Example: Configuring a Device for Peer Certificate Chain Validation
This example shows how to configure a device for certificate chains used to validate peer devices during IKE negotiation.
Requirements
Before you begin, obtain the address of the certificate authority (CA) and the information they require (such as the challenge password) when you submit requests for local certificates.
Overview
This example shows how to configure a local device for certificate chains, enroll CA and local certificates, check the validity of enrolled certificates, and check the revocation status of the peer device.
Topology
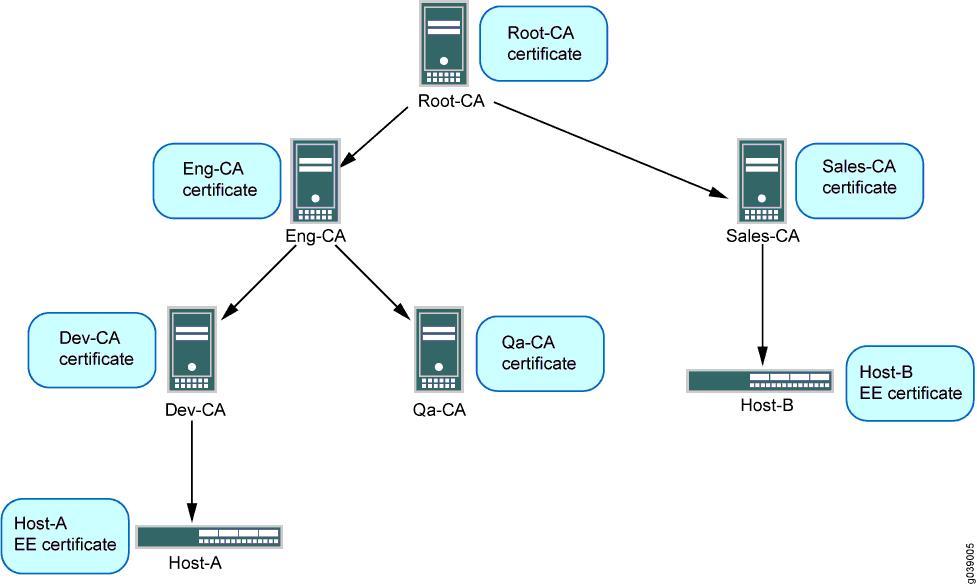
This example shows the configuration and operational commands on Host-A, as shown in Figure 1. A dynamic CA profile is automatically created on Host-A to allow Host-A to download the CRL from Sales-CA and check the revocation status of Host-B’s certificate.
The IPsec VPN configuration for Phase 1 and Phase 2 negotiation is shown for Host-A in this example. The peer device (Host-B) must be properly configured so that Phase 1 and Phase 2 options are successfully negotiated and security associations (SAs) are established.
Configuration
To configure a device for certificate chains:
Configure CA Profiles
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security pki ca-profile Root-CA ca-identity CA-Root set security pki ca-profile Root-CA enrollment url http://10.157.88.230:8080/scep/Root/ set security pki ca-profile Root-CA revocation-check use-crl set security pki ca-profile Eng-CA ca-identity Eng-CA set security pki ca-profile Eng-CA enrollment url http://10.157.88.230:8080/scep/Eng/ set security pki ca-profile Eng-CA revocation-check use-crl set security pki ca-profile Dev-CA ca-identity Dev-CA set security pki ca-profile Dev-CA enrollment url http://10.157.88.230:8080/scep/Dev/ set security pki ca-profile Dev-CA revocation-check use-crl
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure CA profiles:
Create the CA profile for Root-CA.
[edit security pki] user@host# set ca-profile Root-CA ca-identity CA-Root user@host# set ca-profile Root-CA enrollment url http://10.157.88.230:8080/scep/Root/ user@host# set ca-profile Root-CA revocation-check use-crl
Create the CA profile for Eng-CA.
[edit security pki] user@host# set ca-profile Eng-CA ca-identity Eng-CA user@host# set ca-profile Eng-CA enrollment url http://10.157.88.230:8080/scep/Eng/ user@host# set ca-profile Eng-CA revocation-check use-crl
Create the CA profile for Dev-CA.
[edit security pki] user@host# set ca-profile Dev-CA ca-identity Dev-CA user@host# set ca-profile Dev-CA enrollment url http://10.157.88.230:8080/scep/Dev/ user@host# set ca-profile Dev-CA revocation-check use-crl
Results
From configuration mode, confirm your configuration
by entering the show security pki command. If the output
does not display the intended configuration, repeat the configuration
instructions in this example to correct it.
