Selective Class-based Filtering on PTX Routers
Selective Class-based Filtering on PTX Routers
For supported PTX Series routers and line cards, you can filter IPv4 and IPv6 traffic based on the source or destination classification (Source Class Usage, SCU) and (Destination Class Usage, DCU). This is useful because it means you can apply a filter selectively, on a subset of packets in a class, rather than all packets in the class. In addition, the packet flow through the packet forwarding engine (PFE) is optimized, and the filtering is more efficient.
For service providers, class-based filtering allows you to provide advanced services such as:
-
Per-hop behavior manipulation by adjusting the forwarding class of the packet based on the source or destination packet class and other filter criteria.
-
Traffic rate limiting towards certain customer interfaces, with high volume of traffic to drop (for example, under DDoS attack). Normally, you would deploy an outgoing interface filter to rate limit the traffic. However, this may be inefficient because traffic still crosses the fabric in distributed systems and consumes limited fabric bandwidth. The inefficiency becomes even more visible in a Virtual Output Queueing system, like PTX, where admission into the egress queue is happening before the output filter is executed and any subsequent drop action in the output filter requires compensation – more traffic needs to be admitted into the queue, which requires more fabric bandwidth and more egress on-chip buffer space (which is a limited resource). Class-based filters are executed in the ingress pipeline before admission of the packets into the egress queue. This mechanism is recommended over regular output interface filters, if you expect to drop large volumes of traffic towards certain destinations.
Class-based filtering is also effective for "low-and-slow" DoS attacks that target application and server resources by mimicking normal traffic patterns.
To support class-based filtering, two new bind points are introduced at the
forwarding table for PTX routers: source-class and
destination-class.
The CLI hierarchy is shown here, where src-class-name or dest-class-name is the name of the filter you defined in the corresponding policy.
routing-options forwarding-table source-class src-class-name family [inet | inet6] filter <filter-name>
routing-options forwarding-table destination-class dest-class-name family [inet | inet6] filter <filter-name>
You can also configure instance-specific filters across multiple SCU and DCU classes. By default, only one set of counters and policers is instantiated for a filter. In the instance-specific filter, separate set of counters and policers is created for each filter attach point.
firewall family [inet | inet6] filter <filter name> instance-specific
Understanding Class-based Filtering on PTX Routers
Initially, Source Class Usage (SCU) feature was introduced to provide statistics breakdown of traffic sent towards specific interface per originating prefix (identified by the source class). Destination Class Usage (DCU) was originally introduced to provide statistics breakdown of traffic received on an interface per destination prefix (identified by the destination class).
Both source or destination classes are assigned to the packet in the source or destination lookup process. Therefore, source and destination filter match conditions can be evaluated only if the filter is executed after the lookup.
Juniper routers support multiple filter bind points, those that may leverage the result of the source and destination classification are listed below, with usage guidelines:
-
Output interface filter (set interfaces <interface name> family inet filter <output>. Supported on any PTX platform, but not recommended if it is expected to discard large volumes of traffic in a steady state (for example, when implementing a DDoS attack mitigation filter). Discarded DDoS attack traffic may not be compensated by other traffic not matching DDoS attack criteria due to limited fabric bandwidth and limited egress on-chip buffer space.
-
Filter after forwarding table filter lookup (set forwarding-options family inet filter <filter-name> output). Supported on Express 2 (PE) and Express 3 (ZX) platforms. However, the filters are instantiated in the egress pipeline, therefore the discard behavior is similar to the regular output interface filter.
-
Source or destination class specific bind point (set routing-options forwarding-table source-class src-class-name family [inet | inet6] filter <filter- name>). Supported on Express 2 (PE), Express 3 (ZX) and Express 4 (BT) platforms. This filter is instantiated in the ingress pipeline. This is the recommended option to discard large volumes of traffic. This option is also recommended if you need to override forwarding class and subsequently output queue assignment. In a Virtual Output Queueing system, queue is selected in the ingress pipeline and any override must happen in the ingress pipeline too.
-
Note, these filter actions are not supported in the filter bound to the source or destination class specific bind point:
-
routing-instance
-
next-ip
-
next-interface
-
decapsulate
-
encapsulate
-
-
Selective class-based filters cannot be applied on host-bound packets.
-
Packets which fail uRPF lookups, but are restored by uRPF fail-filters are not subject to SCU/DCU lookups. Hence, selective class-based filters cannot be applied on such packets.
-
Filters are applied only to packets ingressing on interfaces which have SCU/DCU feature enabled. This means filters would be applied irrespective of whether SCU is configured on output interfaces or not.
