ON THIS PAGE
Database Contexts
These attack objects and groups are designed to detect known attack patterns and protocol anomalies within the network traffic. You can configure attack objects and groups for databases as match conditions in IDP policy rules.
Service Contexts: MS-SQL
The table displays the security context details for MS-SQL:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
mssql-0x12 (CTS) |
Matches the content of an MS-SQL type 0x12 request message. |
|||
mssql-cancel (CTS) |
Matches the content of an MS-SQL cancel message |
|||
mssql-login (CTS) |
Matches the content of an MS-SQL login message 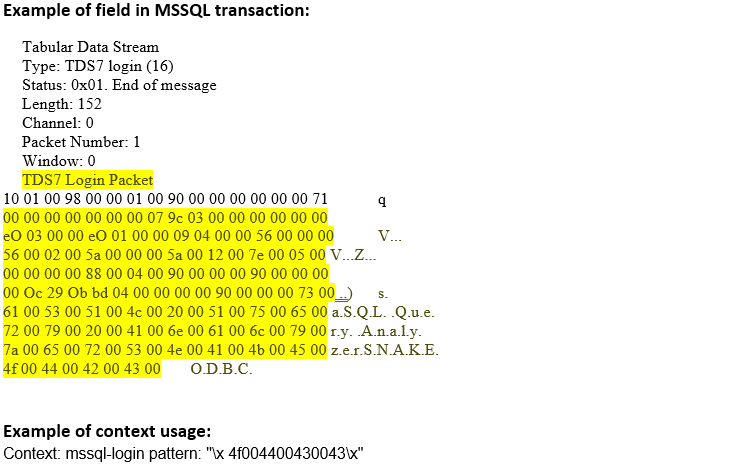 |
|||
mssql-login-app (CTS) |
