Understanding How a RADIUS Server Controls Policy and Charging Control Rules
Policy control by a RADIUS server takes place when an aaa-policy-control policy and charging enforcement function (PCEF) profile is assigned to a subscriber. A RADIUS server activates and deactivates policy and charging control (PCC) rules that you have configured on the MX Series router and assigned to the PCEF profile. A network element, which is a load-balanced group of RADIUS servers, is assigned to the subscriber.
This topic includes the following sections:
Rule Activation When TDF Session Begins
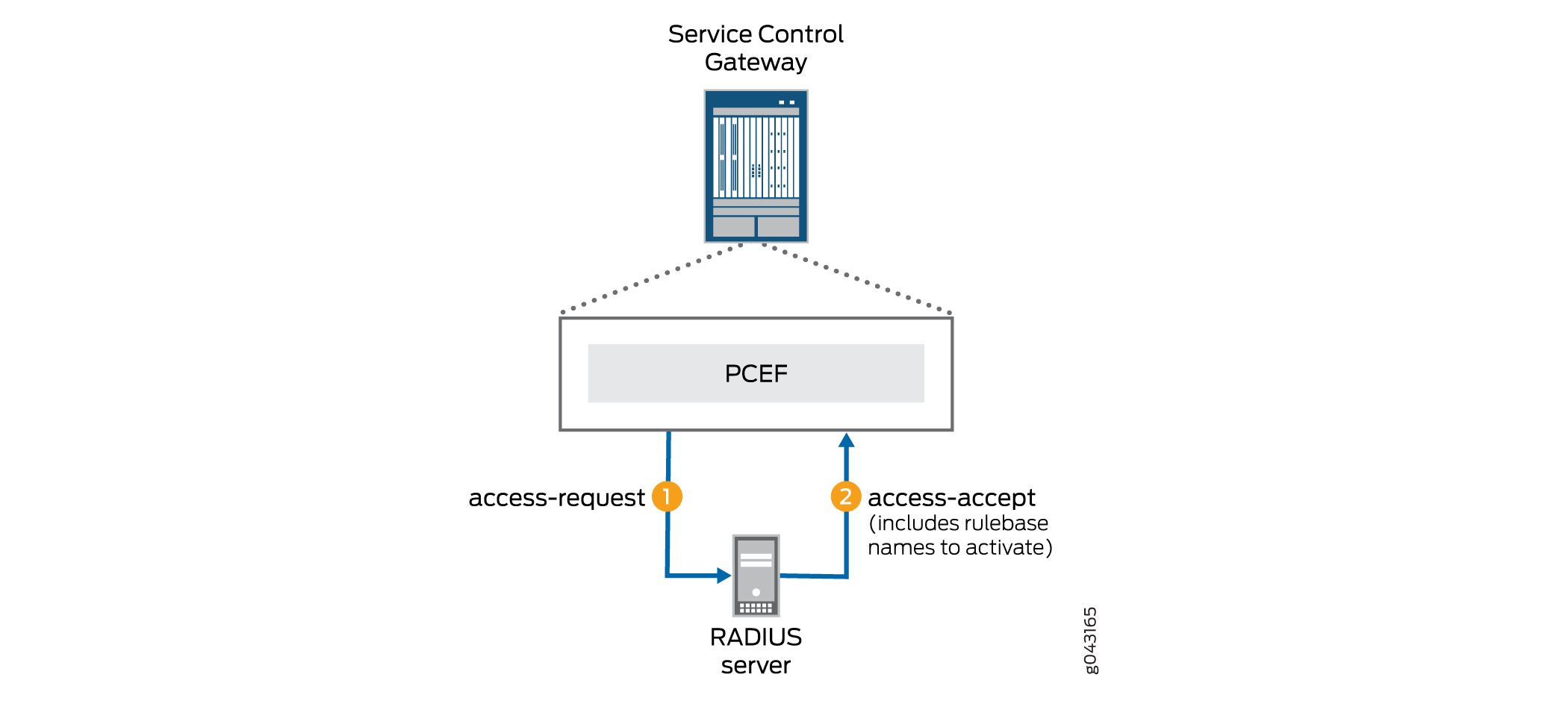
When the traffic detection function (TDF) subscriber session begins, the Junos Subscriber Aware PCEF sends an access request to the RADIUS server. This is shown in Figure 1. This access request includes the subscriber username, IP address, and other relevant AVP information that Subscriber Aware received from the broadband network gateway or Packet Data Network Gateway during the subscriber session setup.
