ON THIS PAGE
Configure Captive Portal for Web Authentication and Firewall User Authentication
Learn how to configure captive portal for Web authentication and firewall user authentication using J-Web.
Overview
What Is Captive Portal?
Captive portal is a method of authenticating devices that need to connect to a network. On an SRX Series Firewalls, you can enable captive portal to redirect Web browser requests to a login page that prompts you to enter your username and password. After successful authentication, you can proceed with the original page request and subsequent network access.
What Is Web Authentication?
With a Web authentication method, you point a browser to an IP address on a device that is enabled for Web authentication. This action initiates an HTTPS session on the IP address that hosts the Web authentication feature on the device. The device then prompts you to enter your username and password, and the result is cached on the device. When the traffic later encounters a Web authentication policy, your access is allowed or denied based on the previous Web authentication results.
You can use other authentication methods as well, but we will not cover those methods in this document. However, we describe each of those methods in brief:
-
Pass-through authentication—Pass-through user authentication is a form of active authentication. In this method, the device prompts you to enter a username and password. If authentication validates your identity, you are allowed to pass through the firewall and access the requested resources.
-
Pass-through with web-redirect—When using this authentication method for HTTPS client requests, you can use the web-redirect feature to direct your requests to the device's internal webserver. The webserver sends a redirect HTTPS response to the client system, directing it to reconnect to the webserver for user authentication. The interface that the client’s request arrives at is the interface on which the redirect response is sent.
What Is Firewall User Authentication?
A firewall user is a network user who must provide a username and password for authentication when initiating a connection across the firewall. Junos OS enables administrators to restrict or to permit firewall users’ access to protected resources (in different zones) behind a firewall based on their source IP address and other credentials. After defining the firewall users, you can create a policy that requires the users to authenticate using one of the three authentication methods (Web, pass-through, or pass-through with web-redirect).
Workflow
Scope
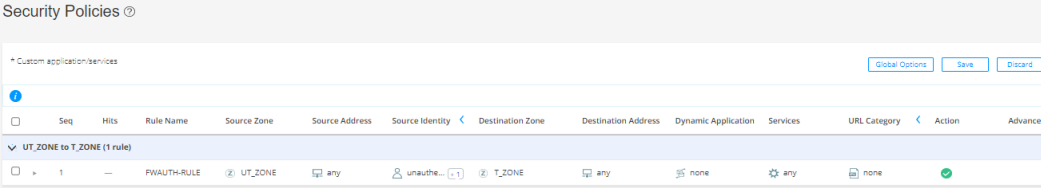
Here’s a sample topology (see Figure 1), which comprises:
-
A firewall user’s device that acts as a client.
-
An SRX Series Firewall that has access to the Internet.
-
A network device that acts as an HTTPS server.
In this sample topology, you’ll use J-Web on the SRX Series Firewall to do the following tasks:
The values used to configure the sample topology are only examples.
|
Step |
Action |
|---|---|
|
1 |
Create a logical interface on ge-0/0/3, assign it the IP address 203.0.113.35, and enable Web authentication. Note:
In this example, the firewall user system IP address is 203.0.113.12, which is in the same subnet as 203.0.113.0/24. Create a logical interface on ge-0/0/2 and assign it the IP address 192.0.2.1. Note:
In this example, the HTTPS server IP address is 192.0.2.1. |
|
2 |
Create an access profile (FWAUTH) and define local authentication services. |
|
3 |
Configure Web authentication settings to display the successful login message. |
|
4 |
Create an untrust (UT_ZONE) and a trust (T_ZONE) zones and assign the ge-0/0/3 and ge-0/0/2 interfaces, respectively. |
|
5 |
Configure captive portal for Web authentication and firewall user authentication in the security policy rules (FWAUTH-RULE). |
|
6 |
Verify that the configured values work for a firewall user:
|
Before You Begin
-
The values used to configure the sample topology are only examples. You can change any details necessary to match your network configuration.
-
Ensure that the SRX Series Firewall you use in this example runs Junos OS Release 21.4R1 or later.
-
Ensure that your device has the required certificates installed to allow authentication. In this example, we'll use cert1, a self-signed certificate.
