Firewall Authentication for Tenant Systems
The firewall authentication feature is introduced for tenant systems in Junos OS Release 18.3R1 on the Juniper SRX Series Firewalls to enable you to restrict or permit users individually or in groups. The authentication requests are initiated based on destination addresses defined in the policies.
Understanding Tenant System Firewall Authentication
A firewall user is a network user who must provide a username and password for authentication when initiating a connection across the firewall.
Firewall authentication is a policy-based authentication method, which requires user to initiate an authentication request through HTTP, FTP or Telnet traffic.
Junos OS enables administrators to restrict and permit firewall users to access protected resources behind a firewall based on their source IP address and other credentials.
The primary administrator configures the following:
maximum and reserved number of firewall authentication sessions in the tenant system.
access profile using the profile configuration command at the
[edit access]hierarchy which is available to all the tenant systems.
Access profiles allows to:
Storing usernames and passwords of users or point to external authentication servers where such information is stored.
Including the order of authentication methods, LDAP or RADIUS server options, and session options.
Associating with a security policy in the tenant system.
After defining the firewall users, create a policy that requires the users to authenticate through one of the authentication modes defined in the Table 1.
Authentication Options |
Description |
Supported Protocols |
Supported Backend |
|---|---|---|---|
Web Authentication |
Users use HTTP to connect to an IP address on the device that is enabled for Web authentication and are prompted for the username and password. Subsequent traffic from the user or host to the protected resource is allowed or denied based on the result of this authentication. |
HTTP HTTPS |
Local LDAP RADIUS SecurId |
Pass-through |
Inline authentication with a host or a user from one zone tries to access resources on another zone. The device uses the supported protocols to collect username and password information, and subsequent traffic from the user or host is allowed or denied based on the result of this authentication. |
HTTP HTTPS TELNET FTP |
Local LDAP RADIUS SecurId |
Web Redirect |
Automatically redirect client to WebAuth page for authentication (http or https) |
HTTP HTTPS |
Local LDAP RADIUS SecurId |
Integrated User Firewall |
SRX Series devices uses WMI client (WMIC) requests to the AD to get IP address-to-user mapping information in Security event logs. |
none |
Active Directory |
User-Firewall |
Same as pass-through but user information is passed to USERID process to go in Auth Table |
HTTP HTTPS |
Local LDAP RADIUS SecurId |
The tenant system administrator configures the following properties for firewall authentication in the tenant system:
Security policy that specifies firewall authentication for matching traffic. Firewall authentication is specified with the firewall-authentication configuration statement at the
[edit security policies from-zone zone-name to-zone zone-name policy policy-name then permit]hierarchy level. In an access profile, users or user groups can be allowed access by the policy can optionally be specified with the client-match configuration statement. If no users or user groups are specified, any user who is successfully authenticated is allowed access.The type of authentication (pass-through or Web authentication), default access profile, and success banner for the FTP, Telnet, or HTTP session. These properties are configured with the firewall-authentication configuration statement at the
[edit access]hierarchy.Host inbound traffic. Protocols, services, or both are allowed to access the tenant system. The types of traffic are configured with the
host-inbound-trafficconfiguration statement at the[edit security zones security-zone zone-name]or[edit security zones security-zone zone-name interfaces interface-name]hierarchy.
Configuring Firewall Authentication for a Tenant System
This example shows how to send different firewall authentication traffic from the client to server across one tenant system using the three authentication modes pass-through, pass-through with web-redirect, and web authentication.
Requirements
This example uses the following hardware and software components:
-
an SRX4100 device
-
Junos OS Release 18.3R1 and later
-
Telnet or HTTP
-
External authentication servers are RADIUS, LDAP, and SecurID
Ensure to have the following configured to send firewall authentication traffic from client to server:
-
Configure security zones for a tenant system
-
Configure interfaces created by the primary administrator
Overview
When a firewall user attempts to initiate a Telnet, HTTP, or HTTPS session to access a resource in another zone, the SRX Series firewall acts a proxy to authenticate the firewall users before allowing the users to access the Telnet, HTTP, or HTTPS servers behind the firewall.
In this example, you can configure a tenant system and bind the security policy to it. When the traffic from is sent from client to server as referred in Figure 1, the users are authenticated based on the authentication process defined in the security policy.
The primary administrator is responsible for creating tenants and assigning the system resources such as routing-instances, interfaces in routing-instances and security-profile to tenant system.
