Configuring Port Mirroring Local and Remote Analysis
Configuring Port Mirroring
You use port mirroring to copy packets and send the copies to a device running an application such as a network analyzer or intrusion detection application so that you can analyze traffic without delaying it. You can mirror traffic entering or exiting a port or entering a VLAN, and you can send the copies to a local access interface or to a VLAN through a trunk interface.
We recommend that you disable port mirroring when you are not
using it. To avoid creating a performance issue If you do enable port
mirroring, we recommend that you select specific input interfaces
instead of using the all keyword. You can also limit the
amount of mirrored traffic by using a firewall filter.
This task uses the Enhanced Layer 2 Software (ELS) configuration style. If your switch runs software that does not support ELS, see Configuring Port Mirroring. For ELS details, see Using the Enhanced Layer 2 Software CLI.
If you want to create additional analyzers without deleting an existing analyzer, first disable the existing analyzer by using the disable analyzer analyzer-name command.
You must configure port mirroring output interfaces as family ethernet-switching.
- Configuring Port Mirroring for Local Analysis
- Configuring Port Mirroring for Remote Analysis
- Filtering the Traffic Entering an Analyzer
Configuring Port Mirroring for Local Analysis
To mirror interface traffic to a local interface on the switch:
Configuring Port Mirroring for Remote Analysis
To mirror traffic to a VLAN for analysis at a remote location:
Filtering the Traffic Entering an Analyzer
This functionality is not supported on NFX150 devices.
In addition to specifying which traffic to mirror by configuring
an analyzer, you can also use a firewall filter to exercise more control
over which packets are copied. For example, you might use a filter
to specify that only traffic from certain applications be mirrored.
The filter can use any of the available match conditions and must
have an action of modifier of port-mirror-instance instance-name. If you use the same analyzer in multiple
filters or terms, the output packets are copied only once.
When you use a firewall filter as the input to a port-mirroring instance, you send the copied traffic to a local interface or a VLAN just as you do when a firewall is not involved.
To configure port mirroring with filters:
Configuring Port Mirroring on SRX Series Firewalls
To configure port mirroring on an SRX device, you must first
configure the forwarding-options and interfaces at the [edit] hierarchy level.
You must configure the forwarding-options statement
to define an instance of the mirror-to port for port mirroring
and also configure the interface to be mirrored.
The mirrored port and the mirror-to port must be under the same Broadcom chipset in an I/O card.
To configure port mirroring:
You can configure an instance clause to specify
multiple mirror-to ports.
To mirror an interface, include the port-mirror-instance statement at the [edit interface mirrored-intf-name] hierarchy level.
The mirrored interface is configured with an instance name,
defined in the forwarding-options. The mirrored port and the mirror-to port are linked through that instance.
instance {
inst-name {
input {
rate number;
run-length number;
}
family any {
output {
interface intf-name;
}
}
}
}
interfaces
mirrored-intf-name {
port-mirror-instance instance-name;
}
Port mirroring on SRX Series Firewalls does not differentiate the traffic direction, but mirrors the ingress and egress samples together.
A sample configuration for port mirroring is shown below:
mirror port ge-1/0/2 to port ge-1/0/9.0
forwarding-options
port-mirroring {
input {
rate 1;
run-length 10;
}
family any {
output {
interface ge-1/0/9.0;
}
}
instance {
inst1 {
input {
rate 1;
run-length 10;
}
family any {
output {
interface ge-1/0/9.0;
}
}
}
}
interfaces {
ge-1/0/2 {
port-mirror-instance inst1;
}
}
Examples: Configuring Port Mirroring for Local Analysis
Use port mirroring to send traffic to applications that analyze traffic for purposes such as monitoring compliance, enforcing policies, detecting intrusions, monitoring and predicting traffic patterns, correlating events, and so on. Port mirroring copies packets entering or exiting an interface or entering a VLAN and sends the copies to a local interface for local monitoring.
This example uses the Enhanced Layer 2 Software (ELS) configuration style. For ELS details, see Using the Enhanced Layer 2 Software CLI.
This example describes how to configure port mirroring to copy traffic sent by employee computers to a switch to an access interface on the same switch.
Requirements
This example uses the following hardware and software components:
Junos OS Release 13.2
A switch
Overview and Topology
This topic includes two related examples that describe how to mirror traffic entering interfaces on the switch to an access interface on the same switch. The first example shows how to mirror all traffic sent by employee computers to the switch. The second example includes a filter to mirror only the employee traffic going to the Web.
Topology
In this example, xe-0/0/0 and xe-0/0/6 serve as connections for employee computers. Interface xe-0/0/47 is connected to a device running an analyzer application.
Multiple ports mirrored to one interface can cause buffer overflow and dropped packets.
Figure 1 shows the network topology for this example.
