SCIM Integration with Microsoft Entra ID and Okta
The Mist Access Assurance cloud uses OAuth 2.0 to integrate with Microsoft Entra ID (Azure AD) and Okta for secure user authentication and authorization. System for Cross-domain Identity Management (SCIM) integration enhances the authorization performance by enabling the Access Assurance cloud to maintain a locally synchronized repository of users and groups, reducing latency and dependency on external IdPs. Follow these steps to integrate SCIM with Entra ID or Okta.
The Mist Access Assurance cloud integrates with external Identity Providers (IdPs) such as Microsoft Entra ID (Azure AD) and Okta using OAuth 2.0. With this integration, Mist Access Assurance manages the:
-
Authentication for EAP-TTLS and Admin-Auth
-
Authorization (retrieving user group information) for EAP-TLS, EAP-TTLS, and Admin-Auth through OAuth 2.0 connections to the IdPs
As the authentication and authorization operations involve real-time communication with external IdPs, each control-path call can introduce additional latency, affecting the overall response time for authentication and policy evaluation. It also adds a potential bottleneck and failure domain in cases where the IdP service is degraded.
To optimize the authorization process, Juniper Mist Access Assurance supports System for Cross-domain Identity Management (SCIM)-based integration with IdPs. A key benefit of SCIM-based integration is reduced latency during the authorization process.
The Mist Access Assurance cloud utilizes SCIM to maintain a locally synchronized repository of user and group information for each customer organization. This repository enables the policy service to assess user group memberships and enforce authorization rules without requiring real-time lookups to the external IdP.