Matches the name of the application in an MS-SQL Login message 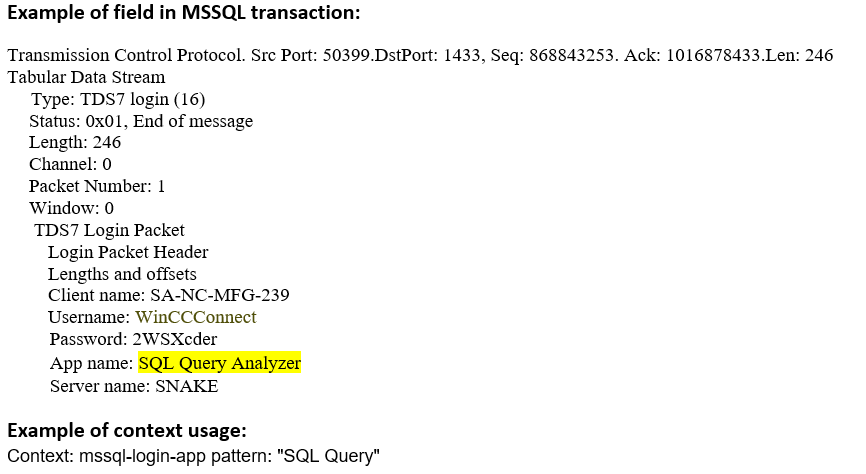 |
|||
mssql-login-client (CTS) |
Matches the name of the client in an MS-SQL Login message 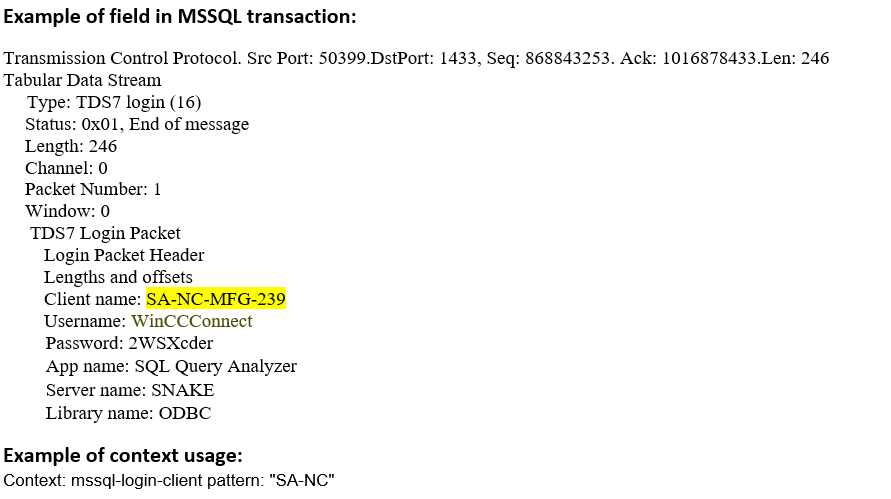 |
|||
mssql-login-database (CTS) |
Matches the name of the database in an MS-SQL Login message |
|||
mssql-login-language (CTS) |
Matches the name of the language in an MS-SQL Login message |
|||
mssql-login-lib (CTS) |
Matches the name of the library in an MS-SQL Login message 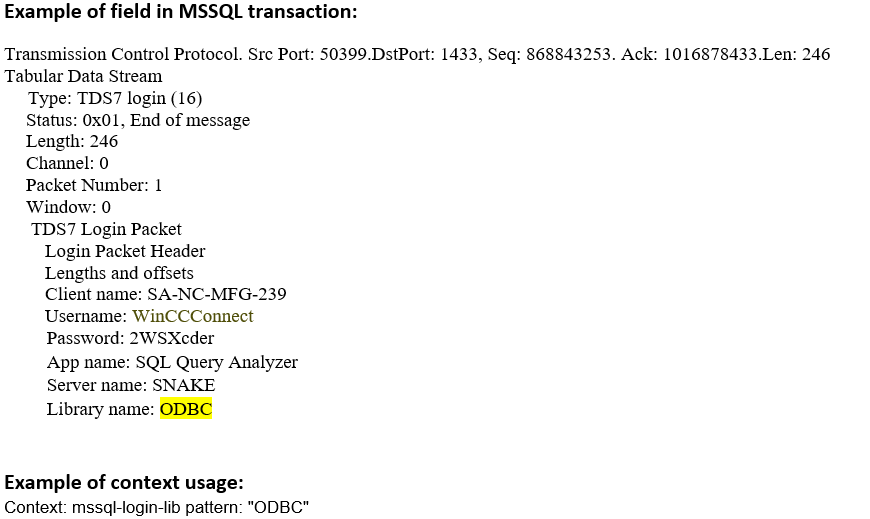 |
|||
mssql-login-pass (CTS) |
Matches the password in an MS-SQL Login message 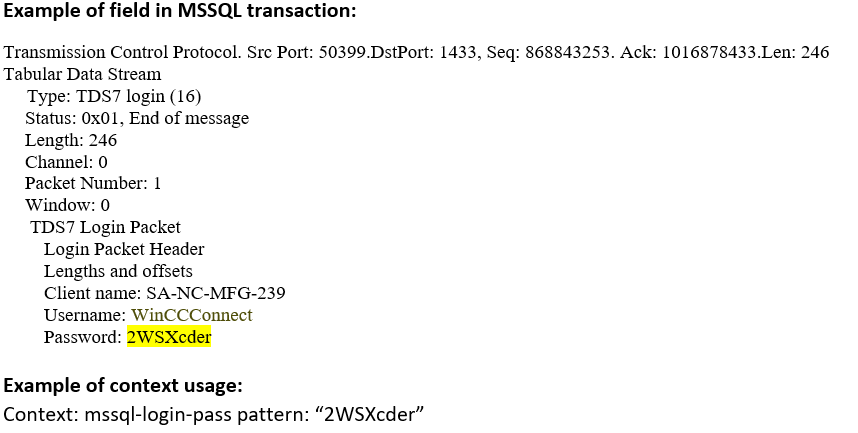 |
|||
mssql-login-server (CTS) |
