Appendix: Next-Generation Firewall JVD Configuration
Generic Workflows and Operations for Creating the Data Center Next-Generation Firewall Topology
This overview illustrates how to use the Juniper SRX Series Firewall CLI and Juniper Security Director Cloud console (the GUI) to provision the data center next-generation firewall architecture. Conceptually, the Juniper SRX Series Firewall is configured on the data center edge to provide visibility and control of traffic that is originating from the following:
- Traffic originating from trusted clients outbound to the Internet. (South-North Traffic)
- Traffic originating from untrusted environment reaching inbound to services configured in the data center. (North-South Traffic)
- Traffic originating from the trusted clients using services hosted with in the data center. (East-West Traffic)
Figure 1 illustrates the workflow for configuring the Juniper SRX Series Firewall using the Junos OS CLI and Juniper Security Director Cloud console.
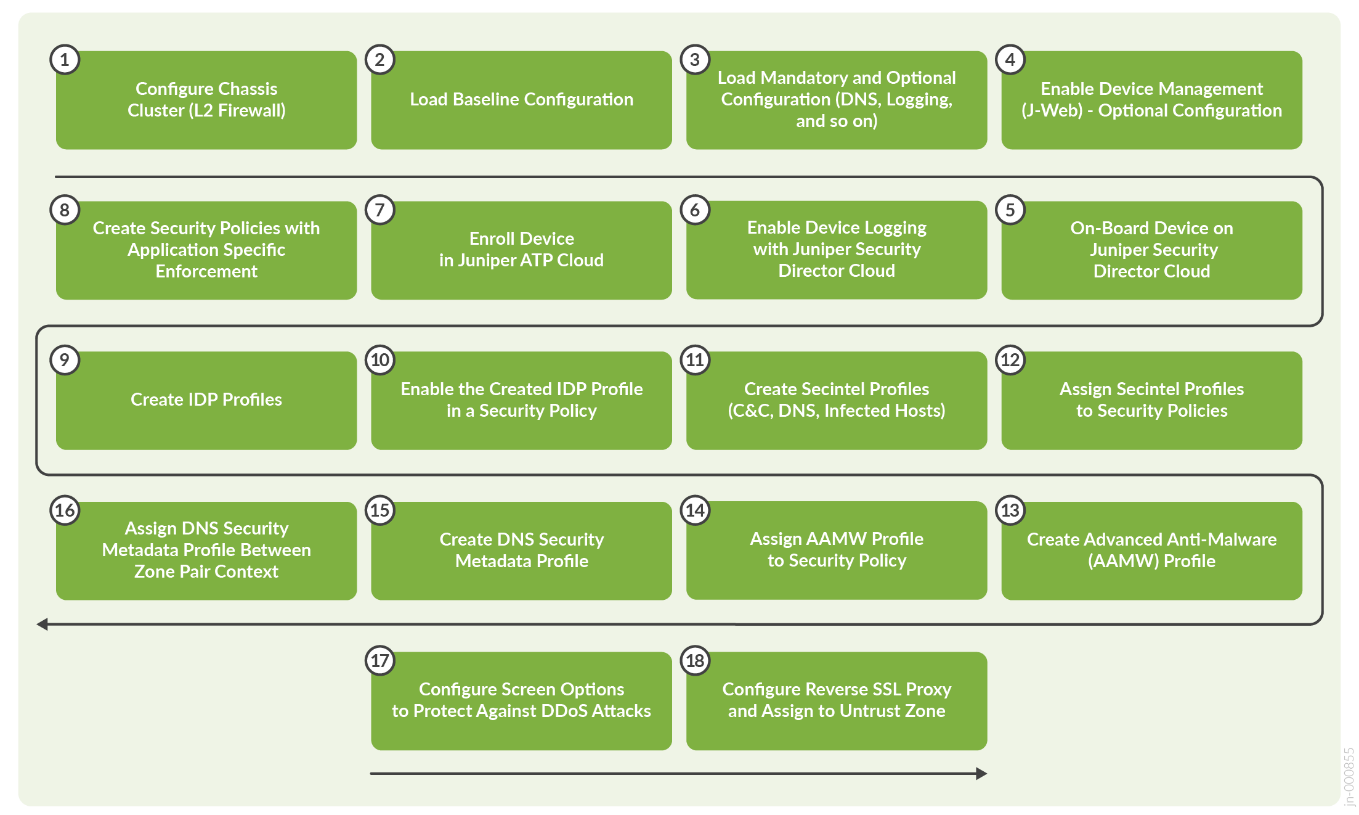
The sequence of configuration tasks in this example is as follows:
- Configure chassis cluster through CLI: Clustering enables high availability.
- Load baseline configuration with interface, zones, addresses, services, firewall policies, NAT, and default routing: Baseline the configuration for the device to carry traffic and able to reach out to Internet.
- Configuring logging to an external SIEM: You can have multiple log streams configured in SRX Series Firewall and point the SRX logging mechanisms to multiple SIEMs.
- Enable web management: Enable web management so that you can access SRX Series Firewall using the on-box management solution through J-Web.
- Discover the device and import baseline configuration to Juniper Security Director Cloud: Discover the device and import the baseline configuration to Juniper Security Director Cloud.
- Enable logging for Juniper Security Director Cloud: Enable logging so that the traffic is logged to Juniper Security Director Cloud from SRX Series Firewall.
- Enroll the device to Juniper ATP Cloud: Juniper ATP Cloud is the threat intelligence component of this solution and the source of SecIntel threat feeds. It also can provide advanced malware detection.
- Create security policies with application specific environment.
- Create IDP profiles that cover the security landscape of the data center environment.
- Assign the created IDP profile in a security policy.
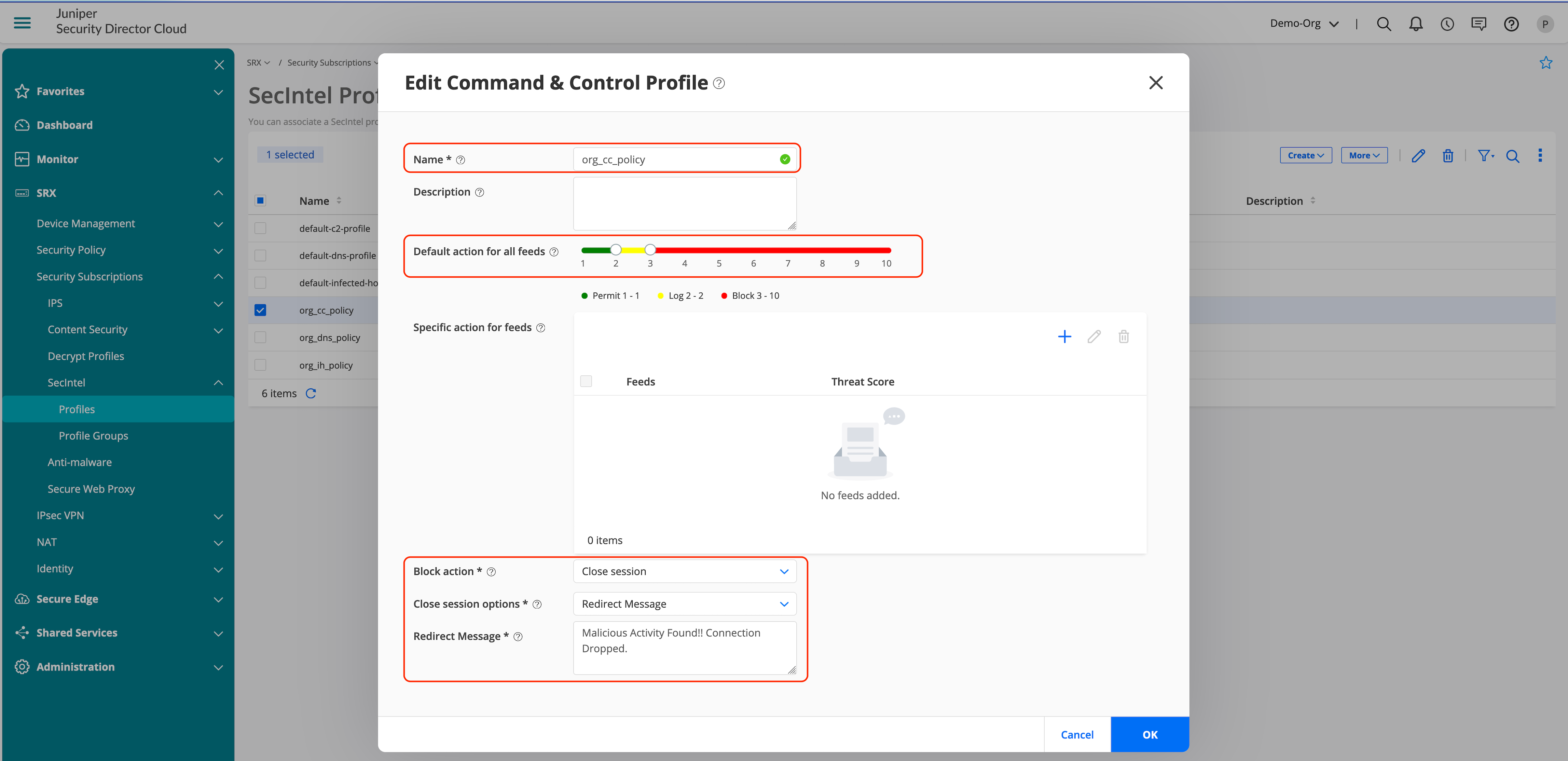
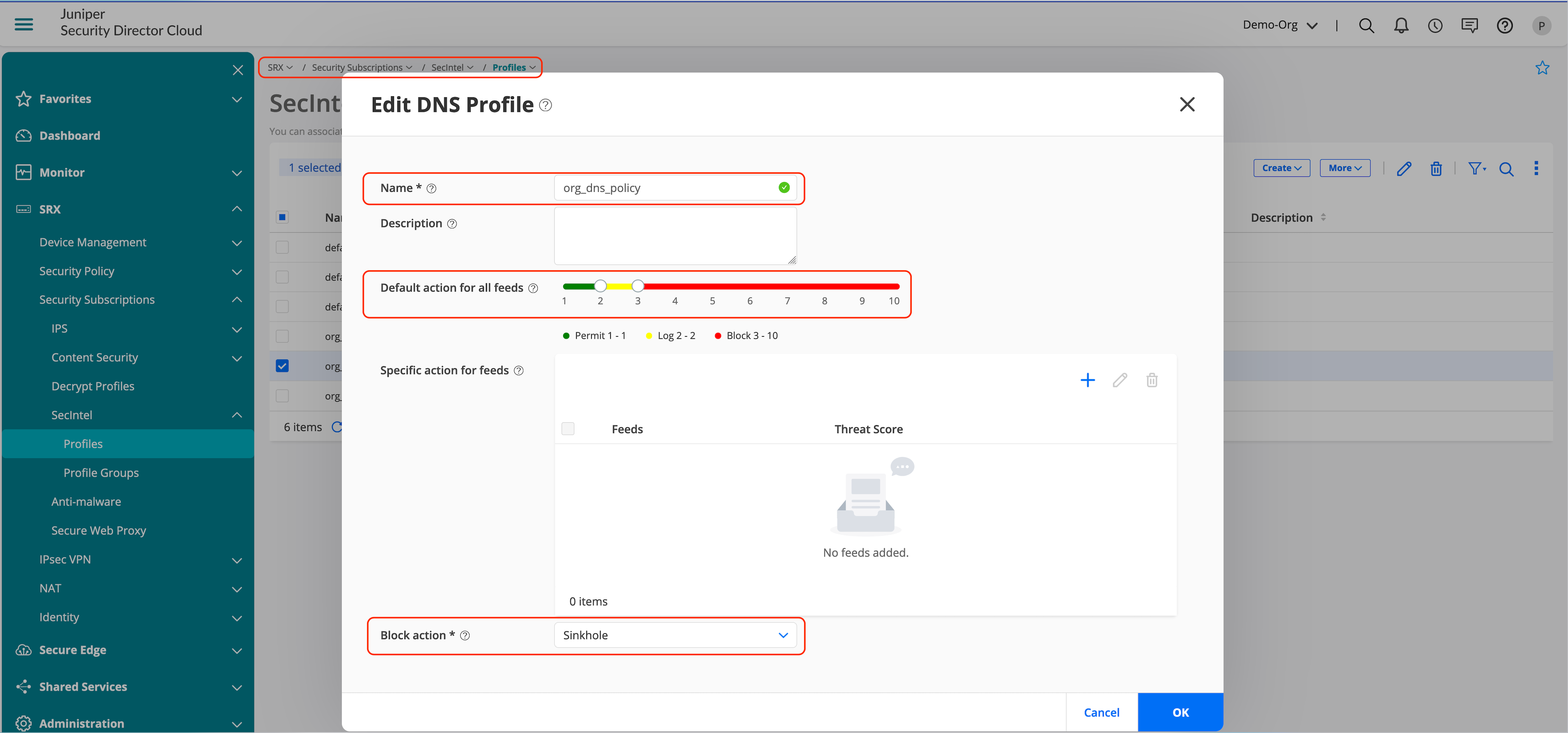
- Create SecIntel Profile: SecIntel Profile contains options for DNS, Command and Control (C&C), and Infected hosts.
- Assign SecIntel Profile to rule: Assigning SecIntel Profile to rule ensures all the traffic using the rule is verified against the SecIntel feeds.
- Create AAMW Profile: The AAMW profile allows you to select the type of traffic to be inspected for malware. Traffic includes HTTP, IMAP, SNB, and SMTP.
- Assign AAMW Profile to Rule: Assign the profile to rule so that all traffic using the rule is inspected for malware based on the profile.
- Create DNS security Meta Data Profile: DNS security allows you to identify DNS related threats such as DGA and DNS tunnelling.
- Assign the DNS Meta Data to Zone Context: All the traffic between the zone set is inspected for DNS security.
- Configure screen options to protect the untrust zone against DDoS attacks.
- Configure reverse SSL proxy to analyze and protect webserver traffic. The traffic is subjected to advances security services.
The configuration for each tested JVD feature is as follows:
Chassis Configuration (CLI)
# Step 1: cli # Configure chassis cluster configuration and Reboot set chassis cluster cluster-id 1 node 0 reboot set chassis cluster cluster-id 1 node 1 reboot # NOTE: Device would reboot and each device would assume a role either as primary or secondary. # Step 2: set interfaces fab0 fabric-options member-interfaces ge-0/0/3 set interfaces fab1 fabric-options member-interfaces ge-5/0/3 # Step 3: Set the interface count to configure redundant interfaces and create the redundant interfaces. cli configure set chassis cluster reth-count 5 set interfaces reth0 redundant-ether-options redundancy-group 1 set interfaces reth1 redundant-ether-options redundancy-group 1 set interfaces reth2 redundant-ether-options redundancy-group 1 set interfaces reth3 redundant-ether-options redundancy-group 1 set interfaces reth4 redundant-ether-options redundancy-group 1 # Node 0 configuration set interfaces ge-0/0/0 gigether-options redundant-parent reth0 set interfaces ge-0/0/1 gigether-options redundant-parent reth1 set interfaces ge-0/0/2 gigether-options redundant-parent reth2 set interfaces ge-0/0/3 gigether-options redundant-parent reth3 set interfaces ge-0/0/4 gigether-options redundant-parent reth4 # Node 1 configuration set interfaces ge-5/0/0 gigether-options redundant-parent reth0 set interfaces ge-5/0/1 gigether-options redundant-parent reth1 set interfaces ge-5/0/2 gigether-options redundant-parent reth2 set interfaces ge-5/0/3 gigether-options redundant-parent reth3 set interfaces ge-5/0/4 gigether-options redundant-parent reth4 # Step 4 - Set Hostname and Management IP: set groups node0 system host-name SRX-NODE0 set groups node0 interfaces fxp0 unit 0 family inet address 192.16.35.10/24 set groups node1 system host-name SRX-NODE1 set groups node1 interfaces fxp0 unit 0 family inet address 192.16.35.11/24 # Step 5: Enable interface monitoring. set chassis cluster redundancy-group 1 interface-monitor ge-0/0/0 weight 255 set chassis cluster redundancy-group 1 interface-monitor ge-0/0/1 weight 255 set chassis cluster redundancy-group 1 interface-monitor ge-0/0/2 weight 255 # Step 6: Set chassis options. set chassis cluster redundancy-group 1 node 0 priority 150 set chassis cluster redundancy-group 1 node 1 priority 100 set chassis cluster redundancy-group 1 preempt
Baseline Configuration (CLI)
UNTRUST: set security zones security-zone untrust screen root-screen set security zones security-zone untrust interfaces reth0.0 host-inbound-traffic system-services ssh set security zones security-zone untrust interfaces reth0.0 host-inbound-traffic system-services ping set security zones security-zone untrust interfaces reth0.0 host-inbound-traffic system-services all set security zones security-zone untrust interfaces reth5.2000 host-inbound-traffic system-services ssh set security zones security-zone untrust interfaces reth2.0 host-inbound-traffic system-services ping TRUST: set security zones security-zone trust interfaces reth1.0 host-inbound-traffic system-services all set security zones security-zone trust interfaces reth3.0 host-inbound-traffic system-services all set security zones security-zone trust interfaces reth4.1200 host-inbound-traffic system-services all SERVICES: set security zones security-zone services screen root-screen set security zones security-zone services interfaces xe-1/1/2.0 host-inbound-traffic system-services ping DEFAULT ROUTE: set routing-options static route 0.0.0.0/0 next-hop 80.80.80.1 set routing-options static route 90.0.0.0/16 next-hop 21.0.0.2 set routing-options static route 190.0.0.0/16 next-hop 30.30.30.2 NAT: Outgoing Internet Traffic set security nat source pool abc address 50.0.0.0/24 set security nat source rule-set nat_to_internet from zone services set security nat source rule-set nat_to_internet from zone trust set security nat source rule-set nat_to_internet to zone untrust set security nat source rule-set nat_to_internet rule 1 match source-address 0.0.0.0/0 set security nat source rule-set nat_to_internet rule 1 match destination-address 0.0.0.0/0 set security nat source rule-set nat_to_internet rule 1 match application any set security nat source rule-set nat_to_internet rule 1 then source-nat pool abc NAT: Incoming destination traffic for web server: set security nat destination pool web-svr-pool address 172.16.0.11/32 set security nat destination pool web-svr-pool address port 443 set security nat destination rule-set WS-NAT rule 1 match destination-address 10.0.0.100/32 set security nat destination rule-set WS-NAT rule 1 match destination-port 443 set security nat destination rule-set WS-NAT rule 1 then destination-nat pool web-svr-pool Global Addresses: set security address-book global address WebSvr-Local 7.7.7.2/32 set security address-book global address win-server 172.16.0.10/32 set security address-book global address web-server 172.16.0.11/32 set security address-book global address client1 192.168.10.10/32 Set security address-book global address web-server-ext 10.0.0.100/32 Services: set applications application-set Internet-services application junos-http set applications application-set Internet-services application junos-https set applications application-set Internet-services application junos-smtp set applications application-set Internet-services application junos-smtps set applications application-set Internet-services application junos-imap set applications application-set Internet-services application junos-imaps set applications application-set Internet-services application junos-dns-udp set applications application-set Internet-services application junos-dns-tcp set applications application-set Internet-services application junos-icmp-all Security Policies: Security Policies between trust to untrust: set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule match source-address any set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule match destination-address any set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule match application any set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule match source-identity "domain08.net\ks_windows1_user_1" set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule match source-identity "domain08.net\ks_user1_user_1" set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule match source-identity unknown-user set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule match source-identity unauthenticated-user deactivate security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule match source-identity set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule match dynamic-application any set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule then permit application-services idp-policy Recommended_WithAudit set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule then permit application-services utm-policy junos-default-utm-policy set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule then permit application-services security-intelligence-policy default-secintel set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule then permit application-services advanced-anti-malware-policy default-antimalware set security policies from-zone trust to-zone untrust policy t2u-allow_internet_rule then log session-close set security policies from-zone trust to-zone untrust policy Block_Offending_Apps match source-address any set security policies from-zone trust to-zone untrust policy Block_Offending_Apps match destination-address any set security policies from-zone trust to-zone untrust policy Block_Offending_Apps match application junos-defaults set security policies from-zone trust to-zone untrust policy Block_Offending_Apps match dynamic-application Block_HighBW_Apps set security policies from-zone trust to-zone untrust policy Block_Offending_Apps then deny set security policies from-zone trust to-zone untrust policy Block_Offending_Apps then log session-close set security policies from-zone trust to-zone untrust application-services security-metadata-streaming-policy apt_services Security Policies between services to untrust: set security policies from-zone services to-zone untrust policy s2u-allow_internet_rule match source-address any set security policies from-zone services to-zone untrust policy s2u-allow_internet_rule match destination-address any set security policies from-zone services to-zone untrust policy s2u-allow_internet_rule match application any set security policies from-zone services to-zone untrust policy s2u-allow_internet_rule match dynamic-application any set security policies from-zone services to-zone untrust policy s2u-allow_internet_rule then permit application-services security-intelligence-policy default-secintel set security policies from-zone services to-zone untrust policy s2u-allow_internet_rule then permit application-services advanced-anti-malware-policy default-antimalware set security policies from-zone services to-zone untrust policy s2u-allow_internet_rule then log session-close Security Policies between trust and services: set security policies from-zone trust to-zone services policy t2s-allow_web_svcs_rule match source-address any set security policies from-zone trust to-zone services policy t2s-allow_web_svcs_rule match destination-address any set security policies from-zone trust to-zone services policy t2s-allow_web_svcs_rule match application junos-http set security policies from-zone trust to-zone services policy t2s-allow_web_svcs_rule match application junos-https set security policies from-zone trust to-zone services policy t2s-allow_web_svcs_rule match dynamic-application junos:HTTP set security policies from-zone trust to-zone services policy t2s-allow_web_svcs_rule match dynamic-application junos:SSL set security policies from-zone trust to-zone services policy t2s-allow_web_svcs_rule then permit application-services idp-policy CS-To-Web-Protection-Rules set security policies from-zone trust to-zone services policy t2s-allow_web_svcs_rule then log session-close Security Policies between untrust to services: set security policies from-zone untrust to-zone services policy u2s-protect_web_svcs match source-address any set security policies from-zone untrust to-zone services policy u2s-protect_web_svcs match destination-address WebSvr-Local set security policies from-zone untrust to-zone services policy u2s-protect_web_svcs match application junos-defaults set security policies from-zone untrust to-zone services policy u2s-protect_web_svcs match dynamic-application junos:HTTP set security policies from-zone untrust to-zone services policy u2s-protect_web_svcs match dynamic-application junos:SSL set security policies from-zone untrust to-zone services policy u2s-protect_web_svcs then permit application-services idp-policy CS-To-Web-Protection-Rules set security policies from-zone untrust to-zone services policy u2s-protect_web_svcs then log session-init set security policies from-zone untrust to-zone services policy u2s-protect_web_svcs then log session-close NETCONF SERVICE: set system services ssh sftp-server set system services rlogin set system services netconf ssh set system services netconf rfc-compliant set system services web-management https system-generated-certificate set system services web-management limits debug-level 9 set system services web-management session idle-timeout 1440 DNS SERVER: set system name-server 8.8.8.8
System and Security Logging Configuration (CLI)
set security log utc-timestamp set security log mode stream set security log format sd-syslog set security log report set security log source-interface reth0.0 set security log transport set security log stream sd-cloud-logs category all set security log stream sd-cloud-logs host srx.sdcloud.juniperclouds.net set security log stream sd-cloud-logs host port 6514 set security log stream sd-cloud-logs transport division line-based set security log stream sd-cloud-logs transport protocol tls set security log stream sd-cloud-logs transport tls-profile syslog-profile
Management Configuration (CLI)
HTTP: set system services web-management http interface reth1.0 HTTPS: set system services web-management https system-generated-certificate set system services web-management https interface reth1.0 set system services web-management https interface fxp0.0 HTTP: set system services rest http HTTPS: set system services rest https server-certificate system-generated-certificate set system services rest enable-explorer
GUI driven feature configuration through Juniper Security Director Cloud:
- Discover device in Juniper Security Director Cloud and import baselined configuration.
- Onboard device in Juniper Security Director Cloud.
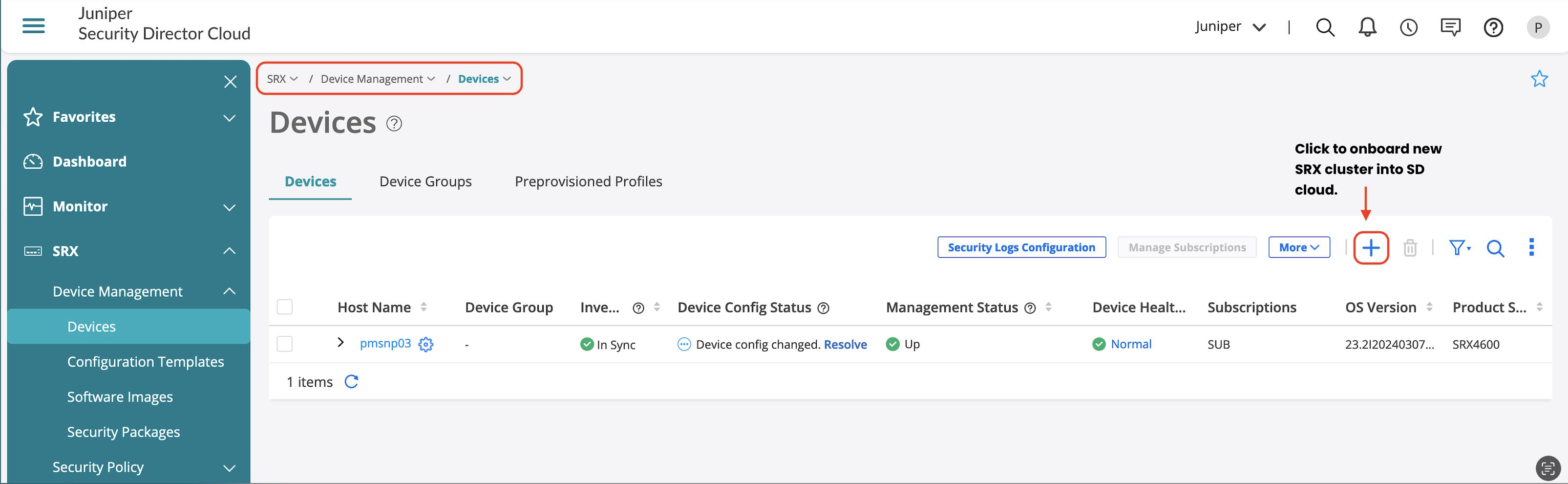
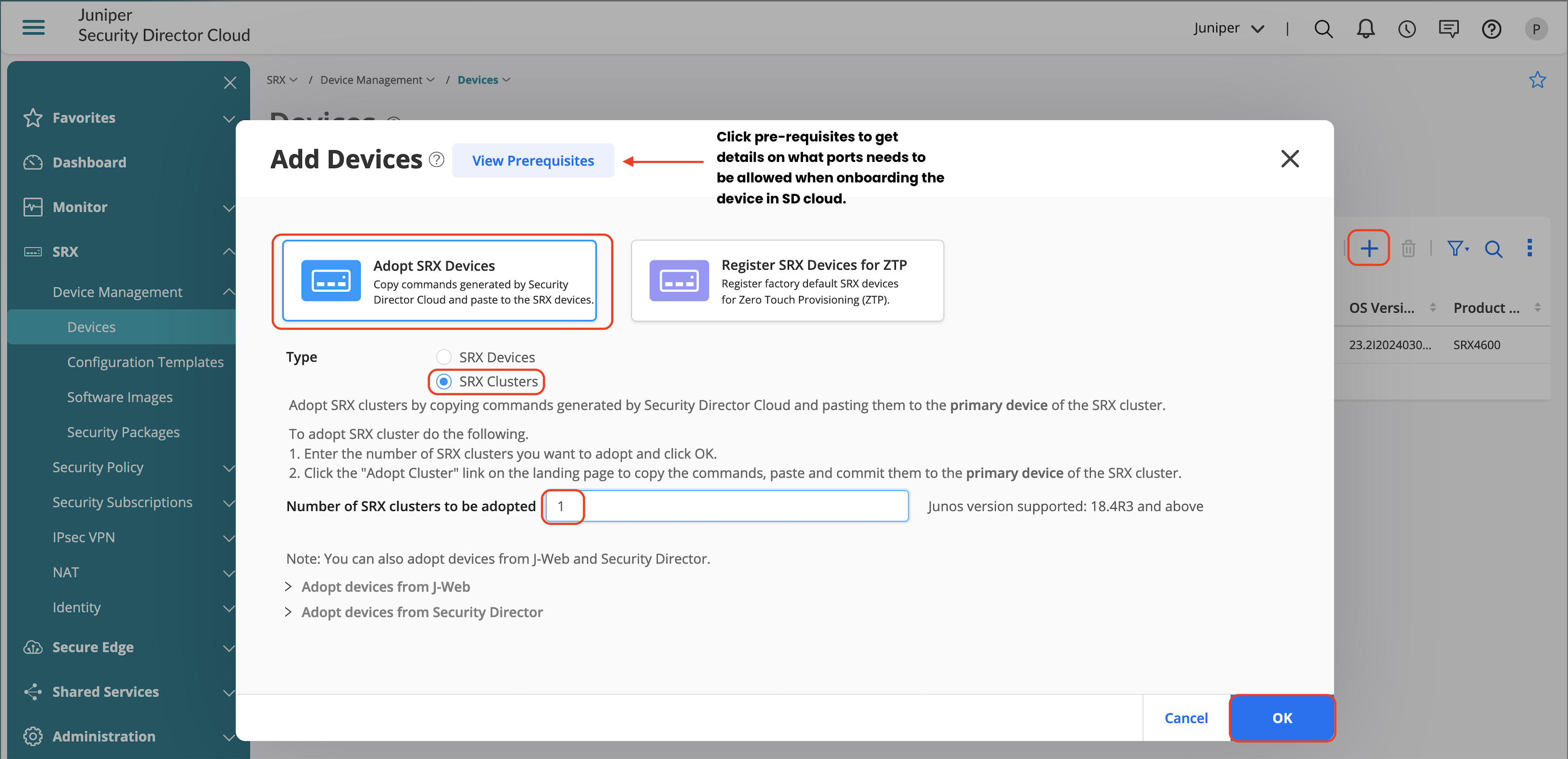
To onboard the SRX Series Firewall, follow the procedure below:
- Go to SRX > Device Management > Device and then click +.
- Select Adopt SRX Devices.
- Select SRX Clusters.
- Enter 1 in the Number of SRX clusters to be adopted field.
- Click OK and then click Close.
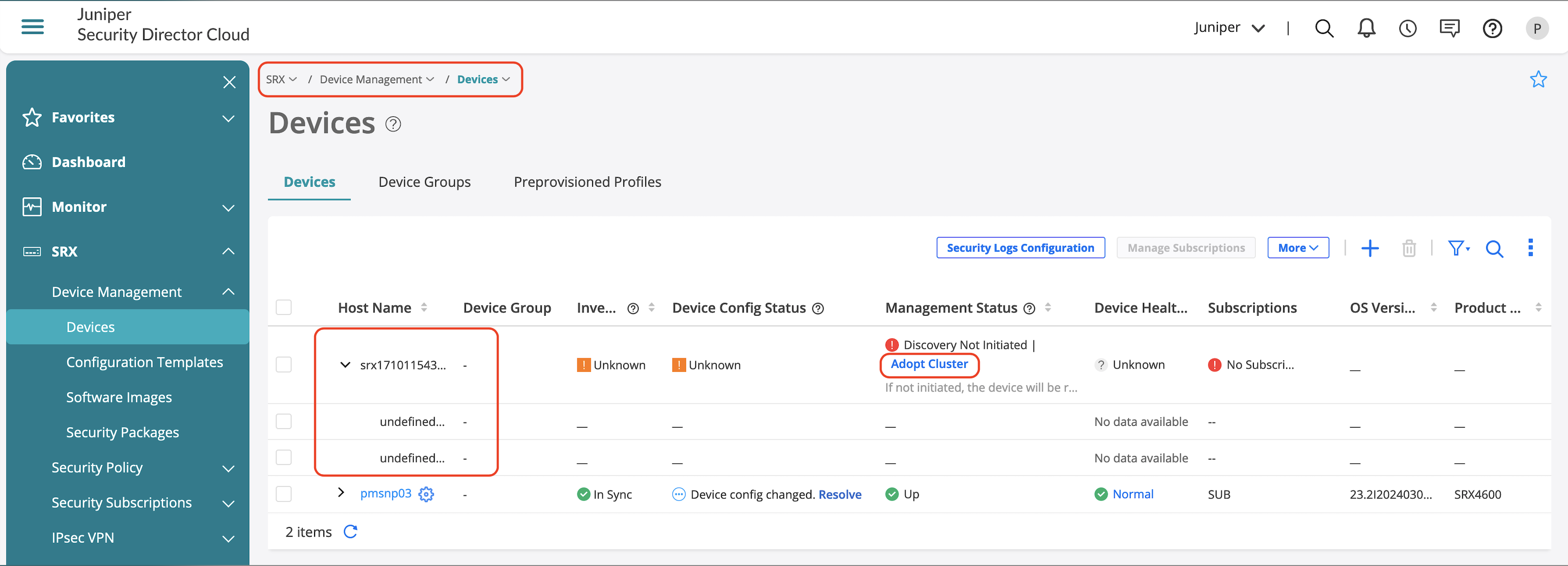
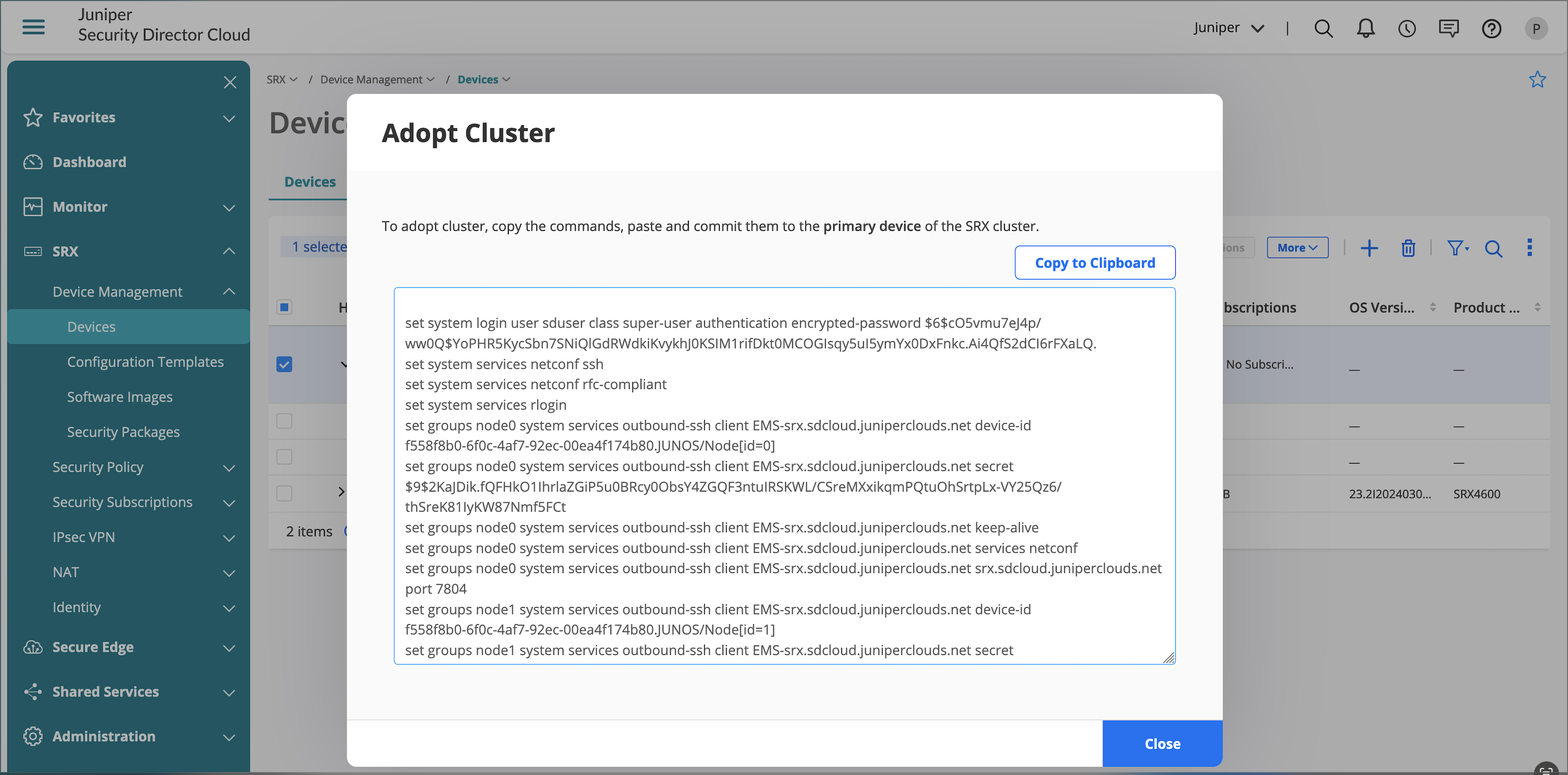
The action above creates a temporary device and to complete the on-boarding process, click Adopt Cluster as seen in Figure 4 . Copy paste the CLI commands on to the node0 of the SRX Cluster.
