ON THIS PAGE
Web Protocol Contexts
These attack objects and groups are designed to detect known attack patterns and protocol anomalies within the network traffic. You can configure attack objects and groups for web protocols as match conditions in IDP policy rules.
Service Contexts: HTTP
The table displays the security context details for HTTP:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
http-authorization (CTS) |
Matches the username and password decoded from the Authorization: Basic header in an HTTP request. 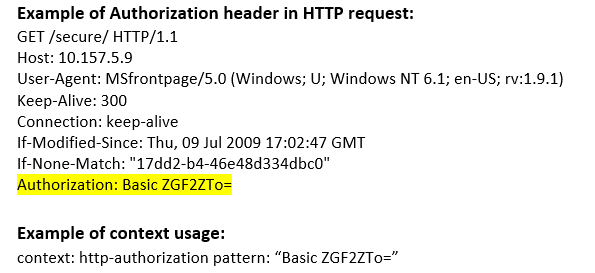 |
|||
http-data (ANY) |
Matches any HTTP data in an HTTP transaction that is not text/html, text/plain, or FORM values in a POST request. 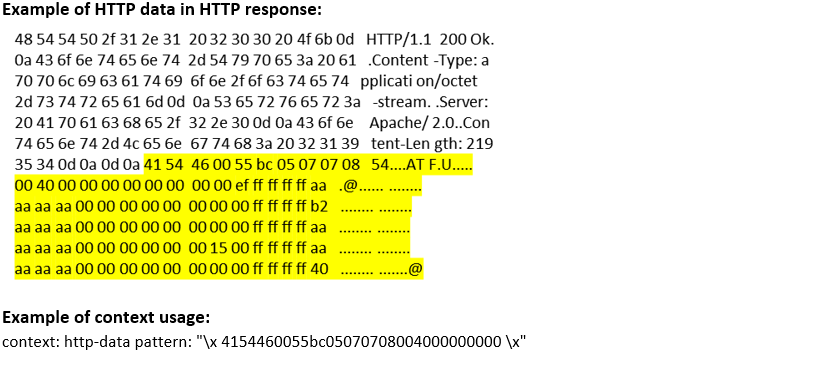 |
|||
http-first-data-chunk (ANY) |
Matches the first data chunk in an HTTP transaction. 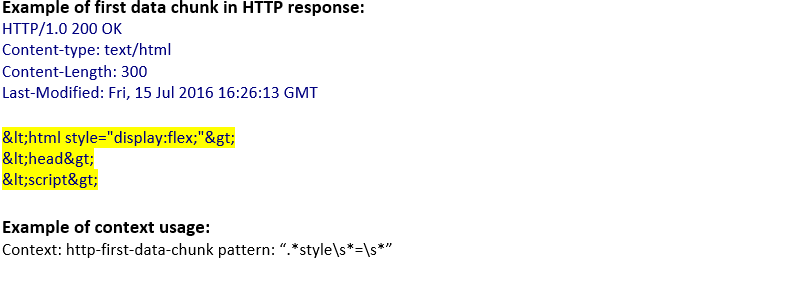 |
|||
http-flash |
Matches http payload when content type is flash video or application.  |
|||
http-form-data (CTS) |
Matches each of the form values in a POST request of an HTTP transaction. |
|||
http-get-url (CTS) |