[edit]
user@host# show security pki
ca-profile Root-CA {
ca-identity Root-CA;
enrollment {
url "http:/;/10.157.88.230:8080/scep/Root/";
}
revocation-check {
use-crl;
}
}
ca-profile Eng-CA {
ca-identity Eng-CA;
enrollment {
url "http:/;/10.157.88.230:8080/scep/Eng/";
}
revocation-check {
use-crl;
}
}
ca-profile Dev-CA {
ca-identity Dev-CA;
enrollment {
url "http:/;/10.157.88.230:8080/scep/Dev/";
}
revocation-check {
use-crl;
}
}
If you are done configuring the device, enter commit from configuration mode.
Enroll Certificates
Step-by-Step Procedure
To enroll certificates:
Enroll the CA certificates.
user@host> request security pki ca-certificate enroll ca-profile Root-CA
user@host> request security pki ca-certificate enroll ca-profile Eng-CA
user@host> request security pki ca-certificate enroll ca-profile Dev-CA
Type yes at the prompts to load the CA certificate.
Verify that the CA certificates are enrolled in the device.
user@host> show security pki ca-certificate ca-profile Root-CA Certificate identifier: Root-CA Issued to: Root-CA, Issued by: C = us, O = juniper, CN = Root-CA Validity: Not before: 07- 3-2015 10:54 UTC Not after: 07- 1-2020 10:54 UTC Public key algorithm: rsaEncryption(2048 bits)user@host> show security pki ca-certificate ca-profile Eng-CA Certificate identifier: Eng-CA Issued to: Eng-CA, Issued by: C = us, O = juniper, CN = Root-CA Validity: Not before: 07- 3-2015 10:54 UTC Not after: 07- 1-2020 10:54 UTC Public key algorithm: rsaEncryption(2048 bits)user@host> show security pki ca-certificate ca-profile Dev-CA Certificate identifier: Dev-CA Issued to: Dev-CA, Issued by: C = us, O = juniper, CN = Eng-CA Validity: Not before: 07- 3-2015 10:54 UTC Not after: 07- 1-2020 10:54 UTC Public key algorithm: rsaEncryption(2048 bits)Verify the validity of the enrolled CA certificates.
user@host> request security pki ca-certificate verify ca-profile Root-CA CA certificate Root-CA verified successfully
user@host> request security pki ca-certificate verify ca-profile Eng-CA CA certificate Eng-CA verified successfully
user@host> request security pki ca-certificate verify ca-profile Dev-CA CA certificate Dev-CA verified successfully
Enroll the local certificate.
user@host> request security pki local-certificate enroll certificate-id Host-A ca-profile Dev-CA challenge-password juniper domain-name host-a.company.net email host-a@company.net subject DC=juniper,CN=Host-A, OU=DEV,O=PKI,L=Sunnyvale,ST=CA,C=US
Verify that the local certificate is enrolled in the device.
user@host> show security pki local-certificate Issued to: Host-A, Issued by: C = us, O = juniper, CN = Dev-CA Validity: Not before: 07- 3-2015 10:54 UTC Not after: 07- 1-2020 10:54 UTC Public key algorithm: rsaEncryption(1024 bits)Verify the validity of the enrolled local certificate.
user@host> request security pki local-certificate verify certificate-id Host-A Local certificate Host-A verification success
Check the CRL download for configured CA profiles.
user@host> show security pki crl CA profile: Root-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Root-CA Effective date: 09- 9-2015 13:08 Next update: 09-21-2015 02:55 CA profile: Eng-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Eng-CA Effective date: 08-22-2015 17:46 Next update: 10-24-2015 03:33 CA profile: Dev-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Dev-CA Effective date: 09-14-2015 21:15 Next update: 09-26-2012 11:02
Configure IPsec VPN Options
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set services ipsec-vpn ike proposal ike_cert_prop_01 authentication-method rsa-signatures set services ipsec-vpn ike proposal ike_cert_prop_01 dh-group group5 set services ipsec-vpn ike proposal ike_cert_prop_01 authentication-algorithm sha1 set services ipsec-vpn ike proposal ike_cert_prop_01 encryption-algorithm aes-256-cbc set services ipsec-vpn ike policy ike_cert_pol_01 mode main set services ipsec-vpn ike policy ike_cert_pol_01 proposals ike_cert_prop_01 set services ipsec-vpn ike policy ike_cert_pol_01 certificate local-certificate Host-A set services ipsec-vpn ipsec proposal ipsec_prop_01 protocol esp set services ipsec-vpn ipsec proposal ipsec_prop_01 authentication-algorithm hmac-sha1-96 set services ipsec-vpn ipsec proposal ipsec_prop_01 encryption-algorithm 3des-cbc set services ipsec-vpn ipsec proposal ipsec_prop_01 lifetime-seconds 300 set services ipsec-vpn ipsec policy ipsec_pol_01 proposals ipsec_prop_01 set services ipsec-vpn ipsec vpn ipsec_cert_vpn_01 ike ipsec-policy ipsec_pol_01
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure IPsec VPN options:
Configure Phase 1 options.