If the Mist Access Assurance cloud encounters any error while retrieving group mapping from the SCIM data, it automatically reverts to the existing OAuth-based authorization by connecting to the external IdP.
Disabling SCIM will remove all synchronized user and group data and prevent any further synchronization from the IdP.
Prerequisites
Before you integrate SCIM, ensure to complete the following tasks:
Integrate Mist Access Assurance with the Microsoft Entra ID or Okta IdP. See Microsoft Entra ID Integration and Okta Integration for detailed instructions.
Ensure that at least one client is onboarded with Mist Access Assurance before proceeding with the SCIM configuration.
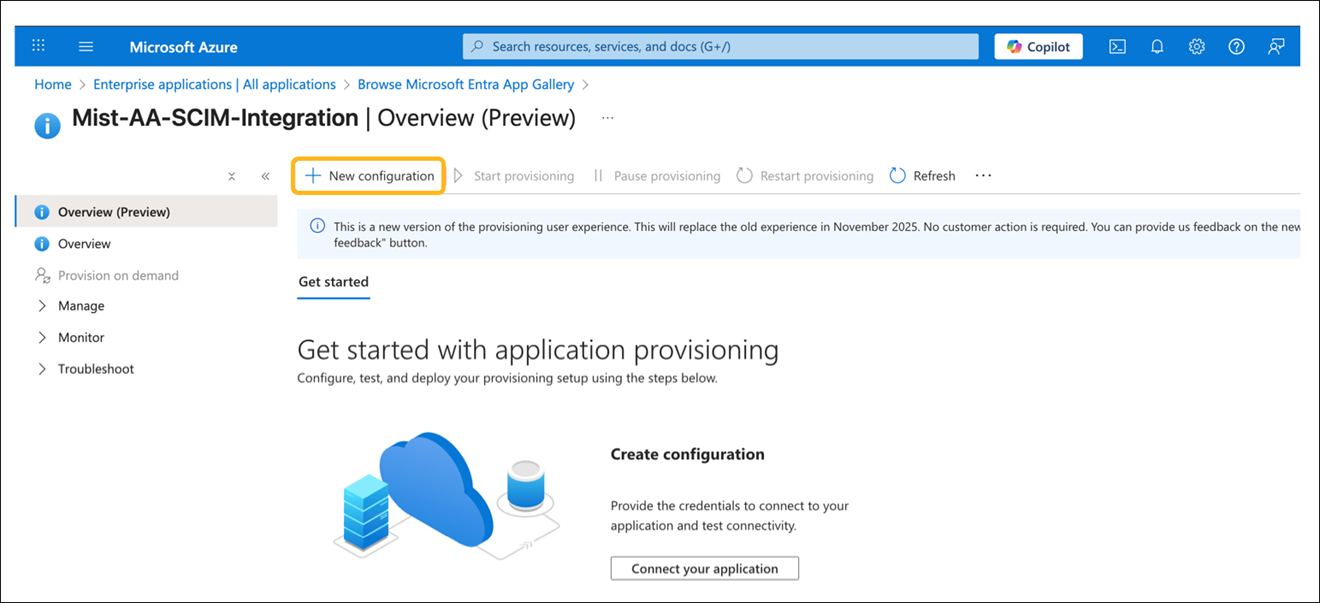
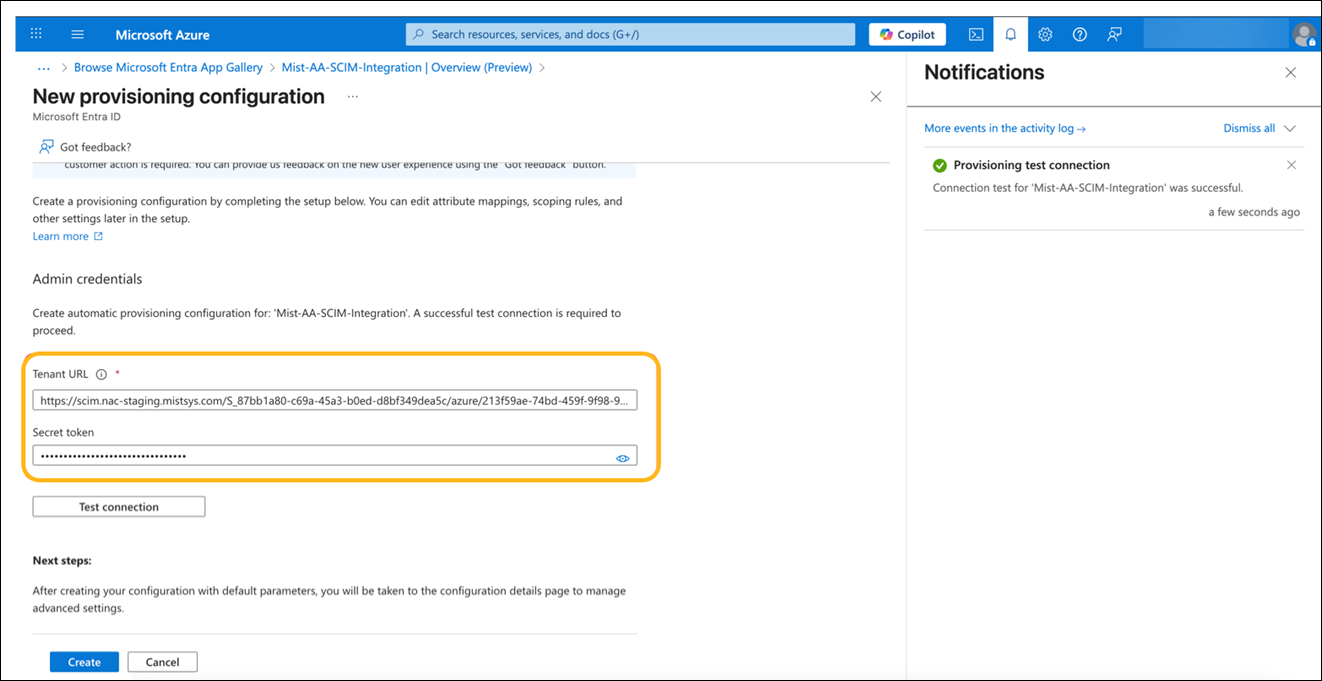
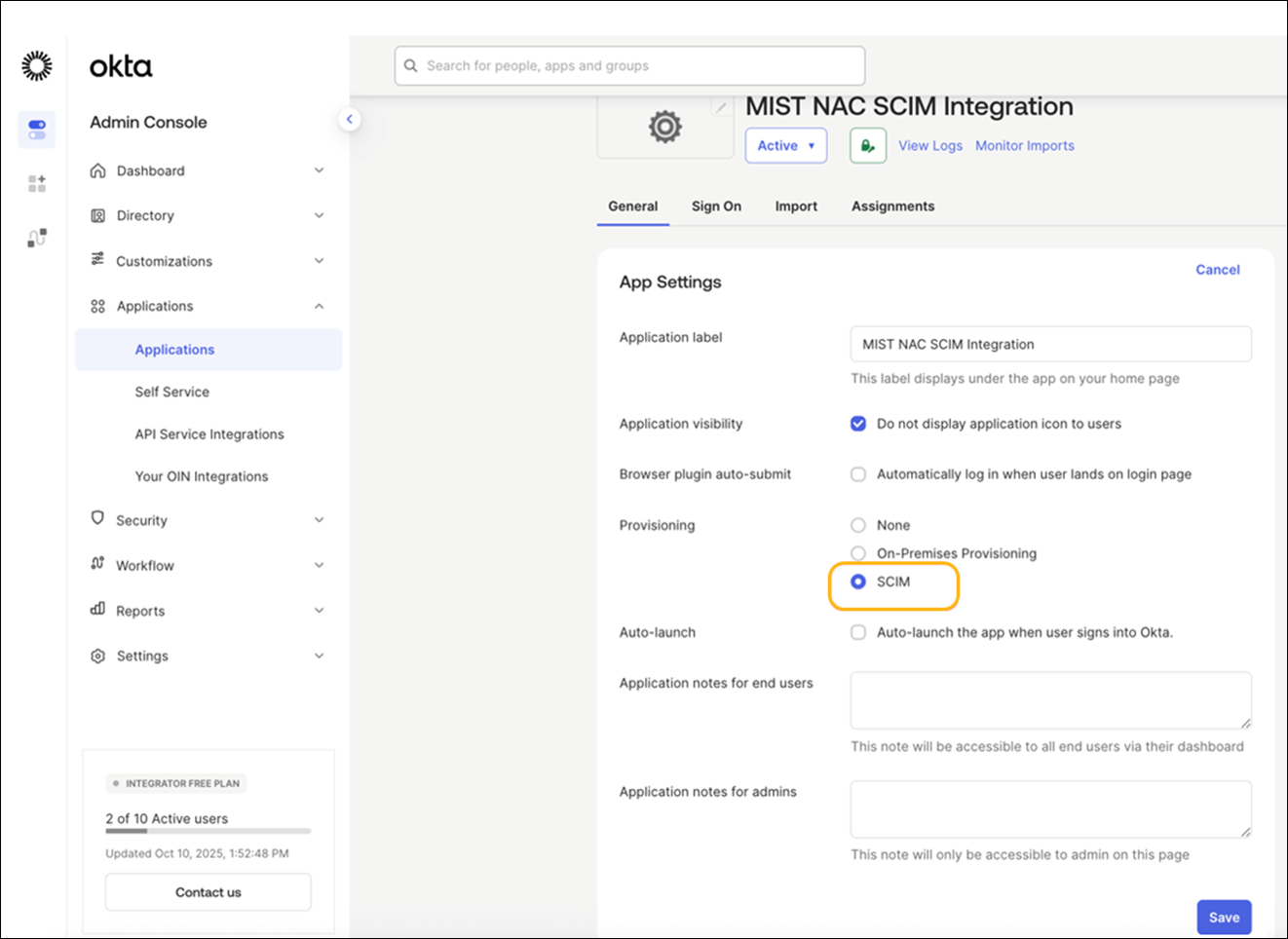
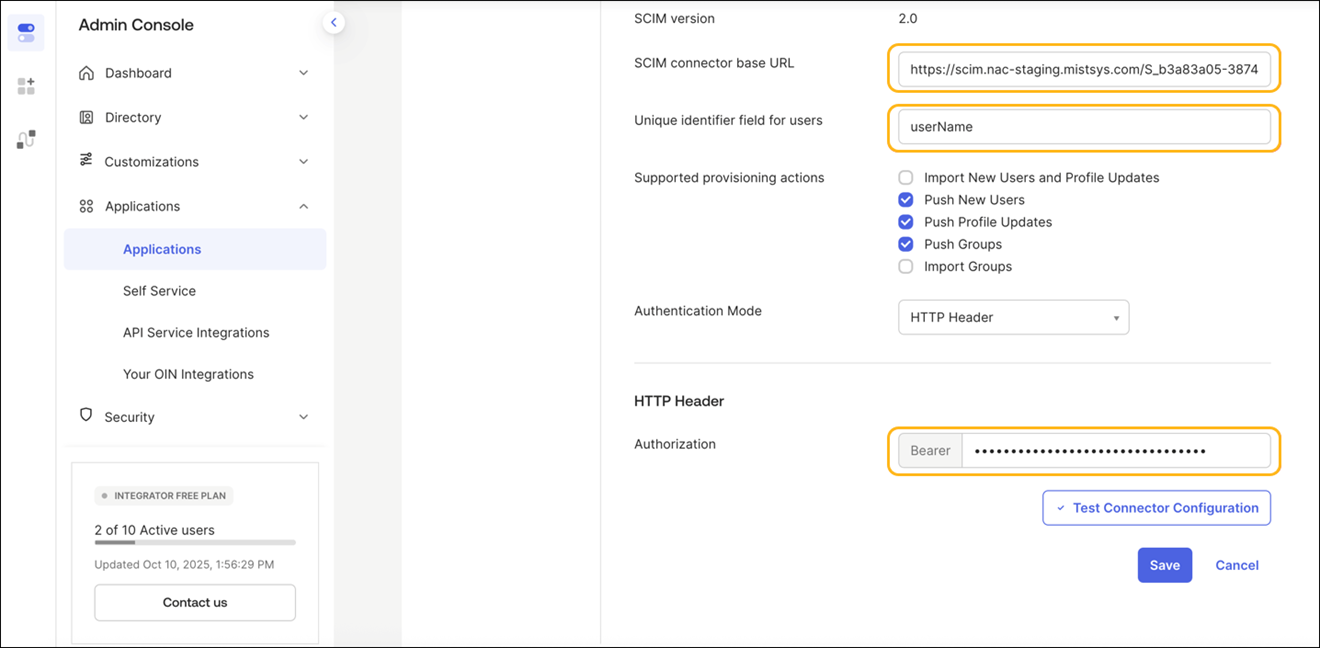
