Use Case and Reference Architecture
You can achieve macro and microsegmentation, for example to secure data and assets, in a VXLAN architecture using GBP. GBPs leverage underlying VXLAN technology to provide location-agnostic endpoint access control. GBPs allow you to implement consistent security policies across your enterprise network domains. You can simplify your network configuration by using GBP, avoiding the need to configure large numbers of firewall filters on all your switches. GBPs block lateral threats by ensuring consistent application of security group policies throughout the network, regardless of the location of endpoints or users. VXLAN-GBP works by leveraging a reserved field in the VXLAN header for use as a Scalable Group Tag (SGT). You can use the SGTs as match conditions in firewall filter rules. Using an SGT is more robust than using port or MAC addresses to achieve similar results. Scalable Group Tags can be assigned statically (by configuring the switch on a per-port or per-MAC basis), or they can be configured on the RADIUS server and pushed to the switch through 802.1X when the user is authenticated.
The segmentation enabled by VXLAN-GBP is especially useful in campus VXLAN environments because it gives you a practical way to create network access policies that are independent of the underlying network topology. It simplifies the design and implementation phases of developing network application and endpoint-device security policies.
You can find more detailed information on the VXLAN-GBP standard in the IEEE RFC, I-D.draft-smith-vxlan-group-policy. For the purposes of this example architecture, VXLAN-GBP leverages a reserved field in the VXLAN header as an SGT, as shown in Figure 1.
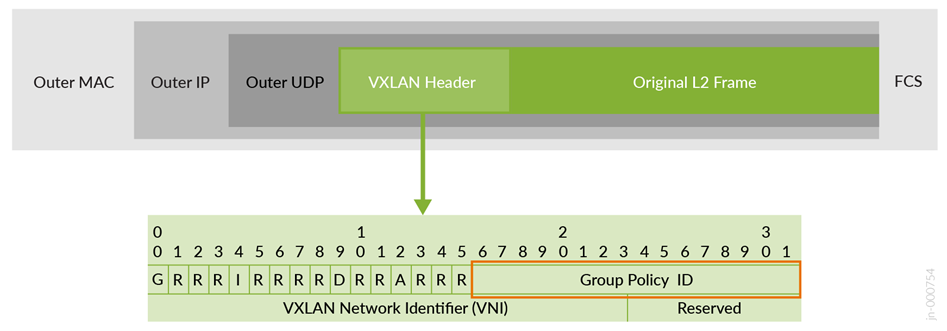
Starting with Junos OS Release 22.4R1, Juniper Networks switches support VXLAN-GBP in egress and ingress enforcing mode as described below:
- GBP egress enforcement:
- This is the IETF standards-based approach.
- The GBP tag is part of the VXLAN data plane and needs to be set as the group policy ID in the VXLAN header.
- For verification of the destination GBP tag from a remote switch, the packet must be sent to the remote switch every time. The remote switch can then act as an enforcement point for traffic egressing the fabric to the next wired client and can, based on SGT Policy, block the traffic, and discard the packet.
- GBP ingress enforcement:
- This is a Juniper Networks proprietary enhancement to the Junos GBP and SGT implementations.
- This enhancement is available starting with Junos OS Release 22.4R1.
- Here, the GBP tag is an extension of the control plane (MP-BGP extension).
- The GBP tag information is added through a vendor-specific attribute to the EVPN Type-2 MAC and IP address information that the fabric shares among its nodes. In this case, the group policy ID in the VXLAN header is always left zero as it is not used for enforcement.
- The huge advantage is that the destination GBP tag of a wired client present on a remote switch is already known because it’s learned through the control plane. With this enhancement, the SGT on the local switch where the source wired client is attached can pre-emptively block traffic that is not allowed to be sent to a destination client on a remote switch. The enforcement of SGTs always happens at the ingress wired client switch. The need for sending all traffic through the fabric even though it may get discarded by the SGT, as in the standards-based approach, does not happen with this solution.
- This extension makes it easier for administrators to debug
GBP-based traffic forwarding decisions. You can review a local
switch to know if traffic would be allowed or blocked by a remote
switch. Junos OS commands like
show ethernet-switching table display
Juniper Mist-managed campus fabrics automatically activate ingress GBP enforcement.
There are different ways you can apply a GBP tag to a wired client to be used by the SGTs to allow or block traffic. See Figure 2.
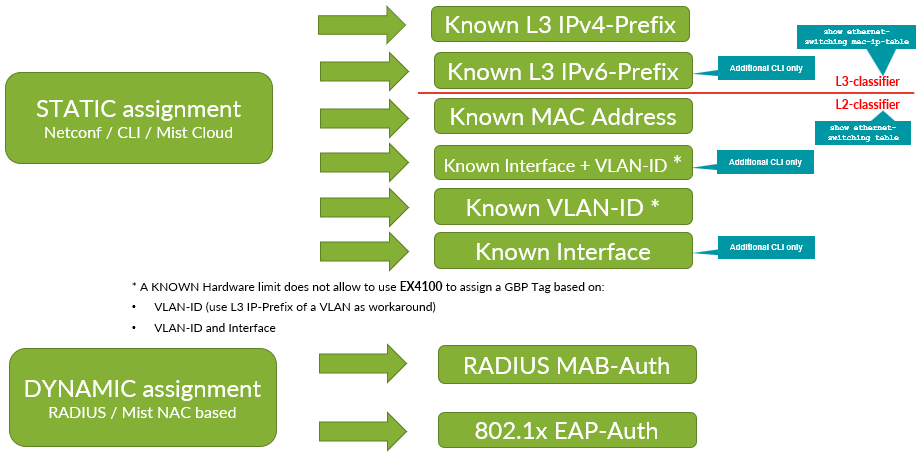
You can assign GBP tags as follows:
- For static GBP tag assignment:
- You must configure static assignment to identify a wired client and assign the GBP tag to it.