Matches the URL in an HTTP get request as it appears in the stream. 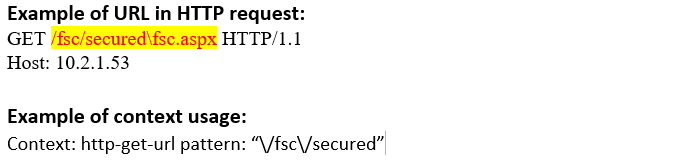 |
|||
http-get-url-parsed (CTS) |
Matches the decoded, normalized URL in an HTTP get request.  |
|||
http-head-url (CTS) |
Matches the URL in an HTTP head request as it appears in the stream.  |
|||
http-head-url-parsed (CTS) |
Matches the decoded, normalized URL in an HTTP head request.  |
|||
http-header (ANY) |
Matches any HTTP header. 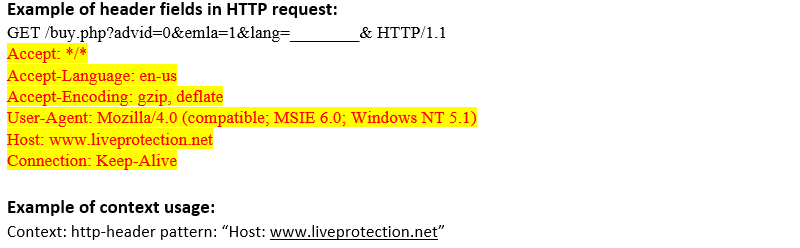 |
|||
http-header-accept (CTS) |
Matches each Accept: header in an HTTP request. 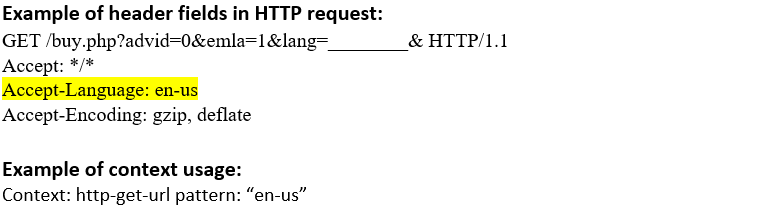 |
|||
http-header- accept-encoding (CTS) |
Matches each Accept-Encoding: header in an HTTP request. 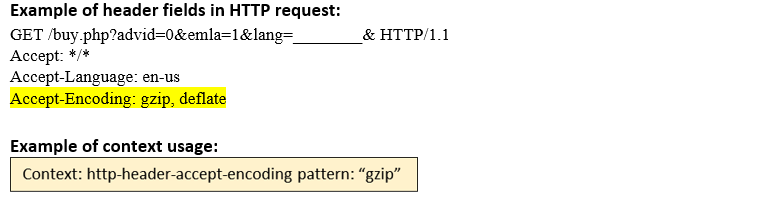 |
|||
http-header- accept-language (CTS) |
Matches each Accept-Language: header in an HTTP request. 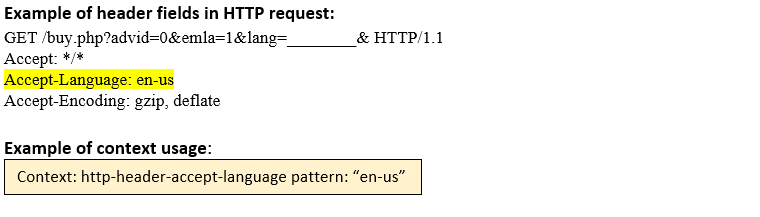 |
|||
http-header- content-encoding (ANY) |
Matches each Content-Encoding: header in an HTTP transaction. 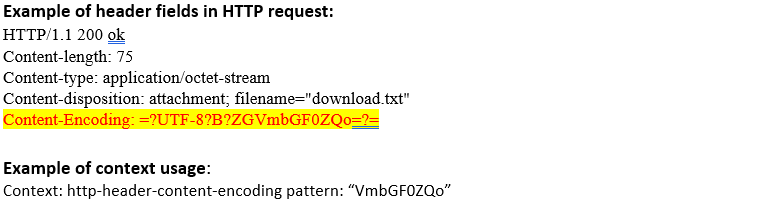 |
|||
http-header- content-language (ANY) |
Matches each Content-Language: header in an HTTP transaction. |
|||