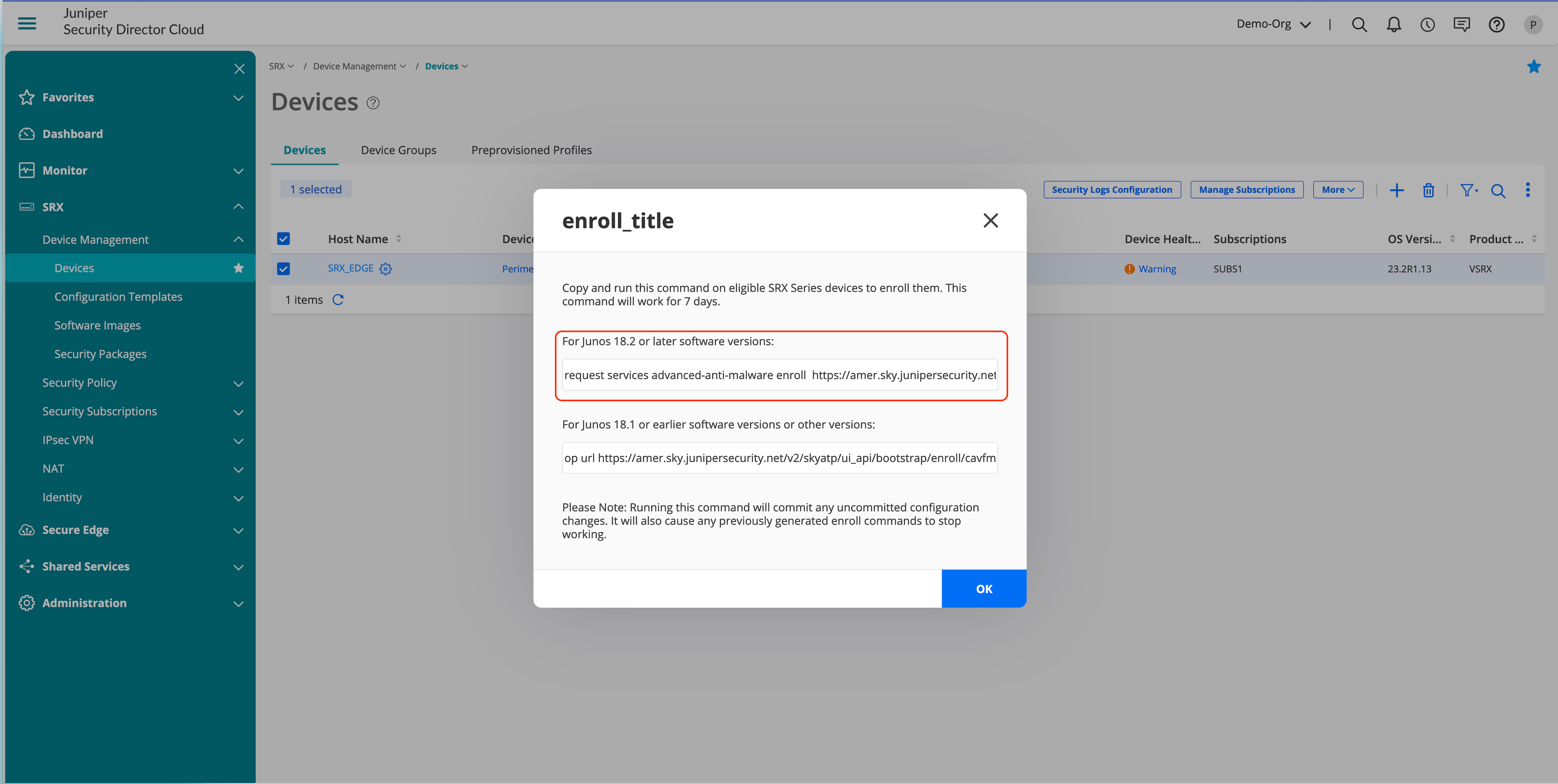
Enroll Device to Juniper ATP Cloud After Device Discovery
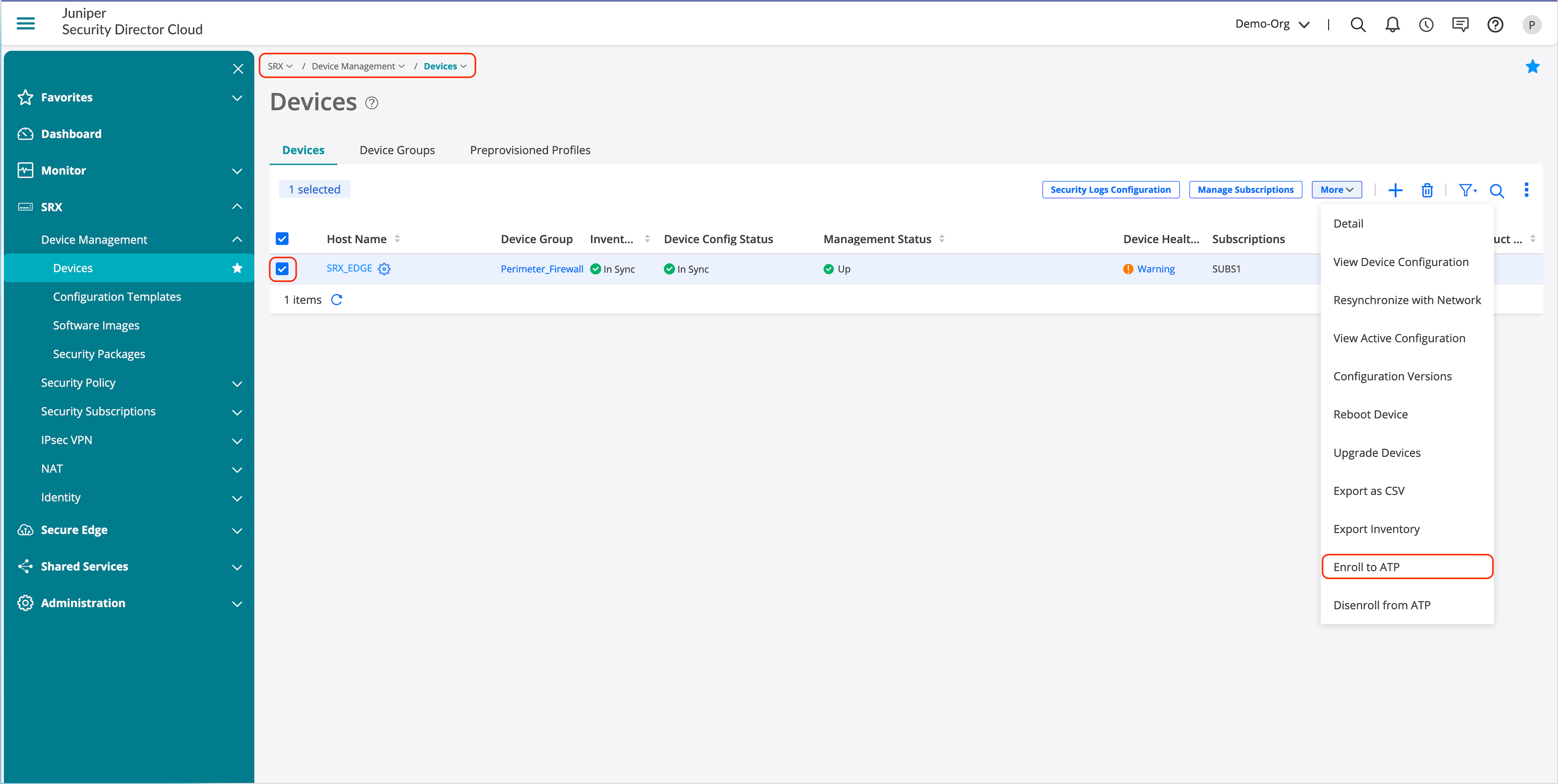
- Go to SRX > Device Management > Device.
- Select Devices.
- Click More and then select Enroll to ATP.
- Log on to your SRX Series Firewall and paste the command into the Junos OS CLI.
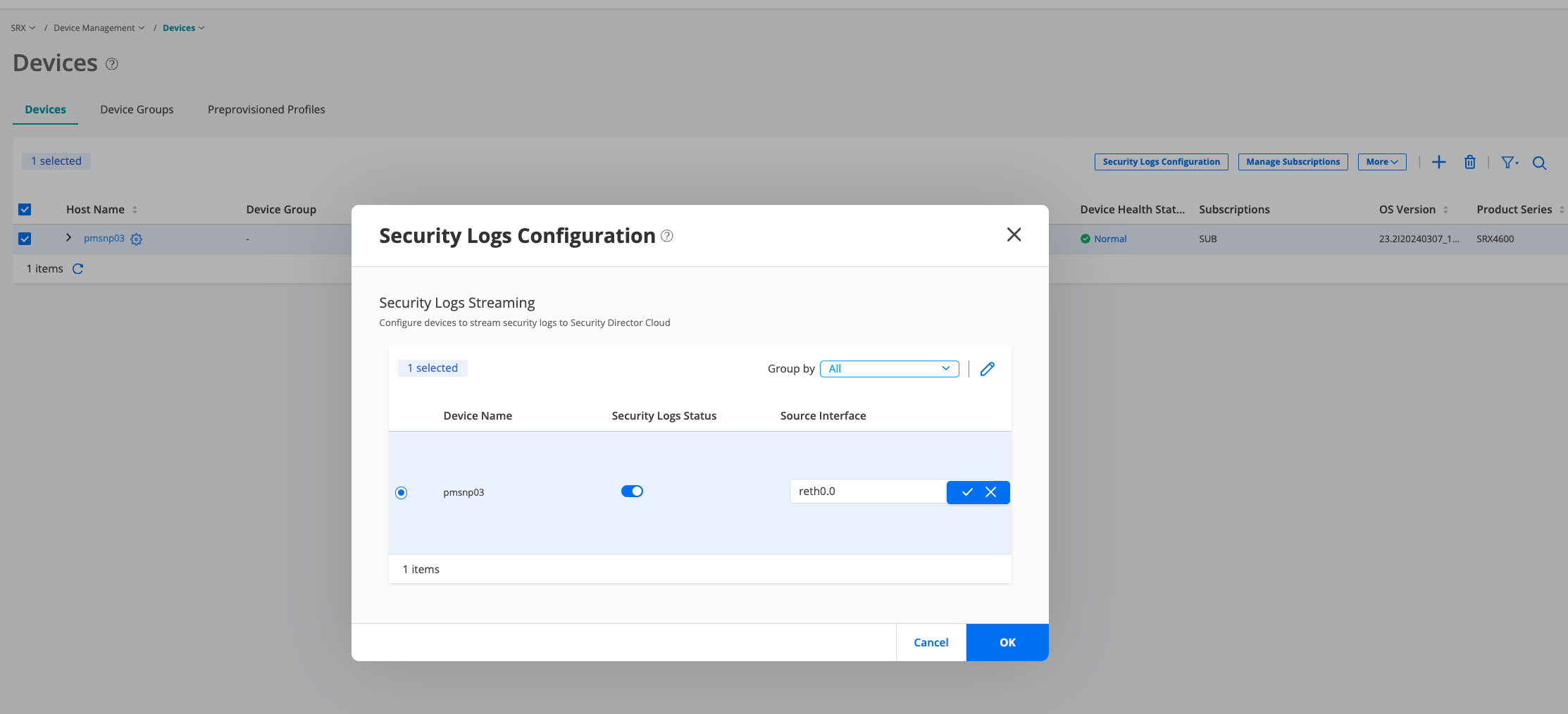
Enable Logging on SRX Series Firewall to Log the Traffic to Juniper Security Director Cloud
Application Security
Configure firewall policy to implement application security in a data center environment. We’ll create a firewall policy to block any high bandwidth social media / shopping websites and apps (Facebook, Amazon) and video sharing websites such as YouTube, Vimeo, and so on.
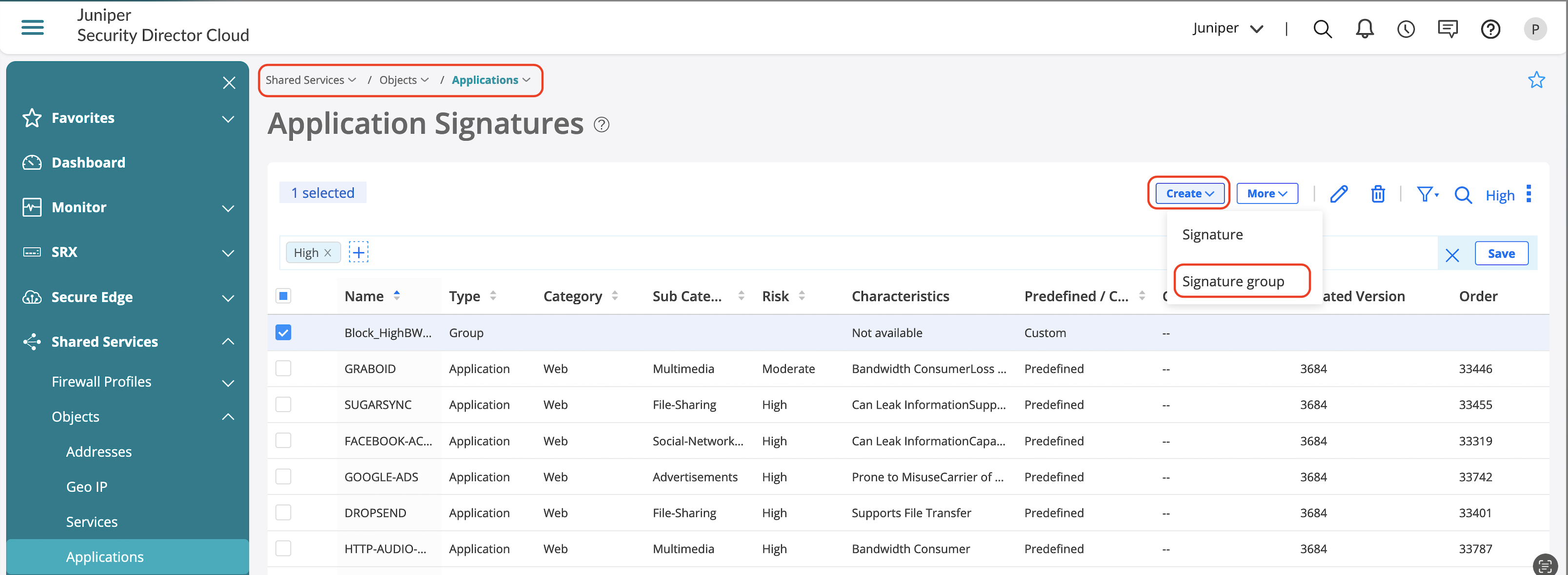
Create an Application Group that you’ll use in the firewall policy:
- Go to Shared Services > Applications.
- Click Create drop-down and then select Signature group.
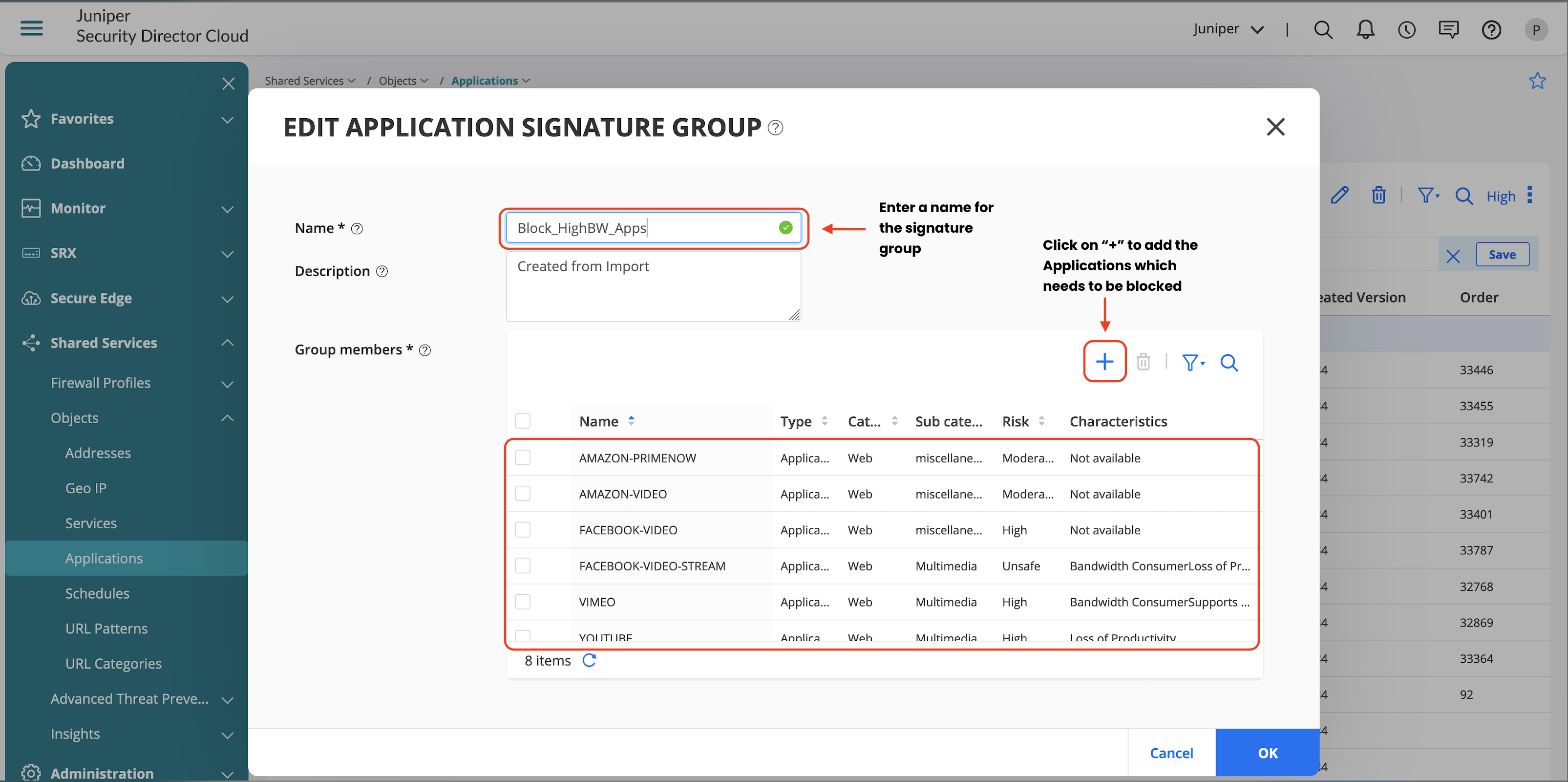
- Enter a name for the Application Group.
- Click + to add all the applications that needs to be blocked.
- Click OK to save the Application Group.
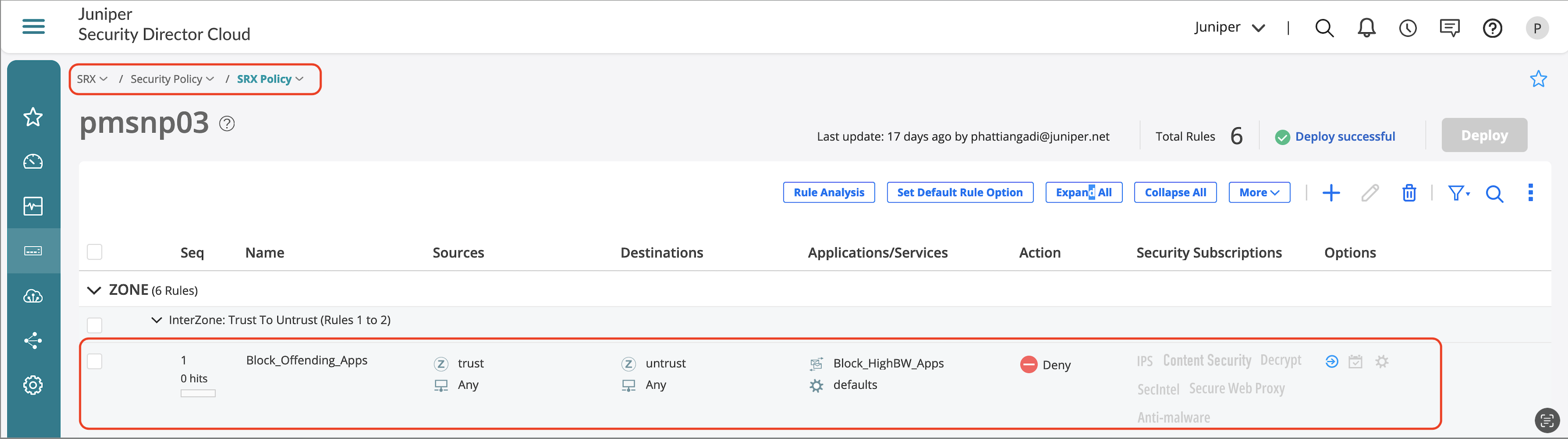
Include the Application Group in a Security Policy for enforcement:
- Go to SRX > Security Policy > SRX Policy.
- Click + to add new firewall rule.
- Enter Source Zone and Source Address.
- Enter Destination Zone and Destination Address.
- Select Services and Application Group that we created with apps that need to be blocked.
- Select Action.
- Enable Logging if needed from Options.
Intrusion Detection and Prevention (IDP)
When implementing IDP, you can consider the following settings when designing the IDP policy:
- Environment (Services running within the data center)
- Applications (Applications that are currently being served through the firewall)
- Exempt any services or protocols that are not be scanned (for example, SSH)
Based on the services implemented for this JVD, we choose to clone the client-to-server based protection and add a few rules that cater to the server-to-client based traffic.
The policy created considers the following settings:
- Services running in the data center (HTTP, HTTPS, MAIL, ICMP, DB, DNS, and so on)
- Signatures to detect malicious activity
- Signatures to detect network / services scanning
- Signatures to detect any DOS and DDOS based attacks
Workflow to create IDP policies and enforce the policies.
To clone predefined policy:
- Go to SRX > Security Subscription > IPS > IPS Profiles.
- Select the predefined policy to clone.
- Click More and then select Clone.
- Enter a new policy name.
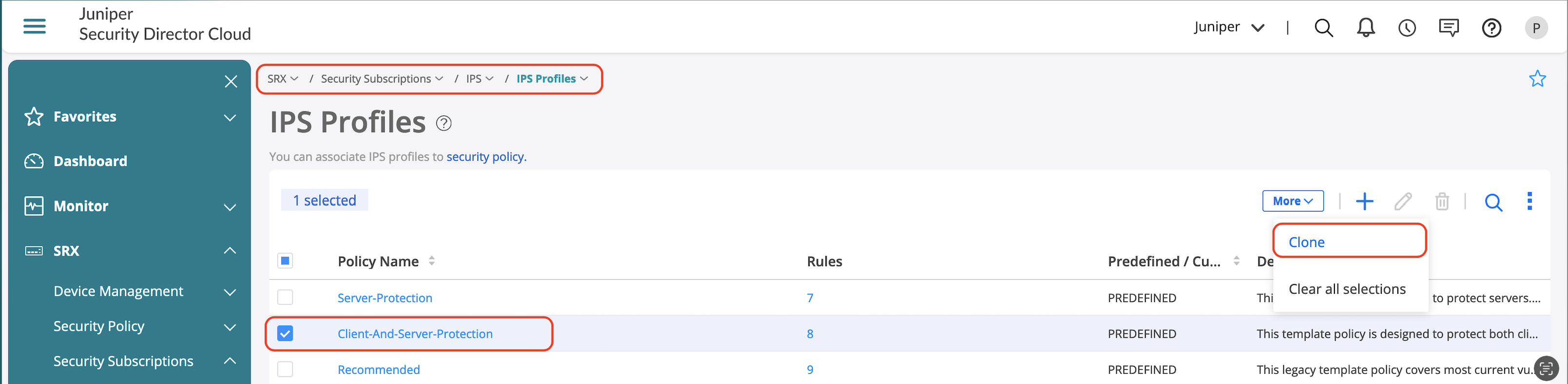
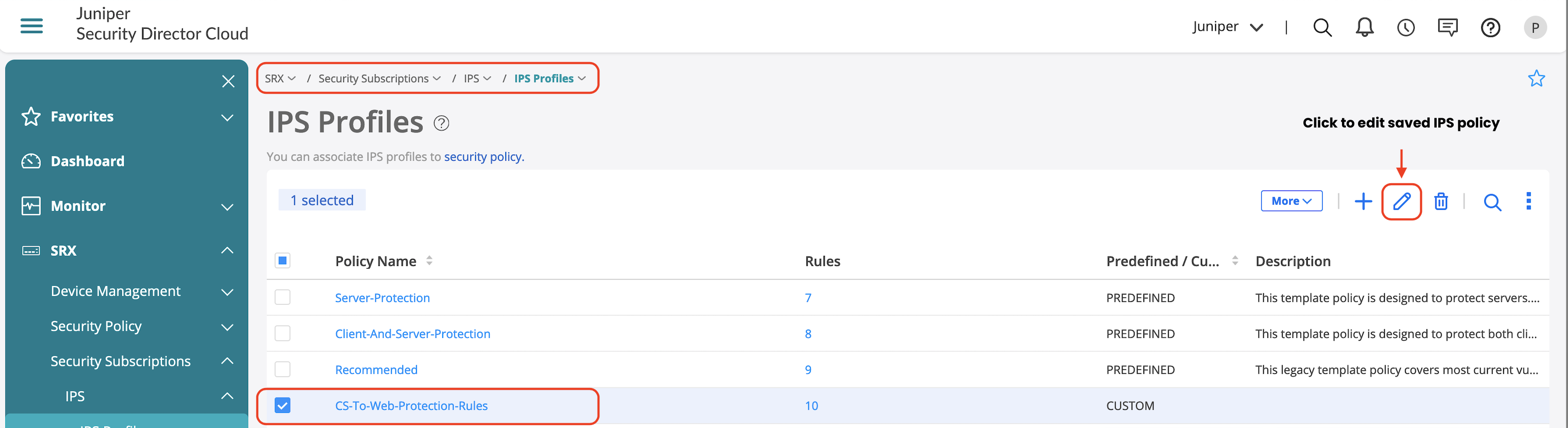
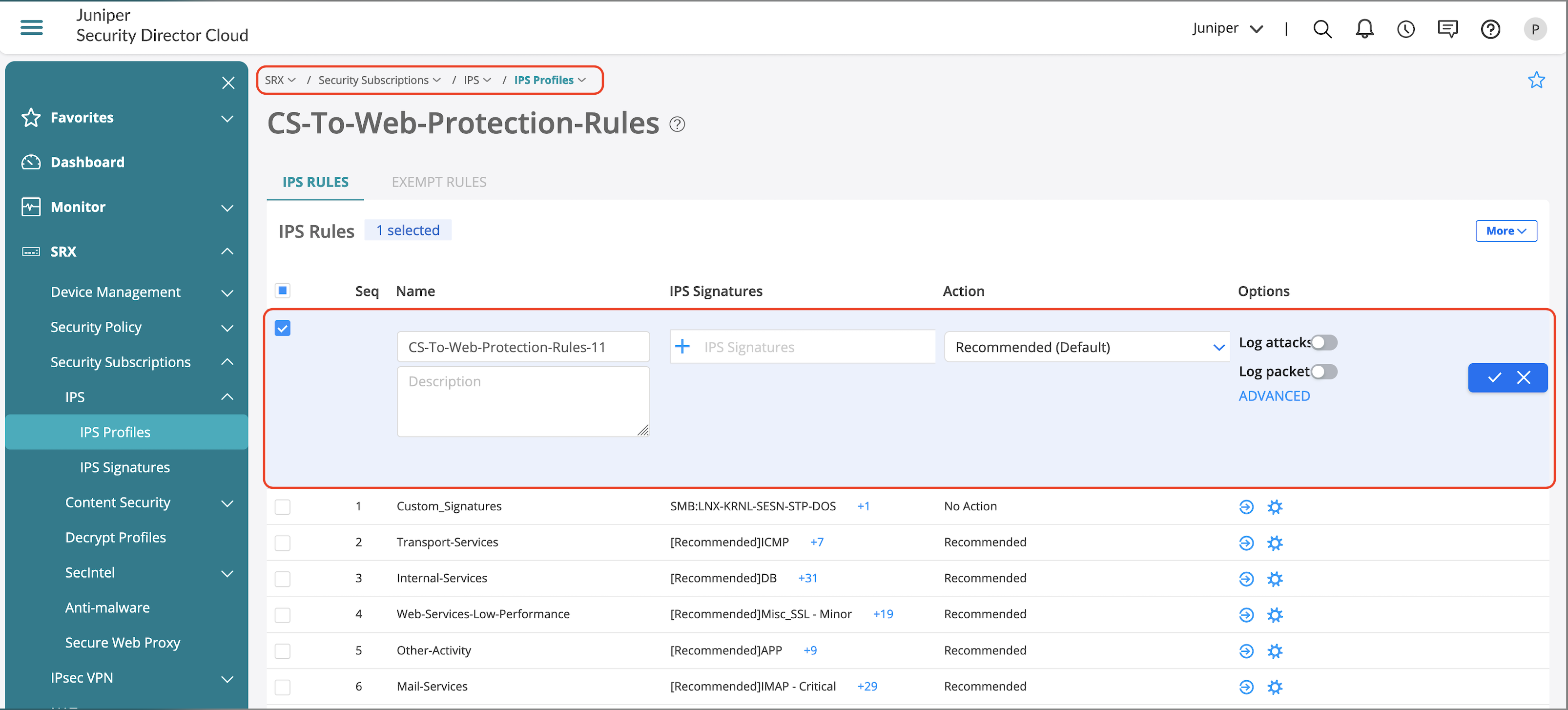
In this JVD, we’ve named the policy CS-To-Web-Protection-Rules and added a few rules which caters to server-to-client protection.
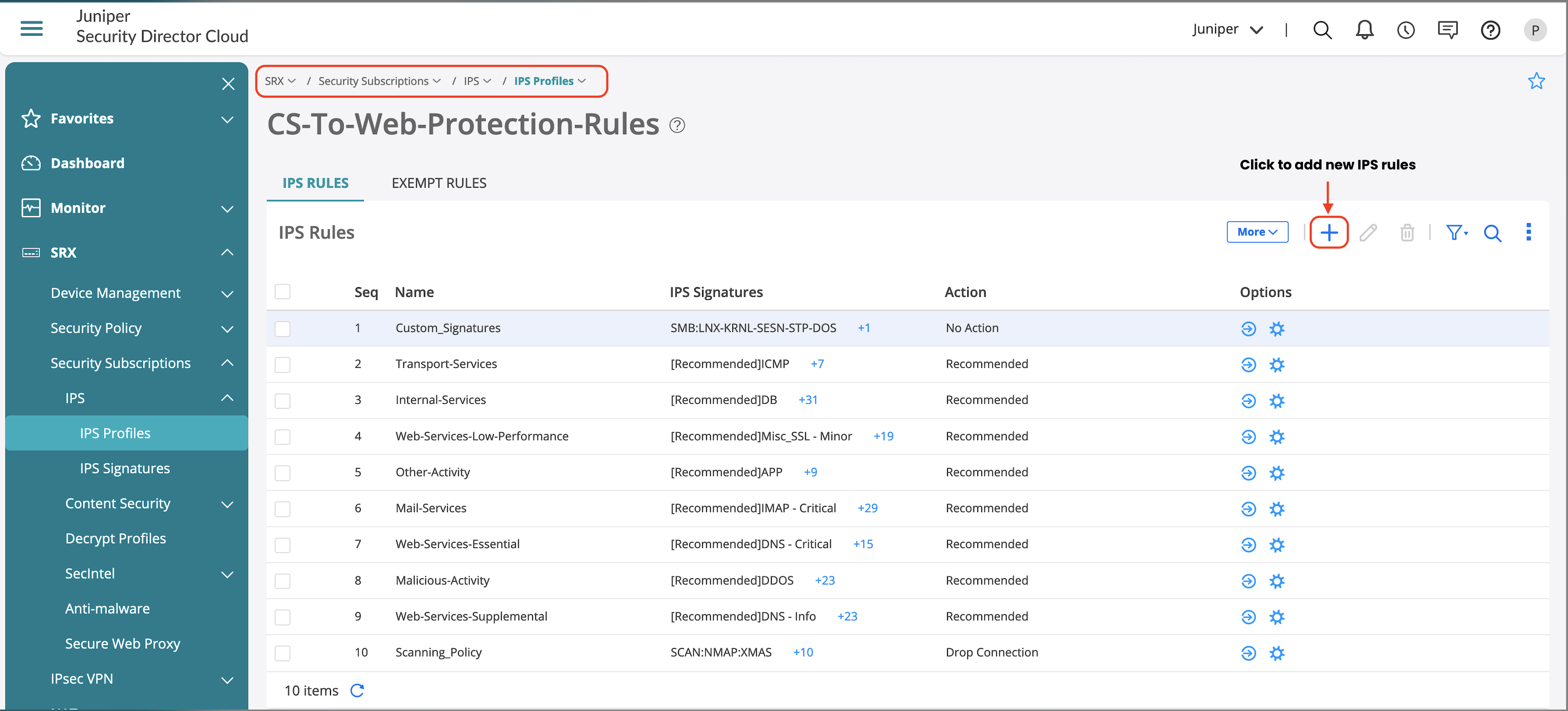
Once new IPS rule is added, update the following:
- Name of the IPS rule.
- Add new IDP signatures.
- Select action if a threat is detected.
- Optional. Log detected attacks.
- IPS rules also have advanced options to enable IP actions on detected attacks.
Each signature that is added comes with a recommended action to take if detected. You can set the action as Recommended. For more information on the signatures and the recommended action, see: https://threatlabs.juniper.net/home/search/#/list/ips?page_number=1&page_size=20
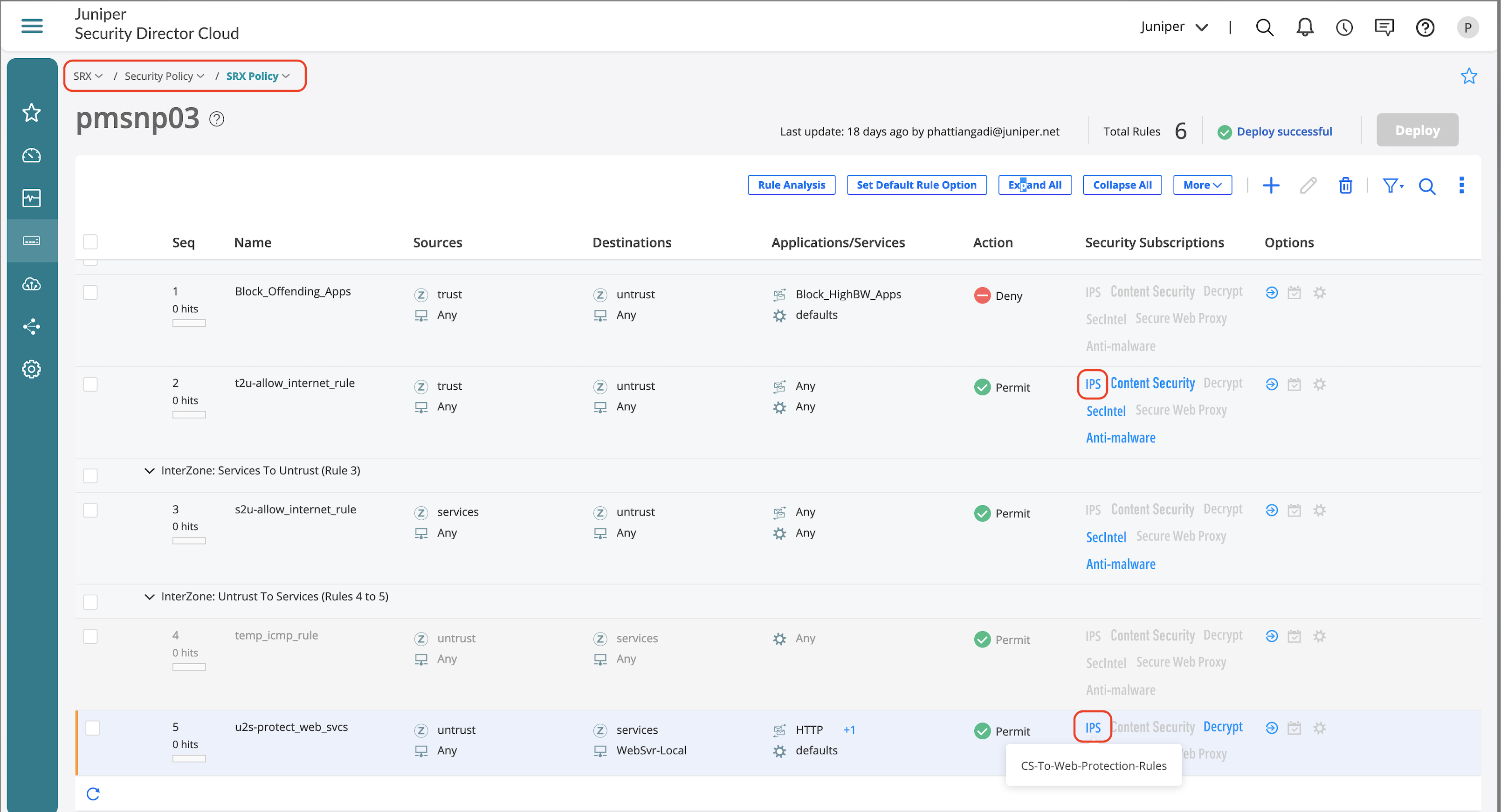
Once IPS profile and rules are created, enforce the IPS profile on a security policy:
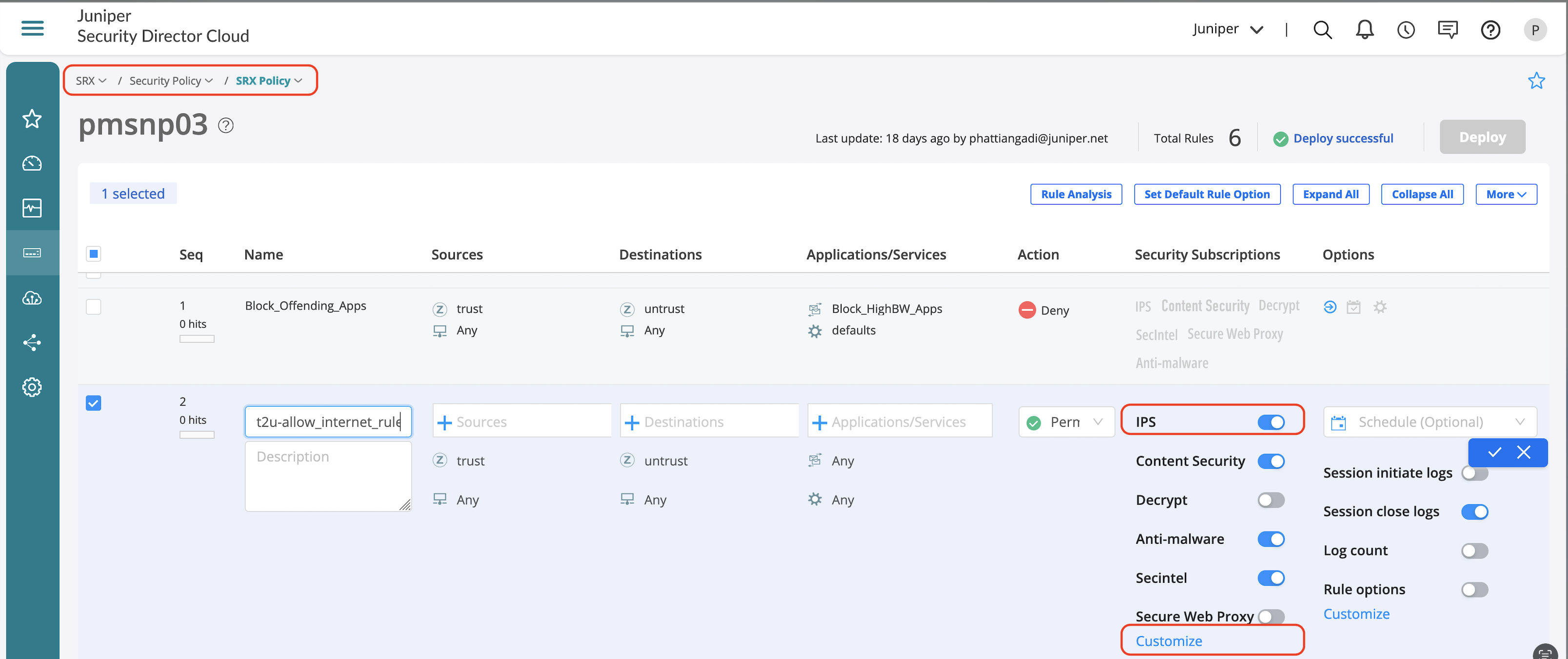
- Click on the firewall rule where IPS needs to be enabled.
