IoT Security Overview
Read this guide to understand about the IoT security solution available on your SRX Series/NFX Series devices and learn how to start using the feature.
Read this topic to learn about Juniper Networks security IoT and how it helps to get visibility into IoT devices in your network.
Introduction
In terms of scale, the Internet of Things (IoT) is taking over the network. As a technology, IoT is transformational, enriching data, adding context into processes, and providing unprecedented levels of visibility across organizations. The volume and variety of IoT devices such as IP cameras, smart elevators, medical equipment, and industrial controllers can add complexity in your network security. With so many devices on the network, you need real-time visibility, intelligent policy enforcement capabilities that work seamlessly across the network. Most IoT endpoints have limited footprints and unknown devices the network can be a reason for security incident.
Knowledge of IoT devices in a network allows users or network administrators to better manage their network security. It is even more important to have visibility of IoT devices in a network especially since zero-day vulnerabilities are exploding.
Juniper Networks security IoT solution provides discovery, visibility, and classification of IoT devices in the network. IoT device visibility helps you to continuously discover, monitor and enforce security policies across all connected IoT devices.
Security IoT Solution
The Juniper Networks Security IoT solution involves the integration of security devices with Juniper ATP Cloud to:
- Provide deep insight into IOT devices in the network in real-time
- Create security policies using the discovered IoT device's attributes
- Enforce security policies to prevent attacks and reduce attack surface
IOT device discovery provides basis for enforcing security policies and address security risk by identifying abnormal behavior of discovered devices.
Features
- Discovery of IoT devices behind Wi-Fi access point
- Support for broad range of IoT devices
- Granular fingerprints on each device including type, brand, model, IP, MAC address
- Single pane of glass for efficient IoT device inventory and classification
- Granular security rules based on IoT device attributes
Benefits of Security IOT
- Discovering and managing all IoT devices in a network without manual intervention increases security operations efficiency and productivity
- Having an real-time inventory of IoT devices and related security policies helps in reducing attack surface within your network.
Use Cases
Security IoT solution is adaptable different environments including healthcare/medical industry, organizations with campus/branch offices, and other industries with smart buildings and offices.
IoT Device Discovery and Security Enforcement - Workflow
Terminology
Let’s get familiar with some of the terminologies in this document before we deep-dive into IoT device discovery and security enforcement.
| IOT Terms | Description |
|---|---|
| IoT devices | IoT devices are the physical devices that establish a wireless connection to a network and can transmit data over the Internet or other networks. IoT devices can be sensors, gadgets, appliances, or machines or embedded into other mobile devices, industrial equipment, environmental sensors, medical devices, and more. |
| Data streaming |
Process of transmitting packets and related metadata from IoT devices to a Juniper ATP Cloud to identify and classify IoT devices. |
| Web socket | A communications protocol is used for bi-directional data transfer between the security device and Juniper ATP cloud to provide confidentiality. |
| Serialization | Protocol buffers (gpb) format used to serialize structured data and enable communication between security device and ATP cloud. |
| Authentication | Process of enabling secure communication between security device and Juniper ATP cloud using TLS1.2 or later versions to ensure authentication, encryption, and integrity of the shared data. |
| IoT device discovery |
Process of identifying IoT devices by searching through an internal database using the streamed data. The details of the discovered IoT devices includes-device brand, type, model, operating system, manufacturer, and so on. Security IoT supports HTTP, DNS, DHCP, SSL, and UPNP protocols for IoT device discovery. |
| IoT device classification |
Building a profile for the discovered IoT devices. Since an IoT device can belong to a wide range of device types, knowing the class of the IoT device is important for enforcing the right type of security policy. Example: An infotainment IoT device has a different traffic profile compared to an industrial IoT device. |
| Data Filtering |
Using data filter helps Juniper ATP Cloud to control the amount of data, type of data it receives from the security device. Filters are especially useful where a large number of IoT devices are available in the network. Security IoT does not support IPv6-based filters. |
| IP address feeds/dynamic address groups |
A dynamic address entry is a group of IP addresses, that share a common purpose or attribute such as a geographical origin, a threat type, or a threat level. IP addresses of discovered IoT devices are grouped into a dynamic address group. You can use IP address feeds to enforce policy in real time secure network. |
IoT Device Discovery and Enforcement Workflow
Following illustration depicts a typical workflow involved in IOT device discovery.