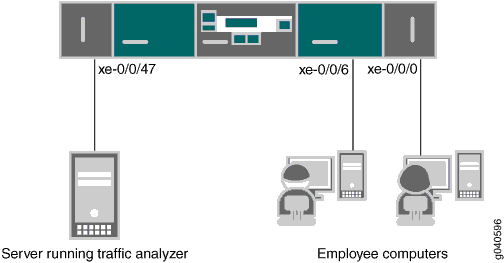
Example: Mirroring All Employee Traffic for Local Analysis
To configure port mirroring for all traffic sent by employee computers for local analysis, perform the tasks explained in this section.
Procedure
CLI Quick Configuration
To quickly configure local port mirroring for ingress traffic to the two ports connected to employee computers, copy the following commands and paste them into a switch terminal window:
[edit] set interfaces xe-0/0/0 unit 0 family ethernet-switching set interfaces xe-0/0/6 unit 0 family ethernet-switching set interfaces xe-0/0/47 unit 0 family ethernet-switching set forwarding-options analyzer employee-monitor input ingress interface xe-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface xe-0/0/6.0 set forwarding-options analyzer employee-monitor output interface xe-0/0/47.0
Step-by-Step Procedure
To configure an analyzer called employee-monitor and specify the input (source) interfaces and the output interface:
Configure the interfaces connected to employee computers as input interfaces for the port-mirror analyzer
employee-monitor:[edit forwarding-options] user@switch# set analyzer employee-monitor input ingress interface xe–0/0/0.0 user@switch# set analyzer employee-monitor input ingress interface xe–0/0/6.0
Configure the output analyzer interface for the
employee-monitoranalyzer. This will be the destination interface for the mirrored packets:[edit forwarding-options] user@switch# set analyzer employee-monitor output interface xe-0/0/47.0
Results
Check the results of the configuration:
[edit]
user@switch# show forwarding-options analyzer
employee-monitor {
input {
ingress {
interface xe-0/0/0.0;
interface xe-0/0/6.0;
}
}
output {
interface {
xe-0/0/47.0;
}
}
}
}
Example: Mirroring Employee Web Traffic with a Firewall Filter
Requirements
This example uses the following hardware and software components:
One QFX5100 switch
Junos OS Release 14.1X53-D30
Overview
Rather than mirror all traffic, it is usually desirable to mirror only certain traffic. This is a more efficient use of your bandwidth and hardware and might be necessary due to constraints on these assets. To select specific traffic for mirroring, you use a firewall filter to match the desired traffic and direct it to a port-mirroring instance. The port-mirroring instance then copies the packets and sends them to the output VLAN, interface, or IP address.
Configuring
To specify that the only traffic that will be mirrored is traffic sent by employees to the Web, perform the tasks explained in this section. To select this traffic for mirroring, you use a firewall filter to specify this traffic and direct it to a port-mirroring instance.
Procedure
CLI Quick Configuration
To quickly configure local port mirroring of traffic from employee computers that is destined for the Web, copy the following commands and paste them into a switch terminal window:
[edit] set interface xe-0/0/47 unit 0 family ethernet-switching set forwarding-options port-mirroring instance employee–web–monitor family ethernet-switching output interface xe-0/0/47.0 set firewall family ethernet-switching filter watch-employee term employee-to-corp from ip-destination-address 192.0.2.16/28 set firewall family ethernet-switching filter watch-employee term employee-to-corp from ip-source-address 192.0.2.16/28 set firewall family ethernet-switching filter watch-employee term employee-to-corp then accept set firewall family ethernet-switching filter watch-employee term employee-to-web from destination-port 80 set firewall family ethernet-switching filter watch-employee term employee-to-web then port-mirror-instance employee-web-monitor set interfaces xe-0/0/0 unit 0 family ethernet-switching filter input watch-employee set interfaces xe-0/0/6 unit 0 family ethernet-switching filter input watch-employee
Step-by-Step Procedure
To configure local port mirroring of employee-to-web traffic from the two ports connected to employee computers:
Configure the output interface:
[edit interfaces] user@switch# set xe-0/0/47 unit 0 family ethernet-switching
Configure the
employee-web-monitoroutput interface. (Configure only the output—the input comes from the filter.)[edit forwarding-options] user@switch# set port-mirroring instance employee–web–monitor family ethernet-switching output interface xe-0/0/47.0
Configure a firewall filter called
watch-employeethat includes a term to match traffic sent to the Web and send it to the port-mirroring instanceemployee-web-monitor. Traffic to and from the corporate subnet (destination or source address of192.0.2.16/28) does not need to be copied, so create another term to accept that traffic before it reaches the term that sends Web traffic to the instance:[edit firewall family ethernet-switching] user@switch# set filter watch-employee term employee-to-corp from ip-destination-address 192.0.2.16/28 user@switch# set filter watch-employee term employee-to-corp from ip-source-address 192.0.2.16/28 user@switch# set filter watch-employee term employee-to-corp then accept user@switch# set filter watch-employee term employee-to-web from destination-port 80 user@switch# set filter watch-employee term employee-to-web then port-mirror-instance employee-web-monitor
Apply the firewall filter to the appropriate interfaces as an ingress filter (egress filters do not allow analyzers):
[edit interfaces] user@switch# set xe-0/0/0 unit 0 family ethernet-switching filter input watch-employee user@switch# set xe-0/0/6 unit 0 family ethernet-switching filter input watch-employee
Results
Check the results of the configuration:
[edit]
user@switch# show
forwarding-options {
port-mirroring {
instance {
employee-web-monitor {
family ethernet-switching {
output {
interface xe-0/0/47.0;
}
}
}
}
}
}
...
