Understanding Private VLANs
VLANs limit broadcasts to specified users. Private VLANs (PVLANs) take this concept a step further by limiting communication within a VLAN. PVLANs accomplish this by restricting traffic flows through their member switch ports (which are called private ports) so that these ports communicate only with a specified uplink trunk port or with specified ports within the same VLAN. The uplink trunk port or link aggregation group (LAG) is usually connected to a router, firewall, server, or provider network. Each PVLAN typically contains many private ports that communicate only with a single uplink port, thereby preventing the ports from communicating with each other.
PVLANs provide Layer 2 isolation between ports within a VLAN, splitting a broadcast domain into multiple discrete broadcast subdomains by creating secondary VLANs (community VLANs and an isolated VLAN) inside a primary VLAN. Ports within the same community VLAN can communicate with each other. Ports within an isolated VLAN can communicate only with a single uplink port.
Just like regular VLANs, PVLANs are isolated on Layer 2 and require one of the following options to route Layer 3 traffic among the secondary VLANs:
A promiscuous port connection with a router
A routed VLAN interface (RVI)
To route Layer 3 traffic among secondary VLANs, a PVLAN needs only one of the options mentioned above. If you use an RVI, you can still implement a promiscuous port connection to a router with the promiscuous port set up to handle only traffic that enters and exits the PVLAN.
PVLANs are useful for restricting the flow of broadcast and unknown unicast traffic and for limiting the communication between known hosts. Service providers use PVLANs to keep their customers isolated from each other. Another typical use for a PVLAN is to provide per-room Internet access in a hotel.
You can configure a PVLAN to span switches that support PVLANs.
This topic explains the following concepts regarding PVLANs on EX Series switches:
Benefits of PVLANs
The need to segregate a single VLAN is particularly useful in the following deployment scenarios:
Server farms—A typical Internet service provider uses a server farm to provide Web hosting for numerous customers. Locating the various servers within a single server farm provides ease of management. Security concerns arise if all servers are in the same VLAN because Layer 2 broadcasts go to all servers in the VLAN.
Metropolitan Ethernet networks—A metro service provider offers Layer 2 Ethernet access to assorted homes, rental communities, and businesses. The traditional solution of deploying one VLAN per customer is not scalable and is difficult to manage, leading to potential waste of IP addresses. PVLANs provide a more secure and more efficient solution.
Typical Structure and Primary Application of PVLANs
A PVLAN can be configured on a single switch or can be configured to span multiple switches. The types of domains and ports are:
Primary VLAN—The primary VLAN of the PVLAN is defined with an 802.1Q tag (VLAN ID) for the complete PVLAN. The primary PVLAN can contain multiple secondary VLANs (one isolated VLAN and multiple community VLANs).
Isolated VLAN/isolated port—A primary VLAN can contain only one isolated VLAN. An interface within an isolated VLAN can forward packets only to a promiscuous port or the Inter-Switch Link (ISL) port. An isolated interface cannot forward packets to another isolated interface; and an isolated interface cannot receive packets from another isolated interface. If a customer device needs to have access only to a gateway router, the device must be attached to an isolated trunk port.
Community VLAN/community port—You can configure multiple community VLANs within a single PVLAN. An interface within a specific community VLAN can establish Layer 2 communications with any other interface that belongs to the same community VLAN. An interface within a community VLAN can also communicate with a promiscuous port or the ISL port. If you have, for example, two customer devices that you need to isolate from other customer devices but that must be able to communicate with one another, use community ports.
Promiscuous port—A promiscuous port has Layer 2 communications with all interfaces in the PVLAN, regardless of whether an interface belongs to an isolated VLAN or a community VLAN. A promiscuous port is a member of the primary VLAN but is not included within any secondary subdomain. Layer 3 gateways, DHCP servers, and other trusted devices that need to communicate with endpoint devices are typically connected to a promiscuous port.