http-header- content-location (ANY) |
Matches each Content-Location: header in an HTTP transaction. |
|||
http-header- content-md5 (ANY) |
Matches each Content-MD5: header in an HTTP transaction. |
|||
http-header- content-type (ANY) |
Matches each Content-Type: header in an HTTP transaction. 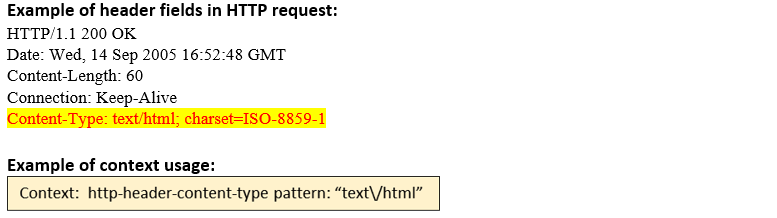 |
|||
http-header- cookie (ANY) |
Matches each Cookie: header in an HTTP transaction. 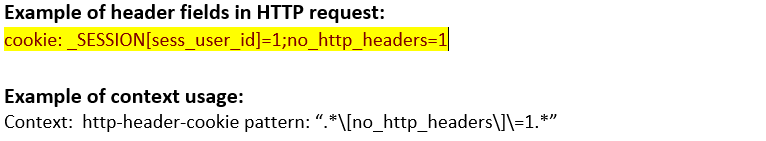 |
|||
http-header- host (CTS) |
Matches each Host: header in an HTTP request. |
|||
http-header- referer (CTS) |
Matches each Referrer: header in an HTTP request. |
|||
http-header- soapaction (ANY) |
Matches each soapaction: header in an HTTP transaction. |
|||
http-header- user-agent (CTS) |
Matches each User-Agent: header in an HTTP request. |
|||
http-header- x-forwarded-for |
 |
|||
http-image (ANY) |
Matches IMATE contents (BMP, PNG) in HTTP transaction.  |
|||
http-jpeg-raw (ANY) |
Matches JPEG content in HTTP transaction. 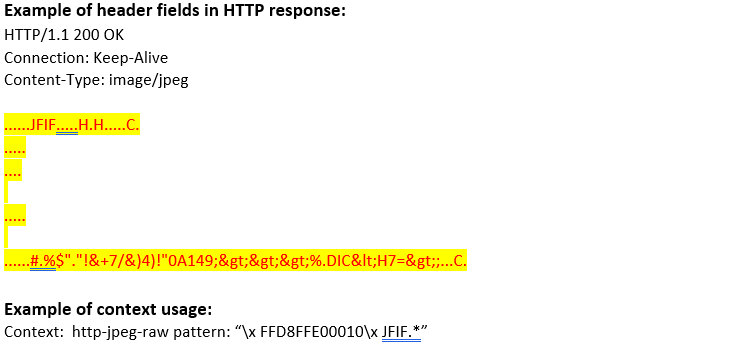 |
|||
http-jpeg-tag (ANY) |