- Click Security Subscriptions.
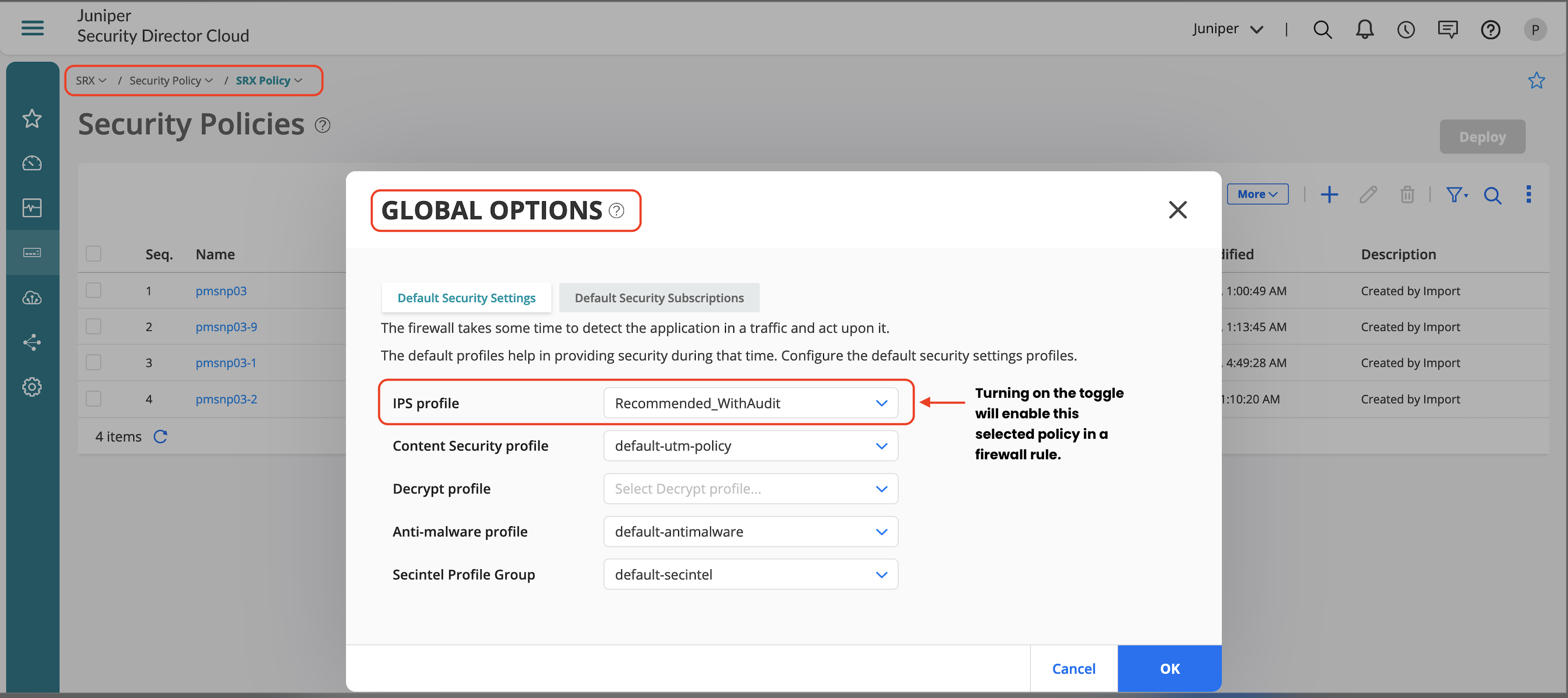
- Either use the global options and turn on just the IPS toggle or click Customize to select a new policy.
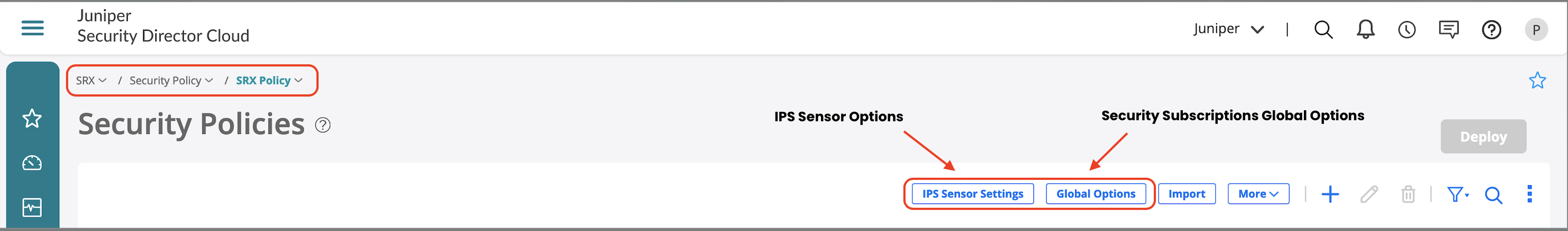
You can set the Global Options on the main SRX Policy page.
SecIntel Configuration
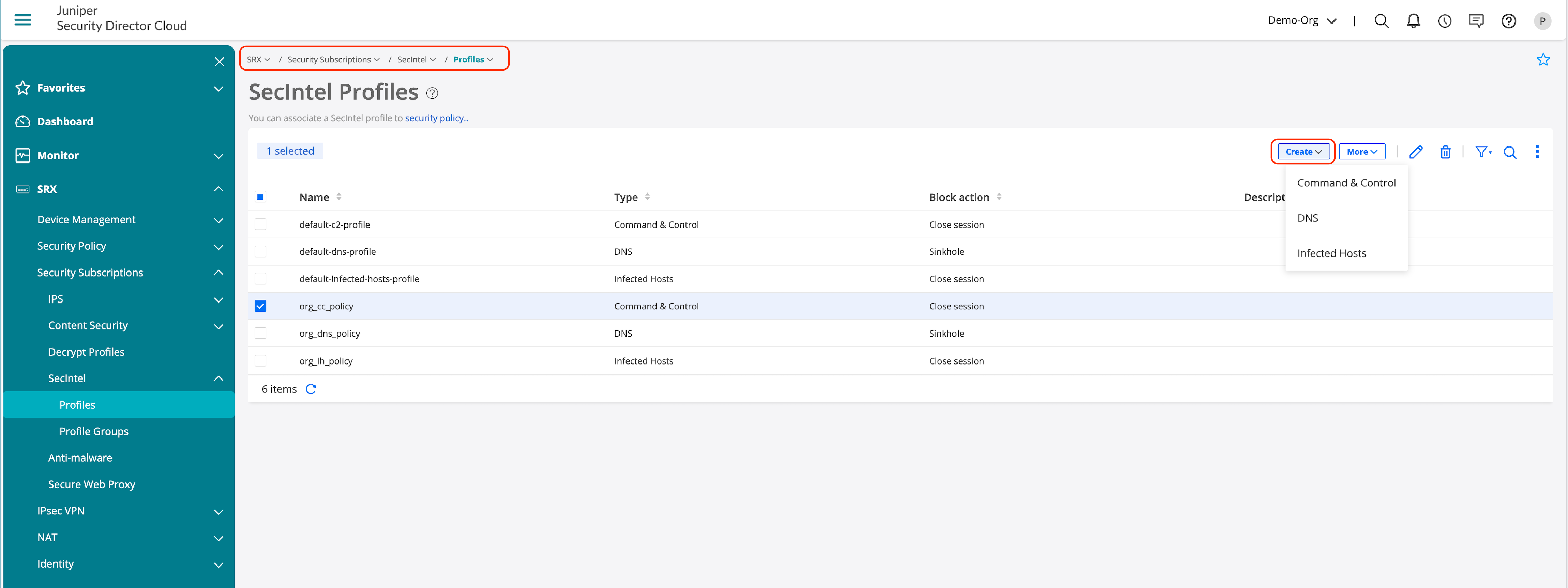
- Go to SRX > Security Subscriptions > SecIntel > Profiles.
- Click Create.
- Configure the profiles for required services.
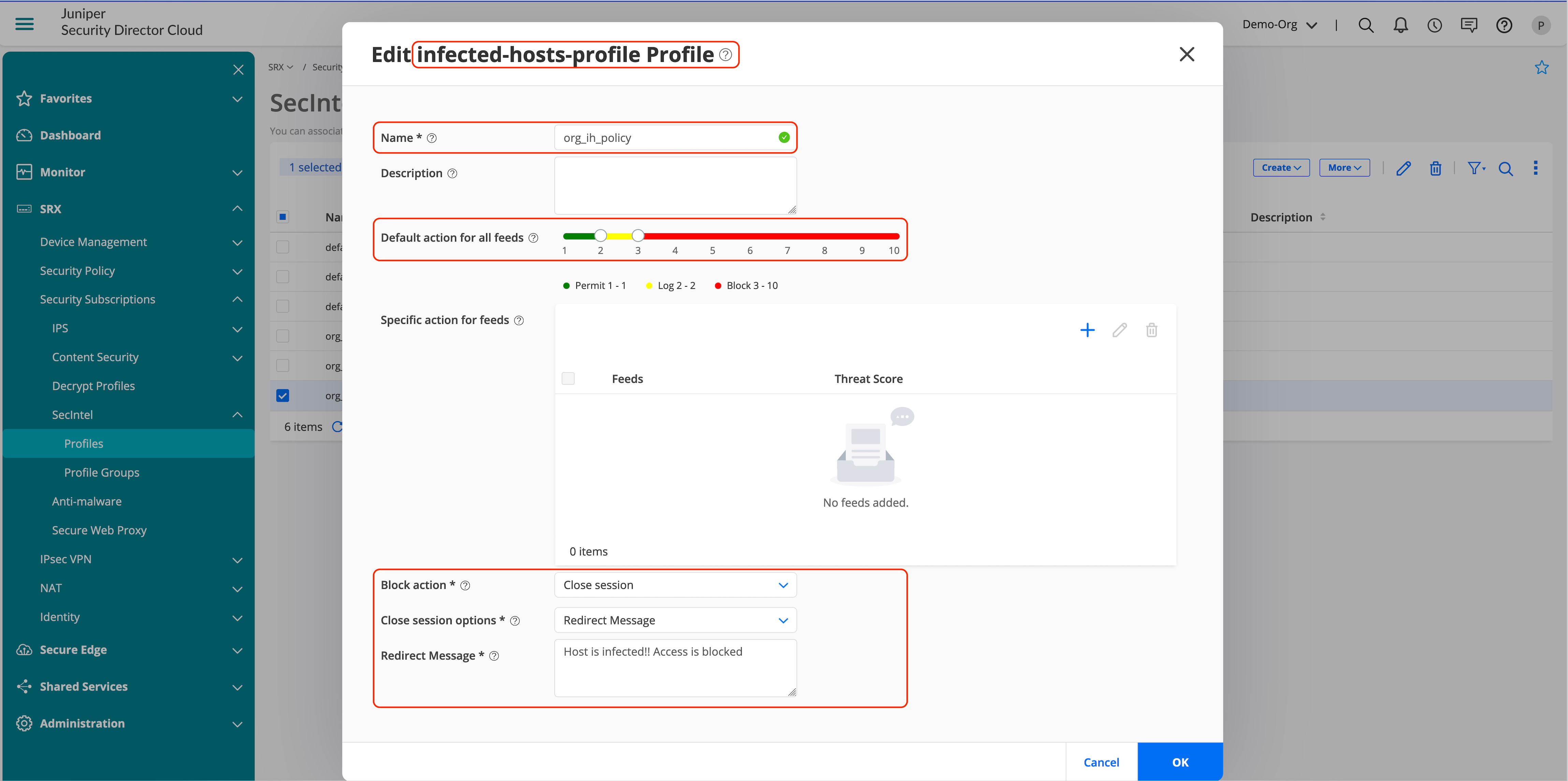
To create profile groups:
- Go to SRX > Security Subscriptions > SecIntel > Profile Groups.
- Click + to create a new profile group.
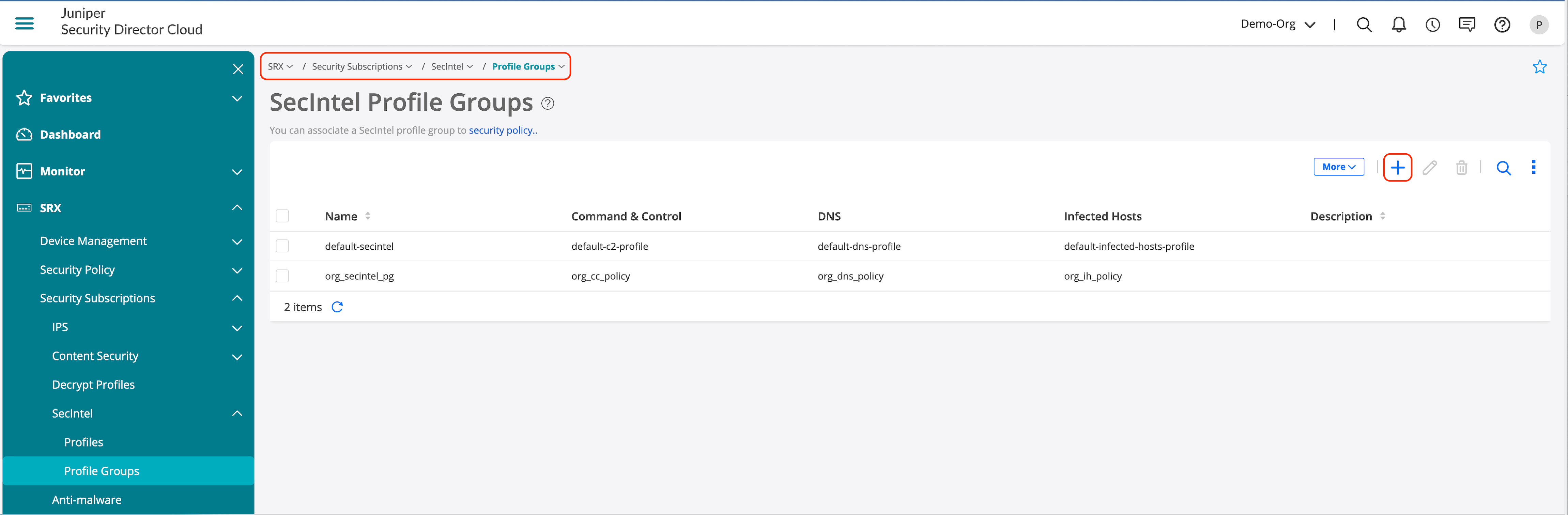
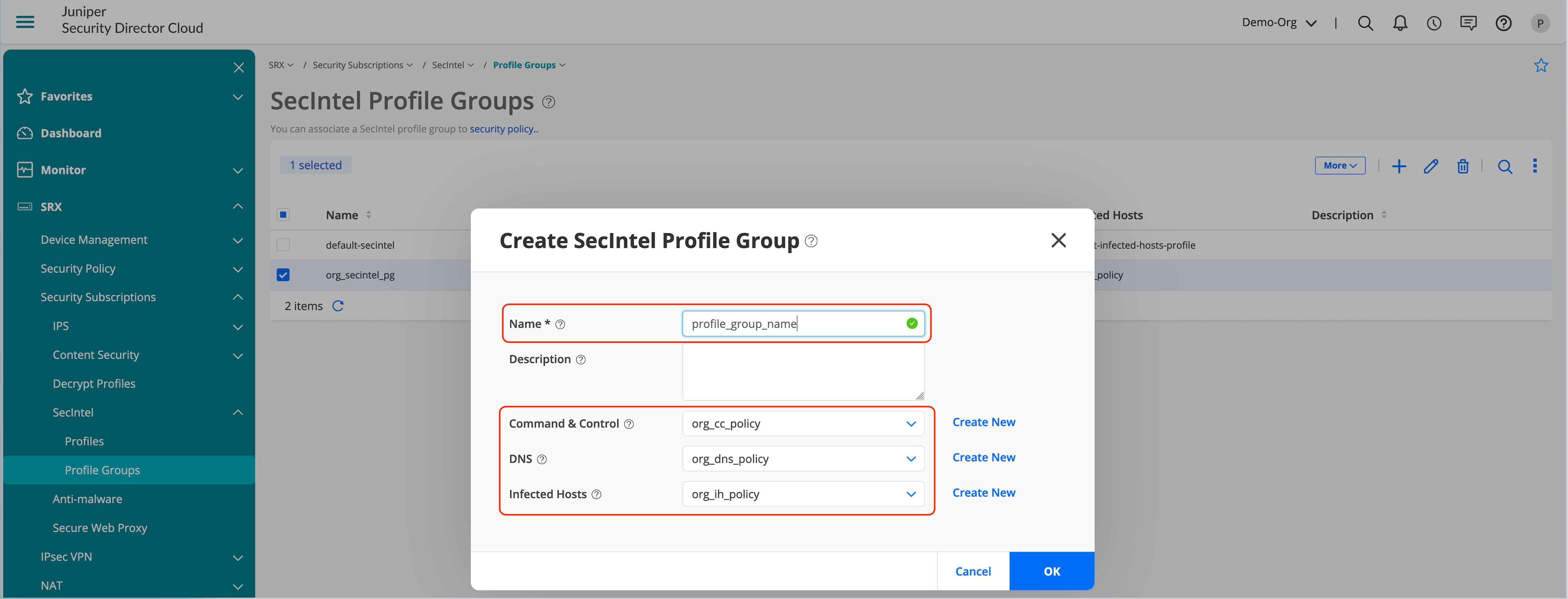
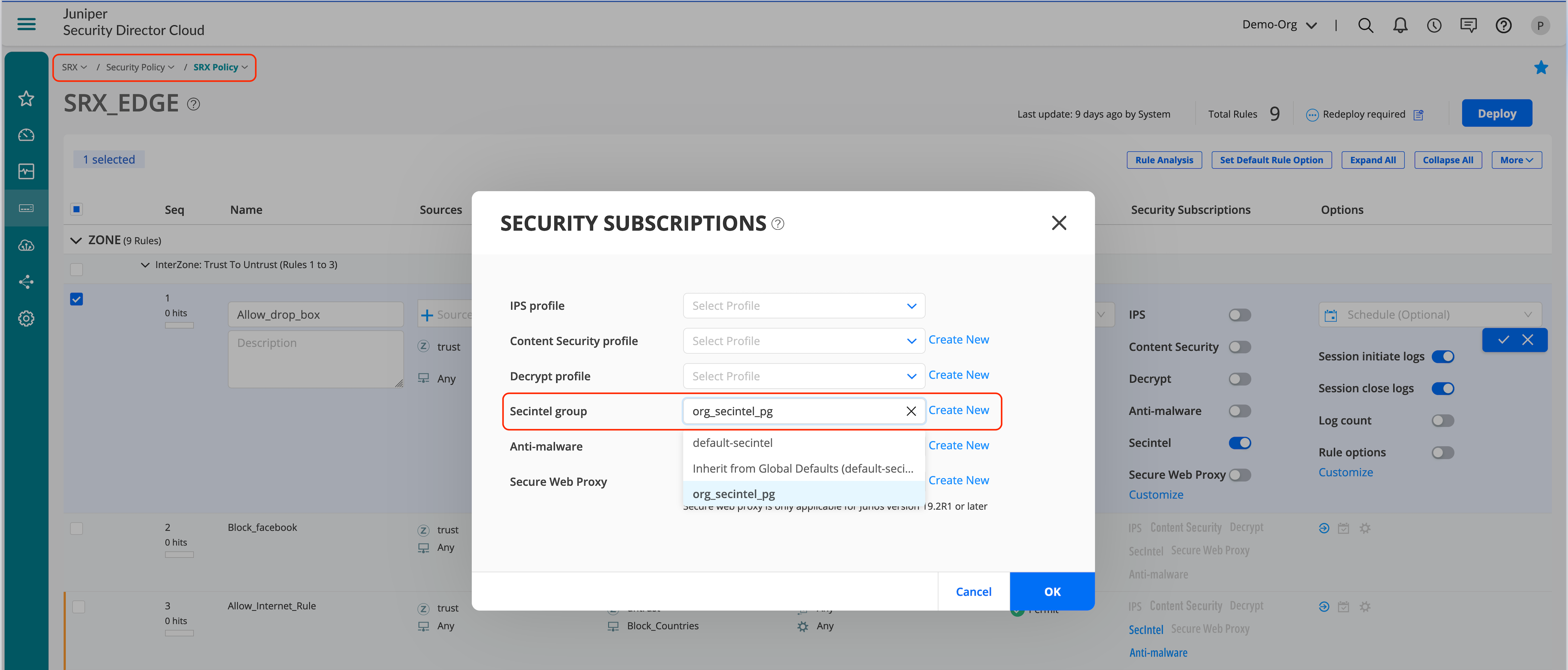
As a final step, let’s enable the SecIntel profile group in a security policy that enforces the detection and remediation for SecIntel profiles based on reputation.
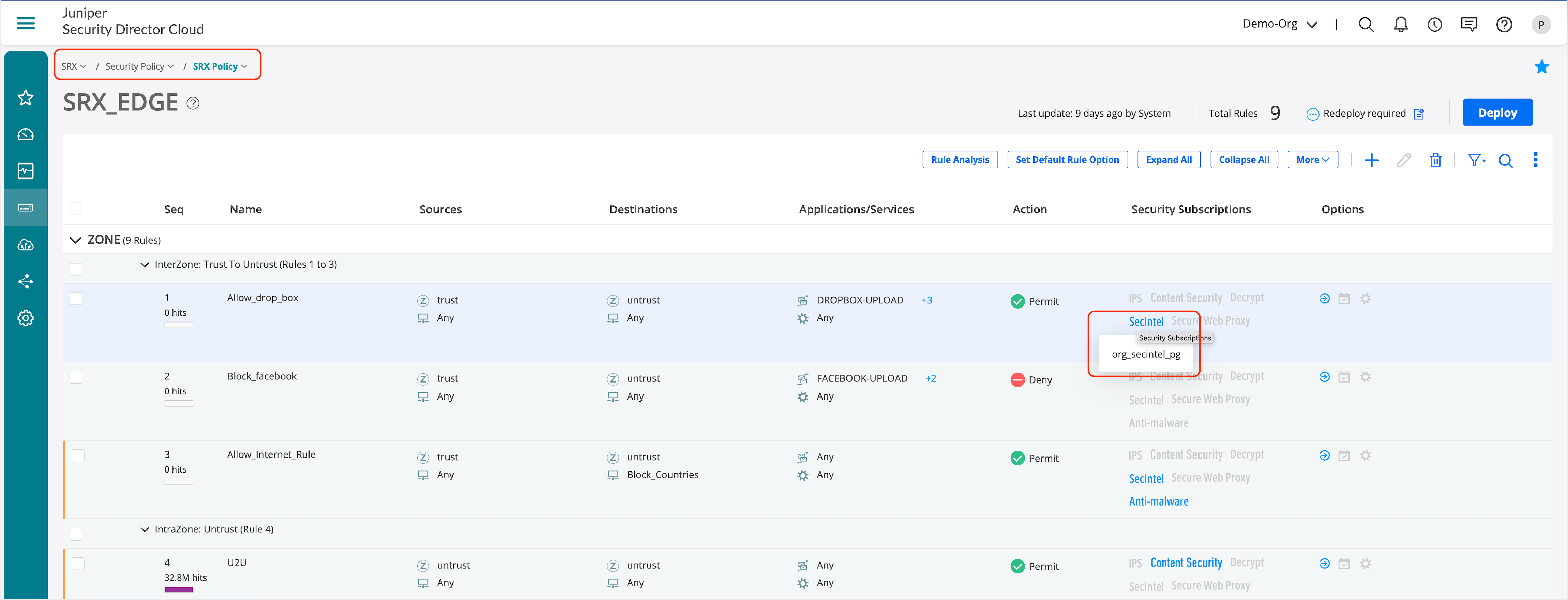
To enable SecIntel profile group in a security policy:
- Go to SRX > Security Policy > SRX Policy.
- Select the policy you want to modify and click the pencil icon.
- Edit policy to enable SecIntel profile group or click on Create New to select a different profile.
Advanced Anti-Malware
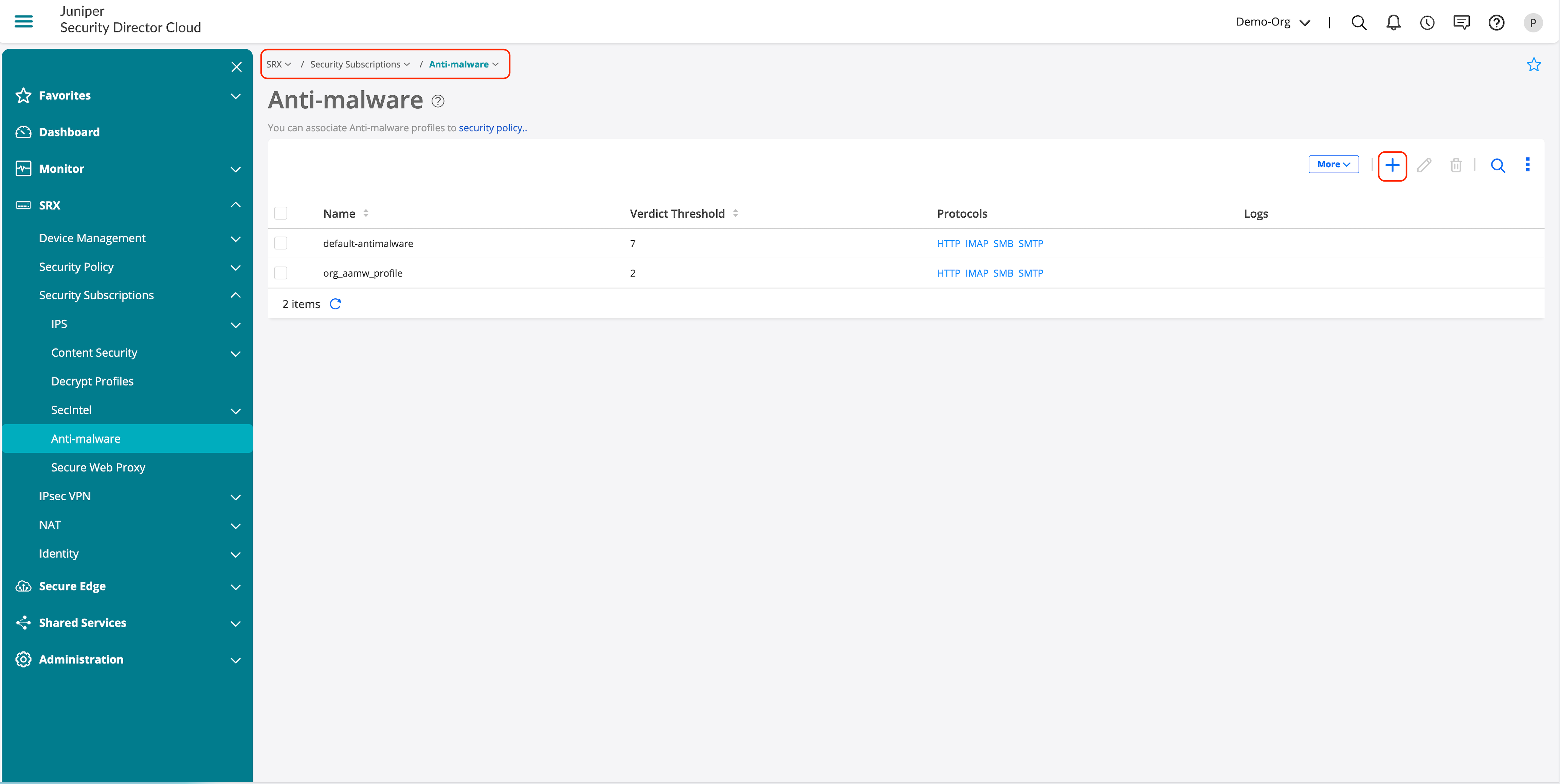
- Go to SRX > Security Subscriptions > Anti-malware.
- Click +.
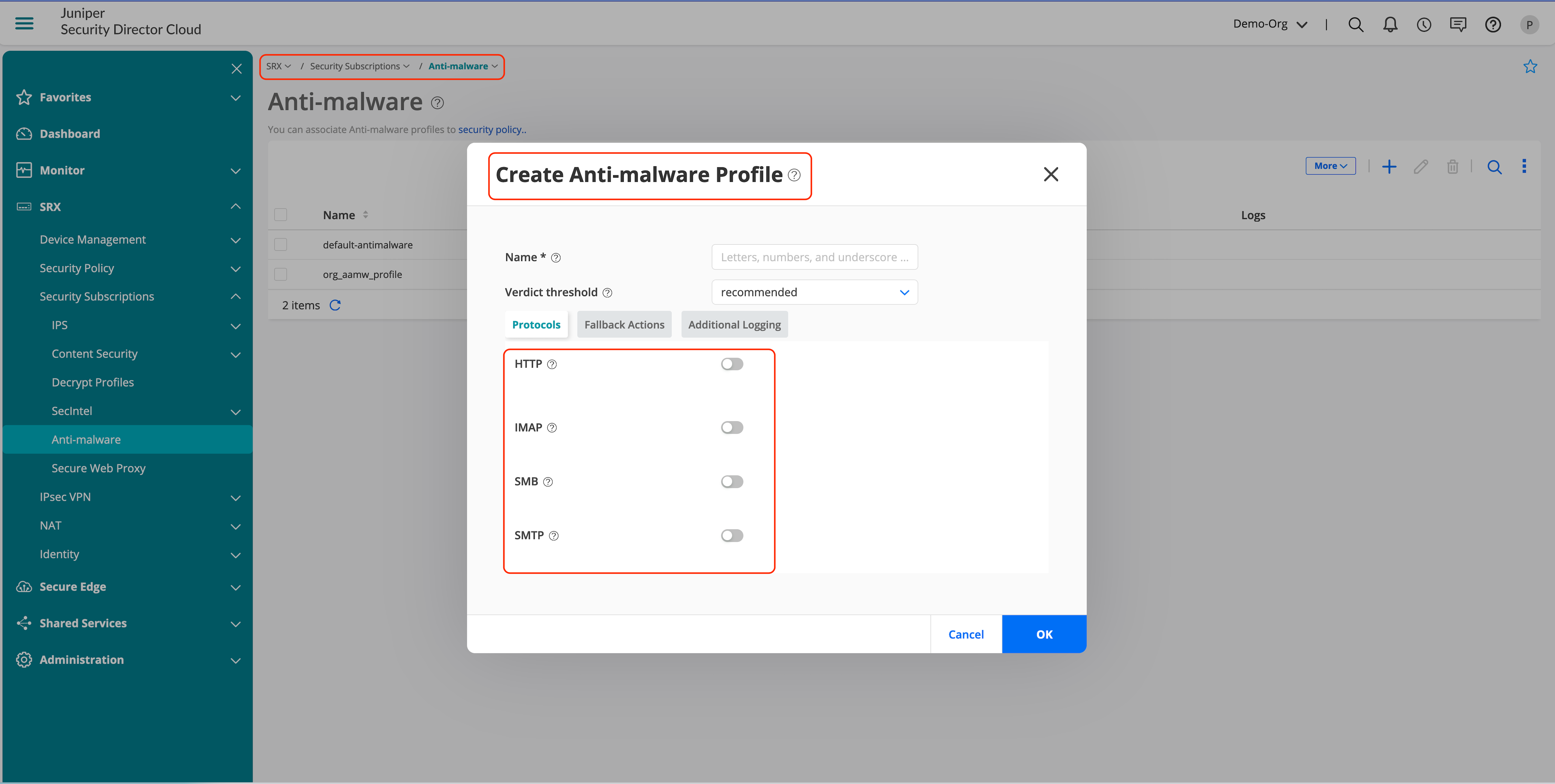
- Configure the protocols that you need to enable and click OK to save the AAMW profile.
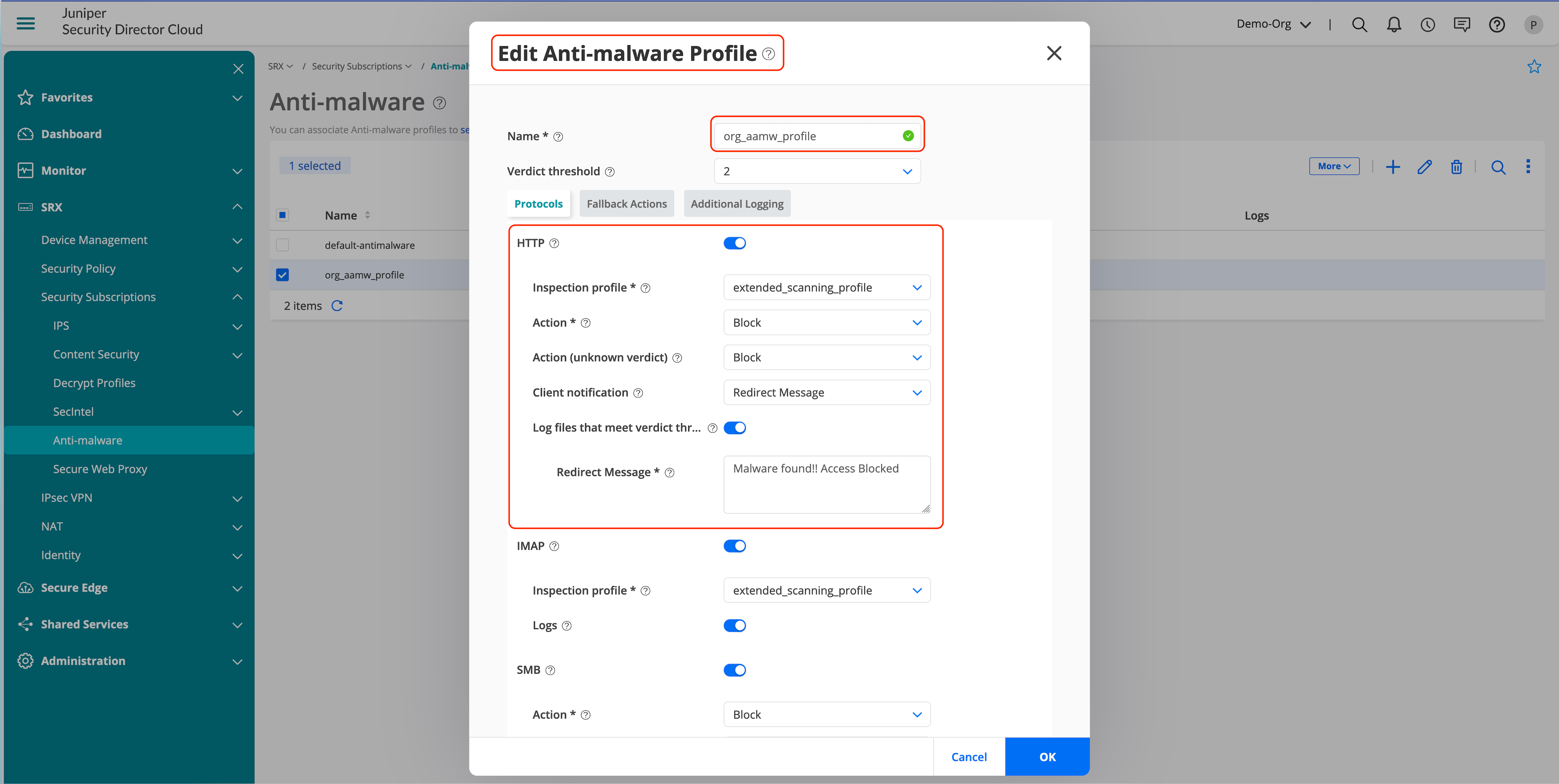
Created AAMW profile is configured in a security policy.
