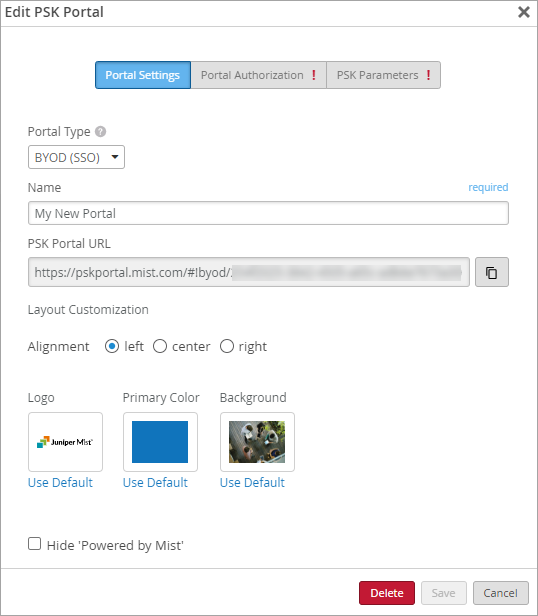
Self-provisioning for IoT and Personal Devices
Automate client onboarding at scale, for personal devices and IoT, with secure self provisioning.
Wireless users in environments like dormitories can securely self-provision their personal devices such as Xboxes, Apple TV, and Roku. Likewise, unattended IoT devices can securely and automatically join a specified VLAN, or network segment. We call this the Personal Network Experience. And because it eliminates the need for client MAC address registration and IT intervention, it is an ideal solution for providing Wi-Fi access at scale.
Self provisioning with the Personal Network Experience works by connecting a SAML-compliant identity provider (IDP), for example, Microsoft Entra ID, to the Mist Active Assurance portal. Users log on to the WLAN, where they are redirected to the single-sign-on service for authentication and authorization. Mist assigns authenticated users a personal preshared key (PSK) that is specific to both the individual user and/or the SSID. Using personal PSKs also enables micro-segmentation, which means you can have users connect to a specific VLAN according to their role or profile. The same is true for IoT devices; they can be automatically connected to a specific VLAN, a best practice for protecting against IoT take-over attacks.
In the Mist console, you can configure both the complexity of the required passphrase, and the frequency of key rotation.

During self-provisioning, laptop users can generate a unique passphrase, then copy and paste it into the portal when prompted. Or, if working from a mobile device, they can have the passphrase emailed to them. Generated passphrases expire after 24 hours.
Before You Begin
- Obtain and activate a Juniper Mist™ Access Assurance subscription. For information about subscription management, see the Juniper Mist Management Guide.
- In your Juniper Mist organization, configure at least one organization-level WLAN with Multi-PSK enabled (either local or cloud PSK options are fine). For help with WLAN configuration, see the Juniper Mist Wireless Assurance Configuration Guide.