Matches JPEG tag of JPEG content in HTTP transaction. JPEG image files provide an area for applications to store metadata such as title, date taken, shutter speed, and so on. There are several slots available, each of which holds a group of metadata tags. A JPEG file contains several segments; each segment contains different kinds of data, delimited by two-byte codes called markers. The markers are hexadecimal; they begin with 0xFF and end with a code (1 byte) indicating the kind of marker. 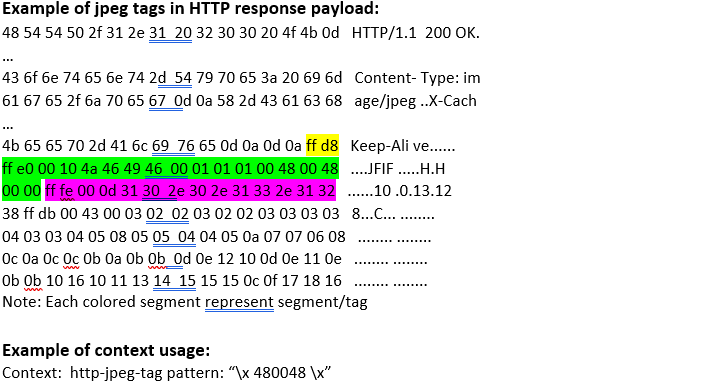 |
|||
http-object-tag-clsid (STC) |
Matches the CLSID of an object tag. 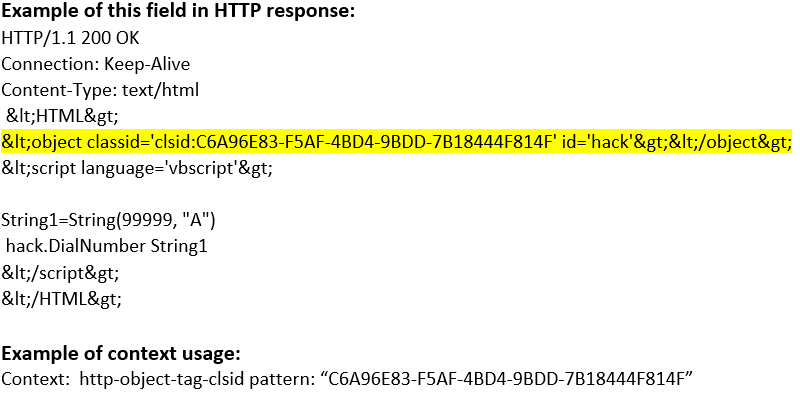 |
|||
http-ole |
Matches Microsofts OLE contents in HTTP transaction. 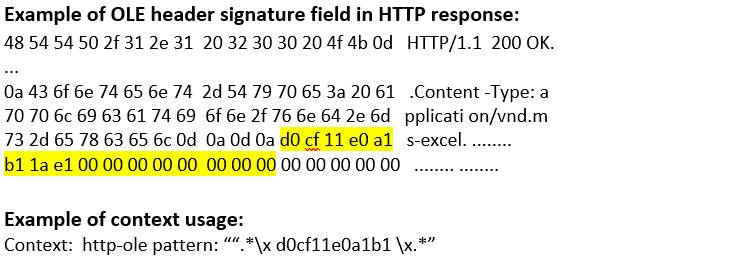 |
|||
http-param-parsed (CTS) |
Matches the decoded CGI parameters in an HTTP request. |
|||
http-pdf |
Matches PDF contents in HTTP transaction. 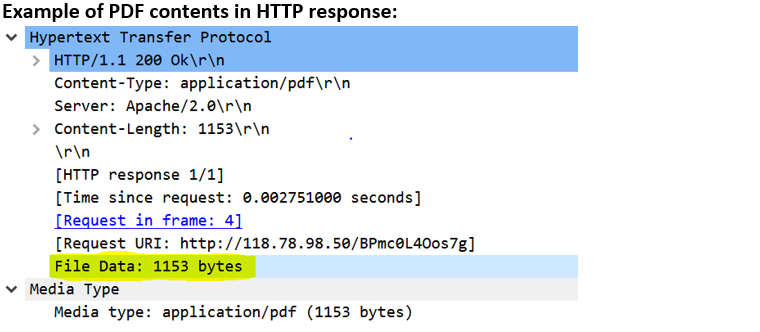 |
|||
http-png-chunk (ANY) |
Matches contents of PNG chunk to HTTP transaction. 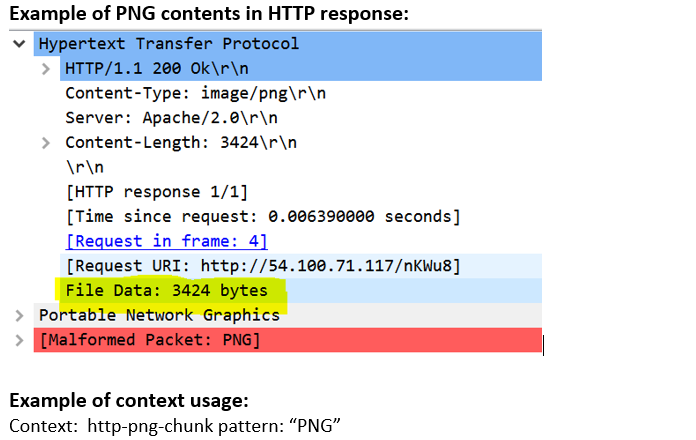 |
|||
http-post-url (CTS) |
Matches the URL in an HTTP post request as it appears in the stream. |
HTTP POST URL |
