File Transfer Contexts
These attack objects and groups are designed to detect known attack patterns and protocol anomalies within the network traffic. You can configure attack objects and groups for FTP as match conditions in IDP policy rules.
Service Contexts: FTP
The table displays the security context details for FTP:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
ftp-account (CTS) |
Matches the FTP login account name. |
|||
ftp-banner (STC) |
Matches the banner returned by the server at the start of an FTP session. 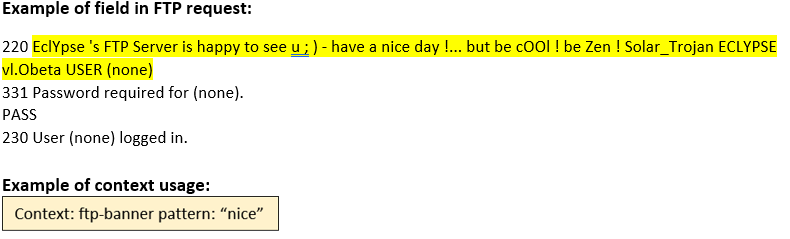 |
|||
ftp-command (CTS) |
Matches each of the FTP command names. 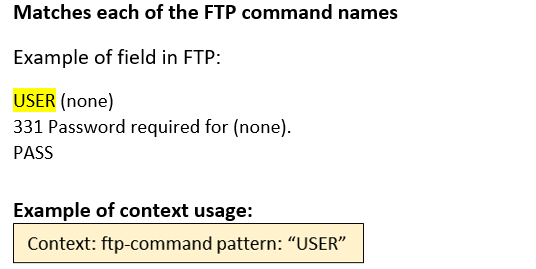 |
|||
ftp-cwd-pathname (CTS) |
Matches the directory name in the CWD command of an FTP session.  |
|||
ftp-dele-pathname (CTS) |
Matches the file name in the DELE command of an FTP session. 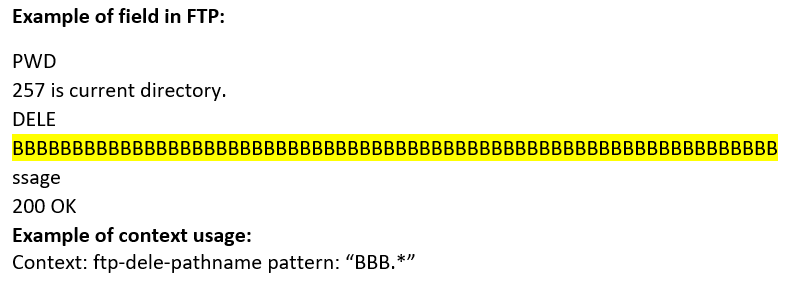 |
|||
ftp-get-filename (CTS) |
Matches the filename in the GET command of an FTP session.  |
|||
ftp-list-pathname (CTS) |
Matches the directory or file name in the LIST command of an FTP session.  |
|||
ftp-mkd-pathname (CTS) |
Matches the directory name in the MKD command of an FTP session.  |
|||
ftp-nlst-pathname (CTS) |
Matches the directory or file name in the NLST command of an FTP session. |
|||
ftp-password (CTS) |
Matches the FTP login password. 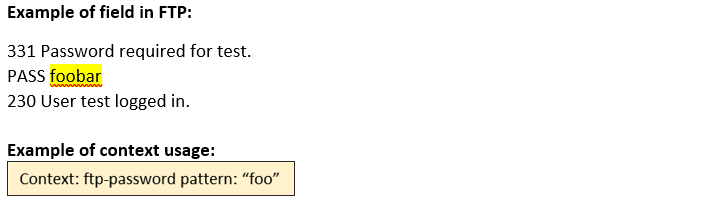 |
|||