Enable SCIM provisioning in the IdP configuration. The SCIM Authentication Token and SCIM Base URL are automatically generated when you enable SCIM provisioning. These parameters are required for synchronizing user and group information from the IdP to Mist Access Assurance.
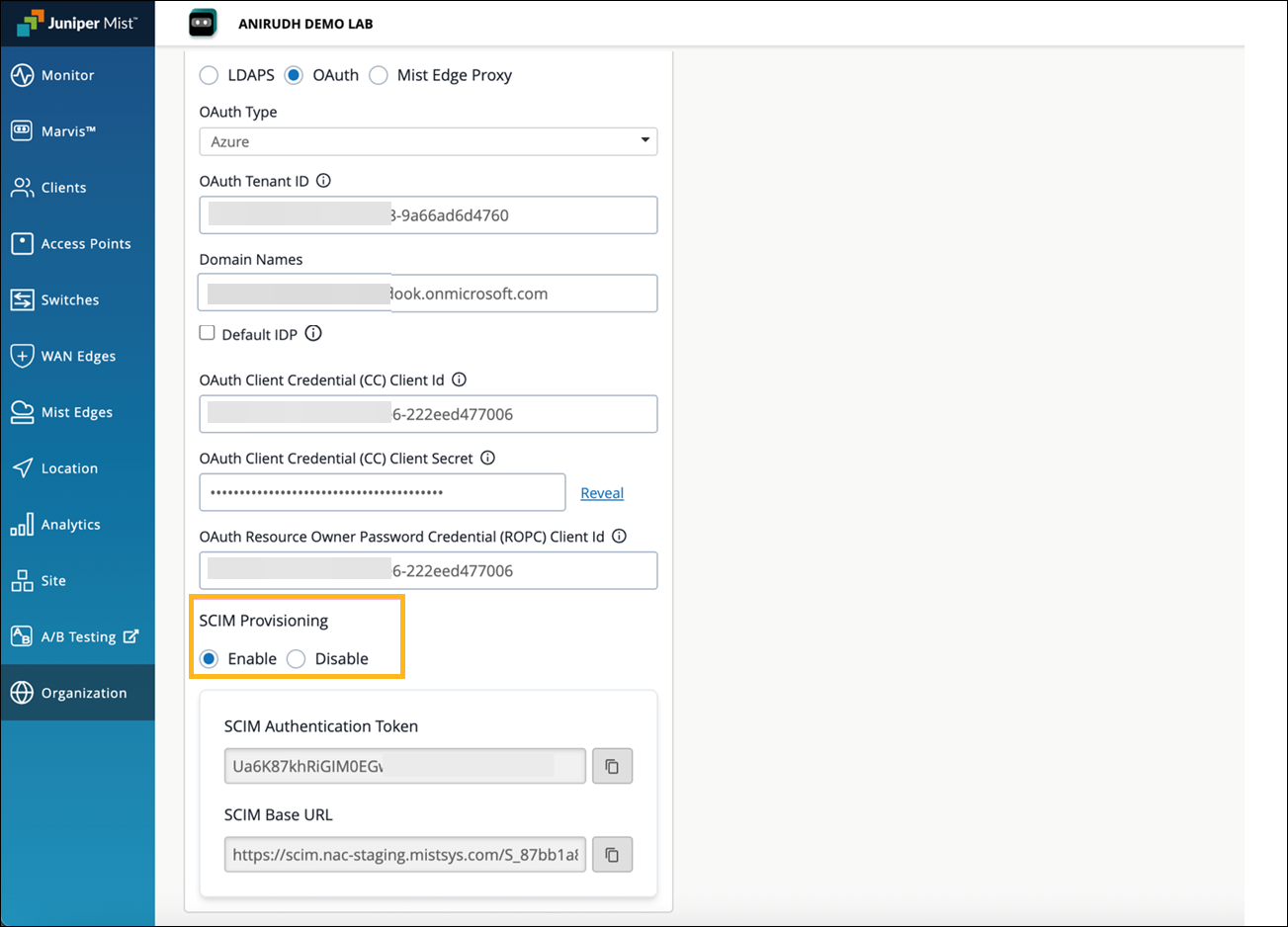
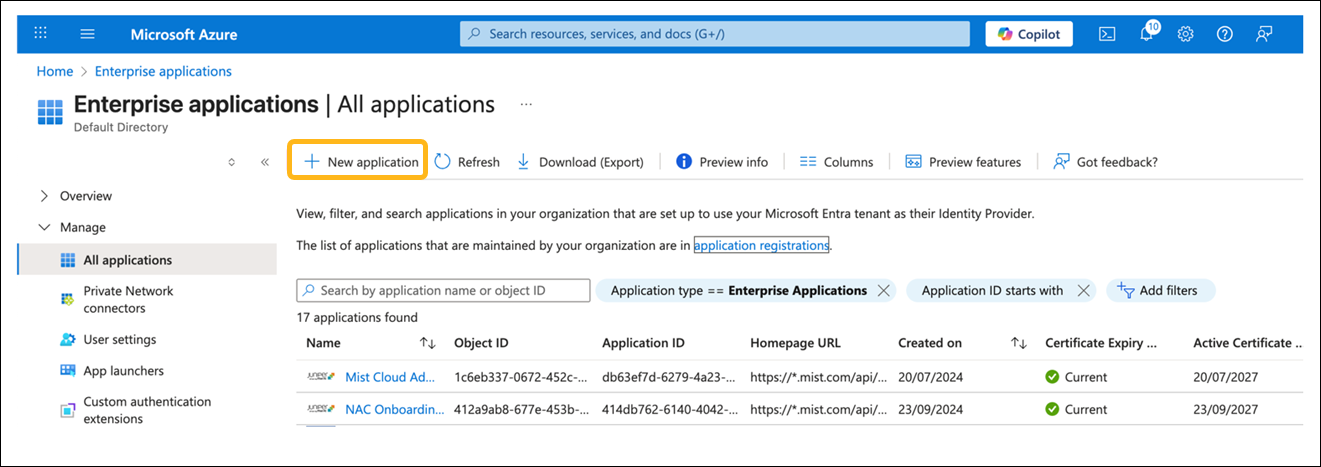
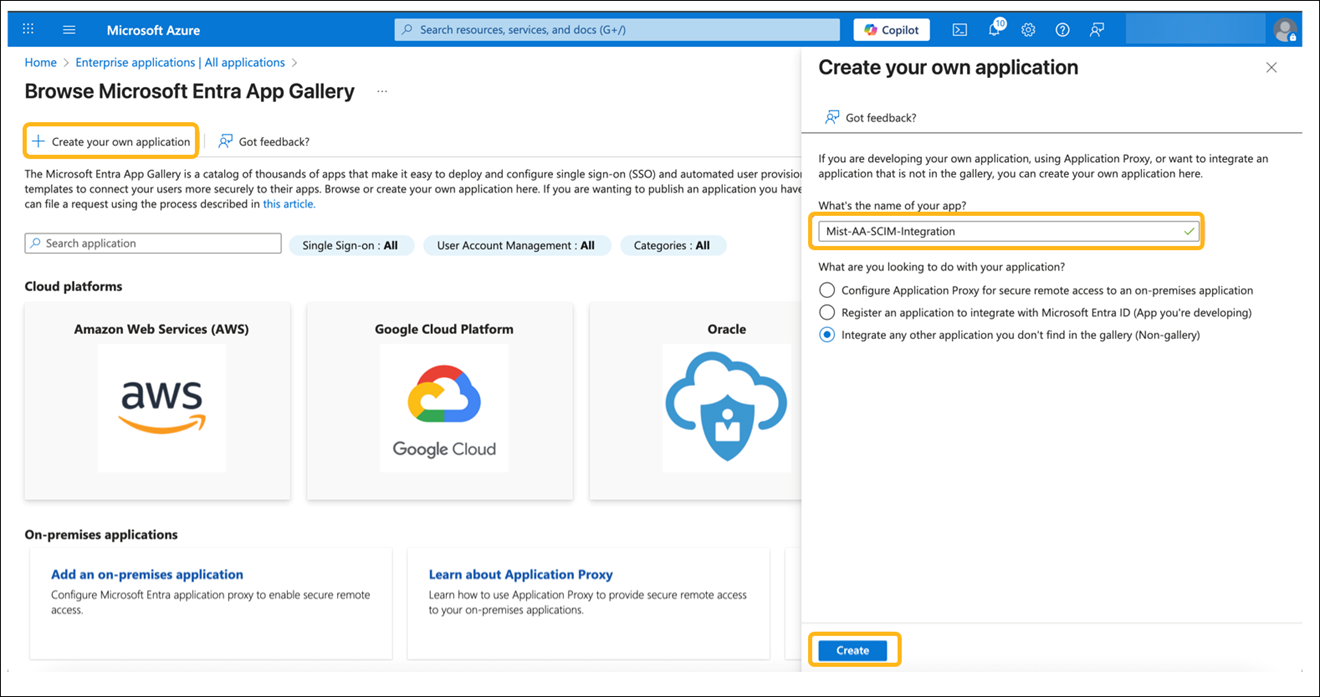
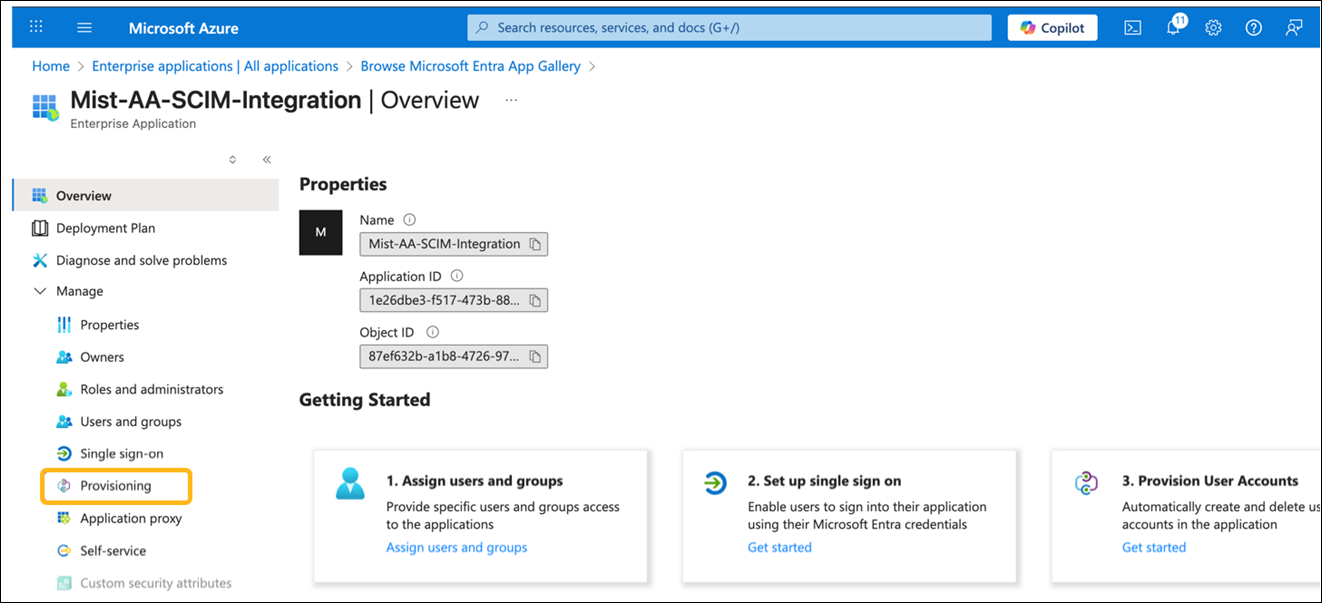
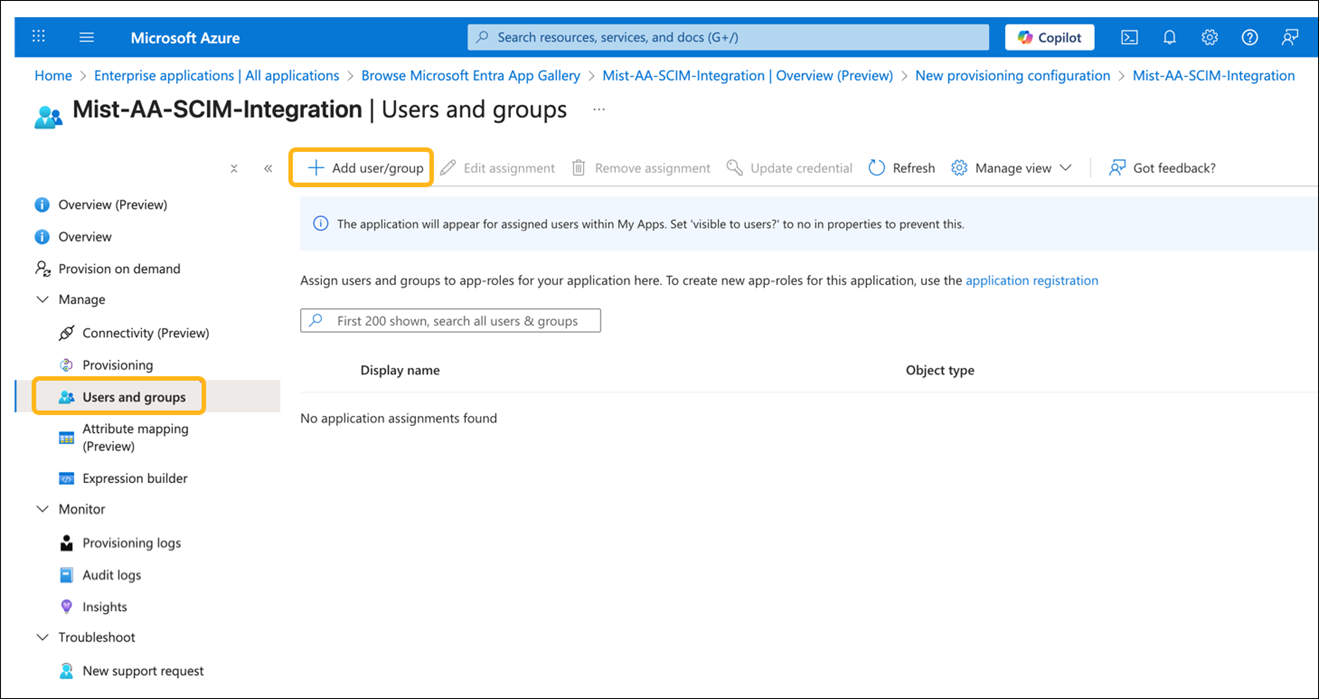
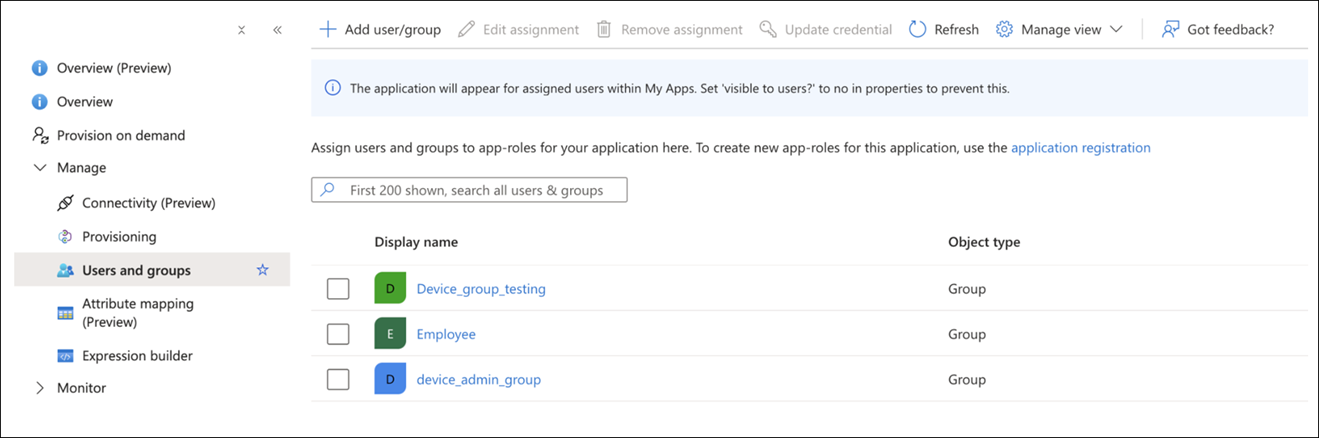
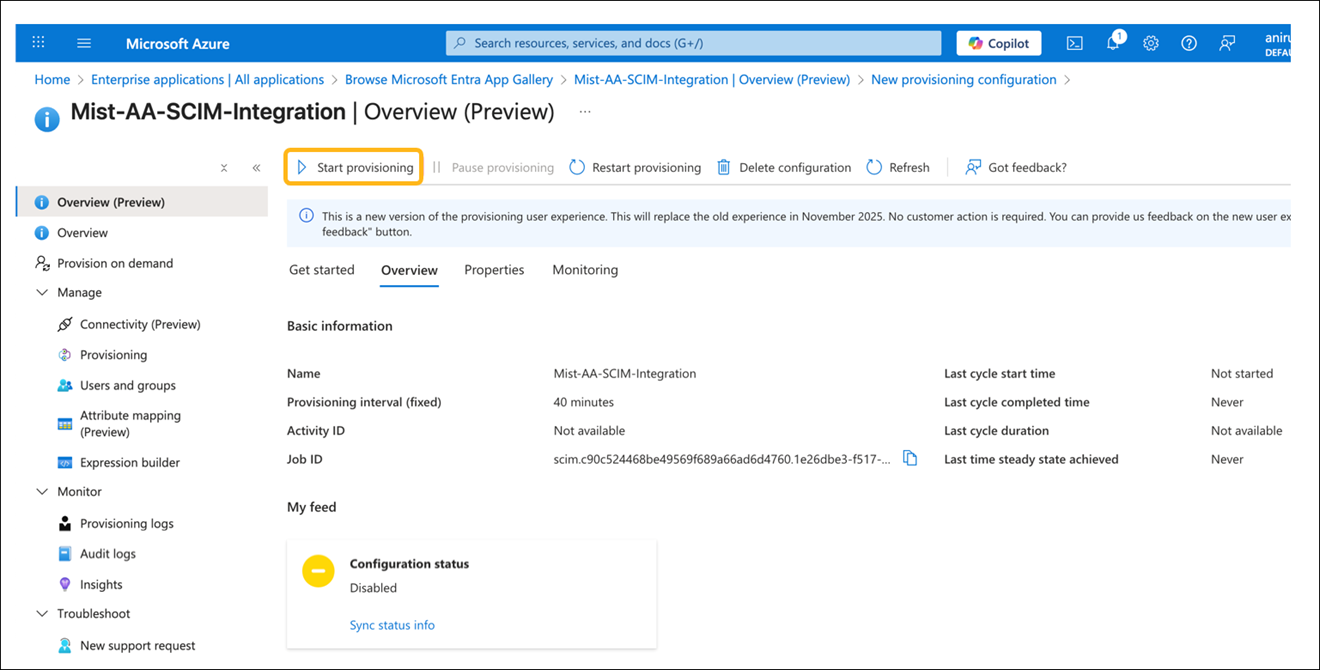
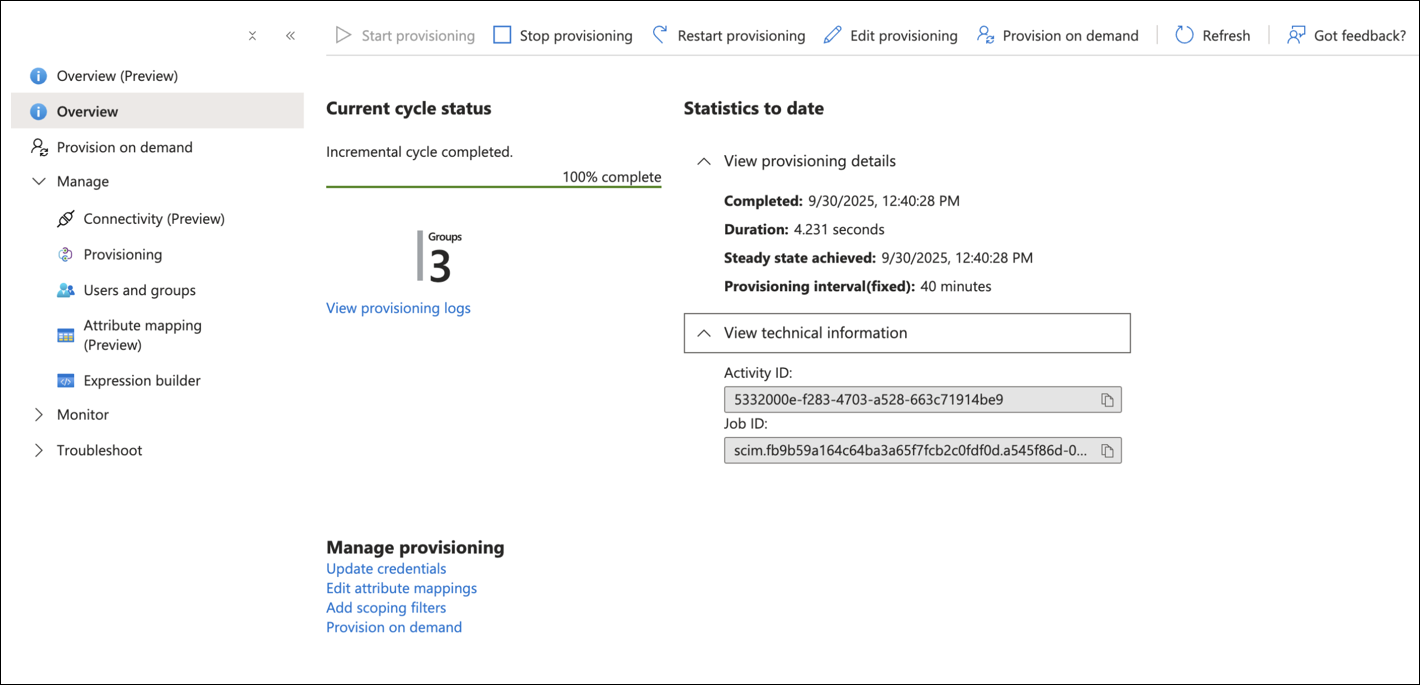
How to Integrate SCIM with Microsoft Entra ID
The screenshots from third-party applications are correct at the time of publishing. We have no way to know when or if the screenshots will be accurate at any future time. Please refer to the third-party website for guidance about changes to these screens or the workflows involved.