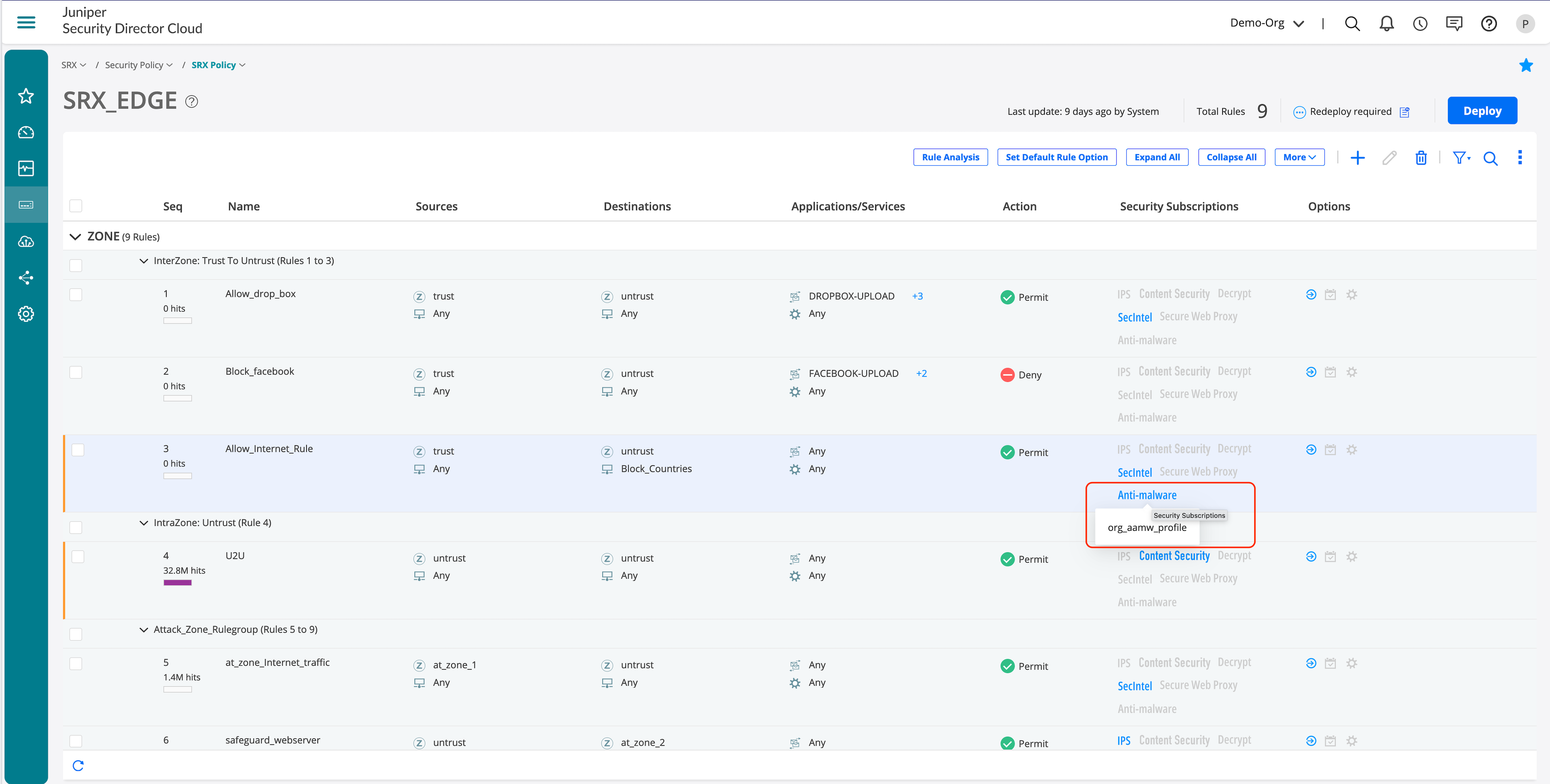
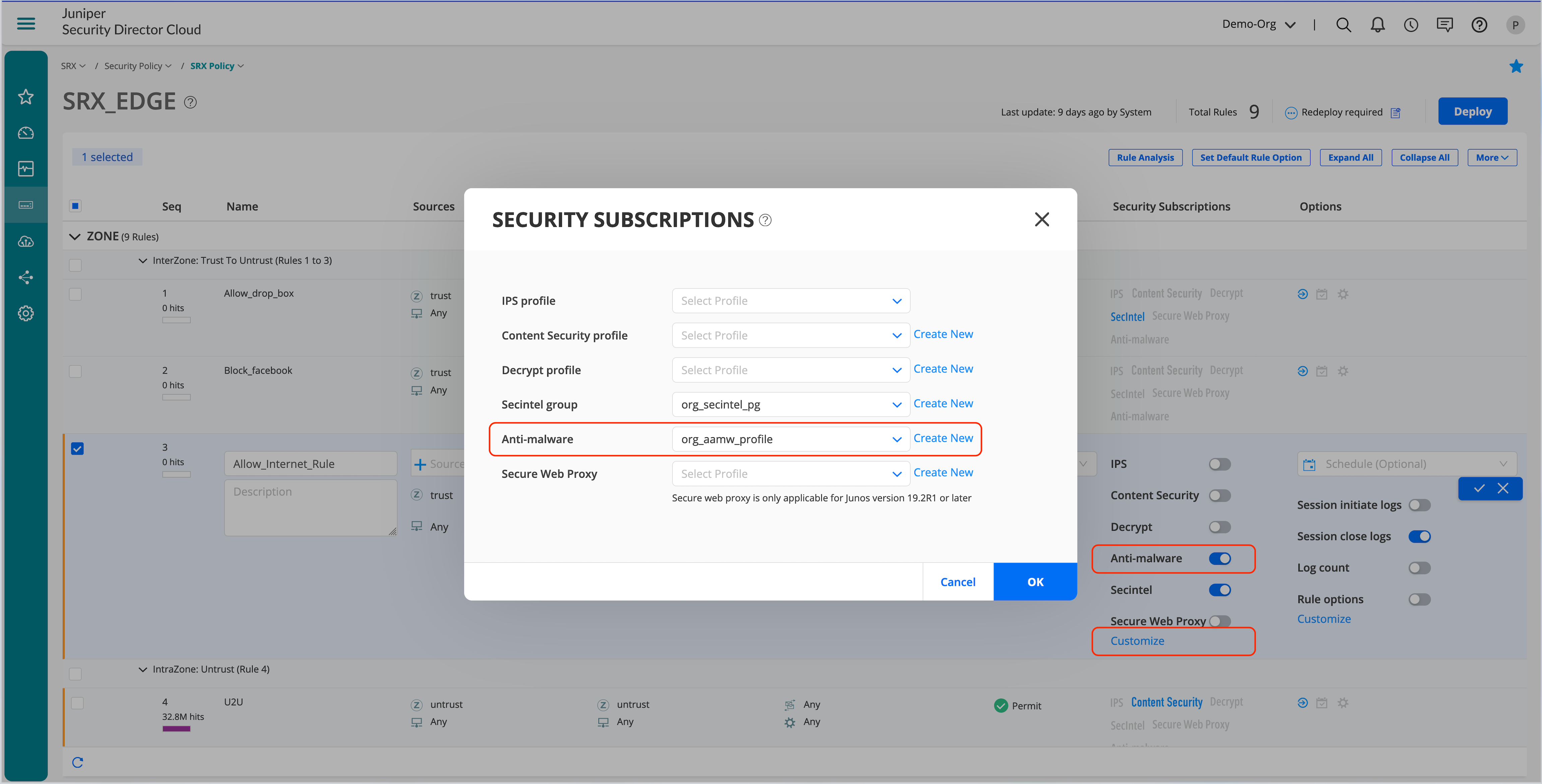
DNS Security
DNS security is configured in two phases:
- Enabling SecIntel phase, which is covered under the SecIntel section.
- Enabling core DNS security features such as DNS DGA and DNS Tunneling, which are covered in this section.
To enable DNS security, follow the path to configure the settings on Juniper Security Director Cloud:
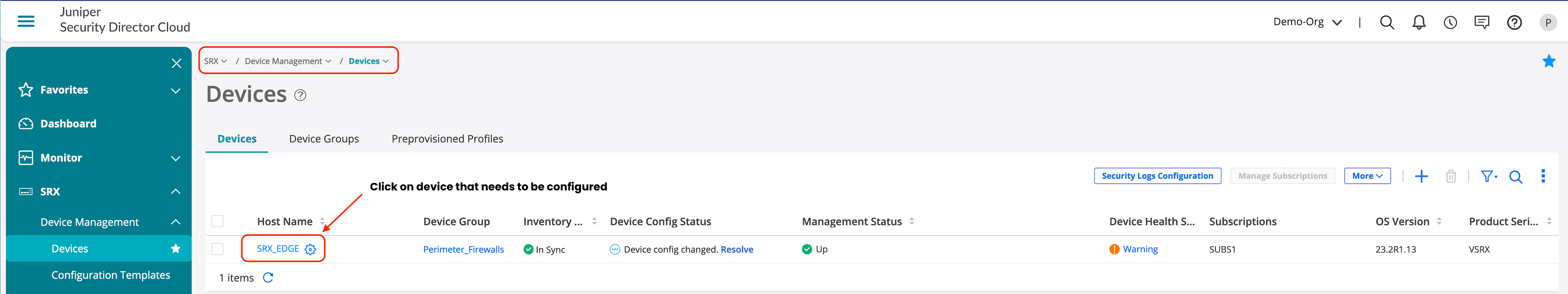
- Go to SRX > Device Management > Devices.
- Click the device we want to configure DNS security.
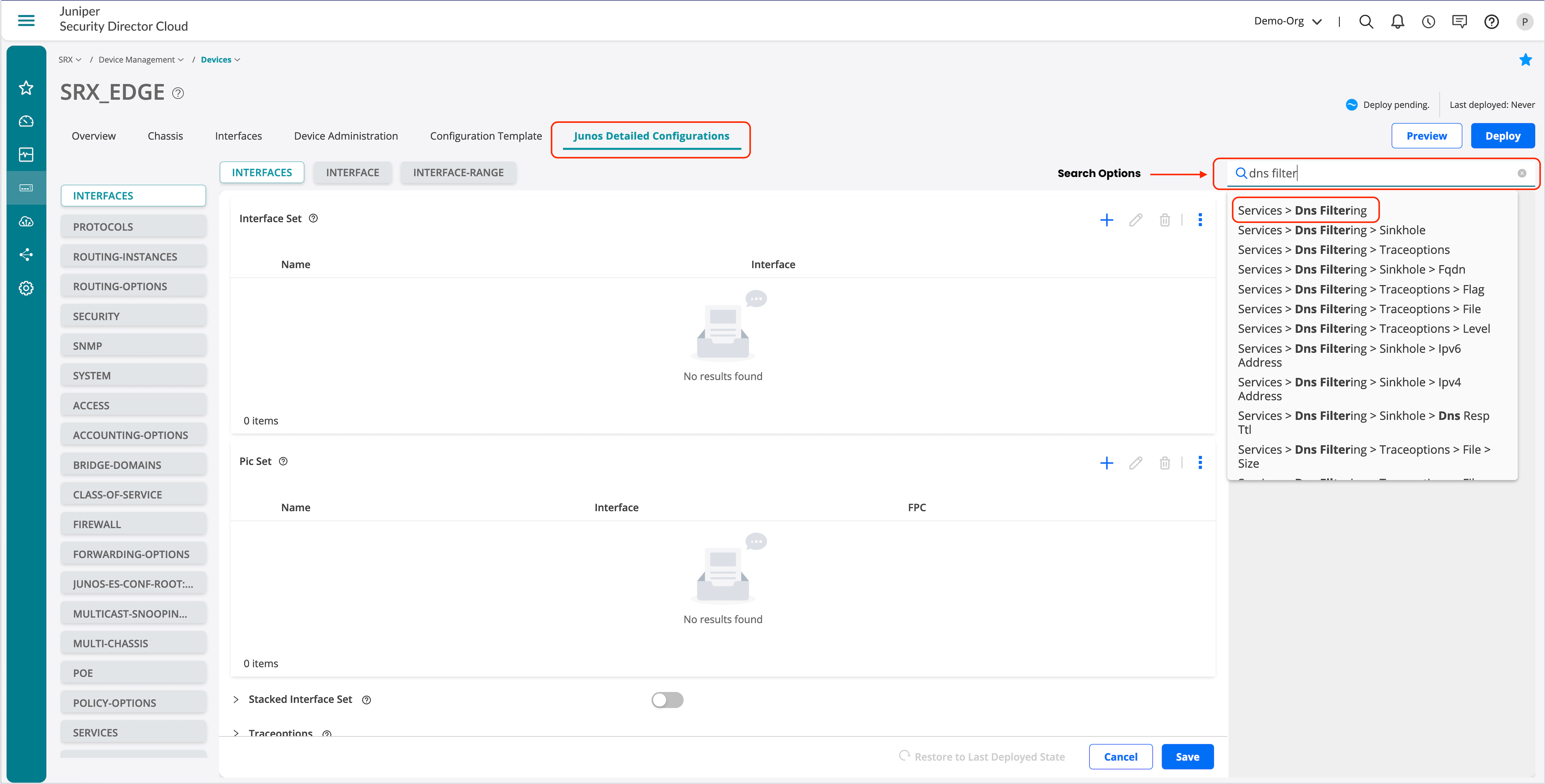
- Click Junos Detailed Configurations.
- Enter DNS filtering in the search section.
- Select Services > Dns Filtering.
- Enter the details.
- Click Save once done.
- Optional. Click Preview if you want to view saved configuration.
- Click Deploy to deploy the configuration to the device.
You can always complete all the configuration sections and save before deploying the final configuration.
Also, this configuration is the same for implementing IoT Security as well.
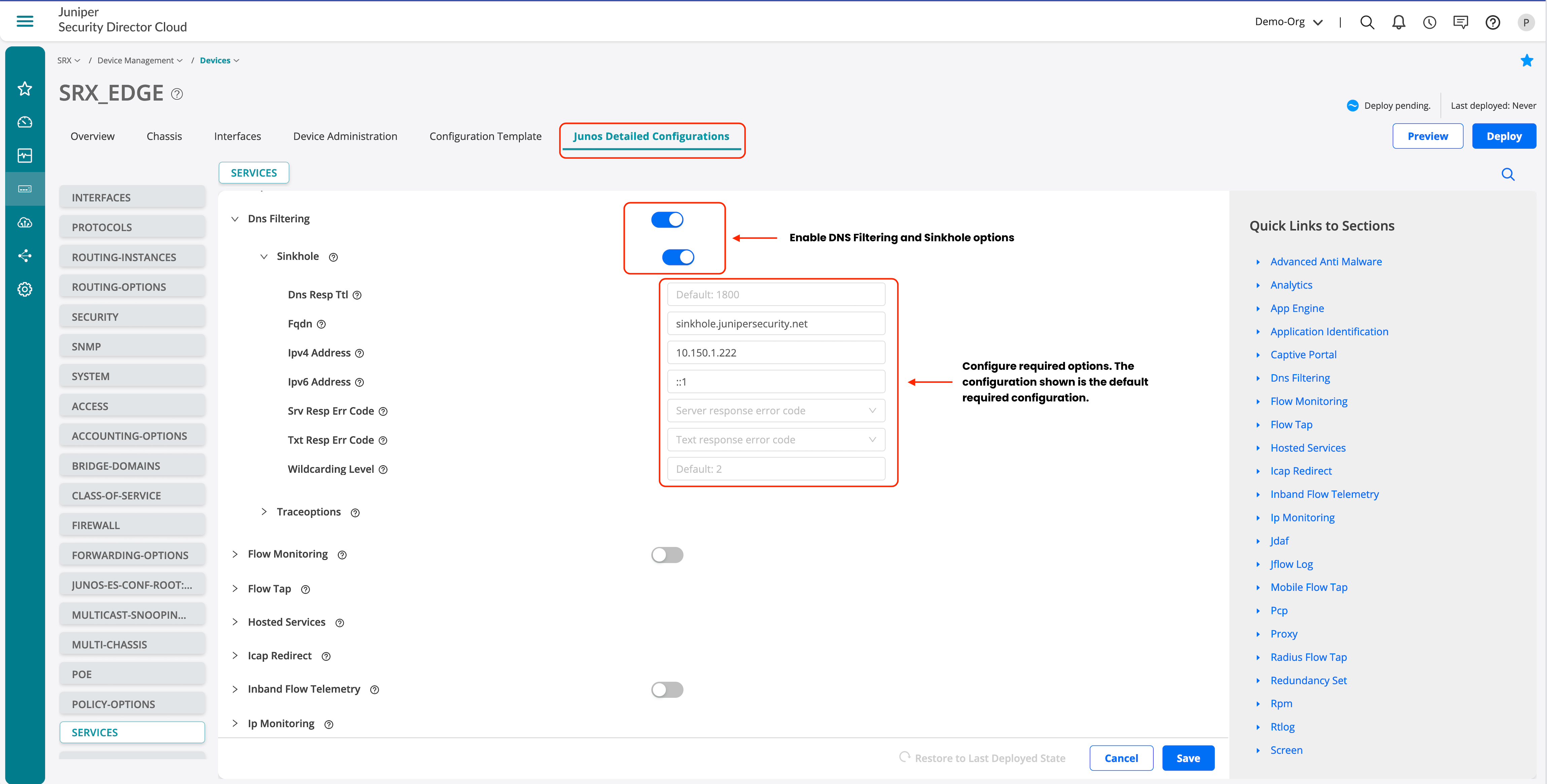
Let’s configure the core DNS security features:
- Enter metadata in the search section.
- Select Services > Security Metadata Streaming.
- Click to proceed to the configuration section.
- Click + to enable DNS metadata configuration.
- Click Save once done.
- Optional. Click Preview if you want to view saved configuration.
- Click Deploy to deploy the configuration to the device.
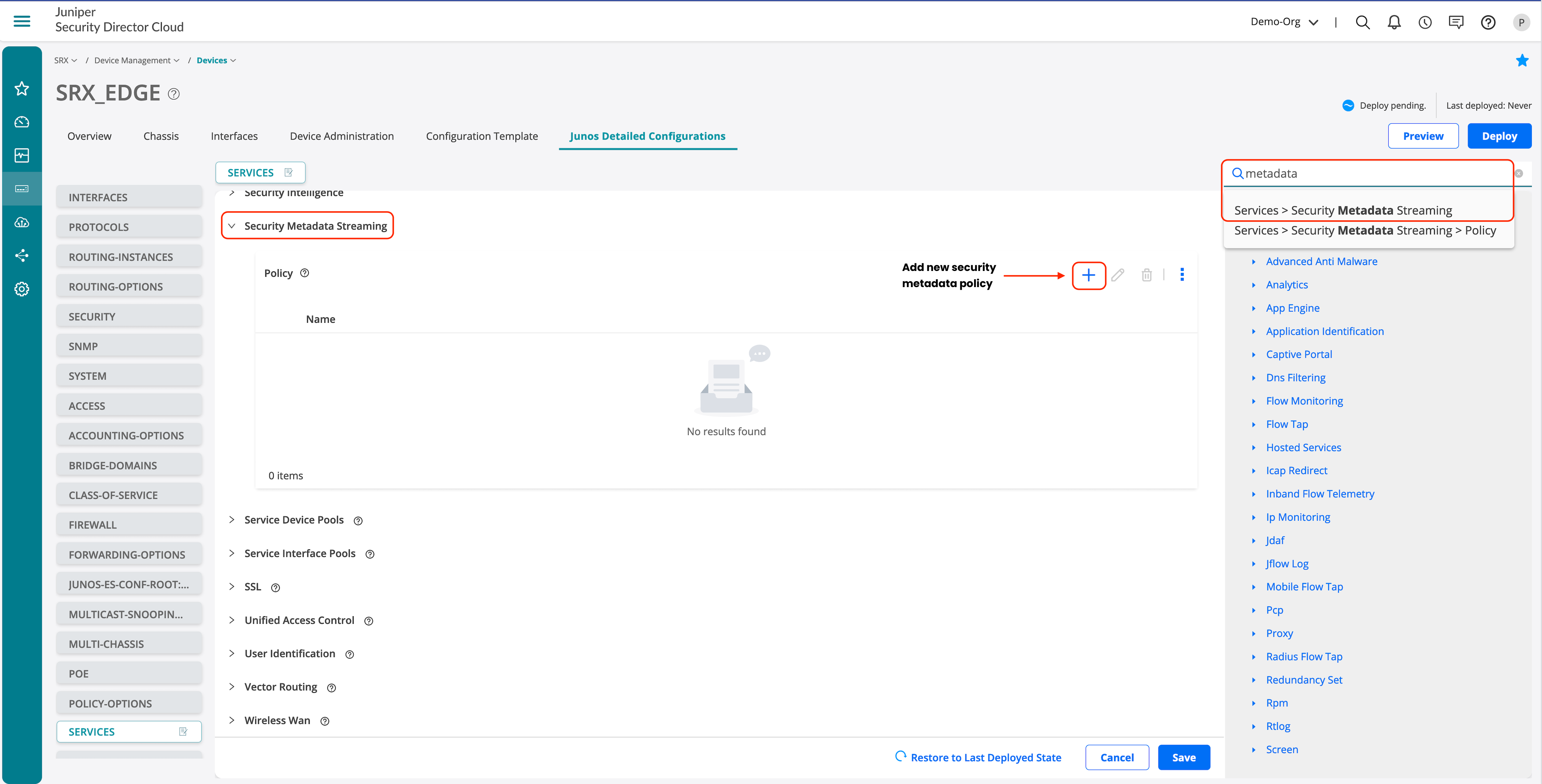
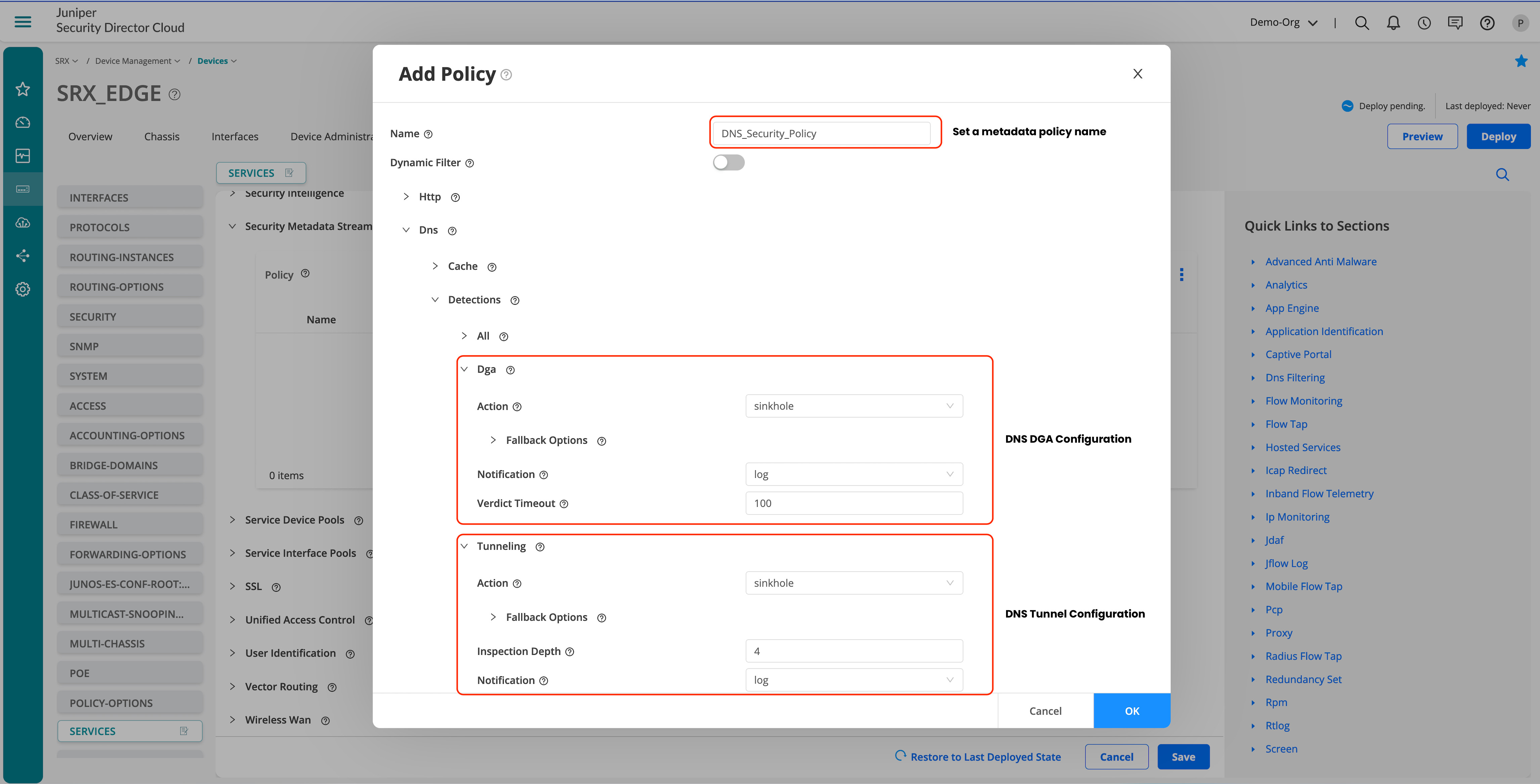
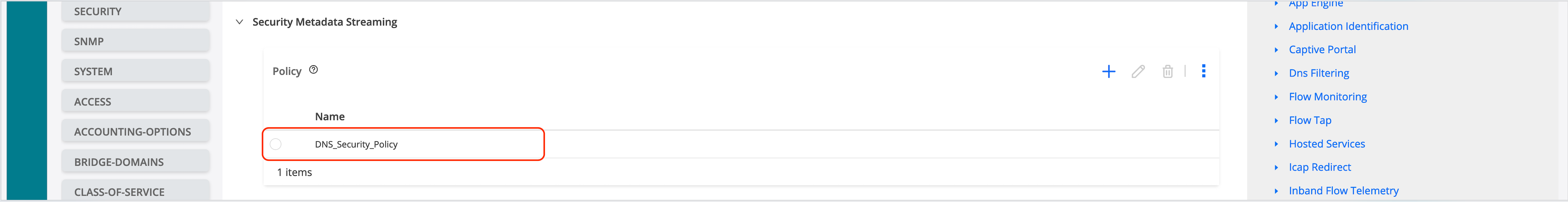
Ensure to save and deploy the configuration once its completed.
Let’s use CLI to configure the metadata streaming policy on a zone pair to enforce DNS security settings.
Ensure that the configuration is deployed before configuring the next steps through CLI.
# Add the security metadata streaming policy: set security policies from-zone trust to-zone untrust application-services security-metadata-streaming-policy DNS_Security_Policy
Security Screens
To configure Security IDS Screen option on Juniper Security Director Cloud:
- Go to SRX > Device Management > Devices.
- Click on the device.
- Click Junos Detailed Configurations.
- Search for screens.
- Select Security > Screen.
- Click + to add a new profile.
Figure 39: Juniper Security Director Cloud—Screens Configuration
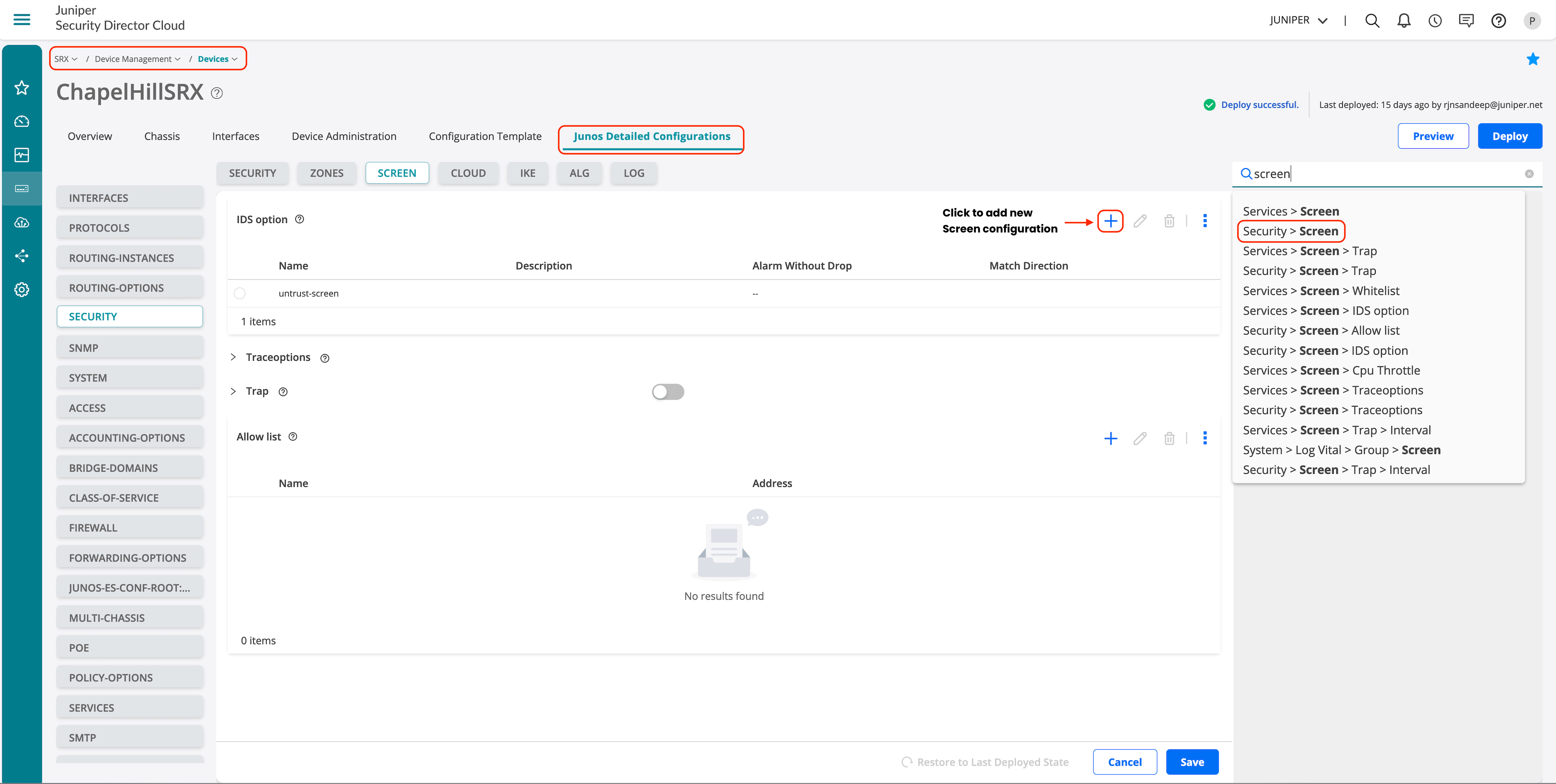 Figure 40: Juniper Security Director Cloud—Screens Flood Attack Options
Figure 40: Juniper Security Director Cloud—Screens Flood Attack Options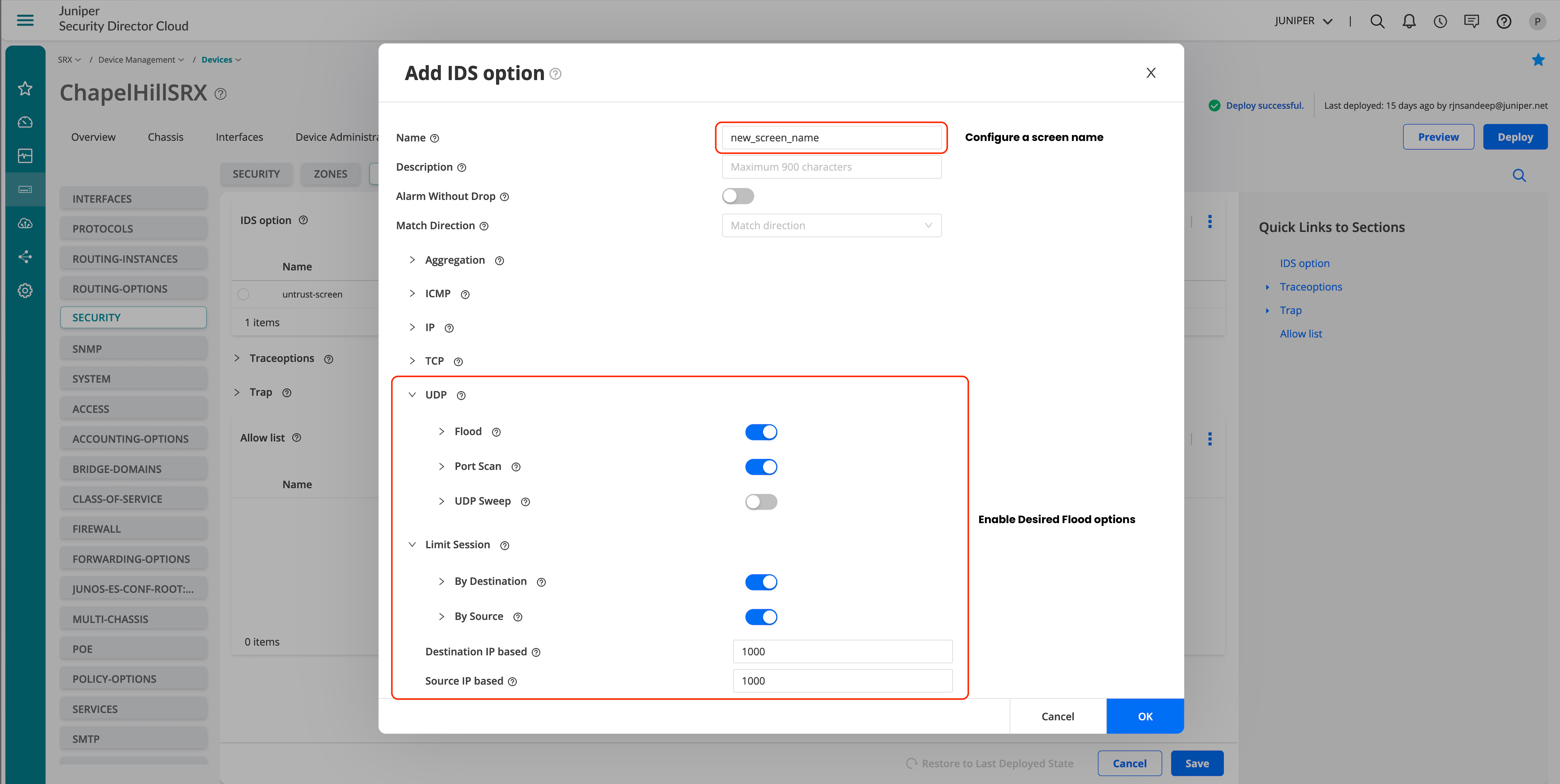
- Click OK to save the screen configuration once the desired configuration is completed.
- Click Zones to enforce the screen on a
specific zone.
Figure 41: Juniper Security Director Cloud—Assign Screens Options to Zone
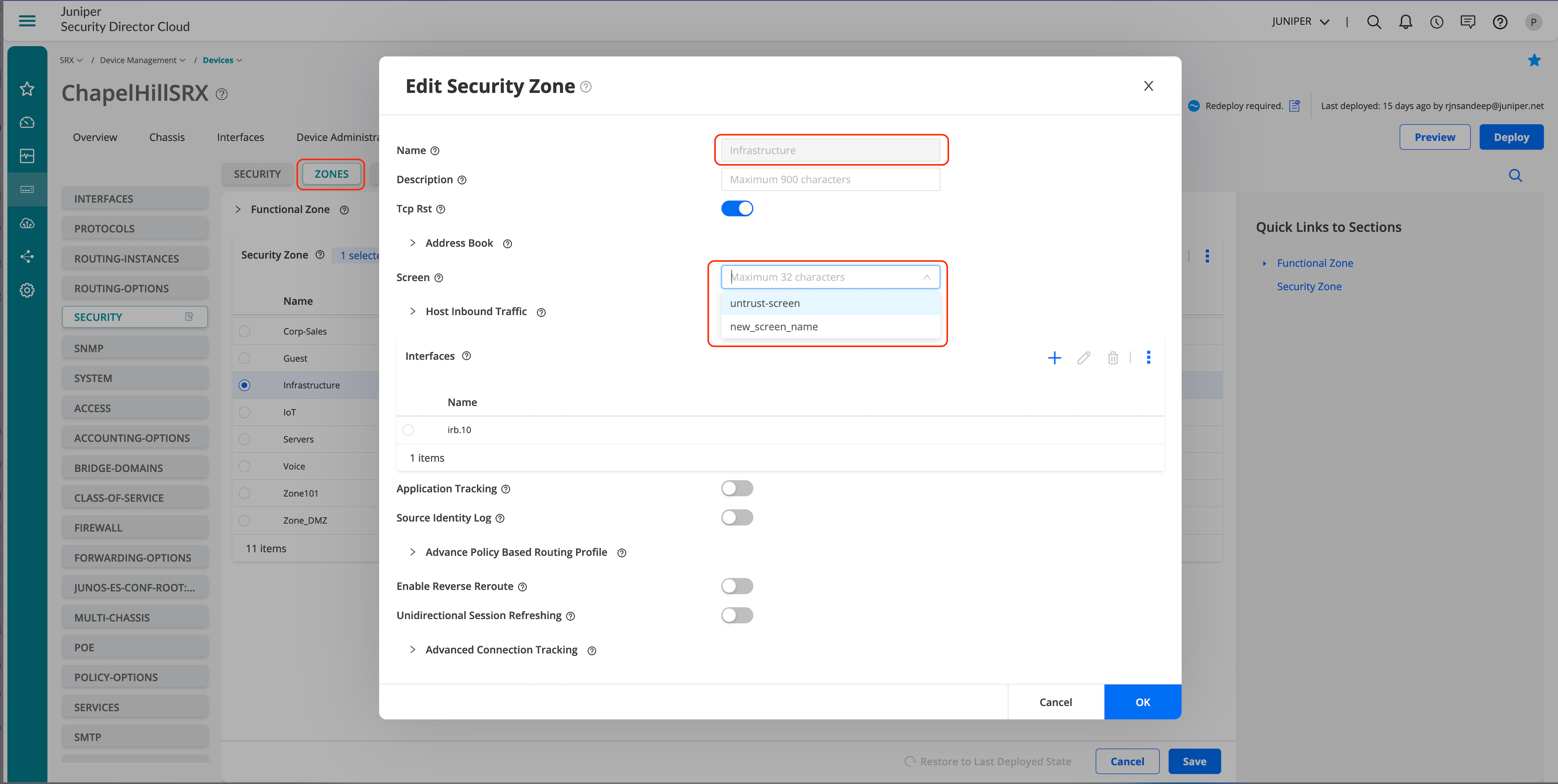
- Click OK to save the configuration once the new screen configuration is applied to the zone.
- Click Deploy to deploy the configuration to the device.
Reverse SSL Proxy
As the data center next-generation firewall use case focuses on protecting internal resources such as webservers, we can optionally implement SSL reverse proxy. SSL reverse proxy ensures advanced services are applied to decrypted webserver traffic and inspected before leaving the firewall to gain the webserver resources.
The creation of the webserver certificates is not covered in this section. You must import this certificate into Juniper Security Director Cloud. This certificate is used when creating the SSL proxy profile.
To create the SSL reverse proxy profile:
- Import webserver certificates.
- Create the SSL reverse proxy profile.
- Go to SRX > Security Subscriptions > Decrypt Profiles.
- Click + to add a new profile.