Inter-Switch Link (ISL)—An ISL is a trunk port that connects multiple switches in a PVLAN and contains two or more VLANs. It is required only when a PVLAN spans multiple switches.
The configured PVLAN is the primary domain (primary VLAN). Within the PVLAN, you configure secondary VLANs, which become subdomains nested within the primary domain. A PVLAN can be configured on a single switch or can be configured to span multiple switches. The PVLAN shown in Figure 1 includes two switches, with a primary PVLAN domain and various subdomains.
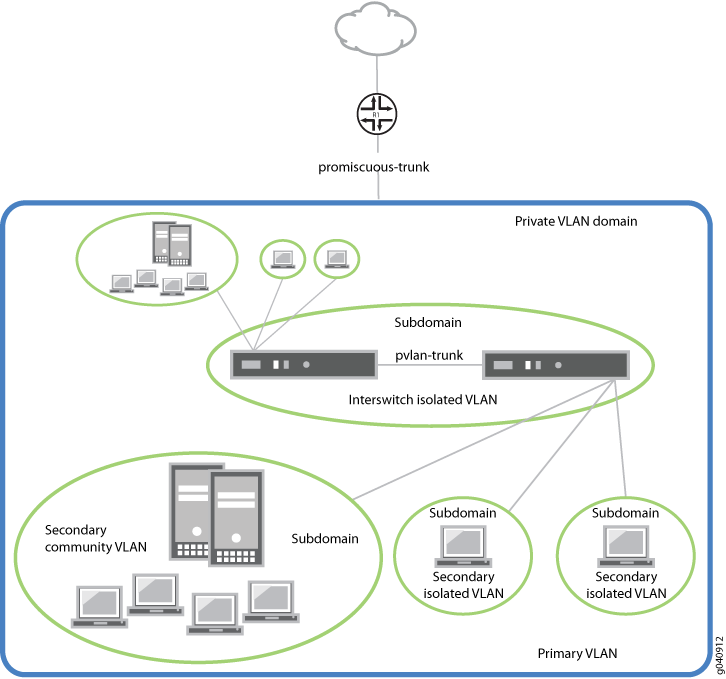
As shown in Figure 3, a PVLAN has only one primary domain and multiple secondary domains. The types of domains are:
Primary VLAN—VLAN used to forward frames downstream to isolated and community VLANs. The primary VLAN of the PVLAN is defined with an 802.1Q tag (VLAN ID) for the complete PVLAN. The primary PVLAN can contain multiple secondary VLANs (one isolated VLAN and multiple community VLANs).
Secondary isolated VLAN—VLAN that receives packets only from the primary VLAN and forwards frames upstream to the primary VLAN. The isolated VLAN is a secondary VLAN nested within the primary VLAN. A primary VLAN can contain only one isolated VLAN. An interface within an isolated VLAN (isolated interface) can forward packets only to a promiscuous port or the PVLAN trunk port. An isolated interface cannot forward packets to another isolated interface; nor can an isolated interface receive packets from another isolated interface. If a customer device needs to have access only to a router, the device must be attached to an isolated trunk port.
Secondary interswitch isolated VLAN—VLAN used to forward isolated VLAN traffic from one switch to another through PVLAN trunk ports. 802.1Q tags are required for interswitch isolated VLANs because IEEE 802.1Q uses an internal tagging mechanism by which a trunking device inserts a 4-byte VLAN frame identification tab into the packet header. An interswitch isolated VLAN is a secondary VLAN nested within the primary VLAN.
Secondary community VLAN—VLAN used to transport frames among members of a community (a subset of users within the VLAN) and to forward frames upstream to the primary VLAN. A community VLAN is a secondary VLAN nested within the primary VLAN. You can configure multiple community VLANs within a single PVLAN. An interface within a specific community VLAN can establish Layer 2 communications with any other interface that belongs to the same community VLAN. An interface within a community VLAN can also communicate with a promiscuous port or the PVLAN trunk port.