Step 1: Create a Logical Interface and Enable Web Authentication
In this step, you’ll do the following tasks:
-
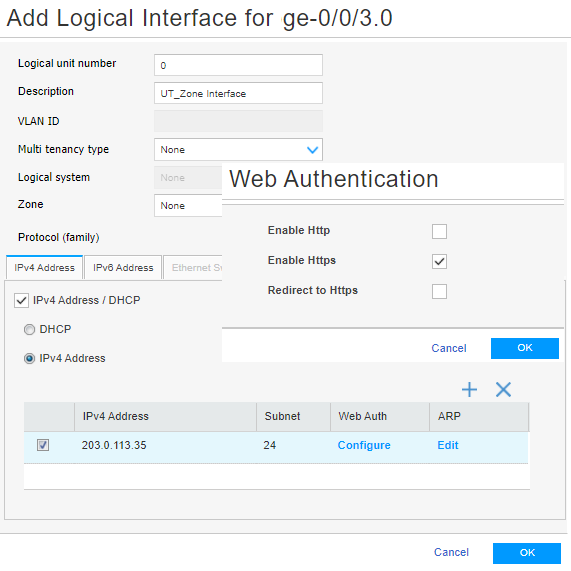
For the ge-0/0/3 interface on the SRX Series Firewall:
-
Create a logical interface for an untrust zone.
-
Assign the IPv4 address 203.0.113.35 to the interface.
Note:You’ll use the same IP address for enabling captive portal.
-
Enable HTTPS on the interface for Web authentication.
-
-
For the ge-0/0/2 interface on the SRX Series Firewall:
-
Create a logical interface for a trust zone.
-
Assign the IPv4 address 192.0.2.1 to the interface.
-
You are here (in the J-Web UI): Network>Connectivity>Interfaces
To create a logical interface for an untrust zone and to enable Web authentication:
To create a logical interface for a trust zone:
-
Select ge-0/0/2 and then select Create>Logical Interface on the upper-right corner of the Interfaces page.
The Add Logical Interface for ge-0/0/2.0 page appears.
-
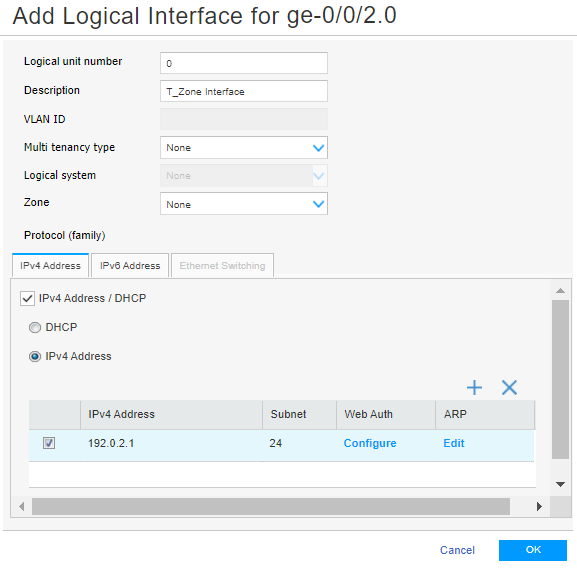
Specify the following details:
Field
Action
Logical unit number
Type 0.
Description
Type T_Zone Interface.
VLAN ID
This field is not editable.
Multi tenancy type
Select None from the list.
Logical system
This field is not editable.
Zone
Select None from the list.
In a later step, we'll create a trust zone (T_ZONE) and assign the ge-0/0/2 interface to it. See Step 4: Create Security Zones and Assign Interfaces to the Zones.
VLAN ID
This field is not editable.
Protocol (family) - IPv4 Address
IPv4 Address / DHCP
Select the check box to enable the IPv4 Address/DHCP configuration.
IPv4 Address
-
Select IPv4 Address.
-
Click +.
-
IPv4 Address—Type 192.0.2.1 (HTTPS server).
-
Subnet—Select 24 using the up or down arrow.
-
Web Auth—Leave as is.
-
ARP—Leave as is.
-
-
Click OK to save the changes.