ftp-pathname (CTS) |
Matches a directory or file name in any of the FTP commands.  |
|||
ftp-put-filename (CTS) |
Matches the filename in the PUT command of an FTP session. 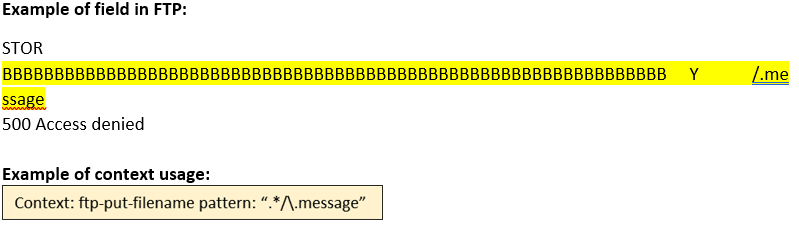 |
|||
ftp-reply-100-line (STC) |
Matches the FTP 1yz Positive Preliminary reply. 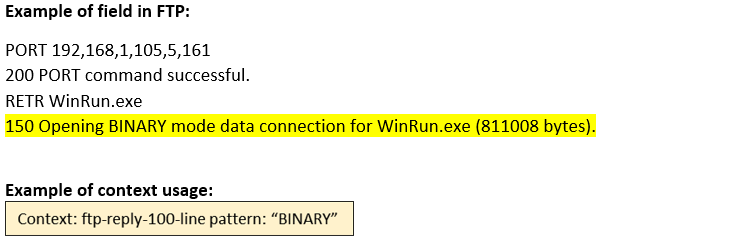 |
|||
ftp-reply-200-line (STC) |
Matches the FTP 2yz Positive Completion reply. 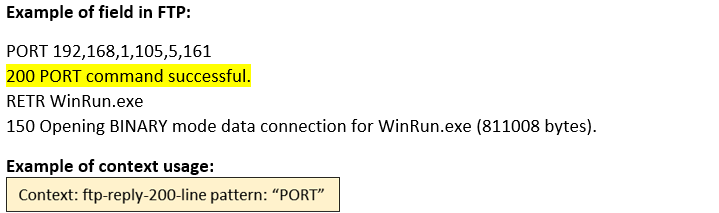 |
|||
ftp-reply-300-line (STC) |
Matches the FTP 3yz Positive Intermediate reply. 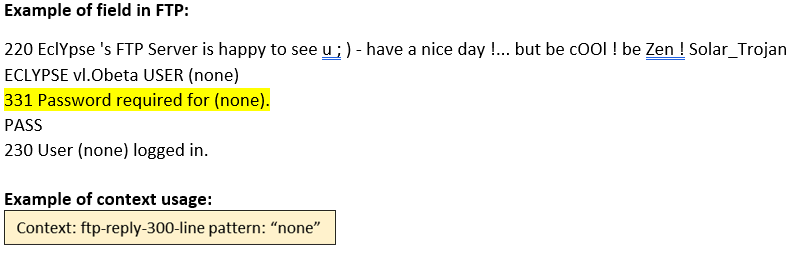 |
|||
ftp-reply-400-line (STC) |
Matches the FTP 4yz Transient Negative Completion reply. |
|||
ftp-reply-500-line (STC) |
Matches the FTP 5yz Permanent Negative Completion reply. 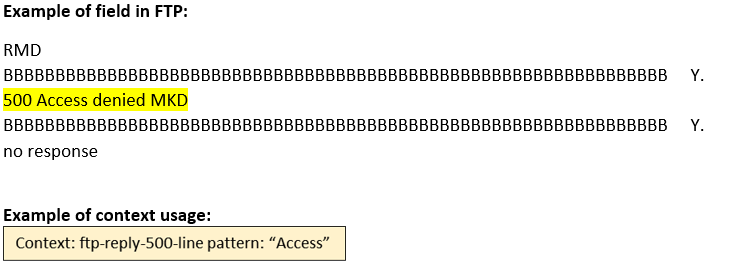 |
|||
ftp-reply-line (STC) |
Matches the FTP reply line.  |
|||
ftp-request (CTS) |
Matches FTP request line (command and arguments).  |
|||
ftp-rmd-pathname (CTS) |
Matches the directory name in the RMD command of an FTP session.  |
|||
ftp-rnfr-pathname (CTS) |
Matches a directory or file name in the RNFR command of an FTP session.  |
|||
ftp-rnto-pathname (CTS) |
Matches a directory or file name in the RNTO command of an FTP session. 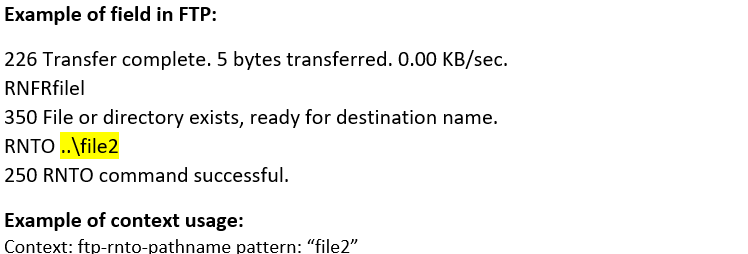 |
|||
ftp-sitestring (CTS) |
Matches the arguments of the SITE command in an FTP session. 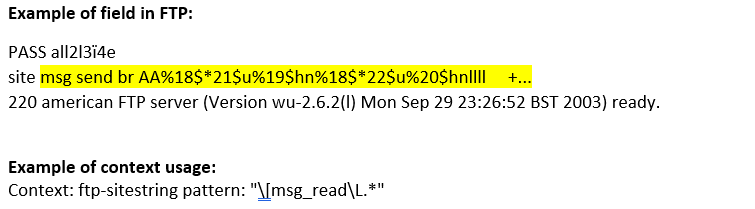 |
|||
