Inline IPsec
Read this topic to learn about the inline IPsec in SRX Series Firewalls.
Overview
Inline IPsec is a Junos OS feature that offloads IPsec traffic processing from the CPU to the Packet Forwarding Engine of a Juniper Networks device. The feature securely encrypts and decrypts IPsec traffic inside the Packet Forwarding Engine ASIC. With this feature, the CPU manages only PowerMode IPsec (PMI) or IPsec VPN that uses Quick Assist Technology (QAT).
Before the introduction of inline IPsec, firewalls performed IPsec operations in the CPU, benefiting from hardware acceleration such as Intel QAT or software optimization like PMI. With inline IPsec, SRX Series Firewalls can use the Packet Forwarding Engine ASIC to improve IPsec performance. Offloading IPsec encryption and decryption to the ASIC contributes to higher throughput. Inline IPsec frees up the firewall CPU for other tasks such as:
-
Internet Key Exchange version 2 (IKEv2) negotiations for preshared keys (PSKs)
-
Post-quantum preshared key (PPK)
-
Public Key Infrastructure (PKI) certificate key negotiations
-
Various encryption and hash functions used in the inline IPsec
You need a valid license to use the inline IPsec feature on your firewall. When you apply the license, the firewall activates the feature by default.
Benefits
-
VPN performance: Improves tunnel performance by offloading encryption and decryption to the ASIC, achieving higher throughputs.
-
CPU optimization: Frees up CPU resources by managing tunnels within the ASIC, allowing the CPU to manage other critical tasks and improving overall firewall performance.
-
VPN security: Enhances security by using Advanced Encryption Standard–Galois/Counter Mode (AES-GCM) encryption algorithms for hardware offloaded tunnels, ensuring strong encryption standards without compromising performance.
-
Deployment: Supports a large number of IPsec tunnels per chassis, making it suitable for large-scale deployments.
-
Agility: Supports the ability to manage few tunnels outside the Packet Forwarding Engine.
How Inline IPsec Works
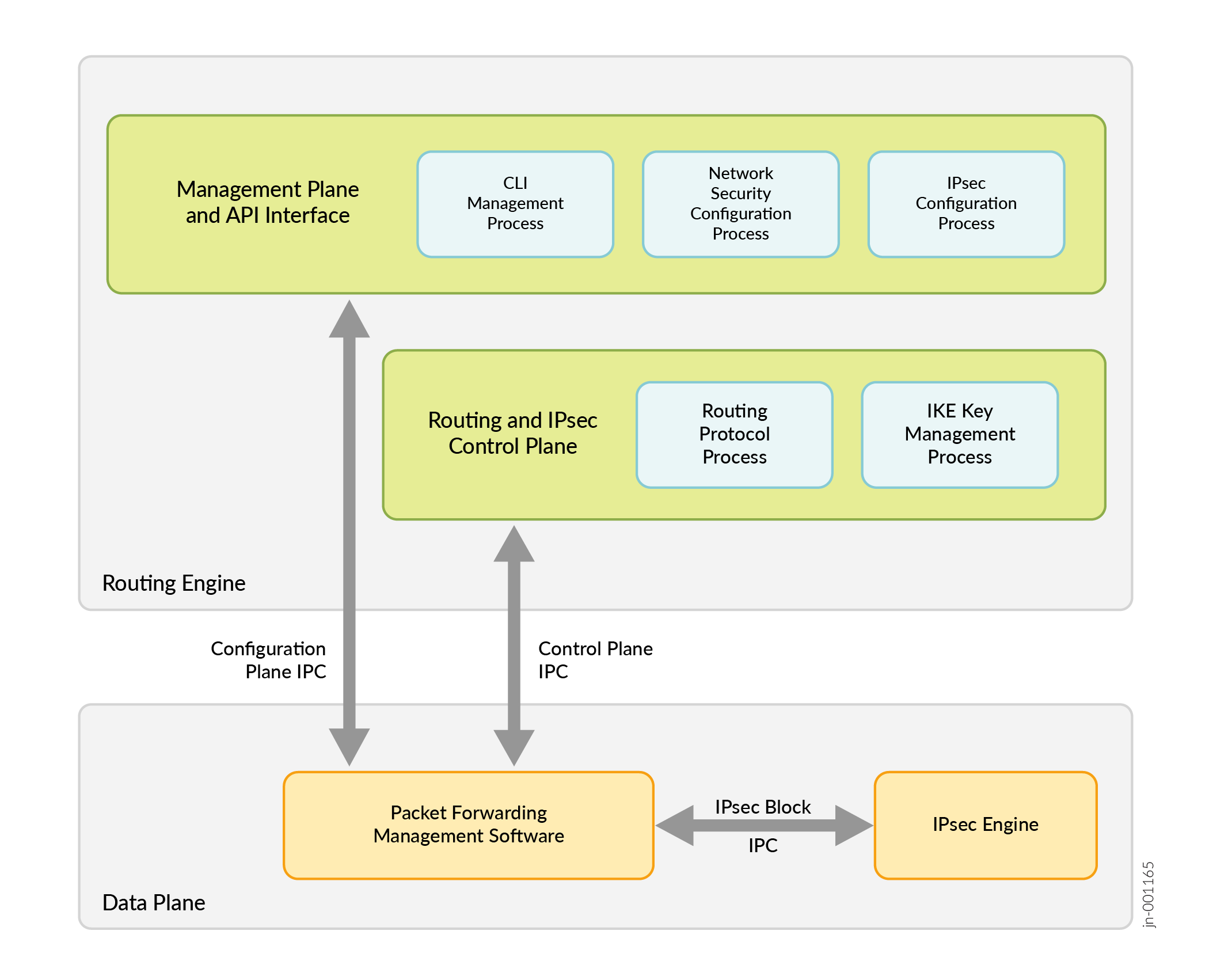
Figure 1 illustrates the architecture of inline IPsec data plane and its interface with the control and management planes. The inline IPsec architecture includes an IPsec engine that handles IPsec operations. As the Packet Forwarding Engine encrypts or decrypts IPsec traffic without relying on CPU cycles, inline IPsec significantly enhances throughput and optimizes firewall performance.
