Transparent Web Proxy
Learn how to configure a transparent web proxy on SRX Series Firewalls with this step-by-step example.
You can use Transparent Web proxy to send traffic to an external proxy server and bypass the proxy server for the selected application traffic. Bypassed application traffic will be sent directly to the target webserver.
In addition, the transparent web-proxy functionality supports HTTP/2, allowing you to relay HTTPS traffic without decryption, ensuring secure and efficient data transmission.
Transparent web proxy allows you to route traffic through an external proxy server without the client browser being aware of it. That is, the proxy operates invisibly to the user, requiring no additional authentication or configuration on their part.
When using a transparent proxy, you can specify certain application traffic to bypass the proxy server. For example, if you want traffic from a specific application (like Yahoo) to go directly to the webserver, you can configure the proxy to exempt this traffic. This bypassed traffic will be sent straight to the target webserver, avoiding the proxy server entirely.
As a result, your firewall performs transparent proxy between the client and the webserver for the specified applications and provides better QoS for the application traffic.
Benefits of Transparent Web Proxy
- Enhances the quality of service for specific application traffic by establishing direct connections to the web server.
- Implements distinct security policies for various types of traffic, allowing you to bypass the proxy for trusted applications while directing other traffic through the proxy for further inspection.
- Bypasses the proxy for high-bandwidth applications like video streaming services, reducing the load on the proxy server and improving overall network performance.
- The proxy transparently processes HTTPS traffic via HTTP CONNECT, while seamlessly relaying all other traffic types—like plain HTTP and HTTP/2—to the client’s designated external proxy, ensuring broad protocol support without disrupting routing.
Limitations
- SRX Series Firewall does not support transparent web proxy or transparent web
proxy feature may not function properly in the following cases:
- When operating in chassis cluster mode or in Multinode High Availability.
- When configured with all layer 7 security features except Advanced policy-based routing (APBR).
- When configured with unified policies (security policies with dynamic applications).
- When operating in transparent-bridge mode.
- When the client device and its proxy server are deployed in the same network segment.
- Transparent proxy bypasses both plain HTTP/2 traffic and HTTP CONNECT requests sent in HTTP/2 frame format.
- SSL proxying must not be applied to sessions processed through the transparent proxy.
Transparent Web Proxy Overview
How Transparent Web Proxy Works?
When the SRX Series Firewall receives a request from a client, it examines the HTTP header to identify the application. Based on the transparent proxy profile, the firewall determines which traffic can bypass the external proxy server. It applies the profile to traffic that matches the security policy rules. Permitted application traffic that matches the dynamic application specified in the profile is directed to the webserver. Otherwise, the permitted traffic is redirected to the configured external proxy server.
For example, if you want to bypass MS Office or Yahoo traffic from external proxy server, you can specify these applications in the transparent web proxy profile. The SRX Series Firewall forwards Yahoo or SMS Office application traffic directly to the server, bypassing the external proxy server. Connections that do not match the applications are routed to the external proxy server.