Figure 2 shows a PVLAN
spanning multiple switches, where the primary VLAN (100) contains two community domains (300 and 400) and one interswitch isolated domain.
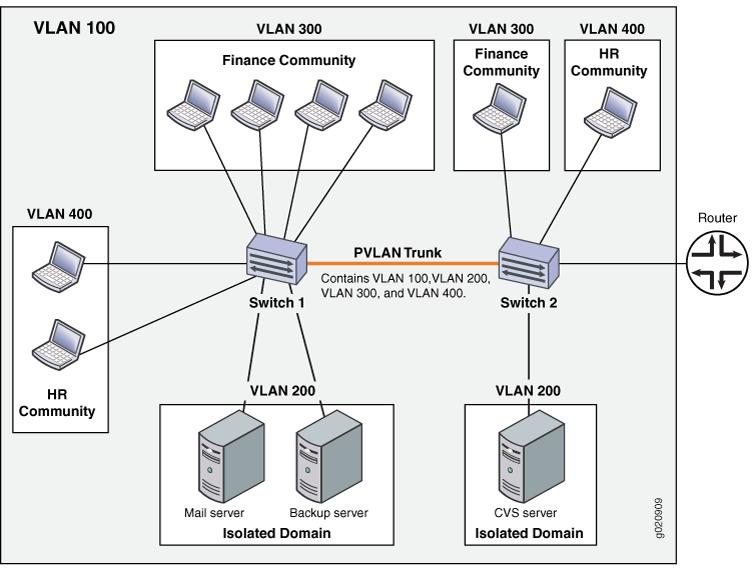
Primary and secondary VLANs count against the limit of 4089 VLANs supported on the QFX Series. For example, each VLAN in Figure 2 counts against this limit.
Typical Structure and Primary Application of PVLANs on MX Series Routers
The configured PVLAN becomes the primary domain, and secondary VLANs become subdomains that are nested inside the primary domain. A PVLAN can be created on a single router. The PVLAN shown in Figure 3 includes one router, with one primary PVLAN domain and multiple secondary subdomains.

The types of domains are:
Primary VLAN—VLAN used to forward frames downstream to isolated and community VLANs.
Secondary isolated VLAN—VLAN that receives packets only from the primary VLAN and forwards frames upstream to the primary VLAN.
Secondary interswitch isolated VLAN—VLAN used to forward isolated VLAN traffic from one router to another through PVLAN trunk ports.
Secondary community VLAN—VLAN used to transport frames among members of a community, which is a subset of users within the VLAN, and to forward frames upstream to the primary VLAN.
PVLANs are supported on MX80 routers, on MX240, MX480, and MX960 routers with DPCs in enhanced LAN mode, on MX Series routers with MPC1, MPC2, and Adaptive Services PICs.
Typical Structure and Primary Application of PVLANs on EX Series Switches
The primary VLAN of the PVLAN is defined with an 802.1Q tag (VLAN ID) for the complete PVLAN. On EX9200 switches, each secondary VLAN must also be defined with its own separate VLAN ID.
Figure 4 shows a
PVLAN on a single switch, where the primary VLAN (VLAN 100) contains two community VLANs (VLAN 300 and VLAN 400) and one isolated VLAN (VLAN 50).