Matches the name of the server in an MS-SQL Login message 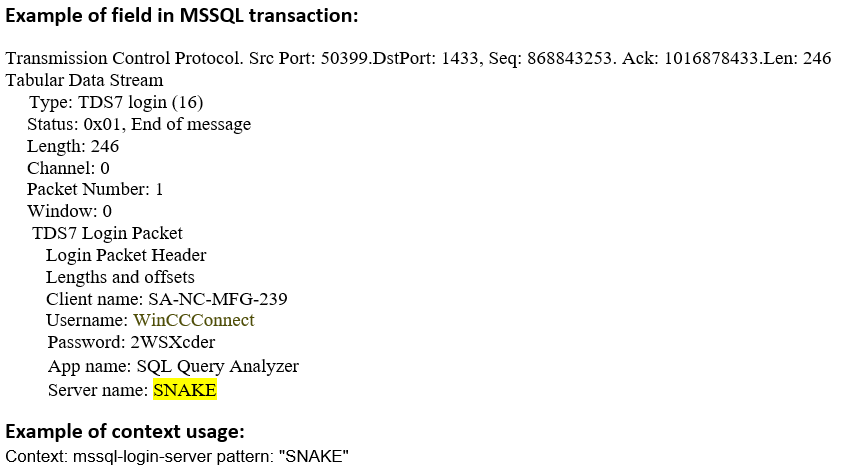 |
|||
mssql-login-user (CTS) |
Matches the name of the user in an MS-SQL Login message 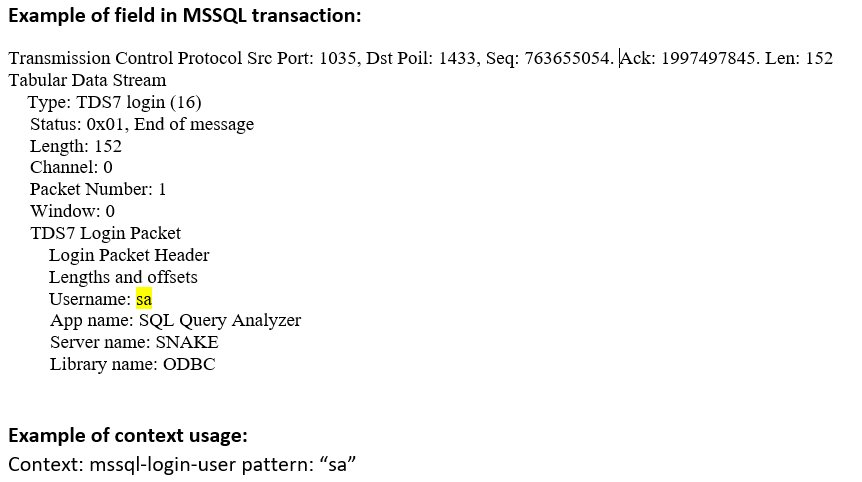 |
|||
mssql-query (CTS) |
Matches the content of an MS-SQL query message. 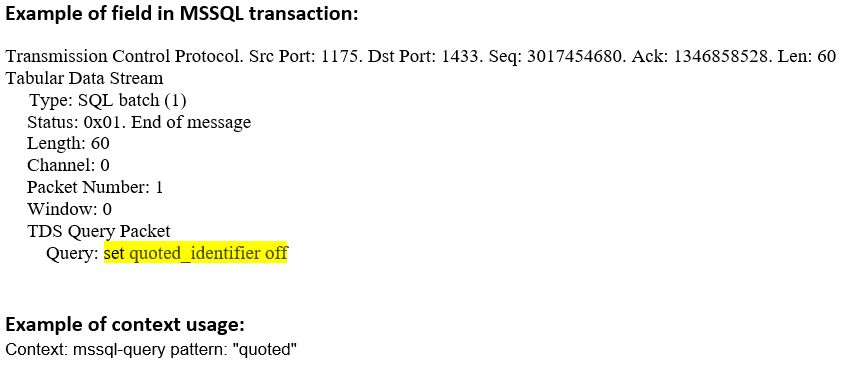 |
|||
mssql-request-other (CTS) |
Matches the content of an MS-SQL unknown Request message. |
|||
mssql-rpe (CTS) |
Matches the content of an MS-SQL RPC message |
|||
mssql-rpc-name (CTS) |
Matches the RPC name in an MS-SQL request message. |
|||
Service Contexts: MYSQL
The table displays the security context details for MYSQL:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