POST /index.html?crap=1085538798 HTTP/1.1 |
1.34. http-post-url pattern: ".*\?.*" |
http-post-url-parsed (CTS) |
Matches the decoded, normalized URL in an HTTP post request. |
|||
http-post-variable (CTS) |
Matches each CGI variable in the form data of an HTTP POST request. 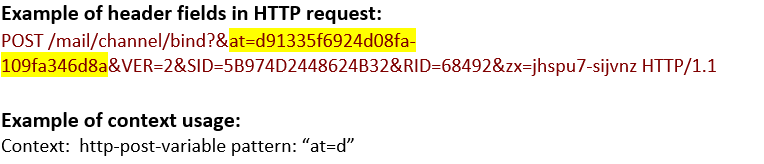 |
|||
http-post- variable-parsed (CTS) |
Matches each decoded CGI variable in the form data of an HTTP POST request. |
|||
http-request (CTS) |
Matches each HTTP request line. 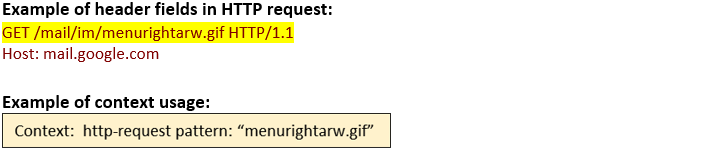 |
|||
http-request-method (CTS) |
Matches the method name in an HTTP request. 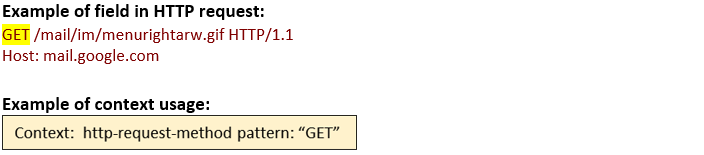 |
|||
http-status (STC) |
Matches the status line in an HTTP reply.  |
|||
http-text-html (ANY) |
Matches the text/html data in an HTTP transaction.  |
|||
http-text-html-body (ANY) |
Matches the body of text/html data in an HTTP tranaction |
|||
http-text-html-head (ANY) |
Matches the header of text/html data in an HTTP transaction.  |
|||
http-text-html-script (ANY) |
Matches the script tag of text/html data in an HTTP transaction.  |
|||
http-text-html-style (ANY) |
