Safe Search Enhancement for Web Filtering
SUMMARY Learn about our safe search enhancement for Content Security Web filtering solutions to enforce the safest Web browsing mode available, by default.
What's Next
Now that you’ve learned about safe search enhancement for Web filtering, you'll be interested to know how to disable the safe search function. Check out juniper-local, websense-redirect, and juniper-enhanced for more information.
Safe Search Enhancement for Web Filtering Overview
- Benefits of Safe Search Enhancement for Web Filtering
- Features of Safe Search Enhancement for Web Filtering
- Limitations of Safe Search Enhancement for Web Filtering
Benefits of Safe Search Enhancement for Web Filtering
Provides the safest Web browsing mode available, by default.
Protects the HTTPS-based search engine cache. This protection is a key security feature requirement for organizations with multiple Web users in educational, financial, health-care, banking, and corporate segments. In a campus or branch, enabling a default safe search solution for all users and blocking the search engine cache provides secure and comfortable Web browsing.
Features of Safe Search Enhancement for Web Filtering
You use Content Security Web filtering to manage Web browsing by preventing access to inappropriate Web content. To do this, you use the following Web filtering solutions:
Redirect Web filtering
Local Web filtering
Enhanced Web Filtering (EWF)
We've enhanced the safe search functionality for these Content Security Web filtering solutions to provide an extremely safe search environment for the Web user. Table 1 describes the features of the safe search enhancement.
Safe Search Feature |
Description |
|---|---|
Default safe search |
By enabling the safe search enhancement feature, you enforce the safest Web browsing mode available by default on the well-known search engines. Doing so helps those users that are not using the strictest safe search settings. If you enable the safe search feature on your security device, it enforces the search service to the strictest mode by URL query rewriting, which is transparent to you. For example, when you do a search request on the search engines Google, Bing, Yahoo, or Yandex, the safe search feature rewrites the requested URLs to the safest search URLs. Here're a few examples of requested and converted URLs:
|
Blocking search engine cache |
By blocking the search engine cache on the well-known search engines, you can hide your Web-browsing activities from other users if you are a part of an organization that has multiple Web users in educational, financial, health-care, banking, and corporate segments. To block the search engine cache, you configure a general URL block pattern and category for the search engine cache service. |
You can disable the safe search option at the Web filtering-level and profile-level configurations. See juniper-local, websense-redirect, and juniper-enhanced.
Limitations of Safe Search Enhancement for Web Filtering
For HTTP safe search enhancement, you must enable stream mode by enabling the
http-reassembleoption at the[edit security utm default-configuration web-filtering]hierarchy level. If you don't enable stream mode, you can't use the safe search feature. As a result, the system sends an HTTP 302 redirect message to the user.For HTTPS safe search enhancement, you must enable the SSL proxy service on the security policy. If SSL proxy bypasses the HTTPS traffic, then the safe search feature also bypasses the HTTPS traffic.
Configure Web Filtering with Safe Search
SUMMARY Use this example to configure Content Security Web filtering solutions and verify the safe search enhancement for Content Security Web filtering.
Requirements
This example uses the following hardware and software components:
An SRX Series Firewall
Junos OS Release 20.2R1
Before you begin:
Make sure you understand how to use Web filtering to manage Web browsing. See Web Filtering Overview.
Configure a Root CA Certificate. See Configuring a Root CA Certificate.
Overview
In this example, you configure the following policies and Web filtering profiles on your security device:
Content Security policies
Security policies
Web filtering profiles
SSL proxy
After you've configured the policies and profiles, you generate the Web filtering statistics and verify the performance of the safe search enhancement.
Figure 1 shows the basic Content Security Web filtering topology. When you enable your security device with the safe search feature, the device rewrites the search requests from the user to the safest search mode of the search engines. The cloud engine or the local engine performs Web filtering on the search requests before forwarding to the Internet or external webserver.
