Destination NAT
Destination NAT changes the destination address of packets passing through the Router. It also offers the option to perform the port translation in the TCP/UDP headers. Destination NAT mainly used to redirect incoming packets with an external address or port destination to an internal IP address or port inside the network.
Understanding Destination NAT
Destination NAT is the translation of the destination IP address of a packet entering the Juniper Networks device. Destination NAT is used to redirect traffic destined to a virtual host (identified by the original destination IP address) to the real host (identified by the translated destination IP address).
When destination NAT is performed, the destination IP address is translated according to configured destination NAT rules and then security policies are applied.
Destination NAT allows connections to be initiated only for incoming network connections—for example, from the Internet to a private network. Destination NAT is commonly used to perform the following actions:
Translate a single IP address to another address (for example, to allow a device on the Internet to connect to a host on a private network).
Translate a contiguous block of addresses to another block of addresses of the same size (for example, to allow access to a group of servers).
Translate a destination IP address and port to another destination IP address and port (for example, to allow access to multiple services using the same IP address but different ports).
The following types of destination NAT are supported:
Translation of the original destination IP address to an IP address from a user-defined pool. This type of translation does not include Port Address Translation (PAT). If the original destination IP address range is larger than the address range in the user-defined address pool, any untranslated packets are dropped.
Translation of the original destination IP address (and optional port number) to one specific IP address (and port number) from a user-defined pool.
Understanding Destination NAT Address Pools
A NAT pool is a user-defined set of IP addresses that are used for translation. Unlike static NAT, where there is a one-to-one mapping that includes destination IP address translation in one direction and source IP address translation in the reverse direction, with destination NAT, you translate the original destination address to an IP address in the address pool.
For destination NAT address pools, specify the following:
Name of the destination NAT address pool
Destination address or address range
Do not overlap NAT addresses for source NAT, destination NAT, and static NAT within one routing instance.
Destination port that is used for port forwarding
Routing instance to which the pool belongs—A destination NAT pool that does not specify a specific routing instance will default to the routing instance of the ingress zone.
You can configure a NAT pool to exist in the default routing instance. Configuration option to specify that a NAT pool exists in the default routing-instance is available. As a result, the NAT pool is reachable from zones in the default routing instance, and from zones in other routing instances.
Understanding Destination NAT Rules
Destination NAT rules specify two layers of match conditions:
Traffic direction—Allows you to specify
from interface,from zone, orfrom routing-instance.Packet information—Can be source IP addresses, destination IP address or subnet, destination port numbers or port ranges, protocols, or applications.
For ALG traffic, we recommend that you not use the destination-port option or the application option as matching conditions.
If these options are used, translation may fail because the port value
in the application payload might not match the port value in the IP
address.
If multiple destination NAT rules overlap in the match conditions,
the most specific rule is chosen. For example, if rules A and B specify
the same source and destination IP addresses, but rule A specifies
traffic from zone 1 and rule B specifies traffic from interface ge-0/0/0, rule B is used to perform destination NAT. An interface
match is considered to be more specific than a zone match, which is
more specific than a routing instance match.
The actions you can specify for a destination NAT rule are:
off—Do not perform destination NAT.
pool—Use the specified user-defined address pool to perform destination NAT.
Destination NAT rules are applied to traffic in the first packet that is processed for the flow or in the fast path for the ALG. Destination NAT rules are processed after static NAT rules but before source NAT rules.
Destination NAT Configuration Overview
The main configuration tasks for destination NAT are as follows:
- Configure a destination NAT address pool that aligns with your network and security requirements.
- Configure destination NAT rules that align with your network and security requirements.
- Configure NAT proxy ARP entries for IP addresses in the same subnet of the ingress interface.
Example: Configuring Destination NAT for Single Address Translation
This example describes how to configure a destination NAT mapping of a single public address to a private address.
Mapping one destination IP address to another can also be accomplished with static NAT. Static NAT mapping allows connections to be established from either side of the gateway device, whereas destination NAT only allows connections to be established from one side. However, static NAT only allows translations from one address to another or between blocks of addresses of the same size.