The RADIUS server responds to the PCEF with an access-accept message, which contains the names of the rulebases to activate. You can configure the AVP that carries the name of a rulebase to be activated; by default the PCEF looks for a rulebase name in the ERX-Service-Activate Juniper vendor-specific attributes (VSA).
Rule Activation and Deactivation When RADIUS Server Sends Request
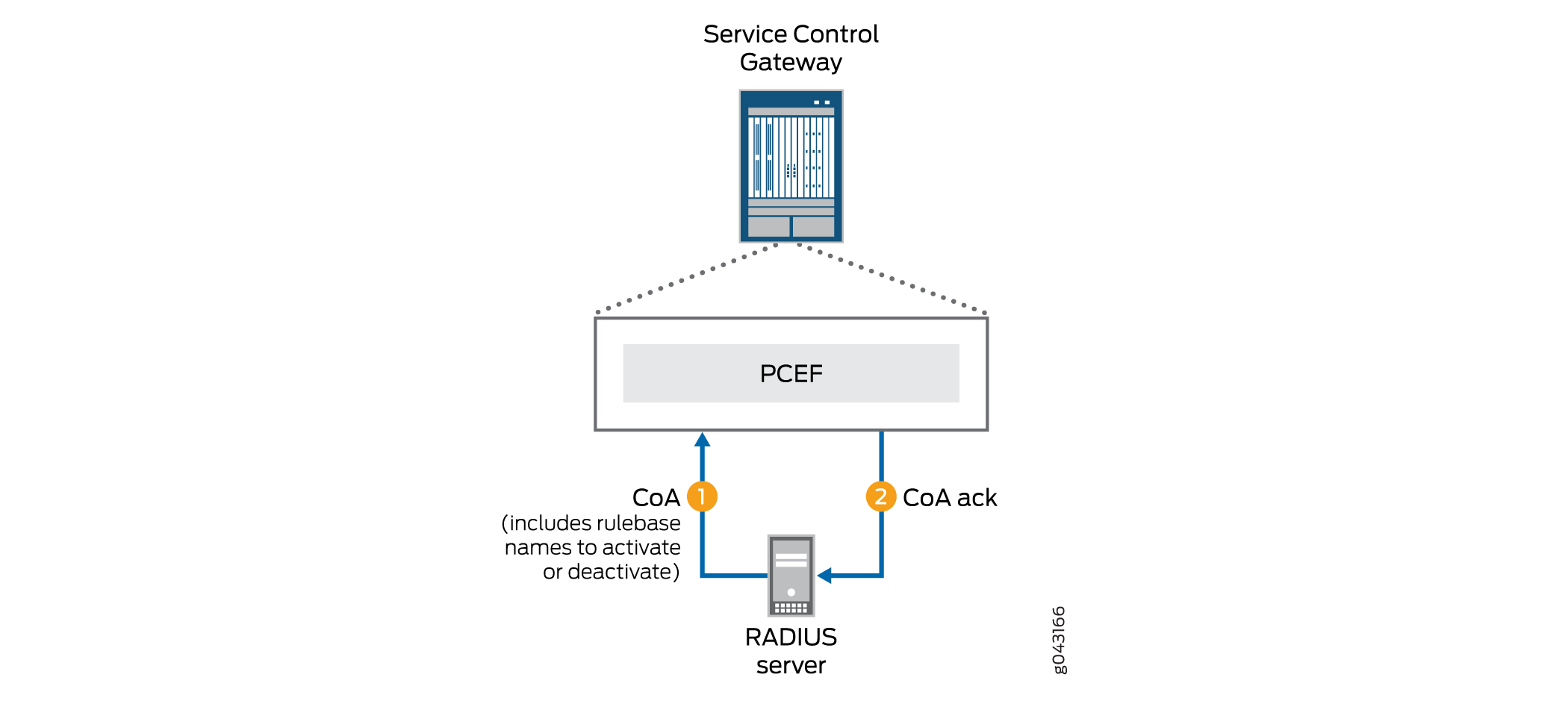
The RADIUS server can initiate the activation or deactivation of rulebases by sending a change of authorization (CoA) request to the PCEF, as shown in Figure 2. You can configure the AVP that carries the name of a rulebase to be activated; by default the PCEF looks for a rulebase name in the ERX-Service-Activate Juniper VSA. You can also configure the AVP that carries the name of a rulebase to be deactivated; by default the PCEF looks for a rulebase name in the ERX-Service-Deactivate Juniper VSA.
