Juniper Mist Authentication Proxy: Third-Party Device Support
Follow these steps to use Juniper Mist Authentication Proxy to support end-client and management-user authentication into third-party devices such as Cisco IOS devices.
Overview
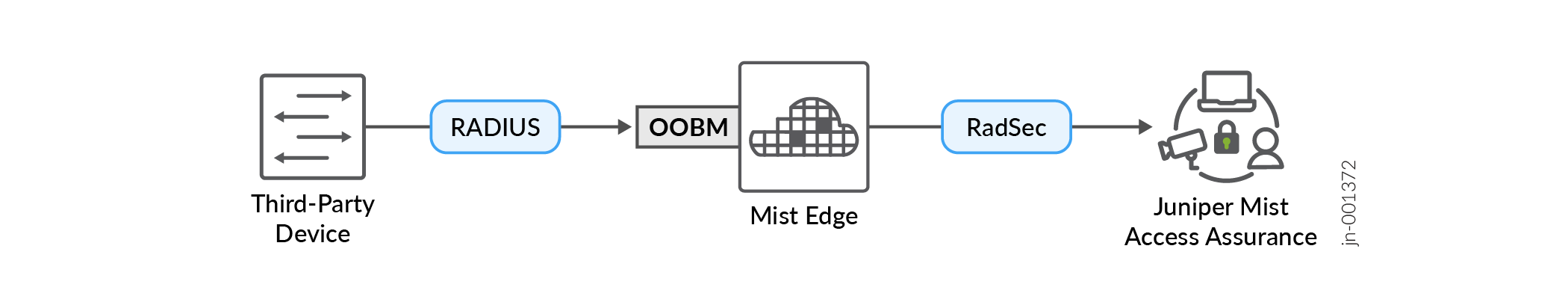
Juniper Mist™ Access Assurance supports end-client and management-user authentication into third-party devices by leveraging a Mist Auth Proxy application running on a Mist Edge platform.
Mist Edge is managed by the Mist Cloud and servers as a “gateway” for any non-Mist managed device that needs to:
-
Perform authentication of end-clients connecting to it (for example, a third-party switch, wireless LAN controller, or access point (AP)
-
Authentication management-users (for example, admin login to a firewall or switch CLI management interface)
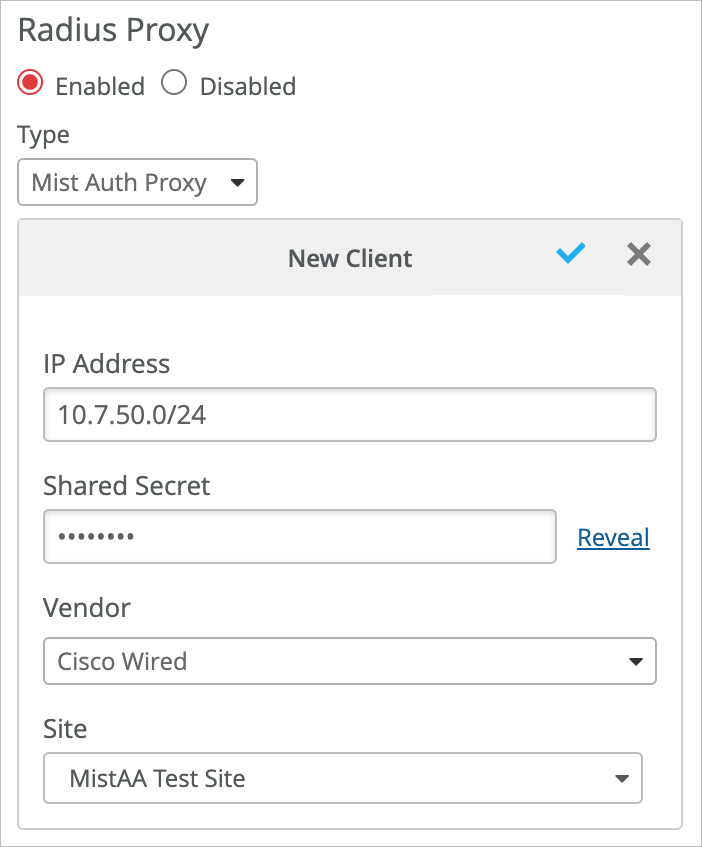
To set this up, you'll add your third-party devices as RADIUS clients at the Mist Edge Cluster. The cluster wraps all authentication traffic into a secured RadSec tunnel and sends it to the Mist Access Assurance cloud.