Matches the style tag of text/html data in an HTTP transaction. 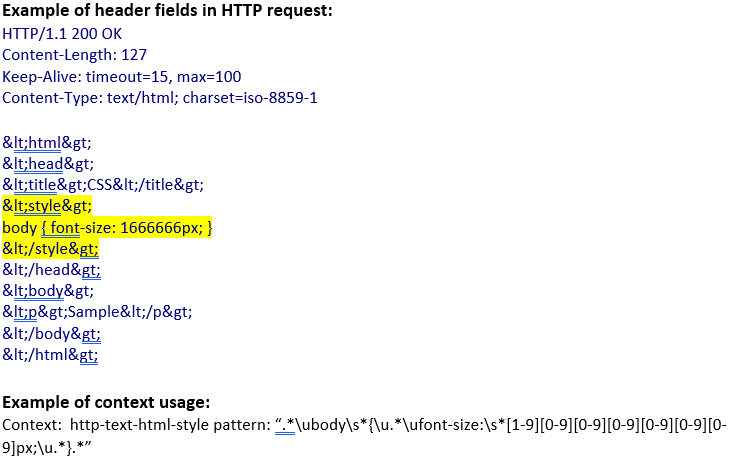 |
|||
http-text-html-tag (ANY) |
Matches any tag inside text/html data in an HTTP transaction. 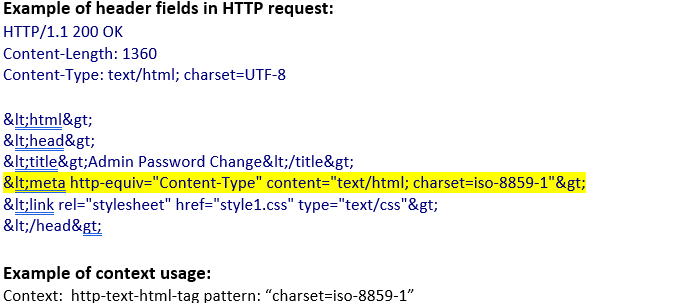 |
|||
http-text-plain (ANY) |
Matches the text/plain data in an HTTP transaction. 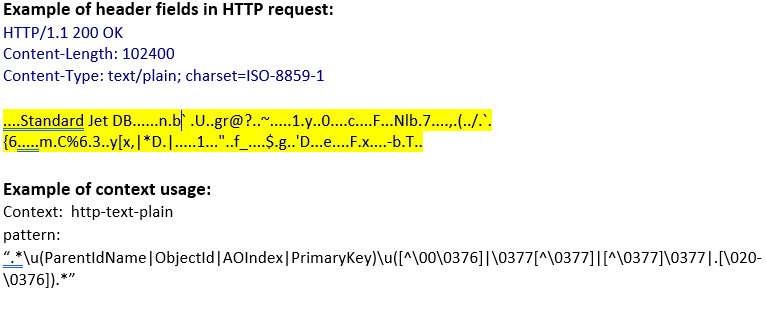 |
|||
http-text-soap (ANY) |
Matches the text/soap data in and HTTP transaction. 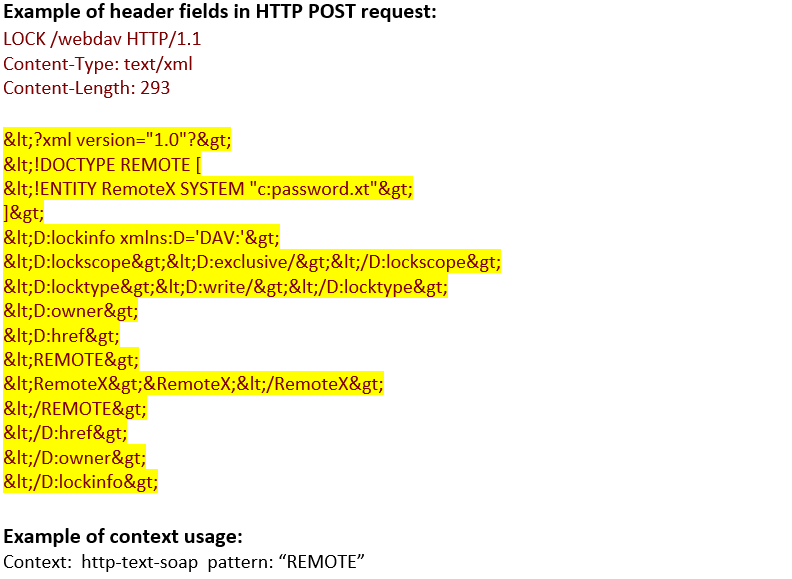 |
|||
http-text-xml (ANY) |
Matches the tex/xml data in an HTTP transaction. 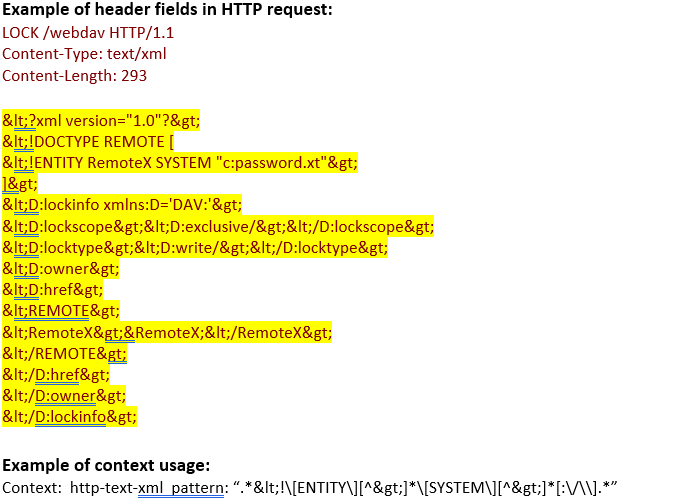 |
|||
http-url (CTS) |
Matches the URL in an HTTP request as it appears in the stream. 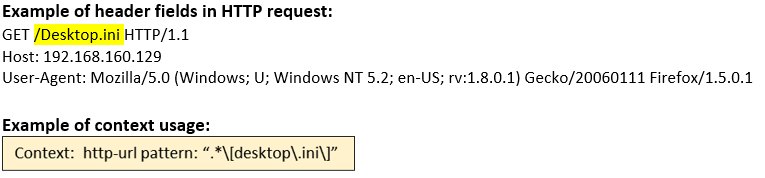 |
|||
http-url-parsed (CTS) |
Matches the decoded, normalized URL in an HTTP request. ![GET request with encoded VBScript code creating XMLHTTP object, connecting to 192.168.200.2. Context pattern for URL parsing: .*\.[rmp]\.](../concept/../../images/s009366.png) |
|||
http-url-parsed-param (CTS) |
Matches the decoded, normalized URL in an HTTP request along with the CGI parameters, if any 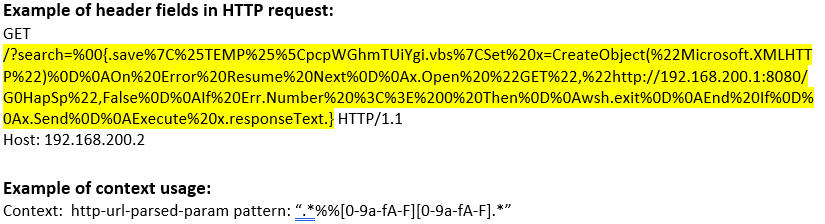 |