|
Feature |
Name |
Description |
|---|---|---|
|
security-profile |
tn1_pf |
Name of the security profile. This profile specifies the resources to allocate to a tenant system to which the security profile is bound. |
|
interfaces |
xe-0/0/1 xe-0/0/2 |
Name of the interfaces. The interfaces provide traffic connectivity. |
|
access profile |
local_pf radius_pf securid_pf |
Name of the access profiles. These profiles are used to define the users and passwords and to obtain authorization information about the user’s access right. |
|
SSL termination profile |
fwauthhttpspf |
Name of the profile. This profile is used for SSL termination services. |
|
routing-instances |
vr1 |
Instance type as virtual routing instance. |
|
security policies |
p7 |
Name of the policy. This policy is used to configure pass-through firewall-authentication using fwauthhttpspf SSL termination profile. |
|
p1 |
Name of the policy. This policy is used to configure pass-through firewall-authentication using local_pf access profile. |
|
|
p4 |
Name of the policy. This policy is used to configure pass-through web-redirect firewall-authentication using radius_pf. |
|
|
p3 |
Name of the policy. This policy is used to configure web-authentication firewall-authentication. |
Topology
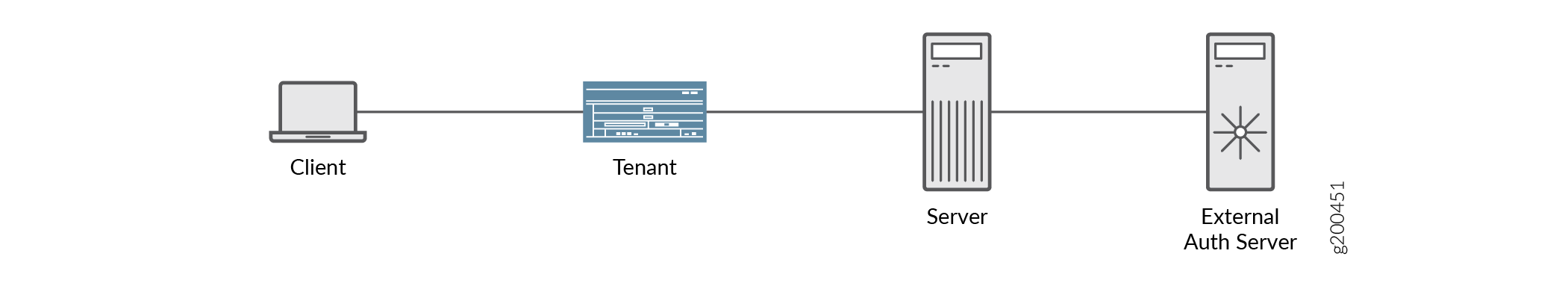
Figure 1 shows the topology used in this configuration example. The tenant shown in this topology is an SRX Series Firewall partitioned to multiple tenants. The external servers supported are RADIUS, LDAP, and SecurID. The communication from the client to the tenant happens over xe-0/0/1 interface and from the tenant to the server happens over xe-0/0/2 interface.
Configuration
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them into a
text file, remove any line breaks, change any details necessary to match your
network configuration, copy and paste the commands into the CLI at the
[edit] hierarchy level, and then enter commit from
configuration mode.
set system security-profile tn1_pf policy maximum 500 set system security-profile tn1_pf policy reserved 100 set system security-profile tn1_pf zone maximum 50 set system security-profile tn1_pf zone reserved 10 set tenants tn1 security-profile tn1_pf set services ssl termination profile fwauthhttpspf server-certificate device set interfaces xe-0/0/1 unit 0 family inet address 192.0.2.0/24 set interfaces xe-0/0/1 unit 0 family inet address 192.0.2.254/16 web-authentication http set interfaces xe-0/0/2 unit 0 family inet address 198.51.100.0/24 web-authentication http set access profile local_pf client test firewall-user password "$ABC123" set access profile local_pf client test1 client-group local-group1 set access profile local_pf client test1 client-group local-group2 set access profile local_pf client test1 firewall-user password "$BCD678" set access profile local_pf client test2 client-group local-group2 set access profile local_pf client test2 firewall-user password "$DEF234" set access profile local_pf client test3 client-group local-group3 set access profile local_pf client test3 firewall-user password "$DBC123" set access profile local_pf client test4 client-group local-group4 set access profile local_pf client test4 firewall-user password "$FAB123" set access profile radius_pf authentication-order radius set access profile radius_pf radius-server 203.0.113.1 secret "$AFD123" set access profile securid_pf authentication-order securid set tenants tn1 routing-instances vr1 instance-type virtual-router set tenants tn1 routing-instances vr1 interface xe-0/0/1.0 set tenants tn1 routing-instances vr1 interface xe-0/0/2.0 set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p1 match source-address any set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p1 match destination-address any set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p1 match application junos-telnet set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p1 then permit firewall-authentication pass-through access-profile local_pf set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p7 match source-address any set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p7 match destination-address any set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p7 match application any set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p7 then permit firewall-authentication pass-through access-profile local_pf set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p7 then permit firewall-authentication pass-through ssl-termination-profile fwauthhttpspf set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p4 match source-address any set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p4 match destination-address any set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p4 match application junos-http set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p4 then permit firewall-authentication pass-through access-profile radius_pf set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p4 then permit firewall-authentication pass-through web-redirect set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p3 match source-address any set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p3 match destination-address any set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p3 match application junos-http set tenants tn1 security policies from-zone tn1_trust to-zone tn1_untrust policy p3 then permit firewall-authentication web-authentication set tenants tn1 security policies policy-rematch set tenants tn1 security zones security-zone tn1_trust interfaces xe-0/0/1.0 host-inbound-traffic system-services all set tenants tn1 security zones security-zone tn1_trust interfaces xe-0/0/1.0 host-inbound-traffic protocols all set tenants tn1 security zones security-zone tn1_untrust interfaces xe-0/0/2.0 host-inbound-traffic system-services all set tenants tn1 security zones security-zone tn1_untrust interfaces xe-0/0/2.0 host-inbound-traffic protocols all set tenants tn1 access firewall-authentication pass-through default-profile local_pf set tenants tn1 access firewall-authentication pass-through telnet banner login ****tenant1_telnet_login_banner set tenants tn1 access firewall-authentication pass-through telnet banner success ****tenant1_telnet_success_banner set tenants tn1 access firewall-authentication pass-through telnet banner fail ****tenant1_telnet_fail_banner set tenants tn1 access firewall-authentication web-authentication default-profile securid_pf set tenants tn1 access firewall-authentication web-authentication banner success ****tenant1_webauth_success_banner
Configuring access profiles and firewall authentication
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode.
