Juniper Mist Secure Edge Connector Overview
Before integrating Secure Service Edge (SSE), get familiar with key concepts, deployment options, and the high-level workflow.
Juniper Mist provides pre-built connectors specifically designed for the Juniper Networks® SRX Series Firewalls and Juniper® Session Smart™ Routers deployed as WAN edge devices. These connectors facilitate seamless integration with your Secure Service Edge (SSE) deployments. With minimal configuration, you can integrate the SSE into the Juniper Mist portal. As a result, your WAN Edge device establishes connections to the SSE using either IPsec or GRE protocols.
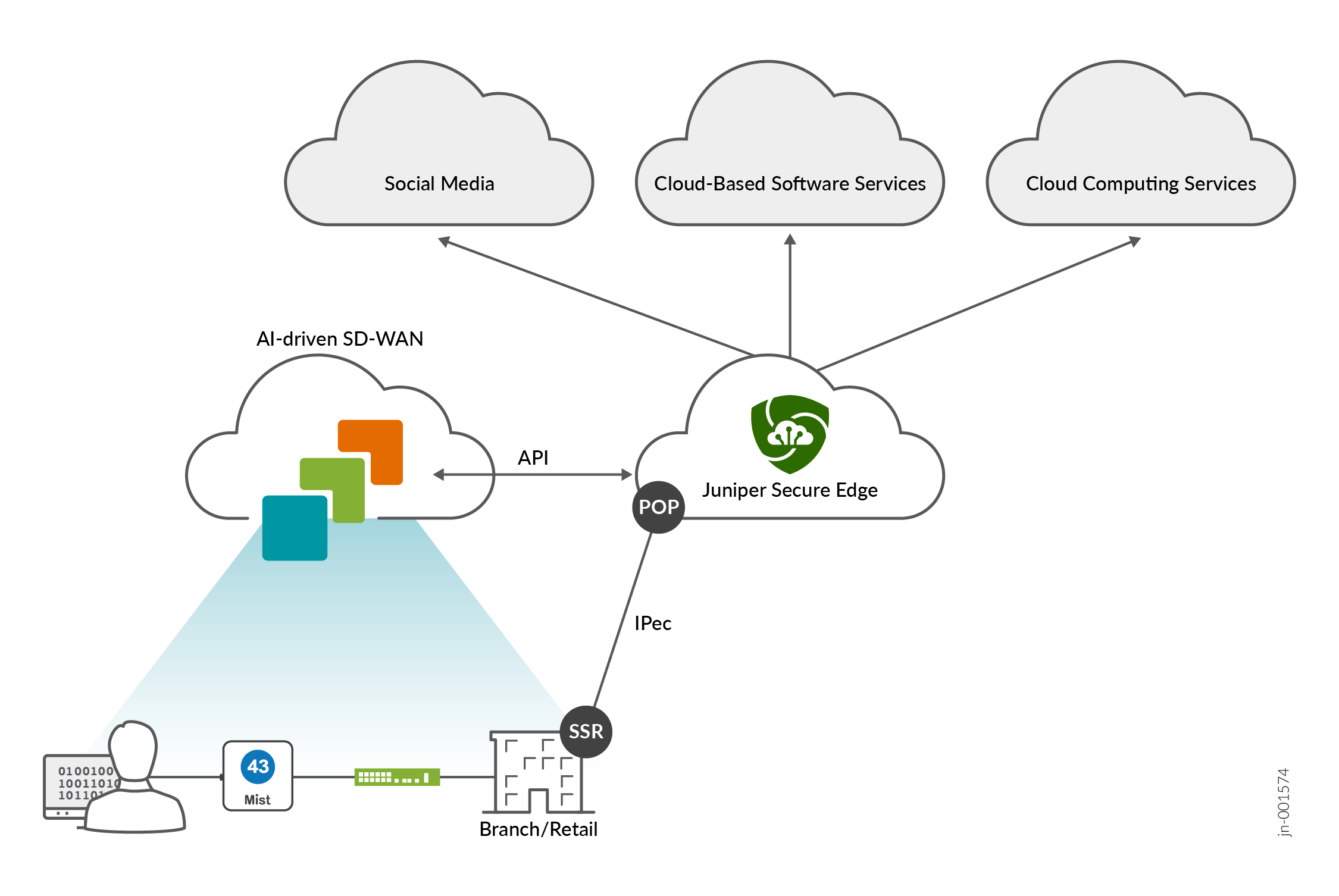
In this solution, an IPsec tunnel is configured between the WAN Edge device and SSE using the Secure Edge Connector (SEC) within the WAN Edge template. Additionally, for Prisma Access auto provisioning and Custom SEC types, a BGP over IPsec connection can be configured to dynamically learn routing destinations from the SSE device.
Juniper Mist supports these SEC types:
- Juniper Secure Edge (manual provisioning and auto provisioning)
- Zscaler (manual provisioning and auto provisioning)
- Custom
-
Palo Alto Prisma Access (auto provisioning)
High-level workflow for setting up secure edge connectors with Juniper Secure Edge, custom, or Zscaler deployment to offload traffic from your WAN edge device (SSR Series Routers or SRX Series Firewalls):
Create and deploy a basic branch template for device connectivity.
Optionally configure a remote network in SSE. This step defines a remote source for inbound connectivity through the tunnel.
Configure an SEC and SSE provider in the device template. This step creates a custom IPsec tunnel to the remote location and define encryption parameters.
Optionally configure a BGP peer to learn routes dynamically.
Configure an application that allows traffic to be steered toward the IPsec tunnel. This application will be used in application policy to allow client networks to access the BGP learned routes.
Configure a traffic steering policy that steers the Internet-bound traffic from the LAN side of a spoke or hub device to the SEC.
Application Policies for SEC
An application policy defines which networks and users (traffic source) can access which applications (traffic destination). You also can use Traffic Steering to define which path to use.
To set up these policies, you need to create networks, applications, and traffic-steering profiles.
-
For outbound traffic—Include the SEC in the traffic steering profile.
-
For inbound traffic through the SEC—Include the remote network in the SEC, and define an application policy that allows inbound access. With this feature, you can securely connect to cloud-hosted services that initiate inbound traffic to a site.
Traffic Steering Profiles for Secure Edge Connector
Traffic steering is required for SEC on both SRX Series Firewalls and Session Smart Routers before Juniper Mist creates the tunnels.
This requirement remains unless:
- A remote network is assigned to an SEC
- A BGP peer is assigned to an SEC
Dynamic Routing for SEC
You can configure BGP peering over your SEC. This configuration leverages BGP for dynamic routing and uses BGP path selection to install routes in the route table.
-
Palo Alto Prisma Access (auto provisioning)
-
Custom
JSE and Zscaler do not support BGP over IPsec for dynamic routing.
High-Level steps include:
-
Verify that your SEC is established and is configured using the custom Secure Edge provider.
-
Configure BGP import and export policies.
-
Configure BGP neighbor options.
-
Select the SEC for this BGP neighbor.
-
Assign import and export policies.
-
Verify that the BGP peers are exchanging routes over the tunnel interface.