The PCEF responds to the CoA request by sending a CoA Ack to the RADIUS server.
Supported Attributes in RADIUS Messages
The following tables list the RADIUS attributes, 3GPP VSAs, and Juniper Networks VSAs that are supported in the RADIUS messages between the MX Series router and a RADIUS server.
Table 1 lists the RADIUS attributes and 3GPP VSAs that are supported in the access-request messages sent to the RADIUS server.
|
Attribute Number |
Attribute Name |
Description |
Content |
|---|---|---|---|
|
1 |
User-Name |
Username for the TDF subscriber if it is provided in the RADIUS accounting request received from the Packet Data Network Gateway (PGW) or broadband network gateway (BNG). This is a RADIUS IETF attribute. |
String |
|
2 |
User-Password |
User password configured in the subscriber’s PCEF profile. This is a RADIUS IETF attribute. |
String |
|
4 |
NAS-IP-Address |
IPv4 address of the MX Series router for communication with the RADIUS server. This is a RADIUS IETF attribute. |
IPv4 address |
|
8 |
Framed-IP-Address |
IPv4 address for the TDF subscriber if it is provided in the RADIUS accounting request received from the PGW or BNG. This is a RADIUS IETF attribute. |
IPv4 address |
|
31 |
Calling-Station-ID |
Identifier for the mobile station of the TDF subscriber if it is provided in the RADIUS accounting request received from the PGW or BNG. This is a RADIUS IETF attribute. |
MSISDN in international format, UTF-8 encoded decimal characters |
|
32 |
NAS-Identifier |
Identifier of the NAS originating the request. This is a RADIUS IETF attribute. |
String |
|
44 |
Acct-Session-ID |
User Session identifier generated by Subscriber Aware for the TDF subscriber. This is a RADIUS IETF attribute. |
UTF-8 encoded string |
|
97 |
Framed-IPv6-Prefix |
IPv6 prefix for the TDF subscriber if it is provided in the RADIUS accounting request received from the PGW or BNG. This is a RADIUS IETF attribute. |
Value indicating the prefix, as specified in RFC 3162 |
|
26/10415/1 (3GPP type 1) |
3GPP-IMSI |
IMSI for the TDF subscriber if it is provided in the RADIUS accounting request received from the PGW or BNG. This is a 3GPP VSA. |
UTF-8 encoded string |
Table 2 lists the VSAs that are supported in the Access-Accept messages sent from the RADIUS server to the PCEF.
|
Attribute Number |
Attribute Name |
Description |
Content |
|---|---|---|---|
|
26-65 |
ERX-Service-Activate |
Specifies a PCC rulebase to activate for the subscriber. Tagged VSA, which supports 8 tags (1-8). This is a Juniper Networks VSA and is the default VSA for carrying rulebase activations; you can also specify a different AVP code and vendor ID. |
string: rulebase-name |
Table 3 lists the VSAs that are supported in the CoA messages sent from the RADIUS server to the PCEF.
|
Attribute Number |
Attribute Name |
Description |
Content |
|---|---|---|---|
|
26-65 |
ERX-Service-Activate |
Specifies a PCC rulebase to activate for the subscriber. Tagged VSA, which supports 8 tags (1-8). This is a Juniper Networks VSA and is the default VSA for carrying rulebase activations; you can also specify a different AVP code and vendor ID. |
string: rulebase-name |
|
26-66 |
ERX-Service-Deactivate |
Specifies a PCC rulebase to deactivate for the subscriber. This is a Juniper Networks VSA and is the default VSA for carrying rulebase deactivations; you can also specify a different AVP code and vendor ID. |
string: rulebase-name |