Good job! You’ve created a logical interface on ge-0/0/2 with IP address 192.0.2.1 for the HTTPS server.
-
Click Commit (at the right-side of the top banner) and select Commit configuration to commit the changes now.
The successful-commit message appears.
You can also choose to commit all configuration changes at once, at the end of Step 5: Enable Web or Firewall User Authentication for Captive Portal in the Security Policy.
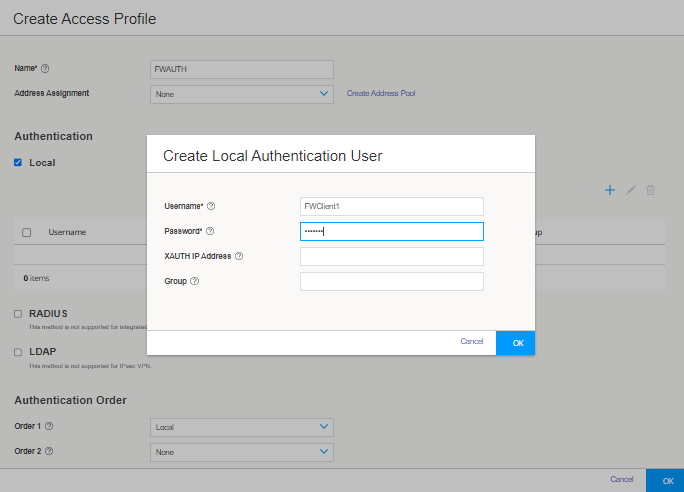
Step 2: Create an Access Profile
Let’s create an access profile to define local authentication services. You will use this access profile in Web authentication settings and security policies.
You are here (in the J-Web UI): Security Services>Firewall Authentication>Access Profile
To create an access profile:
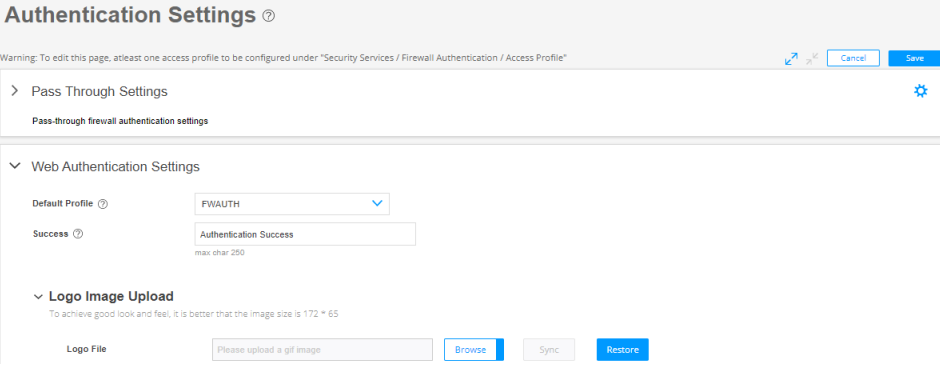
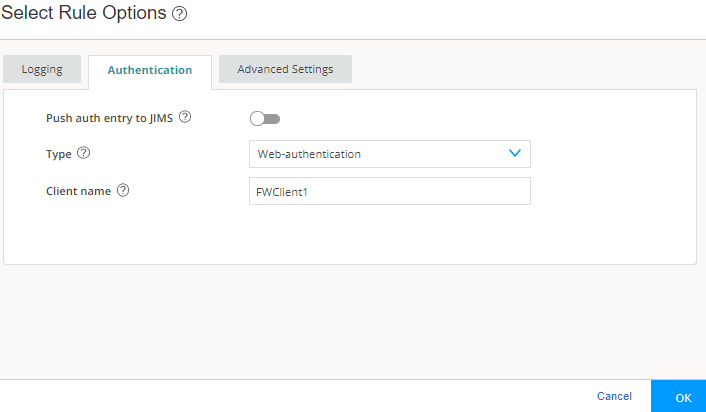
Step 3: Configure Web Authentication Settings
We’ll now assign the created access profile, define a successful-login message, and upload the logo image. You use this image for both Web authentication and captive portal.