Design Considerations
-
Mist Edge can serve as authentication proxy from multiple sites; it is not required to have an edge per site.
-
For redundancy purposes, we recommend to install at least a few Mist Edges in different data centers or points of presense (PoP).
-
Mist Auth Proxy functionality is supported on all Mist Edge platforms. We recommend that you use a dedicated Mist Edge appliance (or VM) for Mist Auth Proxy and avoid combining Mist Auth Proxy with Tunterm or OCProxy functionality.
-
If you are using Mist Edge VM, note that you need only a single network interface and need ME-VM-OC-PROXY to unlock the Mist Auth proxy functionality.
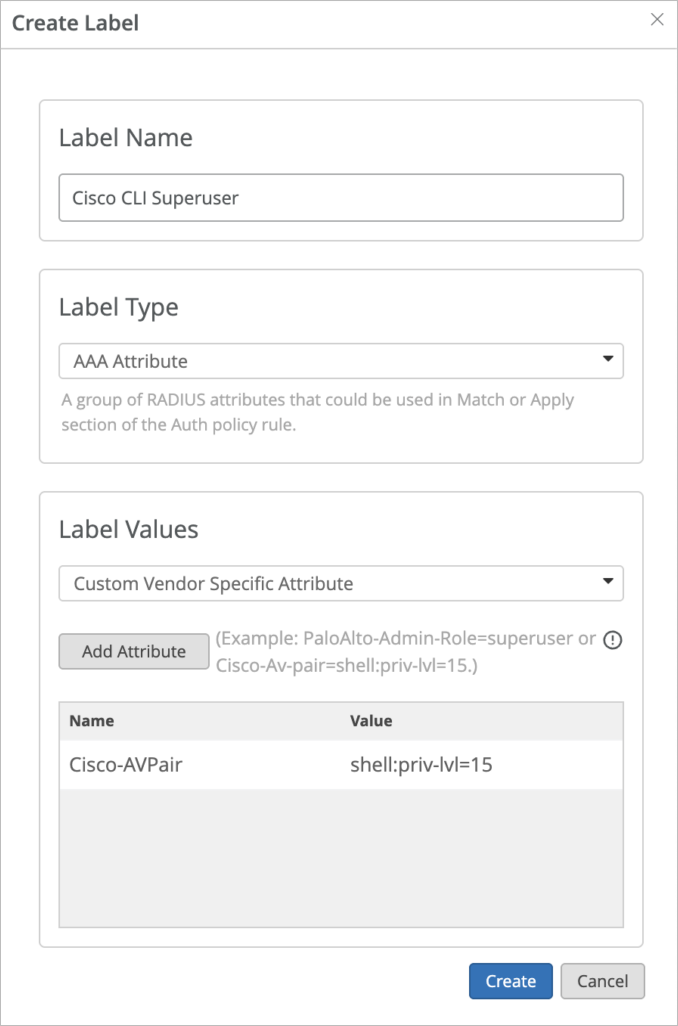
About RADIUS Attributes
- Based on the configured vendor, Mist Access Assurance automatically sends correct RADIUS Attributes in access-accept response to assign VLANs, roles (firewall filters) and session timeouts.
- Leverage custom vendor-specific RADIUS attribute labels to send specific attribute back in case of any special use cases.