-
Configure a security profile tn1_pf and bind it to the tenant system.
[edit system security-profile] user@host# set tn1_pf policy maximum 500 user@host# set tn1_pf policy reserved 100 user@host# set tn1_pf zone maximum 50 user@host# set tn1_pf zone reserved 10
-
Create a tenant system tn1 and bind the security profile tn1_pf to the tenant system.
[edit tenants] user@host# set tn1 security-profile tn1_pf
-
Define the access profile used for SSL termination services for HTTPS traffic to trigger pass-through authentication.
[edit services] user@host# set ssl termination profile fwauthhttpspf server-certificate device
-
Configure interfaces and assign IP addresses. Enable web authentication at xe-0/0/1 interface.
[edit interfaces] user@host# set interfaces xe-0/0/1 unit 0 family inet address 192.0.2.0/24 user@host# set interfaces xe-0/0/1 unit 0 family inet address 192.0.2.254/24 web-authentication http user@host# set interfaces xe-0/0/2 unit 0 family inet address 198.51.100.0/24 web-authentication http
-
Configure routing instances and add interfaces to it.
[edit tenants tn1 routing-instances] user@host# set vr1 instance-type virtual-router user@host# set vr1 interface xe-0/0/1.0 user@host# set vr1 interface xe-0/0/2.0
Step-by-Step Procedure
The primary administrator is responsible for configuring access profiles in the tenant system. To configure access profiles:
-
Create the access profiles to be used for firewall authentication. Access profiles defines clients as firewall users and the passwords that provide them access for firewall authentication. When unauthenticated traffic is permitted for firewall authentication, the user is authenticated based on the access profile configured in this command.
[edit access profile] user@host# set local_pf client test firewall-user password "$ABC123" user@host# set local_pf client test1 client-group local-group1 user@host# set local_pf client test1 client-group local-group2 user@host# set local_pf client test1 firewall-user password "$BCD678" user@host# set local_pf client test2 client-group local-group2 user@host# set local_pf client test2 firewall-user password "$DEF234" user@host# set local_pf client test3 client-group local-group3 user@host# set local_pf client test3 firewall-user password "$DBC123" user@host# set local_pf client test4 client-group local-group4 user@host# set local_pf client test4 firewall-user password "$FAB123"
-
Create an access profile to configure the RADIUS server.
[edit access profile] user@host# set radius_pf authentication-order radius user@host# set radius_pf radius-server 203.0.113.1 secret "$AFD123"
-
Create an access profile to configure SecurID as the server to be used for external authentication.
[edit access profile] user@host# set securid_pf authentication-order securid
Step-by-Step Procedure
Configure different security policies that permit HTTP, HTTPS, and Telnet traffic between zones using pass-through (direct and web-redirect) and web authentication modes in a tenant system.
-
Configure policy p1 for pass-through authentication for Telnet traffic.
[edit tenants tn1 security policies] user@host# set from-zone tn1_trust to-zone tn1_untrust policy p1 match source-address any user@host# set from-zone tn1_trust to-zone tn1_untrust policy p1 match destination-address any user@host# set from-zone tn1_trust to-zone tn1_untrust policy p1 match application junos-telnet user@host# set from-zone tn1_trust to-zone tn1_untrust policy p1 then permit firewall-authentication pass-through access-profile local_pf
-
Configure policy p7 for pass-through authentication for HTTPS traffic.
[edit tenants tn1 security policies] user@host# set from-zone tn1_trust to-zone tn1_untrust policy p7 match source-address any user@host# set from-zone tn1_trust to-zone tn1_untrust policy p7 match destination-address any user@host# set from-zone tn1_trust to-zone tn1_untrust policy p7 match application junos-https user@host# set from-zone tn1_trust to-zone tn1_untrust policy p7 then permit firewall-authentication pass-through access-profile local_pf user@host# set from-zone tn1_trust to-zone tn1_untrust policy p7 then permit firewall-authentication pass-through ssl-termination-profile fwauthhttpspf
-
Configure policy p4 for pass through authentication using web-redirect for HTTP traffic.
[edit tenants tn1 security policies] user@host# set from-zone tn1_trust to-zone tn1_untrust policy p4 match source-address ipv6_addr1 user@host# set from-zone tn1_trust to-zone tn1_untrust policy p4 match destination-address any user@host# set from-zone tn1_trust to-zone tn1_untrust policy p4 match application junos-http user@host# set from-zone tn1_trust to-zone tn1_untrust policy p4 then permit firewall-authentication pass-through access-profile radius_pf user@host# set from-zone tn1_trust to-zone tn1_untrust policy p4 then permit firewall-authentication pass-through web-redirect
-
Configure policy p3 for web authentication for HTTP traffic.
[edit tenants tn1 security policies] user@host# set from-zone tn1_trust to-zone tn1_untrust policy p3 match source-address any user@host# set from-zone tn1_trust to-zone tn1_untrust policy p3 match destination-address any user@host# set from-zone tn1_trust to-zone tn1_untrust policy p3 match application junos-http user@host# set from-zone tn1_trust to-zone tn1_untrust policy p3 then permit firewall-authentication web-authentication user@host# set policy-rematch
-
Configure zones and assign interfaces to each zone in a tenant system.