firewall {
family ethernet-switching {
filter watch-employee {
term employee-to-corp {
from {
ip-source-address 192.0.2.16/28;
ip-destination-address 192.0.2.16/28;
}
then accept;
term employee-to-web {
from {
destination-port 80;
}
then port-mirror-instance employee-web-monitor;
}
}
}
}
...
interfaces {
xe-0/0/0 {
unit 0 {
family ethernet-switching {
filter {
input watch-employee;
}
}
}
}
xe-0/0/6 {
family ethernet-switching {
filter {
input watch-employee;
}
}
}
xe-0/0/47 {
family ethernet-switching;
}
}
Verification
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the port-mirroring instance named employee-web-monitor has been created on the switch with the
appropriate input interfaces and appropriate output interface.
Action
You can verify that the port mirror port-mirroring instance
has been configured as expected by using the show forwarding-options
port-mirroring command.
user@switch> show forwarding-options port-mirroring Instance name : employee-web-monitor Instance Id: 2 Input parameters: Rate :1 Run-length :0 Maximum packet length :0 Output parameters: Family State Destination Next-hop ethernet-switching up xe-0/0/47.0
Meaning
This
output shows the following information about the port-mirroring instance employee-web-monitor:
Has a rate of
1(mirroring every packet, the default setting)The number of consecutive packets sampled (run-length) is
0The maximum size of the original packet that was mirrored is
0(0indicates the entire packet)The state of the output parameters:
upindicates that the instance is mirroring the traffic entering the xe-0/0/0 and xe-0/0/6 interfaces, and is sending the mirrored traffic to the xe-0/0/47 interface
If the state of the output interface is down or if the output interface is not configured, the state value will be down and the instance will
not be programmed for mirroring.
Example: Configuring Port Mirroring for Remote Analysis
Use port mirroring to send traffic to applications that analyze traffic for purposes such as monitoring compliance, enforcing policies, detecting intrusions, monitoring and predicting traffic patterns, correlating events, and so on. Port mirroring copies packets entering or exiting an interface or entering a VLAN and sends the copies either to a local interface for local monitoring or to a VLAN for remote monitoring. This example describes how to configure port mirroring for remote analysis.
- Requirements
- Overview and Topology
- Mirroring All Employee Traffic for Remote Analysis
- Mirroring Employee-to-Web Traffic for Remote Analysis
- Verification
Requirements
This example uses the following hardware and software components:
Junos OS Release 13.2 for the QFX Series
A switch
Overview and Topology
This topic includes two related examples that describe how to mirror traffic entering ports on the switch to an analyzer VLAN so that you can perform analysis using a remote device. The first example shows how to mirror all traffic sent by employee computers to the switch. The second example includes a filter to mirror only the employee traffic going to the Web.
Topology
In this example:
Interfaces
ge-0/0/0andge-0/0/1are Layer 2 interfaces that connect to employee computers.Interface
ge-0/0/2is a Layer 2 interface that connects to another switch.VLAN
remote-analyzeris configured on all switches in the topology to carry the mirrored traffic.
In addition to performing the configuration steps described
here, you must also configure the analyzer VLAN (remote-analyzer in this example) on the other switches that are used to connect
the source switch (the one in this configuration) to the one that
the monitoring station is connected to.