- Match criteria (depending on Junos OS release version) can be:
- Layer 3 IPv4 prefixes and hosts
- Layer 3 IPv6 prefixes and hosts
- Layer 2 MAC address
- Switch interface/port and VLAN ID (not supported on Juniper Networks® EX4100 Switches).
- Layer 2 VLAN ID (not supported on EX4100 Switches).
- Switch interface/port
- For dynamic GBP tag assignment:
- The wired client needs to be authenticated at the switch port when entering the fabric.
- Is based on RADIUS server authorization information which is part of the RADIUS access accept message.
- The wired client authentication can be:
- IEEE 802.1X EAP-based
- MAC Authentication Bypass (MAB)
There is no prioritization between any static GBP tag and dynamic GBP tag assignment. A port can only be used for one of the two assignment methods at any time. Dynamic GBP tag assignment will override any static GBP assignment should you have a conflict. Currently, there is no support for cascading these methods.Within static GBP tag assignment, there is prioritization among the match criteria, but only for those within the same layer (within Layer 2 or within Layer 3). This is because Juniper Mist cloud automatically activates Layer 2 to Layer 3 tagging propagation, but the classification is done in separate tables. For example, a static classifier for IPv4 does not override a static MAC address classifier because of this separation. However, a MAC address classifier overrides a VLAN-based tag classification because of higher priority.
The Juniper Mist portal simplifies this process and abstracts the switch configuration needed as shown in Figure 3.
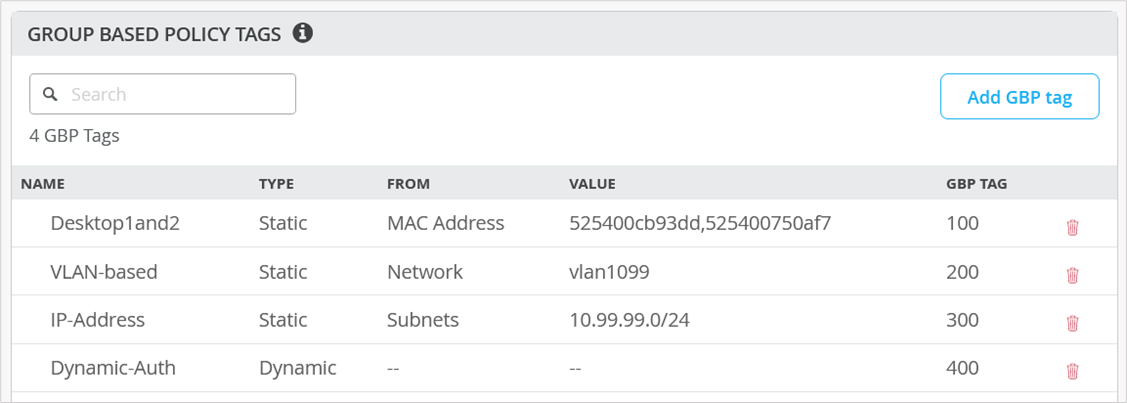
After defining the GBP tag assignment, you need to specify the SGTs as switch policies. Again, the Juniper Mist cloud simplifies and abstracts this process in its portal, allowing you to build an intuitive communication matrix.
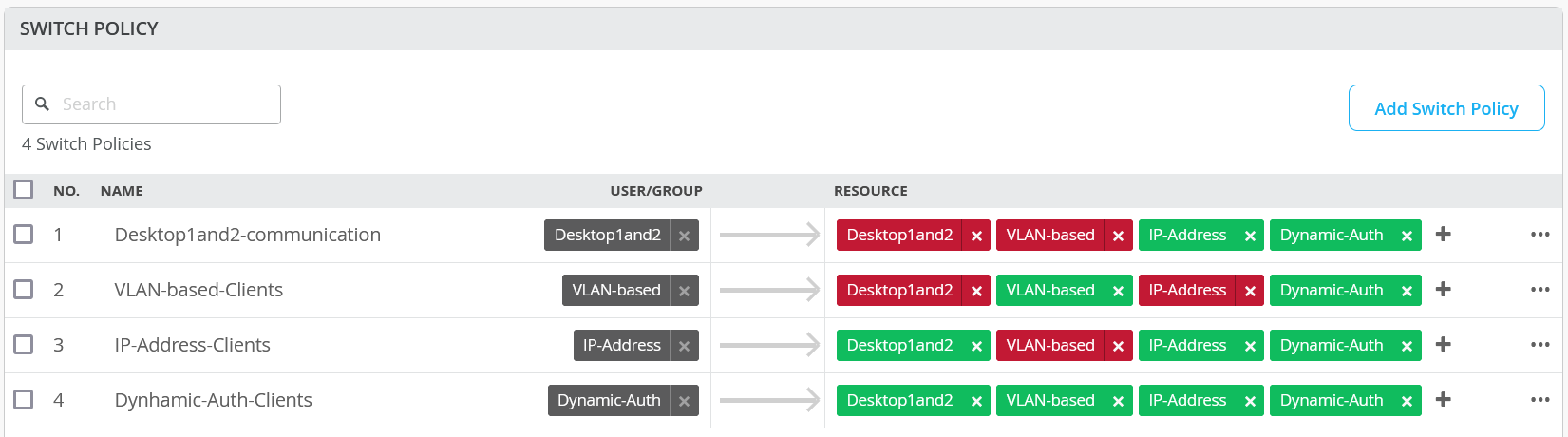
We strongly recommend using a switch template to configure static or dynamic GBP tag assignments and SGT policies since the templates ease the task of distributing this information across all access switches of an IP Clos fabric.