Requirements
This example uses the following hardware and software components:
SRX Series Firewalls
Server
Before you begin:
Configure network interfaces on the device. See the Interfaces User Guide for Security Devices.
Create security zones and assign interfaces to them. See Understanding Security Zones.
Overview
Destination NAT is commonly used to distribute a service located in a private network with a publicly accessible IP address. This allows users to use the private service with the public IP address. Destination NAT address pool and destination NAT rules configurations are used to align your network and improve security requirements.
In this example, first you configure the trust security zone for the private address space and then you configure the untrust security zone for the public address space. In Figure 1, devices in the untrust zone access a server in the trust zone by way of public address 203.0.113.200/32. For packets that enter the Juniper Networks security device from the untrust zone with the destination IP address 203.0.113.200/32, the destination IP address is translated to the private address 192.168.1.200/32.
Topology
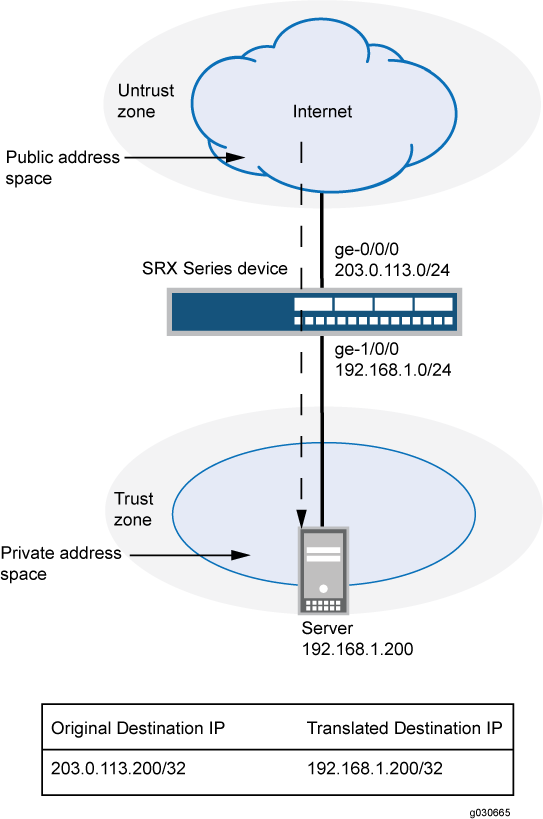
Table 1 shows the parameters configured in this example.
Parameter |
Description |
|---|---|
Trust Zone |
Security zone for the private address space. |
Untrust Zone |
Security zone for the public address space. |
192.168.1.200/32 |
Translated destination NAT IP address. |
192.168.1.0/24 |
Private subnet in private zone. |
203.0.113.200/32 |
Public address of the server. |
Server |
Server address of the private address space. |
ge-0/0/0 and ge-1/0/0 |
NAT interfaces for traffic direction. |
This example describes the following configurations:
Destination NAT pool
dst-nat-pool-1that contains the IP address 192.168.1.200/32.Destination NAT rule set
rs1with ruler1to match packets received from the ge-0/0/0.0 interface with the destination IP address 203.0.113.200/32. For matching packets, the destination address is translated to the address in thedst-nat-pool-1pool.Proxy ARP for the address 203.0.113.200/32 on interface ge-0/0/0.0. This allows the Juniper Networks security device to respond to ARP requests received on the interface for that address.
Security policies to permit traffic from the untrust zone to the translated destination IP address in the trust zone.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security nat destination pool dst-nat-pool-1 address 192.168.1.200/32 set security nat destination rule-set rs1 from interface ge-0/0/0.0 set security nat destination rule-set rs1 rule r1 match destination-address 203.0.113.200/32 set security nat destination rule-set rs1 rule r1 then destination-nat pool dst-nat-pool-1 set security nat proxy-arp interface ge-0/0/0.0 address 203.0.113.200/32 set security address-book global address server-1 192.168.1.200/32 set security policies from-zone untrust to-zone trust policy server-access match source-address any set security policies from-zone untrust to-zone trust policy server-access match destination-address server-1 set security policies from-zone untrust to-zone trust policy server-access match application any set security policies from-zone untrust to-zone trust policy server-access then permit
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the CLI User Guide.
