NDP Proxy and DAD Proxy
This topic provides details on Neighbor Discovery Protocol (NDP) proxy and Duplicate Address Detection (DAD) proxy functionality for interface restricted and interface unrestricted mode.
Overview
The NDP proxy functionality enables packet forwarding among the hosts that are in the same subnet and restricted from communicating directly with each other. NDP proxy is required when you want to enable a host device on different physical segments with same subnet to communicate without an additional gateway and prefix. NDP proxy is like node or a router in the middle of multiple segments with same prefix.
When you configure the device as NDP proxy for addresses, the configured proxy interface (proxy router or node) sends the Neighbor Advertisement (NA) replies to Neighbor Solicitation (NS) on behalf of devices in a different physical segment.
The DAD proxy functionality enables a device to respond to DAD queries for a node that cannot communicate directly with other nodes in the same subnet.
NDP or DAD proxy functionality does not work if the NS is for a link local address.
NDP and DAD Proxy (Interface Restricted Mode)
The NDP proxy functionality (interface restricted mode) enables packet forwarding among the hosts that are in the same subnet and restricted to communicate directly with each other. This functionality is primarily used in a scenario where the proxy node needs to apply access control and intercept traffic flowing among the hosts. When you configure NDP proxy on an SRX Series Firewall, the device sends NA and responds to requests from devices seeking MAC addresses of IPv6 prefixes assigned to hosts inside the SRX Series Firewall.
The DAD feature detects the usage of duplicate addresses on a local link by using Neighbor Solicitation (NS) messages. The DAD feature is for IPv6 address and functions similar to gratuitous ARP in IPv4.
NDP and DAD Proxy (Interface Unrestricted Mode)
Starting in Junos OS Release 22.1R1, we support NDP and DAD proxy functionality across multiple proxy configured interfaces (interface unrestricted mode). NDP interface unrestricted proxy works within the existing IPv6 ND functionality and is invoked only if its enabled. Interface unrestricted mode the ND functionality works together across all the configured interfaces for NDP and DAD proxy.
In earlier releases, NDP and DAD proxy functionality was limited and restricted to only the configured interface. Currently, NDP and DAD proxy functionality works across the multiple configured interfaces (interface unrestricted mode).
With NDP and DAD proxy functionality in interface unrestricted mode, the configured interfaces function together to send Neighbor Advertisement (NA) replies to Neighbor Solicitation (NS) on behalf of nodes in a different physical segment which are not directly reachable by the nodes in the originating segment without the overhead of additional prefix assignment.
When you enable NDP proxy in interface unrestricted mode on interfaces using the
set interfaces interface-name unit
number family inet6 ndp-proxy
interface-unrestricted command, the proxy interfaces:
-
Generates NA for NS requests. Requests are then sent from hosts on behalf of other hosts that are reachable on the subnet through the proxy interfaces.
-
Generates NS and sends to all proxy interfaces for the subnet, when the requested address in NS is not available in the neighbor table.
Looks for forwardable routes for the targeted address in the route table that belongs to the ingress interface of the NS packet. Route lookup provides list of routes pointing to resolve next hops. Proxy uses these next hops to send NS on different ports configured.
Note:When the proxy does the route lookup and the resulting route next hop points to the same interface where the NS has arrived, then proxy drops that NS.
-
Allows you to enforce Neighbor Unreachability Detection (NUD) even if the requested target address is available in neighbor cache and is reachable. The force ND feature is useful when the hosts move from one segment to another. To enable the NDP proxy force resolve functionality use the
set protocols neighbor-discovery ndp-proxy proxy-force-resolvecommand. -
Forwards packets between hosts that it proxies, allowing communication between the hosts, once the neighbors are resolved.
The DAD feature detects the usage of duplicate addresses on a local link by using Neighbor Solicitation (NS) messages.
When you enable DAD proxy on multiple interfaces using the set interfaces
interface-name unit <number>
family inet6 dad-proxy interface-unrestricted command:
-
DAD proxy generates NA reply for the DAD NS requests on behalf of other hosts, if the NS tentative address is reachable through other proxy interface.
- When a DAD NS request arrives and if the tentative address is not available or in stale state in the neighbor cache, the DAD proxy initiates NUD on all other proxy interfaces except the received one.
-
If a DAD request is from a host for a tentative address that is already in the middle of a DAD process by another host, then DAD proxy replies with NA for both hosts.
Configuring NDP Proxy
Configuring DAD Proxy
To configure DAD proxy on an interface or on multiple interfaces:
NDP Proxy Support For User Routes
This topic introduces Neighbor Discovery Protocol (NDP) Proxy support. When this feature is enabled for an interface, host routes are maintained in the Routing Information Base (RIB) for each IPv4 or IPv6 host address present in the Address Resolution Protocol (ARP) and Neighbor Discovery Protocol (NDP) tables.
Let’s take for example, two hosts that are part of the same network segment but are located on different physical networks, each connected to its own gateway. Both the hosts are configured with the same IP address.