Following illustrations show how an SRX Series Firewall provides the transparent Web proxy service.
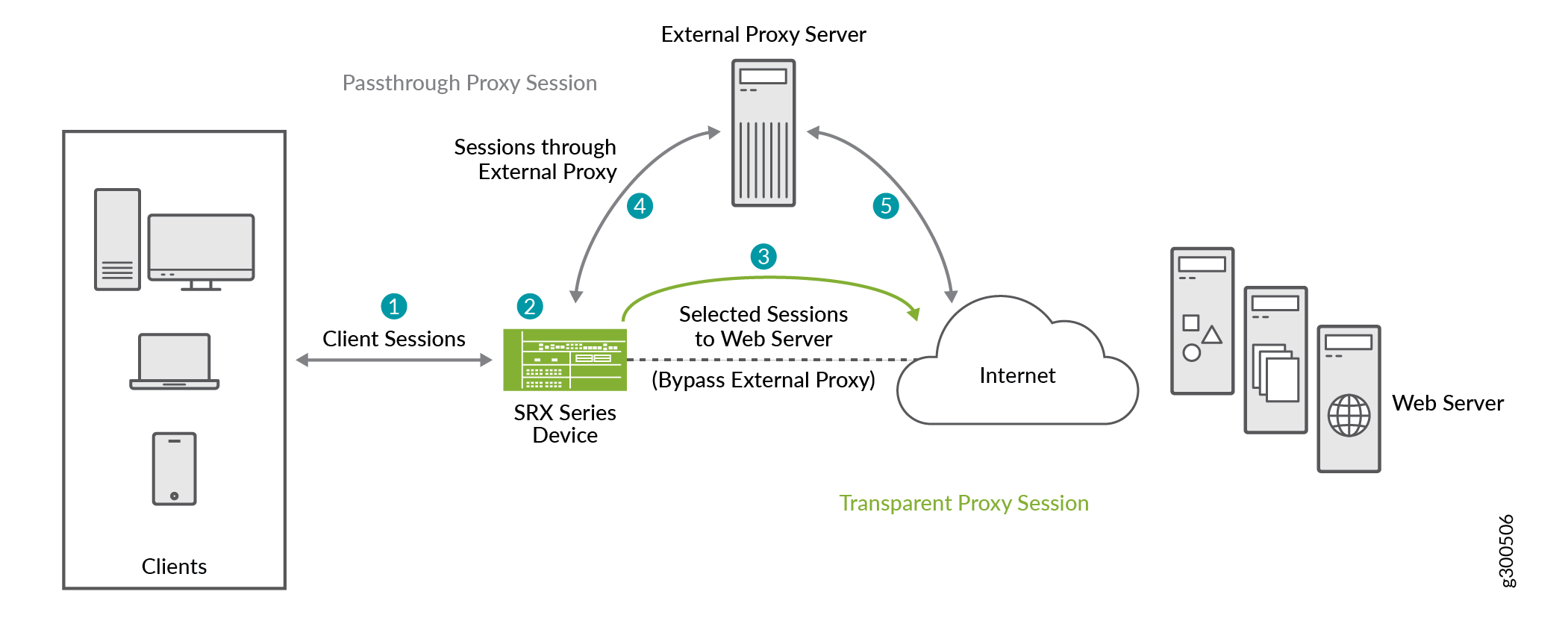
-
The client's browser sends an HTTP connect request to the external proxy server.
-
The SRX Series Firewall intercepts the TCP connections. The device identifies the application in the HTTP header and does a DNS resolution.
-
If the traffic parameters match the security policy rules and the transparent Web proxy profile specifications, the SRX Series Firewall operates in transparent mode. The device uses the client's IP address in transparent mode to initiate a new connection with the webserver, bypassing the external proxy server.
-
For the remaining traffic, the SRX Series Firewall operates in pass-through mode and allows the HTTP connect request to go to the external proxy server. When a client makes a request, the request is sent to the proxy server first, which then forwards the request to the actual server.
- The server responds to the proxy, and the proxy then sends the response back to the client through SRX Series Firewall.
The SRX Series Firewall performs secure Web proxy through the following steps:
To use transparent Web proxy on your SRX Series Firewall, you must:
-
Create a transparent web proxy profile with external proxy server details and the dynamic application or application group that you want to bypass the external proxy server.
- Create a security policy to manage the traffic passing through the device.
- Attach the secure Web proxy profile to the security policy and apply the profile as an application service for the permitted traffic.
Transparent Web Proxy for HTTP/2 Traffic
The transparent web-proxy's support for HTTP/2 allows you to relay encrypted HTTPS traffic using the HTTP/2 protocol without decrypting it. This capability ensures that the ALPN extension used during TLS negotiations is not interfered with, enabling seamless client/server communication. By adopting HTTP/2, your network benefits from features like multiplexing, header compression, and prioritization. These features improve web communication speed and efficiency, offering a more responsive user experience.
Transparent Web Proxy and Secure Web Proxy
Starting in Junos OS Release 25.2R1, we've renamed the secure web proxy as transparent web proxy.
Read one of the following topic for configuring using transparent proxy:
-
If you are using Junos OS version 25.2R1 and later releases, you must configure Transparent Web proxy for same benefits as secure web proxy. See Example: Configure Transparent Web Proxy.
-
If you are using Junos OS version before Junos OS 25.2R1, you can continue to use Secure Web proxy. See Secure Web Proxy.
CLI Configuration Statements Changes
If you are planning to upgrade to Junos OS Release 25.2R1 and later releases, note the following points regarding using proxy functionality:
All existing secure web proxy related CLI statements and commands are
deprecated. That is—Starting in Junos OS Release 25.2R1 secure web proxy
functionality is deprecated— rather than immediately removed—to provide
backward compatibility and an opportunity to bring your configuration into
compliance with the new configuration. As a part of this change, the
[edit services web-proxy secure-proxy] hierarchy and
all the configuration options under this hierarchy are deprecated. That is,
the hierarchy for transparent proxy configuration statements has changed
from set services web-proxy secure-proxy to set
services web-proxy transparent-proxy.