[edit tenants tn1 security zones] user@host# set security-zone tn1_trust interfaces xe-0/0/1.0 host-inbound-traffic system-services all user@host# set security-zone tn1_trust interfaces xe-0/0/1.0 host-inbound-traffic protocols all user@host# set security-zone tn1_untrust interfaces xe-0/0/2.0 host-inbound-traffic system-services all user@host# set security-zone tn1_untrust interfaces xe-0/0/2.0 host-inbound-traffic protocols all
-
Define a success banner for Telnet sessions. Configure firewall authentication pass-through and web authentication banner for applications in a tenant system.
[edit tenants tn1 access firewall-authentication] user@host# set pass-through default-profile local_pf user@host# set pass-through telnet banner login ****tenant1_telnet_login_banner user@host# set pass-through telnet banner success ****tenant1_telnet_success_banner user@host# set pass-through telnet banner fail ****tenant1_telnet_fail_banner user@host# set web-authentication default-profile securid_pf user@host# set web-authentication banner success ****tenant1_webauth_success_banner
Results
From configuration mode, confirm your configuration by entering the show
system security-profile, show interfaces,
show access, show tenants, and
show services ssl termination commands. If the output does
not display the intended configuration, repeat the configuration instructions in
this example to correct it.
user@host# show interfaces
xe-0/0/1 {
unit 0 {
family inet {
address 192.0.2.0/24;
address 192.0.2.254/24 {
web-authentication {
http;
https;
}
}
}
}
}
xe-0/0/2 {
unit 0 {
family inet {
address 198.51.100.0/24;
}
}
}
user@host#show services ssl termination
profile fwauthhttpspf {
server-certificate device;
}
user@host#show access
profile local_pf {
client test {
firewall-user {
password "$ABC123"; ## SECRET-DATA
}
}
client test1 {
client-group [ local-group1 local-group2 ];
firewall-user {
password "$BCD678"; ## SECRET-DATA
}
}
client test2 {
client-group local-group2;
firewall-user {
password "$DEF234"; ## SECRET-DATA
}
}
client test3 {
client-group local-group3;
firewall-user {
password "$DBC123"; ## SECRET-DATA
}
}
client test4 {
client-group local-group4;
firewall-user {
password "$FAB123"; ## SECRET-DATA
}
}
session-options {
client-session-timeout 3;
}
}
profile radius_pf {
authentication-order radius;
session-options {
client-session-timeout 3;
}
radius-server {
203.0.113.1 secret "$AFD123"; ## SECRET-DATA
}
}
user@host# show system security-profile
tn1_pf {
policy {
maximum 500;
reserved 100;
}
zone {
maximum 50;
reserved 10;
}
}
user@host# show tenants
tn1 {
routing-instances {
vr1 {
instance-type virtual-router;
interface xe-0/0/1.0;
interface xe-0/0/2.0;
}
}
security-profile {
tn1_pf;
}
security {
policies {
from-zone tn1_trust to-zone tn1_untrust {
policy p2 {
match {
source-address any;
destination-address any;
application any;
}
then {
permit {
firewall-authentication {
pass-through {
access-profile ldap_pf;
}
}
}
}
}
}
}
zones {
security-zone tn1_trust {
interfaces {
xe-0/0/1.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
}
}
}
security-zone tn1_untrust {
interfaces {
xe-0/0/2.0 {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
}
}
}
}
}
access {
firewall-authentication {
pass-through {
default-profile local_pf;
telnet {
banner {
login ****tenant1_telnet_login_banner;
success ****tenant1_telnet_success_banner;
fail ****tenant1_telnet_fail_banner;
}
}
}
web-authentication {
default-profile radius_pf;
banner {
success ****tenant1_webauth_success_banner;
}
}
}
}
}
If you are done configuring the device, enter commitfrom
configuration mode.
Verification
Verifying Firewall User Authentication and Monitoring Users and IP Addresses in the Authentication Table
Purpose
The administrator for tenant system can use the show security
firewall-authentication users or show security
firewall-authentication history commands to view the
information about firewall users and history for the tenant system. The
administrator for the tenant system can use the same commands to view
information for all tenant systems.
Action
From operational mode, enter the following show commands:
user@host> show security firewall-authentication history tenant tn1 identifier 10
Username: test
Source IP: 10.12.12.10Authentication state: Success
Authentication method: Pass-through using HTTP
Access start date: 2018-05-31
Access start time: 17:07:38
Duration of user access: 0:10:01
Lsys: root-logical-system
Tenant: tn1
Source zone: trust-tn1
Destination zone: untrust-tn1
Access profile: test
Bytes sent by this user: 380
Bytes received by this user: 0
user@host> show security firewall-authentication history tenant tn1
History of firewall authentication data:
Authentications: 2
Id Source Ip Date Time Duration Status User
1 203.0.113.10 2018-05-27 09:33:05 0:01:44 Success test
2 203.0.113.10 2018-05-27 10:01:09 0:10:02 Success test
user@host> show security firewall-authentication users tenant tn1
Firewall authentication data:
Total users in table: 1
Id Source Ip Src zone Dst zone Profile Age Status User
2 203.0.113.10 N/A N/A test 1 Success test
Meaning
The output displays the authenticated firewall users and the firewall authentication history of the users for the tenant system
Understanding Integrated User Firewall Support in a Tenant System
Tenant system supports the user firewall authentication in shared and active mode.
Starting in Junos OS Release 19.1R1, user firewall authentication is supported on tenant systems using a shared model. In this model, the primary logical system shares the user firewall configuration and authentication entries with the tenant system. The primary logical system shares the authentication data with the tenant system, which is collected from the Local authentication, Active Directory (AD) authentication, firewall authenticationft, Juniper Identity Management Service (JIMS), and ClearPass authentication.