When servers are divided into hosts to support flexible deployment and migration across servers and gateways, it is common to configure Layer 2 connectivity between multiple gateways. However, this can result in network issues, such as larger Layer 2 domains and broadcast storms. To resolve this, you can use a route-based proxy Neighbor Discovery on the host gateways. The gateway sends its own MAC address to the source host and the traffic sent from the source host to other hosts is done over routes, instead of Layer 2 switching.
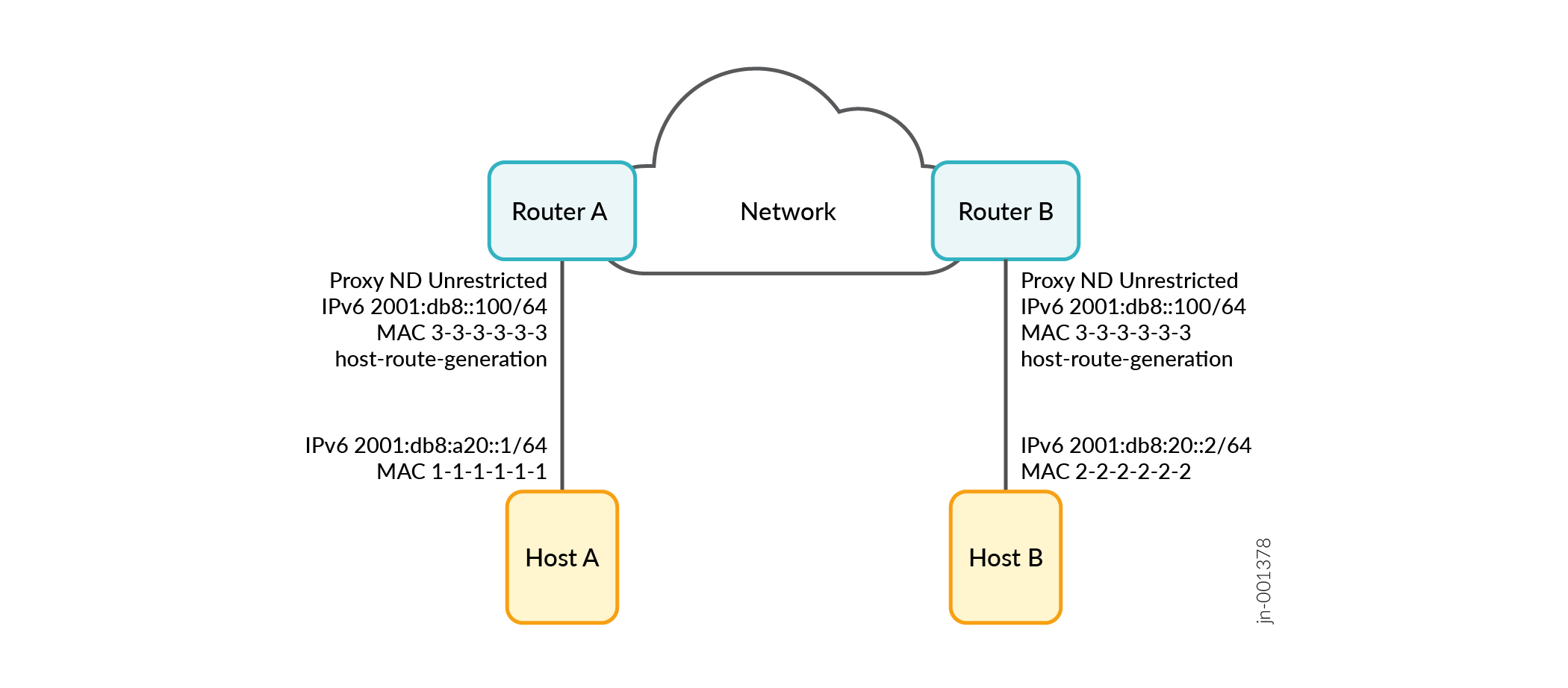
Let’s consider Host A and Host B with IPV6 addresses 2001:db8:a20::1/64 and 2001:db8:20::2/64 to be on the same network segment. Router A and Router B are connected using a Layer 3 network. The interface to the hosts on both routers has the same MAC and IPv6 address. As the destination IPv6 address and local IPv6 address are on the same network segment, if Host A wants to communicate with Host B, it sends a Neighbor Solicitation (NS) packet to request for Host B's MAC address. However, since Host A and Host B are on different physical networks, Host B doesn’t receive the NS and cannot reply.
To address the problem, a new proxy Neighbor Discovery (ND) option based on user routes is introduced. This mode is supported only on unrestricted mode of proxy.
The new proxy mode relies on the host route generation feature to check reachability. When this feature is enabled for an interface, host routes are maintained in the Routing Information Base (RIB) for each IPv4 or IPv6 host address present in the Address Resolution Protocol (ARP) and Neighbor Discovery Protocol (NDP) tables. These host routes that are active in the RIB are available for redistribution into BGP or IGPs, subject to routing protocol export policies. The user route proxy ND relies on these redistributed user routes for checking reachability of hosts.
Proactive ARP detection helps quickly learn reachable VMs and Proactive IPV6 neighbor learning is not supported.
Host routes in non-default routing tables are not supported and therefore, the new user route based proxying is also not supported.