To configure a destination NAT mapping from a public address to a private address:
Create the destination NAT pool.
[edit security nat destination] user@host# set pool dst-nat-pool-1 address 192.168.1.200/32
Create a destination NAT rule set.
[edit security nat destination] user@host# set rule-set rs1 from interface ge-0/0/0.0
Configure a rule that matches packets and translates the destination address to the address in the pool.
[edit security nat destination] user@host# set rule-set rs1 rule r1 match destination-address 203.0.113.200/32 user@host# set rule-set rs1 rule r1 then destination-nat pool dst-nat-pool-1
Configure proxy ARP.
[edit security nat] user@host# set proxy-arp interface ge-0/0/0.0 address 203.0.113.200/32
Configure an address in the global address book.
[edit security address-book global] user@host# set address server-1 192.168.1.200/32
Configure a security policy that allows traffic from the untrust zone to the server in the trust zone.
[edit security policies from-zone untrust to-zone trust] user@host# set policy server-access match source-address any user@host# set policy server-access match destination-address server-1 user@host# set policy server-access match application any user@host# set policy server-access then permit
Results
From configuration mode, confirm your configuration
by entering the show interfaces, show security zones, and show bridge-domains command. If the output does
not display the intended configuration, repeat the instructions in
this example to correct the configuration.
[edit]
user@host# show security nat
destination {
pool dst-nat-pool-1 {
address 192.168.1.200/32;
}
rule-set rs1 {
from interface ge-0/0/0.0;
rule r1 {
match {
destination-address 203.0.113.200/32;
}
then {
destination-nat pool dst-nat-pool-1;
}
}
}
}
proxy-arp {
interface ge-0/0/0.0 {
address {
203.0.113.200/32;
}
}
}
[edit]
user@host# show security address-book
global {
address server-1 192.168.1.200/32;
}
user@host# show security policies
from-zone untrust to-zone trust {
policy server-access {
match {
source-address any;
destination-address server-1;
application any;
}
then {
permit;
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
Confirm that the configuration is working properly.
- Verifying Destination NAT Pool Usage
- Verifying Destination NAT Rule Usage
- Verifying Destination NAT for a Single Address Translation
- Verifying NAT Application to Traffic
Verifying Destination NAT Pool Usage
Purpose
Verify that there is traffic using IP addresses from the destination NAT pool.
Action
From operational mode, enter the show security
nat destination pool all command. View the Translation hits
field to check for traffic using IP addresses from the pool.
user@host>show security nat destination pool all
Total destination-nat pools: 1
Pool name : dst-nat-pool-1
Pool id : 1
Total address : 1
Translation hits: 71
Address range Port
192.168.1.200 - 192.168.1.200 0
Meaning
The show security nat destination pool all command displays the pool of translated addresses. View the Translation
hits field to check for traffic using IP addresses from the pool.
Verifying Destination NAT Rule Usage
Purpose
Verify that there is traffic matching the destination NAT rule.
Action
From operational mode, enter the show security
nat destination rule all command.
user@host>show security nat destination rule all
Total destination-nat rules: 1
Total referenced IPv4/IPv6 ip-prefixes: 1/0
Destination NAT rule: r1 Rule-set: rs1
Rule-Id : 1
Rule position : 1
From interface : ge-0/0/0.0
Destination addresses : 203.0.113.200 - 203.0.113.200
Action : dst-nat-pool-1
Translation hits : 75
Successful sessions : 75
Failed sessions : 0
Number of sessions : 4
Meaning
The show security nat destination rule all command displays the destination NAT rule. View the Translation
hits field to check for traffic that matches the destination rule.
Verifying Destination NAT for a Single Address Translation
Purpose
Verify the configuration of destination NAT for a single address translation.