-
Packets for which selective class-based filter needs to be applied may cause drop in performance. Performance drop would be function of rate of incoming traffic, average packets size, and amount of traffic subjected to the filters. However, packets on which selective class-based filters are not applied, do not affect performance.
-
DCU accounting is applicable for packets dropped by filters.
-
SCU output accounting is not applicable for packets dropped by filters.
-
Selective class-based filters cannot be used with interface-specific knob because this knob is only applicable to interface-attached filters.
-
Lists (input/output lists) of selective class-based filters are not supported.
-
Logical systems are not supported.
-
Only IPv4 and IPv6 are the supported payload protocols. MPLS is not supported.
-
If a packet matches both SCU and DCU selective class-based filters then only the last filter (i.e., DCU filter) is applied to the packet and but not both filters.
Example: Selective Class Based Filtering (PTX Routers)
This example shows how to apply firewall actions (discard, reject, or police) to IPv4 and IPv6 traffic flows on the basis of source or destination classification. It applies to PTX10001-36MR, PTX10003-160C, PTX10003-80C, PTX10004, and PTX10008 routers running Junos Evolved OS release 21.2, PTX10016 routers running JUNOS Evolved OS release 21.4, or PTX3000, PTX-5000, PTX1000, PTX10002, PTX10008, PTX10016 routers running Junos OS release 21.2 or later software.
Requirements
This example uses BGP because BGP can be used to exchange routes between devices in a network topology consisting of customer edge, provider edge, and provider routers. Refer BGP Configuration Overview to read more.
Overview
This example uses three routing devices: a customer edge (CE) device, a provider edge (PE) device, and a provider core (P) device. The configuration for IPv4 traffic is shown, and includes two sets of SCU and DCU classes, plus the firewall filters. In the following figure, the /32 IP prefixes represent hosts connected to the customer edge (CE) and provider (P) routers respectively.
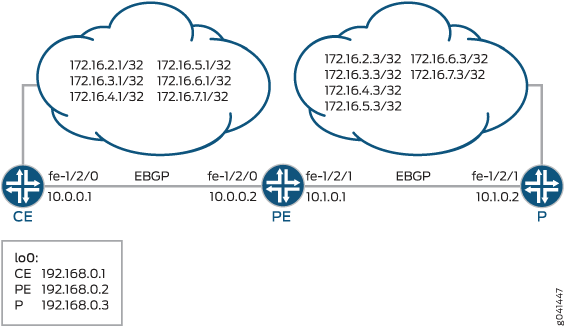
In this example, we define two classes of traffic: scu-1 and scu-2, the first one is assigned to prefixes in the subnet 172.16.2.0/24 and the second one is assigned to prefixes in the subnet 172.16.3.0/24. Other prefixes do not have any class assignments. As shown in the following CLI snippet, routing policy is defined on the PE router to assign prefixes to source-class scu-1 and source-class scu-2.
show policy-options
policy-statement scu-class {
term gold {
from {
route-filter 172.16.2.0/24 orlonger;
}
then source-class scu-1;
accept;
term silver {
from {
route-filter 172.16.3.0/24 orlonger;
}
then source-class scu-2;
accept;
}
To account for traffic ingressing PE's interfaces from CE, the policy called dcu-class defined on the PE router uses route filters to place traffic into dcu-1, other prefixes have no class assignments.
show policy-options
policy-statement dcu-class {
term gold {
from {
route-filter 172.16.5.0/24 orlonger;
}
then destination-class dcu-1;
accept;
}
The policies are then applied to the forwarding table.
forwarding-table {
export [ dcu_class scu_class ];
}
In the next step we configure a filter on the PE router.
show firewall {
family inet {
filter f1 {
term t1 {
from {
protocol icmp;
}
then {
count c1;
}
}
}
}
}
And attach that filter to the specific source and destination class bind points on the PE router.
show routing-options forwarding-table
source-class scu-1 {
family inet {
filter {
f1;
}
}
}
destination-class dcu-1 {
family inet {
filter {
f1;
}
}
}
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a text file, remove any line breaks, change any details necessary to match your network configuration, and then copy and paste the commands into the CLI.
The example uses static routes to provide connectivity and loopback interface addresses for testing the operation.
