Master Password for Configuration Encryption
Use Feature Explorer to confirm platform and release support for specific features.
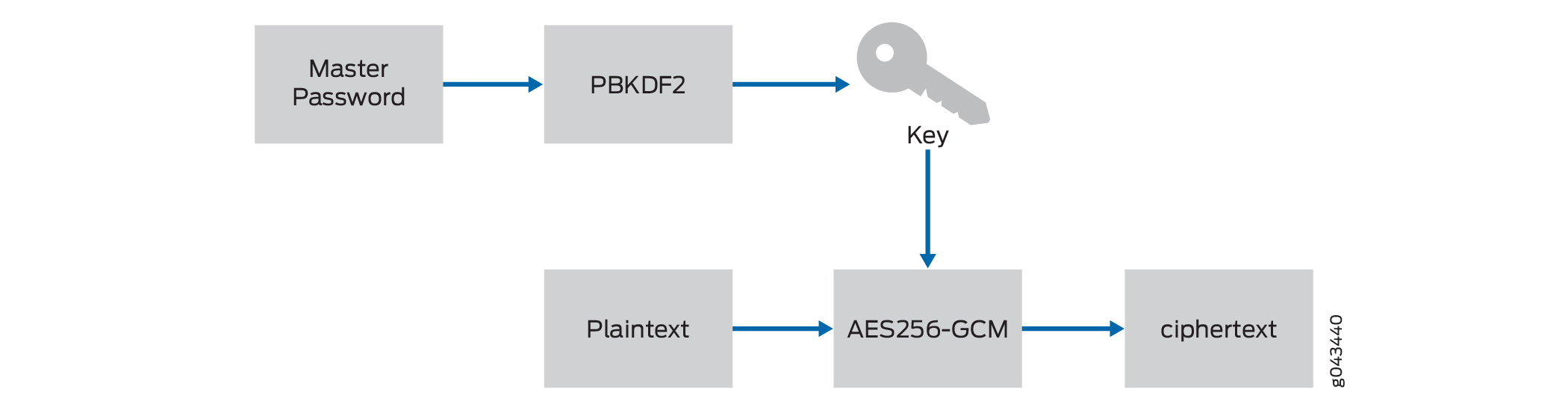
Junos OS and Junos OS Evolved support encryption method for configuration secrets using a master password. The master password derives an encryption key that uses AES256-GCM to protect certain secrets such as private keys, system master passwords, and other sensitive data by storing it in an AES256 encrypted format. For more information, read this topic.
The master password is separate from the device's root password.
Using Trusted Platform Module to Bind Secrets on SRX Series Devices
By enabling the Trusted Platform Module (TPM) on the SRX Series Firewalls, the software layer leverages the use of the underlying TPM chip. TPM is a specialized chip that protects certain secrets at rest such as private keys, system primary passwords, and other sensitive data by storing it in an AES256 encrypted format (instead of storing sensitive data in a clear text format). The device also generates a new SHA256 hash of the configuration each time the administrator commits the configuration. This hash is verified each time the system boots up. If the configuration has been tampered with, the verification fails and the device will not continue to boot. Both the encrypted data and the hash of the configuration is protected by the TPM module using the master encryption password.
Hash validation is performed during any commit operation by performing a validation check of
the configuration file against the saved hash from previous commits. In a chassis cluster
system, hash is independently generated on the backup system as part of the commit process. A
commit from any mode, that is, batch-config, dynamic-config,
exclusive-config, or private config generates the
integrity hash.
Hash is saved only for the current configuration and not for any rollback configurations. Hash is not generated during reboot or shutdown of the device.
The TPM encrypts the following secrets:
-
SHA256 hash of the configuration
-
device primary-password
-
all key-pairs on the device
The TPM chip is enabled by default to make use of TPM functionality. You must configure master encryption password to encrypt PKI key-pairs and configuration hash.
- Limitations
- Configuring Master Encryption Password
- Verifying the Status of the TPM
- Changing the Master Encryption Password
Limitations
The following limitations and exceptions apply to the configuration file integrity feature using TPM:
-
If the master encryption password is not set, data is stored unencrypted.
-
The file integrity feature is not supported along with the configuration file encryption feature that uses keys saved in EEPROM. You can enable only one function at a time.
-
In a chassis cluster, both nodes must have the same TPM settings. This means that both nodes in the chassis cluster must have TPM enabled, or both nodes in the chassis cluster must have TPM disabled. The chassis cluster must not have one node set to TPM enabled and the another node set to TPM disabled.
After the Master Encryption Key (MEK) is configured and operational, downgrading to a Junos version that does not support TPM functionality is not recommended. This is because the non-TPM capable image is not able to decrypt the secrets that were encrypted by TPM after the device reboots to the non-TPM cable version.
If you must downgrade to a non-TPM capable image you must first zeroize the device. The zeroization process ensures the device does not contain any secrets and removes all the keys. After zeroization the device be downgraded to the desired non-TPM capable image.
Configuring Master Encryption Password
Before configuring master encryption password, ensure that you have configured set
system master-password plain-text-password otherwise, certain sensitive data will
not be protected by the TPM.
Set the master encryption password using the following CLI command:
request security tpm master-encryption-password set
plain-text-password
You will be prompted to enter the master encryption password twice, to make sure that these passwords match. The master encryption password is validated for required password strength.