You are here (in the J-Web UI): Security Services>Firewall Authentication>Authentication Settings
To configure Web authentication settings:
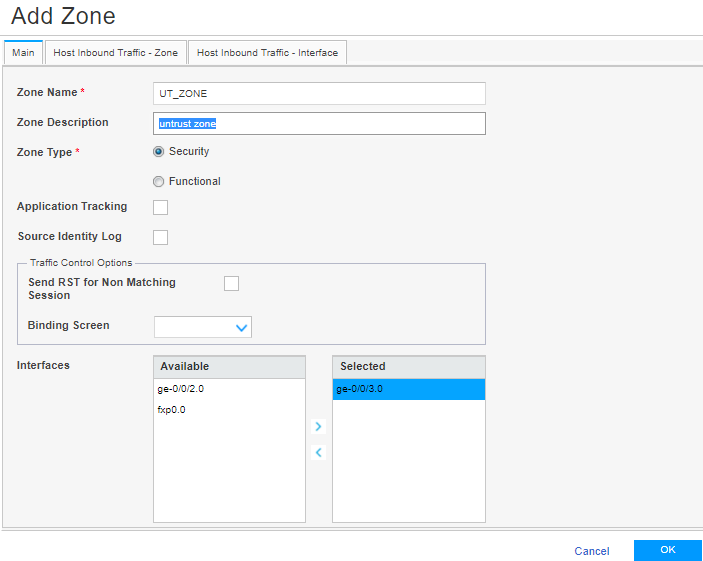
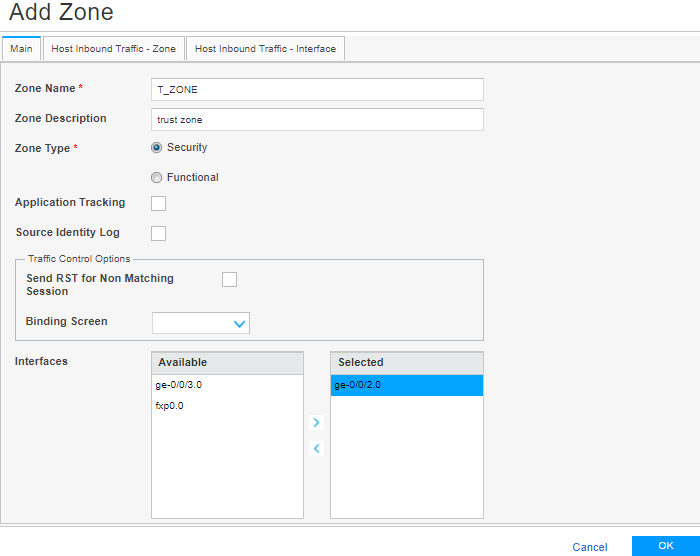
Step 4: Create Security Zones and Assign Interfaces to the Zones
You create a security zone to define one or more network segments that regulate inbound and outbound traffic through policies.
We’ll now separately create:
-
An untrust zone (UT_ZONE) and assign the ge-0/0/3 interface to it.
-
A trust zone (T_ZONE) and assign the ge-0/0/2 interface to it.