|||
http-url-parsed-param- parsed (CTS) |
Matches the decoded, normalized URL in an HTTP request along with the decoded CGI parameters, if any |
|||
http-url-variable (CTS) |
Matches each CGI variable in the URL of an HTTP GET request. 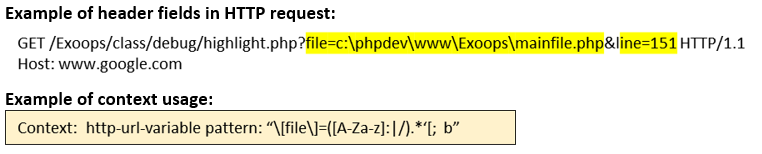 |
|||
http-url- variable-parsed (CTS) |
Matches each decoded CGI variable in the URL of an HTTP GET request. |
|||
http-variable (CTS) |
Matches each CGI variable in an HTTP GET or POST request. 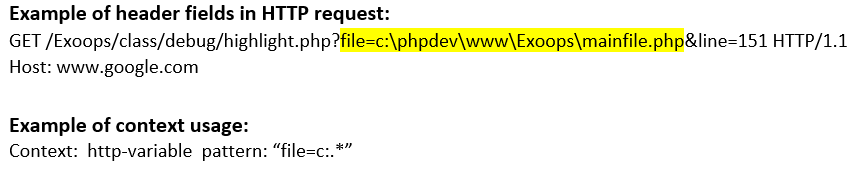 |
|||
http-variable-parsed (CTS) |
Matches each decoded CGI variable in an HTTP GET or POST request. |
|||
Service Contexts: SSL
The table displays the security context details for SSL:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
ssl-cert- common-name (ANY) |
Matches the common name attribute of the SSL certificate. 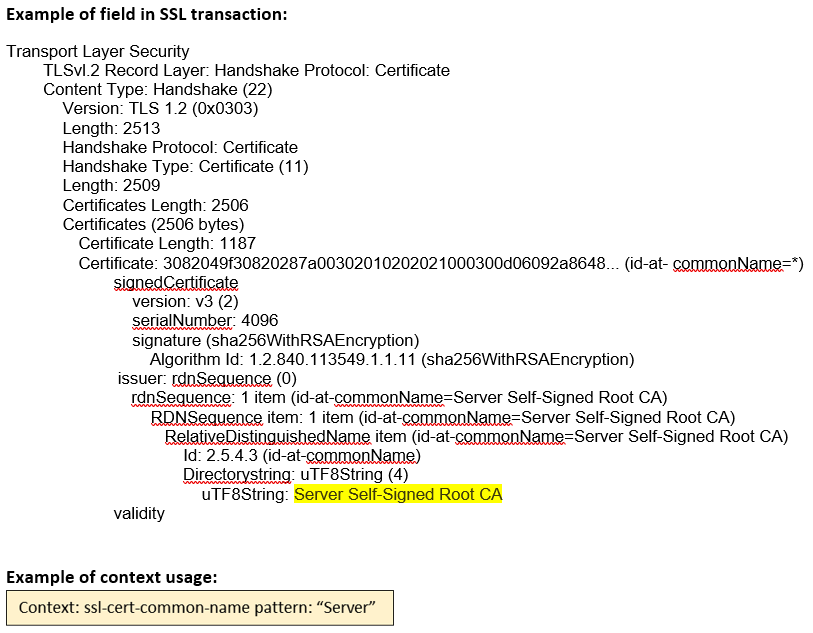 |
|||
ssl-cert- organization-name (ANY) |
Matches the organization name in the SSL certificate. 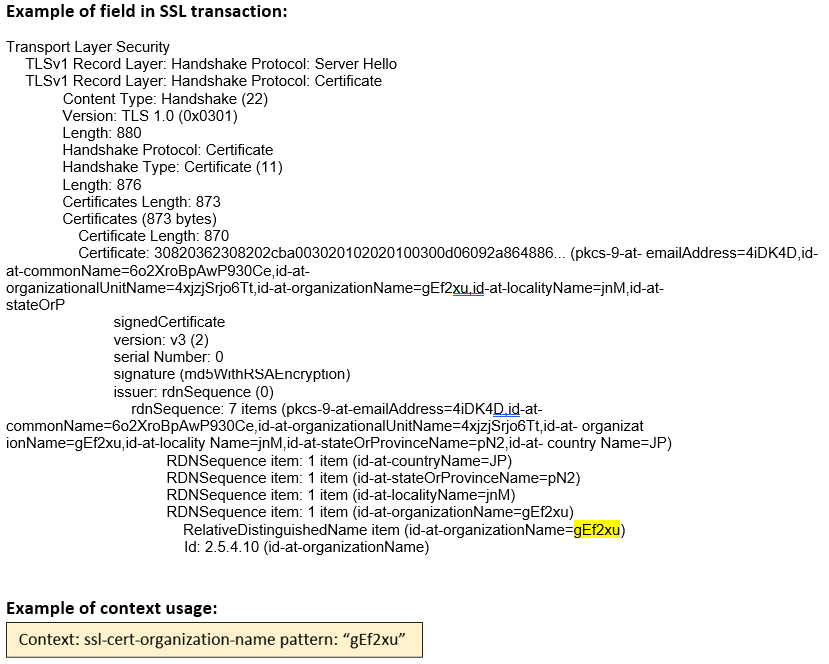 |
|||
ssl-cert- organizational-unit- name (ANY) |