Device CE
set interfaces et-1/2/0 unit 0 family inet address 10.0.0.1/30 set interfaces lo0 unit 0 family inet address 192.168.0.1/32 set interfaces lo0 unit 0 family inet address 172.16.0.1/32 set protocols bgp group ext type external set protocols bgp group ext export send-direct set protocols bgp group ext export send-static set protocols bgp group ext peer-as 200 set protocols bgp group ext neighbor 10.0.0.2 set policy-options policy-statement send-direct term 1 from protocol direct set policy-options policy-statement send-direct term 1 then accept set policy-options policy-statement send-static term 1 from protocol static set policy-options policy-statement send-static term 1 then accept set routing-options static route 10.1.0.0/30 next-hop 10.0.0.2 set routing-options autonomous-system 100
Device PE
set interfaces et-1/2/0 unit 0 family inet address 10.0.0.2/30 set interfaces et-1/2/1 unit 0 family inet accounting source-class-usage input set interfaces et-1/2/1 unit 0 family inet accounting destination-class-usage set interfaces et-1/2/1 unit 0 family inet address 10.1.0.1/30 set interfaces lo0 unit 0 family inet address 192.168.0.2/32 set protocols bgp group ext type external set protocols bgp group ext export send-direct set protocols bgp group ext neighbor 10.0.0.1 peer-as 100 set protocols bgp group ext neighbor 10.1.0.2 peer-as 300 set policy-options policy-statement dcu_class term gold from route-filter 172.16.5.0/24 orlonger set policy-options policy-statement dcu_class term gold then destination-class dcu-1 set policy-options policy-statement scu_class term gold from route-filter 172.16.2.0/24 orlonger set policy-options policy-statement scu_class term gold then source-class scu-1 set policy-options policy-statement scu_class term silver from route-filter 172.16.3.0/24 orlonger set policy-options policy-statement scu_class term silver then source-class scu-1 set policy-options policy-statement send-direct term 1 from protocol direct set policy-options policy-statement send-direct term 1 then accept set firewall family inet filter f1 term 0 from protocol icmp set firewall family inet filter f1 term 0 then count c1 set firewall family inet filter f1 term 0 then accept set routing-options autonomous-system 200 set routing-options forwarding-table export dcu_class set routing-options forwarding-table export scu_class
Device P
set interfaces et-1/2/1 unit 0 family inet address 10.1.0.2/30 set interfaces lo0 unit 0 family inet address 192.168.0.3/32 set interfaces lo0 unit 0 family inet address 172.16.0.3/32 set interfaces lo0 unit 0 family inet address 172.16.0.3/32 set interfaces lo0 unit 0 family inet address 172.16.0.3/32 set interfaces lo0 unit 0 family inet address 172.16.0.3/32 set interfaces lo0 unit 0 family inet address 172.16.0.3/32 set interfaces lo0 unit 0 family inet address 172.16.0.3/32 set protocols bgp group ext type external set protocols bgp group ext export send-direct set protocols bgp group ext export send-static set protocols bgp group ext peer-as 200 set protocols bgp group ext neighbor 10.1.0.1 set policy-options policy-statement send-direct term 1 from protocol direct set policy-options policy-statement send-direct term 1 then accept set policy-options policy-statement send-static term 1 from protocol static set policy-options policy-statement send-static term 1 then accept set routing-options static route 10.0.0.0/30 next-hop 10.1.0.1 set routing-options static route 172.16.2.0/24 discard set routing-options static route 172.16.3.0/24 discard set routing-options static route 172.16.4.0/24 discard set routing-options static route 172.16.5.0/24 discard set routing-options static route 172.16.6.0/24 discard set routing-options static route 172.16.7.0/24 discard set routing-options autonomous-system 300
Step-by-Step Procedure
To group source and destination prefixes in a forwarding class:
-
Create the router interfaces on the PE router.
[edit interfaces] set et-1/2/0 unit 0 family inet accounting source-class-usage output set et-1/2/0 unit 0 family inet address 10.0.0.2/30 set et-1/2/1 unit 0 family inet accounting source-class-usage input set et-1/2/1 unit 0 family inet accounting destination-class-usage set et-1/2/1 unit 0 family inet address 10.1.0.1/30 set lo0 unit 0 family inet address 192.168.0.2/32
-
Configure BGP on PE router.
[edit] set protocols bgp group ext type external set protocols bgp group ext export send-direct set protocols bgp group ext neighbor 10.0.0.1 peer-as 100 set protocols bgp group ext neighbor 10.1.0.2 peer-as 300
-
Configure the autonomous system (AS) number of the PE router.
[edit] set routing-options autonomous-system 200
-
Configure the DCU policy on the PE router.
[edit] set policy-options policy-statement dcu_class term class-1 from route-filter 172.16.5.0/24 orlonger set policy-options policy-statement dcu_class term class-1 then destination-class dcu-1
-
Configure the SCU policy on the PE router.