After master encryption password is set, the system proceeds to encrypt the sensitive data with the master encryption password which is encrypted by the Master Binding Key that is owned and protected by the TPM chip.
If there is any issue with setting the master encryption password, a critical ERROR message is logged on the console and the process is terminated.
Verifying the Status of the TPM
You can use the show security tpm status command to verify the status of
the TPM. The following information is displayed:
-
TPM enabled/disabled
-
TPM ownership
-
TPM’s Master Binding Key status (created or not created)
-
master encryption password status (set or not set)
Starting with Junos OS Release 15.1X49-D120 and Junos OS Release 17.4R1, Trusted Platform
Module (TPM) firmware has been updated. The upgraded firmware version provides additional
secure cryptography and improves security. Updated TPM firmware is available along with the
Junos OS package. For updating TPM Firmware, see Upgrading TPM Firmware on SRX-Devices. To confirm the TPM firmware
version, use the show security tpm status command. TPM
Family and TPM Firmware version output fields
are introduced.
Changing the Master Encryption Password
Changing the master encryption password is done using the CLI.
To change the master encryption password, enter the following command from operational mode:
request security tpm master-encryption-password set
plain-text-password
It is recommended that no configuration changes are made while you are changing the master encryption password.
The system checks if the master encryption password is already configured. If master encryption password is configured, then you are prompted to enter the current master encryption password.
The entered master encryption password is validated against the current master encryption password to make sure these master encryption passwords match. If the validation succeeds, you will be prompted to enter the new master encryption password as plain text. You will be asked to enter the key twice to validate the password.
The system then proceeds to re-encrypt the sensitive data with the new master encryption password. You must wait for this process of re-encryption to complete before attempting to change the master encryption password again.
If for some reason, the encrypted master encryption password file is lost or corrupted, the system will not be able to decrypt the sensitive data. The system can only be recovered by re-importing the sensitive data in clear text, and re-encrypting them.
If the system is compromised, the administrator can recover the system using of the following method:
-
Clear the TPM ownership in u-boot and then install the image in boot loader using TFTP or USB (if USB port is not restricted).
If the installed software version is older than Junos OS Release 15.1X49-D110 and the master encryption password is enabled, then installation of Junos OS Release 15.1X49-D110 will fail. You must backup the configuration, certificates, key-pairs, and other secrets and use the TFTP/USB installation procedure.
Using Trusted Platform Module on MX Series Devices
TPM is used to protect the sensitive data such as master password of system by encryption. TPM supports to encrypt and decrypt the data using keys. To decrypt the encrypted configuration secrets, the master password must be deleted.
Use Feature Explorer to confirm platform and release support for specific features.
A master password is used to encrypt the configuration files stored in the device.
To change the master encryption password, enter the following command from operational mode:
request security tpm master-encryption-password set
plain-text-password
You can prevent to delete or change the master password using
protect option. Once the master password is protected, you need
to apply unprotect option to delete or change the master password.
Run with the following steps:
-
Configure the system master password.
user@host#
set system master-password plain-text-passwordMaster password: Repeat master password: user@host#commit -
Configure to protect the system master password from deletion.
user@host#
protect system master-passworduser@host#commituser@host#show systemhost-name device1; kernel-replication { traceoptions { file kernel_traces.log; flag all; } } ports { console log-out-on-disconnect; } syslog { file messages { daemon any; } } protect: master-password { password-configured; }The system master password is protected. You can delete the master password by unprotecting the master password.
-
Configure to unprotect the master password by entering the right master password.
user@host #
unprotect system master-passwordEnter current master-password: user@host #commithost-name device1; kernel-replication { traceoptions { file kernel_traces.log; flag all; } } ports { console log-out-on-disconnect; } syslog { file messages { daemon any; } } master-password { password-configured; } -
Once the master password is unprotected, you can delete or change the master password on the system.
user@host #
delete system master-passworduser@host #commituser@host #show systemhost-name device1; kernel-replication { traceoptions { file kernel_traces.log; flag all; } } ports { console log-out-on-disconnect; } syslog { file messages { daemon any; } }
Limitations
-
If Master Encryption Key (MEK) is deleted, the data cannot be decrypted. To delete MEK, you have to zeroize the device.
-
To downgrade the Routing Engine, you must zeroized the Routing Engine. Once the device is zeroized it can then be safely downgraded to the image which does not support this feature.
-
In dual Routing Engine configuration, if backup Routing Engine needs to be recovered, due to MEK mismatch, GRES needs to be disabled and backup Routing Engine must be zeroized. Once backup Routine Engine comes up, configure MEK using
request security tpm master-encryption-password set plain-text-passwordcommand on Master RE. -
In dual Routing Engine configuration, if backup Routing Engine needs to be replaced, new backup Routing Engine must be zeroized first before adding in dual Routing Engine configuration, GRES must be disabled and re-configure MEK on master RE using
request security tpm master-encryption-password set plain-text-passwordcommand. -
When you configure OSPF, IS-IS, MACsec, BGP, and VRRP on the device and reset the master password, then there is a time (in seconds) delay for the routing/dot1x subsystem to be active.
-
When you configure master password, MEK, OSPF, IS-IS, MACsec, BGP, and VRRP on the device and reboot the device, then there is a time (in seconds) delay for the routing/dot1x subsystem to be active.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
show security tpm status command. TPM Family and TPM Firmware version output fields are introduced.