In the shared model, user firewall related configuration is configured under the primary logical system, such as authentication source, authentication source priority, authentication entries timeout, and IP query or individual query and so on. The user firewall provides user information service for an application on the SRX Series Firewall, such as policy and logging. Traffic from a tenant system queries the authentication tables from the primary logical system.
The authentication tables are managed by a primary logical system. The tenant systems share the authentication tables. Traffic from the primary logical system and the tenant systems query the same authentication table. Tenant systems enable the use of the source-identity in security policy.
For example, if the primary logical system is configured with employee and the tenant system is configured with the source-identity manager, then the reference group of this authentication entry includes employee and manager. This reference group contains the same authentication entries from primary logical system and tenant system.
Starting in Junos OS Release 19.3R1, support for user firewall authentication is enhanced by using a customized model through integrated JIMS with active mode. In this model, the tenant system extracts the authentication entries from the root level. The primary logical system is configured to the JIMS server based on the logical system and tenant system name. In active mode the SRX Series Firewall actively queries the authenticaton entries received from the JIMS server through HTTPs protocol. To reduce the data exchange, firewall filters are applied.
The user firewall uses the tenant system name as a differentiator and is consistent between the JIMS server and SRX Series Firewall. The JIMS server sends the differentiator which is included in the authentication entry. The authentication entries are distributed into the root logical system, when the differentiator is set as default for the primary logical system.
The user firewall support In-service software upgrade (ISSU) for tenant systems, as user firewall changes the internal database table format from Junos OS Release 19.2R1 onwards. Prior to Junos OS Release 19.2R1, the ISSU is not supported for tenant systems.
Starting in Junos OS Release 20.2R1, logical systems and tenant systems support user firewall authentication with Unified Access Control (UAC).
- Limitation of Using User Firewall Authentication in Tenant Systems
- Limitation of using User Firewall Authentication in customized model on Tenant Systems
Limitation of Using User Firewall Authentication in Tenant Systems
Using user firewall authentication on tenant systems has the following limitation:
The IP addresses under different tenant systems must not overlap. If the address overlap, then the authentication entry is changed when different users log in under different tenant systems.
Limitation of using User Firewall Authentication in customized model on Tenant Systems
Using user firewall authentication in customized model on tenant systems has the following limitation:
The JIMS server configurations to be configured under the root logical systems.
The tenant system name should be consistent and unique between the JIMS server and the SRX Series Firewall.
See Also
Example: Configuring Integrated User Firewall Identification Management for a Tenant System
This example shows how to configure the SRX Series Firewall's advanced query feature for obtaining user identity information from the Juniper Identity Management Service (JIMS) and the security policy to match the source identity for a tenant system. In the primary logical system, user firewall is configured with JIMS, and then the primary logical system manages all of authentication entries coming from JIMS. In this example, the primary logical systems shares the authentication entries with the tenant systems.
Requirements
This example uses the following hardware and software components:
SRX1500 devices operating in chassis clustering
JIMS server
Junos OS Release 19.1 R1
Overview
In this example, you can configure JIMS with HTTPs connection on port 443 and primary server with IPv4 address on the primary logical system, policy p1 with source-identity "group1" of dc0 domain on tenant system TN1, policy p1 with source-identity "group1" of dc0 domain on tenant system TN2, and send traffic from and through tenant system TN1 to tenant system TN2. You can view the authentication entries on primary logical system and tenant systems (TN1 and TN2) even after rebooting the primary node.
Configuration
CLI Quick Configuration
To quickly configure this example, copy the
following commands, paste them into a text file, remove any line breaks,
change any details necessary to match your network configuration,
copy and paste the commands into the CLI at the [edit] hierarchy
level, and then enter commit from configuration mode.
set tenants TN1 security policies from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 match source-address any set tenants TN1 security policies from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 match destination-address any set tenants TN1 security policies from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 match application any set tenants TN1 security policies from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 match source-identity "example.com\group1" set tenants TN1 security policies from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 then permit set tenants TN1 security policies from-zone TN1_trust to-zone TN1_untrust policy TN1_policy2 match source-address any set tenants TN1 security policies from-zone TN1_trust to-zone TN1_untrust policy TN1_policy2 match destination-address any set tenants TN1 security policies from-zone TN1_trust to-zone TN1_untrust policy TN1_policy2 match application any set tenants TN1 security policies from-zone TN1_trust to-zone TN1_untrust policy TN1_policy2 then permit set tenants TN1 security policies from-zone TN1_untrust to-zone TN1_trust policy TN1_policy3 match source-address any set tenants TN1 security policies from-zone TN1_untrust to-zone TN1_trust policy TN1_policy3 match destination-address any set tenants TN1 security policies from-zone TN1_untrust to-zone TN1_trust policy TN1_policy3 match application any set tenants TN1 security policies from-zone TN1_untrust to-zone TN1_trust policy TN1_policy3 then permit set tenants TN1 security policies policy-rematch set tenants TN2 security policies from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 match source-address any set tenants TN2 security policies from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 match destination-address any set tenants TN2 security policies from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 match application any set tenants TN2 security policies from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 match source-identity "example.com\group2" set tenants TN2 security policies from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 then permit set tenants TN2 security policies policy-rematch set services user-identification identity-management connection connect-method https set services user-identification identity-management connection port 443 set services user-identification identity-management connection primary address 192.0.2.5 set services user-identification identity-management connection primary client-id otest set services user-identification identity-management connection primary client-secret "$ABC123" set security policies from-zone root_trust to-zone root_trust policy root_policy1 match source-address any set security policies from-zone root_trust to-zone root_trust policy root_policy1 match destination-address any set security policies from-zone root_trust to-zone root_trust policy root_policy1 match application any set security policies from-zone root_trust to-zone root_trust policy root_policy1 then permit set security policies policy-rematch set security zones security-zone root_trust interfaces reth1.0 host-inbound-traffic system-services all set security zones security-zone root_trust interfaces reth1.0 host-inbound-traffic protocols all set security zones security-zone root_trust interfaces lt-0/0/0.1 host-inbound-traffic system-services all set security zones security-zone root_trust interfaces lt-0/0/0.1 host-inbound-traffic protocols all set firewall family inet filter impair-ldap term allow_all then accept
Configuring user firewall identification management
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the Junos OS CLI User Guide.