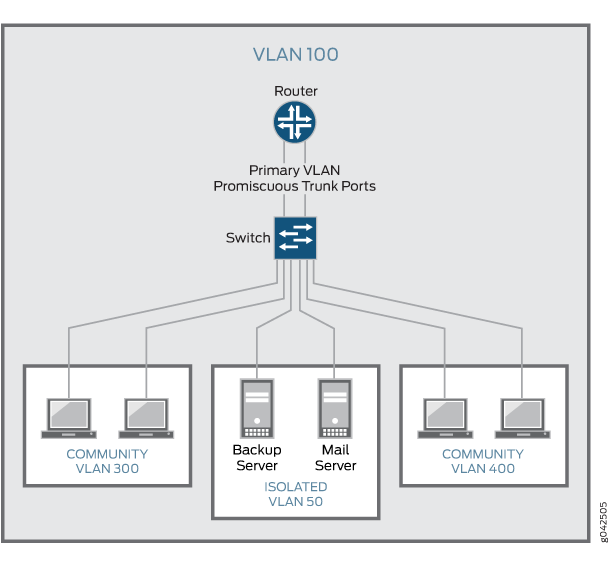
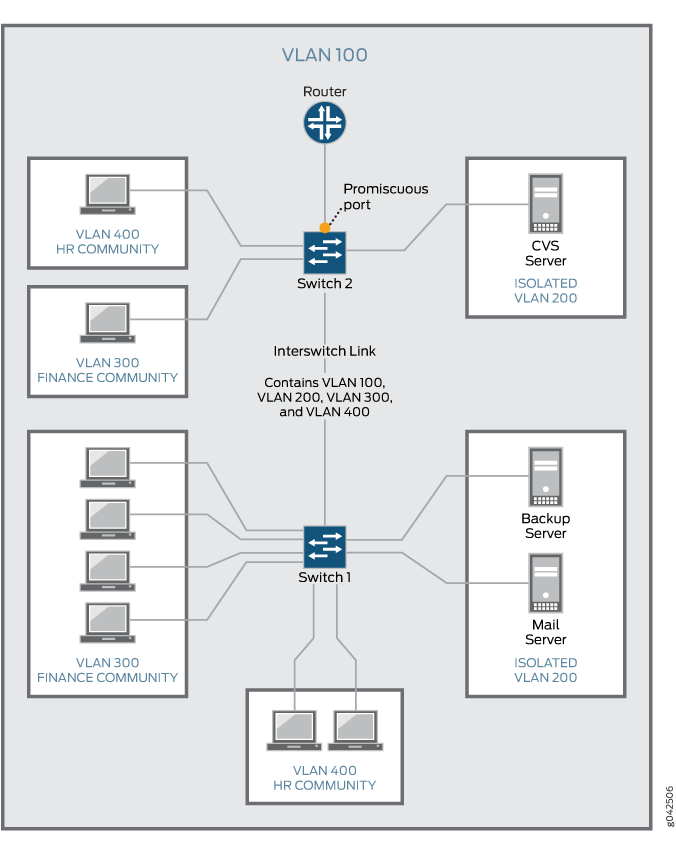
Figure 5 shows a PVLAN
spanning multiple switches, where the primary VLAN (VLAN 100) contains two community VLANs (VLAN 300 and VLAN 400) and one isolated VLAN (VLAN 200). It also shows that Switches
1 and 2 are connected through an interswitch link (PVLAN trunk link).
Also, the PVLANs shown in Figure 4 and Figure 5 use a promiscuous port connected to a router as the means to route Layer 3 traffic among the community and isolated VLANs. Instead of using the promiscuous port connected to a router, you can configure an RVI on the switch in Figure 4 or one of the switches shown in Figure 5 (on some EX switches).
To route Layer 3 traffic between isolated and community VLANs, you must either connect a router to a promiscuous port, as shown in Figure 4 and Figure 5, or configure an RVI.
If you choose the RVI option, you must configure one RVI for the primary VLAN in the PVLAN domain. This RVI serves the entire PVLAN domain regardless of whether the domain includes one or more switches. After you configure the RVI, Layer 3 packets received by the secondary VLAN interfaces are mapped to and routed by the RVI.
When setting up the RVI, you must also enable proxy Address Resolution Protocol (ARP) so that the RVI can handle ARP requests received by the secondary VLAN interfaces.
For information about configuring PVLANs on a single switch and on multiple switches, see Creating a Private VLAN on a Single EX Series Switch (CLI Procedure). For information about configuring an RVI, see Configuring a Routed VLAN Interface in a Private VLAN on an EX Series Switch.