ftp-smnt-pathname (CTS) |
Matches the directory or file name in the SMNT command of an FTP session. |
|||
ftp-stat-pathname (CTS) |
Matches the directory or file name in the STAT command of an FTP session. |
|||
ftp-username (CTS) |
Matches the FTP login user name.  |
|||
Service Contexts: NFS
The table displays the security context details for NFS:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
nfs-create-name (CTS) |
Matches the name of a file or directory in the CREATE procedure. 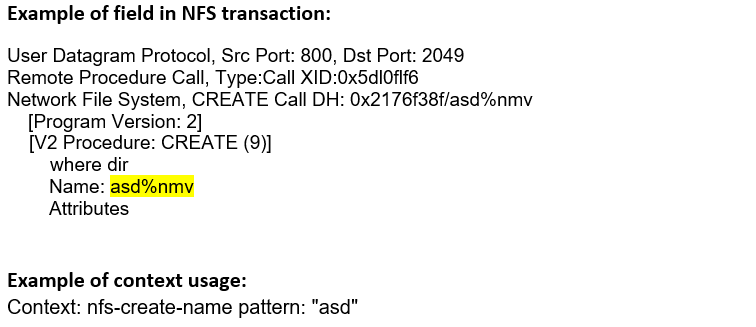 |
|||
nfs-dir-entry (STC) |
Matches the name of each directory entry returned by the READDIR procedure. |
|||
nfs-link-target (CTS) |
Matches the name of the hard link in the LINK procedure. |
|||
nfs-lookup-name (CTS) |
Matches the name of a file or directory in the LOOKUP procedure. 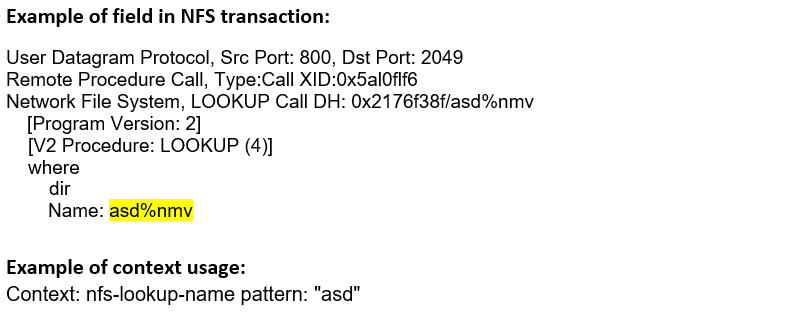 |
|||
nfs-mkdir-name (CTS) |
Matches the name of a directory in the MKDIR procedure. |
|||
nfs-mknod-name (CTS) |
Matches the name of the special file in the MKNOD procedure. |
|||
nfs-readlink-name (STC) |
Matches the name returned by the READLINK procedure |
|||
nfs-remove-name (CTS) |
Matches the name of a file in the REMOVE procedure. |
|||
nfs-rename-from (CTS) |
Matches the source file or directory name in the RENAME procedure. |
|||
nfs-rename-to (CTS) |
Matches the destination file or directory name in the RENAME procedure. |
|||
nfs-rmdir-name (CTS) |
