Snort IPS Signatures
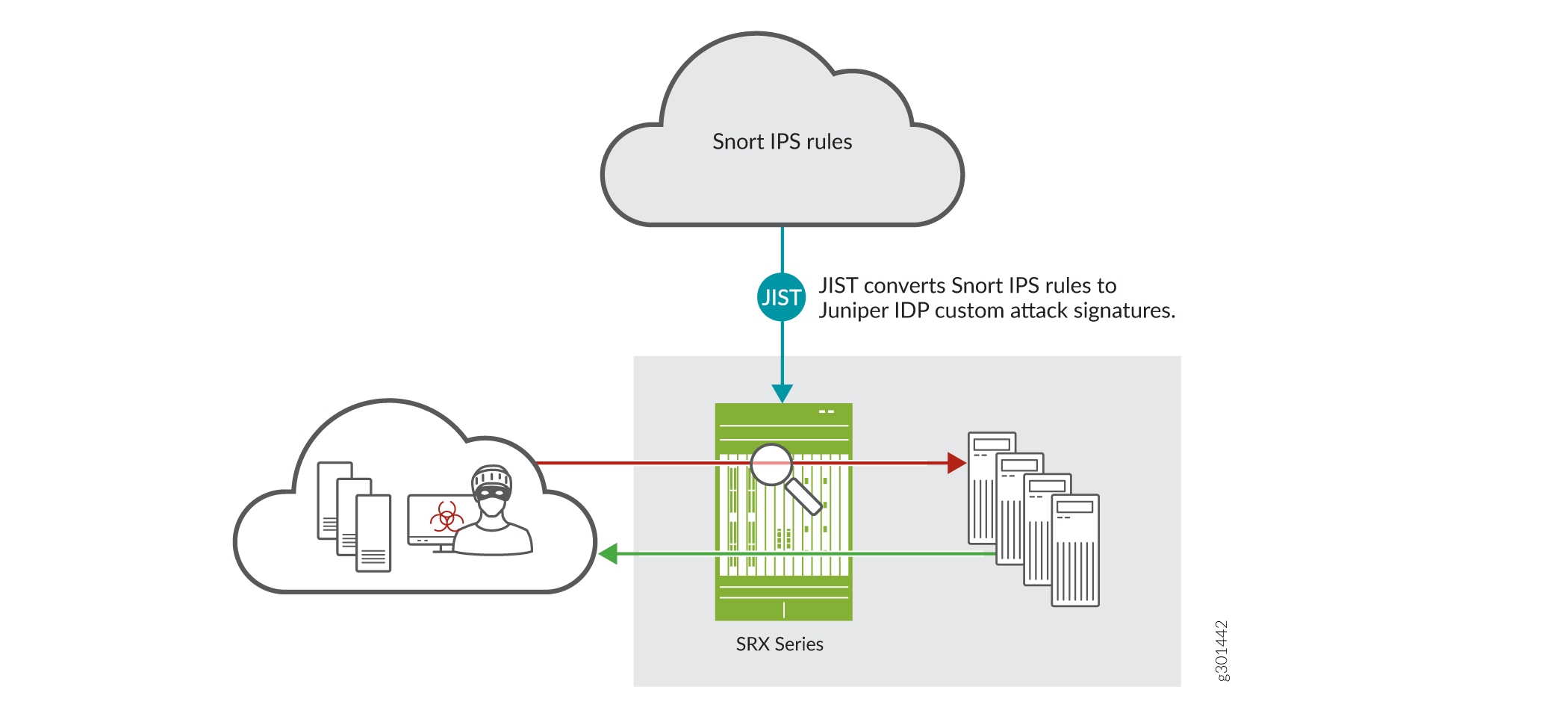
Juniper Networks IDP supports Snort IPS signatures. You can convert the Snort IPS rules into Juniper IDP custom attack signatures using the Juniper Integration of Snort Tool (JIST). These Snort IPS rules help detect malicious attacks.
IDP secures your network by using signatures that help to detect attacks. Snort is an open-source intrusion prevention system (IPS).
Figure 1: Snort IPS Signatures

Benefits of Snort IPS Signatures
- Help detect malicious attacks.
How Snort IPS works?
The JIST tool in Junos OS enables seamless integration with the following actions:
- JIST is included in Junos OS by default. The tool supports Snort version 2 and version 3 rules.
- JIST converts the Snort rules with snort-ids into equivalent custom attack signatures on Junos OS with respective snort-ids as the custom attack names.
- When you run the
requestcommand with Snort IPS rules, JIST generatessetcommands equivalent to the Snort IPS rules. Use therequest security idp jist-conversioncommand to generate thesetcommands as CLI output. To load thesetcommands, use theload set terminalstatement or copy and paste the commands in the configuration mode, and then commit. You can then configure the existing IDP policy with the converted custom attack signatures. - All the Snort IPS rule files that didn’t get converted are written to /tmp/jist-failed.rules. The error log files generated during the conversion are written to /tmp/jist-error.log.
- To view the jist-package version, use the
show security idp jist-package-versioncommand.