Action
From operational mode, enter the show security
nat destination summary command.
user@host>show security nat destination summary
Total pools: 1
Pool name Address Range Routing Port Total
Instance Address
dst-nat-pool-1 192.168.1.200 - 192.168.1.200 0 1
Total rules: 1
Rule name Rule set From Action
r1 rs1 ge-0/0/0.0 dst-nat-pool-1
Meaning
The show security nat destination summary command displays information about destination NAT configuration.
You can verify the following information:
Rule sets
Rules
Address range
NAT pool
Port details
Verifying NAT Application to Traffic
Purpose
Verify that NAT is being applied to the specified traffic.
Action
From operational mode, enter the show security
flow session command.
user@host>show security flow session Session ID: 26415, Policy name: server-access/11, Timeout: 2, Valid In: 203.0.113.219/30 --> 203.0.113.200/54850;icmp, If: ge-0/0/0.0, Pkts: 1, Bytes: 84 Out: 192.168.1.200/54850 --> 203.0.113.219/30;icmp, If: ge-0/0/1.0, Pkts: 1, Bytes: 84 Session ID: 26420, Policy name: server-access/11, Timeout: 2, Valid In: 203.0.113.219/31 --> 203.0.113.200/54850;icmp, If: ge-0/0/0.0, Pkts: 1, Bytes: 84 Out: 192.168.1.200/54850 --> 203.0.113.219/31;icmp, If: ge-0/0/1.0, Pkts: 1, Bytes: 84 Session ID: 26425, Policy name: server-access/11, Timeout: 4, Valid In: 203.0.113.219/32 --> 203.0.113.200/54850;icmp, If: ge-0/0/0.0, Pkts: 1, Bytes: 84 Out: 192.168.1.200/54850 --> 203.0.113.219/32;icmp, If: ge-0/0/1.0, Pkts: 1, Bytes: 84 Session ID: 26431, Policy name: server-access/11, Timeout: 4, Valid In: 203.0.113.219/33 --> 203.0.113.200/54850 ;icmp, If: ge-0/0/0.0, Pkts: 1, Bytes: 84 Out: 192.168.1.200/54850 --> 203.0.113.219/33;icmp, If: ge-0/0/1.0, Pkts: 1, Bytes: 84 Total sessions: 9
Meaning
The show security flow session command displays active sessions on the device
and each session’s associated security policy. The output shows traffic
entering the device destined to a public host at 203.0.113.200 that gets
translated to private destination IP address 192.168.1.200.
Session ID—Number that identifies the session. Use this ID to get more information about the session such as policy name or number of packets in and out.
server-access—Policy name that permitted the traffic from the untrust zone to the translated destination IP address in the trust zone.
In—Incoming flow (source and destination IP addresses with their respective source and destination port numbers, the session is ICMP, and the source interface for this session is ge-0/0/0.0).
Out—Reverse flow (source and destination IP addresses with their respective source and destination port numbers, the session is ICMP, and the destination interface for this session is ge-0/0/1.0).
Example: Configuring Destination NAT for IP Address and Port Translation
This example describes how to configure destination NAT mappings of a public address to private addresses, depending on the port number.
Requirements
Before you begin:
Configure network interfaces on the device. See Interfaces User Guide for Security Devices.
Create security zones and assign interfaces to them. See Understanding Security Zones.
Overview
This example uses the trust security zone for the private address space and the untrust security zone for the public address space. In Figure 2, devices in the untrust zone access servers in the trust zone by way of public address 203.0.113.200 on port 80 or 8000. Packets entering the Juniper Networks security device from the untrust zone are mapped to the private addresses of the servers as follows:
The destination IP address 203.0.113.200 and port 80 is translated to the private address 192.168.1.200 and port 80.
The destination IP address 203.0.113.200 and port 8000 is translated to the private address 192.168.1.220 and port 8000.