[edit services ipsec-vpn ike proposal ike_cert_prop_01] user@host# set authentication-method rsa-signatures user@host# set dh-group group5 user@host# set authentication-algorithm sha1 user@host# set encryption-algorithm aes-256-cbc [edit services ipsec-vpn ike policy ike_cert_pol_01] user@host# set mode main user@host# set proposals ike_cert_prop_01 user@host# set certificate local-certificate Host-A
Configure Phase 2 options.
[edit services ipsec-vpn ipsec proposal ipsec_prop_01] user@host# set protocol esp user@host# set authentication-algorithm hmac-sha1-96 user@host# set encryption-algorithm 3des-cbc user@host# set lifetime-seconds 300 [edit services ipsec-vpn ipsec policy ipsec_pol_01] user@host# set proposals ipsec_prop_01 [edit services ipsec-vpn ipsec vpn ipsec_cert_vpn_01] user@host# set ike ipsec-policy ipsec_pol_01
Results
From configuration mode, confirm your configuration
by entering the show security ike and show security
ipsec commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show services ipsec-vpn ike
proposal ike_cert_prop_01 {
authentication-method rsa-signatures;
dh-group group5;
authentication-algorithm sha1;
encryption-algorithm aes-256-cbc;
}
policy ike_cert_pol_01 {
mode main;
proposals ike_cert_prop_01;
certificate {
local-certificate Host-A;
}
}
[edit]
user@host# show services ipsec-vpn ipsec
proposal ipsec_prop_01 {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm 3des-cbc;
lifetime-seconds 300;
}
policy ipsec_pol_01 {
proposals ipsec_prop_01;
}
If you are done configuring the device, enter commit from configuration mode.
Verification
If certificate validation is successful during IKE negotiation between peer devices, both IKE and IPsec security associations (SAs) are established.
Verifying IKE Phase 1 Status
Purpose
Verify the IKE Phase 1 status.
Action
Enter the show services ipsec-vpn ike security-associations command from operational mode.
user@host> show services ipsec-vpn ike security-associations Remote Address State Initiator cookie Responder cookie Exchange type 192.0.2.0 Matured 63b3445edda507fb 2715ee5895ed244d Main
Verifying IPsec Phase 2 Status
Purpose
Verify the IPsec Phase 2 status.
Action
Enter the show services ipsec-vpn ipsec security-associations command from operational mode.
user@host> show services ipsec-vpn ipsec security-associations
Service set: ips_ss1, IKE Routing-instance: default
Rule: vpn_rule_ms_2_2_01, Term: term11, Tunnel index: 1
Local gateway: 10.0.1.2, Remote gateway: 172.16.0.0
IPSec inside interface: ms-2/2/0.1, Tunnel MTU: 1500
UDP encapsulate: Disabled, UDP Destination port: 0
Direction SPI AUX-SPI Mode Type Protocol
inbound 2151932129 0 tunnel dynamic ESP
outbound 4169263669 0 tunnel dynamic ESP
IKE and IPsec SA Failure for a Revoked Certificate
Checking for Revoked Certificates
Problem
If certificate validation fails during IKE negotiation
between peer devices, check to make sure that the peer’s certificate
has not been revoked. A dynamic CA profile allows the local device
to download the CRL from the peer’s CA and check the revocation
status of the peer’s certificate. To enable dynamic CA profiles,
the revocation-check crl option must be configured on a
parent CA profile.
Solution
To check the revocation status of a peer’s certificate:
Identify the dynamic CA profile that will show the CRL for the peer device by entering the show security pki crl command from operational mode.
user@host> show security pki crl CA profile: Root-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Root-CA Effective date: 09- 9-2012 13:08 Next update: 09-21-2012 02:55 CA profile: Eng-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Eng-CA Effective date: 08-22-2012 17:46 Next update: 10-24-2015 03:33 CA profile: Dev-CA CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Dev-CA Effective date: 09-14-2012 21:15 Next update: 09-26-2012 11:02 CA profile: dynamic-001 CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Sales-CA Effective date: 09-14-2012 21:15 Next update: 09-26-2012 11:02The CA profile
dynamic-001is automatically created on Host-A so that Host-A can download the CRL from Host-B’s CA (Sales-CA) and check the revocation status of the peer’s certificate.Display CRL information for the dynamic CA profile by entering the show security pki crl ca-profile dynamic-001 detail command from operational mode.
Enter
user@host> show security pki crl ca-profile dynamic-001 detail CA profile: dynamic-001 CRL version: V00000001 CRL issuer: C = us, O = juniper, CN = Sub11 Effective date: 09-19-2012 17:29 Next update: 09-20-2012 01:49 Revocation List: Serial number Revocation date 10647C84 09-19-2012 17:29 UTCHost-B’s certificate (serial number 10647084) has been revoked.
