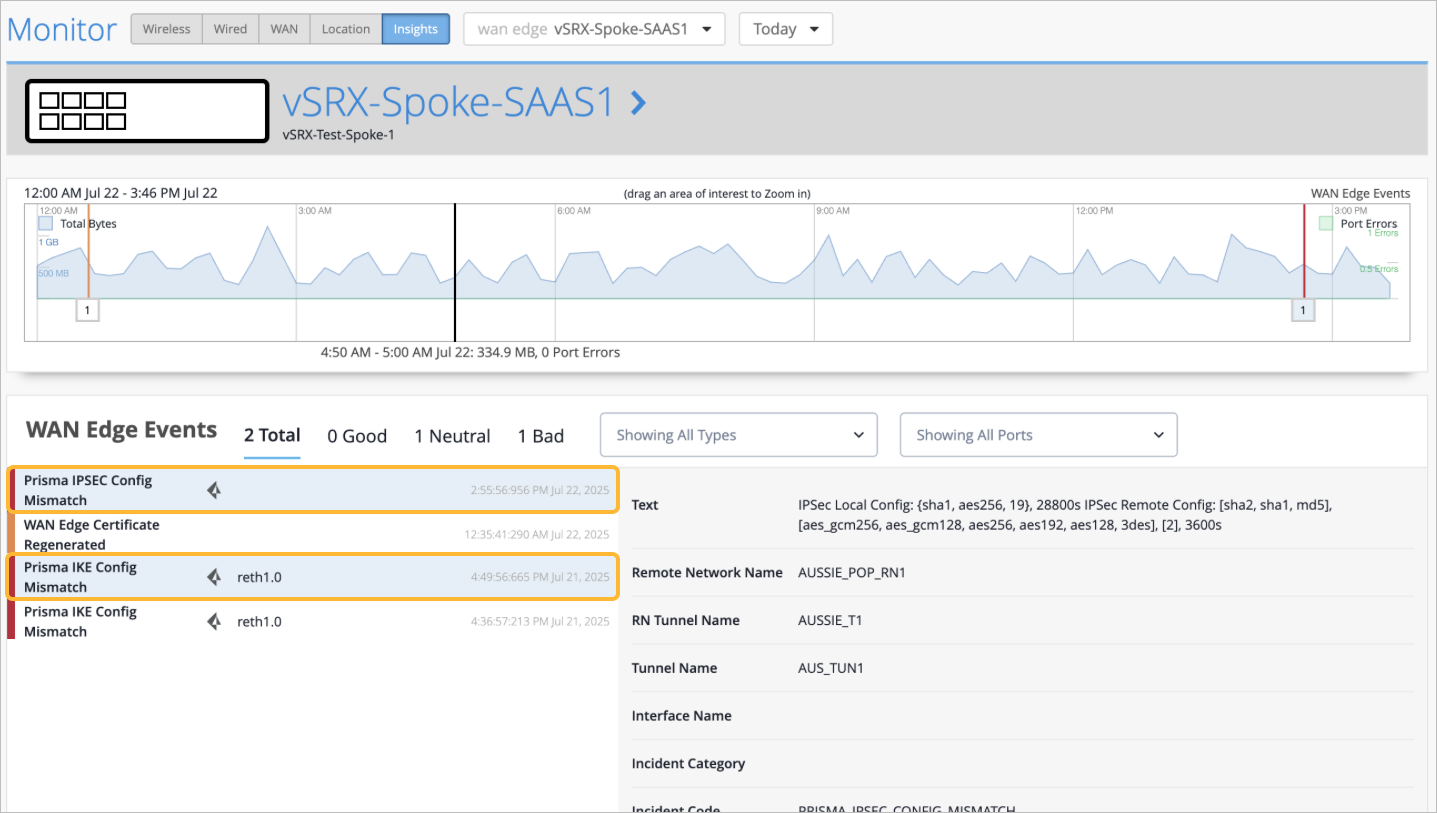
Configuration Mismatch
Marvis constantly compares the site configuration in Mist to the configuration in Prisma. If any deviations are detected, a Prisma Access event is generated and appears in the WAN Edge Events.