Routing Between Isolated and Community VLANs
To route Layer 3 traffic between isolated and community VLANs, you must connect an external router or switch to a trunk port of the primary VLAN. The trunk port of the primary VLAN is a promiscuous port; therefore, it can communicate with all the ports in the PVLAN.
PVLANs Use 802.1Q Tags to Identify Packets
When packets are marked with a customer-specific 802.1Q tag, that tag identifies ownership of the packets for any switch or router in the network. Sometimes, 802.1Q tags are needed within PVLANs to keep track of packets from different subdomains. Table 1 indicates when a VLAN 802.1Q tag is needed on the primary VLAN or on secondary VLANs.
| On a Single Switch | On Multiple Switches | |
|---|---|---|
| Primary VLAN | Specify an 802.1Q tag by setting a VLAN ID. |
Specify an 802.1Q tag by setting a VLAN ID. |
| Secondary VLAN | No tag needed on VLANs. |
VLANs need 802.1Q tags:
|
PVLANs Use IP Addresses Efficiently
PVLANs provide IP address conservation and efficient allocation of IP addresses. In a typical network, VLANs usually correspond to a single IP subnet. In PVLANs, the hosts in all secondary VLANs belong to the same IP subnet because the subnet is allocated to the primary VLAN. Hosts within the secondary VLAN are assigned IP addresses based on IP subnets associated with the primary VLAN, and their IP subnet masking information reflects that of the primary VLAN subnet. However, each secondary VLAN is a separate broadcast domain.
PVLAN Port Types and Forwarding Rules
PVLANs can use up to six different port types. The network depicted inFigure 2 uses a promiscuous port to transport information to the router, community ports to connect the finance and HR communities to their respective switches, isolated ports to connect the servers, and a PVLAN trunk port to connect the two switches. PVLAN ports have different restrictions:
Promiscuous trunk port—A promiscuous port has Layer 2 communications with all the interfaces that are in the PVLAN, regardless of whether the interface belongs to an isolated VLAN or a community VLAN. A promiscuous port is a member of the primary VLAN, but is not included within one of the secondary subdomains. Layer 3 gateways, DHCP servers, and other trusted devices that need to communicate with endpoint devices are typically connected to a promiscuous port.
PVLAN trunk link—The PVLAN trunk link, which is also known as the interswitch link, is required only when a PVLAN is configured to span multiple switches. The PVLAN trunk link connects the multiple switches that compose the PVLAN.
PVLAN trunk port—A PVLAN trunk port is required in multiswitch PVLAN configurations to span the switches. The PVLAN trunk port is a member of all VLANs within the PVLAN (that is, the primary VLAN, the community VLANs, and the interswitch isolated VLAN), and it carries traffic from the primary VLAN and all secondary VLANs. It can communicate with all ports other than the isolated ports.
Communication between a PVLAN trunk port and an isolated port is usually unidirectional. A PVLAN trunk port’s membership in the interswitch isolated VLAN is egress-only, meaning that an isolated port can forward packets to a PVLAN trunk port, but a PVLAN trunk port does not forward packets to an isolated port (unless the packets ingressed on a promiscuous access port and are therefore being forwarded to all the secondary VLANs in the same primary VLAN as the promiscuous port).
Secondary VLAN trunk port (not shown)—Secondary trunk ports carry secondary VLAN traffic. For a given private VLAN, a secondary VLAN trunk port can carry traffic for only one secondary VLAN. However, a secondary VLAN trunk port can carry traffic for multiple secondary VLANs as long as each secondary VLAN is a member of a different primary VLAN. For example, a secondary VLAN trunk port can carry traffic for a community VLAN that is part of primary VLAN pvlan100 and also carry traffic for an isolated VLAN that is part of primary VLAN pvlan400.