To migrate, you will need to replace existing command hierarchies with the new ones as shown in the following table.
| Previous Hierarchy (Secure Web Proxy) | New Hierarchy (Transparent Web Proxy) |
|---|---|
set services web-proxy
secure-proxy
|
set services web-proxy
transparent-proxy
|
set security policies from-zone trust to-zone
untrust policy apply_webproxy then permit
application-services web-proxy profile-name
<trans-proxy-profile-name>
|
set security policies from-zone trust to-zone
untrust policy apply_webproxy then permit
application-services transparent-proxy profile-name
<trans-proxy-profile-name>
|
These adjustments ensure that your configurations are up-to-date and ready to take advantage of the new features.
Example: Configure Transparent Web Proxy
You can use the Transparent wb proxy feature to direct the traffic through an external proxy server or bypass it for specified applications on an SRX Series Firewall. By configuring a transparent Web proxy profile with the external proxy server details and applications to bypass, you ensure traffic is sent directly to the target webserver when applicable. The device inspects HTTP headers and applies the web proxy profile based on security policy rules, redirecting authorized traffic accordingly.
In this example, we’ll configure transparent web proxy to direct an application traffic to the webserver bypassing external proxy server.
|
Reading Time |
15 minutes |
|
Configuration Time |
30 minutes |
- Example Prerequisites
- Before You Begin
- Functional Overview
- Topology Illustration
- Topology Overview
- Configure Transparent Web Proxy
- Verification
- Set Commands on All Devices
- Show Configuration Output
Example Prerequisites
Table 3 lists the hardware and software components that support the configuration.
|
Hardware requirements |
Supported SRX Series Firewalls and vSRX Virtual Firewalls. We’ve tested this example using vSRX instance. |
|
Software requirements |
Junos OS Release 25.2R1. IP address and port number of the external proxy server. Install and configure Application Identification (AppID). For details, see Predefined Application Signatures for Application Identification. A valid application identification feature license on your SRX Series Firewall. See Managing Junos OS Licenses. |
Before You Begin
|
Know more |
|
|
Learn more |
Functional Overview
Table 4 provides a quick summary of the configuration components deployed in this example.
|
Technologies used |
|
|
Primary verification tasks |
Topology Illustration
Following figure shows the topology used in this configuration example.
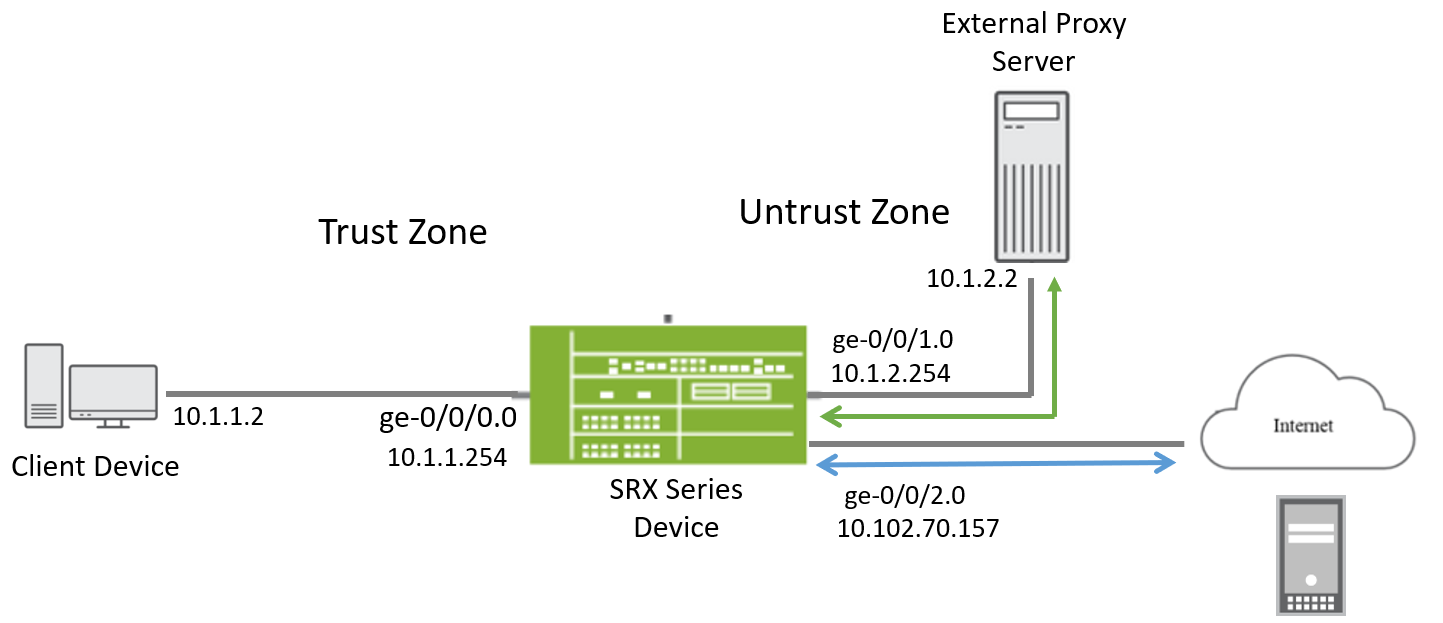
In this example, you configure a transparent web proxy profile on the SRX Series Firewall that forwards most outbound web traffic through the external proxy server. However, traffic destined for specific dynamic applications—such as Yahoo—should bypass the proxy and be forwarded directly to the Internet through the ge-0/0/2.0 interface.