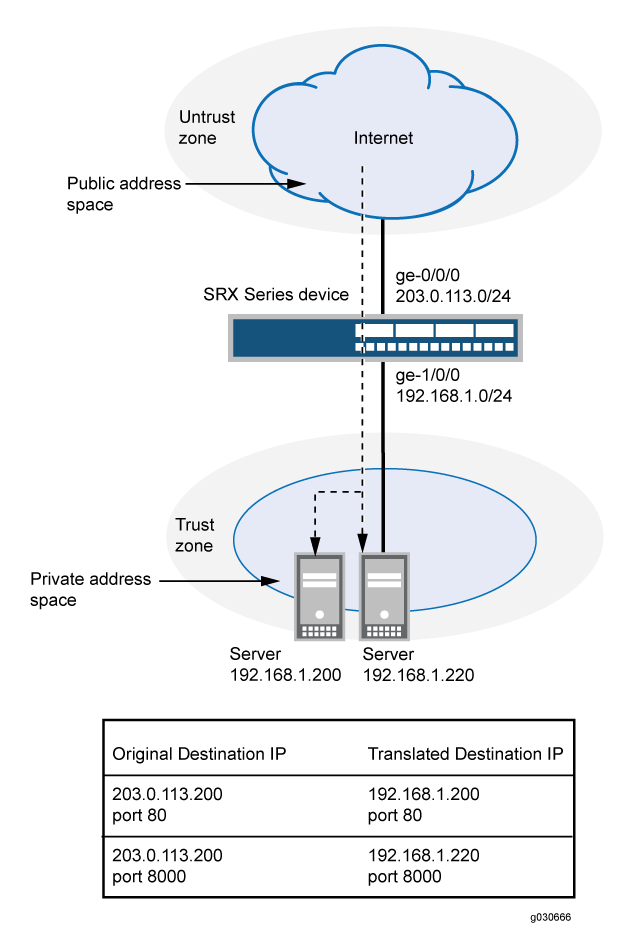
This example describes the following configurations:
Destination NAT pool
dst-nat-pool-1that contains the IP address 192.168.1.200 port 80.Destination NAT pool
dst-nat-pool-2that contains the IP address 192.168.1.220 and port 8000.Destination NAT rule set
rs1with ruler1to match packets received from the untrust zone with the destination IP address 203.0.113.200 and destination port 80. For matching packets, the destination address is translated to the address in thedst-nat-pool-1pool.Destination NAT rule set
rs1with ruler2to match packets received from the untrust zone with the destination IP address 203.0.113.200 and destination port 8000. For matching packets, the destination IP address and port are translated to the address and port in thedst-nat-pool-2pool.Proxy ARP for the address 203.0.113.200/32. This allows the Juniper Networks security device to respond to ARP requests received on the interface for that address.
Security policies to permit traffic from the untrust zone to the translated destination IP addresses in the trust zone.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security nat destination pool dst-nat-pool-1 address 192.168.1.200/32 set security nat destination pool dst-nat-pool-1 address port 80 set security nat destination pool dst-nat-pool-2 address 192.168.1.220/32 set security nat destination pool dst-nat-pool-2 address port 8000 set security nat destination rule-set rs1 from zone untrust set security nat destination rule-set rs1 rule r1 match destination-address 203.0.113.200/32 set security nat destination rule-set rs1 rule r1 match destination-port 80 set security nat destination rule-set rs1 rule r1 then destination-nat pool dst-nat-pool-1 set security nat destination rule-set rs1 rule r2 match destination-address 203.0.113.200/32 set security nat destination rule-set rs1 rule r2 match destination-port 8000 set security nat destination rule-set rs1 rule r2 then destination-nat pool dst-nat-pool-2 set security nat proxy-arp interface ge-0/0/0.0 address 203.0.113.200/32 set security address-book global address server-2 192.168.1.220/32 set security address-book global address server-1 192.168.1.200/32 set security policies from-zone untrust to-zone trust policy server-access match source-address any set security policies from-zone untrust to-zone trust policy server-access match destination-address server-1 set security policies from-zone untrust to-zone trust policy server-access match destination-address server-2 set security policies from-zone untrust to-zone trust policy server-access match application any set security policies from-zone untrust to-zone trust policy server-access then permit
Step-by-Step Procedure
The following example requires you to navigate throughout various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode.
To configure a destination NAT mapping from a public address to a private address:
Create destination NAT pools.