Matches the name of a directory in the RMDIR procedure. |
|||
nfs-symlink-source (CTS) |
Matches the source of the symbolic link in the SYMLINK procedure. |
|||
nfs-symlink-target (CTS) |
Matches the target of the symbolic link in the SYMLINK procedure. |
|||
Service Contexts: SMB
The table displays the security context details for SMB:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
smb-account-name (ANY) |
Matches the SMB account name in the SESSION_SETUP_ANDX request of an SMB session. 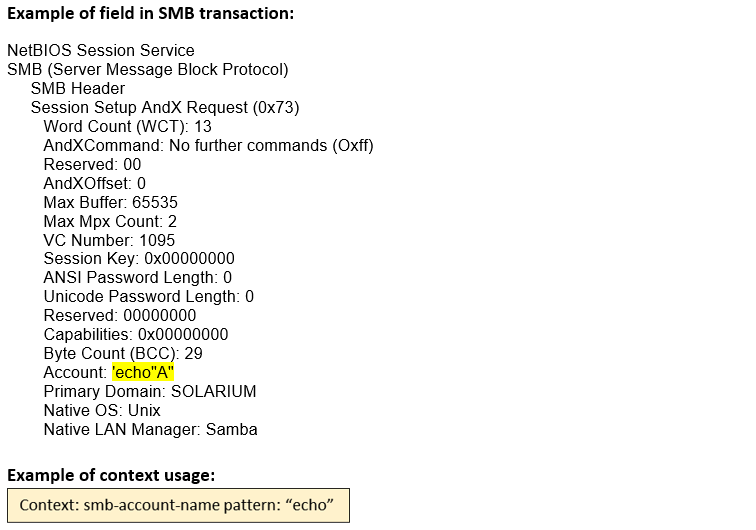 |
|||
smb-atsvc-request (CTS) |
Matches any AT Service requests sent as named pipe transactions over the SMB Transport Layer. The first 2 bytes of this context contains the opcode of the function. 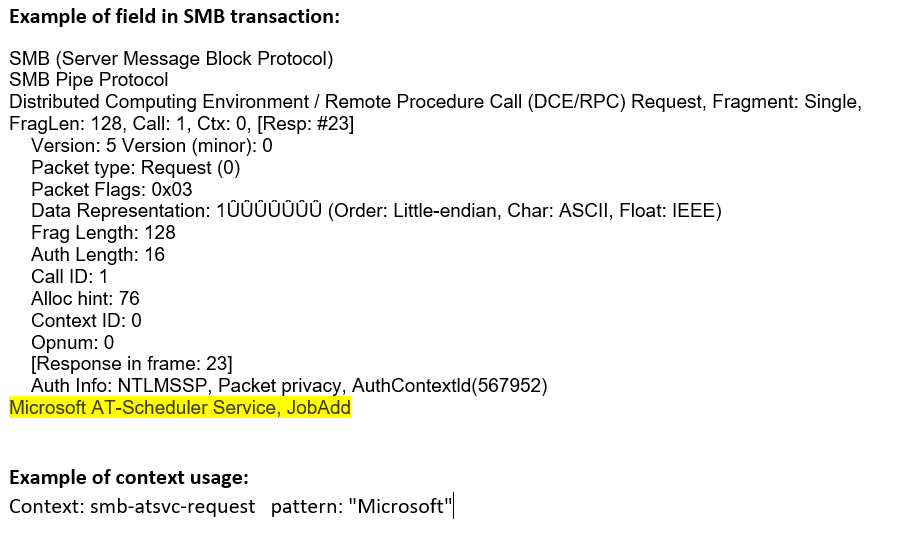 |
|||
smb-atsvc-response (STC) |
Matches any AT Service responses received as named pipe transactions over the SMB Transport Layer. The first 2 bytes of this context contains the opcode of the function. 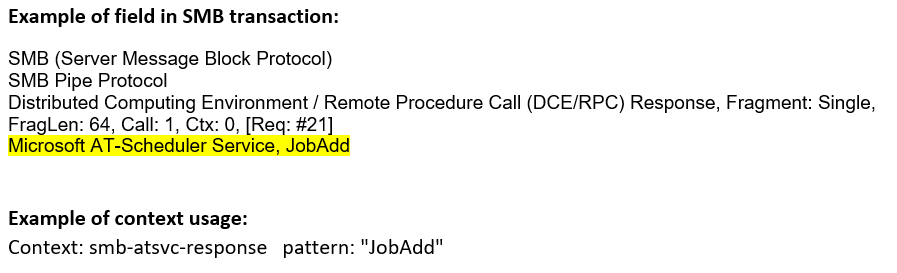 |
|||
smb-browser-request (CTS) |
Matches any Browser requests sent as named pipe transactions over the SMB Transport Layer. The first 2 bytes of this context contains the opcode of the function. |
|||
smb-browser-response (STC) |
Matches any Browser responses received as named pipe transactions over the SMB Transport Layer. The first two bytes of this context contains the opcode of the function. |