To configure user firewall identification management:
Log in to the primary logical system as the primary administrator and enter configuration mode.
user@host> configure user@host#
Create tenant systems.
[edit tenants] user@host#set TN1 user@host#set TN2
Configure a security policy TN1_policy1 with source-identity group1 on the tenant system TN1 that permits traffic from TN1_trust to TN1_trust.
[edit security policies] user@host#set from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 match source-address any user@host#set from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 match destination-address any user@host#set from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 match application any user@host#set from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 match source-identity "example.com\group1" user@host#set from-zone TN1_trust to-zone TN1_trust policy TN1_policy1 then permit
Configure a security policy TN1_policy2 that permits traffic from TN1_trust to TN1_untrust.
[edit security policies] user@host#set from-zone TN1_trust to-zone TN1_untrust policy TN1_policy2 match source-address any user@host#set from-zone TN1_trust to-zone TN1_untrust policy TN1_policy2 match destination-address any user@host#set from-zone TN1_trust to-zone TN1_untrust policy TN1_policy2 match application any user@host#set from-zone TN1_trust to-zone TN1_untrust policy TN1_policy2 then permit
Configure a security policy TN1_policy3 that permits traffic from TN1_untrust to TN1_trust.
[edit security policies] user@host#set from-zone TN1_untrust to-zone TN1_trust policy TN1_policy3 match source-address any user@host#set from-zone TN1_untrust to-zone TN1_trust policy TN1_policy3 match destination-address any user@host#set from-zone TN1_untrust to-zone TN1_trust policy TN1_policy3 match application any user@host#set from-zone TN1_untrust to-zone TN1_trust policy TN1_policy3 then permit user@host#set policy-rematch
Configure security zone and assign interfaces to each zone.
[edit security zones] user@host#set security-zone TN1_trust interfaces reth2.0 host-inbound-traffic system-services all user@host#set security-zone TN1_trust interfaces reth2.0 host-inbound-traffic protocols all user@host#set security-zone TN1_trust interfaces lt-0/0/0.11 host-inbound-traffic system-services all user@host#set security-zone TN1_trust interfaces lt-0/0/0.11 host-inbound-traffic protocols all user@host#set security-zone TN1_untrust interfaces reth3.0 host-inbound-traffic system-services all user@host#set security-zone TN1_untrust interfaces reth3.0 host-inbound-traffic protocols all
Configure a security policy TN2_policy1 with source-identity group1 that permits traffic from TN2_untrust to TN2_untrust on TN2.
[edit security policies] user@host#set from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 match source-address any user@host#set from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 match destination-address any user@host#set from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 match application any user@host#set from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 match source-identity "example.com\group2" user@host#set from-zone TN2_untrust to-zone TN2_untrust policy TN2_policy1 then permit user@host#set policy-rematch
Configure security zones and assign interfaces to each zone on TN2.
[edit security zones] user@host#set security-zone TN2_untrust interfaces reth4.0 host-inbound-traffic system-services all user@host#set security-zone TN2_untrust interfaces reth4.0 host-inbound-traffic protocols all user@host#set security-zone TN2_untrust interfaces lt-0/0/0.21 host-inbound-traffic system-services all user@host#set security-zone TN2_untrust interfaces lt-0/0/0.21 host-inbound-traffic protocols all
-
Configure JIMS as the authentication source for advanced query requests with the primary address. The SRX Series Firewall requires this information to contact the server.
[edit services user-identification identity-management] user@host#set connection port 443 user@host#set connection connect-method https user@host#set connection primary address 192.0.2.5 user@host#set connection primary client-id otest user@host#set connection primary client-secret test user@host#set authentication-entry-timeout 0
Configure security policies and zones on the primary logical system.
[edit security policies] user@host#set from-zone root_trust to-zone root_trust policy root_policy1 match source-address any user@host#set from-zone root_trust to-zone root_trust policy root_policy1 match destination-address any user@host#set from-zone root_trust to-zone root_trust policy root_policy1 match application any user@host#set from-zone root_trust to-zone root_trust policy root_policy1 then permit user@host#set policy-rematch
Configure security zones and assign interfaces to each zone on primary logical system.