Configuration Difference Alerts:
-
Prisma IKE Config Mismatch
-
Prisma IPsec Config Mismatch
Tunnel Statistics
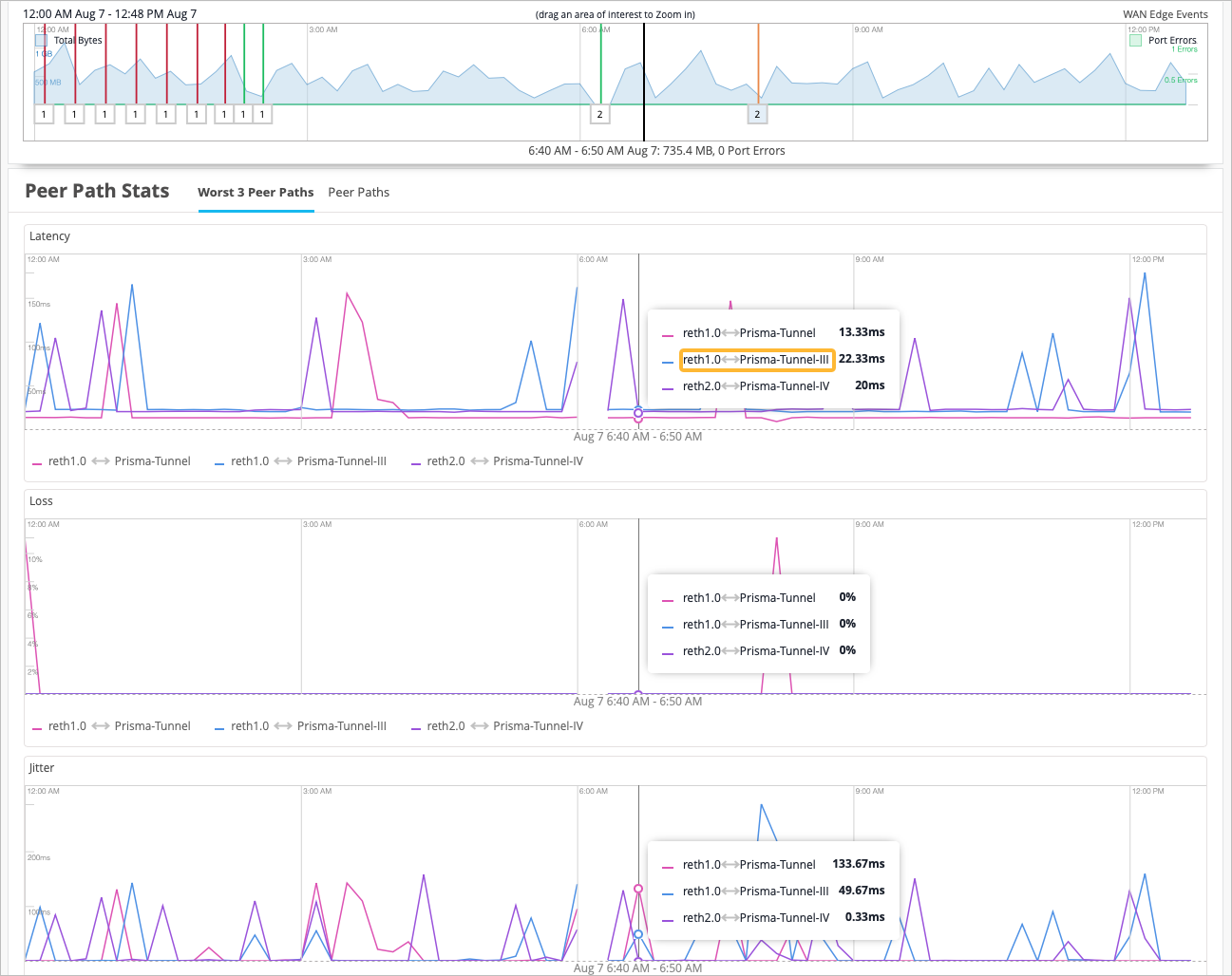
You can view the Prisma tunnel statistics for both Session Smart Router (SSRs) and SRX Series Firewalls under Peer Path Stats on the WAN Edge Insights page.
Tunnel statistics use intelligent probing to a northbound resource and generate the near-real time Key Performance Indicator (KPI). You can see the customer's experience as they access an application through the tunnel in near-real time.
When you hover over the Peer Path Stats chart, you get information about the path in the string that is displayed to you. You can decipher the string as follows:
egress device interface <--> Prisma tunnel name.