|||
smb-called-name (ANY) |
Matches the NetBIOS name of the initiator of an SMB session. |
|||
smb-calling-name (ANY) |
Matches the NetBIOS name of the receiver of an SMB session. 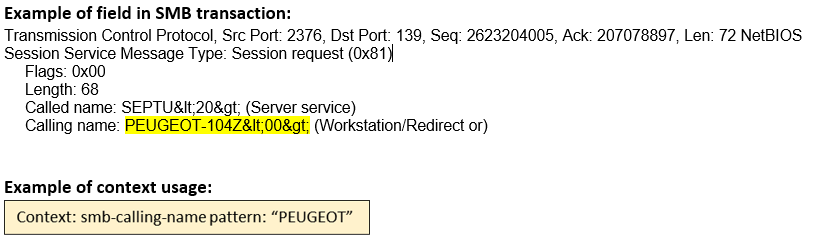 |
|||
smb-connect-path (CTS) |
Matches the connect path in the TREE_CONNECT_ANDX request of an SMB session. 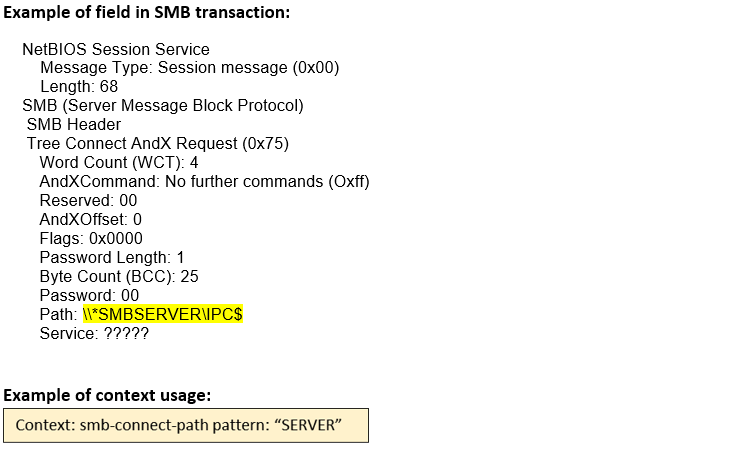 |
|||
smb-connect-service (CTS) |
Matches the connect service in the TREE_CONNECT_ANDX request of an SMB session. 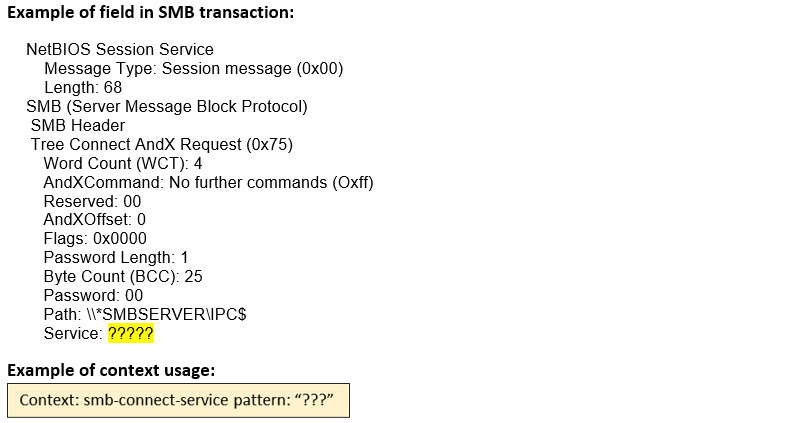 |
|||
smb-copy-filename (CTS) |
Matches the filename in the COPY request of an SMB session. |
|||
smb-data (ANY) |
Matches any SMB data portion. 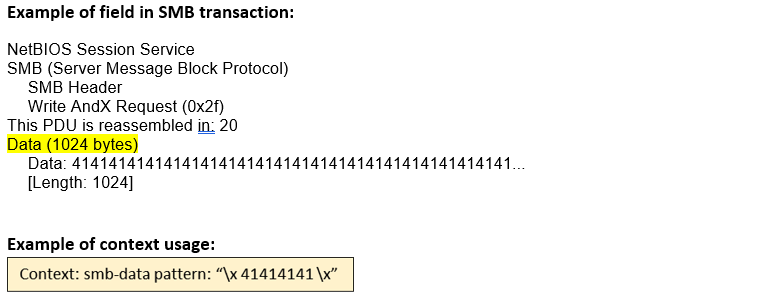 |
|||
smb-dce-rpc (ANY) |
Matches any DCE/RPC message sent over the SMB Transport Layer.  |
|||
smb-dce-rpc-bind (CTS) |
Matches any DCE/RPC bind message sent over the SMB Transport Layer. 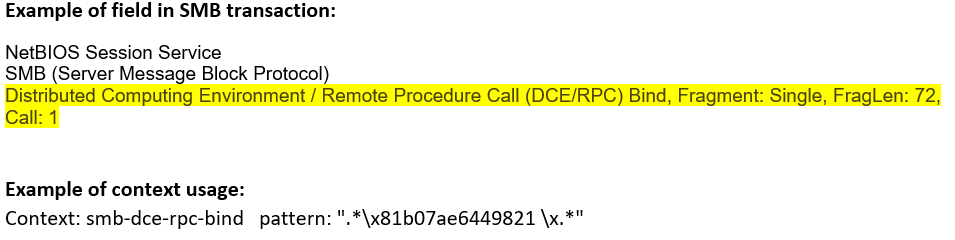 |
|||
smb-dce-rpc-bind-ack (STC) |
Matches any DCE/RPC bind-ack message sent over the SMB Transport Layer. 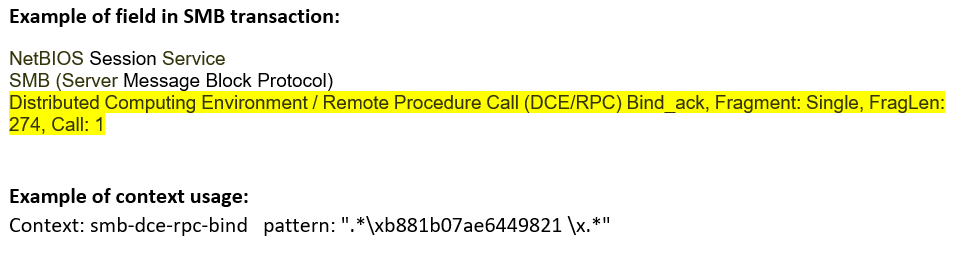 |
|||
smb-dce-rpc-bind-nack (STC) |
Matches any DCE/RPC bind-nack message sent over the SMB Transport Layer. |
|||
smb-dce-rpc-request (CTS) |
Matches any DCE/RPC request message sent over the SMB Transport Layer. 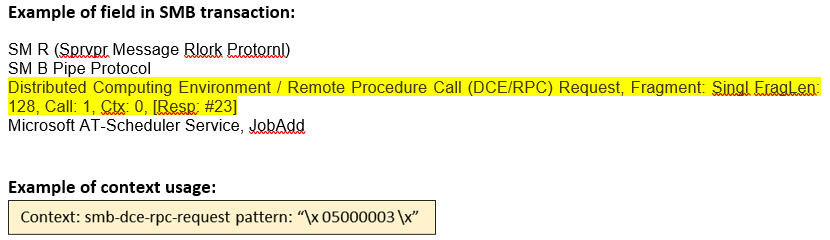 |
|||
smb-dce-rpc- request-obj-uuid (CTS) |