Traffic flow in a transparent web proxy scenario is as follows:
(For regular traffic)
- The client in the trust zone (IP:
10.1.1.2) initiates a web request (e.g., to a general website). - This traffic reaches the SRX firewall via interface
ge-0/0/0.0. The firewall evaluates the traffic against the transparent web proxy profile. Since the traffic is not identified as Yahoo , it is redirected to the external proxy server at10.1.2.2via interfacege-0/0/1.0. - The proxy server then forwards the request to the Internet through its own route.
- The response from the Internet returns to the proxy server, which then
sends it back to the SRX via
ge-0/0/1.0, and the firewall forwards it to the client.
(For Yahoo-specific traffic)
- The client sends a request to a Yahoo service (e.g., mail.yahoo.com).
- The SRX firewall receives this on
ge-0/0/0.0and uses application identification to detect that the traffic is Yahoo-related. - Because Yahoo is exempted in the proxy profile, the firewall bypasses the external proxy .
- Instead, it forwards the traffic directly to the Internet via interface
ge-0/0/2.0. - The response comes back through
ge-0/0/2.0and is routed directly to the client viage-0/0/0.0.
The firewall enforces zone-based policies to control traffic between Trust and Untrust zones.
Our lab environment uses the interface NAT feature to translate internal IPs for outbound Internet access. This example was set up and tested with this lab-specific NAT configuration for outbound traffic from the SRX Series Firewall and does not include NAT configuration details.
Topology Overview
Table 5 shows the details of configuration used in this example.
| Device | Interface | IP Address | Zone | Configured For |
|---|---|---|---|---|
| SRX Series Firewall |
ge-0/0/0 |
10.1.1.254/24 |
Trust |
Connects to client desktop. |
|
ge-0/0/1 |
10.1.2.254/24 |
Untrust |
Connects to proxy server. | |
|
ge-0/0/2 |
10.102.70.157 |
Untrust |
Connects to Internet. |
Configuration Objects:
-
Transparent proxy profile:
- Define the external proxy server's IP (10.1.2.2) and port.
- Apply the profile to outbound HTTP/HTTPS traffic from the Trust zone.
-
Application-based proxy bypass:
- Use application identification to detect Yahoo traffic.
- Exempt Yahoo traffic from proxy redirection.
-
Traffic flow behavior:
- Yahoo traffic: Routed directly to the Internet via ge-0/0/2.0, bypassing the proxy.
- All other web traffic: Redirected to the external proxy server via ge-0/0/1.0.
Configure Transparent Web Proxy
Use the following steps:
Verification
Use the following show commands to verify the feature in this example.
| Commands | Verification Task |
|---|---|
|
|
Display transparent web proxy session details. |
show services web-proxy transparent-proxy
statistics
|
Display transparent web proxy statistics. |
Check Transparent Web Proxy Session Detail
Purpose
View and verify the details of transparent web proxy session.