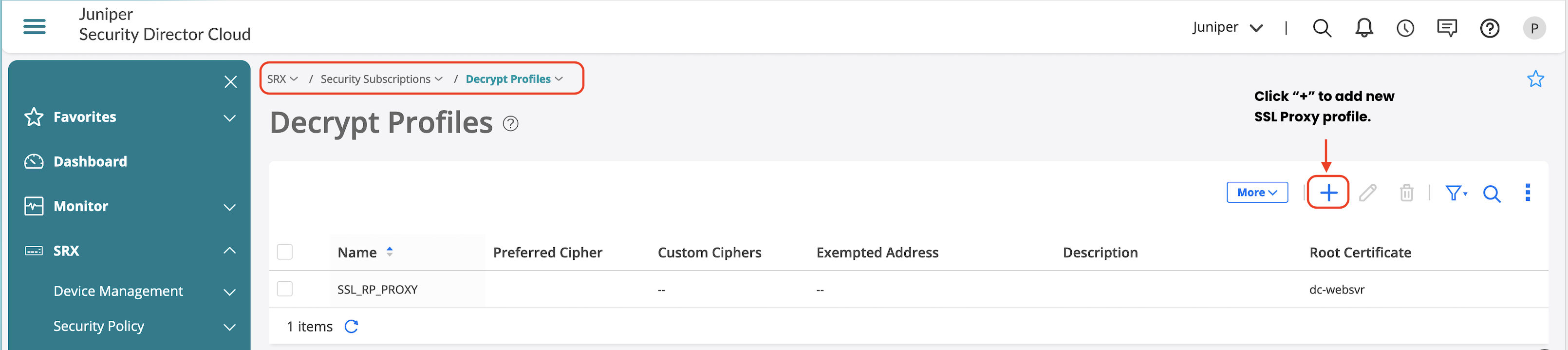
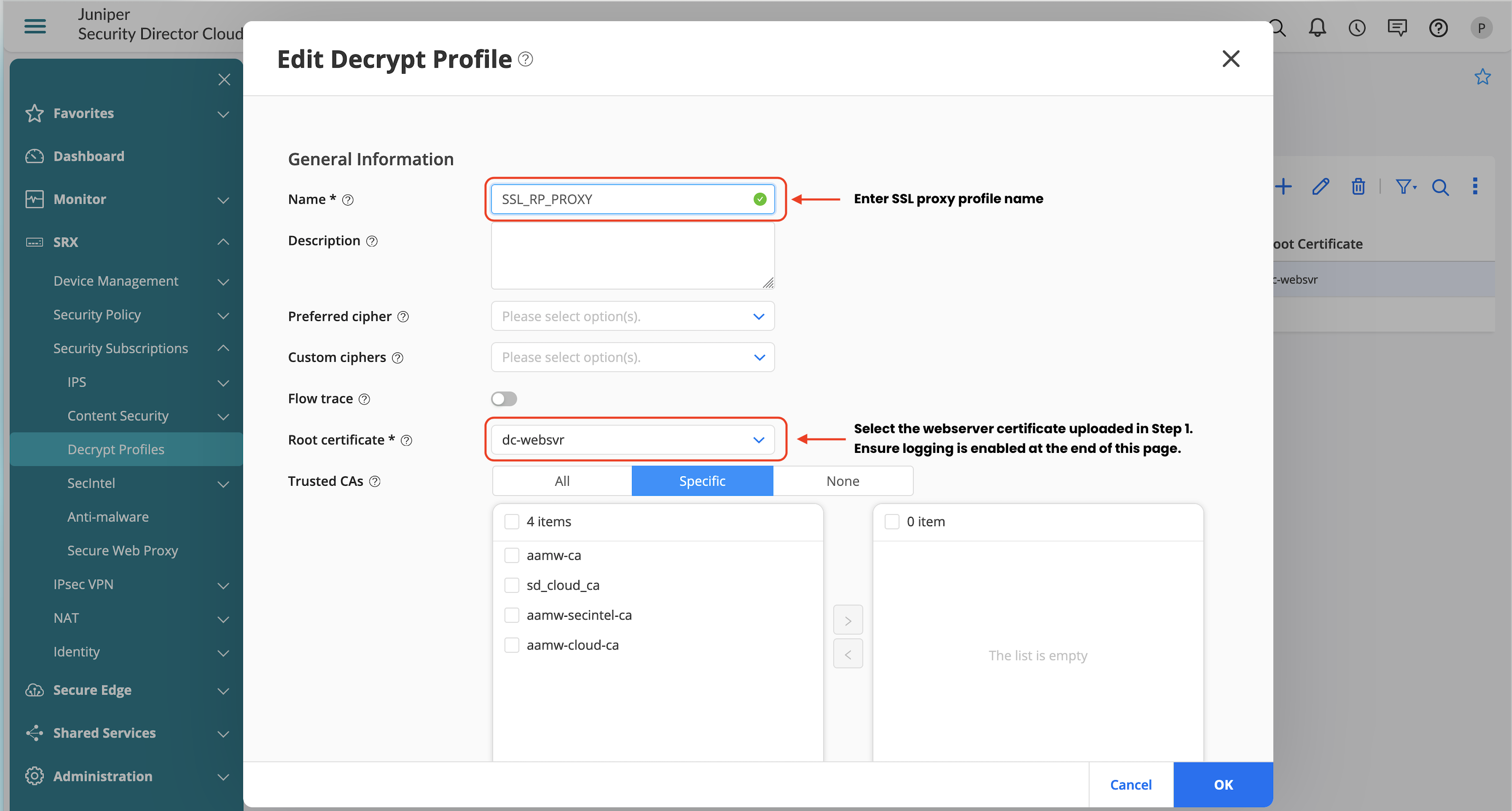
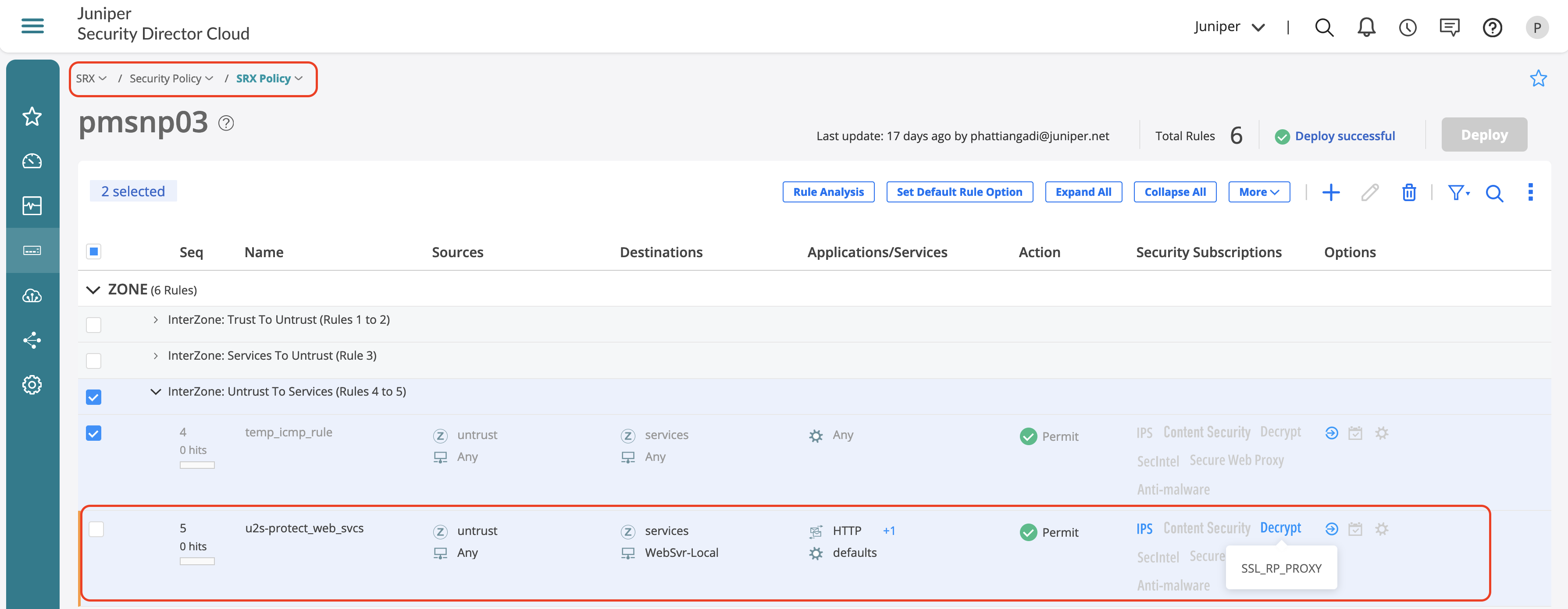
Include the profile in a firewall rule for enforcement:
- Go to SRX > Security Policy > SRX Policy.
- Click + to add new firewall rule.
- Enter Source Zone and Source Address.
- Enter Destination Zone and Destination Address.
- Select Services and Applications.
- Select Advanced Services under security subscriptions that must be enabled. In this example, IPS is selected.
- Select the SSL Reverse proxy profile created in the previous step.
Data Center Next-Generation Firewall Solution Validation
The configuration provides advanced security services in data center environment using next-generation firewalls. In this section, we’ll focus on validating the solution that is implemented with this JVD.
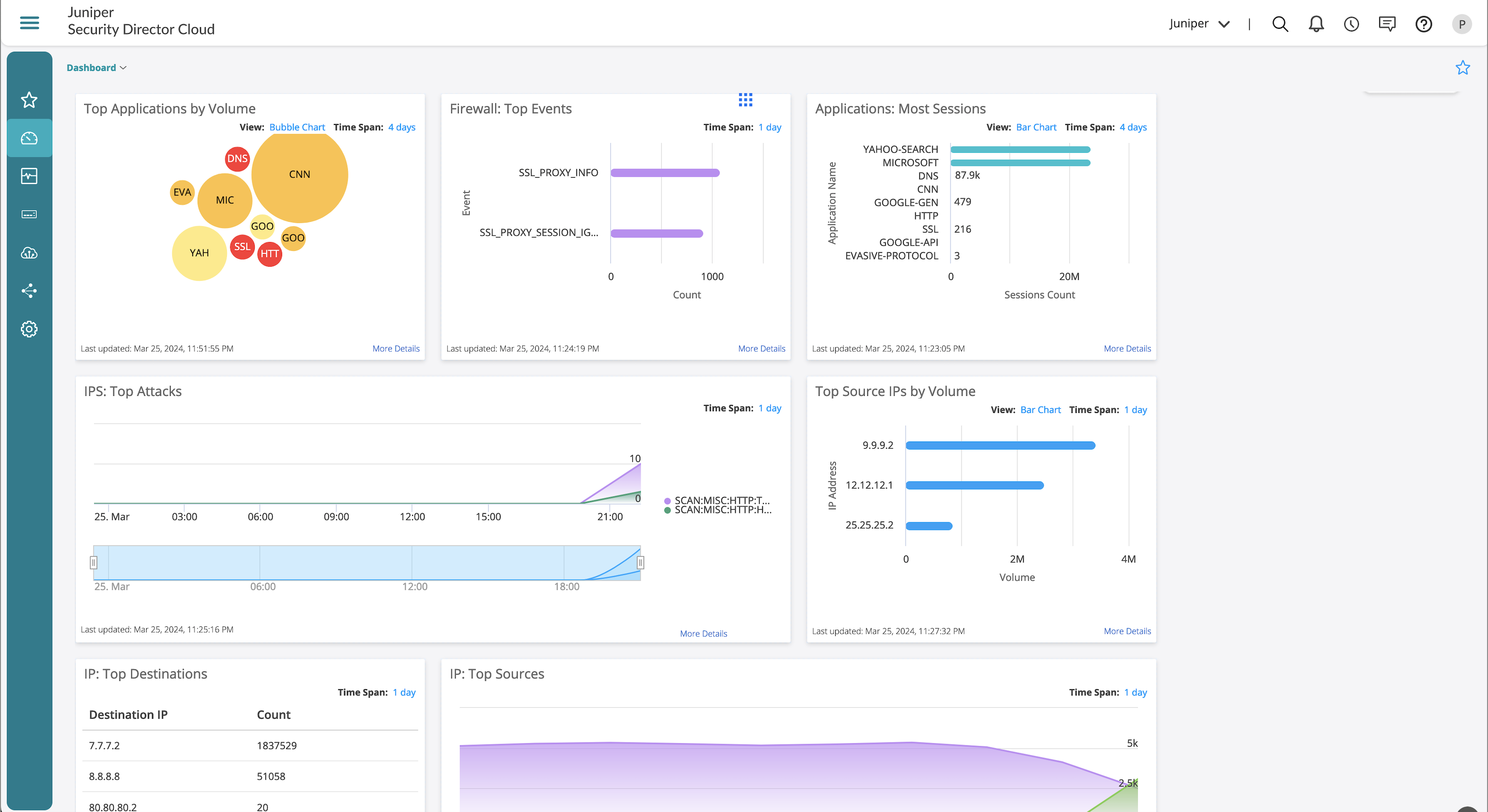
Let’s start with the Juniper Security Director Cloud Dashboard, which is the landing page when logged in. The Dashboard page provides a landscape of what is happening in the environment through various readily available widgets.
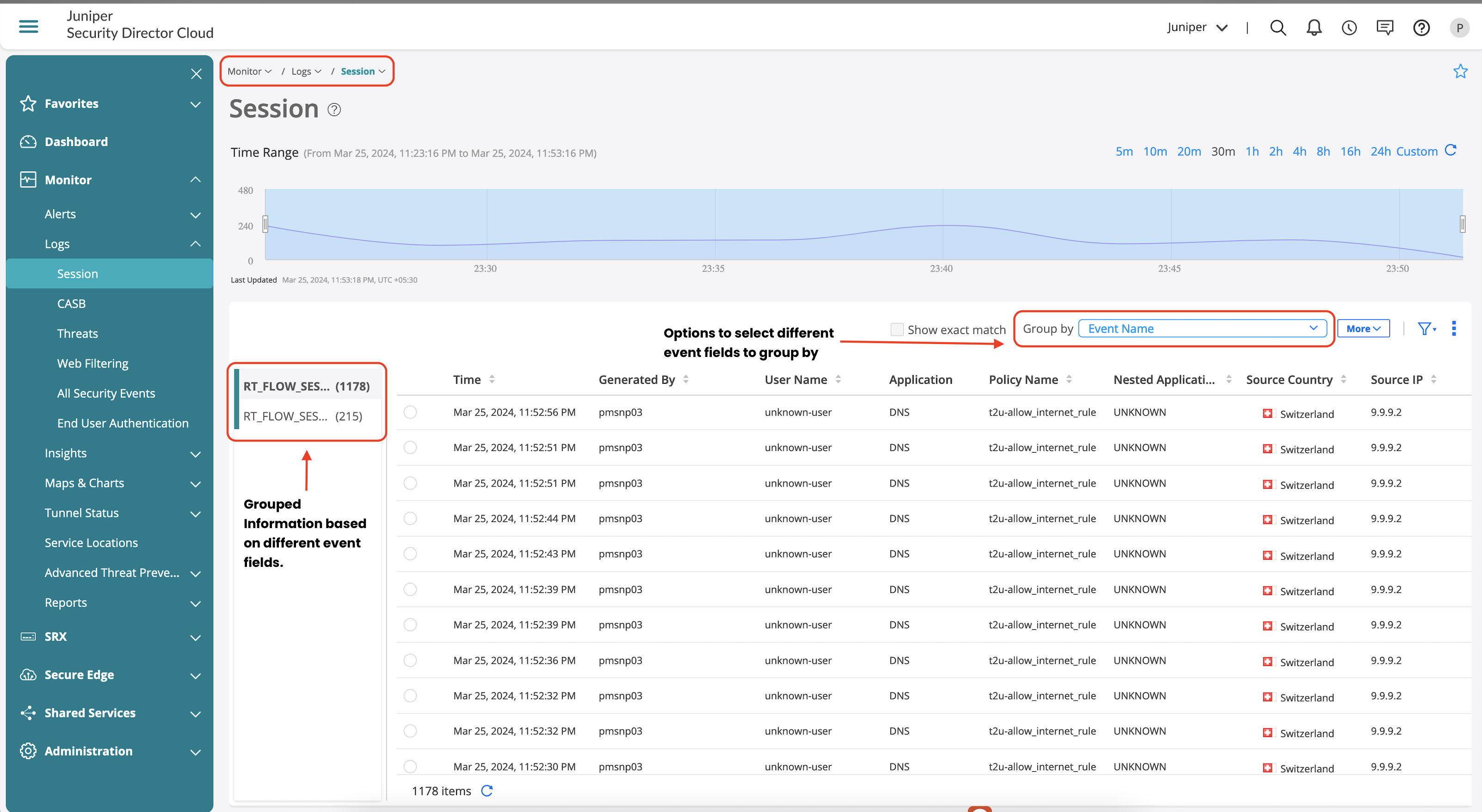
The Monitor > Logs > Session page provides a snapshot of the traffic flow through the environment. Using Session page, you can filter information based on various options that’s provided on the page.
| Filter Options | Description |
|---|---|
|
Use Show advanced filter to search through the logs. All the event fields are used to run through the search. |
|
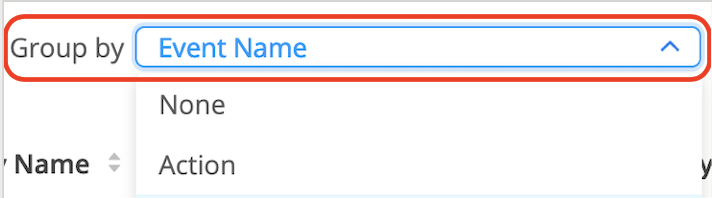
Use Group by to sort through the logs based on predefined field. Which is shown in the next screenshots. |
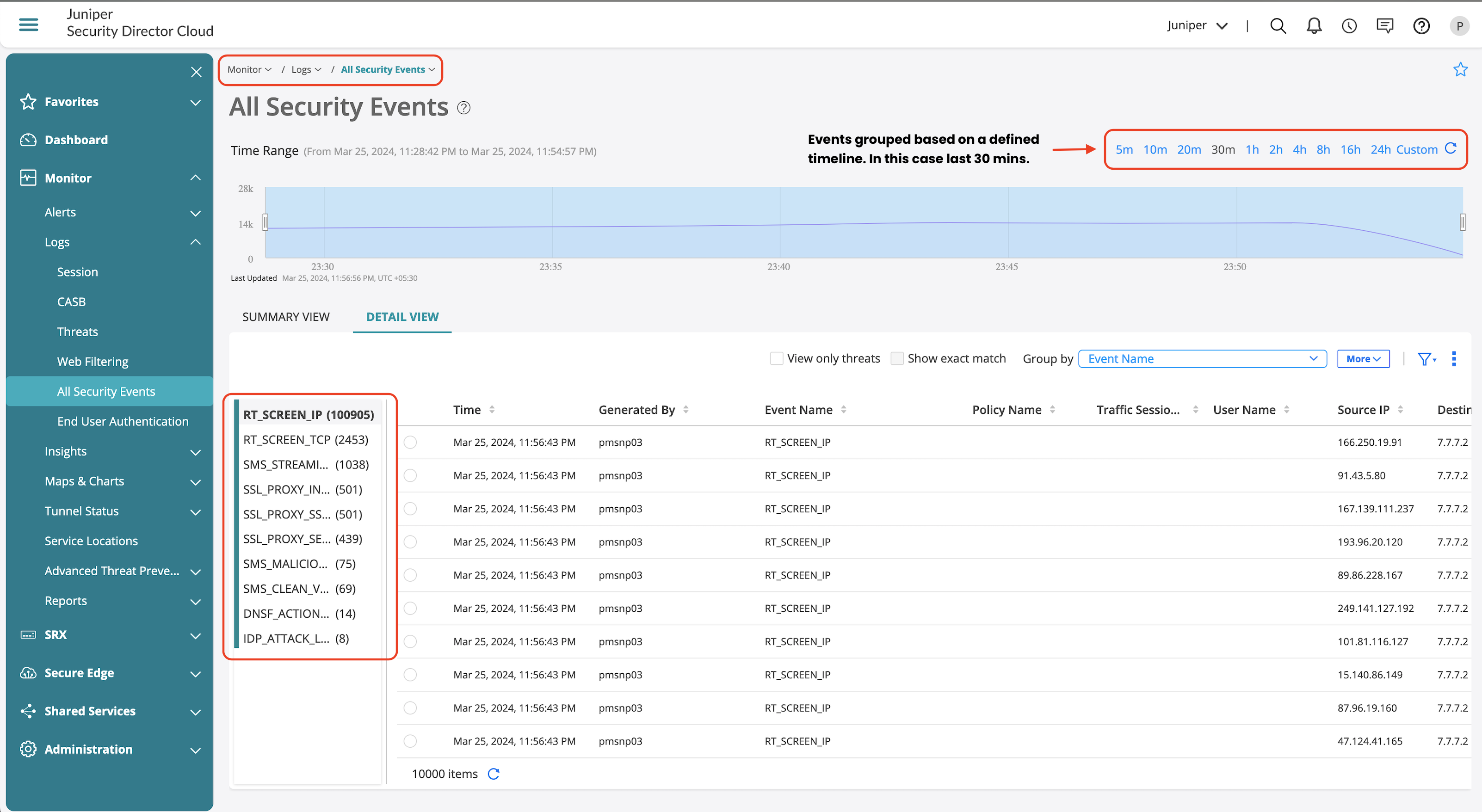
All Security Events page provide details on all the security events received from the device.
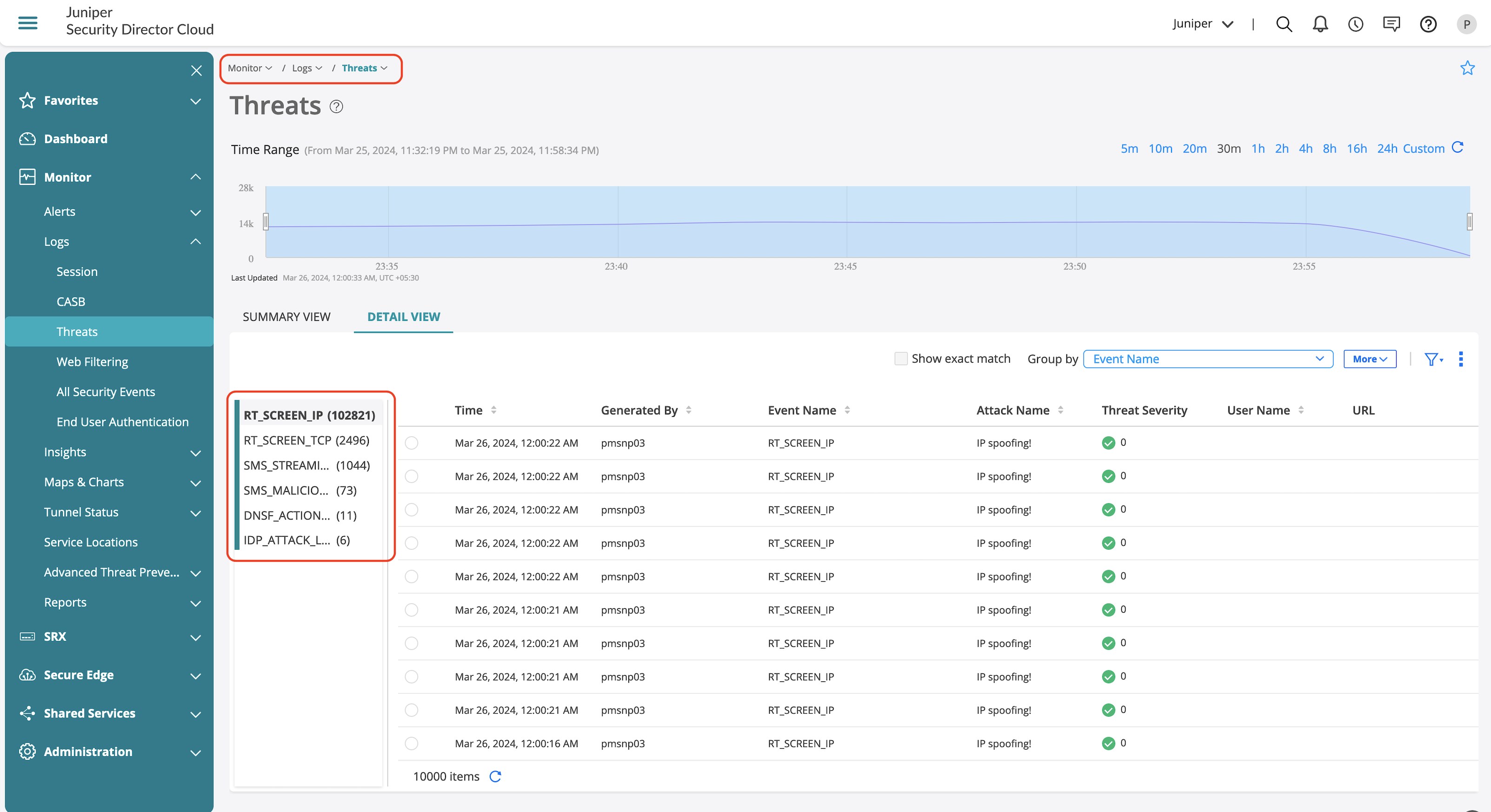
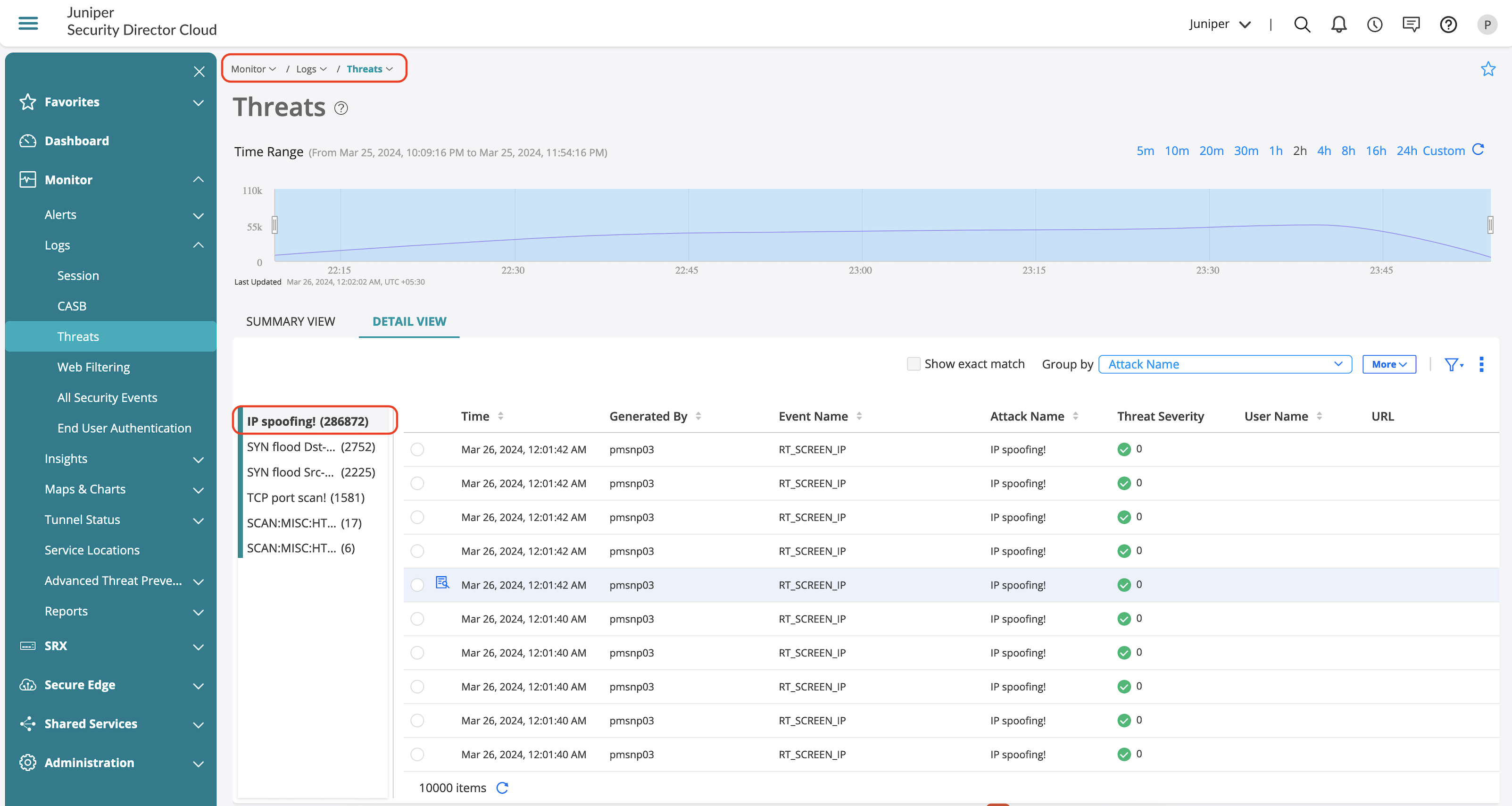
Threats page focuses only on the threats identified in the environment.
Application Security Validation
Grouped applications provide a view on identified applications from the traffic where the firewall has processed.
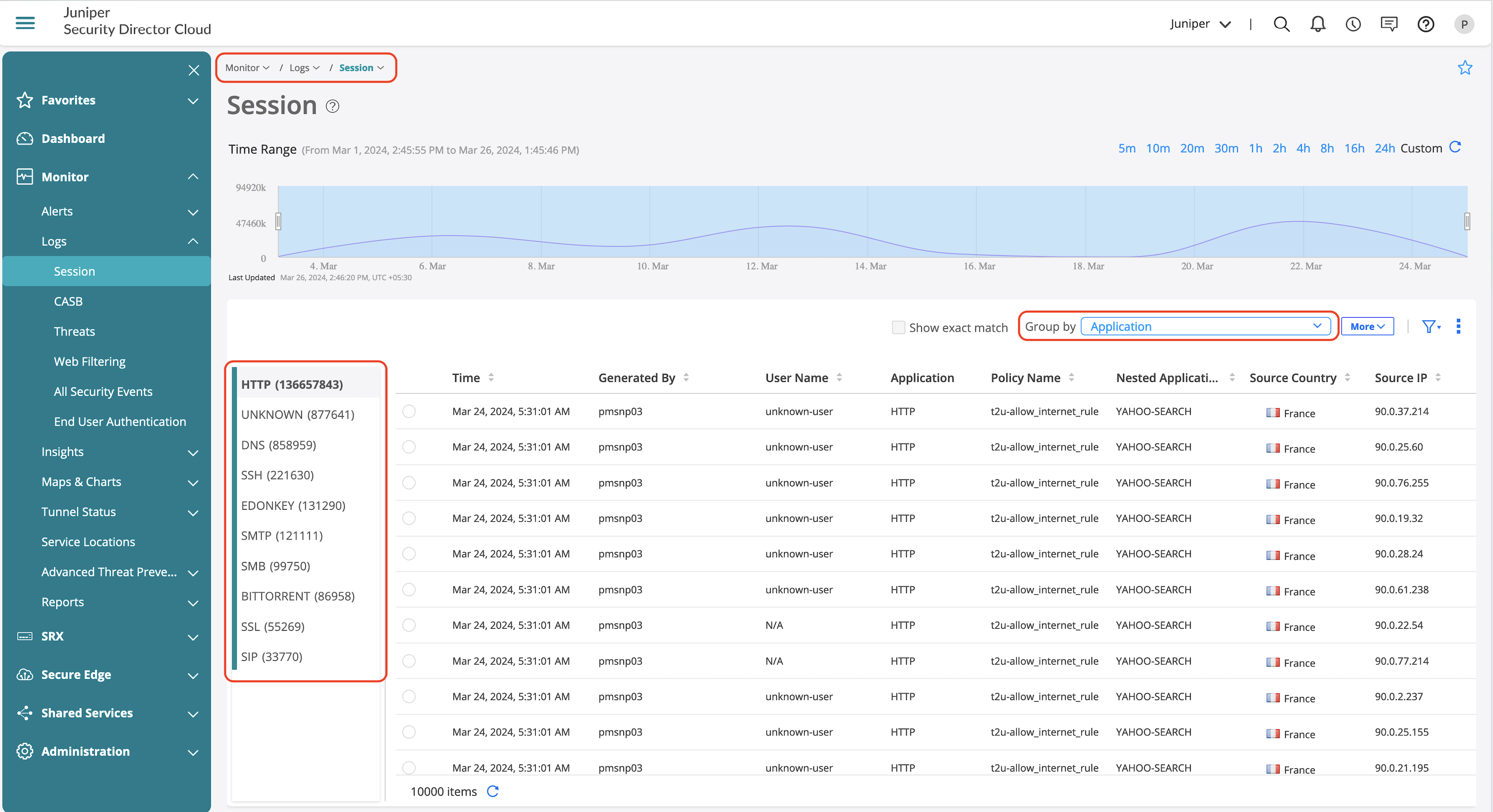
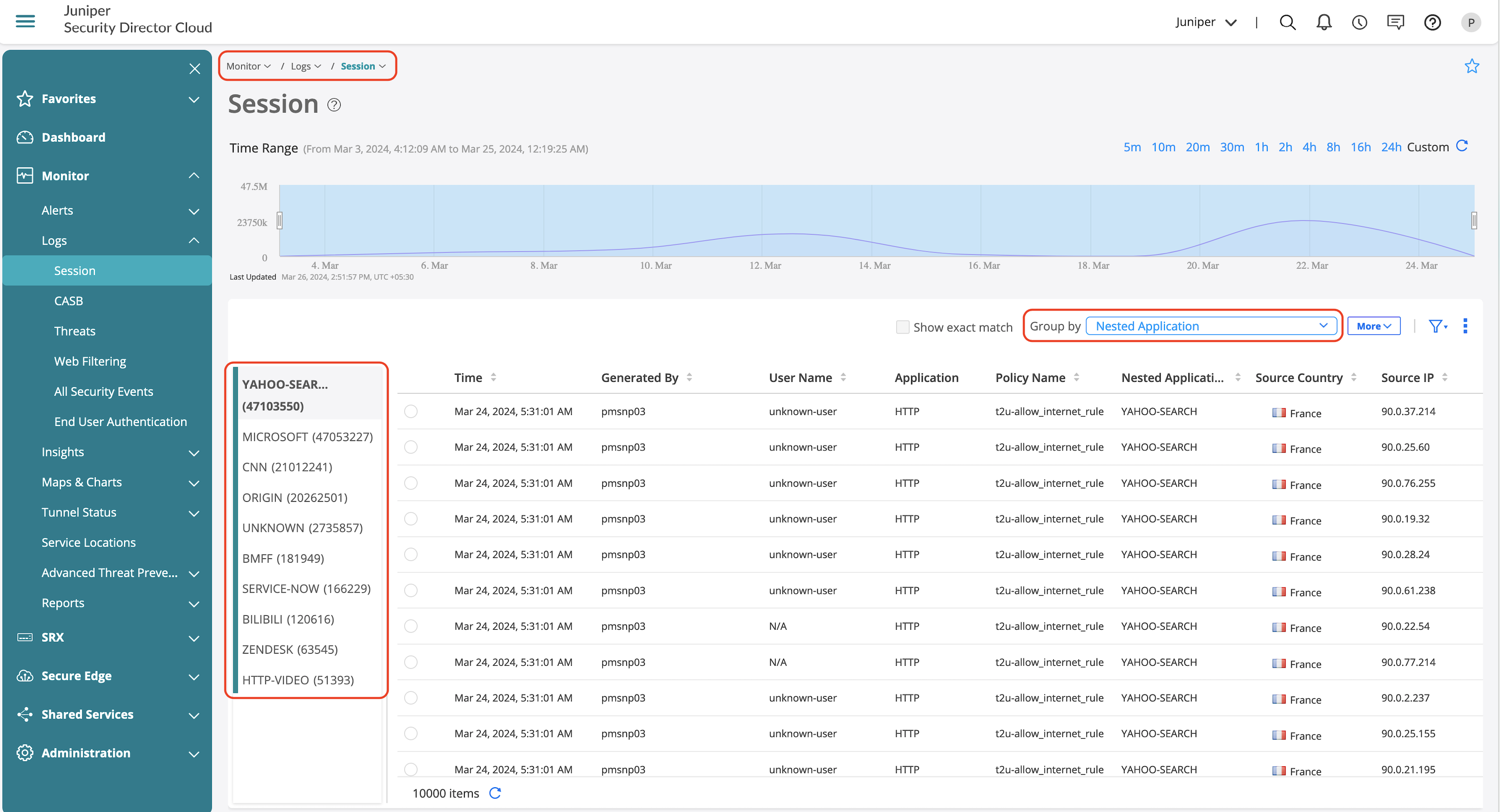
Grouping using Nested Applications provides information on the actual applications using the applications that is shown in Figure 49.