Matches the organizational unit name in the SSL certificate. 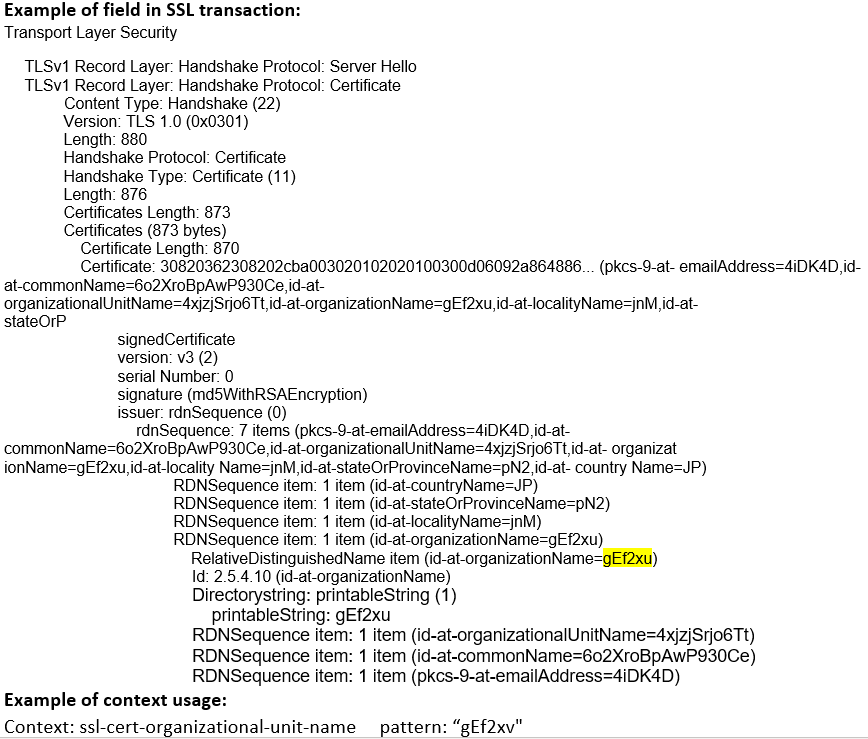 |
|||
ssl-certificate (ANY) |
Matches the entire SSL certificate content. 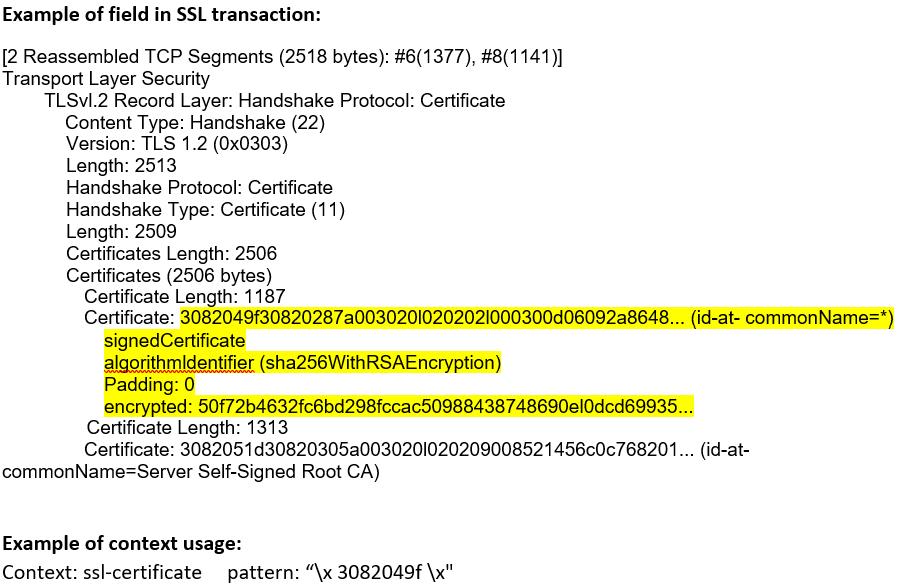 |
|||
ssl-change-cipher-spec (ANY) |
Matches the Change-Cipher-Spec Message Content |
|||
ssl-client-hello (CTS) |
Matches SSL client hello message content. 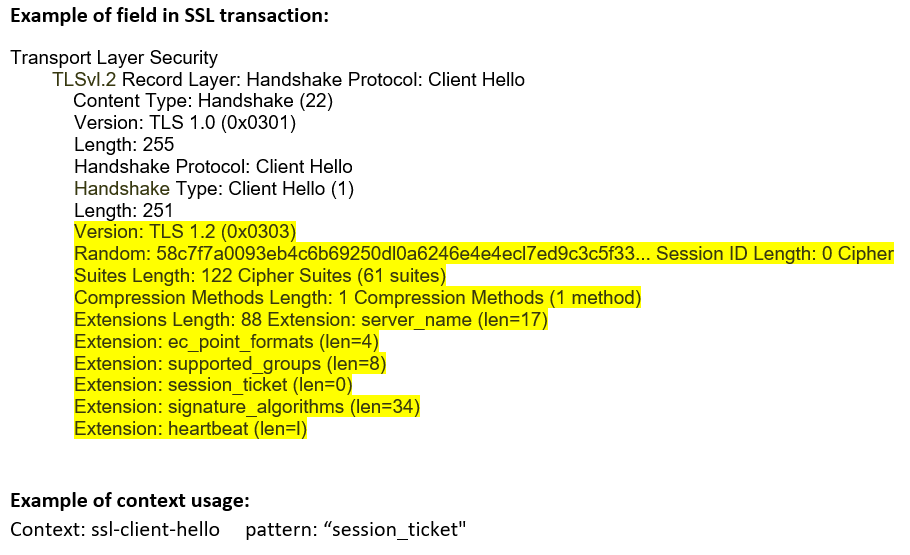 |
|||
ssl-client-key- exchange (CTS) |
Matches SSL client key exchange message content. 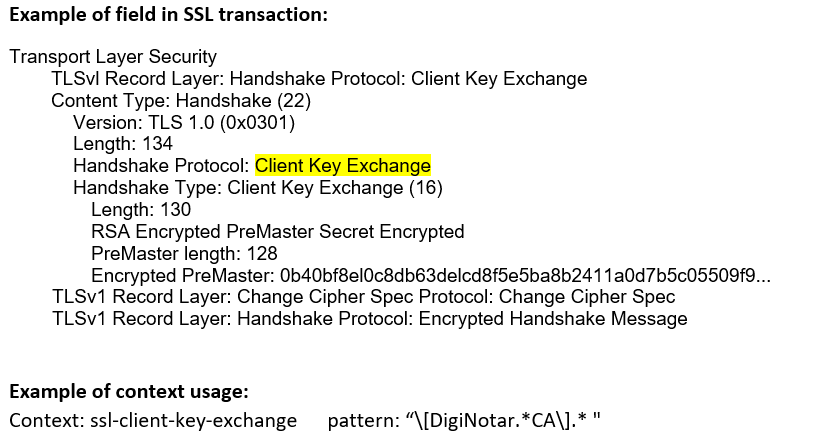 |
|||
ssl-client-version (CTS) |
Matches the client SSL version. 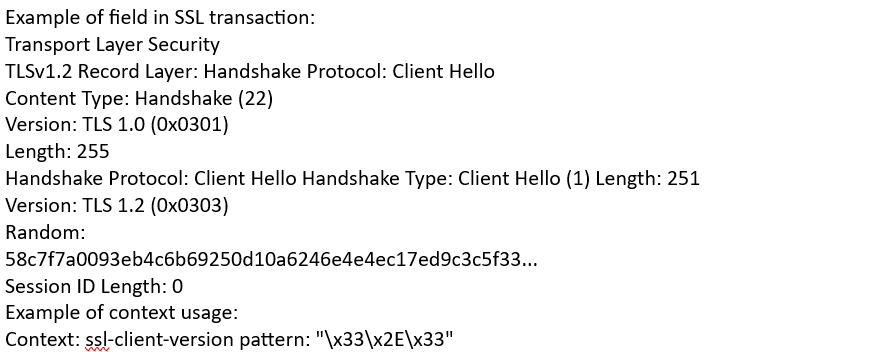 |
|||
ssl-selected- cipher-suite (STC) |
Matches the selected cipher suite in the server hello message. 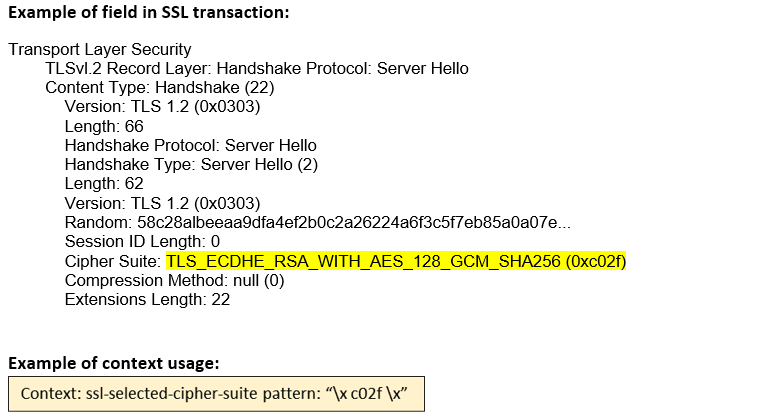 |
|||
ssl-server-hello (STC) |
Matches SSL server hello message content. 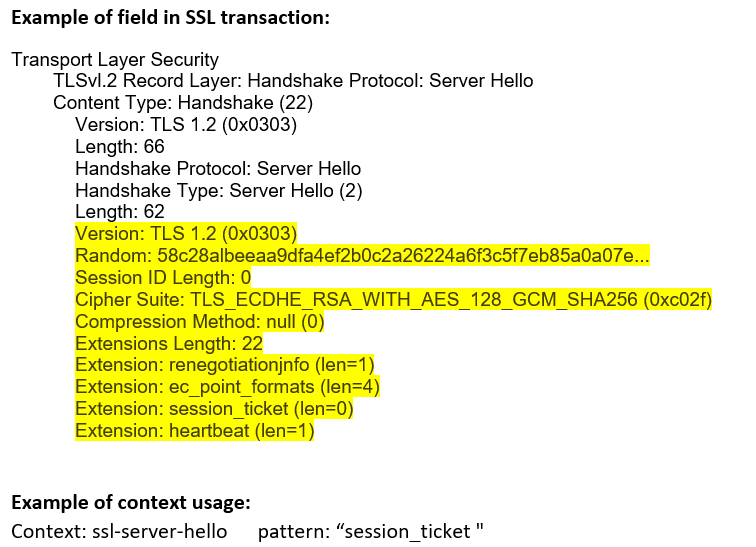 |
|||
ssl-server- key-exchange (STC) |
Matches SSL server key exchange message content. 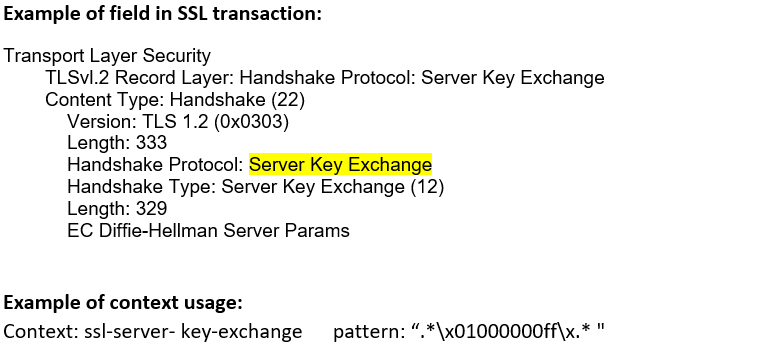 |
|||
ssl-server- version (STC) |
Matches the SSL server version. 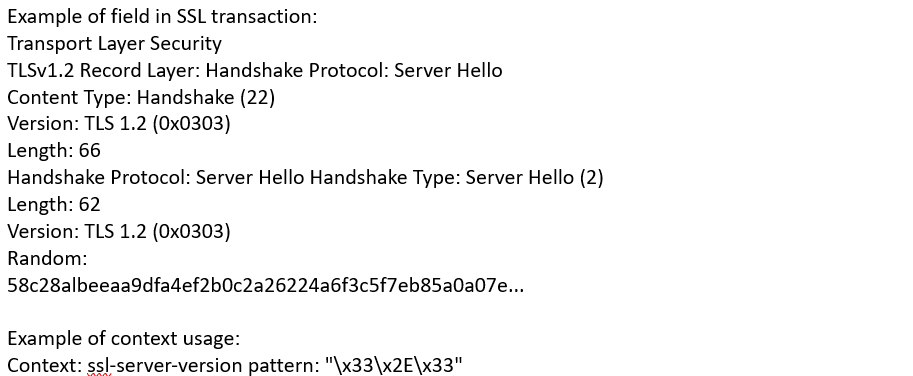
|
|||