[edit] set policy-options policy-statement scu_class term class-1 from route-filter 172.16.2.0/24 orlonger set policy-options policy-statement scu_class term class-1 then source-class scu-1
-
Apply the policies to the forwarding table on the PE router.
[edit] set routing-options forwarding-table export dcu_class set routing-options forwarding-table export scu_class
-
Create the filter on the PE router.
[edit] set firewall family inet filter f1 from protocol icmp then count c1
-
Bind the filter to the source class and destination class bind points on the PE router.
Binding the filter to destination class usage.
[edit] set routing-options forwarding-table destination-class dcu-1 family inet filter f1
Binding the filter to source class usage.
[edit] set routing-options forwarding-table source-class scu-1 family inet filter f1
-
(Optional) Configure a routing policy that advertises direct routes on the PE router.
[edit] set policy-options policy-statement send-direct term 1 from protocol direct set policy-options policy-statement send-direct term 1 then accept
Results
From configuration mode , confirm your configuration by issuing the
show interfaces, show protocols,
show policy-options, and show
routing-options commands on the PE router. If the output does
not display the intended configuration, repeat the instructions in this
example to correct the configuration.
show interfaces
et-1/2/0 {
unit 0 {
family inet {
address 10.0.0.2/30;
}
}
}
et-1/2/1 {
unit 0 {
family inet {
accounting {
source-class-usage { input;
}
}
address 10.1.0.1/30;
}
}
}
lo0 {
unit 0 {
family inet {
address 192.168.0.2/32;
}
}
}
show interface statistics et-1/2/0
Physical interface: et-1/2/0:0, Enabled, Physical link is Up
Interface index: 1087, SNMP ifIndex: 622
Link-level type: Ethernet, MTU: 1514, LAN-PHY mode, Speed: 10Gbps, BPDU Error: None, Loop Detect PDU Error: None, MAC-REWRITE Error: None, Loopback: Disabled,
Source filtering: Disabled, Flow control: Enabled, Media type: Fiber Device flags : Present Running
Interface flags: SNMP-Traps
CoS queues : 8 supported, 8 maximum usable queues
Current address: e4:5d:37:4e:e8:40, Hardware address: e4:5d:37:4e:e8:40 Last flapped : 2021-03-16 09:33:43 PDT (03:39:51 ago)
Statistics last cleared: 2021-03-16 13:13:01 PDT (00:00:33 ago) Input rate : 0 bps (0 pps)
Output rate : 0 bps (0 pps) Input errors: 0, Output errors: 0 Active alarms : None
Active defects : None
PCS statistics Seconds
Bit errors 0
Errored blocks 0
PRBS Mode : Disabled
Interface transmit statistics: Disabled Link Degrade :
Link Monitoring : Disable
Logical interface et-1/2/0:0.0 (Index 1047) (SNMP ifIndex 673)
Flags: Up SNMP-Traps
Encapsulation: ENET2
Input packets : 14
Output packets: 6
Protocol inet, MTU: 1500
Flags: Sendbcast-pkt-to-re, SCU-out
Packets Bytes
Source class (packet-per-second) (bits-per-second)
scu-1 6 504
( 0)( 0)
Addresses, Flags: Is-Preferred Is-Primary
Destination: 44.4.4/24, Local: 44.4.4.4, Broadcast: 44.4.4.255
Protocol inet6, MTU: 1500
Flags: None, SCU-out
Packets Bytes
Source class (packet-per-second) (bits-per-second)
scu-1 0 0
( 0) ( 0)
Addresses, Flags: Is-Preferred Is-Primary
Destination: 4001::/64, Local: 4001::4001
Addresses, Flags: Is-Preferred
Destination: fe80::/64, Local: fe80::e65d:37ff:fe4e:e840
Protocol multiservice, MTU: Unlimited
Flags: None
show firewall Filter: f1 Counters: Name Bytes Packets c1 0 0 Filter: v4_instance_new-scu-scu-1 Counters: Name Bytes Packets c_v4_instance_new-scu-scu-1 504 6 Filter: v6_instance_new-scu-scu-1 Counters: Name Bytes Packets c_v6_instance_new-scu-scu-1 0 0
show policy-options
policy-statement dcu_class {
term class-1 {
from {
route-filter 172.16.5.0/24 orlonger;
}
then destination-class dcu-1;
}
}
policy-statement scu_class {
term class-1 {
from {
route-filter 172.16.2.0/24 orlonger;
}
then source-class scu-1;
}
}
policy-statement send-direct {
term 1 {
from protocol direct;
then accept;
}
}
show routing-options
autonomous-system 200;
forwarding-table {
export [ dcu_class scu_class ];
}If you are done configuring the device, enter commit from configuration mode.