[edit security nat destination] user@host# set pool dst-nat-pool-1 address 192.168.1.200 port 80 user@host# set pool dst-nat-pool-2 address 192.168.1.220 port 8000
Create a destination NAT rule set.
[edit security nat destination] user@host# set rule-set rs1 from zone untrust
Configure a rule that matches packets and translates the destination address to the address in the pool.
[edit security nat destination] user@host# set rule-set rs1 rule r1 match destination-address 203.0.113.200 user@host# set rule-set rs1 rule r1 match destination-port 80 user@host# set rule-set rs1 rule r1 then destination-nat pool dst-nat-pool-1
Configure a rule that matches packets and translates the destination address to the address in the pool.
[edit security nat destination] user@host# set rule-set rs1 rule r2 match destination-address 203.0.113.200 user@host# set rule-set rs1 rule r2 match destination-port 8000 user@host# set rule-set rs1 rule r2 then destination-nat pool dst-nat-pool-2
Configure proxy ARP.
[edit security nat] user@host# set proxy-arp interface ge-0/0/0.0 address 203.0.113.200/32
Configure addresses in the global address book.
[edit security address-book global] user@host# set address server-2 192.168.1.220/32 user@host# set address server-1 192.168.1.200/32
Configure a security policy that allows traffic from the untrust zone to the servers in the trust zone.
[edit security policies from-zone untrust to-zone trust] user@host# set policy server-access match source-address any destination-address [server-1 server-2] application any user@host# set policy server-access then permit
Results
From configuration mode, confirm your configuration
by entering the show security nat and show security
policies commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show security nat
destination {
pool dst-nat-pool-1 {
address 192.168.1.200/32 port 80;
}
pool dst-nat-pool-2 {
address 192.168.1.220/32 port 8000;
}
rule-set rs1 {
from zone untrust;
rule r1 {
match {
destination-address 203.0.113.200/32;
destination-port 80;
}
then {
destination-nat pool dst-nat-pool-1;
}
}
rule r2 {
match {
destination-address 203.0.113.200/32;
destination-port 8000;
}
then {
destination-nat pool dst-nat-pool-2;
}
}
}
}
proxy-arp {
interface ge-0/0/0.0 {
address {
203.0.113.200/32;
}
}
}
user@host# show security policies
from-zone untrust to-zone trust {
policy server-access {
match {
source-address any;
destination-address [ server-1 server-2 ];
application any;
}
then {
permit;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
To confirm that the configuration is working properly, perform these tasks:
- Verifying Destination NAT Pool Usage
- Verifying Destination NAT Rule Usage
- Verifying NAT Application to Traffic
Verifying Destination NAT Pool Usage
Purpose
Verify that there is traffic using IP addresses from the destination NAT pool.
Action
From operational mode, enter the show security nat destination
pool all command. View the Translation hits field to check for
traffic using IP addresses from the pool.
Verifying Destination NAT Rule Usage
Purpose
Verify that there is traffic matching the destination NAT rule.
Action
From operational mode, enter the show security nat destination
rule all command. View the Translation hits field to check for
traffic that matches the rule.
Example: Configuring Destination NAT for Subnet Translation
This example describes how to configure a destination NAT mapping of a public subnet address to a private subnet address.
Mapping addresses from one subnet to another can also be accomplished with static NAT. Static NAT mapping allows connections to be established from either side of the gateway device, whereas destination NAT allows connections to be established from only one side. However, static NAT only allows translations between blocks of addresses of the same size.
Requirements
Before you begin:
Configure network interfaces on the device. See Interfaces User Guide for Security Devices.
Create security zones and assign interfaces to them. See Understanding Security Zones.
Overview
This example uses the trust security zone for the private address space and the untrust security zone for the public address space. In Figure 3, devices in the untrust zone access devices in the trust zone by way of public subnet address 203.0.113.0/24. For packets that enter the Juniper Networks security device from the untrust zone with a destination IP address in the 203.0.113.0/24 subnet, the destination IP address is translated to a private address on the 192.168.1.0/24 subnet.