Understand the following behavior of inline IPsec in SRX Series Firewall:
-
Either the IPsec initiator, the responder, or both can use the feature.
-
The firewall performs IPsec Encapsulating Security Payload (ESP) packet encryption and decryption on the built-in ASIC.
-
The IKE protocol used for authentication and key exchanges runs in the CPU.
-
After the IKE negotiations, the iked process manages the tunnel distribution to the Packet Forwarding Engine.
-
The firewall supports:
-
Inline IPsec protocols based on both IPv4 and IPv6 addresses.
-
Inline IPsec for both the IKEv1 and IKEv2 protocols.
-
You'll notice the following actions in your firewall with inline IPsec:
-
The iked process marks the inline IPsec tunnel for hardware offloading in the session flow. This action prevents the tunnel from using the CPU for IPsec encryption and decryption tasks.
-
The output of the command
show security ipsec security associationdisplays:-
Hardware Offloaded: Yesfor an inline IPsec VPN tunnel. -
Hardware Offloaded: Nowhen the CPU processes the tunnel.
-
-
The flowd process shows the incoming and outgoing packets for IPsec VPN traffic flows.
To globally disable the inline IPsec hardware offloading of IPsec tunnel processing in the Packet Forwarding Engine ASIC:
-
Use the command
set security ipsec hw-offload-disable.When you configure this statement, the firewall handles all the IPsec tunnels in CPU instead of the Packet Forwarding Engine ASIC. See ipsec (Security).
Feature Support for Inline IPsec
Firewalls must meet certain criteria to establish IPsec tunnels using inline IPsec feature. Table 1 provides the feature support information for inline IPsec, outlining the criteria that determine the tunnel eligibility for the feature. With inline IPsec the CPU manages the features not supported by ASIC, optimizing the firewall performance. The CPU also supports every feature that inline IPsec supports.
| Features Supported by ASIC | Features Supported by CPU |
|---|---|
|
Packet Forwarding Engine on YT ASIC processes IPsec VPN |
CPU processes all the IPsec VPN features that uses PMI and QAT. The features include both the Authentication Header (AH) and ESP-based tunnels with AES-GCM and other supported encryption protocols in PMI. See PowerMode IPsec. In addition to managing the PMI and QAT features, the CPU also handles all other features that the Packet Forwarding Engine ASIC does not support. See the following entries in this column for more details. |
|
Tunnel mode using ESP |
Tunnel mode using AH |
| Encryption algorithms AES-GCM with 128-bit key or 256-bit key |
All encryption algorithms other than AES-GCM with 128-bit key or 256-bit key |
|
Deployment mode supporting site-to-site IPsec VPN |
Deployment mode supporting point-to-multipoint (P2MP) VPNs, group VPN, and Auto Discovery VPN (ADVPN). Interchassis link (ICL) encryption in Multinode High Availability (MNHA). |
|
Antireplay window size up to 4096 |
Antireplay window size greater than 4096 |
|
Up to 4000 security associations (SA) or 2000 tunnels |
More than 4000 or multiple SAs, also known as child SAs |
|
Network Address Translation-Traversal (NAT-T) Tunnel |
Tunnel with |
Note the following limitations with inline IPsec:
-
When you set the Don’t Fragment (DF) bit for active offloaded tunnels, the configuration takes effect after a rekey.
-
When you configure the Differentiated Services Code Point (DSCP) copy for active offloaded tunnels, the configuration takes effect after a rekey.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
