Remote Access Contexts
These attack objects and groups are designed to detect known attack patterns and protocol anomalies within the network traffic. You can configure attack objects and groups for remote access as match conditions in IDP policy rules.
Service Contexts: SSH
The table displays the security context details for SSH:
Display Name |
Description Example of Contexts |
|||
|---|---|---|---|---|
ssh-header (ANY) |
Matches the header at the start of an SSH session. 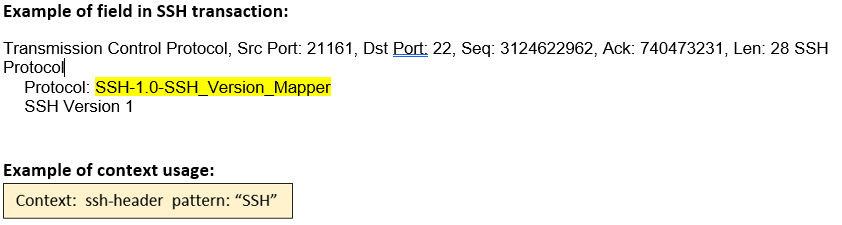 |
|||
Service Contexts: Telnet
The table displays the security context details for Telnet:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
telnet-option (ANY) |
Matches each of the telnet options in a Telnet session. 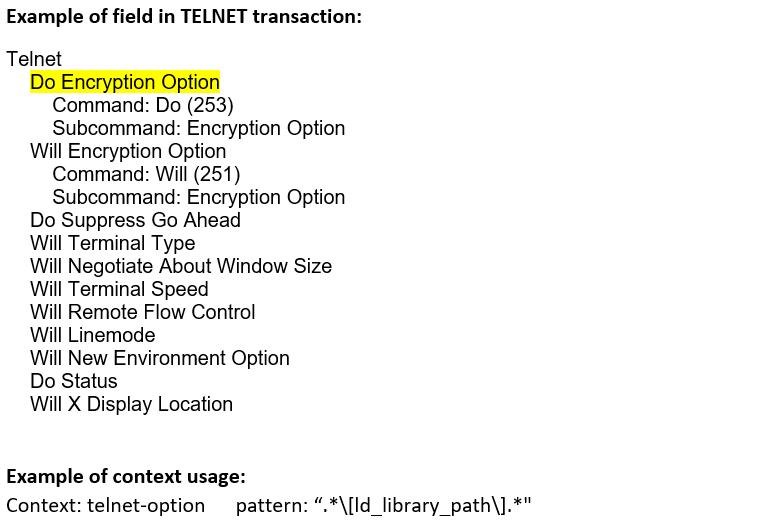 |
|||
telnet-subnegotiation (ANY) |
Matches each of the telnet subnegotiation options in a Telnet session. ![TELNET transaction showing suboptions Negotiate About Window Size highlighted in yellow and Suboption End with context telnet-subnegotiation and pattern .*\[ld_library_path\].*](../concept/../../images/s009561.png) |
|||
telnet-user (CTS) |
Matches the Telnet user name. |
|||
Service Contexts: VNC
The table displays the security context details for VNC:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
vnc-client-version (CTS) |
Matches the version number of the VNC protocol sent by the client. 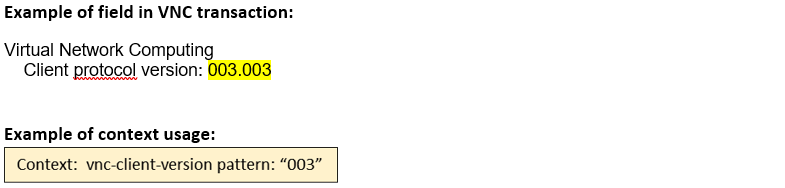 |
|||
vnc-reason (STC) |
Matches the connection fail reason reported by the VNC server.  |
|||
vnc-server-version (STC) |
Matches the version number of the VNC protocol sent by the server. 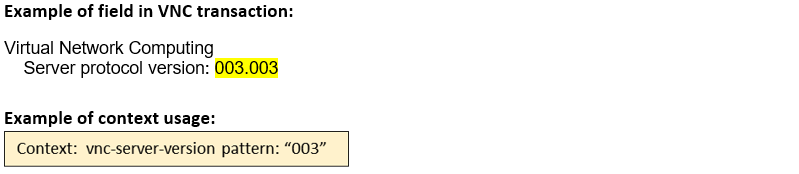 |
|||