IDP Feature Validation
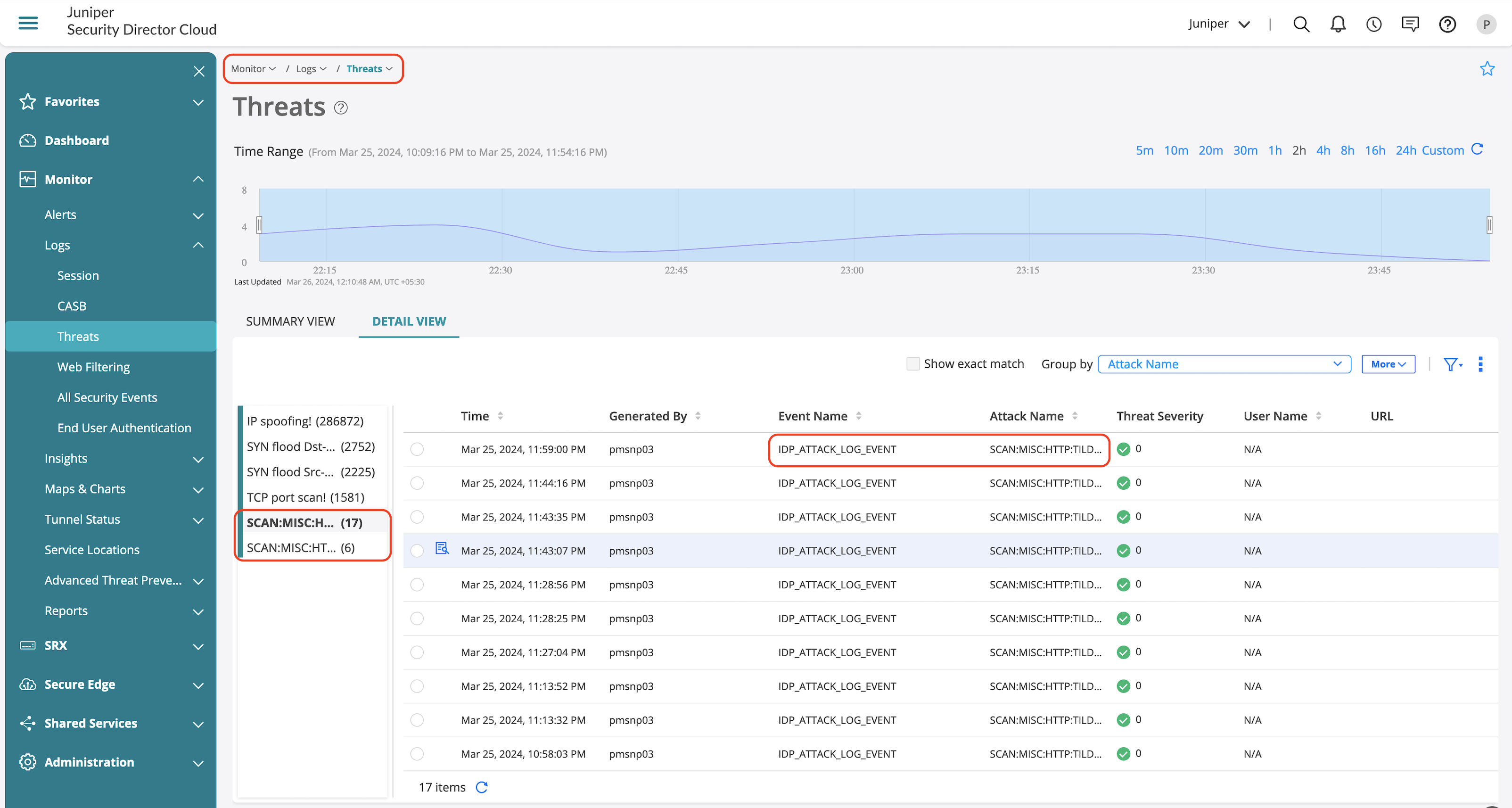
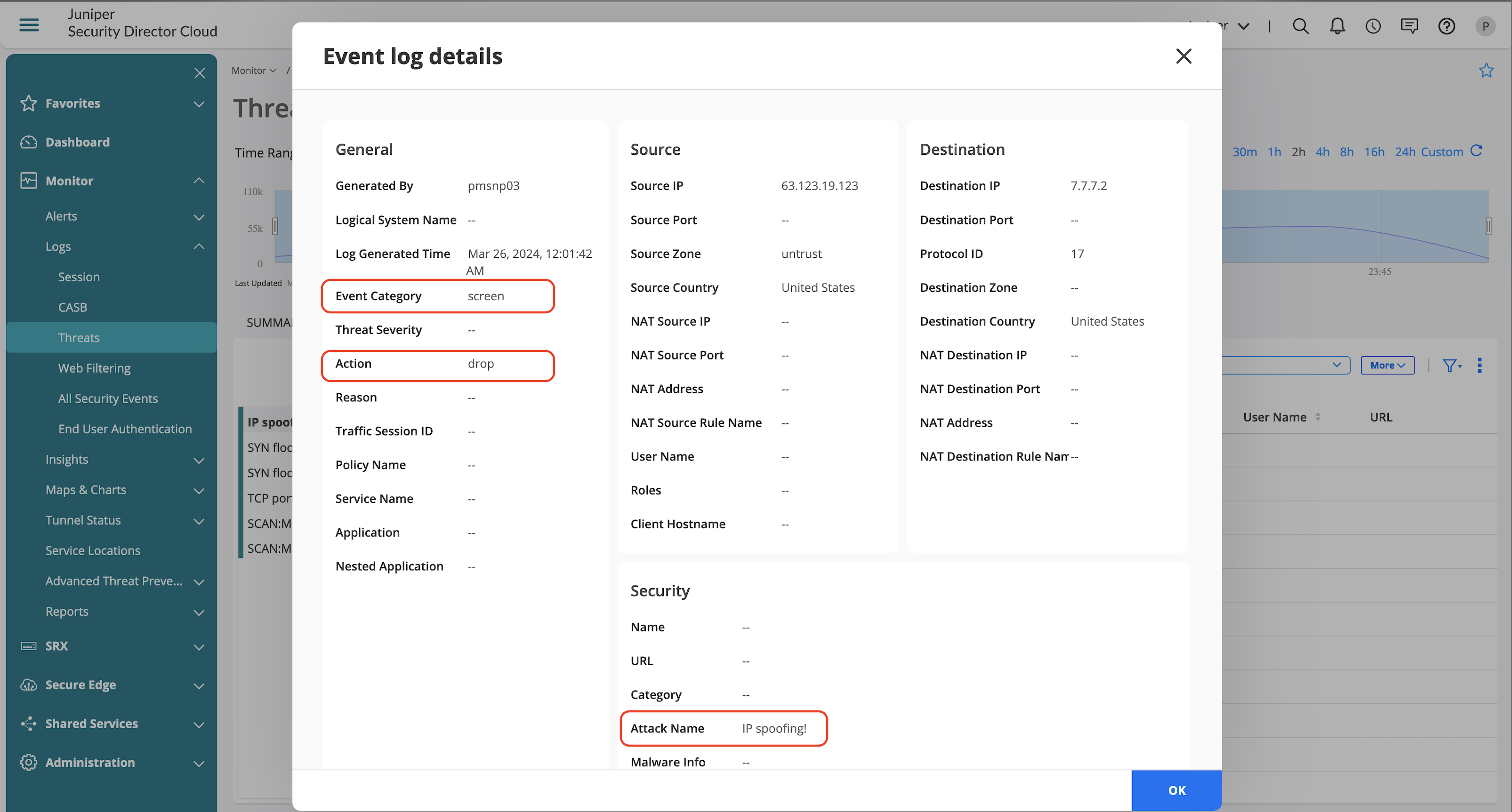
Threats page provides information on the detected IDP attacks in the environment. You can also view the detailed information of the following:
- Source and destination zone
- Source and destination IP addresses
- IDP policy and rule that triggered the detection
- Detected attack and its severity
- Action taken on the detected attack
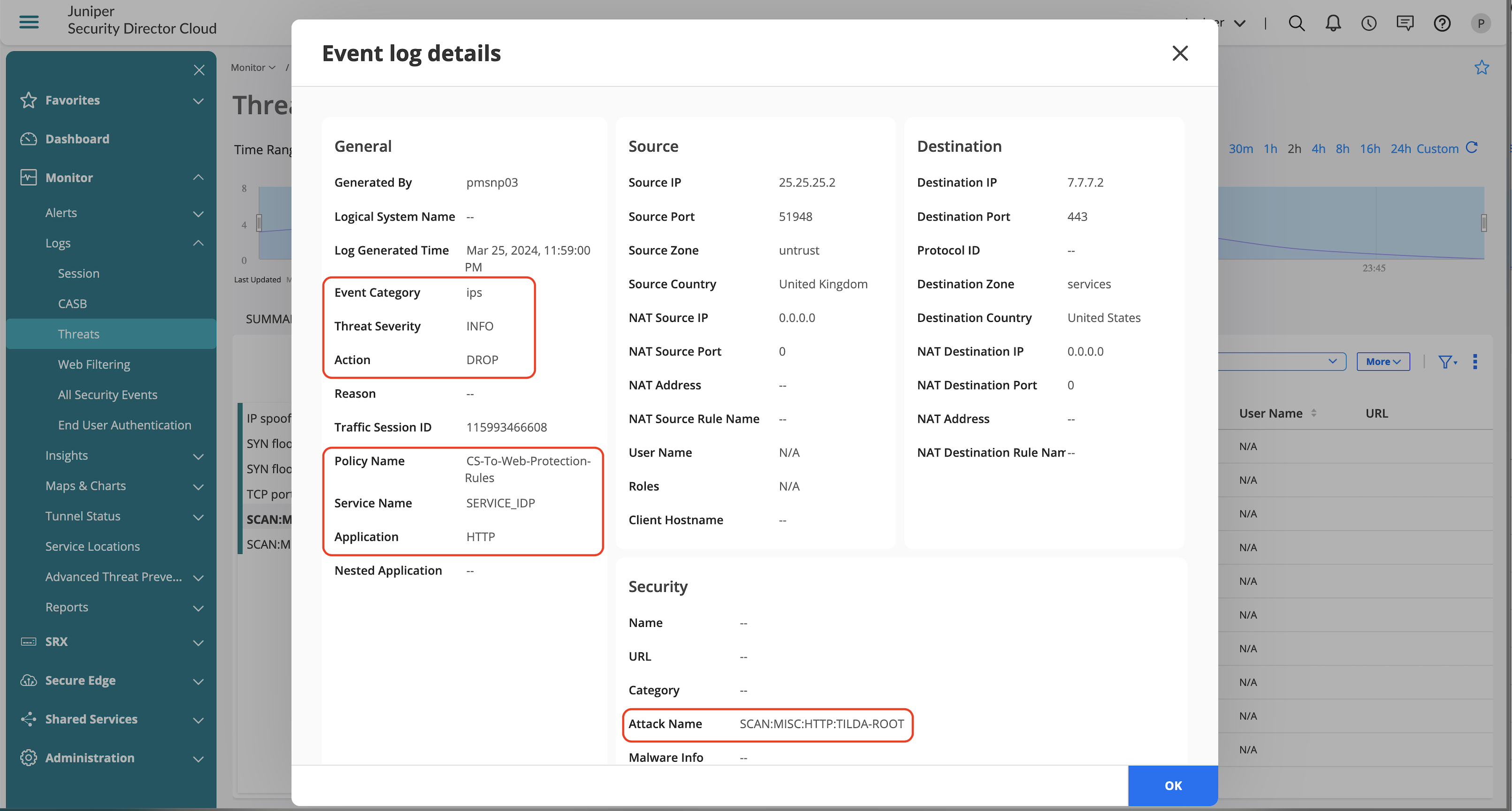
IDP Detailed Information
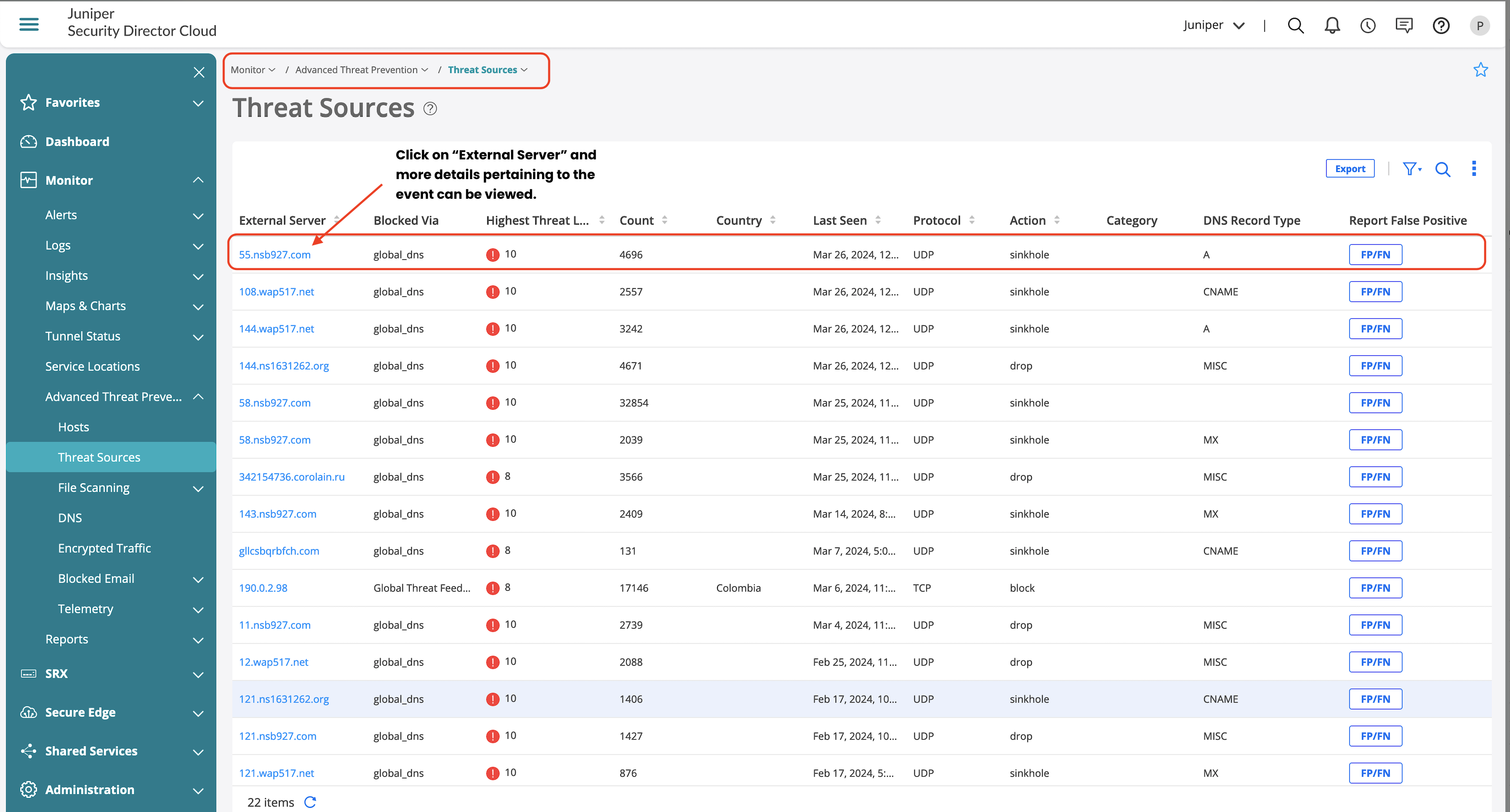
SecIntel Feature Validation
SecIntel feeds applied on the firewall policy generates logs when the traffic matches the configured risk level.
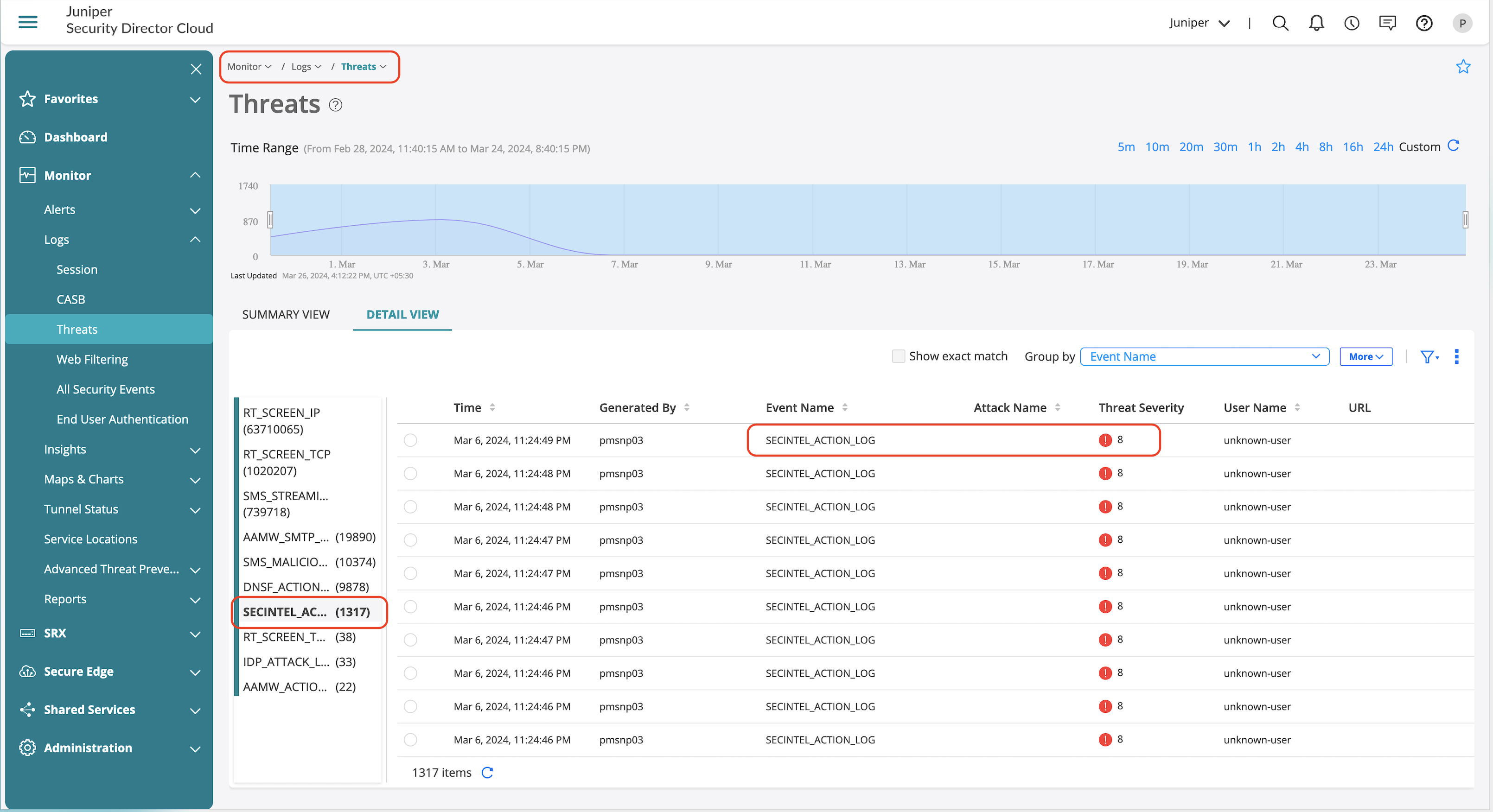
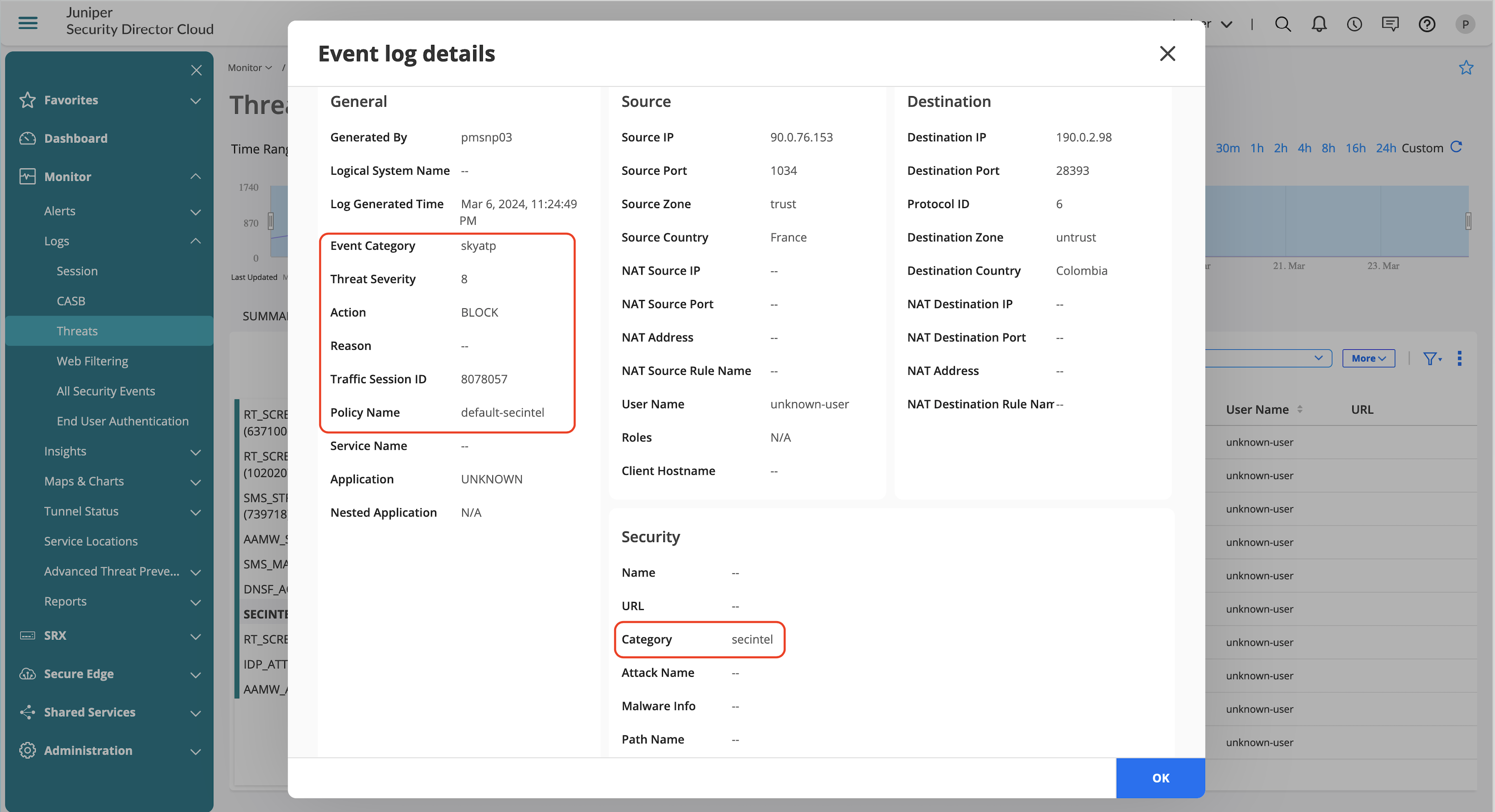
Detailed view shows information on the category and SecIntel policy that enforced the action including the source, destination, and corresponding zones.
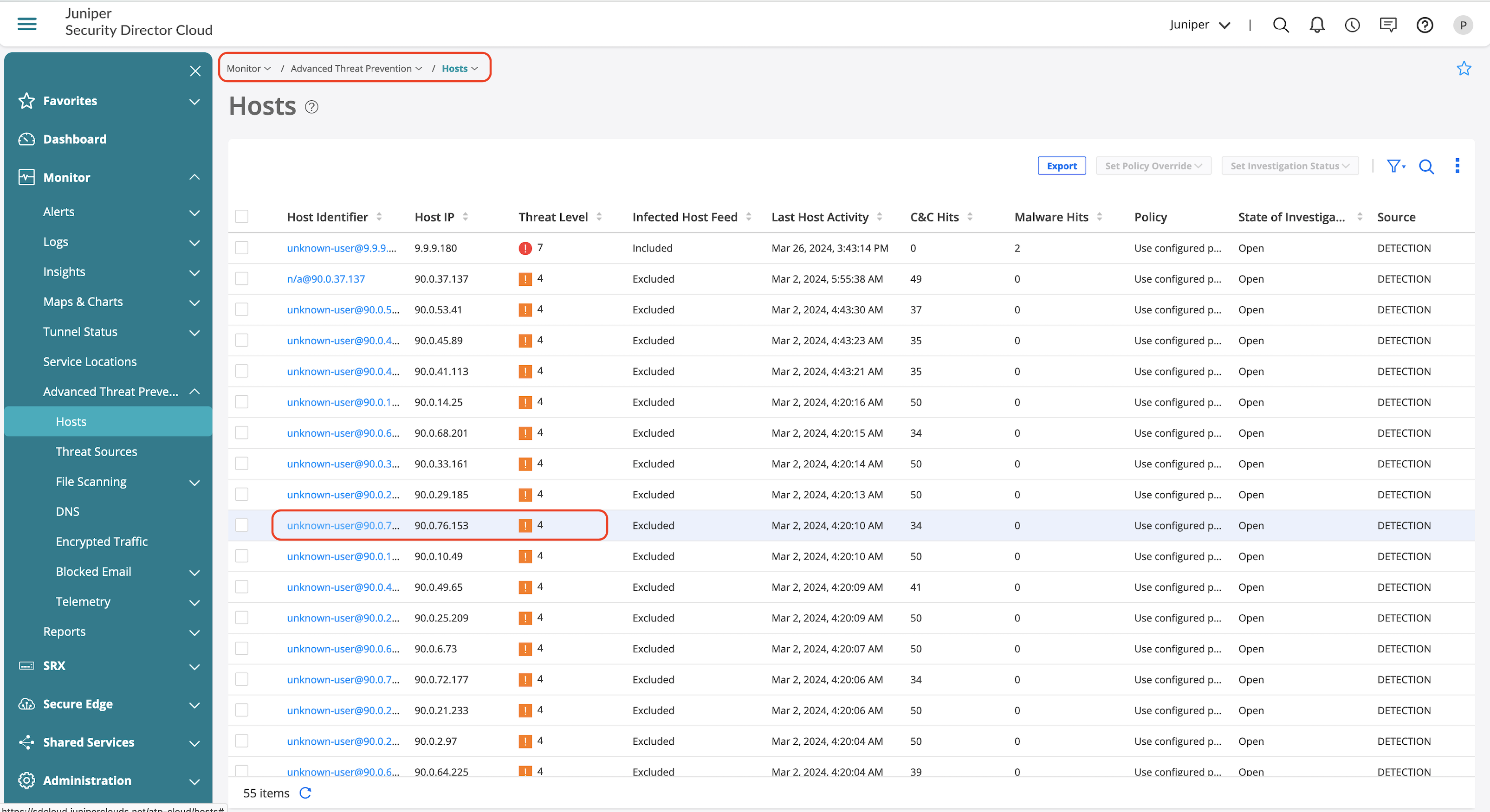
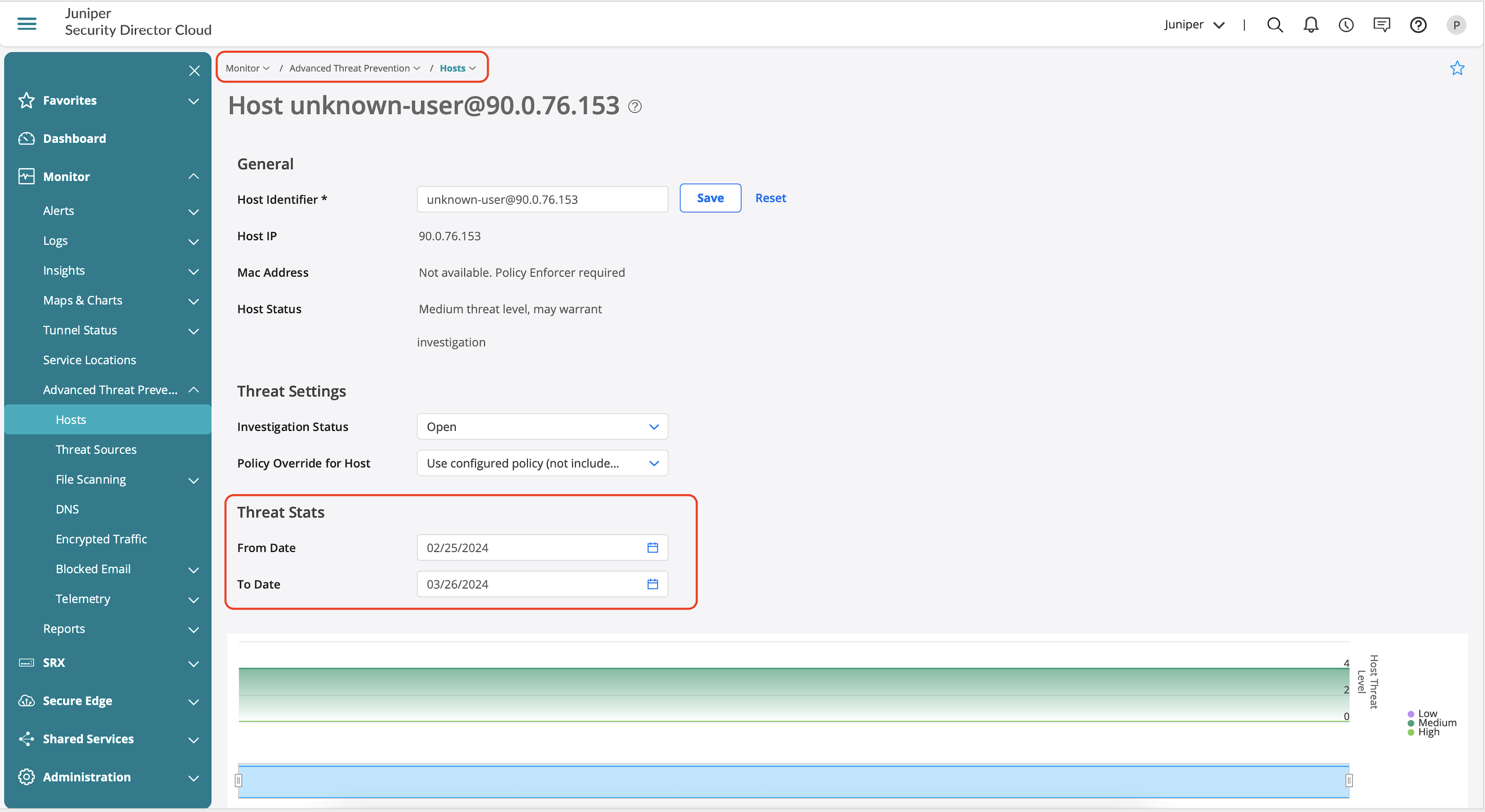
Advanced Threat Prevention dashboard also provides details on the client that initiated the traffic and the history of when the event occurred.
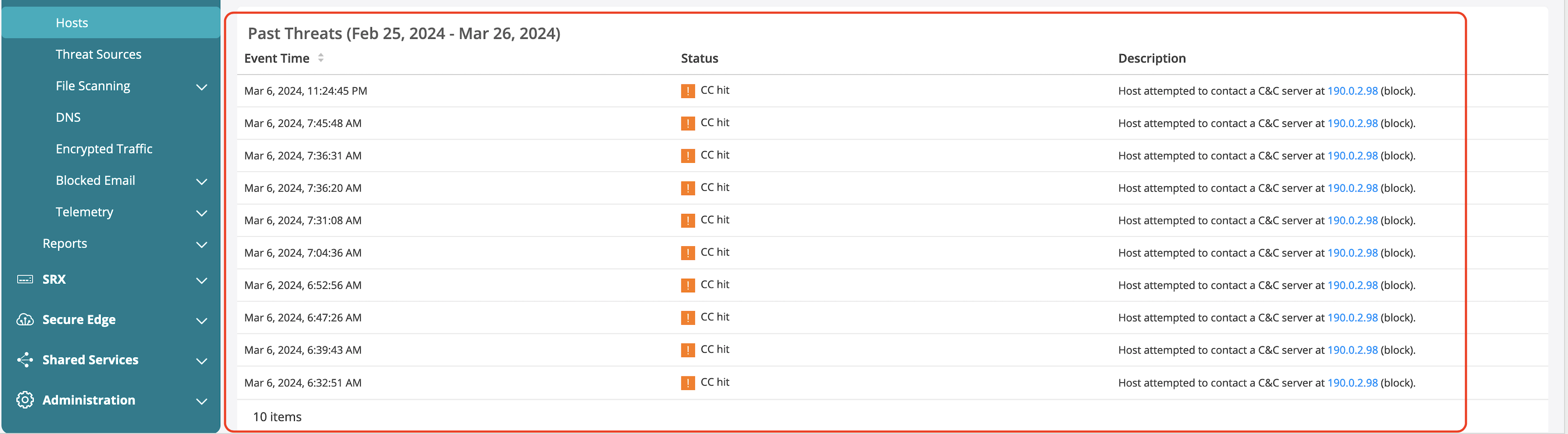
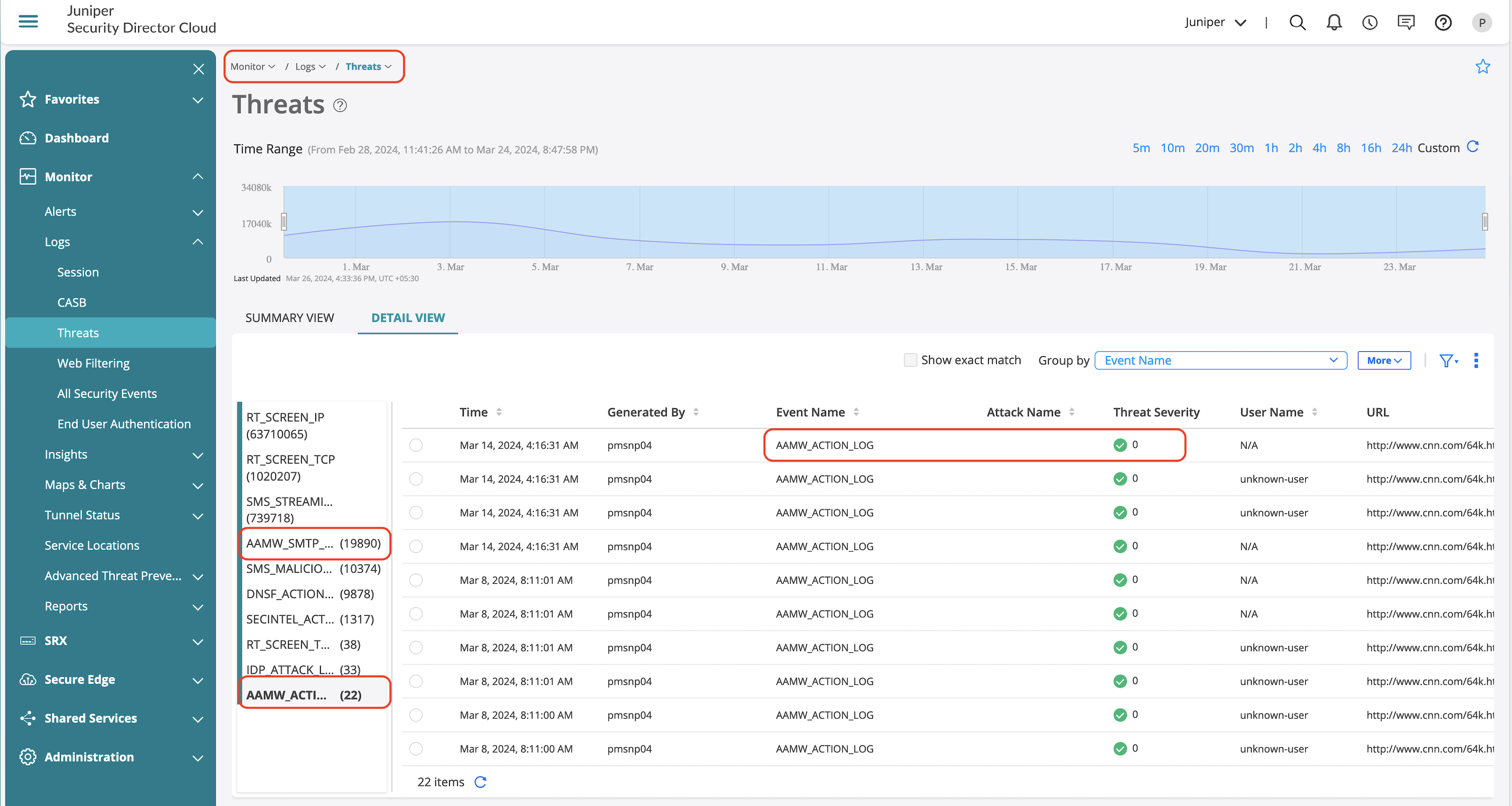
Advanced Anti-Malware Feature Validation
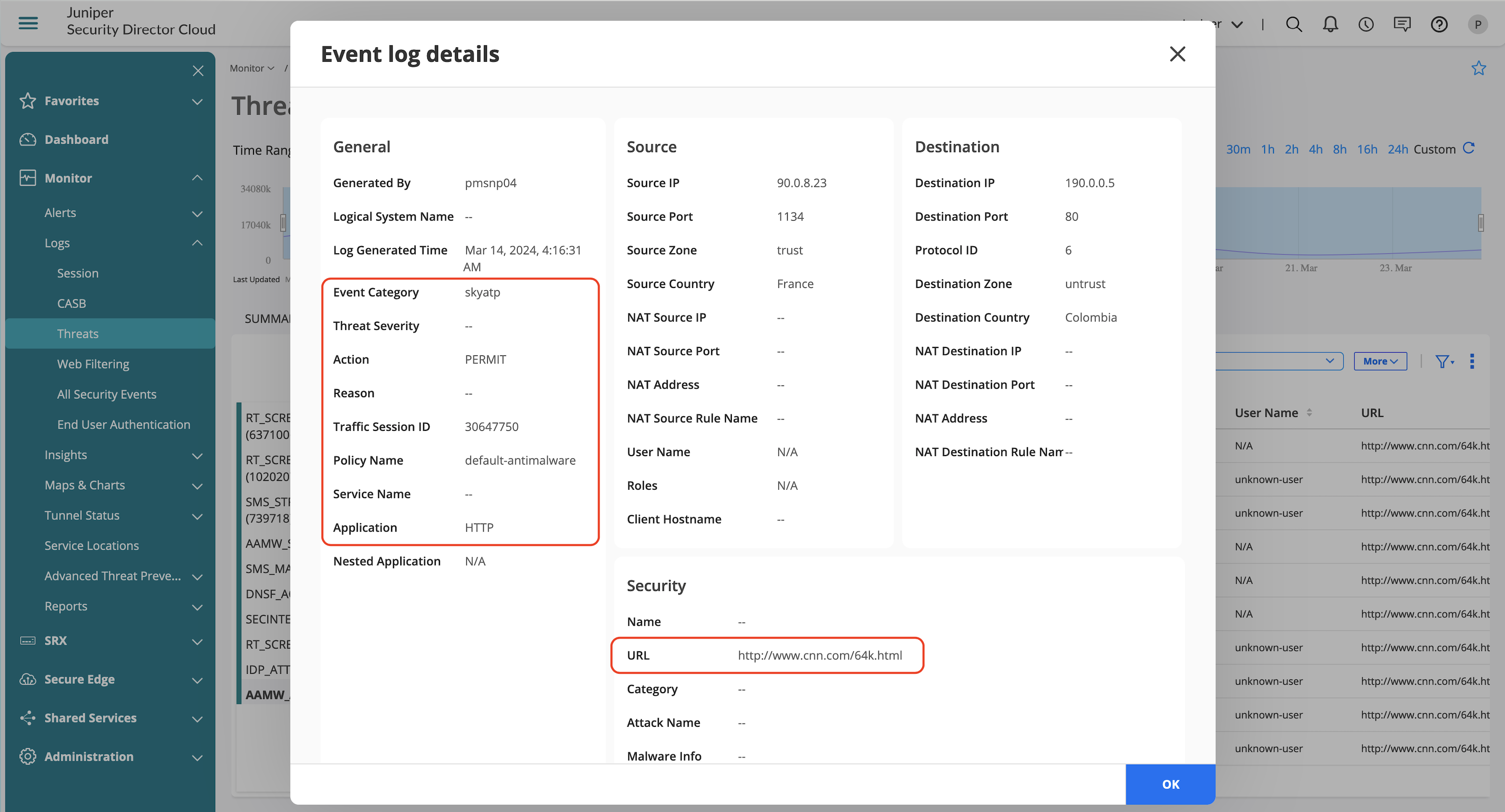
Configured AAMW policy might result in several logs depending on what protocol is identified. Few key logs provide information on the action enforced by AAMW.