mysql-login- request-caps (CTS) |
Matches the MYSQL Login Request Caps Data. 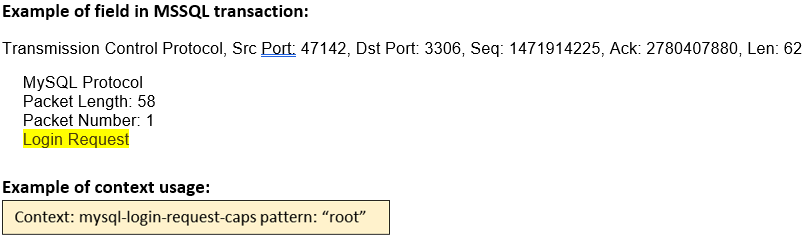 |
|||
mysql-login- request-caps-pswd (CTS) |
Matches the MYSQL Login Request Caps Password. 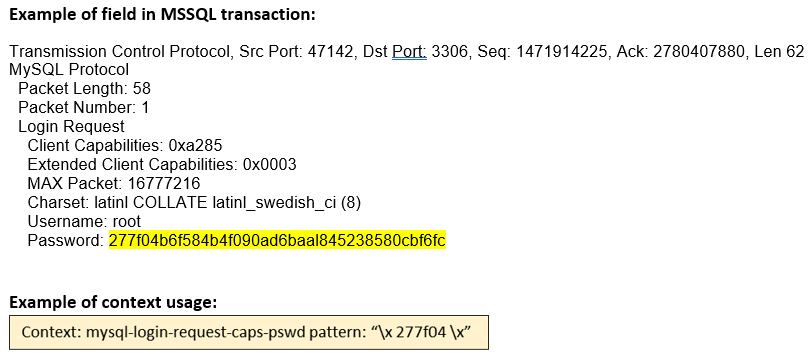 |
|||
mysql-login- request-caps-user (CTS) |
Matches the MYSQL Login Request Caps Username. 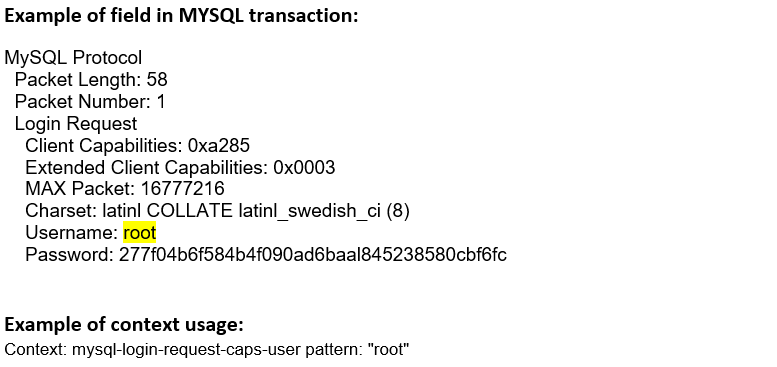 |
|||
mysql-preamble (ANY) |
Matches the 4 first bytes of the packet. |
|||
mysql-req-command (CTS) |
Matches the MYSQL Request Command. 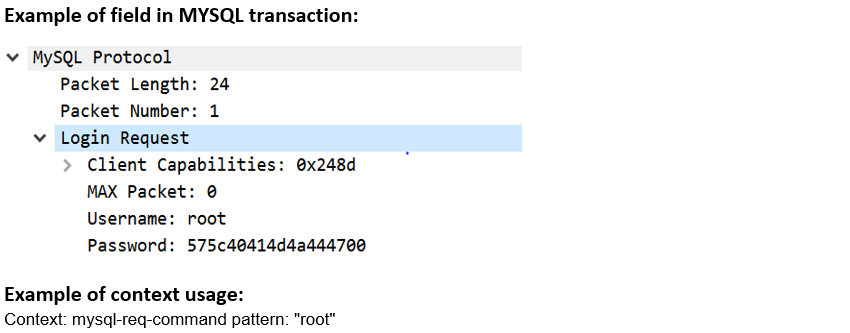 |
|||
mysql-response (STC) |
Matches the MYSQL Response.  |
|||
mysql-server-greeting (STC) |
Matches the MYSQL Server Greeting Data.  |
|||