[edit security zones] user@host#set security-zone root_trust interfaces reth1.0 host-inbound-traffic system-services all user@host#set security-zone root_trust interfaces reth1.0 host-inbound-traffic protocols all user@host#set security-zone root_trust interfaces lt-0/0/0.1 host-inbound-traffic system-services all user@host#set security-zone root_trust interfaces lt-0/0/0.1 host-inbound-traffic protocols all user@host#set firewall family inet filter impair-ldap term allow_all then accept
Results
From configuration mode, confirm your configuration
by entering the show services user-identification identity-management show chassis cluster command. If the output does not
display the intended configuration, repeat the configuration instructions
in this example to correct it.
user@host# show services user-identification identity-management
connection {
connect-method https;
port 443;
primary {
address 192.0.2.5;
client-id otest;
client-secret "$ABC123"; ## SECRET-DATA
}
}
user@host# show chassis cluster
reth-count 5;
control-ports {
fpc 3 port 0;
fpc 9 port 0;
}
redundancy-group 0 {
node 0 priority 200;
node 1 priority 1;
}
redundancy-group 1 {
node 0 priority 100;
node 1 priority 1;
}
redundancy-group 2 {
node 0 priority 100;
node 1 priority 1;
}
redundancy-group 3 {
node 0 priority 100;
node 1 priority 1;
}
redundancy-group 4 {
node 0 priority 100;
node 1 priority 1;
}
If you are done configuring the device, enter commit from configuration mode.
Verification
To confirm that the configuration is working properly, perform the below tasks:
Verifying chassis cluster status and authentication entries
Purpose
To verify authentication entries in a tenant system.
Action
To verify the configuration is working properly, enter
the show services user-identification authentication-table authentication-source
identity-management tenant TN1 command.
user@host> show services user-identification authentication-table authentication-source identity-management tenant TN1
node0:
--------------------------------------------------------------------------
Logical System: root-logical-system
Domain: ad2012.jims.com
Total entries: 3
Source IP Username groups(Ref by policy) state
2001:db8:aaaa: N/A Valid
2001:db8:aaaa: administrator Valid
203.0.113.50 administrator Valid
node1:
--------------------------------------------------------------------------
Logical System: root-logical-system
Domain: ad2012.jims.com
Total entries: 3
Source IP Username groups(Ref by policy) state
2001:db8:aaaa: N/A Valid
2001:db8:aaaa: administrator Valid
203.0.113.50 administrator Valid
Meaning
The output displays the authentication entries that are shared from the primary logical system to the tenant system.
Verifying chassis cluster status
Purpose
Verify chassis cluster status after rebooting the primary node.
Action
To verify the configuration is working properly, enter
the show chassis cluster status command.
user@host> show chassis cluster status
Monitor Failure codes:
CS Cold Sync monitoring FL Fabric Connection monitoring
GR GRES monitoring HW Hardware monitoring
IF Interface monitoring IP IP monitoring
LB Loopback monitoring MB Mbuf monitoring
NH Nexthop monitoring NP NPC monitoring
SP SPU monitoring SM Schedule monitoring
CF Config Sync monitoring RE Relinquish monitoring
Cluster ID: 6
Node Priority Status Preempt Manual Monitor-failures
Redundancy group: 0 , Failover count: 0
node0 200 hold no no None
node1 1 secondary no no None
Redundancy group: 1 , Failover count: 0
node0 0 hold no no CS
node1 1 secondary no no None
Redundancy group: 2 , Failover count: 0
node0 0 hold no no CS
node1 1 secondary no no None
Redundancy group: 3 , Failover count: 0
node0 0 hold no no CS
node1 1 secondary no no None
Redundancy group: 4 , Failover count: 0
node0 0 hold no no CS
node1 1 secondary no no NoneMeaning
The output displays user identification management session existing on TN1 and TN2 after rebooting the primary node.
Example: Configure Integrated User Firewall in Customized Model for Tenant System
This example shows how to configure the integrated user firewall by using a customized model through the Juniper Identity Management Service (JIMS) server with active mode for a tenant system. The primary logical systems does not share the authentication entries with the tenant systems. The SRX Series Firewall queries the authentication entries received from the JIMS server through HTTPs protocol in active mode.
In this example following configurations are performed:
-
Active JIMS Server Configuration
-
Tenant System IP Query Configuration
-
Tenant System Authentication Entry Configuration
-
Tenant System Security Policy Configuration
Requirements
This example uses the following hardware and software components:
-
JIMS server version 2.0
-
Junos OS Release 19.3R1
Before you begin, be sure you have following information:
-
The IP address of the JIMS server.
-
The port number on the JIMS server for receiving HTTPs requests.
-
The client ID from the JIMS server for active query server.
-
The client secret from the JIMS server for active query server.
Overview
In this example, you can configure JIMS with HTTPs connection on port 443 and
primary server with IPv4 address on the primary logical system, policy p2 with
source-identity group1 on tenant system
TSYS1.
Configuration
CLI Quick Configuration
To quickly configure this example, copy the following commands, paste them
into a text file, remove any line breaks, change any details necessary to
match your network configuration, copy and paste the commands into the CLI
at the [edit] hierarchy level, and then enter commit from
configuration mode.
set services user-identification logical-domain-identity-management active query-server jims1 connection connect-method https set services user-identification logical-domain-identity-management active query-server jims1 connection port 443 set services user-identification logical-domain-identity-management active query-server jims1 connection primary address 192.0.2.5 set services user-identification logical-domain-identity-management active query-server jims1 connection primary client-id otest set services user-identification logical-domain-identity-management active query-server jims1 connection primary client-secret "$ABC123" set tenants TSYS1 services user-identification logical-domain-identity-management active ip-query query-delay-time 30 set tenants TSYS1 services user-identification logical-domain-identity-management active invalid-authentication-entry-timeout 1 set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 match source-address any set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 match destination-address any set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 match application any set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 match source-identity "example.com\group1" set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 then permit
Configuring Integrated User Firewall in Customized Model:
Step-by-Step Procedure
The following example requires you to navigate various levels in the configuration hierarchy. For instructions on how to do that, see Using the CLI Editor in Configuration Mode in the Junos OS CLI User Guide.