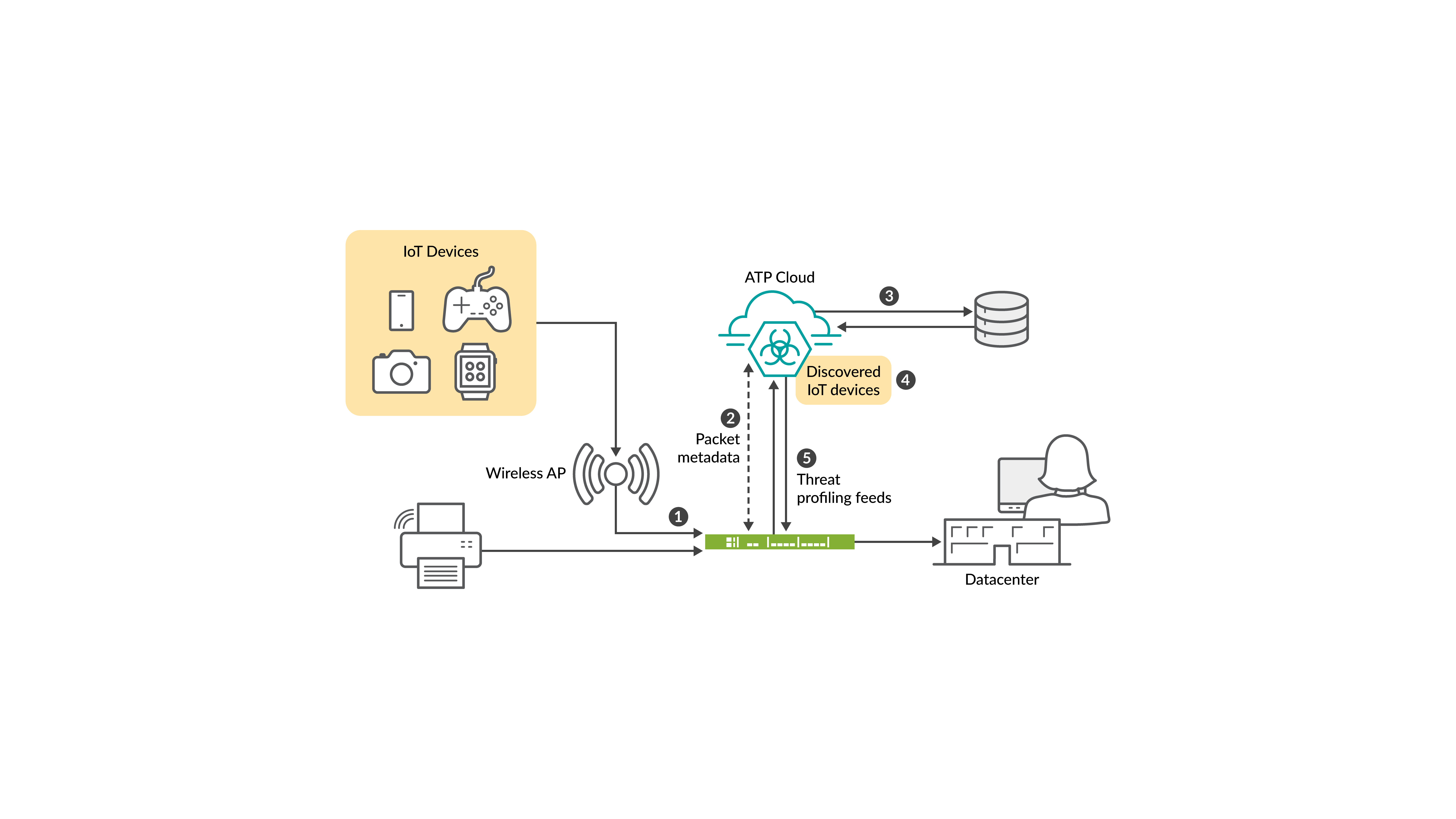
- Security device inspects network traffic from IoT devices.
- Security device connects to Juniper ATP cloud and streams details to the Juniper ATP cloud. The details include metadata about traffic flow, and packet payloads.
- Juniper ATP Cloud uses the streamed data to get the details of the IoT device such as brand, device model, class, vendor, IP, MAC address, and other properties of IoT devices.
- Juniper ATP Cloud successfully classifies the IoT device. The devices that Juniper ATP Cloud discovers and identifies appear on the Juniper ATP Cloud page. You can use the device details to create a IP address feeds in the form of dynamic address group using adaptive threat profiling feature.
- The security device downloads the feed. You can create security rules based on the IP address feeds to enforce granular security rules based on the IoT device attributes.
The security device continues to analyze the traffic pattern of the discovered IoT devices and detect any traffic deviation (for example, reachability and amount of traffic it might send) for these devices. You can isolate an IoT device from the network depending on the policy, and enforce a customized security policy to limit the reach of these devices in the network.
What's Next?
In the next section, you'll learn how to configure IoT device discovery and enforcement on your security device.