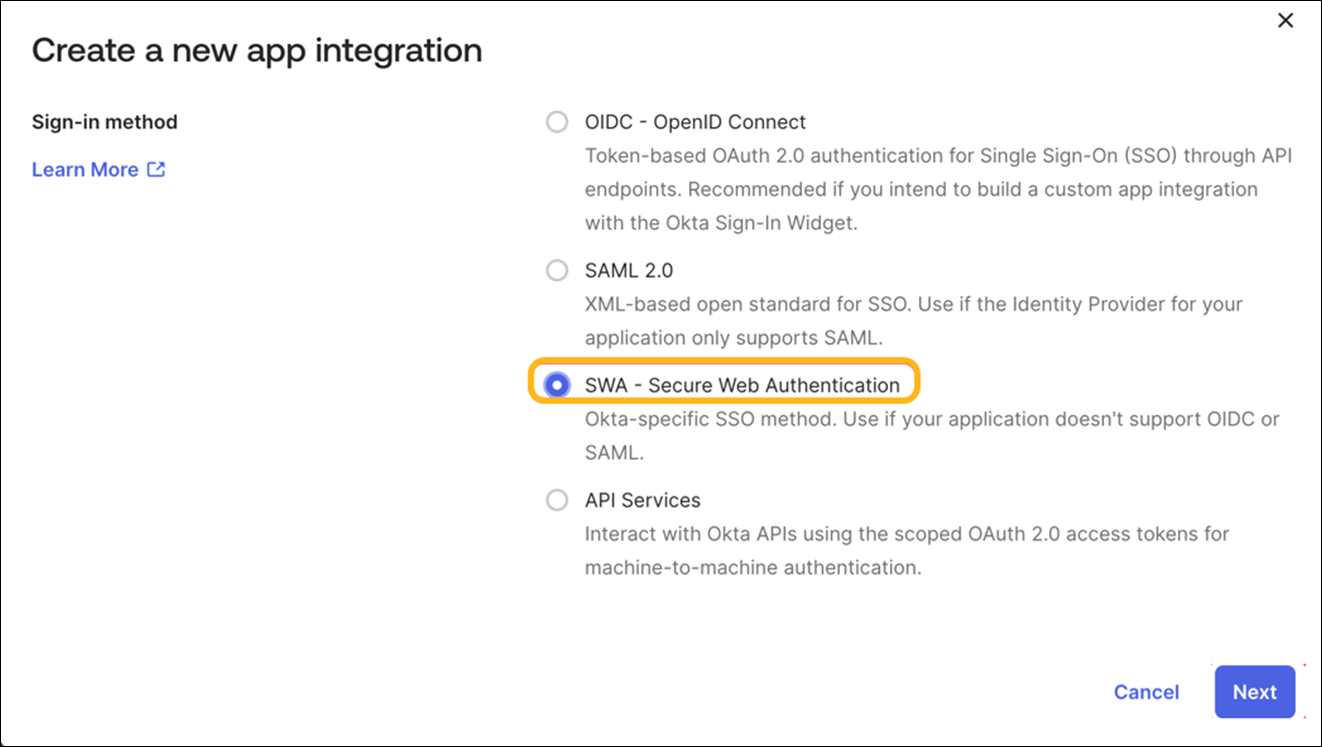
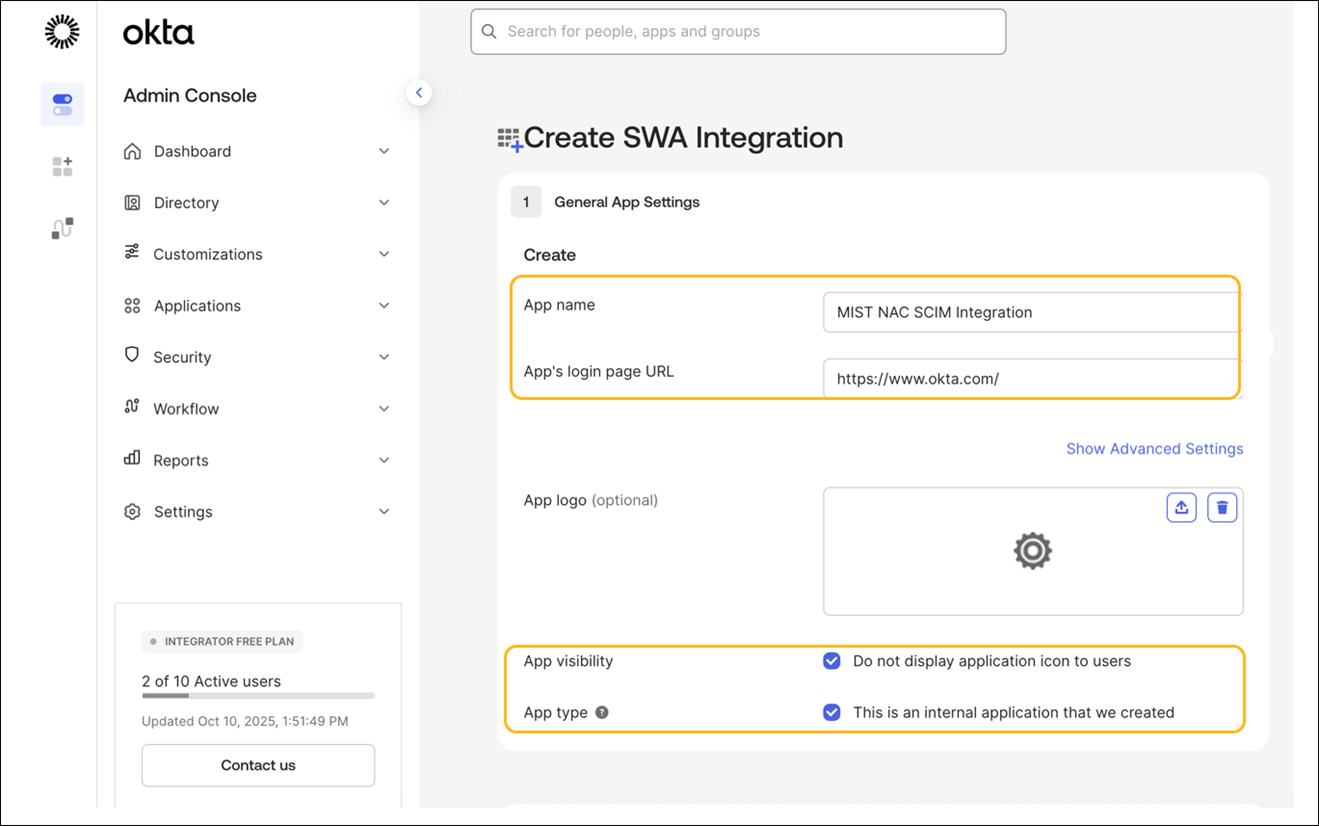
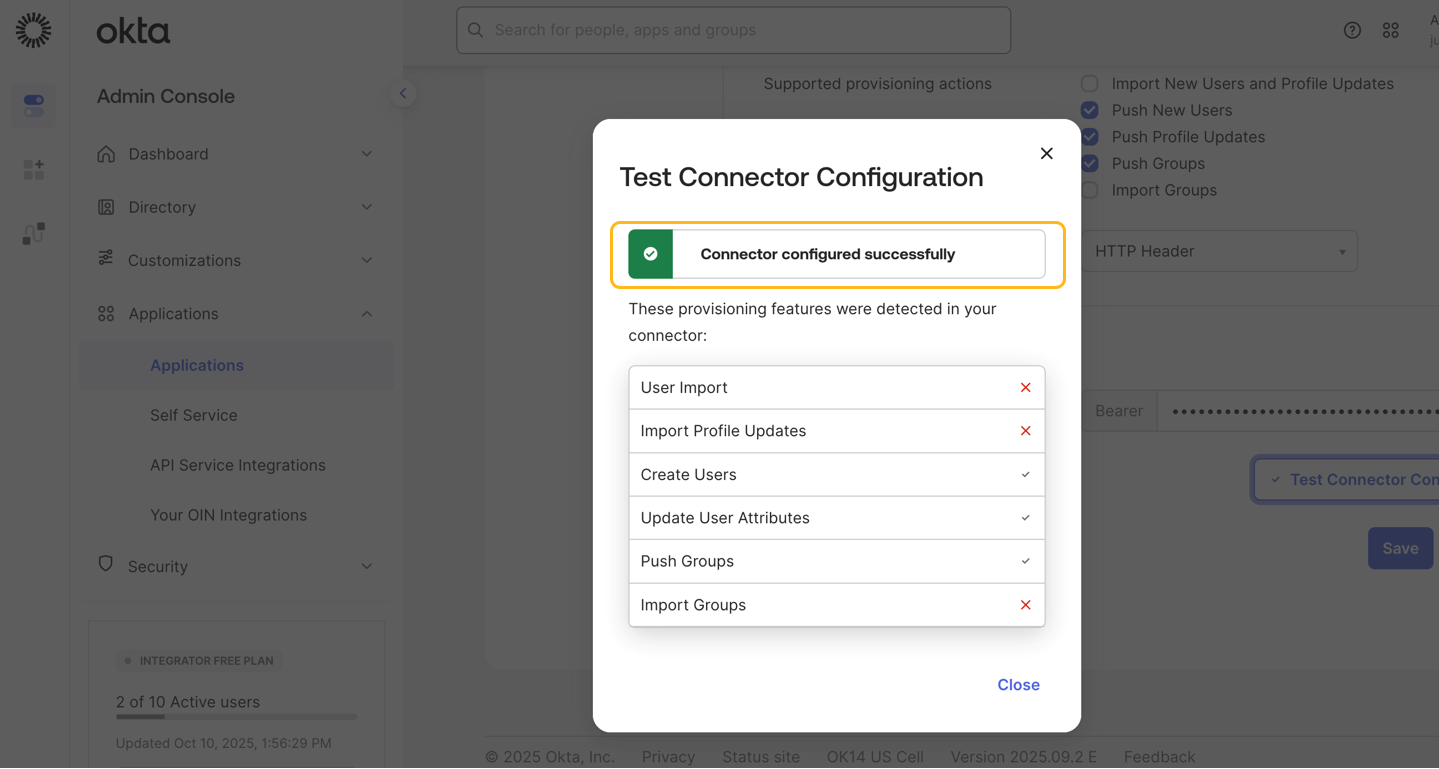
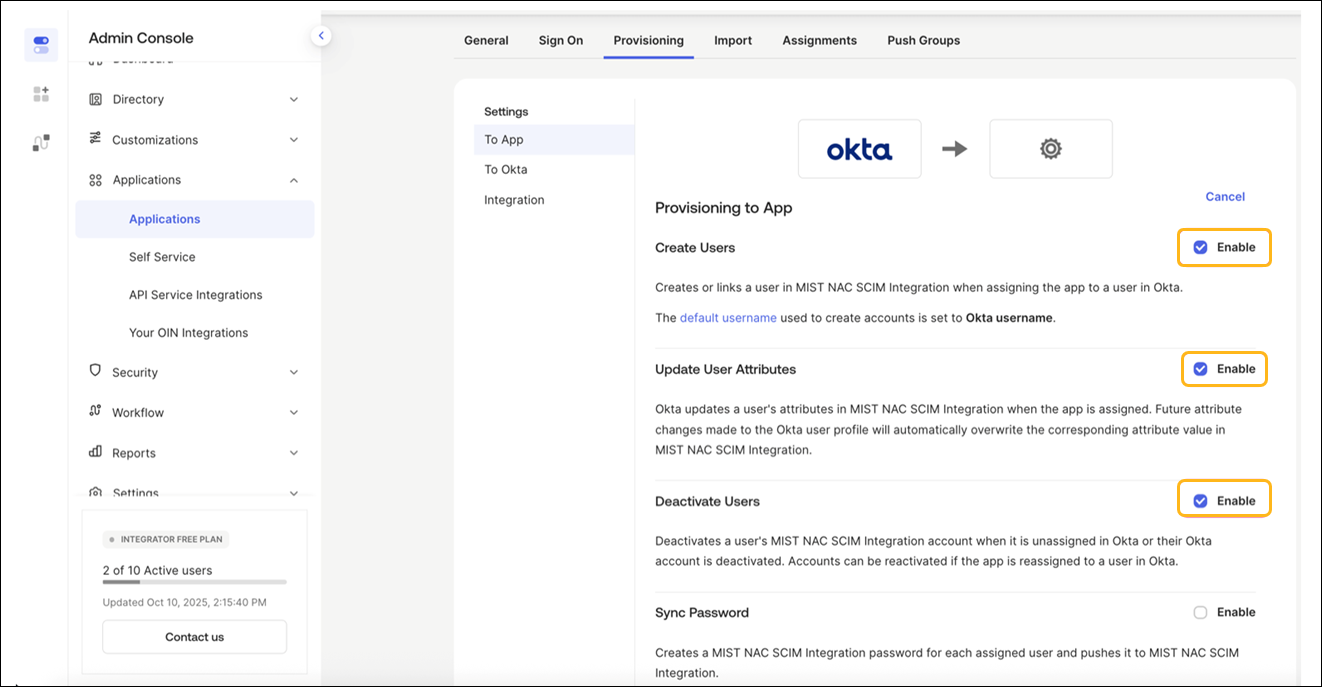
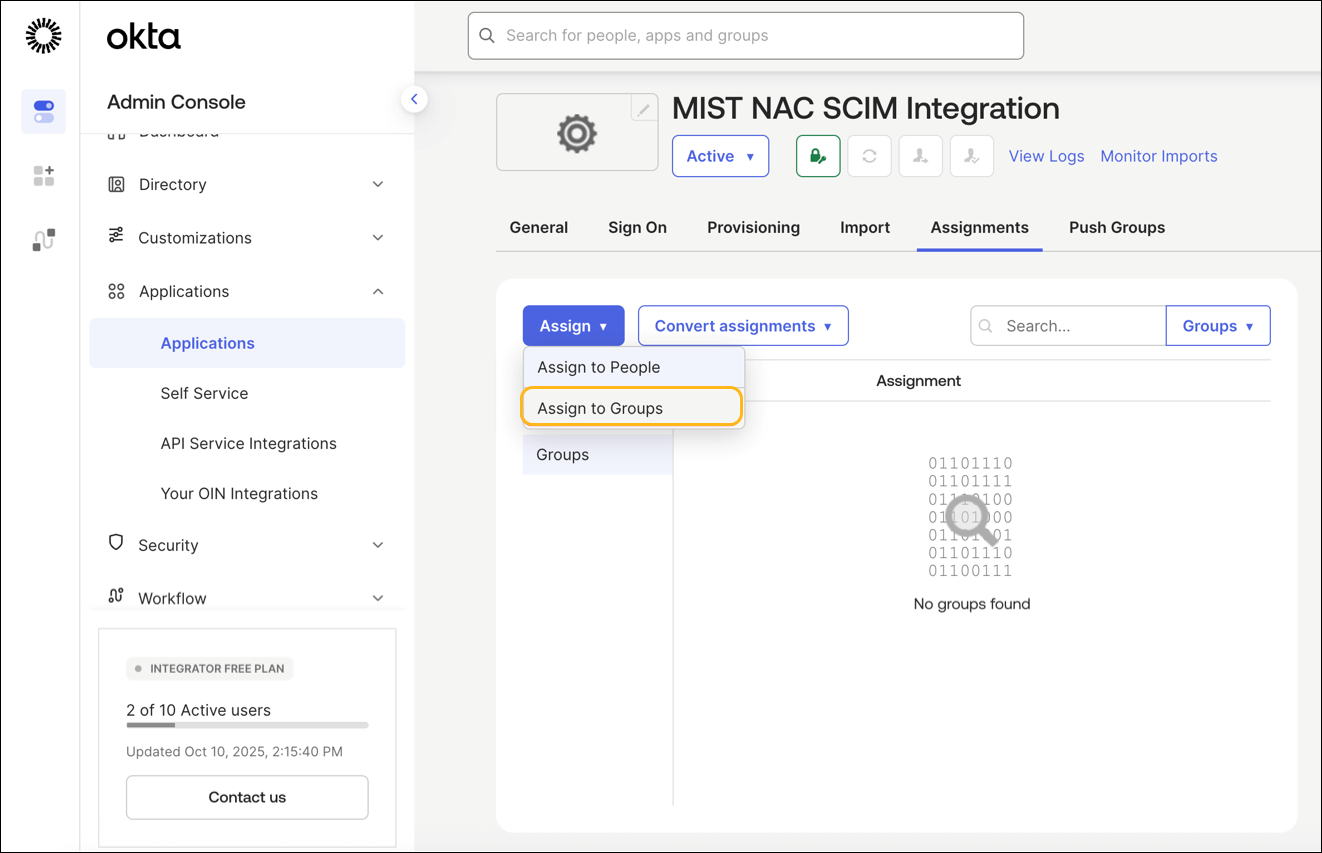
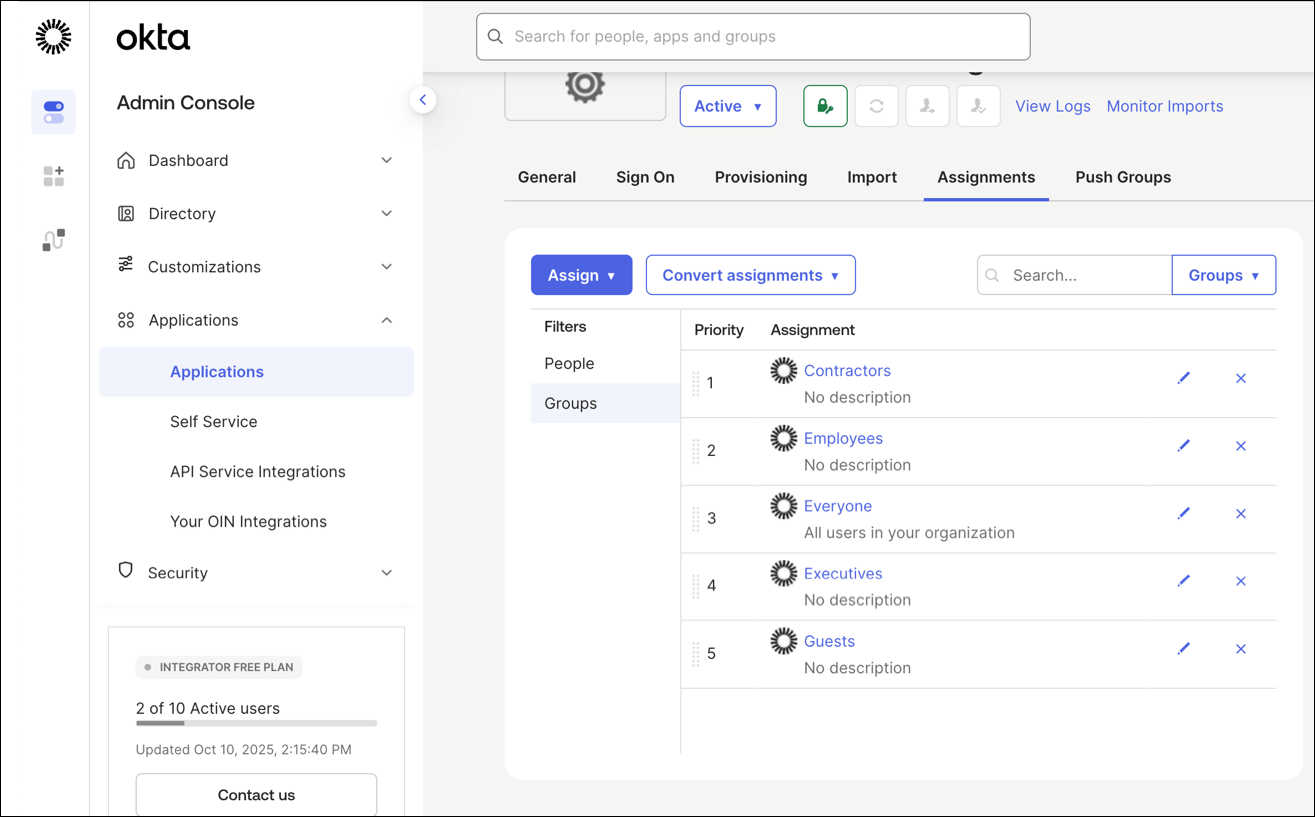
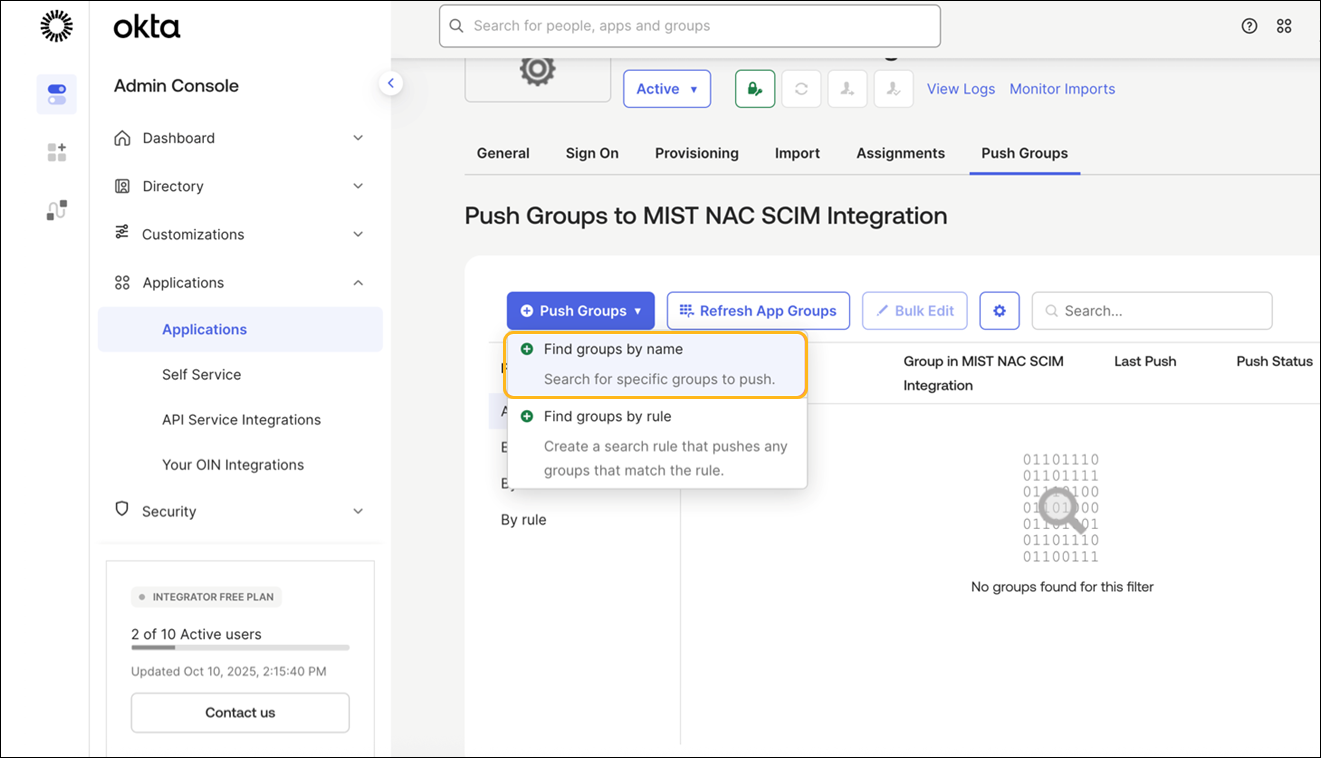
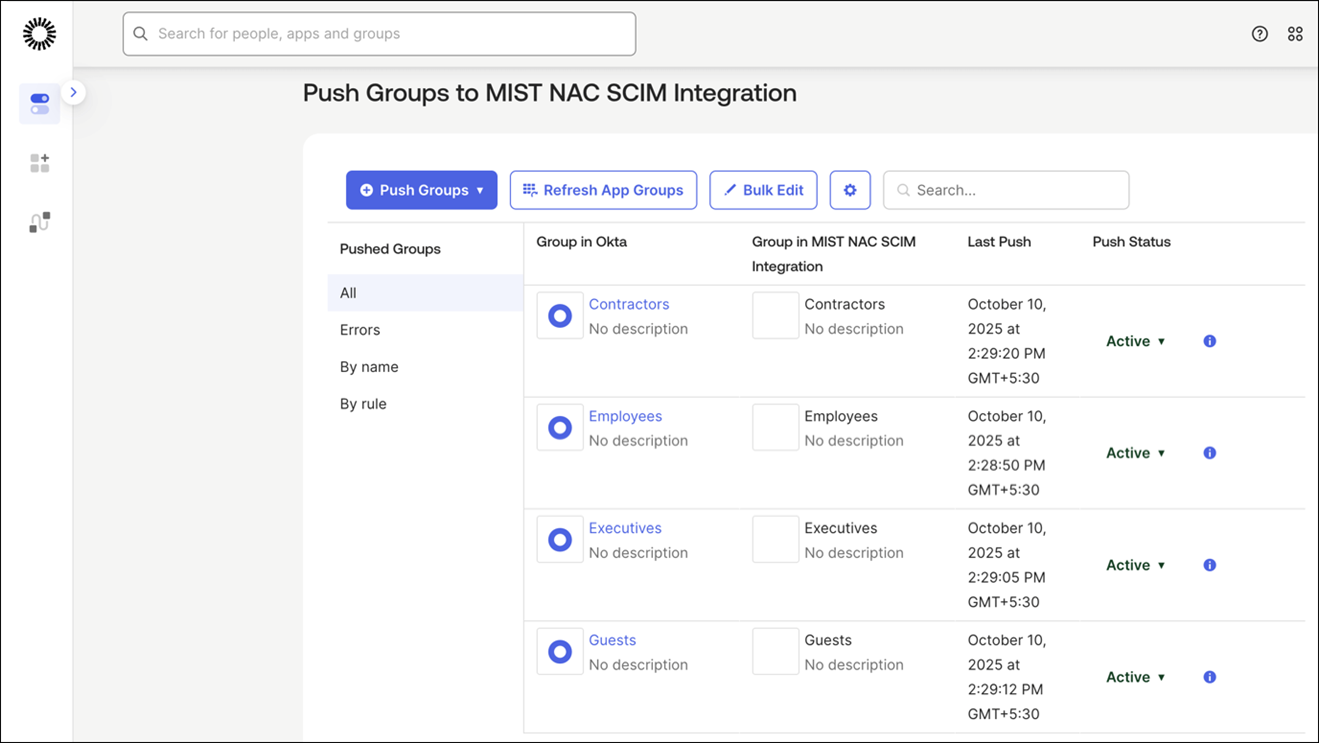