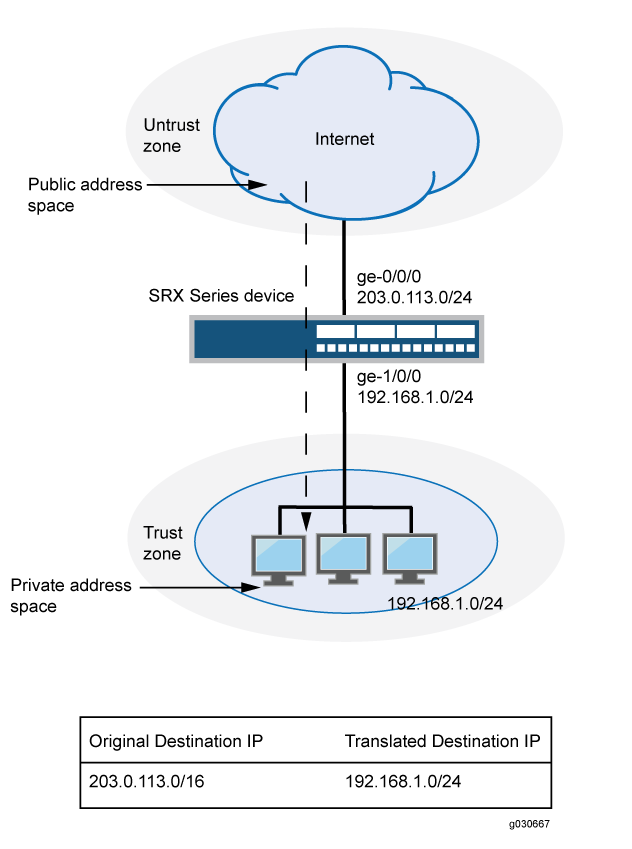
This example describes the following configurations:
Destination NAT pool
dst-nat-pool-1that contains the IP address 192.168.1.0/24.Destination NAT rule set
rs1with ruler1to match packets received from the ge-0/0/0.0 interface with the destination IP address on the 203.0.113.0/24 subnet. For matching packets, the destination address is translated to the address in thedst-nat-pool-1pool.Proxy ARP for the addresses 203.0.113.1/32 through 203.0.113.62/32 on the interface ge-0/0/0.0; these are the IP addresses of the hosts that should be translated from the 203.0.113.0/24 subnet. This allows the Juniper Networks security device to respond to ARP requests received on the interface for those addresses. The address 203.0.113.0/24 is assigned to the interface itself, so this address is not included in the proxy ARP configuration. The addresses that are not in the 203.0.113.1/32 through 203.0.113.62/32 range are not expected to be present on the network and would not be translated.
Security policies to permit traffic from the untrust zone to the translated destination IP addresses in the trust zone.
Configuration
Procedure
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set security nat destination pool dst-nat-pool-1 address 192.168.1.0/24 set security nat destination rule-set rs1 from interface ge-0/0/0.0 set security nat destination rule-set rs1 rule r1 match destination-address 203.0.113.0/24 set security nat destination rule-set rs1 rule r1 then destination-nat pool dst-nat-pool-1 set security nat proxy-arp interface ge-0/0/0.0 address 203.0.113.1/32 to 203.0.113.62/32 set security address-book global address internal-net 192.168.1.0/24 set security policies from-zone untrust to-zone trust policy internal-access match source-address any set security policies from-zone untrust to-zone trust policy internal-access match destination-address internal-net set security policies from-zone untrust to-zone trust policy internal-access match application any set security policies from-zone untrust to-zone trust policy internal-access then permit
Step-by-Step Procedure
The following example requires you to navigate throughout various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode.
To configure a destination NAT mapping from a public subnet address to a private subnet address:
Create the destination NAT pool.
[edit security nat destination] user@host# set pool dst-nat-pool-1 address 192.168.1.0/24
Create a destination NAT rule set.
[edit security nat destination] user@host# set rule-set rs1 from interface ge-0/0/0.0
Configure a rule that matches packets and translates the destination address to an address in the pool.