Action
From operational mode, run the following commands:
user@host> show services web-proxy transparent-proxy session detail Transparent Proxy sessions: Client Session ID : 8590193205, Proxy Session ID: 8590193206 Client: 10.1.2.254/13250 ---> 10.1.2.2/8080 Proxy : 10.1.1.2/35662 ---> 69.147.88.7/443 Proxy Request: CONNECT:www.yahoo.com:443 Dynamic Web App: junos:YAHOO Client Session ID : 8590193212, Proxy Session ID: 8590193213 Client: 10.1.2.254/13739 ---> 10.1.2.2/8080 Proxy : 10.1.1.2/35680 ---> 69.147.88.8/443 Proxy Request: CONNECT:www.yahoo.com:443 Dynamic Web App: junos:YAHOO Client Session ID : 8590193210, Proxy Session ID: 8590193211 Client: 10.1.2.254/24706 ---> 10.1.2.2/8080 Proxy : 10.1.1.2/35672 ---> 74.6.231.20/443 Proxy Request: CONNECT:yahoo.com:443 Dynamic Web App: junos:YAHOO
user@host> show services web-proxy transparent-proxy session summary Transparent Proxy sessions: Client Session Proxy Session [8590193288] 10.1.2.254/28677 ---> 10.1.2.2/8080 [8590193289] 10.1.1.2/48870 ---> 69.147.88.7/443
Meaning
In these samples, observe the client and proxy session details. The client session extends from the SRX Series Firewall to the proxy server. The proxy session connects the client device directly to the webserver. Additionally, you can observe proxy requests and dynamic web applications.
Our lab uses the interface NAT configuration for outbound Internet access. The sample output reflects this setup, showing NATed IPs and ports specific to our lab configuration.
Check Transparent Web Proxy Statistics
Purpose
View transparent web proxy session statistics.
Action
From operational mode, run the following command:
user@host> show services web-proxy transparent-proxy statistics
Transparent Proxy :
Active Transparent proxy sessions 0
Active Passthrough sessions 0
Active HTTP passthrough sessions 0
Active HTTPS passthrough sessions 0
Total Transparent proxy sessions 4
Total Passthrough sessions 0
Total HTTP Passthrough sessions 0
Total HTTPS Passthrough sessions 0
Meaning
Output displays that the number of transparent web proxy sessions. The proxy has handled four sessions in total, all through the transparent proxy. There are no passthrough (bypassed) sessions have occurred.
Set Commands on All Devices
Set Commands on SRX Series Firewall
set services application-identification set services web-proxy transparent-proxy profile yahoo-profile proxy-address external_proxy ip 10.1.2.2/32 set services web-proxy transparent-proxy profile yahoo-profile proxy-address external_proxy port 8080 set services web-proxy transparent-proxy profile yahoo-profile dynamic-web-application junos:YAHOO set security policies from-zone trust to-zone untrust policy policy-for-transparent-proxy match source-address any set security policies from-zone trust to-zone untrust policy policy-for-transparent-proxy match destination-address any set security policies from-zone trust to-zone untrust policy policy-for-transparent-proxy match application any set security policies from-zone trust to-zone untrust policy policy-for-transparent-proxy then permit application-services transparent-proxy profile-name yahoo-profile set security policies pre-id-default-policy then log session-close set security zones security-zone trust host-inbound-traffic system-services all set security zones security-zone trust host-inbound-traffic protocols all set security zones security-zone trust interfaces ge-0/0/0.0 set security zones security-zone untrust host-inbound-traffic system-services all set security zones security-zone untrust interfaces ge-0/0/2.0 set security zones security-zone untrust interfaces ge-0/0/1.0 set interfaces ge-0/0/0 unit 0 family inet address 10.1.1.254/24 set interfaces ge-0/0/1 unit 0 family inet address 10.1.2.254/24 set interfaces ge-0/0/2 unit 0 family inet address 10.102.70.157/24
Show Configuration Output
From configuration mode, confirm your configuration by entering the show
commands. If the output does not display the intended configuration,
repeat the configuration instructions in this example to correct it.
Transparent Web Proxy
[edit]
user@host# show services
application-identification;
web-proxy {
transparent-proxy {
profile yahoo-profile {
proxy-address external_proxy {
ip 10.1.2.2/32;
port 8080;
}
dynamic-web-application junos:YAHOO;
}
}
}
Security Policies
[edit]
user@host# show security policies
policy policy-for-transparent-proxy {
match {
source-address any;
destination-address any;
application any;
}
then {
permit {
application-services {
transparent-proxy {
profile-name yahoo-profile;
}
}
}
}
Security Zones
[edit]
user@host# show security zones
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
ge-0/0/0.0;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
all;
}
}
interfaces {
ge-0/0/2.0;
ge-0/0/1.0;
}
}
Interfaces
[edit]
user@host# show interfaces
ge-0/0/0 {
unit 0 {
family inet {
address 10.1.1.254/24;
}
}
}
ge-0/0/1 {
unit 0 {
family inet {
address 10.1.2.254/24;
}
}
}
ge-0/0/2 {
unit 0 {
family inet {
address 10.102.70.157/24;
}
}
}