Matches object UUID of any DCE/RPC request message. 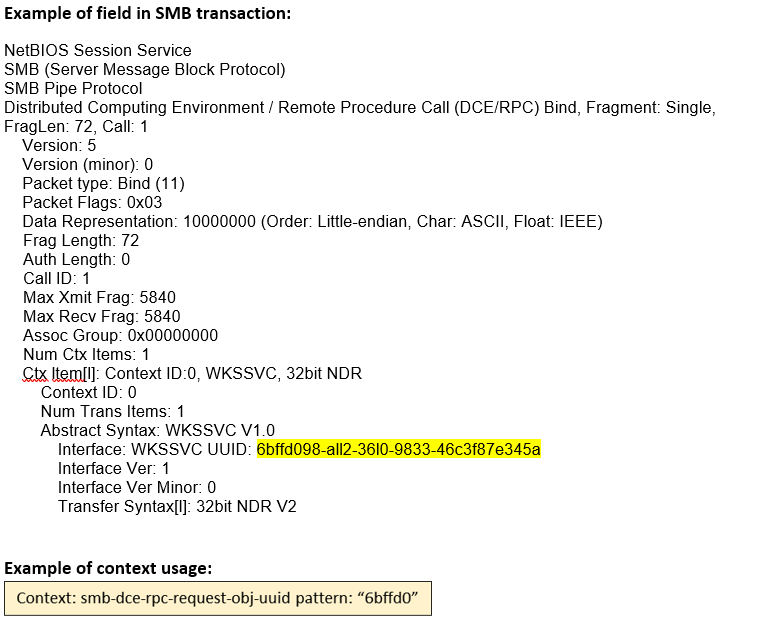 |
|||
smb-dce-rpc- response (STC) |
Matches any DCE/RPC response message sent over the SMB Transport Layer. 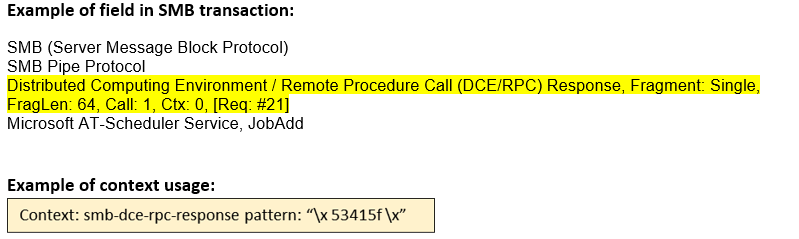 |
|||
smb-delete- filename (CTS) |
Matches the filename in the DELETE request of an SMB session. |
|||
smb-dialect (CTS) |
Matches each SMB dialect string in the NEGOTIATE request of an SMB session. |
|||
smb-header |
Matches any SMB header portion 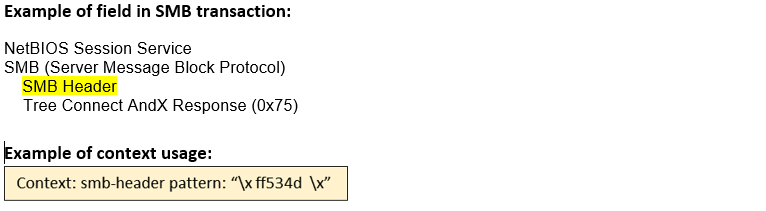 |
|||
smb-lanman- request (CTS) |
Matches any LANMAN requests sent as named pipe transactions over the SMB Transport Layer. The first 2 bytes of this context contains the opcode of the function. 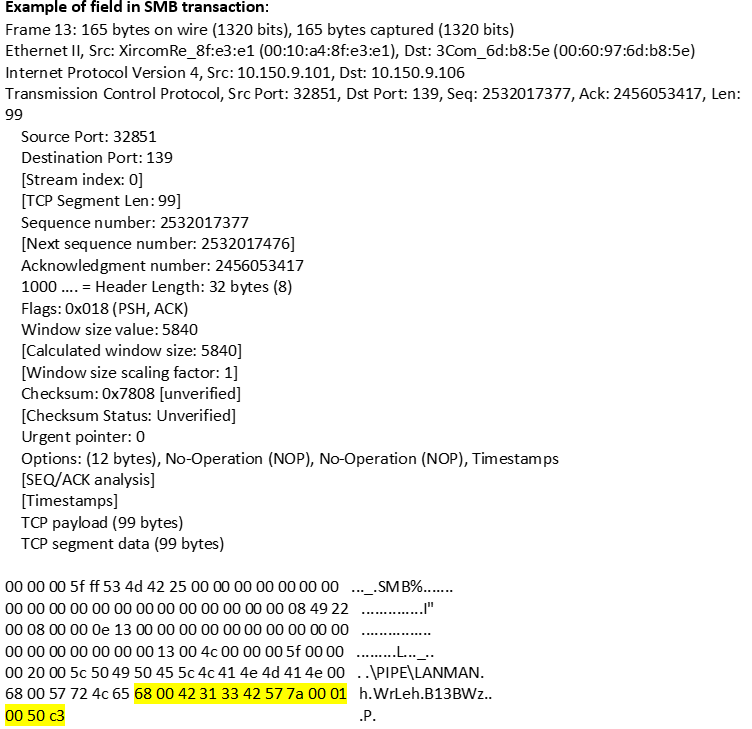 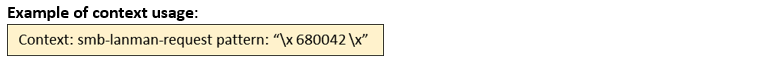 |
|||
smb-lanman- response (STC) |
Matches any LANMAN responses received as named pipe transactions over the SMB Transport Layer. The first 2 bytes of this context contains the opcode of the function. 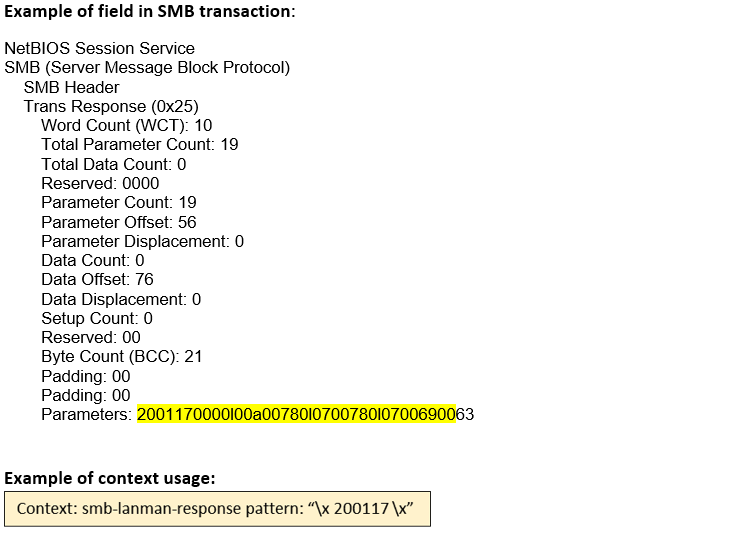 |
|||
smb-lsarpc- request (CTS) |
Matches any Local Security Authority requests sent as named pipe transactions over the SMB Transport Layer. The first 2 bytes of this context contains the opcode of the function. |
|||
smb-move- filename (CTS) |
Matches the filename in the MOVE request of an SMB session. |
|||
smb-native- lanman (ANY) |
Matches the native LANMAN in the SESSION_SETUP_ANDX request of an SMB session. 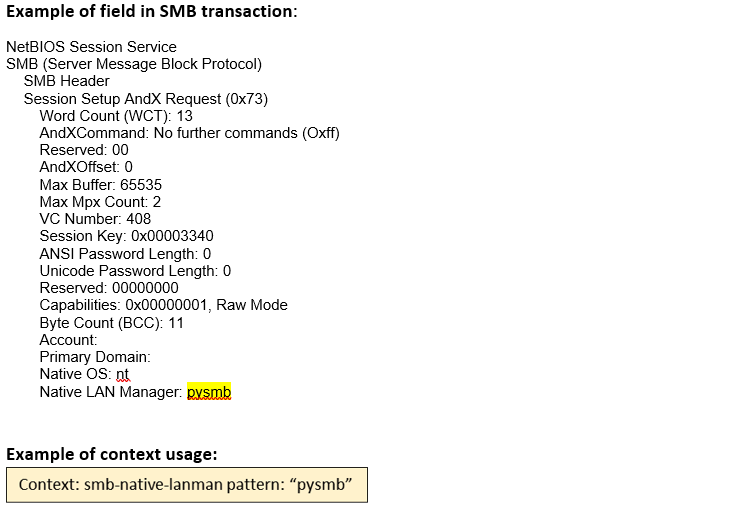 |