You are here (in the J-Web UI): Security Policies & Objects>Zones/Screens
To create UT_ZONE (untrust zone) and T_ZONE (trust zone) and to assign the defined interfaces to the zones:
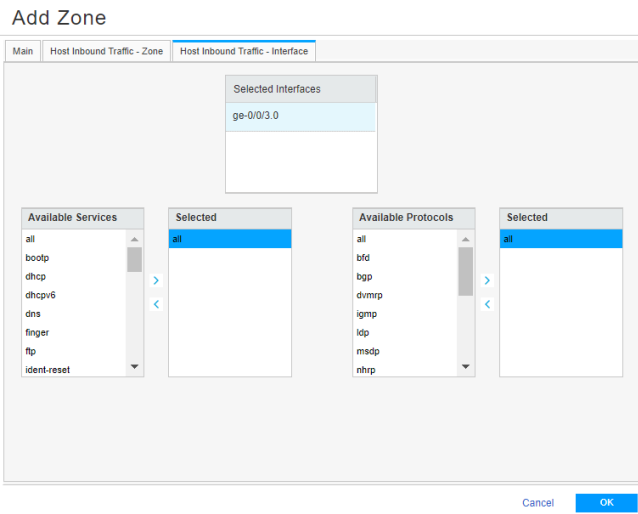
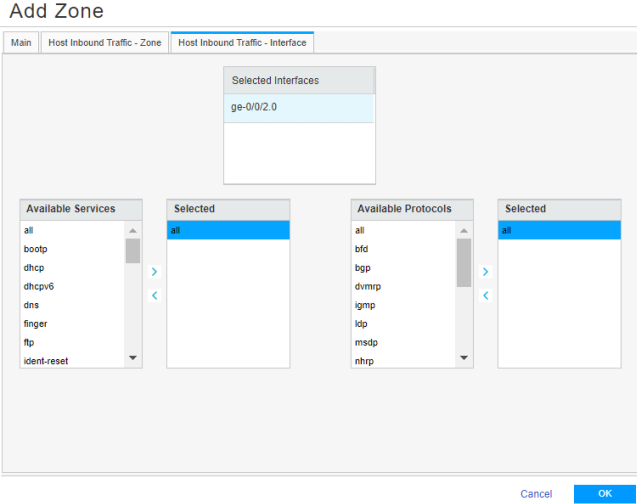
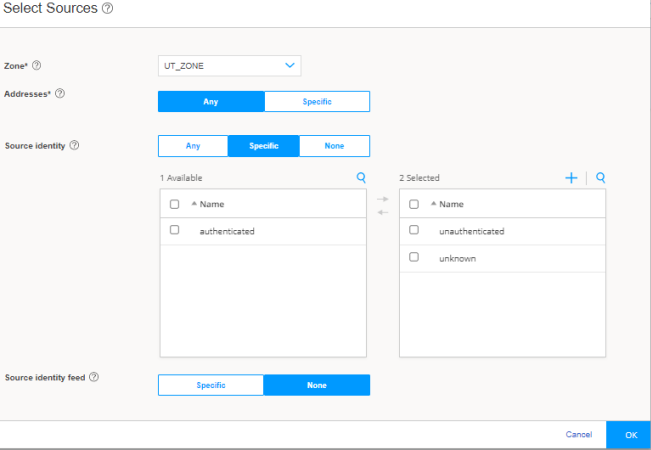
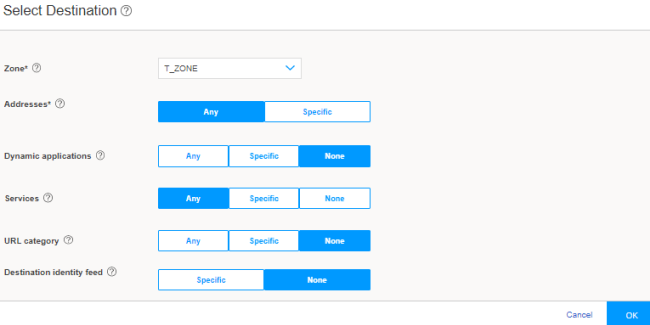
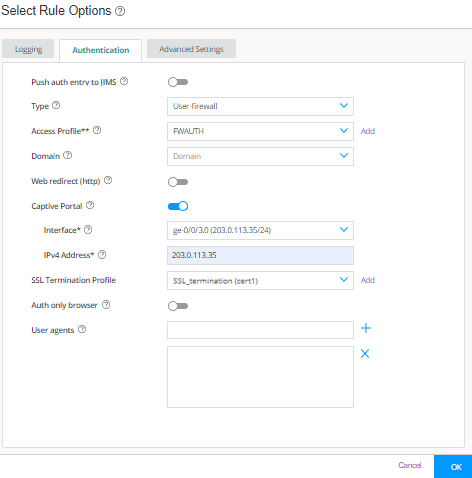
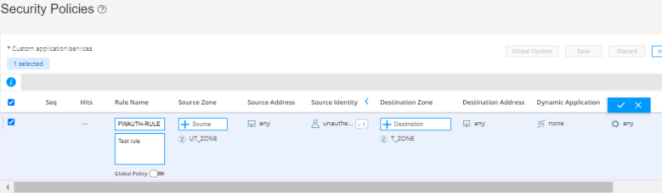
Step 5: Enable Web or Firewall User Authentication for Captive Portal in the Security Policy
We’ll now enable captive portal in the security policy rules to redirect a client HTTPS request to the internal HTTPS server of the device.