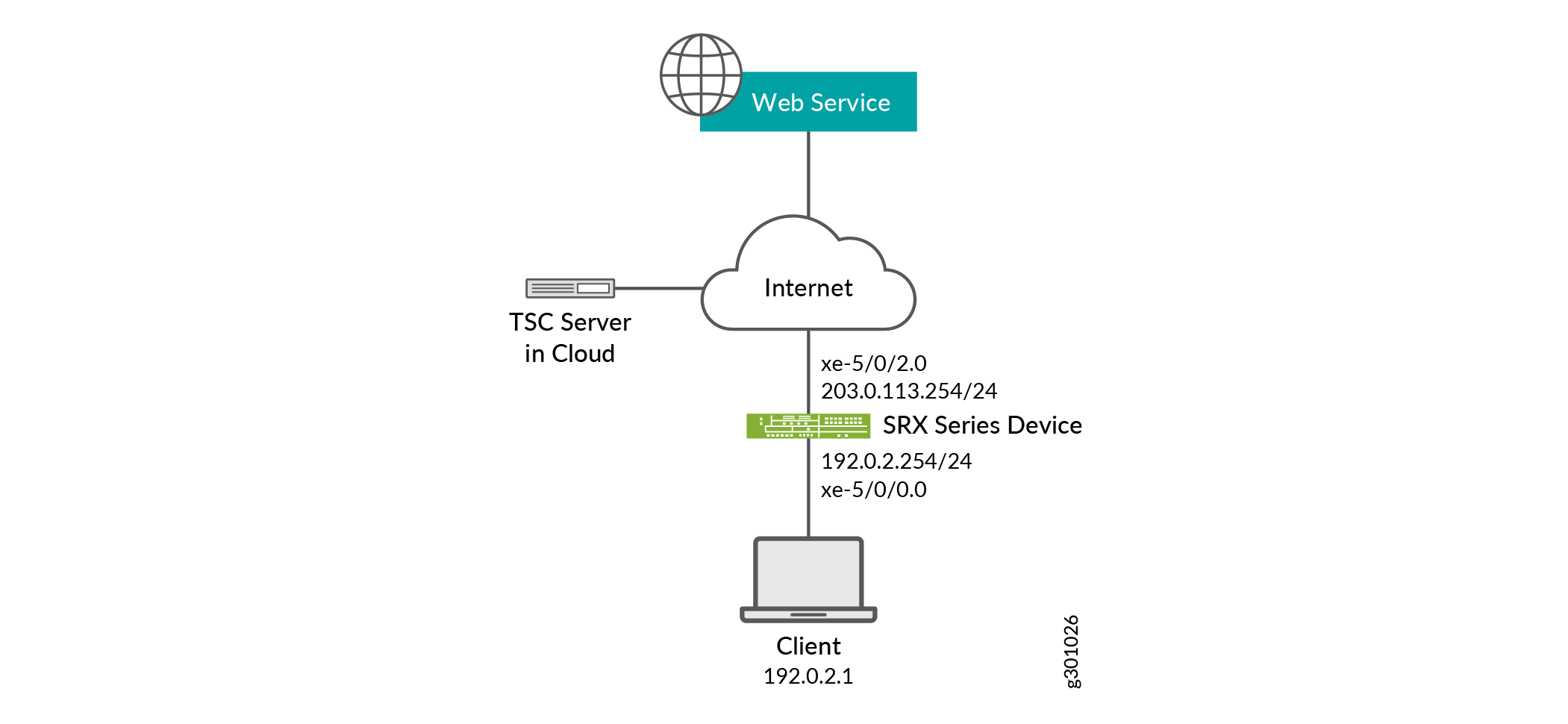
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security utm default-configuration web-filtering type juniper-enhanced set security utm default-configuration web-filtering http-reassemble set security utm default-configuration web-filtering juniper-enhanced default log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile ewf_my_profile1 category Enhanced_Search_Engines_and_Portals action log-and-permit set security utm feature-profile web-filtering juniper-enhanced profile ewf_my_profile1 default log-and-permit set security utm utm-policy utmpolicy1 web-filtering http-profile ewf_my_profile1 set security policies from-zone trust to-zone internet policy sec_policy match source-address any set security policies from-zone trust to-zone internet policy sec_policy match destination-address any set security policies from-zone trust to-zone internet policy sec_policy match application junos-ping set security policies from-zone trust to-zone internet policy sec_policy match application junos-http set security policies from-zone trust to-zone internet policy sec_policy then permit application-services utm-policy utmpolicy1 set security policies default-policy deny-all set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces xe-5/0/0.0 set security zones security-zone internet host-inbound-traffic system-services all set security zones security-zone internet host-inbound-traffic protocols all set security zones security-zone internet interfaces xe-5/0/2.0 set interfaces xe-5/0/0 unit 0 family inet address 192.0.2.254/24 set interfaces xe-5/0/2 unit 0 family inet address 203.0.113.254/24
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the Junos OS CLI User Guide.
To configure Content Security Web filtering:
-
Configure Content Security Web filtering solution.