Community port—Community ports communicate among themselves and with their promiscuous ports. Community ports serve only a select group of users. These interfaces are separated at Layer 2 from all other interfaces in other communities or isolated ports within their PVLAN.
Isolated access port—Isolated ports have Layer 2 connectivity only with promiscuous ports and PVLAN trunk ports—an isolated port cannot communicate with another isolated port even if these two ports are members of the same isolated VLAN (or interswitch isolated VLAN) domain. Typically, a server, such as a mail server or a backup server, is connected on an isolated port. In a hotel, each room would typically be connected on an isolated port, meaning that room-to-room communication is not possible, but each room can access the Internet on the promiscuous port.
Promiscuous access port (not shown)—These ports carry untagged traffic. Traffic that ingresses on a promiscuous access port is forwarded to all secondary VLAN ports on the device. If traffic ingresses into the device on a VLAN-enabled port and egresses on a promiscuous access port, the traffic is untagged on egress. If tagged traffic ingresses on a promiscuous access port, the traffic is discarded.
Interswitch link port—An interswitch link (ISL) port is a trunk port that connects two routers when a PVLAN spans those routers. The ISL port is a member of all VLANs within the PVLAN (that is, the primary VLAN, the community VLANs, and the isolated VLAN).
Communication between an ISL port and an isolated port is unidirectional. An ISL port’s membership in the interswitch isolated VLAN is egress-only, meaning that incoming traffic on the ISL port is never assigned to the isolated VLAN. An isolated port can forward packets to a PVLAN trunk port, but a PVLAN trunk port cannot forward packets to an isolated port. Table 3 summarizes whether Layer 2 connectivity exists between the different types of ports.
Table 2 summarizes Layer 2 connectivity between the different types of ports within a PVLAN on EX Series switches that support ELS.
From Port Type |
To Isolated Ports? |
To Promiscuous Ports? |
To Community Ports? |
To Inter-Switch Link Port? |
|---|---|---|---|---|
Isolated |
Deny |
Permit |
Deny |
Permit |
Promiscuous |
Permit |
Permit |
Permit |
Permit |
Community 1 |
Deny |
Permit |
Permit |
Permit |
Port Type |
Promiscuous Trunk |
PVLAN Trunk |
Secondary Trunk |
Community |
Isolated Access |
Promiscuous access |
|---|---|---|---|---|---|---|
Promiscuous trunk |
Yes |
Yes |
Yes |
Yes |
Yes |
Yes |
PVLAN trunk |
Yes |
Yes |
Yes |
Yes—same community only |
Yes |
Yes |
Secondary Trunk |
Yes |
Yes |
No |
Yes |
No |
Yes |
Community |
Yes |
Yes |
Yes |
Yes—same community only |
No |
Yes |
Isolated access |
Yes |
Yes—unidirectional only |
No |
No |
No |
Yes |
Promiscuous access |
Yes |
Yes |
Yes |
Yes |
Yes |
No |
Table 4 summarizes whether or not Layer 2 connectivity exists between the different types of ports within a PVLAN.
Port Type To: → From:↓ |
Promiscuous |
Community |
Isolated |
PVLAN Trunk |
RVI |
|---|---|---|---|---|---|
Promiscuous |
Yes |
Yes |
Yes |
Yes |
Yes |
Community |
Yes |
Yes—same community only |
No |
Yes |
Yes |
Isolated |
Yes |
No |
No |
Yes Note:
This communication is unidirectional. |
Yes |
PVLAN trunk |
Yes |
Yes—same community only |
Yes Note:
This communication is unidirectional. |
Yes |
Yes |
RVI |
Yes |
Yes |
Yes |
Yes |
Yes |
As noted in Table 4, Layer 2 communication between an isolated port and a PVLAN trunk port is unidirectional. That is, an isolated port can only send packets to a PVLAN trunk port, and a PVLAN trunk port can only receive packets from an isolated port. Conversely, a PVLAN trunk port cannot send packets to an isolated port, and an isolated port cannot receive packets from a PVLAN trunk port.