To configure Integrated User Firewall in Customized Model:
-
Configure JIMS as the authentication source for advanced query requests with the primary address. The SRX Series Firewall requires this information to contact the server.
user@host# set services user-identification logical-domain-identity-management active query-server jims1 connection connect-method https user@host# set services user-identification logical-domain-identity-management active query-server jims1 connection port 443 user@host# set services user-identification logical-domain-identity-management active query-server jims1 connection primary address 192.0.2.5 user@host# set services user-identification logical-domain-identity-management active query-server jims1 connection primary client-id otest user@host# set services user-identification logical-domain-identity-management active query-server jims1 connection primary client-secret "$ABC123"
-
Configure the IP query delay time for TSYS1.
user@host# set tenants TSYS1 services user-identification logical-domain-identity-management active ip-query query-delay-time 30
-
Configure the authentication entry attributes for TSYS1.
user@host# set tenants TSYS1 services user-identification logical-domain-identity-management active invalid-authentication-entry-timeout 1
-
Configure the security policy p2 that permits traffic from-zone untrust to-zone trust for TSYS1.
user@host# set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 match source-address any user@host# set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 match destination-address any user@host# set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 match application any user@host# set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 match source-identity "example.com\group1" user@host#set tenants TSYS1 security policies from-zone untrust to-zone trust policy p2 then permit
Results
From configuration mode, confirm your configuration by entering the
show services user-identification
logical-domain-identity-management and show tenants
TSYS1 commands. If the output does not display the intended
configuration, repeat the configuration instructions in this example to
correct it.
user@host# show services user-identification logical-domain-identity-management
active {
query-server jims1 {
connection {
connect-method https;
port 443;
primary {
address 10.1.1.1;
client-id otest;
client-secret "$ABC123"; ## SECRET-DATA
}
}
}
}
user@host# show tenants TSYS1
security {
policies {
from-zone untrust to-zone trust {
policy p2 {
match {
source-address any;
destination-address any;
application any;
source-identity "example.com\group1";
}
then {
permit;
}
}
}
}
}
services {
user-identification {
logical-domain-identity-management {
active {
invalid-authentication-entry-timeout 1;
ip-query {
query-delay-time 30;
}
}
}
}
}
If you are done configuring the device, enter commit from
configuration mode.
Verification
To confirm that the configuration is working properly, perform the below tasks:
- Verifying the User Identification Identity Management status
- Verifying the User Identification Identity Management status counters
- Verifying the User Identification Authentication Table
Verifying the User Identification Identity Management status
Purpose
Verify the user identification status for identity-management as the authentication source.
Action
To verify the configuration is working properly, enter the show
services user-identification logical-domain-identity-management
status command.
user@host>show services user-identification logical-domain-identity-management status
node0:
--------------------------------------------------------------------------
Query server name :jims1
Primary server :
Address : 10.1.1.1
Port : 443
Connection method : HTTPS
Connection status : Online
Last received status message : OK (200)
Access token : isdHIbl8BXwxFftMRubGVsELRukYXtW3rtKmHiL
Token expire time : 2017-11-27 23:45:22
Secondary server :
Address : Not configured
Meaning
The output displays the statistical data about the advanced user query function batch queries and IP queries, or show status on the Juniper Identity Management Service servers.
Verifying the User Identification Identity Management status counters
Purpose
Verify the user identification counters for identity-management as the authentication source.
Action
To verify the configuration is working properly, enter the show
services user-identification logical-domain-identity-management
counters command.
user@host>show services user-identification logical-domain-identity-management counters
node0:
--------------------------------------------------------------------------
Query server name :jims1
Primary server :
Address : 10.208.137.208
Batch query sent number : 65381
Batch query total response number : 64930
Batch query error response number : 38
Batch query last response time : 2018-08-14 15:10:52
IP query sent number : 10
IP query total response number : 10
IP query error response number : 0
IP query last response time : 2018-08-13 12:41:56
Secondary server :
Address : Not configured
Meaning
The output displays the statistical data about the advanced user query function batch queries and IP queries, or show counters on the Juniper Identity Management Service servers.
Verifying the User Identification Authentication Table
Purpose
Verify the user identity information authentication table entries for the specified authentication source.
Action
To verify the configuration is working properly, enter the show
services user-identification authentication-table
authentication-source all tenant TSYS1 command.
user@host>show services user-identification authentication-table authentication-source all tenant TSYS1
node0:
--------------------------------------------------------------------------
Tenant System: TSYS1
Domain: ad03.net
Total entries: 4
Source IP Username groups(Ref by policy) state
10.12.0.2 administrator posture-healthy Valid
10.12.0.15 administrator posture-healthy Valid
2001:db8:3000::5 N/A posture-healthy Valid
fe80::342c:302b N/A posture-healthy Valid
Meaning
The output displays the entire content of the specified authentication source’s authentication table, or a specific domain, group, or user based on the user name. Display the identity information for a user based on the IP address of the user’s device.
Change History Table
Feature support is determined by the platform and release you are using. Use Feature Explorer to determine if a feature is supported on your platform.