|||
smb-native-os (ANY) |
Matches the native OS in the SESSION_SETUP_ANDX request of an SMB session. 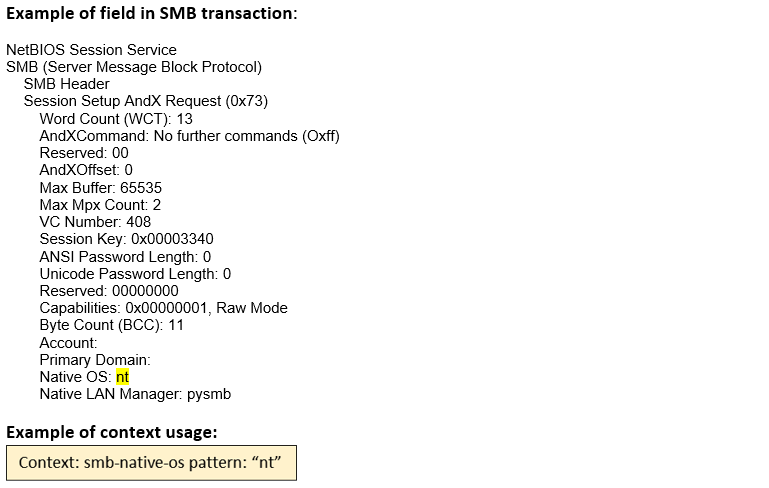 |
|||
smb-open-filename (CTS) |
Matches the filename in the NT_CREATE_ANDX and OPEN_ANDX requests of an SMB session. 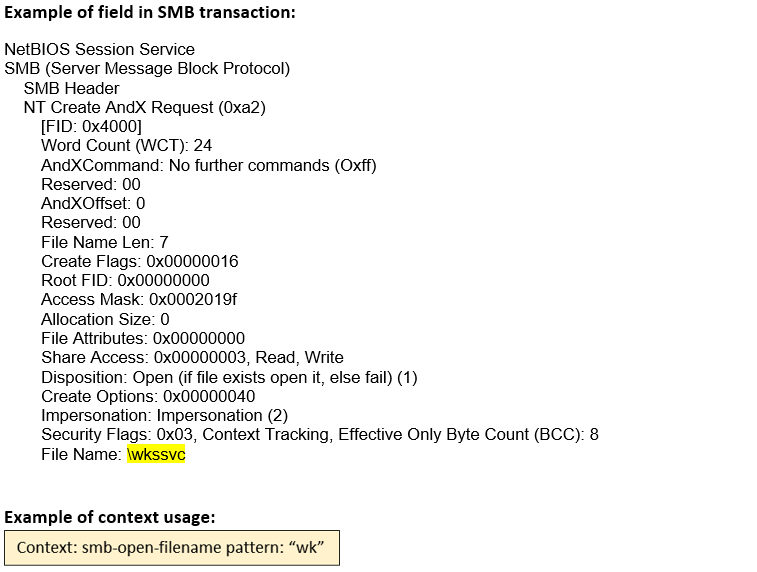 |
|||
smb-primary-domain (ANY) |
Matches the SMB primary domain name in the SESSION_SETUP_ANDX request of an SMB session. |
|||
smb-rename-filename (CTS) |
Matches the filename in the RENAME request of an SMB session. 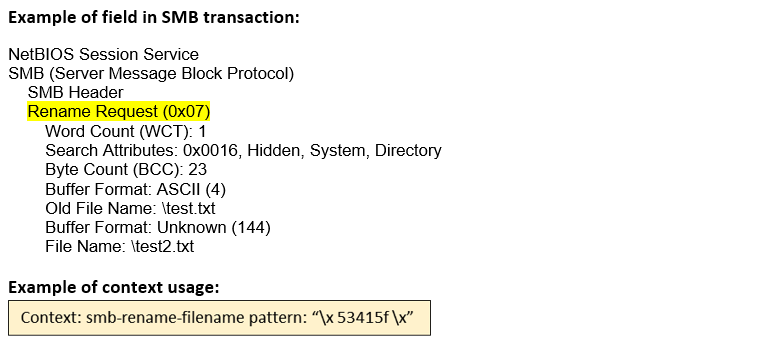 |
|||
smb-samr-request (CTS) |
Matches any Security Account Manager requests sent as named pipe transactions over the SMB Transport Layer. The first 2 bytes of this context contains the opcode of the function. 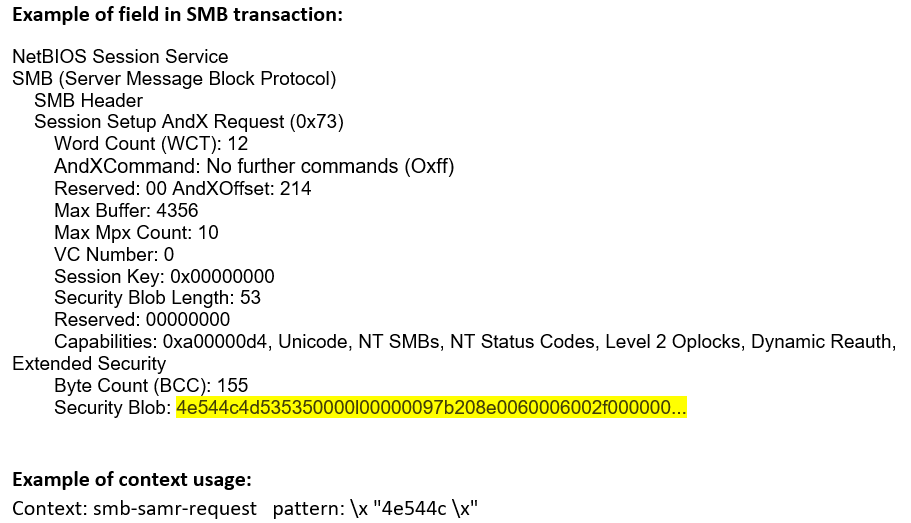 |
|||
smb-samr-response (STC) |
Matches any Security Account Manager responses received as named pipe transactions over the SMB Transport Layer. The first 2 bytes of this context contains the opcode of the function. |
|||
smb-session-header |
Matches any SMB session header portion 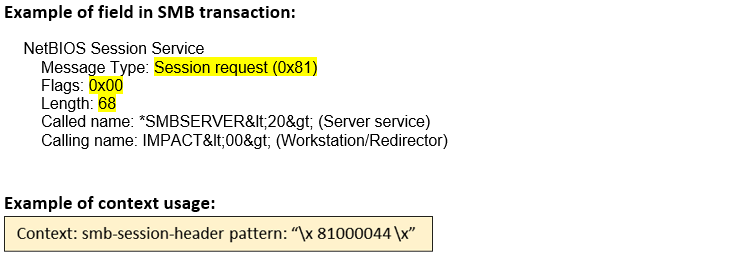 |
|||
smb-srvsvc-request (CTS) |
Matches any Server Service requests sent as named pipe transactions over the SMB Transport Layer. The first two bytes of this context contains the opcode of the function. 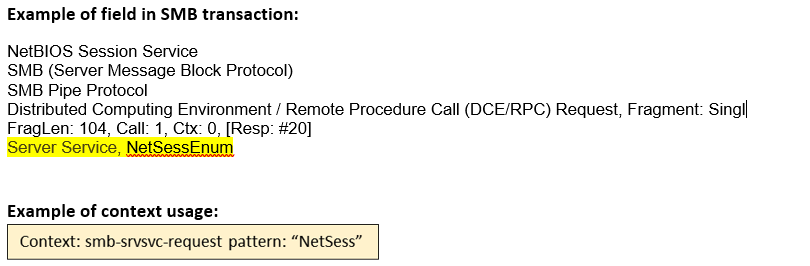 |