How to Integrate SCIM with Okta
Some of the screenshots included in this topic are sourced from third-party applications. Be aware that these screenshots might change over time and might not always match the current version of the applications.
Client Connection and Verification
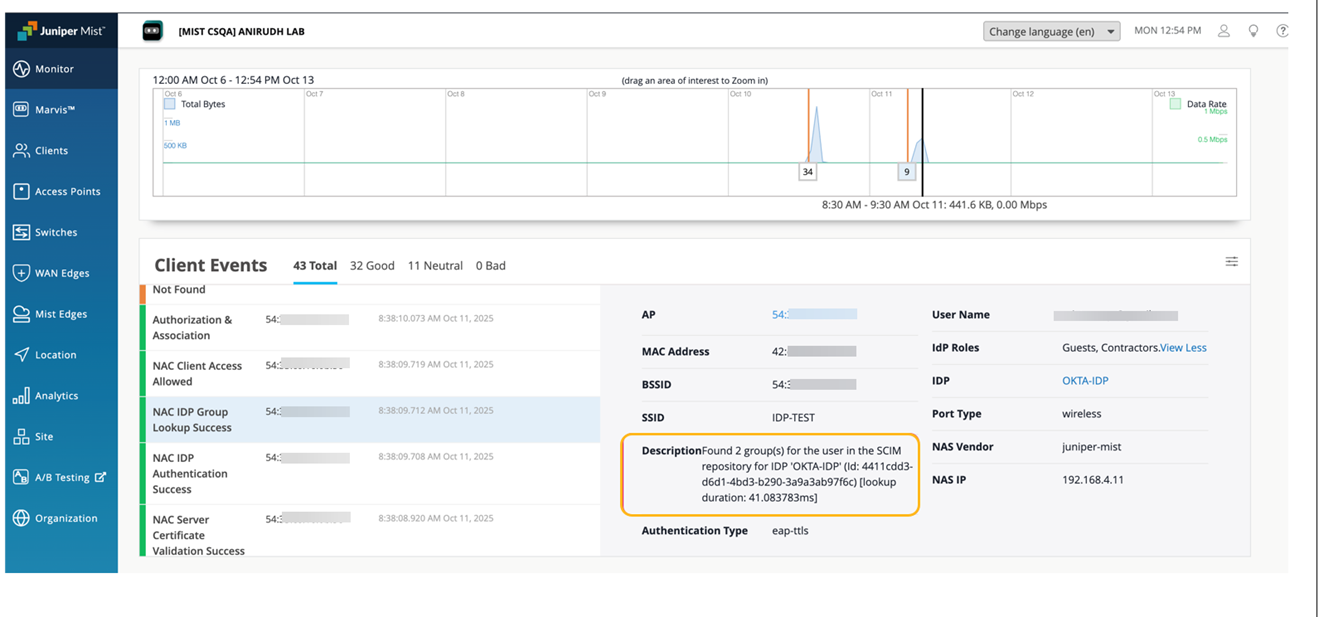