Mirroring All Employee Traffic for Remote Analysis
Procedure
CLI Quick Configuration
To quickly configure this section of the example,
copy the following commands, paste them into a text file, remove any
line breaks, change any details necessary to match your network configuration,
and then copy and paste the commands into the CLI at the edit hierarchy level:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching port-mode trunk set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/0.0 set forwarding-options analyzer employee-monitor input ingress interface ge-0/0/1.0 set forwarding-options analyzer employee-monitor output vlan remote-analyzer
Step-by-Step Procedure
To configure basic remote port mirroring:
Configure the analyzer VLAN (called
remote-analyzerin this example):[edit vlans] user@switch# set vlans remote-analyzer vlan-id 999
Configure the interface connected to another switch for trunk mode and associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set ge-0/0/10 unit 0 family ethernet-switching port-mode trunk user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999
Configure the
employee-monitoranalyzer:[edit forwarding-options] user@switch# set analyzer employee–monitor user@switch# set analyzer employee-monitor input ingress interface ge-0/0/0.0 user@switch# set analyzer employee-monitor input ingress interface ge-0/0/1.0 user@switch# set analyzer employee-monitor output vlan remote-analyzer
Configure the
remote-analyzerVLAN on the switches that connect this switch to the monitoring workstation.
Results
Check the results of the configuration:
[edit]
user@switch# show
forwarding-options {
analyzer employee-monitor {
input {
ingress {
interface ge-0/0/0.0;
interface ge-0/0/1.0;
}
}
output {
vlan {
remote-analyzer;
}
}
}
}
Mirroring Employee-to-Web Traffic for Remote Analysis
CLI Quick Configuration
To quickly configure this section of the example,
copy the following commands, paste them into a text file, remove any
line breaks, change any details necessary to match your network configuration,
and then copy and paste the commands into the CLI at the edit hierarchy level:
[edit] set vlans remote-analyzer vlan-id 999 set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk set interfaces ge-0/0/10 unit 0 family ethernet-switching vlan members 999 set forwarding-options port-mirroring instance employee-web-monitor loss-priority high output vlan 999 set firewall family ethernet-switching filter watch-employee term employee-to-web from destination-port 80 set firewall family ethernet-switching filter watch-employee term employee-to-web then port-mirror-instance employee-web-monitor set ge-0/0/0 unit 0 family ethernet-switching filter input watch-employee set interfaces ge-0/0/1 unit 0 family ethernet-switching filter input watch-employee
Procedure
Step-by-Step Procedure
Configure the analyzer VLAN (called
remote-analyzerin this example):[edit vlans] user@switch# set remote-analyzer vlan-id 999
Configure an interface to associate it with the
remote-analyzerVLAN:[edit interfaces] user@switch# set interfaces ge-0/0/10 unit 0 family ethernet-switching interface-mode trunk user@switch# set ge-0/0/10 unit 0 family ethernet-switching vlan members 999
Configure the
employee-web-monitoranalyzer. (Configure only the output—the input comes from the filter.)[edit forwarding-options] user@switch# set forwarding-options port-mirroring instance employee-web-monitor output vlan 999
Configure a firewall filter called
watch-employeeto match traffic sent to the Web and send it to the analyzeremployee-web-monitor:[edit firewall family ethernet-switching] user@switch# set filter watch-employee term employee-to-web from destination-port 80 user@switch# set filter watch-employee term employee-to-web then port-mirror-instance employee-web-monitor
Apply the firewall filter to the appropriate interfaces as an ingress filter:
[edit interfaces] user@switch# set ge-0/0/0 unit 0 family ethernet-switching filterinput watch-employee user@switch# set ge-0/0/1 unit 0 family ethernet-switching filter input watch-employee
Configure the
remote-analyzerVLAN on the switches that connect this switch to the monitoring workstation.
Results
Check the results of the configuration:
[edit]
user@switch# show
interfaces {
...
ge-0/0/10 {
unit 0 {
family ethernet-switching {
interface-mode trunk;
vlan {
members remote-analyzer;
}
}
}
}
ge-0/0/0 {
unit 0 {
family ethernet-switching {
filter {
input watch-employee;
}
}
}
}
ge-0/0/1 {
unit 0 {
family ethernet-switching {
filter {
input watch-employee;
}
}
}
}
}
...
firewall {
family ethernet-switching {
...
filter watch-employee {
term employee-to-web {
from {
destination-port 80;
}
then port-mirror-instance employee-web-monitor;
}
}
}
}
forwarding-options analyzer {
employee-web-monitor {
output {
vlan {
999;
}
}
}
vlans {
remote-analyzer {
vlan-id 999;
}
}
Verification
Verifying That the Analyzer Has Been Correctly Created
Purpose
Verify that the analyzer named employee-monitor or employee-web-monitor has been created on the switch
with the appropriate input interfaces and appropriate output interface.
Action
You can verify the port mirror analyzer is configured
as expected using the show analyzer command.
user@switch> show analyzer Analyzer name : employee-monitor Output VLAN : remote-analyzer Ingress monitored interfaces : ge-0/0/0.0 Ingress monitored interfaces : ge-0/0/1.0
Meaning
This output shows that the employee-monitor analyzer is
mirroring the traffic entering ge-0/0/0 and ge-0/0/1 and is sending the mirror traffic to the analyzer remote-analyzer.