|||
smb-svcctl-request (CTS) |
Matches any Service Control Manager requests sent as named pipe transactions over the SMB Transport Layer. The first two bytes of this context contains the opcode of the function. 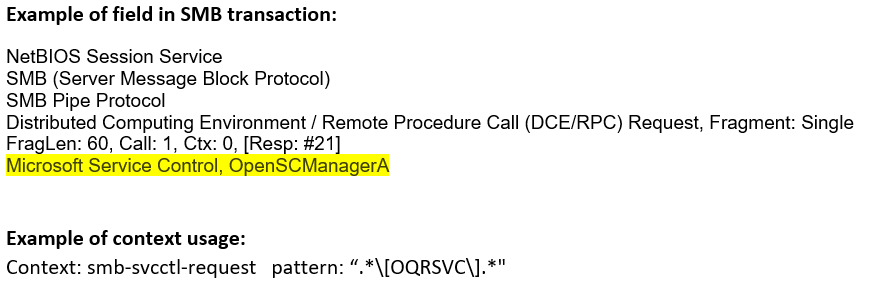 |
|||
smb-trans2-request (CTS) |
Matches any SMB Transaction2 request.  |
|||
smb-trans2-response (STC) |
Matches any SMB Transaction2 response. 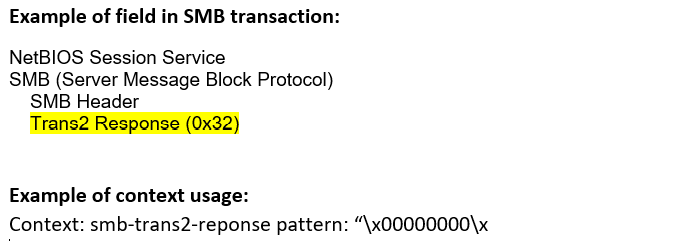 |
|||
smb-trans2-set-path-info (CTS) |
Matches any SMB Transaction2 SET-PATH-INFORMATION request. 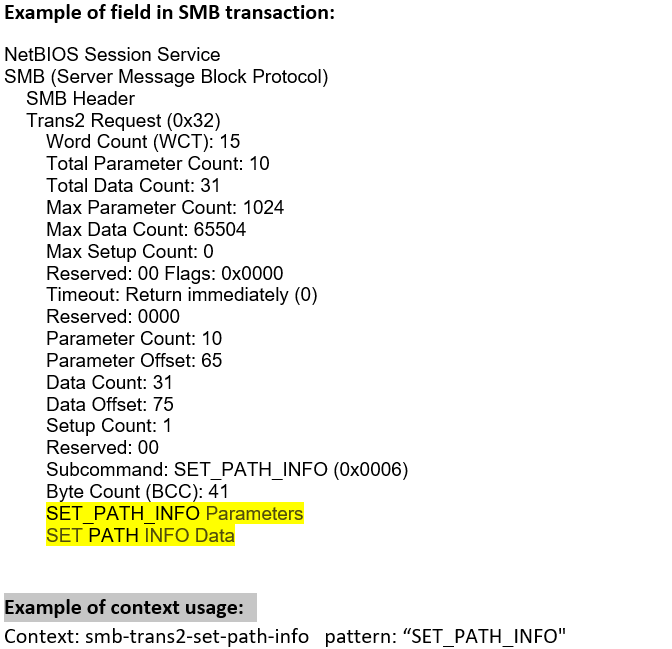 |
|||
Service Contexts: TFTP
The table displays the security context details for TFTP:
Context and Direction |
Description Example of Contexts |
|||
|---|---|---|---|---|
tftp-filename (CTS) |
Matches any filename in a TFTP session. ![TFTP transaction field example with Opcode Read Request 1, highlighted source file string ;]ApWm.T.T\T, truncated data type, context tftp-filename, pattern T\.IT.](../concept/../../images/s009562.png) |
|||
tftp-get-filename (CTS) |
Matches the get filename in a TFTP session. ![TFTP transaction highlighting Opcode as Read Request 1 and Source File as ;]ApWm&T.IT. Context usage example shows pattern &T.IT for TFTP transactions.](../concept/../../images/s009563.png) |
|||
tftp-put-filename (CTS) |
Matches the put filename in a TFTP session. 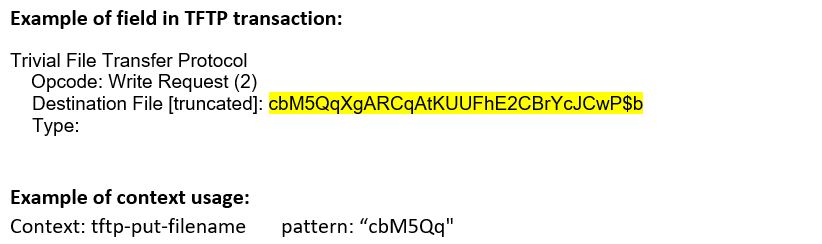 |
|||