| Log Information | Description |
|---|---|
| AAMW_ACTION_LOG | Action taken based on the verdict delivered based on the sandboxing result by Juniper ATP Cloud and defined risk profile on the SRX Series Firewall. |
| AAMW_HOST_INFECTED_EVENT_LOG | If the verdict found is malicious, the host infected event log is generated. |
| AAMW_MALWARE_EVENT_LOG | If the verdict as a result of the sandboxing is malicious, the malware event log is generated. |
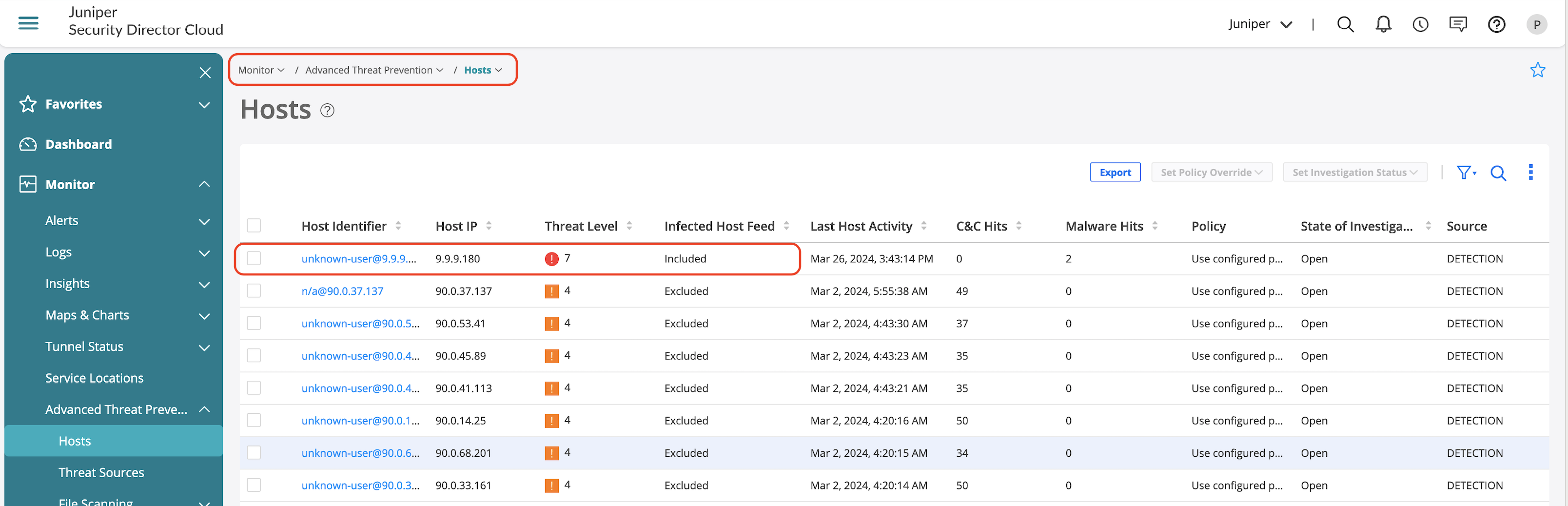
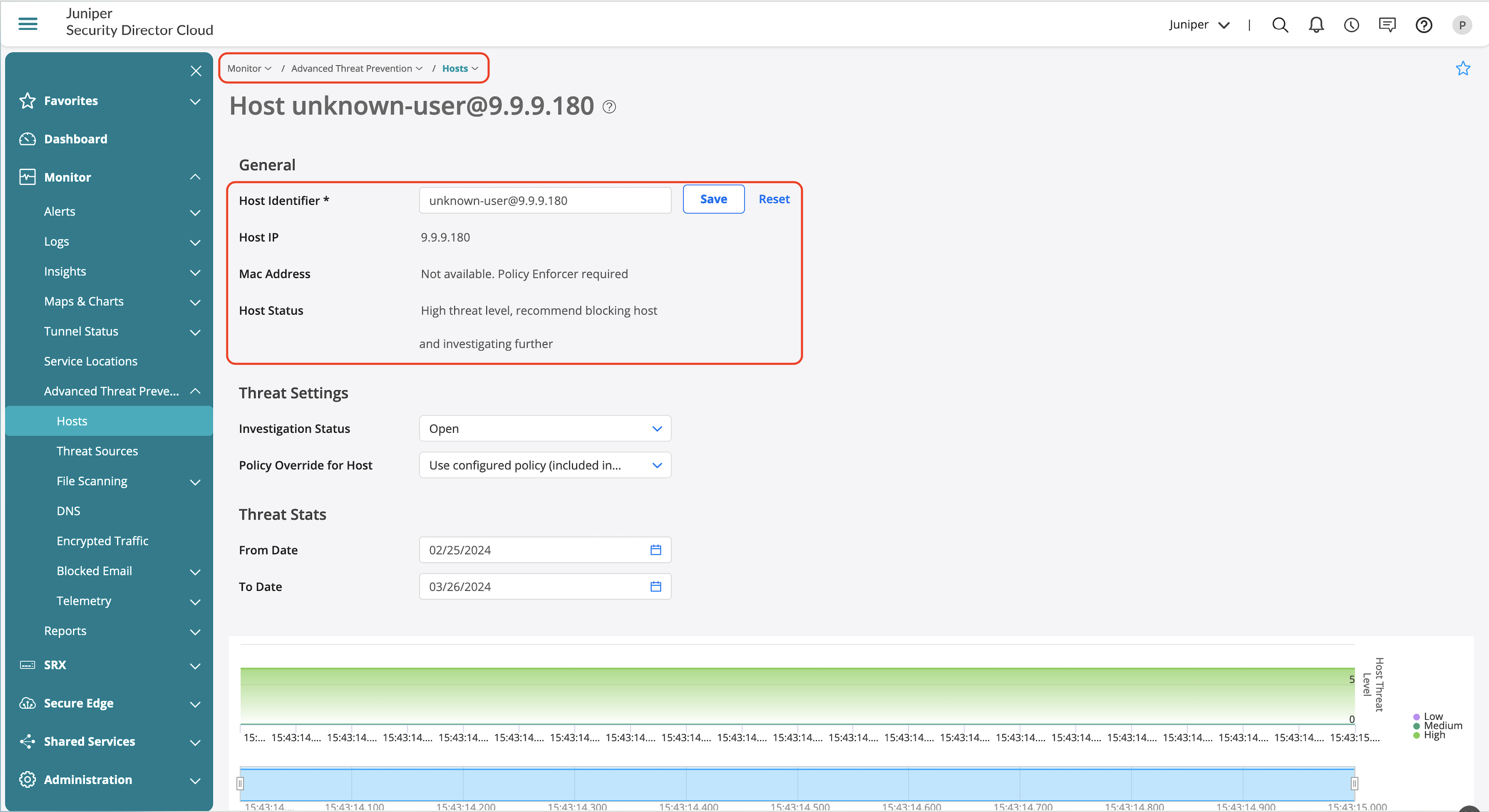
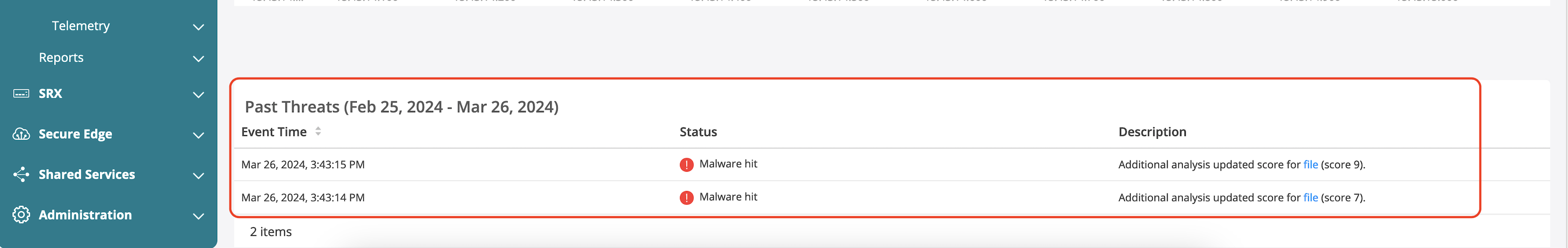
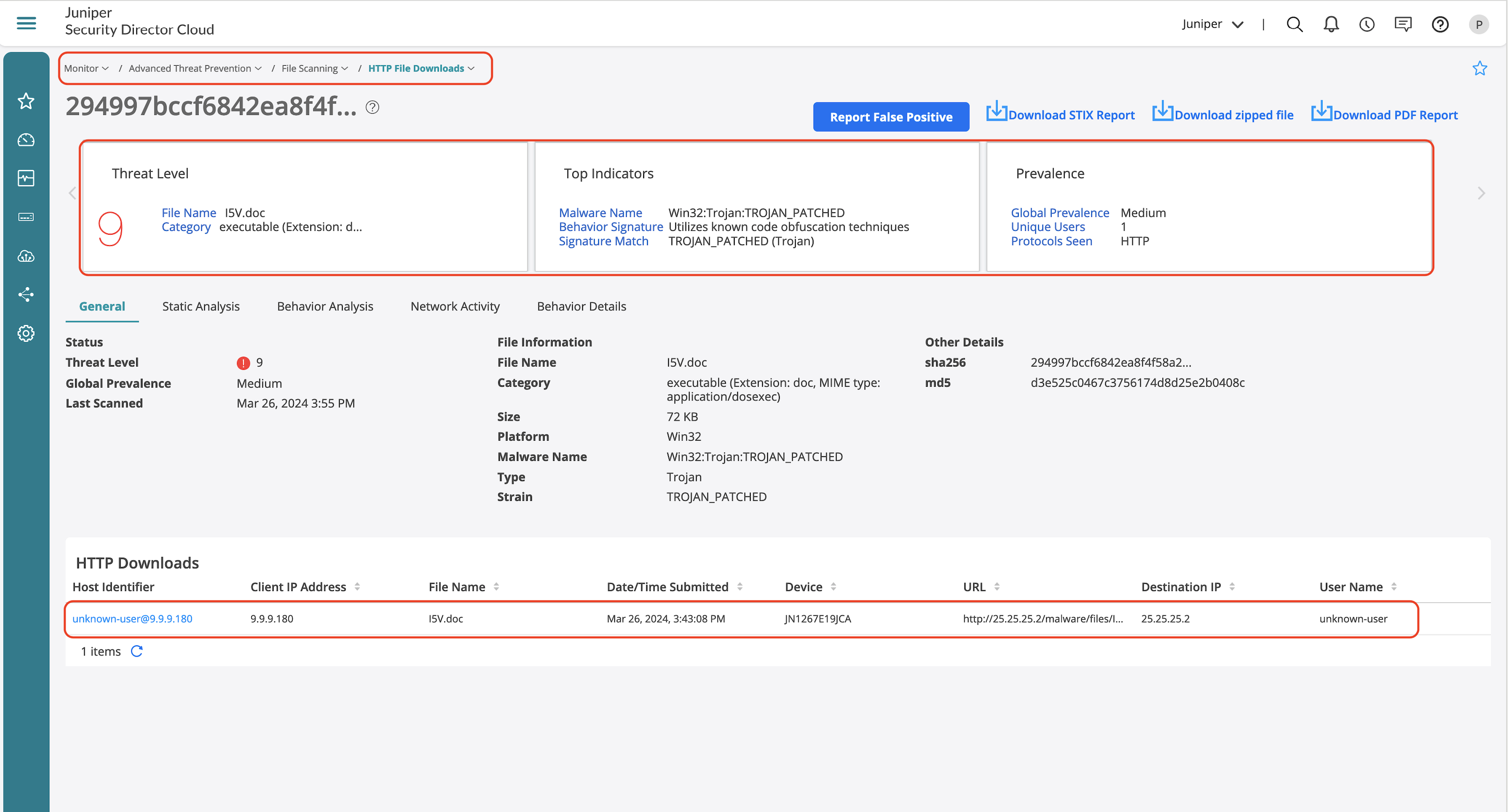
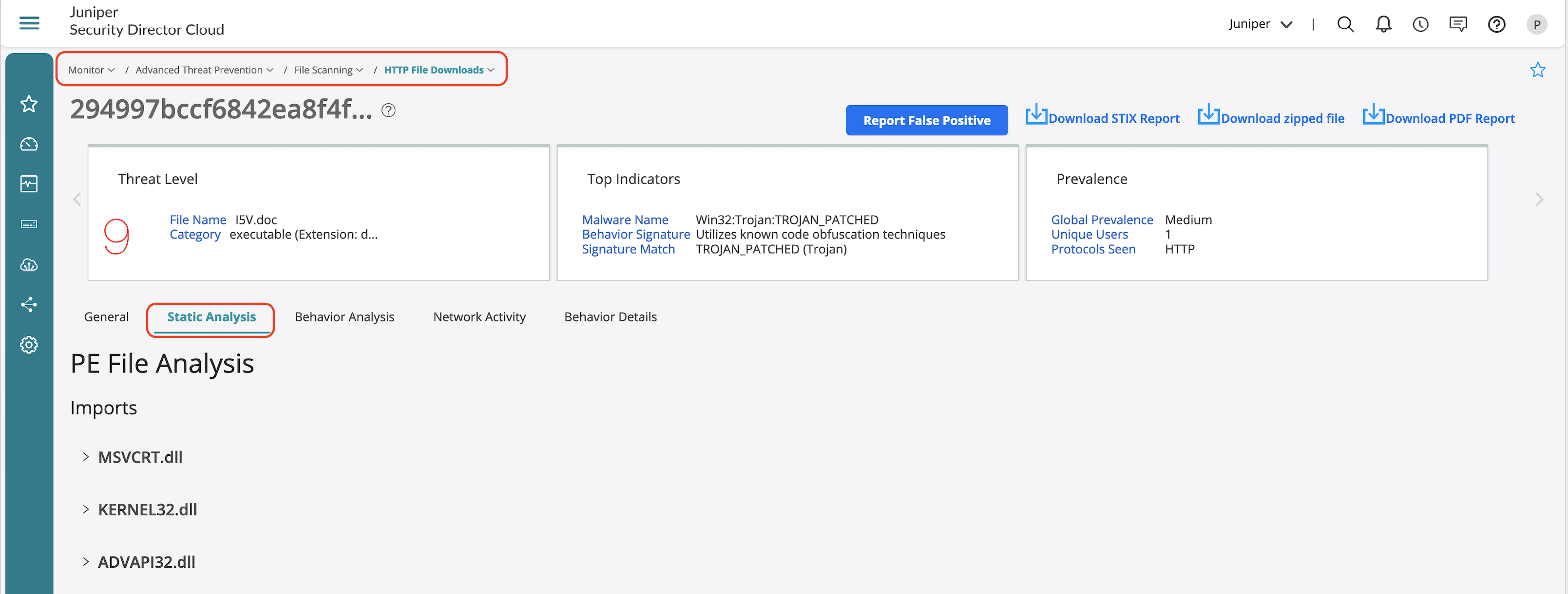
ATP Infected host view provides the following details:
- Indicators of compromise (IOC).
- Static analysis of the identified malicious file.
- Behavior analysis to identify key behaviors based on the assigned threat level to derive how malicious is the identified file.
- Network activity provides details on the malware activity identified during sandboxing.
- Behavior details outline the behavioural steps identified during sandboxing.
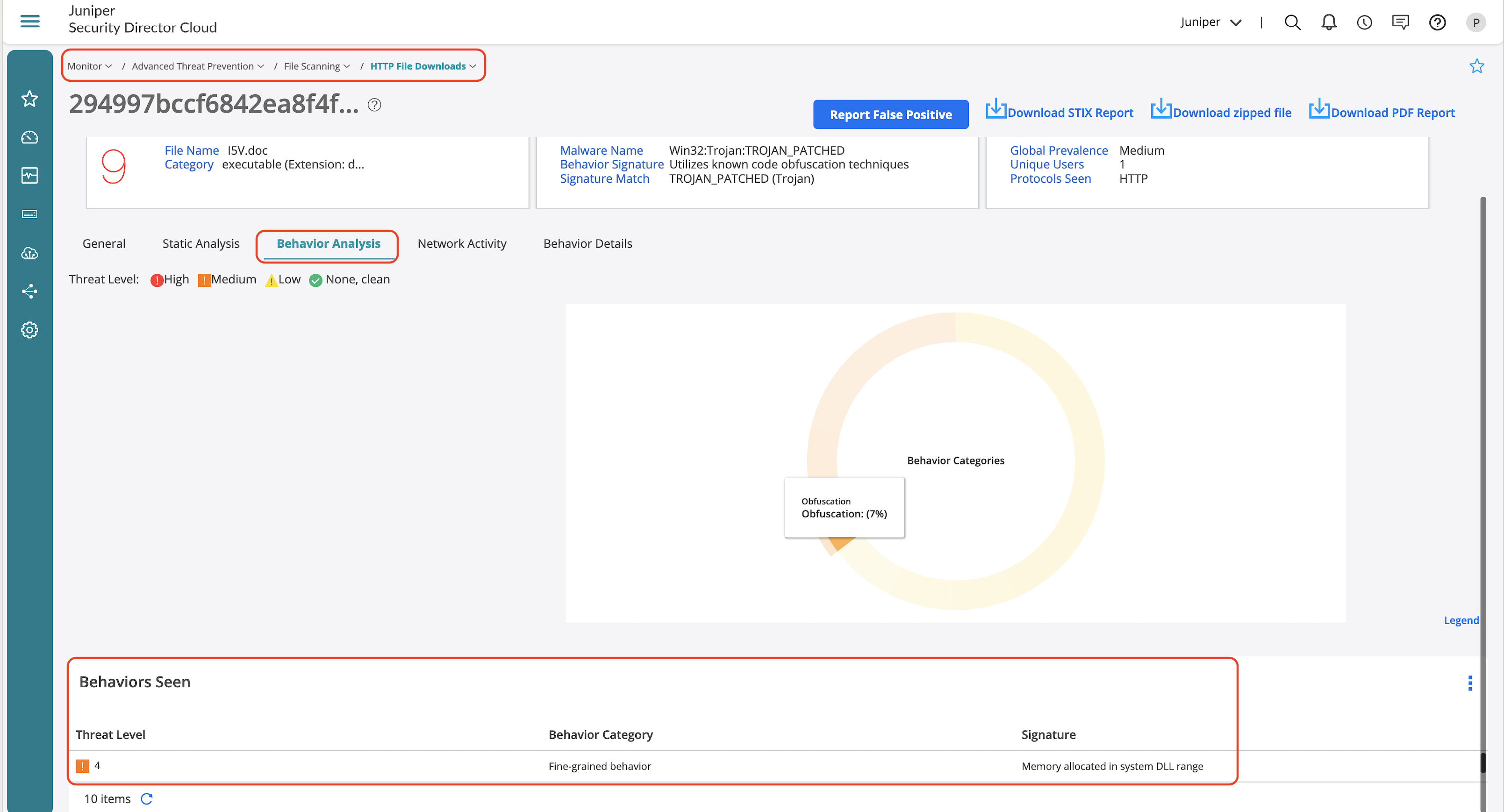
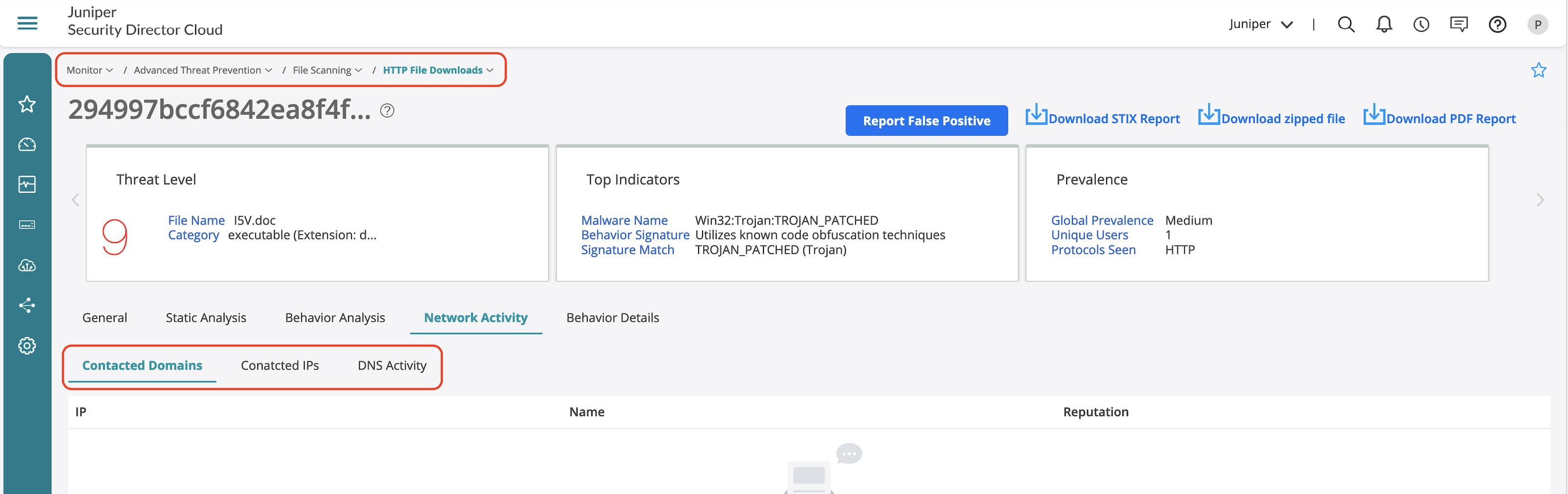
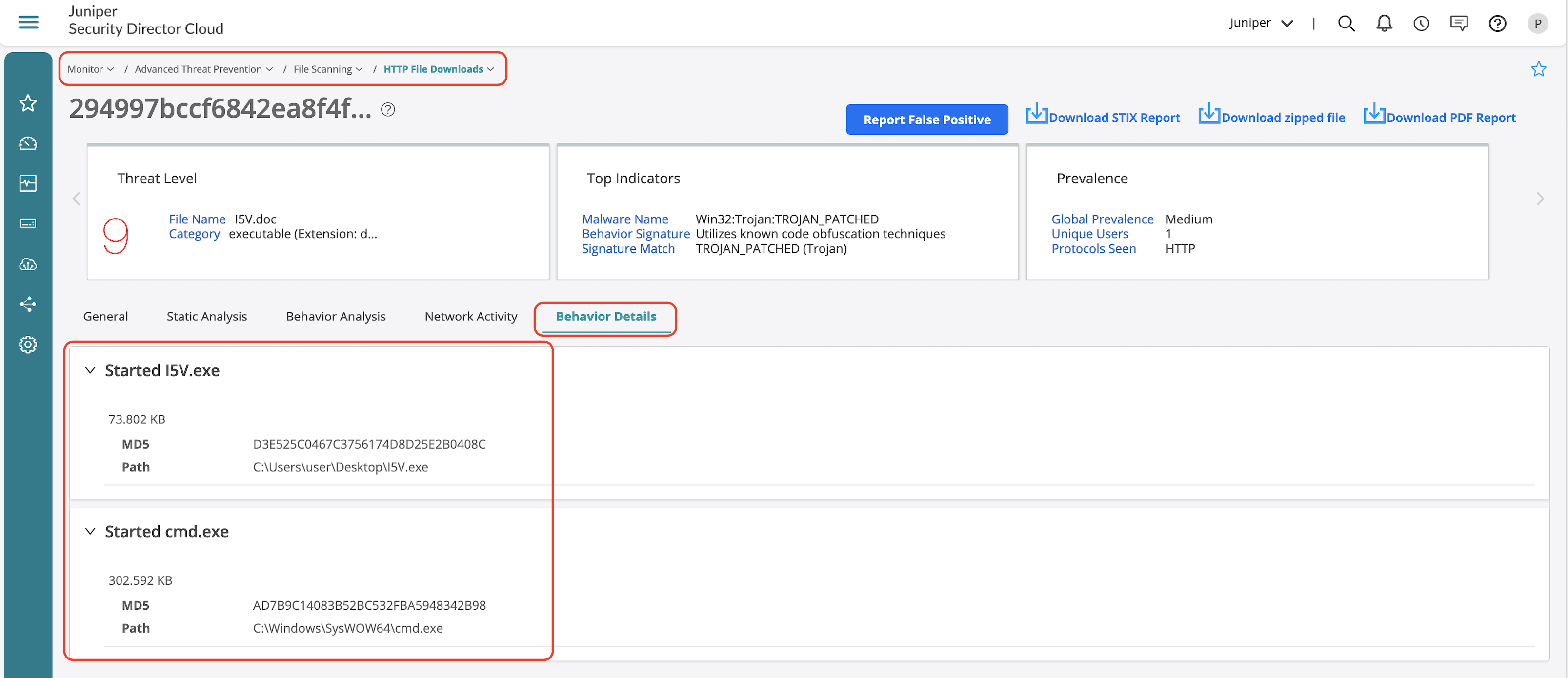
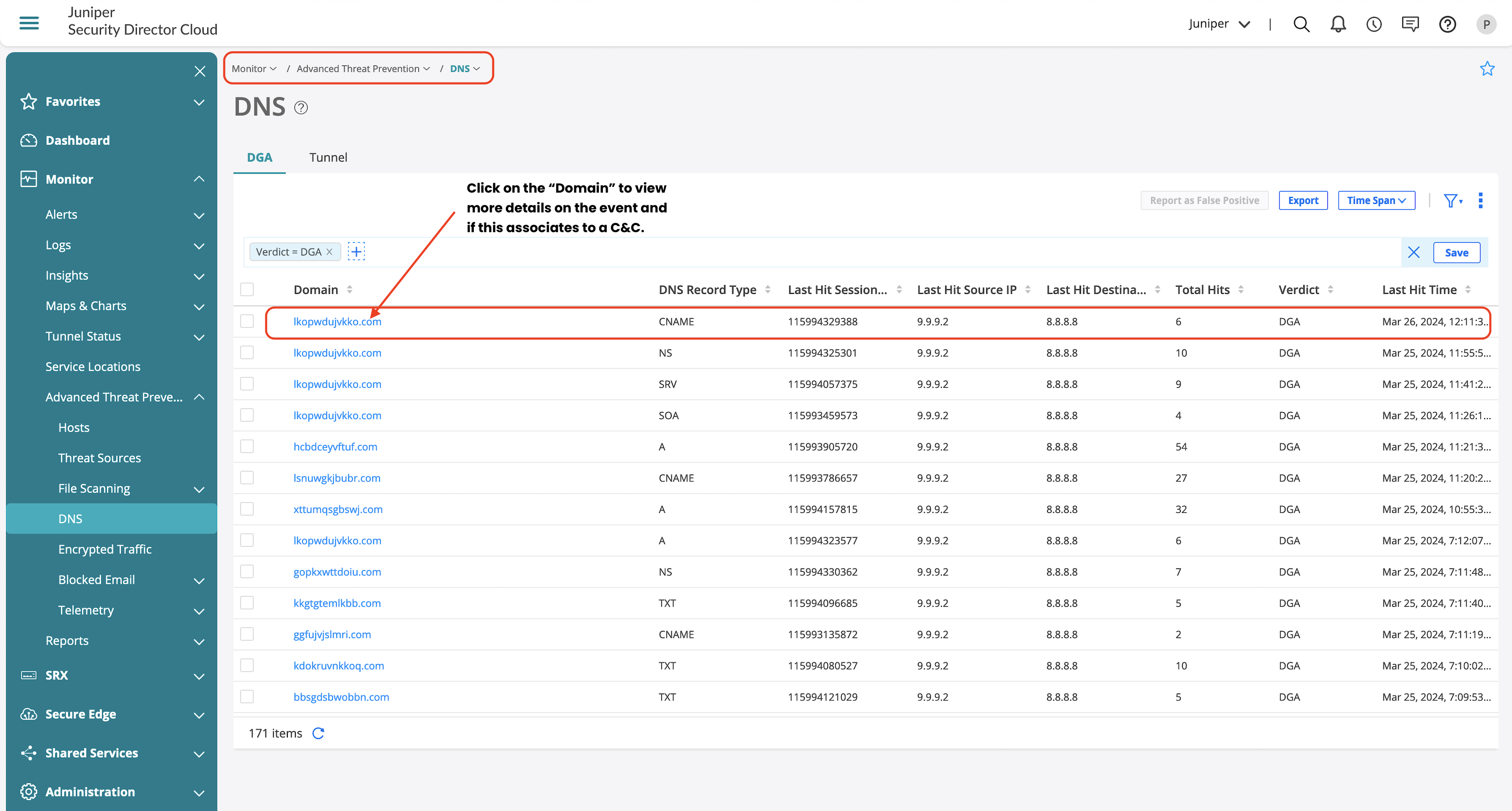
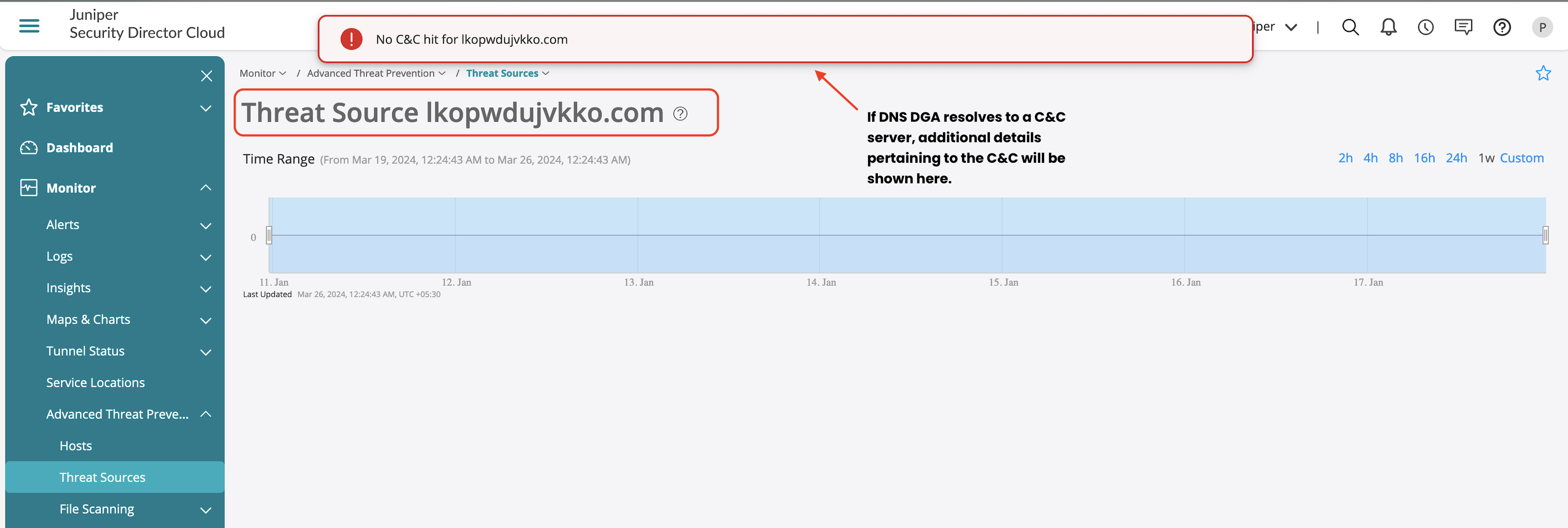
DNS Security Feature Validation
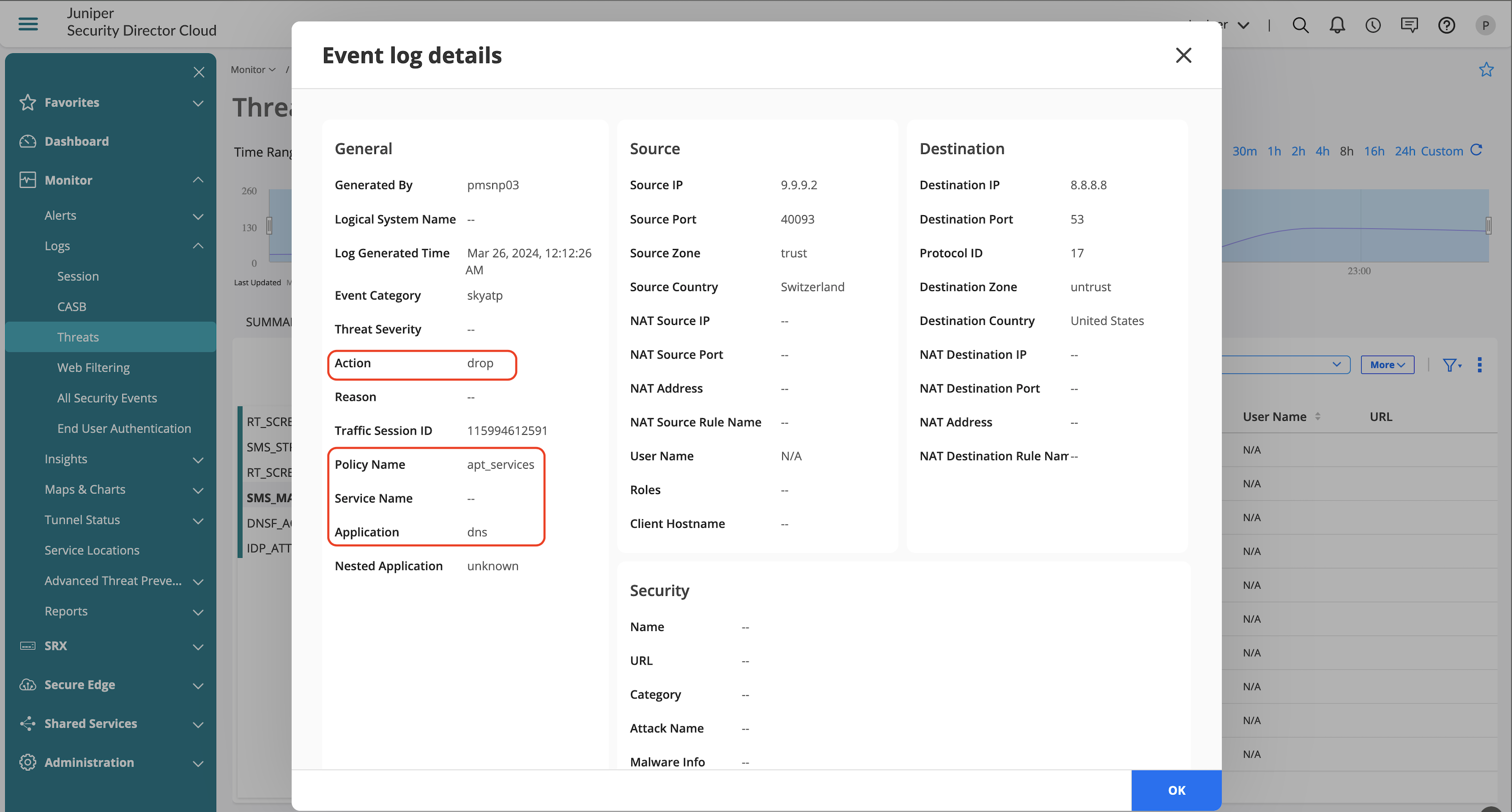
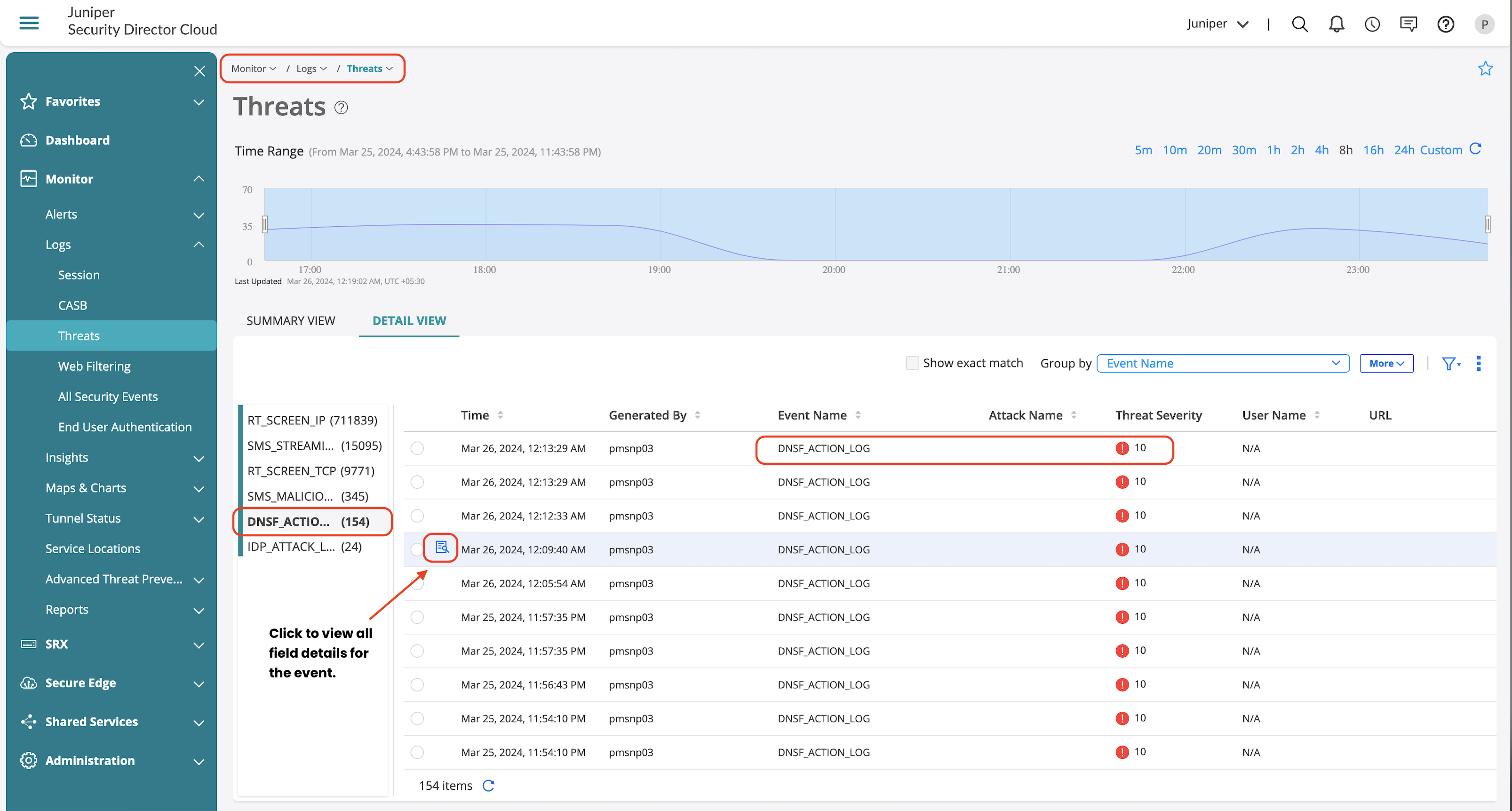
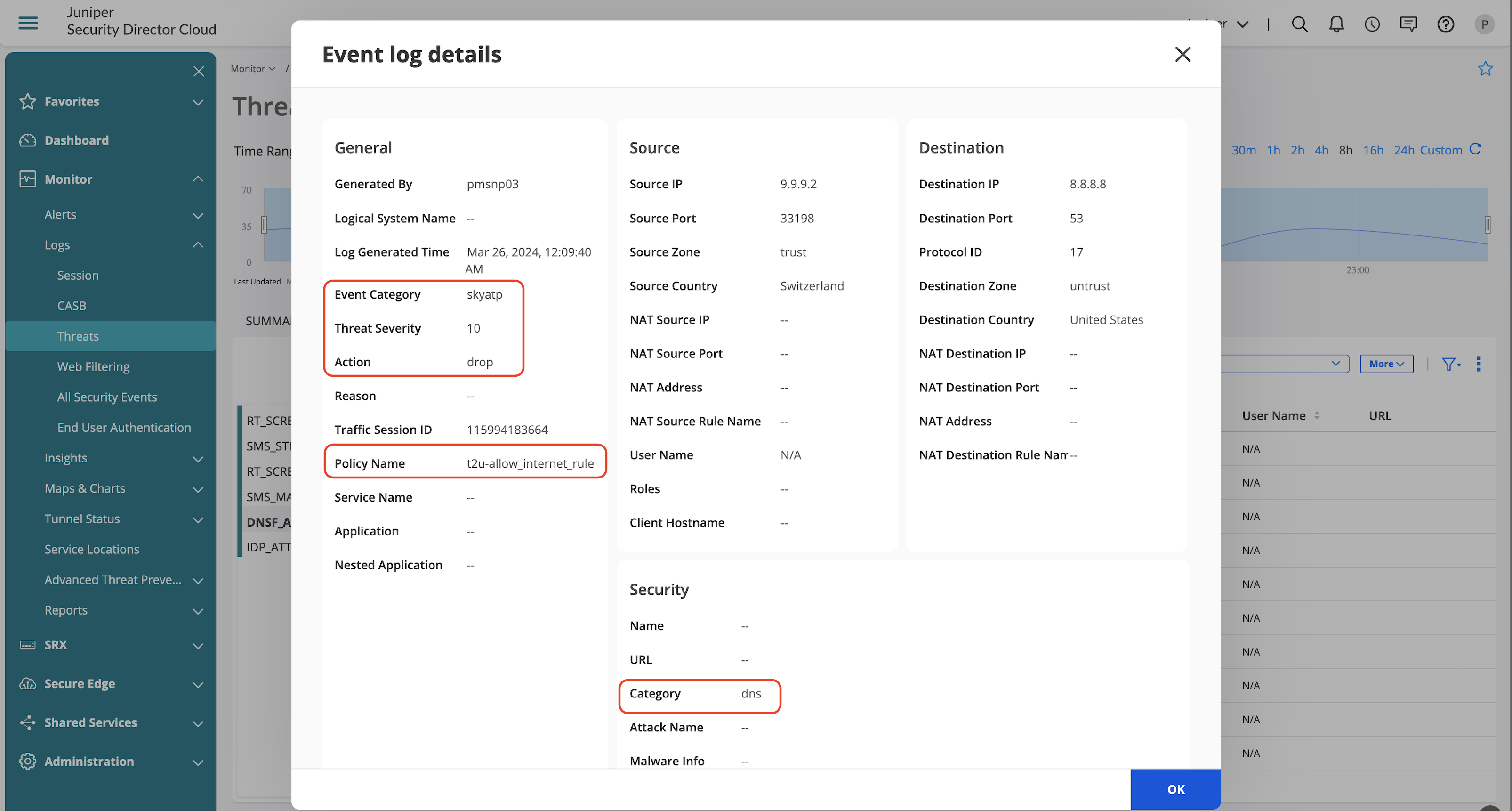
DNS security logs are generated based on each DNS security features such as DGA and DNS tunneling, if any identified DNS traffic is found to be malicious appropriate logs are generated.