You are here (in the J-Web UI): Security Policies & Objects>Security Policies
To configure security policy rule for captive portal:
Step 6: Verify the Web Authentication and User Authentication Configuration
Purpose
The final step! Let’s see whether your configuration works for a firewall user:
-
For Web authentication, you’ll successfully authenticate using https://203.0.113.35. This is the same IPv4 address that you configured in Step 1: Create a Logical Interface and Enable Web Authentication.
-
For firewall user authentication, you’ll successfully authenticate using https://203.0.113.35 and then get redirected to https://192.0.2.1 for accessing the HTTPS server. These are the same IPv4 addresses that you configured in Step 1: Create a Logical Interface and Enable Web Authentication.
Action
To verify the Web authentication configuration:
-
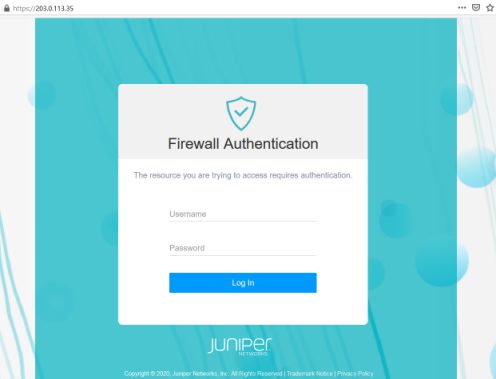
Type https://203.0.113.35 in your Web browser.
The Firewall Authentication login page appears.
-
Type the following credentials, and then click Log In.
-
Username—FWClient1
-
Password—$ABC123
Congratulations! You are successfully authenticated. You can also see the success message Authentication Success that you configured.
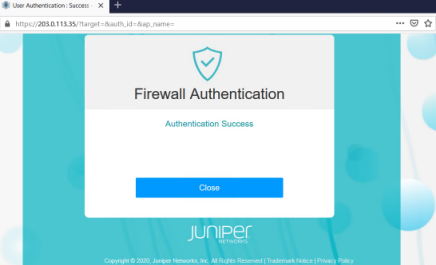
-
-
Click Close.
To verify firewall user authentication:
-
Type https://192.0.2.1 in your Web browser.
You are redirected to https://203.0.113.35 for Web authentication.
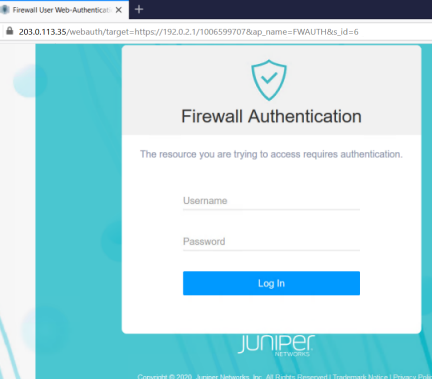
-
Type the following credentials, and then click Log In.
-
Username—FWClient1
-
Password—$ABC123
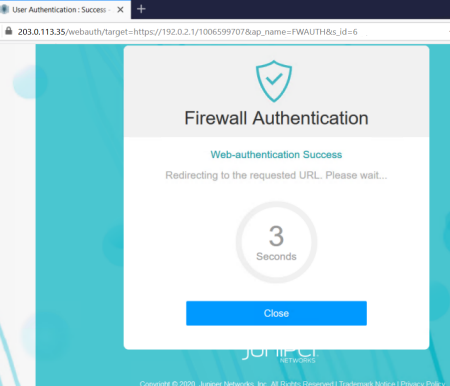
Congratulations! You are successfully authenticated. Soon, you’ll be redirected to https://192.0.2.1, and you’ll be able to access the HTTPS server.
-
What's Next
To keep going, visit the J-Web for SRX Series Documentation page in the Juniper TechLibrary.