-
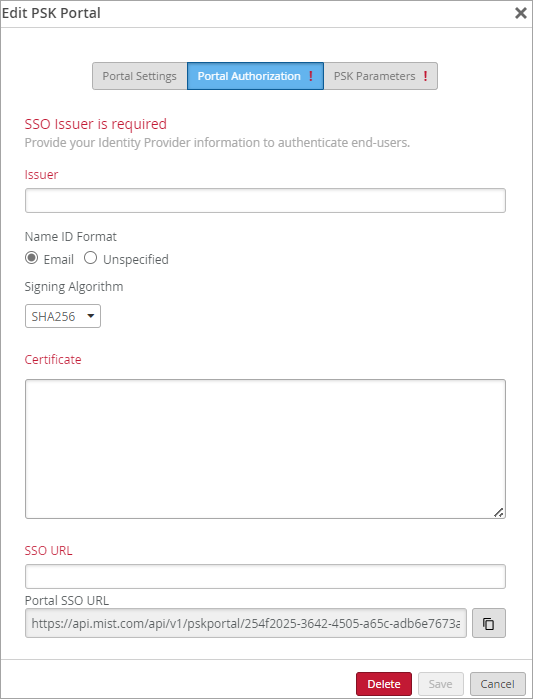
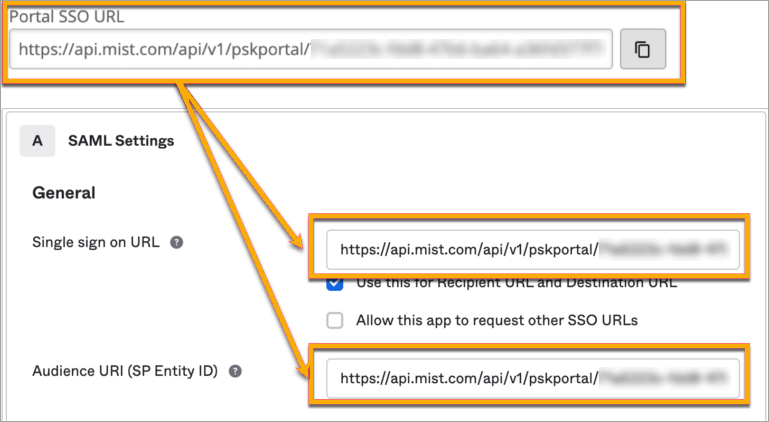
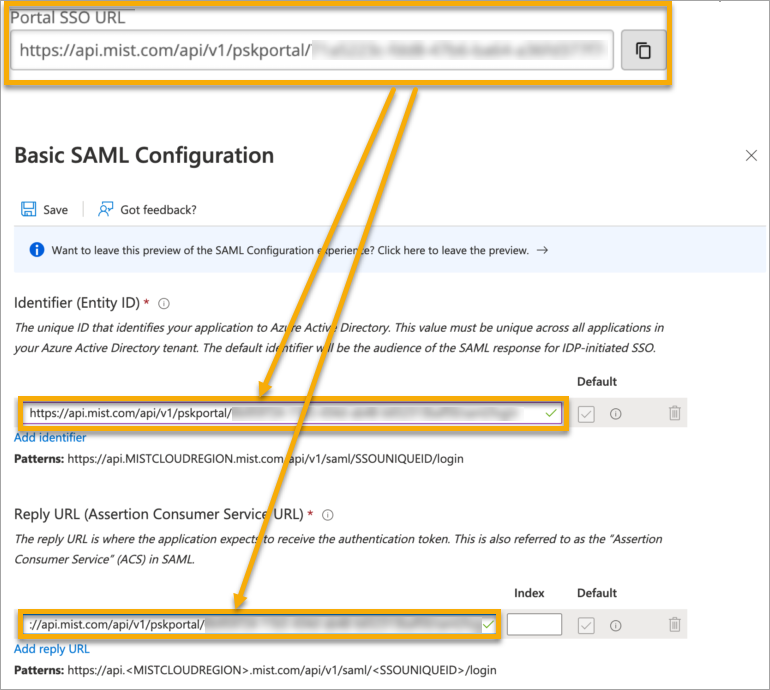
In your IdP admin console, configure a SAML 2.0 app integration. Your PSK portal will integrate with this application to enable Single Sign-On (SSO) access to your portal users. You can use a wide variety of IdPs (such as Okta and Microsoft Azure), as long as they support SAML 2.0. For help setting up a SAML 2.0 app integration, see your IdP documentation.
Copy the following information from your SAML 2.0 app integration, and save it so that you can use it to set up your PSK portal in Juniper Mist.
-
Signing Algorithm
-
Issuer ID (this key may vary, for example, in Okta, this value is called Identity Provider Issuer and in Azure, it's called Azure AD Identifier.
-
SSO URL (this key may vary, for example, in Okta, this value is called Identity Provider Single Sign-On URL and in Azure, it's called Login URL.
-
Certificate—Copy the full text of the certificate, from the BEGIN CERTIFICATE line through the END CERTIFICATE line.
-
Configure Self-Provisioning
To set up client onboarding with a BYOD PSK Portal: