DNS Proxy Overview
A domain name system (DNS) proxy allows clients to use an SRX300, SRX320, SRX340, SRX345, SRX550M, or SRX1500 device as a DNS proxy server. A DNS proxy improves domain lookup performance by caching previous lookups. A typical DNS proxy processes DNS queries by issuing a new DNS resolution query to each name server that it has detected until the hostname is resolved.
DNS Proxy Cache
When a DNS query is resolved by a DNS proxy, the result is stored in the device's DNS cache. This stored cache helps the device to resolve subsequent queries from the same domain and avoid network latency delay.
If the proxy cache is not available, the device sends the query to the configured DNS server, which results in network latency delays.
DNS proxy maintains a cache entry for each resolved DNS query.
These entries have a time-to-live (TTL) timer so the device purges
each entry from the cache as it reaches its TTL and expires. You can
clear a cache by using the clear system services dns-proxy cache command , or the cache will automatically expire along with TTL
when it goes to zero.
DNS Proxy with Split DNS
The split DNS proxy feature allows you to configure your proxy server to split the DNS query based on both the interface and the domain name. You can also configure a set of name servers and associate then with a given domain name. When you query that domain name, the device sends the DNS queries to only those name servers that are configured for that domain name to ensure localization of DNS queries.
You can configure the transport method used to resolve a given domain name—for example, when the device connects to the corporate network through an IPsec VPN or any other secure tunnel. When you configure a secure VPN tunnel to transport the domain names belonging to the corporate network, the DNS resolution queries are not leaked to the ISP DNS server and are contained within the corporate network.
You can also configure a set of default domain (*) and name servers under the default domain to resolve the DNS queries for a domain for which a name server is not configured.
Each DNS proxy must be associated with an interface. If an interface has no DNS proxy configuration, all the DNS queries received on that interface are dropped.
Figure 1 shows how the split DNS proxy works in a corporate network.
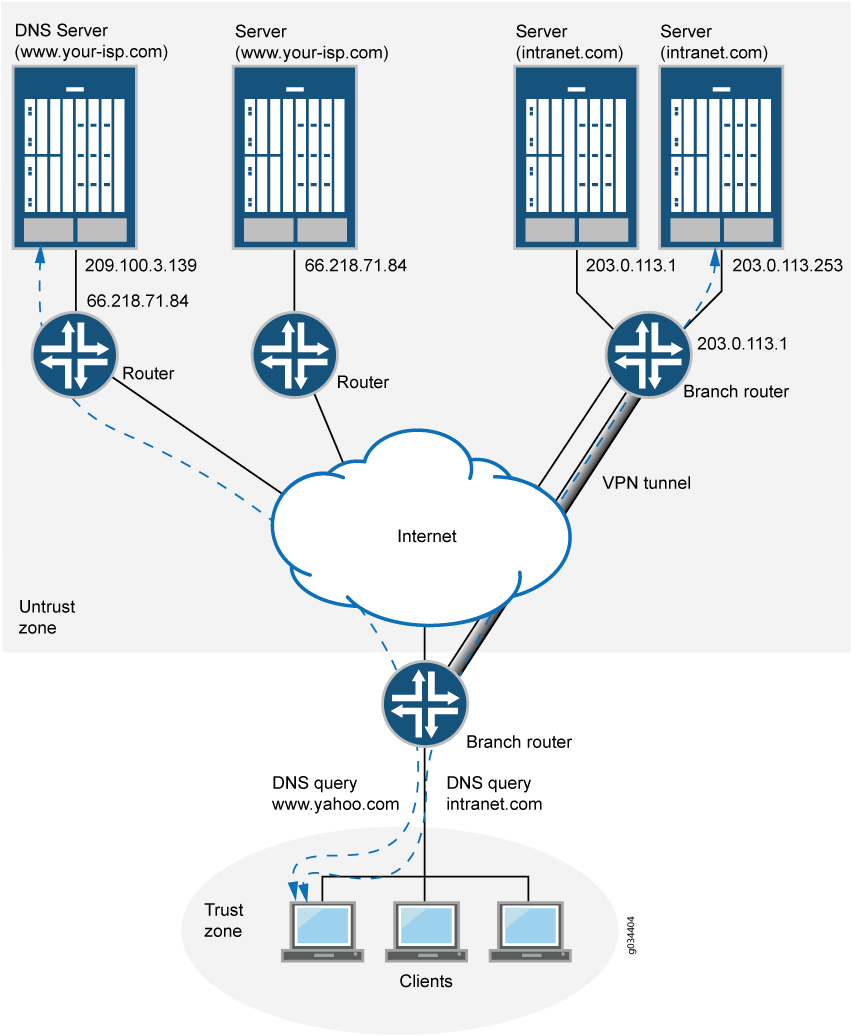
In the corporate network shown in Figure 1, a PC client that points to the SRX Series Firewall as its DNS server makes two queries—to www.your-isp.com and to www.intranet.com, The DNS proxy redirects the www.intranet.com, query to the www.intranet.com DNS server (203.0.113.253), while the www.your-isp.com query is redirected to the ISP DNS server (209.100.3.130). Although the query for www.your-isp.com is sent to the ISP DNS server as a regular DNS query using clear text protocols (TCP/UDP), the query for the www.intranet.com domain goes to the intranet’s DNS servers over a secure VPN tunnel.
A split DNS proxy has the following advantages:
-
Domain lookups are usually more efficient. For example, DNS queries meant for a corporate domain (such as acme.com) can go to the corporate DNS server exclusively, while all others go to the ISP DNS server. Splitting DNS lookups reduces the load on the corporate server and can also prevent corporate domain information from leaking onto the Internet.
-
A DNS proxy allows you to transmit selected DNS queries through a tunnel interface, which prevents malicious users from learning about the internal configuration of a network. For example, DNS queries bound for the corporate server can pass through a tunnel interface to use security features such as authentication and encryption.
Dynamic Domain Name System Client
Dynamic DNS (DDNS) allows clients to dynamically update IP addresses for registered domain names. This feature is useful when an ISP uses Point-to-Point Protocol (PPP), Dynamic Host Configuration Protocol (DHCP), or external authentication (XAuth) to dynamically change the IP address for a customer premises equipment (CPE) router (such as a security device) that protects a Web server. Internet clients can reach the Web server by using a domain name even if the IP address of the security device has previously changed dynamically.
A DDNS server maintains a list of the dynamically changed addresses and their associated domain names. The device updates these DDNS servers with this information periodically or in response to IP address changes. The Junos OS DDNS client supports popular DDNS servers such as dyndns.org and ddo.jp
Figure 2 illustrates how the DDNS client works.
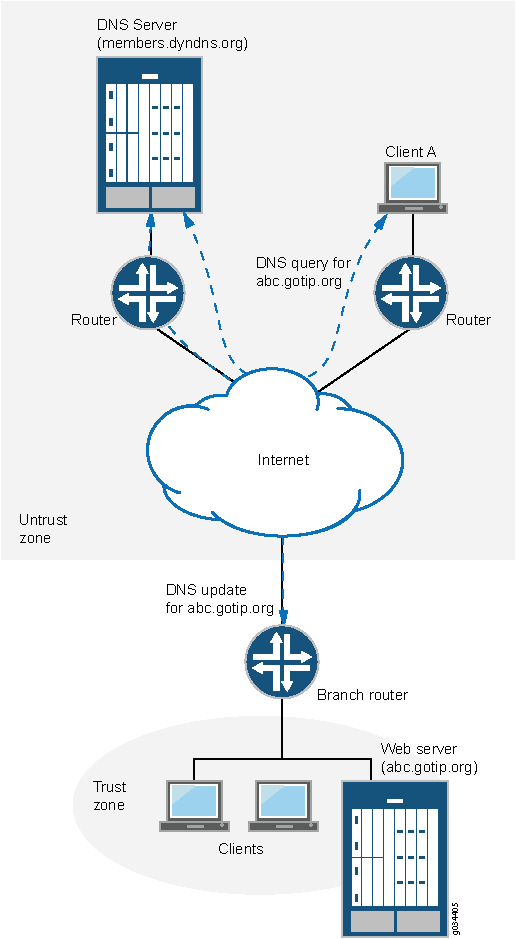
The IP address of the internal Web server is translated by Network Address Translation (NAT) to the IP address of the untrust zone interface on the device. The hostname abc-host.com is registered with the DDNS server and is associated with the IP address of the device’s untrust zone interface, which is monitored by the DDNS client on the device. When the IP address of abc-host.com is changed, the DDNS server is informed of the new address.
If a client in the network shown in Figure 2 needs to access abc-host.com, the client queries the DNS servers on the Internet. When the query reaches the DDNS server, it resolves the request and provides the client with the latest IP address of abc-host.com.