[edit security nat destination] user@host# set rule-set rs1 rule r1 match destination-address 203.0.113.0/24 user@host# set rule-set rs1 rule r1 then destination-nat pool dst-nat-pool-1
Configure proxy ARP.
[edit security nat] user@host# set proxy-arp interface ge-0/0/0.0 address 203.0.113.1/32 to 203.0.113.62/32
Configure an address in the global address book.
[edit security address-book global] user@host# set address internal-net 192.168.1.0/24
Configure a security policy that allows traffic from the untrust zone to the devices in the trust zone.
[edit security policies from-zone untrust to-zone trust] user@host# set policy internal-access match source-address any destination-address internal-net application any user@host# set policy internal-access then permit
Results
From configuration mode, confirm your configuration
by entering the show security nat and show security
policies commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example
to correct it.
[edit]
user@host# show security nat
destination {
pool dst-nat-pool-1 {
address 192.168.1.0/24;
}
rule-set rs1 {
from interface ge-0/0/0.0;
rule r1 {
match {
destination-address 203.0.113.0/24;
}
then {
destination-nat pool dst-nat-pool-1;
}
}
}
}
proxy-arp {
interface ge-0/0/0.0 {
address {
203.0.113.1/32 to 203.0.113.62/32;
}
}
}
user@host# show security policies
from-zone untrust to-zone trust {
policy internal-access {
match {
source-address any;
destination-address internal-net;
application any;
}
then {
permit;
}
}
}
If you are done configuring the device, enter commit from configuration mode.
Verification
To confirm that the configuration is working properly, perform these tasks:
- Verifying Destination NAT Pool Usage
- Verifying Destination NAT Rule Usage
- Verifying NAT Application to Traffic
Verifying Destination NAT Pool Usage
Purpose
Verify that there is traffic using IP addresses from the destination NAT pool.
Action
From operational mode, enter the show security nat destination
pool all command. View the Translation hits field to check for
traffic using IP addresses from the pool.
Verifying Destination NAT Rule Usage
Purpose
Verify that there is traffic matching the destination NAT rule.
Action
From operational mode, enter the show security nat destination
rule all command. View the Translation hits field to check for
traffic that matches the rule.
Monitoring Destination NAT Information
Purpose
View the destination Network Address Translation (NAT) summary table and the details of the specified NAT destination address pool information.
Action
Select Monitor>NAT> Destination NAT in the J-Web user interface, or enter the following CLI commands:
show security nat destination summaryshow security nat destination pool pool-name
Table 2 summarizes key output fields in the destination NAT display.
Field |
Values |
Action |
|---|---|---|
| Rules | ||
Rule-set Name |
Name of the rule set. |
Select all rule sets or a specific rule set to display from the list. |
Total rules |
Number of rules configured. |
– |
ID |
Rule ID number. |
– |
Name |
Name of the rule . |
– |
Ruleset Name |
Name of the rule set. |
– |
From |
Name of the routing instance/zone/interface from which the packet flows. |
– |
Source address range |
Source IP address range in the source pool. |
– |
Destination address range |
Destination IP address range in the source pool. |
– |
Destination port |
Destination port in the destination pool. |
– |
IP protocol |
IP protocol. |
– |
Action |
Action taken for a packet that matches a rule. |
– |
Alarm threshold |
Utilization alarm threshold. |
– |
Sessions (Succ/Failed/Current) |
Successful, failed, and current sessions.
|
– |
Translation hits |
Number of times a translation in the translation table is used for a destination NAT rule. |
– |
| Pools | ||
Pool Name |
The names of the pools. |
Select all pools or a specific pool to display from the list. |
Total Pools |
Total pools added. |
– |
ID |
ID of the pool. |
– |
Name |
Name of the destination pool. |
– |
Address range |
IP address range in the destination pool. |
– |
Port |
Destination port number in the pool. |
– |
Routing instance |
Name of the routing instance. |
– |
Total addresses |
Total IP address, IP address set, or address book entry. |
– |
Translation hits |
Number of times a translation in the translation table is used for destination NAT. |
– |
| Top 10 Translation Hits | ||
Graph |
Displays the graph of top 10 translation hits. |
– |