When a client is connected, you'll see the client events on the Insights page on the Mist portal. In the following examples, clients were connected using both EAP-TLS and EAP-TTLS authentication methods. In both cases, the authorization (that is, user group retrieval and mapping) was performed through the Mist Access Assurance SCIM database. This behavior can be verified in the event description, where the source of group information is shown as the SCIM repository.
Example 1: Client connected using the EAP-TLS authentication
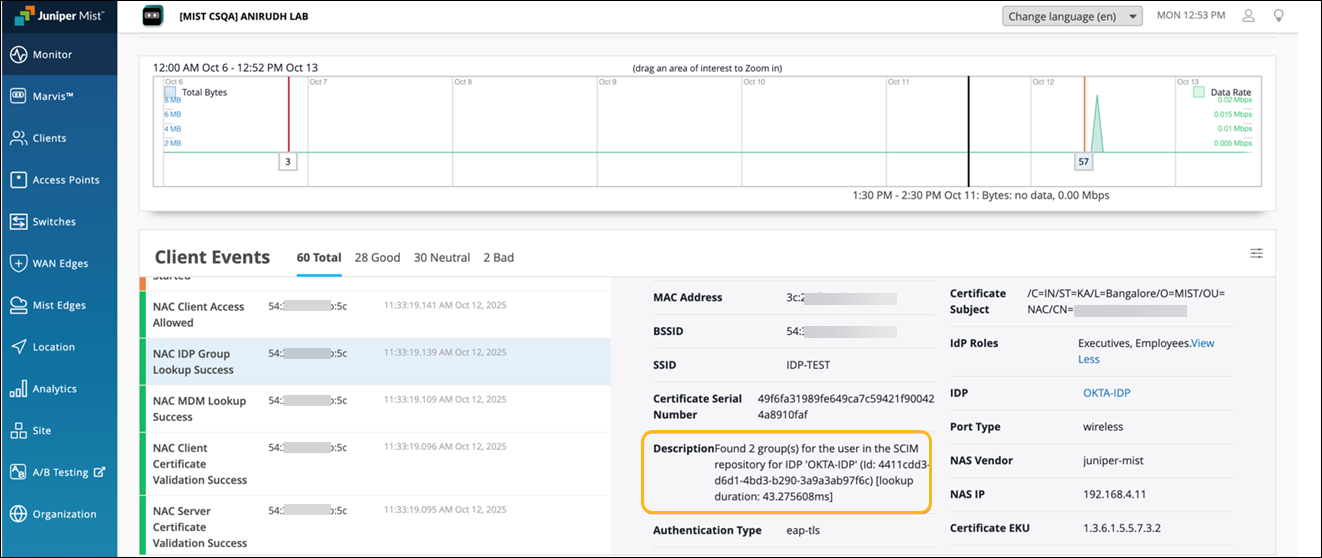
Example 2: Client connected using the EAP-TTLS authentication