[edit security utm] user@host# default-configuration web-filtering type juniper-enhanced user@host# default-configuration web-filtering http-reassemble user@host# default-configuration web-filtering juniper-enhanced default log-and-permit user@host# feature-profile web-filtering juniper-enhanced profile ewf_my_profile1 category Enhanced_Search_Engines_and_Portals action log-and-permit user@host# feature-profile web-filtering juniper-enhanced profile ewf_my_profile1 default log-and-permit user@host# utm-policy utmpolicy1 web-filtering http-profile ewf_my_profile1
Configure the security policies to control HTTP or HTTPS traffic from the trust zone to the Internet zone.
[edit security policies] user@host# from-zone trust to-zone internet policy sec_policy match source-address any user@host# from-zone trust to-zone internet policy sec_policy match destination-address any user@host# from-zone trust to-zone internet policy sec_policy match application junos-ping user@host# from-zone trust to-zone internet policy sec_policy match application junos-http user@host# from-zone trust to-zone internet policy sec_policy then permit application-services utm-policy utmpolicy1 user@host# default-policy deny-all
Configure security zones.
[edit security zones security-zone] user@host# trust host-inbound-traffic system-services all user@host# trust host-inbound-traffic protocols all user@host# trust interfaces xe-5/0/0.0 user@host# internet host-inbound-traffic system-services all user@host# internet host-inbound-traffic protocols all user@host# internet interfaces xe-5/0/2.0
Configure interfaces.
[edit interfaces] user@host# xe-5/0/0 unit 0 family inet address 192.0.2.254/24 user@host# xe-5/0/2 unit 0 family inet address 203.0.113.254/24
Results
From configuration mode, confirm your configuration
by entering the show security policies, show security
utm, and show interfaces commands. If the output
does not display the intended configuration, repeat the configuration
instructions in this example to correct it.
user@host# show security policies
from-zone trust to-zone internet {
policy sec_policy {
match {
source-address any;
destination-address any;
application [ junos-ping junos-http ];
}
then {
permit {
application-services {
utm-policy utmpolicy1;
}
}
}
}
}
default-policy {
deny-all;
}
user@host# show security utm
default-configuration {
web-filtering {
http-reassemble;
type juniper-enhanced;
juniper-enhanced {
default log-and-permit;
}
}
}
feature-profile {
web-filtering {
juniper-enhanced {
profile ewf_my_profile1 {
category {
Enhanced_Search_Engines_and_Portals {
action log-and-permit;
}
}
default log-and-permit;
}
}
}
}
utm-policy utmpolicy1 {
web-filtering {
http-profile ewf_my_profile1;
}
}
user@host# show interfaces
xe-5/0/0 {
unit 0 {
family inet {
address 192.0.2.254/24;
}
}
}
xe-5/0/2 {
unit 0 {
family inet {
address 203.0.113.254/24;
}
}
}
If you are done configuring the feature on your device, enter commit from configuration mode.
Verification
Verify Safe Search Function
Purpose
Verify that the safe search feature is enabled for Content Security Web filtering solutions.
Action
From operational mode, enter the show security
utm web-filtering statistics command to view the Web filtering
statistics. In the output, the Safe-search redirect and Safe-search rewrite fields display the enhanced safe search
redirect and rewrite statistics.
user@host> show security utm web-filtering statistics
UTM web-filtering statistics:
Total requests: 0
white list hit: 0
Black list hit: 0
No license permit: 0
Queries to server: 0
Server reply permit: 0
Server reply block: 0
Server reply quarantine: 0
Server reply quarantine block: 0
Server reply quarantine permit: 0
Custom category permit: 0
Custom category block: 0
Custom category quarantine: 0
Custom category qurantine block: 0
Custom category quarantine permit: 0
Site reputation permit: 0
Site reputation block: 0
Site reputation quarantine: 0
Site reputation quarantine block: 0
Site reputation quarantine permit: 0
Site reputation by Category 0
Site reputation by Global 0
Cache hit permit: 0
Cache hit block: 0
Cache hit quarantine: 0
Cache hit quarantine block: 0
Cache hit quarantine permit: 0
Safe-search redirect: 0
+Safe-search rewrite: 0
SNI pre-check queries to server: 0
SNI pre-check server responses: 0
Web-filtering sessions in total: 64000
Web-filtering sessions in use: 0
Fallback: log-and-permit block
Default 0 0
Timeout 0 0
Connectivity 0 0
Too-many-requests 0 0
Meaning
The output displays that the safe search feature is enabled and there are no safe search redirects and safe search rewrites.