If you enable no-mac-learning on a primary
VLAN, all isolated VLANs (or the interswitch isolated VLAN) in the
PVLAN inherit that setting. However, if you want to disable MAC address
learning on any community VLANs, you must configure no-mac-learning on each of those VLANs.
Creating a PVLAN
The flowchart shown in Figure 6 gives you a general idea of the process for creating PVLANs. If you complete your configuration steps in the order shown, you will not violate these PVLAN rules. (In the PVLAN rules, configuring the PVLAN trunk port applies only to a PVLAN that spans multiple routers.)
The primary VLAN must be a tagged VLAN.
If you are going to configure a community VLAN ID, you must first configure the primary VLAN.
If you are going to configure an isolation VLAN ID, you must first configure the primary VLAN.
Configuring a voice over IP (VoIP) VLAN on PVLAN interfaces is not supported.
Configuring a VLAN on a single router is relatively simple, as shown in Figure 6.
Configuring a primary VLAN consists of these steps:
Configure the primary VLAN name and 802.1Q tag.
Set no-local-switching on the primary VLAN.
Configure the promiscuous trunk port and access ports.
Make the promiscuous trunk and access ports members of the primary VLAN.
Within a primary VLAN, you can configure secondary community VLANs or secondary isolated VLANs or both. Configuring a secondary community VLAN consists of these steps:
Configure a VLAN using the usual process.
Configure access interfaces for the VLAN.
Assign a primary VLAN to the community VLAN,
Isolated VLANs are created internally when the isolated VLAN has access interfaces as members and the option no-local-switching is enabled on the primary VLAN.
802.1Q tags are required for interswitch isolated VLANs because IEEE 802.1Q uses an internal tagging mechanism by which a trunking device inserts a 4-byte VLAN frame identification tab into the packet header.
Trunk ports are only needed for multirouter PVLAN configurations—the trunk port carries traffic from the primary VLAN and all secondary VLANs.
Limitations of Private VLANs
The following constraints apply to private VLAN configurations:
An access interface can belong to only one PVLAN domain, that is, it cannot participate in two different primary VLANs.
A trunk interface can be a member of two secondary VLANs as long as the secondary VLANs are in two different primary VLANs. A trunk interface cannot be a member of two secondary VLANs that are in the same primary VLAN.
A single region of Multiple Spanning Tree Protocol (MSTP) must be configured on all VLANs that are included within the PVLAN.
VLAN Spanning Tree Protocol (VSTP) is not supported.
IGMP snooping is not supported with private VLANs.
Routed VLAN interfaces are not supported on private VLANs
Routing between secondary VLANs in the same primary VLAN is not supported.
Some configuration statements cannot be specified on a secondary VLAN. You can configure the following statements at the
[edit vlans vlan-name switch-options]hierarchy level only on the primary PVLAN.If you want to change a primary VLAN to be a secondary VLAN, you must first change it to a normal VLAN and commit the change. For example, you would follow this procedure:
Change the primary VLAN to be a normal VLAN.
Commit the configuration.
Change the normal VLAN to be a secondary VLAN.
Commit the configuration.
Follow the same sequence of commits if you want to change a secondary VLAN to be a primary VLAN. That is, make the secondary VLAN a normal VLAN and commit that change and then change the normal VLAN to be a primary VLAN.
The following features are not supported on PVLANs on Junos OS switches with support for the ELS configuration style:
Egress VLAN firewall filters
Ethernet ring protection (ERP)
Flexible VLAN tagging
Multichassis link aggregation groups (MC-LAGs)
Port mirroring
Q-in-Q tunneling
VLAN Spanning Tree Protocol (VSTP)
Voice over IP (VoIP)
You can configure the following statements at the [edit
vlans vlan-name switch-options] hierarchy
level only on the primary PVLAN:
