Security Policies Overview
To secure their business, organizations must control access to their LAN and their resources. Security policies are commonly used for this purpose. Secure access is required both within the company across the LAN and in its interactions with external networks such as the Internet. Junos OS provides powerful network security features through its stateful firewall, application firewall, and user identity firewall. All three types of firewall enforcement are implemented through security policies. The stateful firewall policy syntax is widened to include additional tuples for the application firewall and the user identity firewall.
In a Junos OS stateful firewall, the security policies enforce rules for transit traffic, in terms of what traffic can pass through the firewall, and the actions that need to take place on traffic as it passes through the firewall. From the perspective of security policies, the traffic enters one security zone and exits another security zone. This combination of a from-zone and to-zone is called a context. Each context contains an ordered list of policies. Each policy is processed in the order that it is defined within a context.
A security policy, which can be configured from the user interface, controls the traffic flow from one zone to another zone by defining the kind(s) of traffic permitted from specified IP sources to specified IP destinations at scheduled times.
Policies allow you to deny, permit, reject (deny and send a TCP RST or ICMP port unreachable message to the source host), encrypt and decrypt, authenticate, prioritize, schedule, filter, and monitor the traffic attempting to cross from one security zone to another. You decide which users and what data can enter and exit, and when and where they can go.
An SRX Series Firewall secures a network by inspecting, and then allowing or denying, all connection attempts that require passage from one security zone to another.
Logging capability can also be enabled with security policies during session
initialization (session-init) or session close
(session-close) stage.
-
To view logs from denied connections, enable log on
session-init. -
To log sessions after their conclusion/tear-down, enable log on
session-close.
Session log is enabled at real time in the flow code which impacts the user
performance. If both session-close and
session-init are enabled, performance is further degraded as
compared to enabling session-init only.
Through the creation of policies, you can control the traffic flow from zone to zone by defining the kinds of traffic permitted to pass from specified sources to specified destinations at scheduled times.
At the broadest level, you can allow all kinds of traffic from any source in one zone to any destination in all other zones without any scheduling restrictions. At the narrowest level, you can create a policy that allows only one kind of traffic between a specified host in one zone and another specified host in another zone during a scheduled interval of time. See Figure 1.
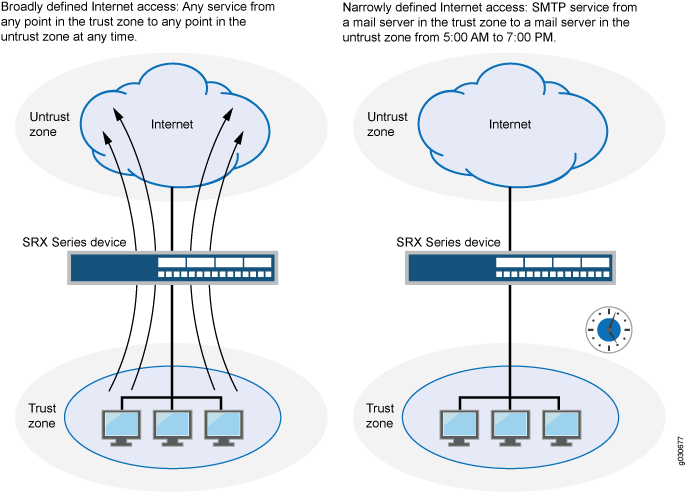
Every time a packet attempts to pass from one zone to another or between two interfaces bound to the same zone, the device checks for a policy that permits such traffic (see Understanding Security Zones and Example: Configuring Security Policy Applications and Application Sets). To allow traffic to pass from one security zone to another—for example, from zone A to zone B—you must configure a policy that permits zone A to send traffic to zone B. To allow traffic to flow the other way, you must configure another policy permitting traffic from zone B to zone A.
To allow data traffic to pass between zones, you must configure firewall policies.
Platform-Specific Security Policies Behavior
Use Feature Explorer to confirm platform and release support for specific features.
Use the following table to review platform-specific behavior for your platform:
|
Platform |
Difference |
|---|---|
|
SRX Series |
SRX300, SRX320, SRX340, SRX345, SRX380, and SRX550M devices that support a factory-default security policy:
|
|