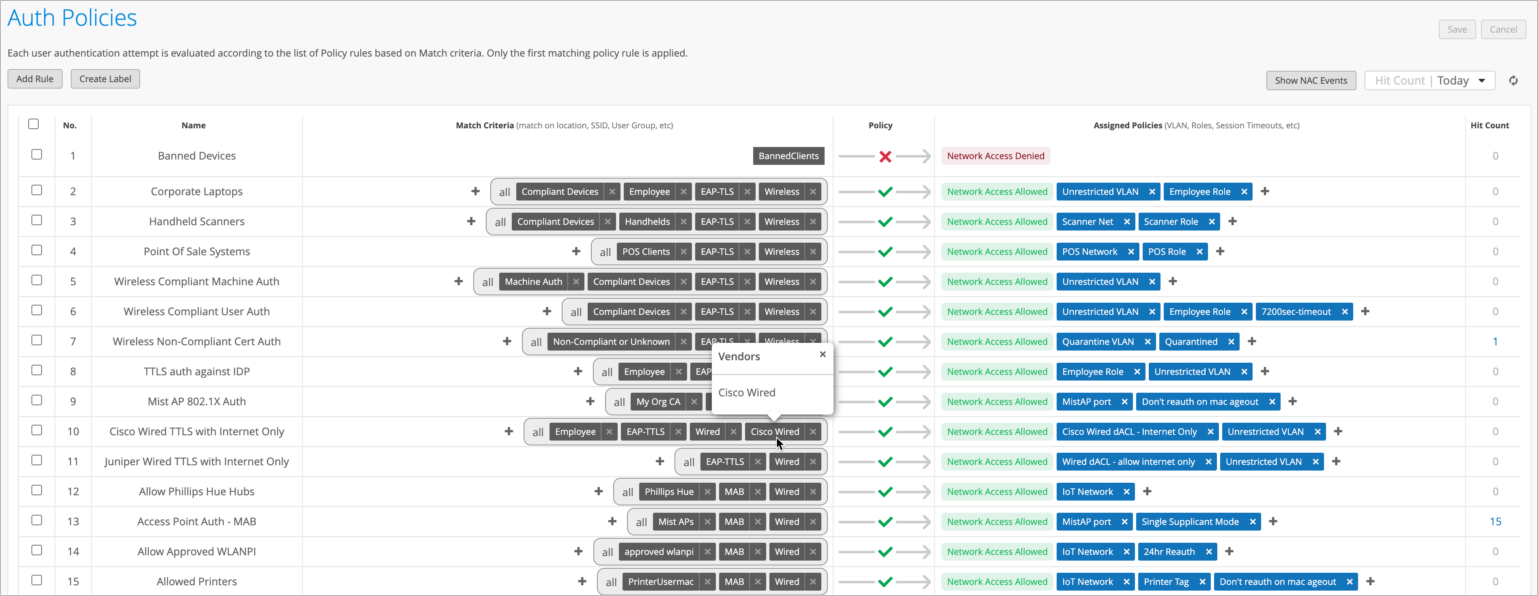
Add a Third-Party Vendor and Configure an Authentication Policy
Configuring Your Third-Party Vendor Device
Point your third-party vendor devices towards Mist Edge OOBM IP address as the RADIUS server.
If you're deploying multiple Mist Edges, add each Mist Edge as RADIUS server in failover or load-balance mode, depending on your third-party device support.
Example: Cisco IOS Device Configuration
! aaa group server radius Mist-Access-Assurance server name MistEdge deadtime 2 ! aaa authentication login default group Mist-Access-Assurance aaa authorization exec default group Mist-Access-Assurance ! ! ! radius server MistEdge address ipv4 <mist edge OOBM IP Address> auth-port 1812 acct-port 1813 key <shared secret> !