| Log Information | Description |
|---|---|
| SMS_STREAMING | Log is generated for DNS REQ when ‘notification log’ is configured under any detections (dga, tunneling, and all). |
| SMS_CLEAN_VERDICT | Log is generated when the cloud verdict is ‘clean’ and ‘notification log-detection’ is configured under any detections (dga and all). |
| SMS_MALICIOUS_VERDICT | Log is generated when the cloud verdict is malicious or tunneling is detected and ‘notification log-detection’ is configured under any detections (dga, tunneling and all). |
| SMS_FALLBACK_EVENT | Log is generated when the cloud verdict is not received in verdict-timeout interval. Log is generated only when ‘fallback-options notification log’ is configured under any detection (dga, tunneling and all). |
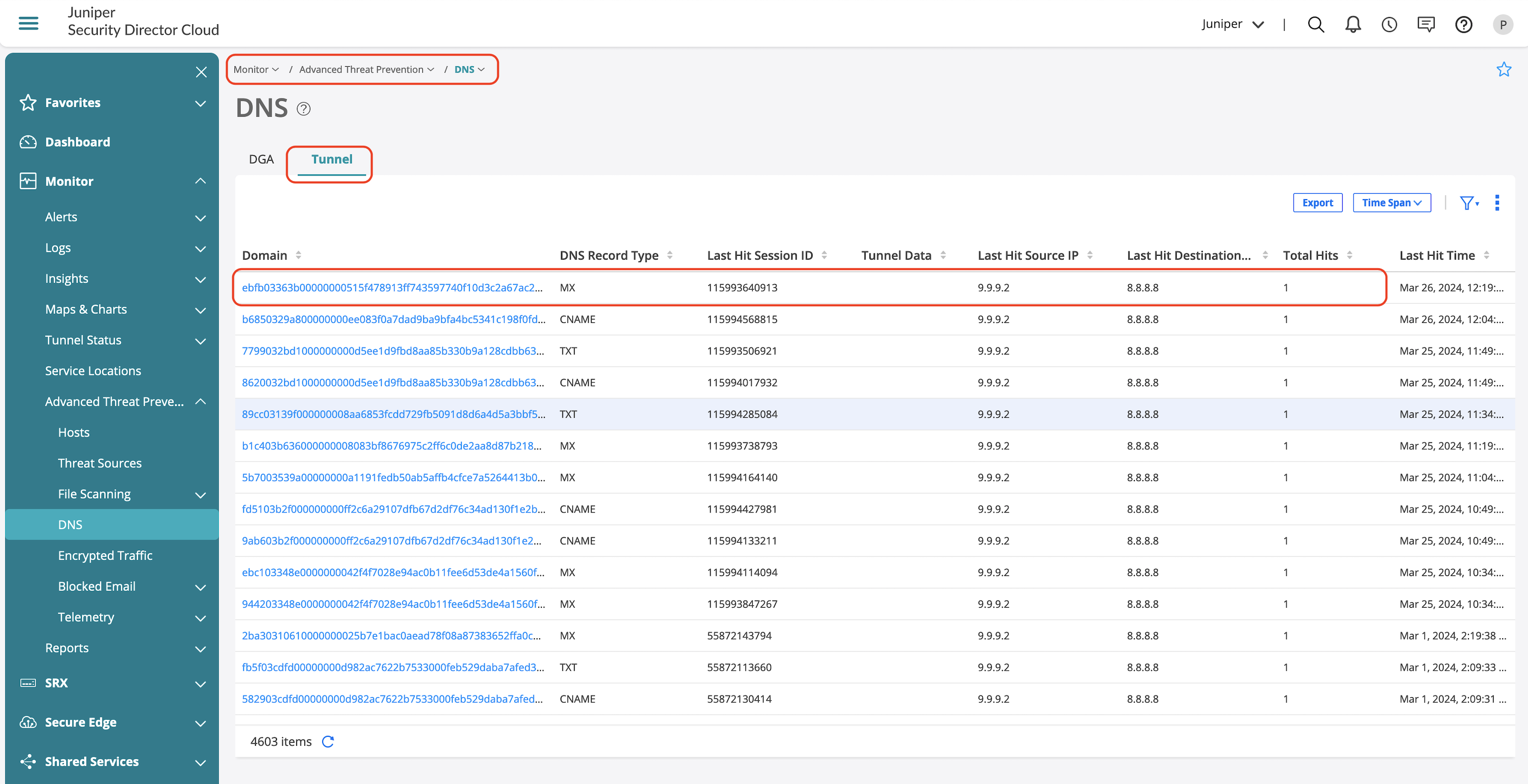
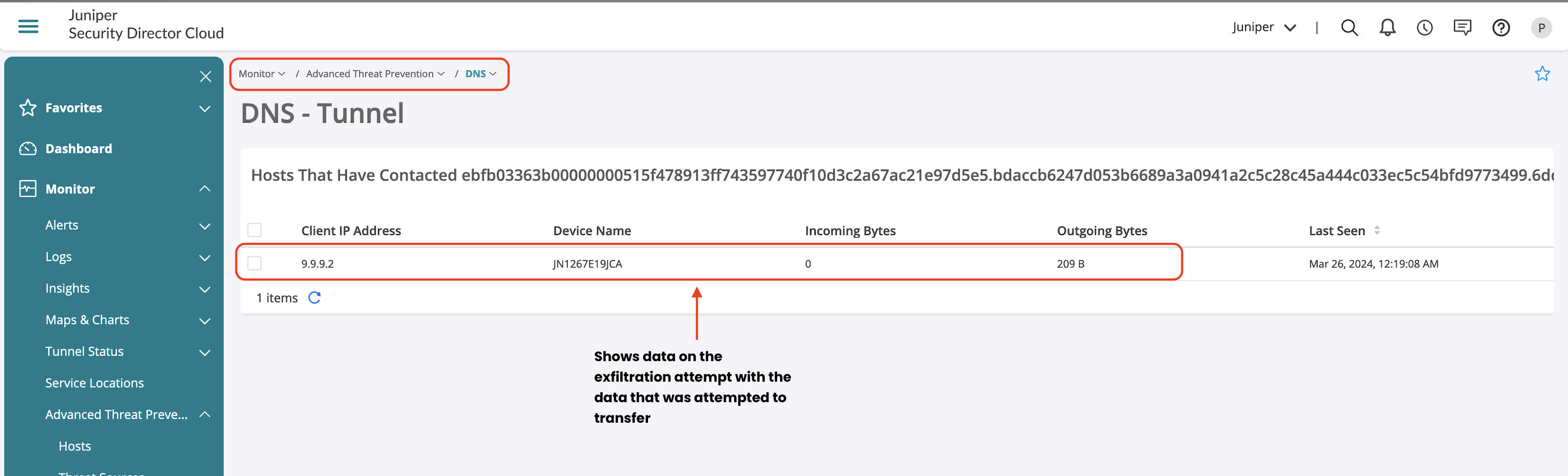
Apart from generated logs, you can also view the offense details from Advanced Threat Prevention section, which provides information on the following:
- Client which generated the offense.
- Offense details if its DGA or DNS Tunneling.
- Information on the IOC and exfiltration attempts.
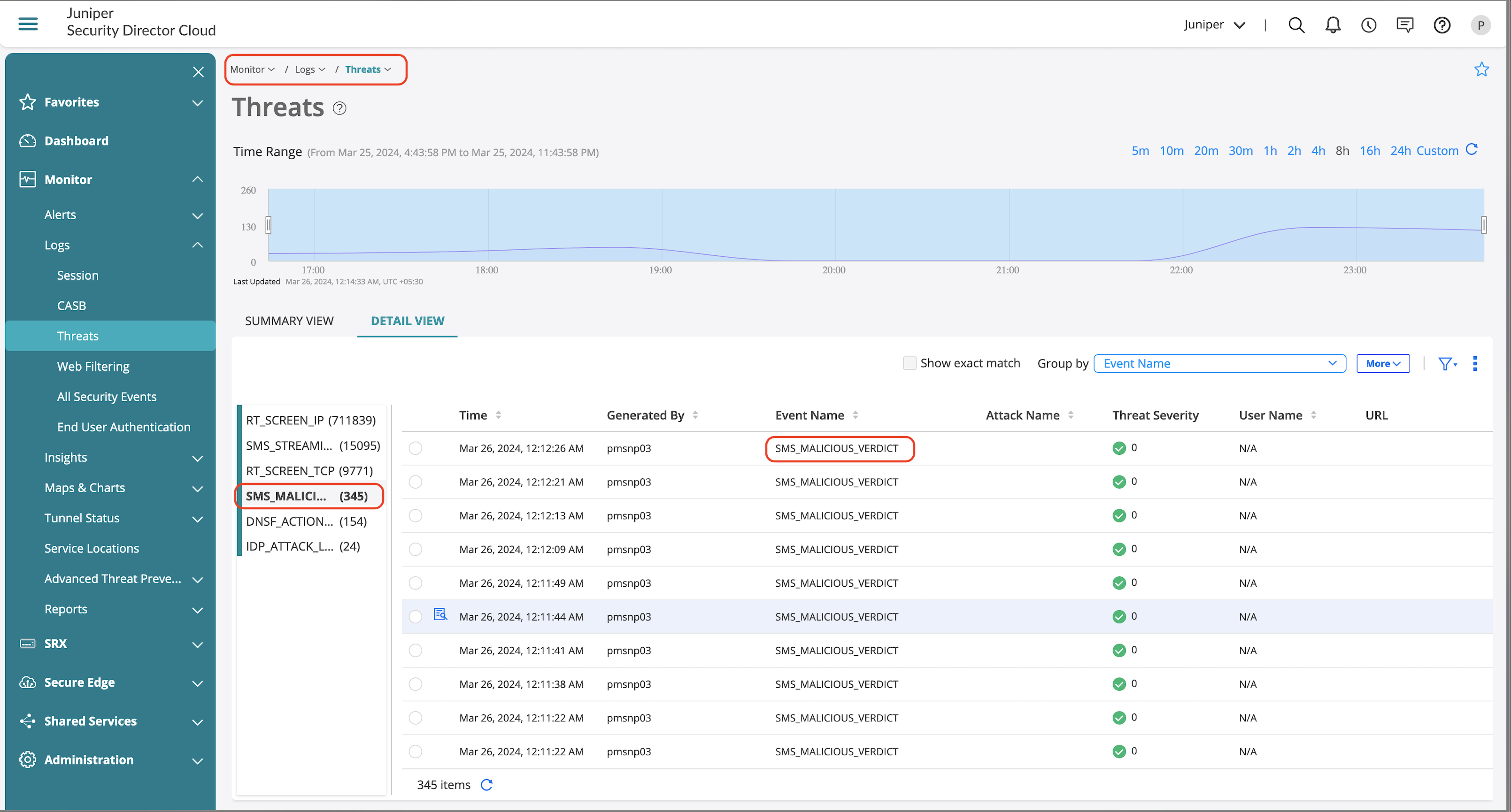
.
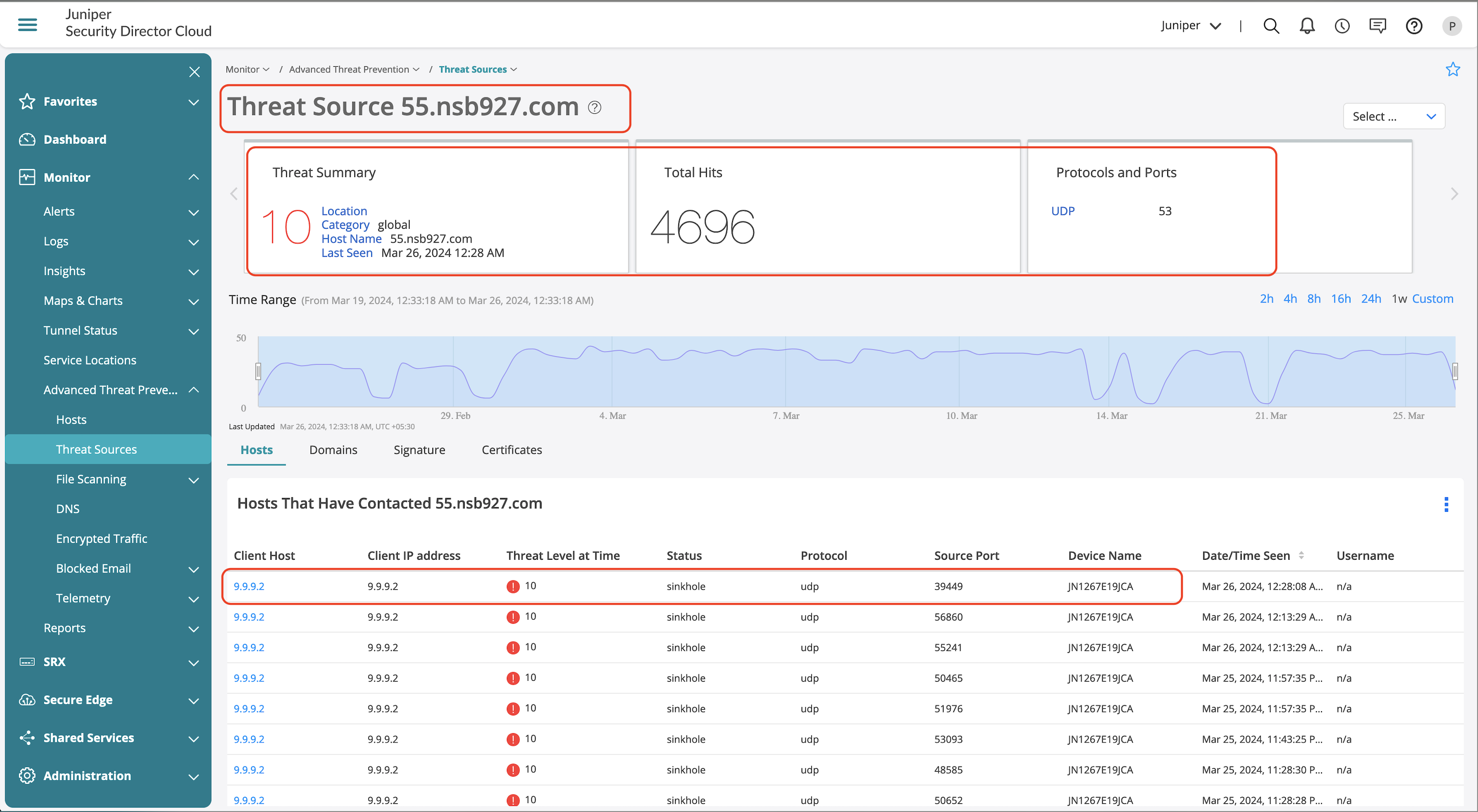
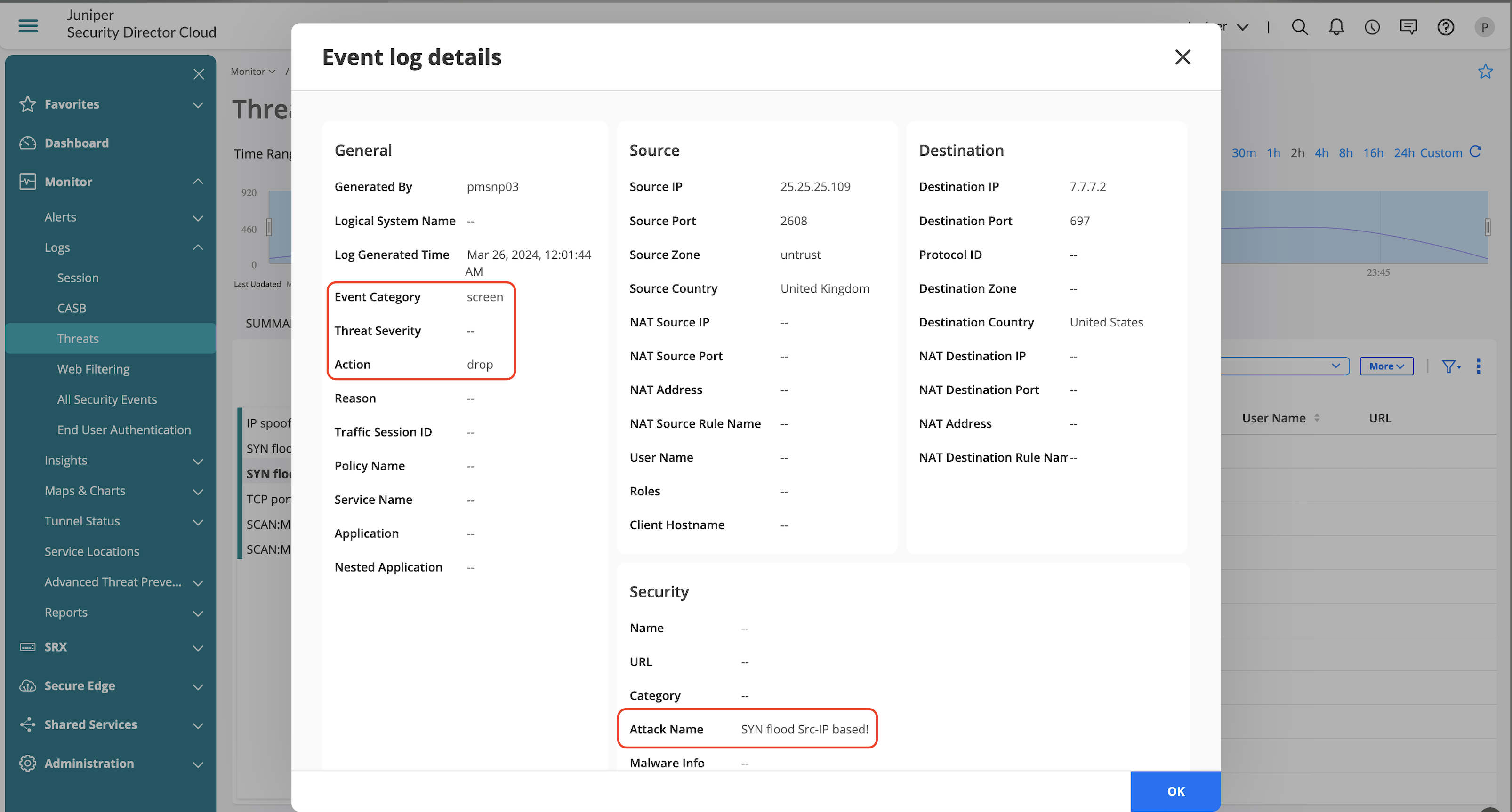
Screens Feature Validation
IP Spoofing
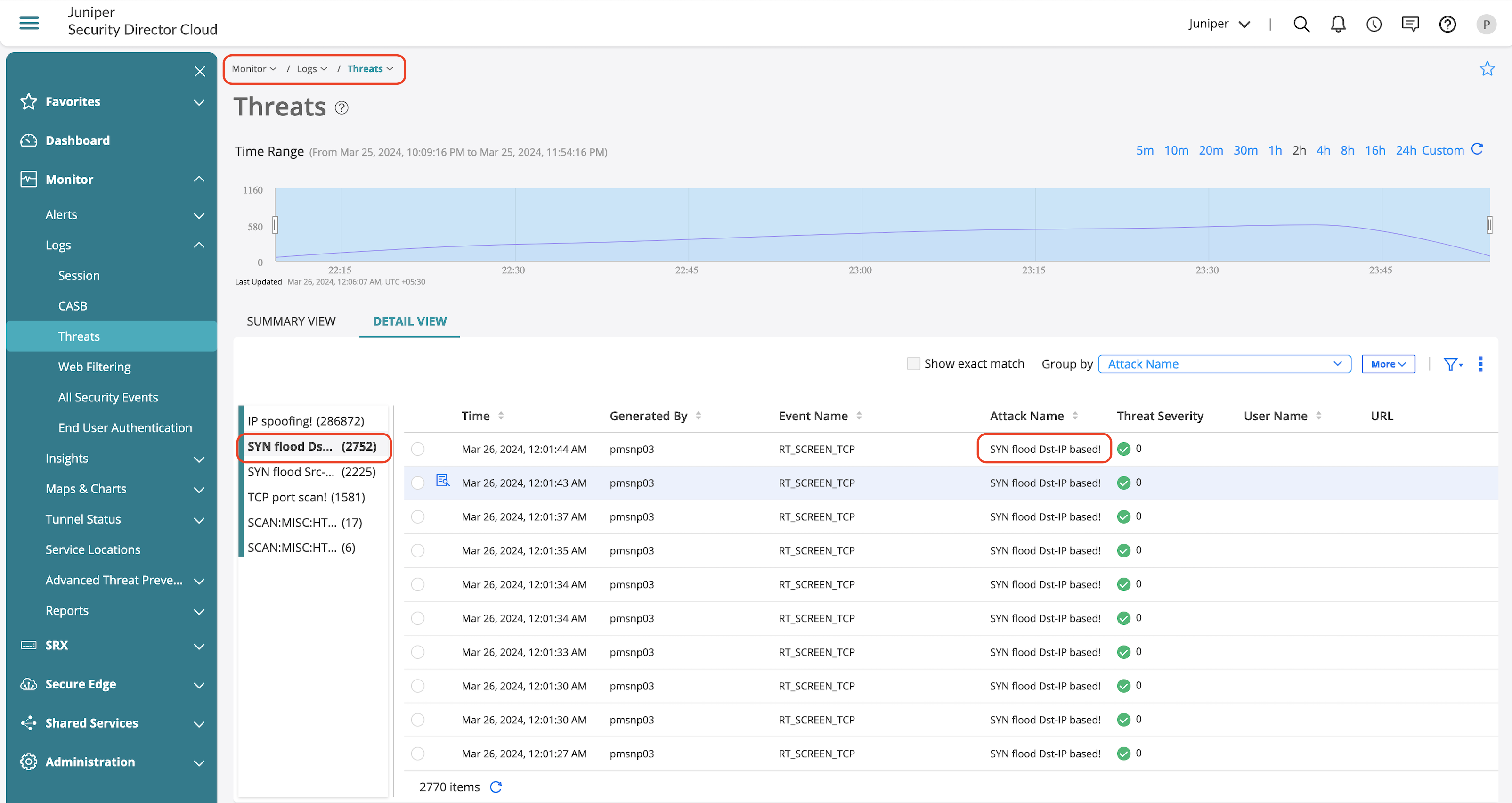
SYN Flood—(Apply Source and Destination Limits)
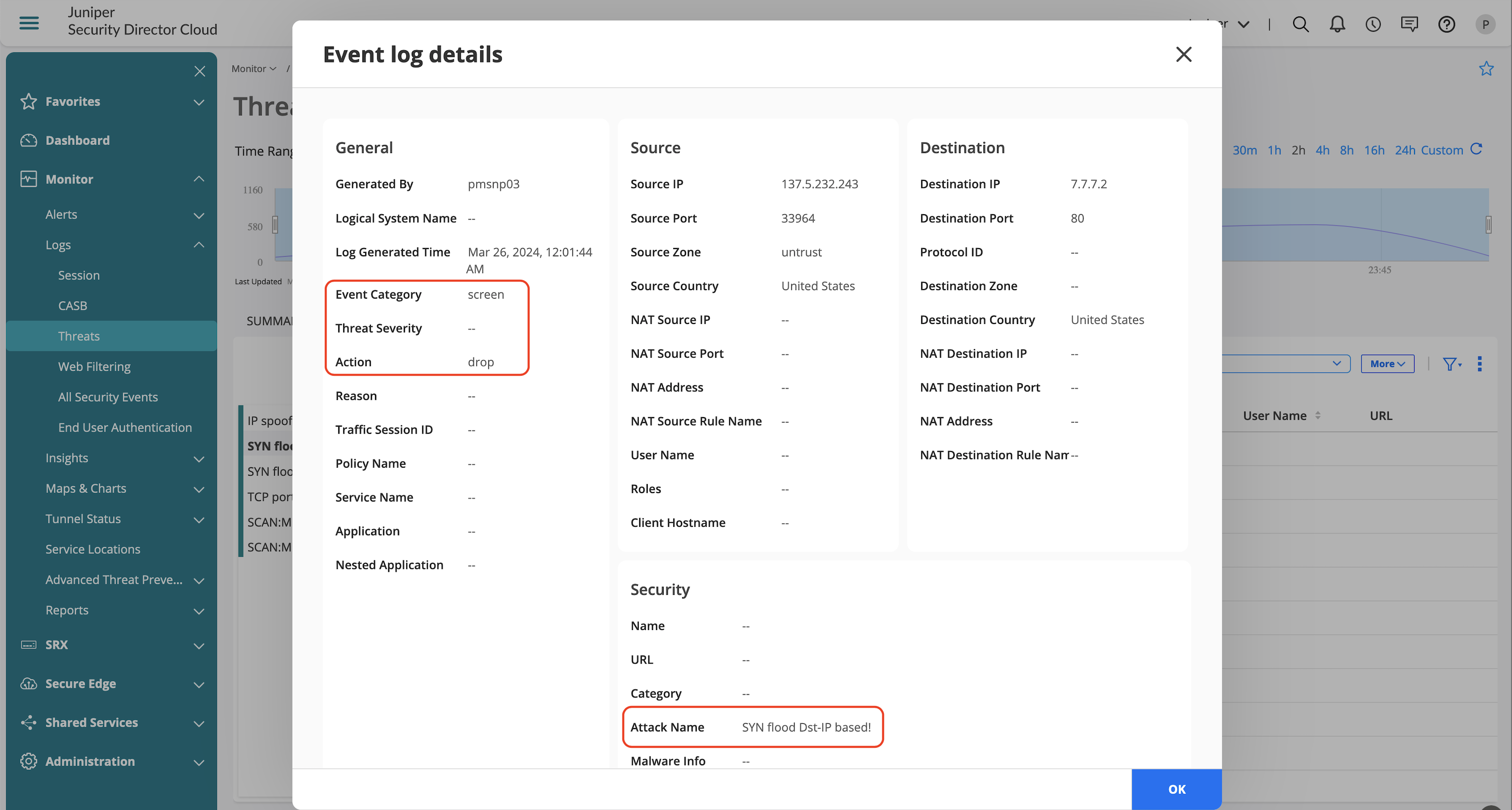
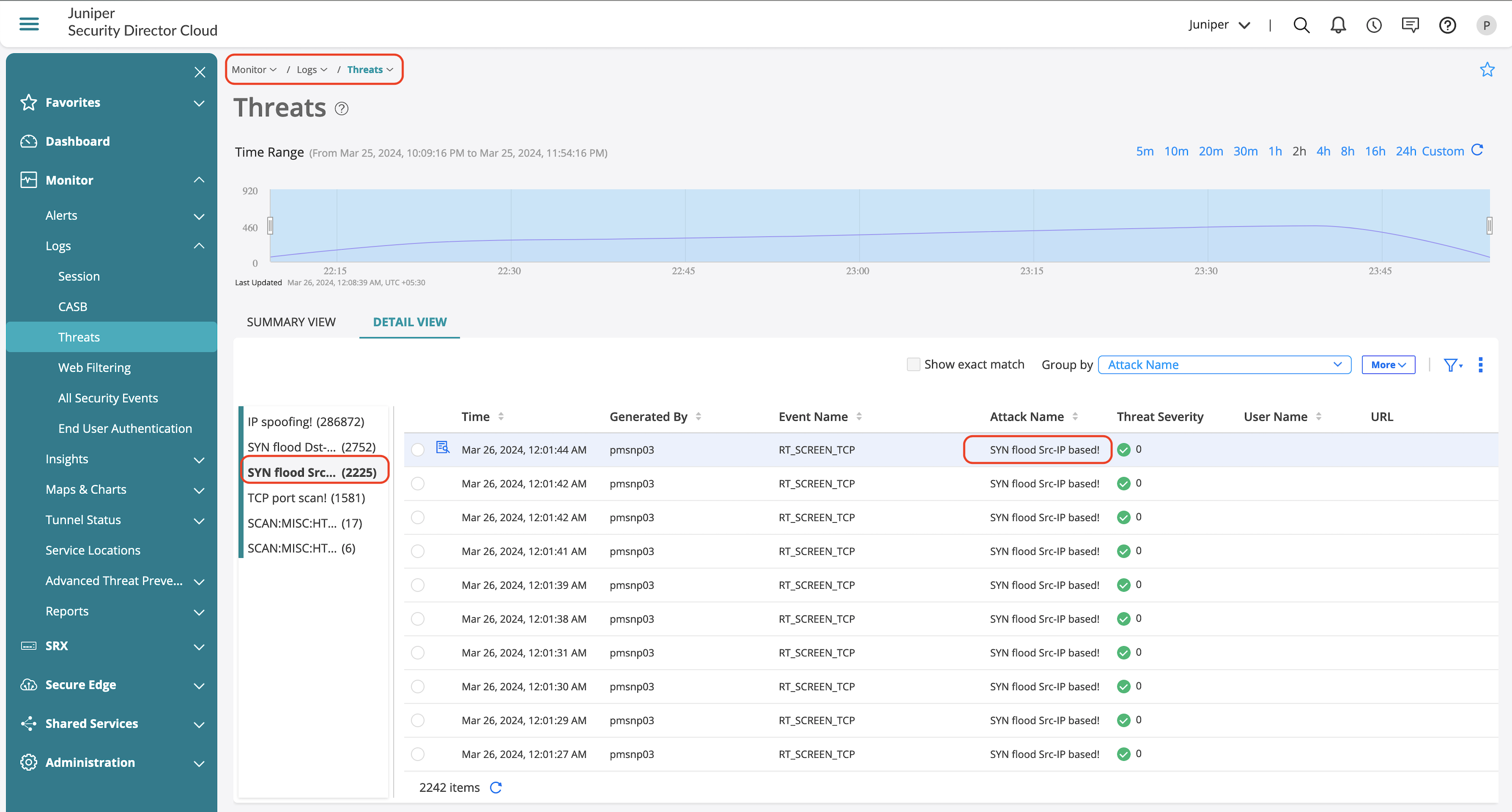
.
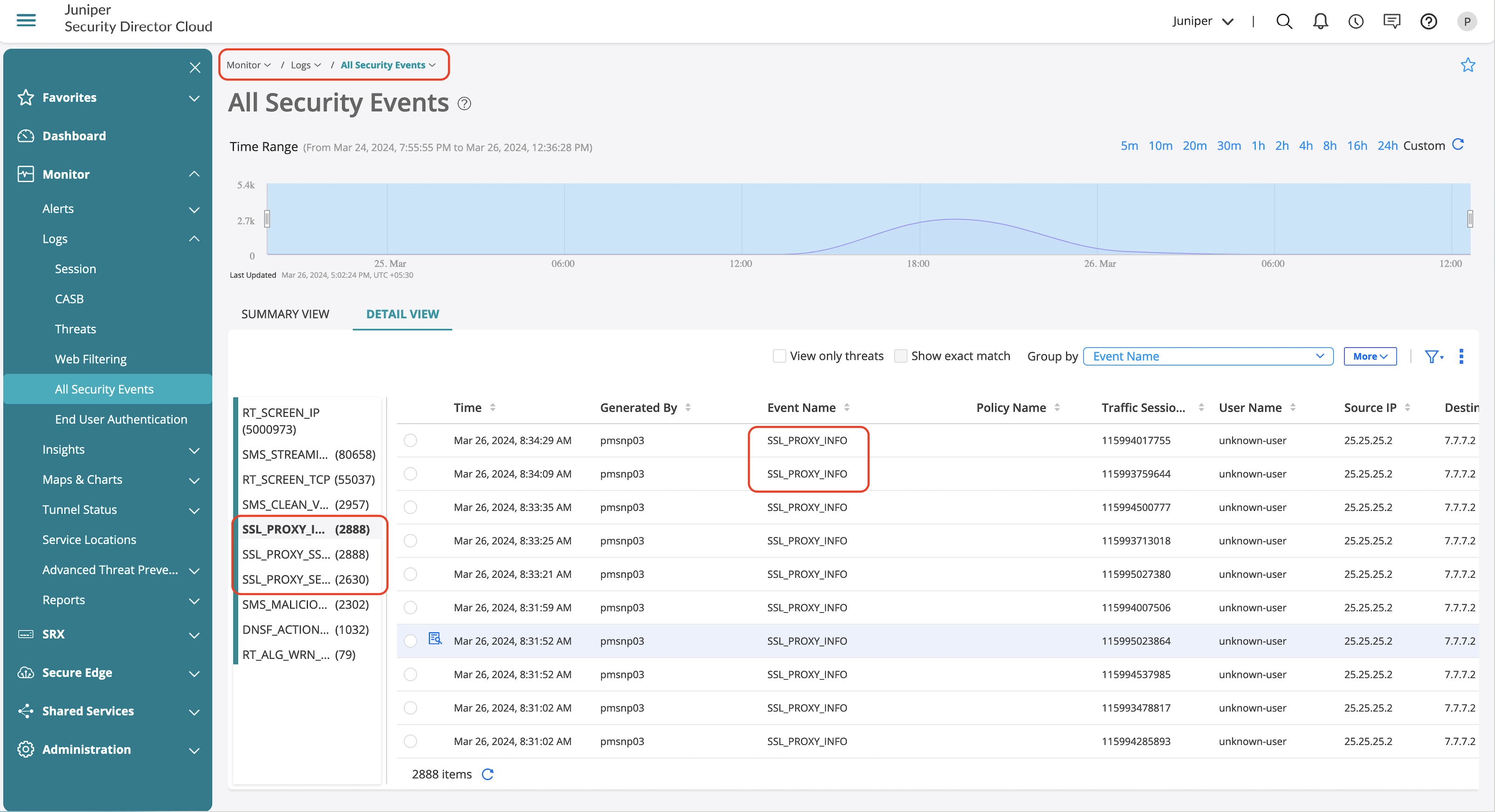
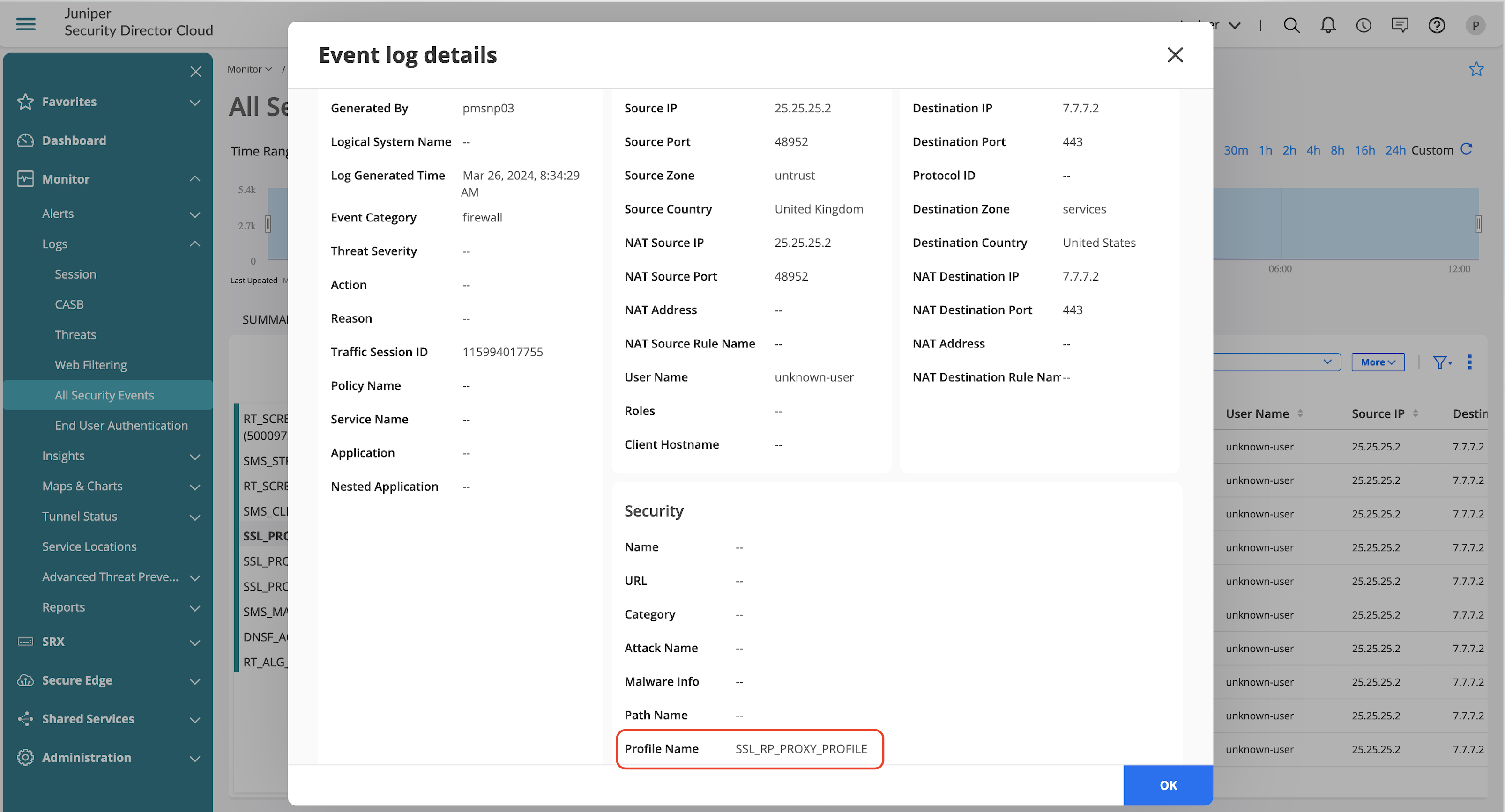
Reverse SSL Proxy Validation
Reverse SSL proxy enables to decrypt specific traffic destined to a webserver for subjecting the traffic through advanced security services.
Once applied on a security policy, you’ll notice several logs that might define the action that SSL proxy takes.
| Log Information | Description |
|---|---|
| SSL_PROXY_SSL_SESSION_DROP | Log is generated when SSL proxy drop a session. |
| SSL_PROXY_SSL_SESSION_ALLOW | Log is generated when SSL session is processed by SSL proxy even after encountering minor errors. |
| SSL_PROXY_SESSION_IGNORE | Log is generated after detection of non-SSL sessions which are initially mistaken as SSL sessions. |
| SSL_PROXY_SESSION_WHITELIST | Log is generated when a SSL proxy session is whitelisted. |
| SSL_PROXY_ERROR | Log is generated for reporting errors during SSL proxy. |
| SSL_PROXY_WARNING | Log is generated for reporting warnings during SSL proxy. |
| SSL_PROXY_INFO | Log is generated for reporting general information during SSL proxy. |