user123@company.net@10.148.2.21
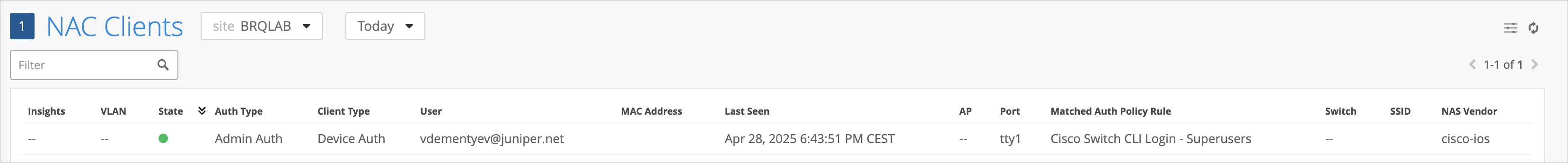
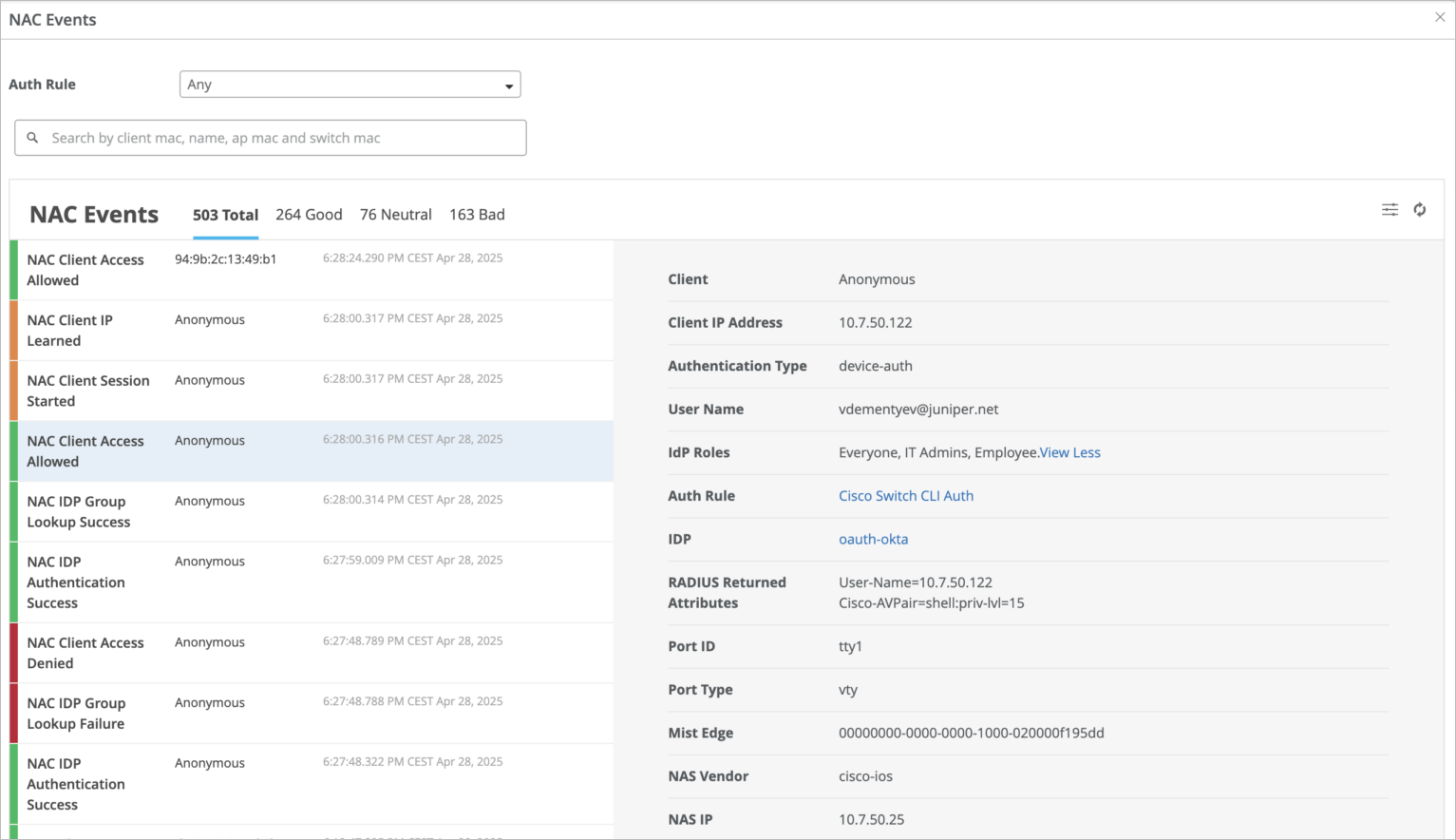
Checking Login Records
As part of your verification process for your new auth policy, you can check the status of all login attempts on the NAC Clients page and the NAC Events page.